Dr Rajiv Desai
An Educational Blog
ELECTRONIC VOTING
Electronic Voting:
_____
_____
Prologue:
Voting is the bridge between the governed and the government. The right to vote freely for the candidate of one’s choice is of the essence of a democratic society. Every voter’s vote is entitled to be counted once. It must be correctly counted and reported. The Voting System of a country consists of certain regulations which define how the preference of people is collected and how outcome of the polling process is indicating the will of people. A popular quote says that “It’s not the people who vote that count, it’s the people who count the votes.” Elections are a defining feature of democratic government, but all too frequently, we take the actual mechanics of the election for granted. We speak at length of such issues as who is allowed to vote, how campaigns are conducted, and how they are financed, but most people’s understanding of the actual voting process is something like the following: “You go to the polls, cast your vote, and then they count it and they announce the winner.” The focus should be on how you cast your vote, who they are who count it, how they go about counting it, and how the winner is determined.
In an age of electronic banking and online college degrees, why hasn’t the world gone to voting on touchscreen computers? In recent years, information technology has greatly affected all aspects of life, and to a large extent, this includes politics. In order to choose people to various positions different methods have been set up, with researchers continually trying to find improvement to the existing methods. The most recent method devised is electronic voting to phase out paper ballot. Voting technologies have a surprisingly long history. In the United States, mechanical lever voting machines were first used for elections in 1892 and were commonly used in U.S. elections until the 1990s. Electronic technologies began to appear in the 1960s with punch card counting machines. In the following decades, technologies such as DRE (direct recording electronic) voting machines, ballot scanning machines and Internet voting began to appear. The U.S. was at the forefront of adopting many of these technologies. Through the 1990s and the first decade of the new millennium, an increasing number of countries around the world also started to adopt these technologies. One must differentiate between electronic vote counting and electronic vote recording. Punch card and optical scanning machines count votes electronically but votes are recorded on paper ballots. DRE machines allow vote recording (e-ballot) and counting electronically. DRE machines are also called electronic voting machines (EVM) in many parts of the world, and Indian EVM is a stand-alone DRE. The marriage of technology and democracy in electronic voting goes some way towards shielding the counting from human interference. An indigenous EVM was introduced by the Election commission of India (ECI) to overcome the issues with manual voting which was slower and inefficient in the largest democracy, India. EVMs are being used in 20 countries, with six of these countries still piloting the technology. Globally, very different trends are seen in different regions. Europe and North America can be seen as moving away from the use of EVMs, while South America and Asia show increasing interest in using electronic voting technologies.
There is a simple reason as to why banking transactions and many other types of online transfers of value work: they can be verified. People can check if money was sent, e-mails were delivered or digitally encrypted and/or signed documents were decrypted or read by only the intended and so on. If the electronic transaction were tampered with, one would know. With election systems, however, the part about tampering is not fully solved. Most voting systems have as their cornerstone, the secrecy of the vote. Everyone knows who they voted for, but one cannot check that the eventual accounting of the votes was not tampered with because, in the simple case, one would be revealing his vote. Tamper-resistant and anonymous validations are active areas of research and there are some practical ideas that could address them, but issues of trust still remain. The criticality of the source code of electronic voting systems being open source, verifiable, rebuildable and repeatable is but a small step in the direction of trust.
______
A voting system is only as good as the public believes it to be.
–McGaley and Gibson, 2003
People will use insecure systems if they feel or think they are secure.
–Oostveen and van den Besselar, 2004
_______
_______
Abbreviations and synonyms:
E-voting = electronic voting
I-voting = internet voting = online voting
DRE = direct recording electronic (voting machine)
ECI = Election commission of India
EVM = electronic voting machine
NOTA = None of the above
VVPAT = Voter Verified Paper Audit Trail
EMB = Election Management Bodies
PCOS = precinct count optical scanning
NVT = new voting technologies
BU = ballot unit
CU = control unit
EBP = Electronic Ballot Printer
BMD = Ballot marking device
E2E-V = end-to-end (cryptographic) verifiability
CIA = Confidentiality, Integrity and Availability.
HAVA= Help America Vote Act
BEL = Bharat Electronics Limited
ECIL = Electronics Corporation of India Limited
OMR (Optical Mark Recognition) and OCR (Optical Character Recognition) are two methods of getting information from paper into a digital format. OMR can read the marks filled in circles but it can’t recognize the characters. OCR (Optical Character Recognition) recognizes all the characters from the paper document, collects and stores them into editable document. Both OMR and OCR are applied in electronic voting system.
_______
_______
Election and voting:
Democracy is government by the people. It is a continual participative operation, not a cataclysmic, periodic exercise. The heart of the democratic system is free and fair election periodically held, based on adult franchise. Elections are a vital part of democratic processes including, political transitions, implementation of peace agreements and consolidation of democracy. ‘Democracy’ and ‘free and fair election’ are inseparable twins. There is almost an inseverable umbilical cord joining them. In a democracy the little man – voter has overwhelming importance and cannot be hijacked from the course of free and fair election. His freedom to elect a candidate of his choice is the foundation of a free and fair election.
Elections are unique. They change the fate of nations, influence participation and activism in politics, and deeply affect the lives and attitudes of citizens. Elections demonstrate a clear importance for our society- so not only must election systems work; the people must believe that they work. Free and fair elections to choose political representatives are a cornerstone of a democracy and a fundamental human right of the people. Article 21 of the Universal Declaration of Human Rights (UDHR), states:
“Everyone has the right to take part in the government of his country, directly or through freely chosen representatives. Everyone has the right of equal access to public service in his country. The will of the people shall be the basis of the authority of government; this will shall be expressed in periodic and genuine elections which shall be by universal and equal suffrage and shall be held by secret vote or by equivalent free voting procedures.”
_
Stages of Election Process:
Whatever the jurisdiction and its specific characteristics, administering an election is a year-round activity, involving varying sets of people to carry out processes at different stages. These stages generally consist of the following:
- Voter registration.
Among other things, local election officials register eligible voters and maintain voter registration lists, including updates to registrants’ information and deletions of the names of registrants who are no longer eligible to vote.
- Absentee and early voting.
This type of voting allows eligible persons to vote in person or by mail before election day. Election officials must design ballots and other systems to permit this type of voting, as well as educating voters on how to vote by these methods.
- The conduct of an election.
Election administration includes preparation before election day, such as local election officials arranging for polling places, recruiting and training poll workers, designing ballots, and preparing and testing voting equipment for use in casting and tabulating votes, as well as election day activities, such as opening and closing polling places and assisting voters to cast votes.
- Vote counting.
At this stage, election officials tabulate the cast ballots; determine whether and how to count ballots that cannot be read by the vote counting equipment; certify the final vote counts; and perform recounts, if required.
As shown in figure below, each stage of an election involves people, processes, and technology.
Electronic voting systems are primarily involved in the last two stages, during which votes are cast and counted. However, the type of system that a jurisdiction uses may affect earlier stages. For example, in a jurisdiction that uses optical scan systems, paper ballots like those used on election day may be mailed in the absentee voting stage. On the other hand, a jurisdiction that uses DRE technology would have to make a different provision for absentee voting.
_
Not all votes are cast in traditional polling places on Election Day – an increasing number of voters vote absentee by mail or at in-person early voting facilities. All jurisdictions now provide accessible equipment for voters with disabilities. Most jurisdictions use different voting systems for these different voting stages. In American election voting, the majority of votes are cast in polling places. There are essentially two methods used to capture the voter’s selections: a paper ballot marked by the voter, either physically or through the use of an assistive ballot-marking device, or a software interface in which votes are recorded directly into computer memory. Most paper ballots cast are tabulated by optical scanners in the U.S., though there a significant number of jurisdictions that count paper ballots cast at polling places manually.
_
Figure below shows time-sequence of a typical voting process:
__
Generic voting principles:
- Only eligible persons vote.
- No person gets to vote more than once.
- The vote is secret.
- Each (correctly cast) vote gets counted.
- The voters trust that their vote is counted.
_______
Secret ballot:
Australian ballot, also called secret ballot, the system of voting in which voters mark their choices in privacy on uniform ballots printed and distributed by the government or designate their choices by some other secret means. Victoria and South Australia were the first states to introduce secrecy of the ballot (1856), and for that reason the secret ballot is referred to as the Australian ballot. The system spread to Europe and the United States to meet the growing public and parliamentary demand for protection of voters. The secret ballot, also known as Australian ballot, is a voting method in which a voter’s choices in an election or a referendum are anonymous, forestalling attempts to influence the voter by intimidation, blackmailing, and potential vote buying. The system is one means of achieving the goal of political privacy. Secret ballots are used in conjunction with various voting systems. The most basic form of secret ballot utilizes blank pieces of paper, upon which each voter writes his or her choice. Without revealing the votes to anyone, the voter would fold the ballot paper and place it in a sealed box, which is emptied later for counting. An aspect of secret voting is the provision of a voting booth to enable the voter to write on the ballot paper without others being able to see what is being written. Today, printed ballot papers are usually provided, with the names of the candidates or questions and respective check boxes. Provisions are made at the polling place for the voters to record their preferences in secret, and the ballots are designed to eliminate bias and to prevent anyone from linking voter to ballot. A problem of privacy arises with moves to improve efficiency of voting by the introduction of postal voting and electronic voting. Some countries permit proxy voting, which some argue is inconsistent with voting privacy.
_
Secrecy in voting by disabled:
Ballot design and polling place architecture often denies the disabled the possibility to cast a vote in secret. In many democracies disabled persons may vote by appointing another person who is allowed to join them in the voting booth and fill the ballot in their name. This does not assure secrecy of the ballot. ISG TopVoter, a voting machine which assures secret ballot for voters with disabilities as seen in the figure below:
_
Secrecy vs. reliability:
The United Kingdom secret ballot arrangements are sometimes criticized because it is possible to link a ballot paper to the voter who cast it. Each ballot paper is individually numbered and each elector (voter) also has a number. When an elector is given a ballot paper, their number is noted down on the counterfoil of the ballot paper (which also carries the ballot paper number). This means, of course, that the secrecy of the ballot is not guaranteed, if anyone can gain access to the counterfoils, which are locked away securely before the ballot boxes are opened at the count. Polling station officials colluding with election scrutineers may therefore determine how individual electors have voted.
This measure is thought to be justified as a security arrangement so that if there was an allegation of fraud, false ballot papers could be identified. The process of matching ballot papers to voters is formally permissible only if an Election Court requires it; in fact, the Election Court has never made such an order since the secret ballot was introduced in 1872, although reportedly prisoners in a UK prison were observed identifying voters’ ballot votes on a list in 2008. The legal authority for this system is set out in the Parliamentary Elections Rules in Schedule 1 of the Representation of the People Act 1983.
In the United States, sometimes the number on the ballot is printed on a perforated stub which is torn off and placed on a ring (like a shower curtain ring) before the ballot is cast into the ballot box. The stubs prove that an elector has voted and ensure that they can only vote once, but the ballots themselves are both secret and anonymous. At the end of voting day, the number of ballots inside the box should match the number of stubs on the ring, certifying that every ballot was cast by a registered elector, and that none of them were lost or fabricated. Sometimes the ballots themselves are numbered, making the vote trackable. In 2012, this procedure was ruled legal by Federal District Judge Christine Arguello in Colorado, who determined that the U.S. Constitution does not grant a right to a secret ballot.
Criticism:
Some people believe that the secret ballot enables election fraud and so should be eliminated or supplemented with other ways of verifying voting, such as cryptographically secure receipts.
_
The election system must be sufficiently robust to withstand a variety of fraudulent behaviors and must be sufficiently transparent and comprehensible that voters and candidates can accept the results of an election. The design of a “good” voting system, whether electronic or using traditional paper ballots or mechanical devices must satisfy a number of competing criteria. The anonymity of a voter’s ballot must be preserved, both to guarantee the voter’s safety when voting against a malevolent candidate, and to guarantee that voters have no evidence that proves which candidates received their votes. The existence of such evidence would allow votes to be purchased by a candidate. The voting system must also be tamper resistant to thwart a wide range of attacks, including ballot stuffing by votes and incorrect tallying by insiders.
_____
Electoral frauds:
Electoral fraud, sometimes referred to as election manipulation or vote rigging, is illegal interference with the process of an election, either by increasing the vote share of the favored candidate, depressing the vote share of the rival candidates, or both. What exactly constitutes electoral fraud varies from country to country. Voting procedures play a significant role in the conduct of free and fair elections in a democracy. It converts voters’ preferences into a political mandate which in turn forms the basis for policymaking. In practice, however, illegal efforts to shape electoral outcomes in a democracy are not uncommon (Lehoucq, 2003). Electoral fraud not only undermines public trust in democratic institutions by electing political leaders that have the greatest capacity to organize electoral fraud but it also adversely affects the provision of public goods. In presence of electoral fraud, there are no checks and balances on the political leaders to stop them from spending disproportionately on private goods, at the expense of public goods, to buy the loyalty of a small fraction of people with whose support they commit the fraud. Electoral frauds such as false voter registration, voter intimidation, and irregularities in tallying procedures are clandestine and illegal efforts to shape election results (Lehoucq 2003). Due to their illicit nature, it’s hard to study the effects of these practices as political agents are careful not to leave trails. One of the reasons behind controversies associated with the choice of voting technology is that there is little systematic empirical evidence on the relationship between voting technology and election outcomes. Electoral fraud undermines public trust in democratic institutions creating political instability, and may affect long-term growth.
In India, the largest democracy with more than 800 million registered voters and a complex multi-party system, electoral fraud has been one of the leading causes of concern. For example, in several constituencies under the paper ballot system, polling booths would be captured, and ballot boxes would be stuffed (Verma, 2005). Among various forms of electoral violation, such as multiple voting, vote buying, and voter intimidation, booth capturing is a major concern. Srinivas (1993) attributed the rise in violence in the early 90s to the politico-economic system and especially to booth capturing. Booth capturing involves “criminal groups, delegated by political parties, capturing a polling station and stuffing the ballot box with large numbers of votes for the favored candidate” (Herstatt and Herstatt 2014). To address frauds and simplify the electoral procedure, the Election Commission of India (ECI) introduced electronic voting machines (EVMs) in the late 90’s. An important feature of the EVMs was that it could register only five votes per minute. This feature had significant adverse implications for electoral fraud as polling booths had to be captured for a longer period to rig elections, thereby significantly increasing the cost of electoral fraud. Besides enhancing the fairness of the electoral process, the ECI also envisaged that EVMs would improve the efficiency of tallying the electoral results thereby reducing the incidence of human error.
_
It has been documented that vote buying and vote selling is very prevalent in real world election voting. In Mexico, voters were so suspicious about the integrity of elections because of the electoral fraud committed by parties (Dominguez & James, 1998). Such fraud relied on many techniques including ballot stuffing by both voters and electoral officials; stealing of ballot boxes between the polling units and collation centers; intimidation of voters, observers and party officials; and manipulating voter’s registration lists (Ferree, Gibson, & Long, 2014; Asunka, Brierley, Golden, Kramon, & Ofosu, 2013; Craig & Cornelius, 1995; Heskey & Bowler, 2005). Vote buying, selling and coercion is common practice in elections. In an analysis done in Taiwan (Nichter S., 2014) as little as $10 was paid to voters to sell their votes. This is not surprising because of the economic situation in many countries, and vote buyers usually target poor voters. In the USA five Democratic Party Operatives were convicted in a federal court in 2004 for offering poor people cigarettes, medicine, beer and $5 to $10 dollars for their votes (Nichter S., 2008). In other cases, electoral officials are part of this electoral fraud. A report about the 2012 elections in Ghana recorded issues like double voting, under age voting, over voting and voting by ineligible individuals (Asunka, Brierley, Golden, Kramon, & Ofosu, 2013). This was possible because the poll-site officials were trusted to prevent this. These issues are difficult to address solely by human supervision because the trusted polling officials are sometimes part of the fraud, usually for financial gain.
Voting systems cannot prevent all forms of electoral fraud since there is always a financial incentive to cheat the system due to socio-economic challenges. However, design of voting systems should take these threats into account and leverage on technical security wherever possible to ensure that any deliberate attempt to circumvent the technology is detected.
_____
Electoral integrity:
Electoral integrity refers to international standards and global norms governing the appropriate conduct of elections. These standards have been endorsed in a series of authoritative conventions, treaties, protocols, and guidelines by agencies of the international community, notably by the decisions of the UN General Assembly, by regional bodies such as the Organization for Security and Cooperation in Europe (OSCE), the Organization of American States (OAS), and the African Union (AU), and by member states in the United Nations. Following endorsement, these standards apply universally to all countries throughout the electoral cycle, including during the pre-electoral period, the campaign, on polling day, and in its aftermath.
______
Trust in voting system:
Today’s political climate is riven with discontent and mistrust of the institutions of government, yet apart from public discourse, the vote is still how we make our will known. Mistrust in lawmakers or institutions may be nearly endemic, but we still rely on the principle that they can be voted out. When our voting systems fail though, voters lose trust in the electoral process, and that is corrosive. Without that trust, our democracy could crumble. In such an environment, it is of critical importance that we safeguard that most fundamental part of our democracy by ensuring voting systems work properly and that it is possible for those responsible for operating our elections to demonstrate to the public that their votes indeed are being captured and counted as they intended, and that the outcomes are correct.
In the U.S. many states use unreliable and insecure electronic voting machines, and many states have made their situation worse by adding some forms of Internet voting for some voters, which cannot be checked for accuracy at all. Even in states where verifiable systems are used, too often the check on the voting system’s function and accuracy is not done. The voting equipment now in use are aging; resources are severely impacted by the state of the economy over the past several years; shortages of both equipment and human resources are likely. After all the effort necessary to overcome the other hurdles to casting a ballot, it is patently unfair that once you get to the ballot box, that the ballot itself fails you. Taken together, these problems threaten to silently disenfranchise voters, potentially in sufficient numbers to alter outcomes.
_____
None of the above (NOTA):
“None of the above”, or NOTA for short, also known as “against all” or a “scratch” vote, is a ballot option in some jurisdictions or organizations, designed to allow the voter to indicate disapproval of the candidates in a voting system. It is based on the principle that consent requires the ability to withhold consent in an election, just as they can by voting “No” on ballot questions. On 27 September 2013, the Supreme Court of India ruled that the right to register a “none of the above” vote in elections should apply, and ordered the Election Commission to provide such a button in the electronic voting machines, noting that it would increase participation. The Election Commission also clarified that even though votes cast as NOTA are counted, they are considered as invalid votes so they will not change the outcome of the election process. They are not taken into account for calculating the total valid votes and will not be considered for determining the forfeiture of deposit. In the 2014 general election, NOTA polled 1.1% of the votes, counting to over 6,000,000. Blank votes may be cast for several different reasons. In many cases it is argued that blank votes are cast by voters who are unhappy with the election or with the system itself, or by voters who are truly indifferent to the options available because of lack of knowledge or because none of the options match the preferences of the voter.
______
Vote counting:
There exist various methods through which the ballots cast at an election may be counted to obtain one or more winners.
- Manual counting:
Manual counting requires a physical ballot that represents voter intent. The physical ballots are read and interpreted; then results are individually tabulated. This method is used in Sweden for example, and conducted as follows. The voter casts three ballots, one for each of the three elections (national, regional, and local), each in a sealed envelope. The party and candidate names are pre-printed on the ballot, or the voter can write them in on a blank ballot. When voting has finished, all envelopes are opened on the counting table, for one election at a time. They are sorted in piles according to party, inspecting them for validity. The piles are then counted manually, while witnesses around the table observe. The count is recorded, and the same pile is counted again. If the results do not agree, it is counted a third time. When all piles are counted and the results agree, the result is certified and transmitted for central tabulation. The count as received is made public, to allow anyone to double-check the tabulation and audit the raw data. There appears to be a high level of confidence in this system among the population, as evidenced by the lack of criticism of it. Such a system may be used for recounts in areas where mechanical or automated counting systems are used.
- Electromechanical and Optical scan counting:
Paper ballots, typically punched cards or marksense (optical scan ballot), are collected and fed into a machine to tabulate vote totals. Tabulation can occur with each individual ballot, or in batches.
- Direct-recording voting (mechanical) counting:
Voters selecting switches (levers), pushing plastic chips through holes, or pushing mechanical buttons which increment a mechanical counter (sometimes called the odometer) for the appropriate candidate voting.
- Direct-recording electronic counting:
Voting data and ballot images are recorded in memory components. Tabulation of the voting data stored in a removable memory component and as printed copy. The system may also provide a means for transmitting individual ballots or vote totals to a central location for consolidating and reporting results from precincts at the central location. This consolidation can be any subset of machines, such as all voting machines in a polling station, or all voting machines in a precinct etc.
Note:
Precinct is one of several districts into which a city or town is divided for voting; each contains one polling place.
_____
Election recount:
An election recount is a repeat tabulation of votes cast in an election that is used to determine the correctness of an initial count. Recounts will often take place in the event that the initial vote tally during an election is extremely close. Election recounts will often result in changes in contest tallies. Errors can be found or introduced from human factors, such as transcription errors, or machine errors, such as misreads of paper ballots. Alternately, tallies may change because of a reinterpretation of voter intent.
United States:
Of the 4,687 statewide general elections held from 2000 to 2015, 27 were followed by a recount, and only three resulted in a change of outcome from the original count: Washington gubernatorial election, 2004, Vermont Auditor of Accounts election, 2006, and United States Senate election in Minnesota, 2008.
Recount methods:
- Machine recount:
A machine recount is a retabulation of ballots cast during the election. This can be done using an optical scan voting system, punched card system or DRE voting machine. With document-based Ballot Voting Systems, ballots are counted a second time by some form of machine. With Non-document-based Ballot Voting Systems officials will recollect vote data from each voting machine which will be combined by a central tabulation system.
- Manual recount:
A manual or “hand” recount involves each individual physical representation of voter intent being reviewed for voter intent by one or more individuals. With DRE voting machines, a voter-verified paper audit trail (VVPAT) is examined from each voter. For some DREs that do not generate a VVPAT, images can be printed for each ballot cast and counted individually.
_____
_____
Electoral Systems:
A country’s electoral system is the method used to calculate the number of elected positions in government that individuals and parties are awarded after elections. In other words, it is the way that votes are translated into seats in parliament or in other areas of government (such as the presidency). There are many different types of electoral systems in use around the world, and even within individual countries, different electoral systems may be found in different regions and at different levels of government (e.g., for elections to school boards, city councils, state legislatures, governorships, etc.). Some electoral systems elect a single winner to a unique position, such as prime minister, president or governor, while others elect multiple winners, such as members of parliament or boards of directors. There are a large number of variations in electoral systems, but the most common systems are first-past-the-post voting, the two-round (runoff) system, proportional representation and ranked or preferential voting. Some electoral systems, such as mixed systems, attempt to combine the benefits of non-proportional and proportional systems. Please read my article ‘The farce of democracy’ on this website at https://www.drrajivdesaimd.com/2010/03/01/the-farce-of-democracy/ posted in March 2010. It delineates various electoral systems and its pitfalls.
_
Figure above shows the map of electoral system for national legislatures, as of 2012. Red is first-past-the-post; maroon two-round runoff; puce instant runoff; dark blue winner-optimized proportional; orange plurality-at-large; brown general ticket; yellow single non-transferable; citron modified cumulative; lime Borda count; light blue party-list proportional; mint single transferable; purple and lavender mixed-member proportional; and dark pink, persian rose, fuchsia, and light deep pink are parallel voting.
______
______
Voting methods:
_
Figure below shows different voting methods:
_
Voting Method is a fundamental aspect of election administration and management. The fashion in which a voter exercises his/her right to vote, keeping in mind the quotients of secrecy, verifiability and transparency, is a crucial component of elections. With the advancement of technology in our contemporary times, voting methods have also escalated new heights with newer innovations entering the world of electoral processes. Selection of an appropriate voting method which is trustworthy for all stakeholders in a participatory electoral democracy, however, constitutes a permanent debate among experts and policy makers of election administration across the globe. Different democracies have adopted different voting methods over time depending on their specific historical conditions and legal-constitutional provisions.
_
Voting methods are as old as the practice of election. The idea of ‘election’ goes back to approximately 508 B.C in Ancient Greece. The term election has evolved from the Greek word eklektos meaning ‘picked out/ chosen/ selected’. And the formal act of this ‘picking out/ choosing/ selecting’ out of ‘two or more candidates or courses of action’ done through a definite method is therefore called ‘voting’. In ancient Athenian polity, there used to be different methods of voting. The most common method was ‘show of hands’ by men as mark of support in favor of a decision in the assembly which used to meet once in a month. Another method was that the voters had to drop a clay or 2 metal tokens issued to them in a clay pot which served as a ballot box. Interestingly, there was also a practice of holding ‘negative election’ in ancient Greece where the male landowners used to vote for political leader(s)/ candidate(s) whom they wanted to be exiled. In negative election, the voters used to write their choice on broken pieces of pots. Similar examples can be traced in the annals of ancient Indian history. In between 8th and 16th century, there used to be electoral systems, functional at the level of ‘Saba’ in the kingdoms of the southern part of Indian sub-continent under the Cheras, Cholas, Pallavas, Pandyas and Vijaynagar dynasties. The members of the Saba were elected by the entire village community through a system called Kudu Olai (Kudu meaning ‘Pot’ and Olai meaning ‘Palm Leaf ’). A village was divided into kudumbus or wards and each ward had to write the name of the eligible person on a palm leaf (olai) and then drop it in a pot (kudu). Popular democratic electoral systems also existed under the Chola dynasty in 920 A.D. which we know from the Uttaramerur inscription found in present day Tamil Nadu. There are also examples of democratic political organizations and associations which emerged under the influence of Buddhism like the gana and the sangha.
__
Paper Ballots:
One of the early definitions of paper ballot was provided in the Tennessee Acts of 1796 (U.S.A) which says:
“A ballot is a ticket or scroll of paper, purporting to express the voter’s choice, given by the voter to the officer or person holding an election, to be put in the ballot box”. In U.S.A., the early ballot papers were paper slips provided by the voters themselves on which they used to write their choices before dropping them in the ballot boxes. This practice was soon replaced by pre-printed paper ballots which were distributed by political parties and candidates. Such a use of ballot papers had its own set of disadvantages. Firstly, the element of voter privacy could be compromised. It was possible that the voter could write his name/ signature on the ballot to disclose his identity or the paper ballots may be printed of a particular colour for easy identification. The use of such ballot papers came with higher chances of electoral malpractices like stuffing of ballot boxes with unlawful votes. Moreover, there were also possibilities that the polling officers, to whom the voters used to handover the ballots, could manipulate with the ballots. However, in spite of multiple disadvantages, this type of voting method was followed till the late 19th century. In the United Kingdom, the traditional voting method was open voting where there was no secrecy quotient. It was only after the Ballot Act, 1872 that secret ballots were introduced.
First used in the Australian state of Victoria in 1856, the paper ballot listing all the candidates was first known as “the Australian ballot.” The modern system of election using paper ballots was first used in 1856 in Australia. The great Australian innovation was to print standardized ballots at government expense, distribute them to the voters at the polling places, and require that the voters vote and return the ballots immediately. Today, the security against election fraud this provides seems obvious, but in the 19th century, it was not obvious to most observers, and it was not until 1888 that this ballot was used in the United States.
American elections have been evolving since the nation was founded. Voting rights have been revised and extended by four constitutional amendments and several judicial and legislative actions. The voting process itself has changed continuously over the last two hundred years. The earliest elections were conducted by voice vote or with paper ballots put into ballot boxes. These paper ballots, called party tickets, listed names from just one party. The voter was essentially just a conduit for the straight ticket voting demands of the party. As the United States grew and the electorate expanded in the decades following the Civil War, improvements appeared in the form of the Australian or blanket ballot (which listed the names of all candidates), and ballot boxes with new security features. In 1888, the first “Australian Secret Ballot” was adopted in Massachusetts. The “Australian Ballot” is an official ballot printed at public expense on which the names of all nominated candidates appear. It is distributed only at the polling place and voted in secret. Paper ballots use uniform official ballots on which the names of all candidates and issues are printed. Voters record their choices, in private, by marking the boxes next to the candidate or issue choice they select and drop the voted ballot in a sealed ballot box. Numerous other revisions to the voting process have taken place, the most recent of which include the adoption of postcard mail-in voter registration, vote-by-mail absentee ballots, optical-scan ballots and computerized touch-screen voting systems.
Paper Ballots that are hand counted:
Paper ballots are the simplest to understand; they can preserve the anonymity of the voter; voters can be confident that their votes have been correctly recorded; and recounting of votes is possible. Paper votes are immune to all kinds of cyberattacks and there is no malware that can steal them while appropriate safeguards can be put in place to prevent and detect human mischief. Hence this system has transparency, verifiability and accountability. But there are usually a worrying number of invalid votes and hand counting is a laborious and time-consuming process, especially in a country like India where population is very high and literacy level is low. An invalid vote is a vote which doesn’t count towards the final election result as voter’s intention cannot be clearly determined. The risk of booth capture and stuffing of ballot papers has been drastically reduced with enhanced police security for polling stations in India.
Data from international institute for democracy and electoral assistance’s voter turnout database shows that the global average proportion of invalid votes is slightly less than three per cent. The same data also indicates that there are, on average, fewer invalid votes in presidential elections than parliamentary ones, as well as slight geographical variation. It is also pointed out that even a level around the three to four per cent mark can be contentious in a very close election. A look at the Indian data shows that of 35,937 constituencies that went to the Assembly polls between 1961 and 2003, nearly 4,993 saw the polling of more invalid votes than the margin between the winner and the runner-up. This is a rather huge number suggesting that invalid votes could have affected even the final formation of the government in some States.
_
Alternative to paper ballot system:
The search for alternative voting methods in the United States was motivated by two factors. First, the entrenched political machines of late 19th century America learned quite quickly how to craft the laws governing the counting of votes under the rules of the Australian ballot so that those laws favored the entrenched political machine. One of the classic approaches to subverting any election technology is to take control of the vote count. In the case of any physical ballot involving marks on paper, there will be marks that are on the borderline between acceptable and unacceptable votes, and vote counting rules that allow selective counting of marginal marks lie at the heart of a broad class of election rigging. The most widely used approach to this is based on objective and uniform standards for counting votes. If carefully chosen, these standards allow a skilled participant in the vote count to disqualify votes based on technicalities even when there is a clear indication of voter intent. Michigan’s law governing the validity of ballot markings on hand counted paper ballots illustrates this approach remarkably well. By carefully controlling the makeup of the vote counting teams, the party in power can use these objective rules to selectively exclude votes for the opposition. Specifically, the party in power must ensure that the representatives of the opposition on each vote counting team are relatively poorly trained, while their own representatives trained to aggressively apply the rules only to ballots containing votes for the opposition while accepting obvious voter intent on ballots favoring their side. According to the 1910 Encyclopedia Britannica entry for voting machines, it was common in many jurisdictions for as many as 40 percent of votes to be excluded in the count!
The second problem unique to the American system is the institution of the general election. Paper ballots are easy to count if there are only a few offices on the ballot, with only a few candidates per office, as is the norm in most parliamentary democracies. In American general elections, it is common to find well over 30 candidates on one ballot, divided between 8 to 15 offices, and this was the case even before the advent of ballot initiatives! An accurate hand count for ballots of this complexity is both difficult and time consuming.
_
Voting Machines:
The alternative to paper ballots is the voting machines. The first image of voting machine, designed by Benjamin Jolly, can be traced back to 1838 in the pamphlets published by the London Working Men’s Association in the People’s Charter. In Jolly’s voting machine, there were a number of holes on the top corresponding to the names of the candidates. The voter had to drop a brass ball in one of the hole of his choice which after passing through the machine dropped into a tray on the front of the machine in front of judges. The voter couldn’t drop more than one ball as the judges could see it after each vote cast. The voter in this system could vote behind a partition.
_
Mechanical Lever Machines:
In the second half of the 19th century, lever voting machine was designed and developed. The Myers Automatic Booth Lever Voting Machine, designed by Jacob H. Myers, was first used in 1892 in New York. On mechanical lever voting machines, the name of each candidate or ballot issue choice is assigned a particular lever in a rectangular array of levers on the front of the machine. A set of printed strips visible to the voters identifies the lever assignment for each candidate and issue choice. The voter enables the machine with a lever that also closes a privacy curtain. The voter pulls down selected levers to indicate choices. When the voter exits the booth by opening the privacy curtain with the handle, the voted levers are automatically returned to their original horizontal position. As each lever returns, it causes a connected counter wheel within the machine to turn and record the voter’s choice. Interlocks in the machine prevent the voter from voting for more choices than permitted. By 1930, lever machines had been installed in virtually every major city in the United States, and by the 1960’s well over half of the Nation’s votes were being cast on these machines. Mechanical lever machines were used by 12.8% of registered voters in the United States as of the 2004 Presidential election. These machines are no longer made and are being replaced with newer electronic systems.
_
From Mechanical to Electronic Systems:
_
Punched Cards:
The first new technology to effectively challenge lever voting machines was the now infamous Votomatic voting machine. In the early 1960s new computer-read ballot systems entered the market for voting equipment and eventually triumphed over mechanical machines. Voters used either a stylus or punch to perforate a computer punch card ballot or mark a standardized form. Punchcards were used first in the 1964 Presidential election. By 1982, approximately half of the American electorate was voting by punch-card system. In the 2004 Presidential election, some variation of the punchcard system was used by 18.6% of registered voters in the United States.
The Votomatic ballot and the more recent mark-sense ballot both represent a return to the Australian secret ballot, but with the added benefit of an automated and, we hope, impartial vote count produced using tabulating machinery. With this return to paper ballots, we gained the ability to recount the vote in the event there is a challenge, but we also introduce the question of how to interpret marginal votes. Almost everyone is an expert at interpreting marks on paper. As a result, we can easily distinguish intentional marks from smudges or defects in the paper. This expertise is a key element in our ability to conduct a hand recount of paper ballots, and it fails utterly when the time comes to recount punched cards. With a punched card, a piece of dangling or pregnant chad is the analog to a smudge or an accidental pencil tick. None of us have the wealth of experience interpreting chad that almost all of us have with marks on paper!
From a legal perspective, a ballot is an instrument, just like a deed or a check. When the ballot is deposited in the ballot box, it becomes anonymous, but just prior to the moment when the ballot is deposited, it ought to be possible to hand the ballot to the voter and ask “does this ballot properly represent your intent?”. Votomatic punched card ballots fail this simple test! While the ballot is in the Votomatic machine, the voter can punch holes in it but is unable to see the ballot itself. Once removed from the machine, the voter can see the holes, but without the ballot labels printed on the machine, the voter is unable to tell what those holes mean. The problems with Votomatic ballots were severe enough that, by the early 1970s, IBM abandoned the technology, and in 1988, the National Bureau of Standards published a report by Saltman recommending the immediate abandonment of this technology. By that time, punched card voting was the most widely used voting technology in the United States, and problems quite similar to many of the problems encountered in Florida election had been encountered in many local elections.
_
2000 presidential election in Florida:
Punched cards received considerable notoriety in 2000 when their uneven use in Votomatic style systems in Florida was alleged to have affected the outcome of the U.S. presidential election. Invented by Joseph P. Harris, Votomatic was manufactured for a time under license by IBM. William Rouverol, who built the prototype and wrote patents, stated that after the patents expired in 1982, lower quality machines had appeared on the market. The machines used in Florida had five times as many errors as a true Votomatic, he said.
Punched-card-based voting systems, the Votomatic system in particular, use special cards where each possible hole is pre-scored, allowing perforations to be made by the voter pressing a stylus through a guide in the voting machine. A problem with this system is the incomplete punch; this can lead to a smaller hole than expected, or to a mere slit in the card, or to a mere dimple in the card, or to a hanging chad. This technical problem was claimed by the Democratic Party to have influenced the 2000 U.S. presidential election in the state of Florida; critics claimed that punched card voting machines were primarily used in Democratic areas and that hundreds of ballots were not read properly or were disqualified due to incomplete punches, which allegedly tipped the vote in favor of George W. Bush over Al Gore.
_
Optical Mark Sense Ballots (optical scans):
The oldest optical-scan voting systems scan ballots using optical mark recognition scanners. Optical mark-sense voting systems were developed in the early 1970’s by American Information Systems of Omaha, alternately in competition with and in cooperation with Westinghouse Learning Systems of Iowa City. The latter was the licensee of the University of Iowa’s patents on the optical mark-sense scanning machine. Optical scan voting systems use a ballot card on which candidates and issue choices are preprinted next to an empty rectangle, circle, oval, or an incomplete arrow. Voters record their choices by filling in the rectangle, circle or oval, or by completing the arrow. After voting, the voters either place the ballot in a sealed box or feed it into a computer tabulating device at the precinct. The tabulating device reads the votes using “dark mark logic,” whereby the computer selects the darkest mark within a given set as the correct choice or vote. Essentially the only advantage of mark-sense technology over punched card technology is that it uses marks on a printed paper ballot. This is an important advantage! This means that no special machines are required to vote on the ballot, it means that, with proper ballot design, a voter can easily verify that the markings on the ballot exactly convey his or her intent, and it means that, during a hand recount, no special expertise is required to interpret the intent of the voters. Unfortunately, the first generation of optical mark-sense voting machines was extremely sensitive to the particular type of pen or pencil used to mark the ballot, and to the exact details of the mark itself. As a result, early machines, including many still in use today, had real difficulty distinguishing faint deliberate marks from smudged erasures, and they tended to have mark sensing thresholds that required a fairly dark mark. The newest generation of optical mark-sense readers uses visible wavelength image processing technology instead of simple infrared sensors to read the marks. Many of the more recent offerings use either FAX machine scanning mechanisms or computer page-scanning devices to obtain the image of the ballot, and they operate by finding each marking target before they search the target for acceptable marks. Such machines can easily ignore relatively dark smudged erasures while catching relatively faint deliberate marks.
_
Touch Screen Voting:
Introduced in the 1990s, computer touch screen and direct recording electronic (DRE) voting systems use familiar graphic layouts and capture votes digitally. The most recent development in the evolution of voting systems is direct recording electronic, or DRE’s. They are an electronic implementation of the old mechanical lever systems. As with the lever machines, there is no ballot; the possible choices are visible to the voter on the front of the machine. The voter directly enters choices into electronic storage with the use of a touch-screen, push-buttons, or similar device. An alphabetic keyboard is often provided with the entry device to allow for the possibility of write-in votes. The voter’s choices are stored in these machines via a memory cartridge, diskette or smart-card and added to the choices of all other voters.
Direct Recording Electronic (DRE):
In 2000, after the dispute on the voting method in the USA presidential elections, the voting method was reviewed. Accordingly, Direct Recording Electronic (DRE) Systems (like the widely used AccuVote TS developed by Premier Election Solutions, commonly called Diebold) were introduced. DRE Systems uses one of three basic interfaces (pushbutton, touchscreen or dial) through which voters record their votes directly into computer memory. The voter’s choices are stored in DREs via a memory cartridge, diskette or smart car. Some DREs can be equipped with Voter Verified Paper Audit Trail (VVPAT) printers. The direct recording electronic method, DRE, uses a voting machine with the candidates printed on a computer screen. The voters push a button or the appropriate spot on the surface to record their choices. Those wishing to write-in a candidate are able to use a keyboard to type the name. In 2004, 28.9% of the registered voters in the United States used some type of direct recording electronic voting system.
The newest voting technology uses direct-recording electronic voting machines. These were developed after microcomputers became sufficiently inexpensive that they could be incorporated into a voting machine. Much of the rhetoric today about voting system reform asks why we can’t have voting machines that are as ubiquitous and convenient as automatic teller machines. This turn of phrase is a reference to the newest generation of direct-recording voting machines; these make no attempt to emulate earlier technology; physically, they are little more than repackaged personal computers with touch screen input and special software to make them function as voting systems.
All of today’s direct-recording voting machines attempt to offer far stronger audit and security tools than the old lever machines they functionally replace. Instead of simply storing vote totals on odometer wheels inside the machine, they store an electronic record called a ballot image recording each voter’s choices, and they store an audit trail of all actions involving the machine, from pre-election testing to the printing of vote totals after the polls close. These records are stored in duplicate form, for example, in a hard drive in the machine as well as in a removable memory pack of some kind or on an adding machine tape inside the machine. Should any disaster strike or should a recount be requested, it should be possible to recover all votes that have been cast on such a machine.
Unlike any system resting on paper ballots, none of the information stored inside a direct-recording electronic voting machine can be said to have the status of a legal instrument. Instead, the record is created by the software within the voting machine in response to the voter’s actions, and the record is only as trustworthy as the software itself. It is far from easy to test and inspect software to assure that it functions as advertised, and it is far from easy to assure that the software resident in a machine today is the same software that was authorized for use in that machine months or years ago.
_
EVM from DRE:
Electronic Voting Machine (EVM) is a simple electronic device used to record votes in place of ballot papers and boxes which were used earlier in conventional voting system. From stand-alone direct recording electronic (DRE) machines comes the electronic voting machines (EVM) used in Indian elections. These stand-alone machines have no possibility of any kind of network connectivity and the voters cast their votes at an assigned polling station on the day of election under strict administrative security ensured by the Election Commission of India. The Indian EVMs also have a Voter Verified Paper Audit Trail (VVPAT) which helps the voter to confirm her vote. In Brazil, which claims to be the first country to deploy nationwide electronic voting, the machines used in elections are called ‘Electronic Ballot Boxes’ which are stand-alone direct electronic recording systems. Venezuela uses stand-alone voting machines (SATIS) manufactured by Smartmatic which were fully implemented across the nation in 2004.These machines are distinctively different from the other forms of Internet Voting and Optical Scanners.
_
Voting By Mail:
Voting-by-mail is relatively new. This method was first tried in Monterey, California in 1977. Since that time, hundreds of elections have been held by mail – from local ballot initiatives to some contests for federal office. Supporters argue that voting by mail is more convenient for voters and minimizes costs of administering an election. They also say that it increases voter turnout. In Washington state average turnout increased from 38 percent to 53 percent in counties that used mail. One county saw its turnout increase to 68 percent, another county’s turnout – in a primary – increased to nearly 72 percent.
_
Internet voting:
Internet Voting is where the voting system is networked for recording and counting of votes. This type of voting can be done either online or through a machine kept at a designated polling station. In U.S.A, there are four types of internet usage for election management, viz. (i) online distribution of blank ballots; (ii) internet marking of ballot and return; (iii) online marking of ballots; and (iv) internet-based marking of ballots recorded as with a DRE device.
Internet voting systems fall into several categories like poll site, kiosk, and remote. Each defines the location where the ballot is cast and relates directly to the technical challenges inherent in that system. Poll Site Internet Voting is seen by many as the most likely first step, increasing the efficiency of voting and avoiding the problem of lack of universal access to the Internet from voters’ homes. Still, security and other technological issues have not been resolved to the satisfaction of most experts. Kiosk Voting Machines could be located in convenient locations such as malls, libraries and schools. They also could increase Internet access, but pose specific security and privacy concerns. Remote Voting would allow individuals to vote from virtually any location with an Internet connection. While this has substantial benefits it also possesses substantial security risks that are likely to take much research and debate to adequately resolve.
Some advocates of Internet voting argue that Internet voting might encourage greater political participation among young adults, a group that stays away from the polling place in droves. It would hold special appeal for military personnel overseas, whose ability to vote is a growing concern. There are serious concerns, however, regarding computer security and voter fraud, unequal access across socioeconomic lines (the “digital divide”), and the civic consequences of moving elections away from schools and other polling places and into private homes and offices.
_______
_______
Introduction to electronic voting:
_
The birth of democracy was in Athens in the sixth century B.C. where the first form of electoral laws was introduced. Since that time, electoral systems have been designed and developed according to the characteristics of the countries in democratic governments around the world. Voting systems have evolved in response to the problems and the needs of political systems. In many countries, interest in e-Voting is growing very rapidly. The number of e-Voting experiments taking place is also growing with different approaches and motivations of each country. By closely studying these experiences, it is possible to learn new and interesting lessons, lead to different schemes, and create a valid e-Voting system.
E-Voting machines were in use in the Netherlands for 20 years, with nearly the whole population vote using one of the DRE voting systems available to vote. The introduction of this technology in the 1980s was not preceded by a public debate. In 2006, 90% of all votes in the Netherlands were expressed on the computer. The idea of e-Voting was introduced to Estonia in 2001. Their vision was to introduce Vote-over-Internet (VoI) in uncontrolled environments. Although at first they thought VoI could be used in the 2002 elections, they had to wait until 2005 to be a real option VoI in local elections. The first objective of VoI is to increase the participation maintaining voter interest in voting and increasing the interest of the younger generation. The other objective is to stay in touch with modern Information and Communication Technology (ICT) and facilitate voting. In 2002, the first e-Voting was conducted in Japan. Since then, ten local governments have conducted a total of twenty cases of e-Voting. In Japan, after “e-Japan Strategy”, which aims to build an e-Government, was released in January 2001; many e orts of an e-Government and e-Democracy have been attempted. E-Voting can be seen in this trend. In Korea, the participation rate is declining, a fact led some to find a way to increase the participation rate. But an increase in the participation rate does not necessarily promote the quality of the representation itself. Due to the disproportionate representation in society, it can also over-represent the group that has been over-represented while an underrepresented group becomes more under-represented. Therefore, improving the quantitative representation only make sense if the qualitative representation is made at the same time.
_
Traditional voting systems were based on paper process. Electorate has to visit physically at election center to cast their vote. At election center electorate present his identity proof in front of election conducting representatives at that particular center. When authentication is completed, electorate is allowed to take a list of representatives (which is on printing paper) and put a stamp on his/her choice. Electorate fold this printing paper and put in box popularly known as Ballot box. Representatives will put a mark on nails of electorate to prevent duplicity or fraud by an electorate.
In the last decade, we have observed a shift from paper forms to their contemporary electronic equivalents. Many services that once required a citizen to physically present himself at a counter and fill out paper forms have now been made available over the internet, where, after some kind of authentication, the same service is provided over a digital medium. The advantages are numerous and significant, as it is more convenient for the citizen and digital information is far more suitable for automated processing.
As a consequence, it is only fair that one starts thinking about an electronic equivalent for voting. Most countries still use paper ballots which are counted by hand after the voting period ends. This obviously has drawbacks: paper is wasted, manual vote counting takes time and is potentially more error-prone than electronic vote counting. As tempting as electronic voting may seem, it is important to realize the potential risks and drawbacks. The possibility to cast a vote, and the confidence that all votes are being taken into account in a honest manner is one of the main pillars of a modern democracy. The trade-off between advantages and risks of electronic voting is thus one that deserves careful thought. Because biometric identifiers cannot be easily misplaced, forged, or shared, they are considered more reliable for person recognition than traditional token or knowledge-based methods. So, the Electronic voting system has to be improved based on the current technologies viz., biometric system.
_
Electronic voting most directly affects two large parties: the voters, and the government. Theoretically, in order for electronic voting to be instituted, there must be a significant advantage (greater than the costs) to one or both of these groups. Ideally, voters gain a better voting experience at the polls, are more confident that their vote will be correctly counted, and are able to vote more easily and efficiently. The government is potentially able to increase voter turnout, reduce costs, increase voter confidence, renew interest in the political system (and voting), and ensure the most democratic process possible. One of the significant benefits of this new system is the possibility for increased efficiency. With Electronic Voting Machines voters can submit their votes, and be reasonably confident that their vote will count (namely avoiding the “hanging chad” problem that handicapped the 2000 presidential elections in the United States). New Electronic Voting Machines can also stop voters from common election faults, such as picking too many or no candidates, also thereby increasing the general effectiveness of voting.
__
Electronic voting is a means of having a paperless voting system:
Electronic voting is a term used to describe any of several means of determining people’s collective intent electronically. Electronic voting includes voting by kiosk, internet, telephone, punch card, and optical scan ballot (a.k.a. mark-sense). Research shows a number of reasons why e-voting has started to grow in importance over the last two decades or so.
- One of the biggest contributory factors which influence the growing popularity of e-voting is due to the 2000 US presidential election in Florida. The main parties involved were Al Gore and George Bush. Florida law states that if the winning margin is less than a quarter of a percent, there has to be a recount by law. Consequently, it took around four days to eventually clarify who the winning candidate was. The US felt embarrassed by the event, which led to widespread calls for electoral reform in the United States. On October 29th 2002, the “Help America Vote Act” was setup in response to the 2000 election. The act authorized the United States federal government to provide funds to the states to replace their mechanical voting equipment with electronic voting equipment. This act encouraged the development and usage of electronic voting systems.
- The other factor influencing the growing popularity of e-voting is to encourage more people to vote who are not currently doing so. It has been recorded that of the last 5 US presidential elections, the average number of voters was little over 46%. It has also been shown that 15% of these non-voters are physically unable to vote. Also 8% blame their inability to get off work, and 7% cite unplanned travel stops them from voting. The problem that exists therefore is that the lifestyle people live, is not compatible with current methods of voting. E-voting therefore appears a much more appealing option. For instance, it would be far easier to connect to the Internet after a hard day at work, and cast your vote on-line. This would also be much more convenient for people working odd hours, or even those who find it hard to get around i.e. they may have not got a car, or they live a good distance from public transport pick up and drop off points. People could also cast their vote if they were abroad, possibly on holiday, or away on a business trip. If the infrastructure was setup, they could vote using their PDA or mobile phone.
______
Electronic voting is a system of voting that uses electronic methods to record and/or count votes. Some electronic voting systems use physical ballots that are then counted electronically, and others replace physical ballots with electronic voting machines. In some cases, voters are even able to cast their votes over the internet. An electronic voting system is a voting system in which the election data is recorded, stored and processed primarily as digital information.
_
Most broadly, electronic voting refers to both the electronic means of casting a vote and the electronic means of tabulating votes. In this broad sense, most voting methods currently in use in the United States employ electronics. This can include punch card systems, optical scan voting systems, direct-recording electronic (DRE) and Internet voting. In common usage now, however, “electronic voting” refers to DRE voting systems most often utilizing touch-screens as well as electronic panels with push buttons or pointing devices to record votes. This is an important distinction because other systems which employ electronics, nevertheless, have a physical ballot that at least could be counted manually. DREs do not.
A DRE system, simply stated, is a type of computer. Voters view ballots on a screen and make choices using an input device such as a bank of buttons or a touchscreen. Some DRE systems employ an additional tool such as a card swipe or cartridge system used to activate the system before a ballot can be cast. Votes are stored on a memory card, internal hard drive, flash memory, compact disc or other memory device. Most commonly election officials transport these memory devices to a centralized location for tabulation, just as they would with paper-based ballots. Some machines have the capability to broadcast results over a modem-to-modem line.
_
Electronic voting (also known as e-voting) is voting that uses electronic means to either aid or take care of casting and counting votes. Depending on the particular implementation, e-voting may use standalone electronic voting machines (also called EVM) or computers connected to the Internet. It may encompass a range of Internet services, from basic transmission of tabulated results to full-function online voting through common connectable household devices. The degree of automation may be limited to marking a paper ballot, or may be a comprehensive system of vote input, vote recording, data encryption and transmission to servers, and consolidation and tabulation of election results.
A worthy e-voting system must perform most of these tasks while complying with a set of standards established by regulatory bodies, and must also be capable to deal successfully with strong requirements associated with security, accuracy, integrity, swiftness, privacy, auditability, accessibility, cost-effectiveness, scalability and ecological sustainability.
Electronic voting technology can include punched cards, optical scan voting systems and specialized voting kiosks (including self-contained direct-recording electronic voting systems, or DRE). It can also involve transmission of ballots and votes via telephones, private computer networks, or the Internet.
In general, two main types of e-voting can be identified:
- e-voting which is physically supervised by representatives of governmental or independent electoral authorities (e.g. electronic voting machines located at polling stations);
- remote e-voting via the Internet (also called I-voting) where the voter submits their votes electronically to the election authorities, from any location.
When considering electronic voting solutions, a clear distinction can be made between what is commonly referred to as I-voting or internet voting and a more traditional form of electronic voting that employs controlled voting booths where the actual vote is cast on an electronic device. Here I will discuss both regular e-voting and I-voting. For the sake of completeness, it must be noted that there is also a category of electronic voting solutions that remain very close to the concept of a physical paper ballot. These systems are mainly an electronic interface to generate paper votes, which may then be counted more efficiently. Different approaches exist, such as punch cards, electronic recognition of pencil markers or printed votes.
______
Overview of e-voting:
Voting is regarded as one of the most effective methods for individuals to express their opinions on a given topic. E-voting refers to the use of computers or computerised voting equipment to cast ballots in an election. Chaum pioneered the notion of e-voting and then many protocols were proposed (Chaum 1981). The first practical e-voting protocol for large scale elections is of Fujioka et al. (Fujioka 1992). Verifiability was firstly introduced in this protocol however it requires more voter involvement and accuracy can be violated that the malicious authority can add votes if any voter abstains from voting in the counting stage.
The basic process of any e-election is almost standard although a wide variety of e-voting systems and protocols exist. Any e-voting system should include these actors:
- Voter: Voter has the right for voting, and he votes in the election.
- Registration Authority: Registration authority or authorities register eligible voters before the election day. These authorities ensure that only registered voters can vote and they vote only once on the election day. Registration authorities may be registrar, authenticator, authoriser, ballot distributor and/or key generator.
- Tallying Authority: The tallying authorities collect the cast votes and tally the results of the election. Tallying authorities may be counter, collector and/or tallier.
_
Any e-voting system should also involve these four phases:
- Registration: Voters register themselves to registration authorities and the list of eligible voters is compiled before the election day.
- Authentication and Authorisation: On the election day registered voters request ballot or voting privilege from the registration authorities. Registration authorities check the credentials of those attempting to vote and only allow those who are eligible and registered before.
- Voting: Voter casts his vote.
- Tallying: The tallying authorities count the votes and announce the election results.
A general e-voting process and the actors involved can be summarized as seen in the figure below:
______
Electronic ballots:
Electronic voting systems may use electronic ballot to store votes in computer memory. Systems which use them exclusively are called DRE voting systems. When electronic ballots are used there is no risk of exhausting the supply of ballots. Additionally, these electronic ballots remove the need for printing of paper ballots, a significant cost. When administering elections in which ballots are offered in multiple languages (in some areas of the United States, public elections are required by the National Voting Rights Act of 1965), electronic ballots can be programmed to provide ballots in multiple languages for a single machine.
_____
Electronic Voting Process:
When designing an electronic voting service, it is essential to consider ways in which the voting processes performed electronically without sacrificing voter privacy or introducing opportunities for fraud. An electronic voting system used for effecting national or regional elections combined with the traditional voting process (where the identity of a voter establishes through visual and documentary means) ensures democracy.
Figure below illustrates a voting process in an electronic voting system.
The first process is to identify a potential voter and authenticate this voter. The electronic voting system must be high availability to all users at all times. A record should be kept of people who do not vote, as this would increase the measure of security. The next phase is to ascertain whether the voter is eligible to vote this forms part of the democratic right to vote. People ineligible and that have already voted are cannot gain access to the electronic voting system. Users will then proceed to voting screen where they will be given a list of choices which they can vote on. When users cast their votes, their vote should contain the following attributes; privacy to guarantee users, anonymity, accuracy so the vote cannot be altered in anyway, and the vote cannot be deleted from the final tally. The vote should be verifiable by anyone wishing to count votes. Non-repudiated so as voters cannot deny they have voted. A paper-based copy should be produced at this stage to track all vote results in case there an error occurs with electronic voting systems. The electronic voting systems will then take votes and add them to a final tally of votes. If there is, any concern about the way in which the elections have been conducted paper-based copies of votes can verify the result.
______
Typical features and functionalities of e-voting systems:
Internally, electronic voting systems have many functions, including encryption, randomization, communication and security systems. A specific analysis of these functionalities goes beyond the scope of this article. However, it is useful to consider the following list of some of the end-user functionalities that such systems can provide to both voters and election officials.
- Electronic voter lists and voter authentication. Part of an electronic voting system can be an electronic voter list, covering either a single polling station or the entire country. This list can be used to authenticate eligible voters and to record that they have cast their vote.
- Poll worker interfaces. Special functionalities that are only available to poll workers, for example, resetting the vote count at the opening of the polling station, closing polling, printing and transmission of results.
- Interfaces for casting votes. These include touch screens, optical mark recognition (OMR) ballot papers that are fed into a scanner, touch-sensitive tablets, push buttons, web pages or special client software for Internet voting.
- Special interfaces for handicapped voters. These include Braille or audio input devices for the blind, easier access for voters with physical disabilities, and simpler interfaces for illiterate voters.
- Interfaces for the results output. For voting machines this is often a printer. However, some machines only use digital displays. Once voting is closed this interface can be used to display or print the results that were recorded by the voting machine. If results are printed the printouts can be used as physical evidence of the results produced by the voting machine, and copies can be distributed to stakeholders present at the polling station and can also be posted for public display.
- Printers for printing a voter-verifiable receipt for each vote (VVPAT).
- Result transmission system. Many voting machines can transmit results to central counting systems, for example via the Internet, telephone, mobile phone or satellite connection. In the absence of communication links, the results can also be transported physically, using electronic storage media such as memory cards.
- Result tabulation systems, usually located at result processing centers. At the end of election day, they receive electronic results from polling stations and automatically tabulate the results for the various competitions and districts.
- Result publication systems. Preliminary and final results can be published in many different ways including on websites, CDs, and geographic visualization systems, and if required on all levels of detail down to single polling stations. The more detailed the published results are, the more transparent the election.
- Confirmation code systems. Some e-voting solutions allow for control codes that are intended to allow individual verification of each vote by the relevant voter.
______
Hardware:
Inadequately secured hardware can be subject to physical tampering. Some critics, such as the group “Wij vertrouwen stemcomputers niet” (“We do not trust voting machines”), charge that, for instance, foreign hardware could be inserted into the machine, or between the user and the central mechanism of the machine itself, using a man in the middle attack technique, and thus even sealing DRE machines may not be sufficient protection. This claim is countered by the position that review and testing procedures can detect fraudulent code or hardware, if such things are present, and that a thorough, verifiable chain of custody would prevent the insertion of such hardware or software. Security seals are commonly employed in an attempt to detect tampering, but testing by Argonne National Laboratory and others demonstrates that existing seals can usually be quickly defeated by a trained person using low-tech methods. Voting machine vendors and election officials have long insisted that no one can manipulate voting machines and ballots because tamper-evident seals used to secure them would prevent intruders from doing so without anyone noticing. Election officials say security ties and seals prevent anyone with physical access to voting machines from manipulating them. But a researcher has shown how he can easily defeat them with a soda can. He can do so without leaving evidence of tampering.
Software:
Security experts, such as Bruce Schneier, have demanded that voting machine source code should be publicly available for inspection. Others have also suggested publishing voting machine software under a free software license as is done in Australia. Software such as Sammaty come under GNU GPL, which means their source code is publicly available and hence transparent.
Data storage:
Each voting terminal has two distinct types of internal data storage. A main (or system) storage area contains the terminal’s operating system, program executables, static data files such as fonts, and system configuration information, as well as backup copies of dynamic data files such as the voting records and audit logs (Kohno et al, 2004).
Network:
The Diebold voting machines cannot work in isolation. They must be able to both receive a ballot definition file as input and report voting results as output. There are essentially two ways to load a voting terminal with an initial election configuration: via some removable media, such as a flash memory card, or over a network connection. In the latter case, the voting terminal could either be plugged directly into the Internet, could be connected to an isolated local network, or could use a dialup connection (the dial-up connection could be to a local ISP, or directly to the election authorities modem banks) (Kohno et al, 2004).
_____
Open standards:
In order to be able to use e-voting systems or services from different suppliers, these must be interoperable. Interoperability means that the input and output conform to open standards and especially open standards for e-voting. Such standards need to be updated on a regular basis to take account of legal and technical developments.
The main benefits of using open standards are:
- Greater choice of products and suppliers
- Less dependency on a single supplier
- Avoidance of proprietary lock-in
- Stability or reduction in costs
- Easier accommodation of future changes
Countries, in particular decentralised ones with a variety of states/members and thus a variety of electoral practices, may decide to adopt such standards at the country level. At the regional level, countries may decide to adopt regional standards.
_______
Proprietary source code vs. open source code:
“Source code” is the part of software that most computer users don’t ever see; it’s the code computer programmers can manipulate to change how a piece of software—a “program” or “application”—works. Programmers who have access to a computer program’s source code can improve that program by adding features to it or fixing parts that don’t always work correctly. Open source software is software with source code that anyone can inspect, modify, and enhance. Any expert who wants to analyse and understand an electronic voting system needs to have access to its programming source code. Currently, commercially available e-voting solutions are commonly based on proprietary source codes. For commercial and security reasons vendors are usually reluctant to provide access to this source code. However, vendors do increasingly recognize the need to allow source code access and several EMBs already include such access in their e-voting system requirements. The possibilities for public inspection of commercial source codes are often limited in time and scope, come at additional cost, and still only allow limited insight into the functioning of the system being examined. Using voting systems based on proprietary code therefore often results in IT experts calling for a switch to open source systems. In contrast to proprietary systems, the source code of such systems is publicly available and fully accessible to all interested experts. Opponents of the publication of source codes argue that most currently available systems are not perfect and that publishing them will expose weaknesses to the public and to potential attackers.
Advocates of the open source approach, including most computer security experts, argue that, although publishing the code can reveal problems, it also guarantees that solutions will be found quickly. For open source advocates, keeping the codes secret is viewed as ‘security by obscurity’ and creates a situation where only a few insiders know about the weaknesses of a system. While some efforts to develop open source e-voting systems are ongoing, such systems are currently not readily available. It should be noted that access to source codes is only one step towards full technical transparency. To fully understand an e-voting system’s behaviour, the compilers which are used to translate the human-readable source codes into machine-readable code, the voting system’s hardware and the operating system need to be analysed as well.
Software used on DRE machines must be open to public scrutiny. This also has two functions: it allows any interested party to examine the software and find bugs, which can then be corrected, a public analysis that improves security; and it increases public confidence in the voting process – if the software is public, no one can insinuate that the voting system has unfairness built into the code (companies that make these machines regularly argue that they need to keep their software secret for security reasons. Don’t believe them. In this instance, secrecy has nothing to do with security).
_
Systems with or without voter authentication:
Some e-voting systems are only used for casting the vote and voter authentication remains manual; others contain an additional module for authenticating voters based on an electronic poll book or electoral register. All Internet voting systems, and some voting machines in polling stations, contain an authentication module. A voting system that performs both functions—voter identification and the casting of the ballot—is inherently open to criticism and potentially to malpractice. Even when the two functions are kept rigidly separate, there may be a possibility for inside operators to cross-check the two data sets. This possibility requires the establishment of specific technical and procedural security measures to guarantee that these two sets of information cannot be linked under any circumstances. The secrecy of the vote relies on these measures and it is important that they can be clearly communicated and demonstrated to interested stakeholders.
_
Internationally vs domestically developed systems:
Developing reliable and secure e-voting systems according to the parameters mentioned above is a substantial effort that is often beyond the capacities of a single election administration or the domestic commercial IT sector. Therefore many EMBs purchase their e-voting solutions from international vendors. Usually only EMBs in countries with a very large electorate will find it sustainable to develop and maintain an electronic voting solution domestically. An important advantage of this approach is that the costs of the system are invested in the local economy and local competence is built in the process. At the same time it can be difficult for locally-built systems to take on board the lessons learned from experiences in other countries. When developing a local e-voting solution it is important not to do this in a vacuum and to review and compare internationally available systems, as well as analysing the latest trends and research and connecting this analysis to an understanding of the local needs and the rationale for the introduction of the technology. A mixed approach, between local and international sourcing options, is to have international vendors partner with local companies to produce some of the e-voting equipment in country, and by so doing invest some of the costs of e-voting back into the local economy.
________
E-voting: not comparable to any other ICT application?
Virtually every information and communication technology (ICT) application is built in a way that allows verification of its proper functioning by observing the application’s outputs. If a customer does not trust a bank’s electronic banking system, he or she can check their account overview and confirm that all transactions are reflected properly. If the owner of a car does not trust the electronics in the car, every starting of the engine gives an opportunity to test that system.
E-voting systems are fundamentally different. Due to the requirement to protect the secrecy of the vote, they have to avoid any connection between the voter’s identity and the vote cast. This is in itself a challenge as standard ICT systems are inherently built for tracking and monitoring transactions that happen on them. More importantly, breaking the link between voter and vote means that the examination of an e-voting system after an election cannot prove directly that every vote was indeed counted and tallied as cast. This is why indirect proofs of the validity of the electronic results, such as paper trails or system certification, in combination with stringent quality control and security procedures, are exceptionally important. Without such mechanisms, manipulated or incorrect results produced by an e-voting system could remain undetected for a long time.
______
The primary reason for expanding the use of technology in the electoral process (generally known as e-voting) is the desire to overcome the limitations of conventional voting systems. Other reasons include faster tallying times, providing ease to voters with disabilities, and increasing voter turnout rates. While the use of computers has been proven valuable in many fields, in the case of e-voting, several countries, including the US, have experienced negative results. In some races, the problems resulted in the necessity to manually handle compromised ballots, repeat entire elections using paper ballots, issue new laws and requirements, and in countries like Germany, Ireland, and the Netherlands, suspend the use of e-voting.
On the other hand, the idea of equipping DREs with a verified paper audit trail was introduced several years ago. However, the practical development of this idea is still questionable. The studies show that the majority of voters fail to detect mismatches between their electronic ballot and the paper trail leading to uncertainty regarding the value of this process.
Elections are critical and require a high degree of security (far more than is required in an e-commerce system). It would not be paranoid to say that many individuals and organizations exist that might want to alter the behavior of voting computers to suit their own purposes. The main reason for the difficulty in implementing a secure evoting system is the conflict between the principles of accuracy and secrecy in the electoral process. In e-commerce systems, a buyer can always get a receipt to document his purchase. Conversely, due to fundamental voting regulations, providing documentation of a vote is forbidden, which means that the voter has no choice but to trust that a system records his vote as cast, counts it as recorded, and is secure and private enough to ensure that no one will be able to view or change his ballot. To resolve this conflict and to eliminate the need for the infamous chain of custody, cryptographers have suggested a protocol known as end-to-end cryptographic voting. The goal behind the end-to-end concept is to provide voters with confidence in the integrity of election results, regardless of the software used and without the need to blindly trust election officials. All that must be accomplished without enabling the voters to prove to others how they voted. Generally, end-to-end systems provide the voter with some kind of assurance that his vote was recorded-as-intended (ballot casting assurance) in the form of encrypted proof. Additionally, such systems publish all the encrypted proofs so that the public may verify the integrity of the election as a whole (universal verifiability). While such an approach might sound like the perfect solution, several new threats have been raised.
_____
Do we need electronic voting systems?
- They could lead to increased voter turnout (USA 2001: 59%, 18-24 yrs: 39%), thus supporting democratic process.
- They could give elections new potential (by providing ballots in multiple languages, accommodating lengthy ballots, facilitate early and absentee voting, etc.) thus enhancing democratic process.
- They could open a new market, thus supporting the commerce and the employment.
_
Barriers to electronic voting:
- Lack of common voting system standards across nations.
- Time and difficulty of changing national election laws.
- Time and cost of certifying a voting system.
- Security and reliability of electronic voting. Equal access to Internet voting for all socioeconomic groups.
- Difficulty of training election judges on a new system. Political risk associated with trying a new voting system.
- Need for security and election experts.
_
Advantages of electronic voting over the traditional ballot paper/ballot box system are:
- It eliminates the possibility of invalid and doubtful votes which, in many cases, are the root causes of controversies and election petitions. Charles Stewart of the Massachusetts Institute of Technology estimates that 1 million more ballots were counted in the 2004 USA presidential election than in 2000 because electronic voting machines detected votes that paper-based machines would have missed.
- It makes the process of counting of votes much faster than the conventional system.
- It reduces to a great extent the quantity of paper used thus saving a large number of trees making the process eco-friendly.
- It reduces cost of printing almost nil as only one sheet of ballot paper required for each Polling.
_
Concerns about electronic voting:
Two major problems seem inherent:
- Lack of a tangible record. A paper ballot, for example, is a tangible physical object which can be indelibly marked. Computer memory, however, can be easily altered leaving no trace of its original marking.
- The possibility of fraud on a monumental scale. A single programmer can insert self-erasing code that can alter millions of ballots and the outcome of elections.
In addition, a host of other problems remain entrenched in the system. These include:
- Lack of transparency: Current electronic voting systems do not have publicly reviewable inner workings (source code). By examining the source code, critics argue, computer scientists could determine that the program performs the intended task without error. Vendors, however, claim their source code to be proprietary knowledge and a trade secret.
- Insufficient standards, testing and certification: voting system are typically certified to federal and/or state standards that are several years old and older standards often will have gaping flaws. Implementing new standards has been a slow, cumbersome and costly process. Certification is done by for-profit laboratories accredited by the National Institute of Standards and Technology, but chosen and paid by the manufacturers.
- Insufficient oversight: Various electronic voting companies were found to have employees who have previously been convicted of serious crimes, including felonies. A Diebold e-voting programming director was found to have criminal records for embezzlement, a crime very similar technically to election fraud.
_
Vulnerability comparisons with other voting systems:
Election fraud may occur and go undetected in systems with indelible (e.g., paper) ballots, but it is, in principle, detectable, and flagrantly egregious behavior can usually be limited through the courts and public pressure. If legal procedures are pursued or if an investigative team is dogged, fraud can be exposed and justice served. For example, the Miami Herald won a Pulitzer prize for reporting on vote buying and ballot tampering by the campaign of Xavier Suarez, who had been elected mayor of Miami. As a result, Suarez was forced to step down after 111 days in office. With electronic voting systems, however, fraud may be undetectable, and those who have been declared the losers are left with no recourse to verify results.
Electronic voting is often facilitated by kiosk hardware systems that are introduced to polling stations. These machines typically include an interactive touchscreen interface through which voters can cast their ballots. Among the many security and accuracy issues cited with electronic voting is the question of whether there is a way to accurately observe voting results and test whether every vote was recorded. Without a paper backup, accurate audits can be difficult. While some systems may have failsafe event logging, not all of them do, and that has led to the idea that electronic voting should be scaled back or better regulated in elections. For example, many election officials have cited a difference between the physical headcounts of people going into a polling place, and the number of ballots cast, asking why anyone would go to a polling place to record an empty ballot.
Another issue with the machines involves access. Whenever officials of a given party have time alone with machines, there is a possibility of tampering or fraud. Critics point to things like the availability of USB flash drive ports on the electronic voting machines as an easy way to tamper with the system. In general, the many unknowns of these types of systems have led to a big debate about whether or not they should be used in elections.
______
Electronic voting in polling stations is in place in some of the world’s largest democracies, and Internet voting is used in some, initially mainly small and historically conflict-free, countries. Many countries are currently considering introducing e-voting systems with the aim of improving various aspects of the electoral process. E-voting is often seen as a tool for advancing democracy, building trust in electoral management, adding credibility to election results and increasing the overall efficiency of the electoral process. The technology is evolving fast and election managers, observers, international organizations, vendors and standardization bodies are continuously updating their methodologies and approaches. Properly implemented, e-voting solutions can eliminate certain common avenues of fraud, speed up the processing of results, increase accessibility and make voting more convenient for citizens—in some cases, when used over a series of electoral events, possibly even reducing the cost of elections or referendums in the long term.
Unfortunately not all e-voting projects succeed in delivering on such high promises. The current e-voting technology is not problem-free. Legislative and technical challenges have arisen in some cases; in others, there has been skepticism about or opposition to the introduction of new voting technologies. The inherent challenges of e-voting are considerable and linked to the complexities of electronic systems and procedures. Many e-voting solutions lack transparency for voters and even for election administrators. Most e-voting solutions are only fully understood by a small number of experts and the integrity of the electoral process relies largely on a small group of system operators instead of thousands of poll workers. If not carefully planned and designed, the introduction of e-voting can undermine confidence in the whole electoral process. It is therefore important to devote adequate time and resources to considering its introduction and looking at previous experiences of electronic voting.
____
ACCURATE:
ACCURATE (A Center for Correct, Usable, Reliable, Auditable, and Transparent Elections) was established in 2005 by a group of computer scientists, psychologists and policy experts to address problems with electronic voting. The NSF-funded organization seeks to provide fundamental research and reference materials about electronic voting for use by policy makers, vendors, the elections community and the general public.
The goals of the center are:
- to research ways in which technology can be used to improve voting systems and the voting process.
- to develop the science that will help inform the election community and the public about the tradeoffs among various voting technologies and procedures.
- to serve as a resource to the elections community, politicians, vendors and the public about issues related to public policy, technology, and law with respect to voting.
- to publish and disseminate their research so that future systems can benefit from the center’s work.
_____
_____
Pyramid of trust for e-voting:
Figure below shows pyramid of trust for e-voting:
The top of the pyramid—and the ultimate goal of electoral reform by implementing an e-voting solution—is a credible electoral process that enjoys a high level of public trust and confidence in the new system. Public trust is initially mainly built on the socio-political context in which e-voting is introduced. Some factors in this context can be directly addressed by a comprehensive e-voting implementation strategy, while others, such as a general lack of trust in the EMB or fundamental political or technical opposition, will be more difficult to change.
A supportive socio-political context significantly helps the introduction of e-voting and can temporarily even cover up problems that may occur in the detailed technical implementation. Trust in a solution that is technically weak can, however, be misleading. Weaknesses in the operational, technical or legal foundations will eventually surface and may then discredit not only e-voting, but possibly the entire electoral process, especially when the political stakes of an election are high. The complete cancellation of electronic voting from a country’s electoral framework may be the consequence, as has happened in Germany, Ireland and the Netherlands. A negative socio-political context creates serious risks, even if the technical and operational foundations of the e-voting solution are sound. It is very difficult to make e-voting systems transparent and their operations understood in the short and even medium term by a non-expert audience. Weak social and political support will hinder the implementation of a trusted e-voting solution as opponents will find it much easier to undermine trust in this voting technology by pointing to some of its inherent weaknesses.
E-voting tends to take a good deal of the responsibility for the electoral process away from thousands of polling station officials and place this responsibility in the central election administration and the implementers of the e-voting system. In doing so, the implementation of e-voting reduces the risk of widespread fraud and manipulation at polling station level, but concentrates the risk of manipulation at the central level. This is beneficial in an environment where there is little public confidence in polling station officials, but where the central election administration is trusted. However, in an electoral environment where there is little trust in the central EMB structure, the introduction of electronic voting systems can easily become subject to rumour mongering about potential central manipulation. Some of these rumours may be hard to refute.
Note:
An EMB (Election Management Bodies) is an organization or body that has the sole purpose of, and is legally responsible for, managing some or all of the elements that are essential for the conduct of elections and direct democracy instruments—such as referendums, citizens’ initiatives and recall votes—if those are part of the legal framework. For example, election commission of India (ECI) is EMB for India.
______
______
Typologies of electronic voting:
The term electronic voting is a blanket term used to describe an array of voting methods that operate using electronic technology. There are three primary types of electronic voting, namely machine counting, computer voting and on-line or Internet voting. With respect to the last of these types, there are four kinds of electronic voting that use the Internet; these include kiosk Internet voting, polling place Internet voting, precinct Internet voting and remote Internet voting (Alvarez and Hall, 2004). Kiosk Internet voting typically involves the use of a computer at a specific location that is controlled by election officials. This differs from electronic machine voting because, among other things, the ballot is cast over the Internet. Polling place Internet voting is conducted at any polling station through the use of a computer that is controlled by election representatives. Precinct Internet voting is analogous to polling place voting except that it must occur at the voter’s designated precinct polling place (Alvarez and Hall, 2004). Remote Internet voting is voting by Internet from a voter’s home or potentially any other location with Internet access.
_
There are other distinctions to be made when it comes to electronic voting machines, which are also important in implementation:
-Remote and non-remote voting machines
-Supervised (controlled) and unsupervised (uncontrolled) environments
Electronic voting can be conducted either in controlled or in uncontrolled environments. Electronic voting in controlled environments happens when the casting of votes takes place in polling stations, polling kiosks or other locations under the supervision of staff appointed by the electoral management body (EMB). By that means the election administration can to a great extent control the voting technology as well as the procedures and conditions under which voters are casting their ballots. Electronic voting in controlled environments can be seen as the electronic equivalent of traditional paper-based voting in polling stations, embassies and so on. It is possible to combine remote voting with supervised environments, for example, Internet voting computers set up in polling stations. This allows polling staff to verify the identity of voters by using voter lists before allowing them to vote, and to ensure secrecy of the vote – two significant challenges with other forms of remote voting.
Electronic voting in uncontrolled environments happens without any supervision and from voting devices that cannot be controlled by the election administration. This can be from home, on the voter’s personal computer, or potentially anywhere on mobile or public devices. With voting in uncontrolled environments, concerns about the secrecy of the vote, family voting, intimidation, vote-buying, the loss of the election day ritual, the impact of the digital divide and the technical separation of voter identity and ballot paper, as well as the technical integrity of the device from which the votes are cast, all need specific consideration. Current forms of Internet voting have not yet been able to provide a definitive solution to such concerns. Electronic voting in uncontrolled environments can be seen as the electronic equivalent of postal voting or absentee voting.
_____
Key Distinctions for Implementation of Electronic Voting as derived from above paragraph:
Remote Voting: An electronic device used to cast a vote, and then transmits the ballot choice across a communication channel. The ballot choice is then recorded in a central location, e.g. Internet voting and SMS voting.
Non-Remote Voting Machines: An electronic device used to cast a vote, which records the ballot choice made on a local medium, e.g. the machine itself or a printed ballot.
Supervised Environments: A voting machine used in a location where election staff is present to manage the voting process, such as a polling station.
Unsupervised Environments: A voting device used in a location where no election staff is present to manage the voting process, such as any computer the voter uses for Internet voting.
______
The terminology of e-voting is nascent, and a crucial distinction lies between the various different ways in which voters can vote electronically.
- Electronic Machine Voting
Electronic machine voting simply refers to the use of any electronic apparatus to record and count votes in a fixed public place (Leenes et al, 2003). This may be a specialised voting machine in a voting booth with touch screens or a stand-alone PC specially installed for this purpose in a voting kiosk.
- Electronic Ballot Voting
Electronic ballot voting refers to the casting of ballots at public sites where election officials control the voting ICT systems. Voters use touch screens or push buttons to select choices, special software will record votes, which are stored electronically in the machine (IPI, 2003). These systems maybe connected with virtual private networks (VPN) using secure socket layer (SSL) for security, votes automatically counted and verified at a central Facility (Langa, 2000). In these kinds of systems, they can be only be accessed at the poll site under the observation of election officials.
- Electronic Kiosks Voting
Kiosk voting offers an intermediate step between poll site and remote voting. In this model, voting terminals would be tamper proof and located in convenient places like shopping centers, post offices, or schools, but remain under the control of election officials (IPI, 2003). Election officials, observers, or even cameras would address security and privacy concerns, and prevent coercion or other forms of intervention. The challenges and risks associated with kiosk voting are considerable, but more approachable than those associated with remote distance voting are.
- Electronic Distance Voting
Electronic distance voting implies the electronic registration, culling and counting of votes cast from different locations (Leenes et al, 2003). It typically allows the voter to use a more generic technology such as interactive digital TV, telephone, Short Message Service (SMS) or the Internet, to cast their vote from any preferred place.
______
_______
Overview of Electronic Voting and Counting Technologies:
Traditional electoral procedures involving casting and hand counting paper ballots have come to dominate elections since their introduction in the mid-19th century. Technology increasingly offers new mechanisms for conducting traditionally-manual processes, and elections are no exception. There are many different technologies that can be used to support the electoral process. The current discourse on these technologies includes such terms as electronic voting machines, e-voting, e-enabled elections, new voting technologies (NVT), remote voting, precinct count optical scanning (PCOS), and e-counting. This array of terminology relates to different technological solutions. The field of election technologies concerning voting and counting is developing, and the conceptual framework is still emerging. Therefore, it is easy to find the same terms being used in different ways in different countries or regions, which can create confusion.
When discussing electronic voting, two separate, but sometimes related technologies are generally referred to – electronic voting and electronic counting. The traditional paper-based voting system consists of a voter manually marking the paper ballot and then the ballot being counted by hand by election officials. In elections using electronic voting or counting technologies, one or both of these processes are automated electronically.
Electronic counting involves the use of a device to count votes cast. The most common such counting machines use scanning technologies, such as optical mark recognition (OMR) or optical character recognition (OCR), to count ballots that have been completed manually by voters. This broad category of technologies also includes punch card counting machines and electronic ballot boxes used to count electronic records on tokens produced by electronic voting machines.
Electronic voting and electronic counting technologies, while representing different stages of the electoral process, can be combined, as is done by the DRE voting machine. It not only enables the voter to make his or her ballot choices, but also records them directly on the machine and produces results on the machine at the end of the voting process.
It is not mandatory, however, to combine the technologies. It is possible to have electronic voting without electronic counting and electronic counting without electronic voting. It is also possible to have voting and counting on entirely different devices, whereby a voting machine is used to produce tokens with the ballot choices made and a separate counting device tallies the votes recorded on these tokens.
_
Electronic Voting System:
Figure above illustrates an amalgamation of the technologies. Each separate electronic voting system connects to a central depot where votes are count up at the end of an election. The alternative to connecting to a central depot would be votes recorded on individual electronic voting systems would remain there. A security organisation after the election collects disks containing votes and delivers to an undisclosed location where all votes are count up in secret. The latter would be more secure as data delivered by hand is more secure as opposed to the delivery via the Internet.
_
Common Electronic Voting and Counting Technologies:
There are many different electronic voting and counting technologies being used globally. The variety of technologies used makes it difficult to easily categorize them. The most common types of technologies are identified are as follows:
- Direct Recording Electronic (DRE) System:
Direct recording electronic voting systems are complicated, because there are so many different types. The three main types of DRE voting machines use touchscreens, push-buttons, and dials to register votes. While there are only a few companies that make DRE voting machines, there are dozens of different models in service. DRE systems use a keyboard, touch-screen, mouse, pen or other electronic device to allow a voter to record his or her vote electronically. DREs are used in non-remote, supervised locations (polling stations). The DRE system captures the voter’s choices and stores an electronic record of their vote in the machine. The data captured by each individual DRE unit is then transmitted by either electronic means (i.e., Internet, cellular network or memory card) or manually (i.e., by printing the results from each machine and tabulating them) to capture the total number of votes cast for specific parties or candidates. DRE systems may or may not produce a paper record to allow the voter to verify their voting choices. This paper record, also called a voter verified paper audit trail (VVPAT), has been implemented in multiple ways in different countries. Stand-alone DRE is also known as EVM.
A DRE directly records the cast ballots and stores the data in its memory. Thus, a single machine is used for composition, casting, and recording of votes. The third step, recording of the cast ballot in a memory device, is invisible to the voter. Assurance that the vote is recorded as cast relies on testing of the machine’s hardware and software before the election and confidence that the software running during the election is the same software as the one tested before the election. Both of these are subjects of much controversy.
Whereas testing for faults in hardware or unintentional errors in software can be highly reliable, the same is not true for malicious software. Most security professionals believe that an insider attack at the software development stage could make it to the final product without being detected (although there is disagreement about the likelihood of such an attack). This problem is compounded by the fact that source code is usually not made available for public scrutiny.
Cryptographic techniques can partially solve the problem of software authentication. When the software is evaluated and certified, a cryptographic hash (a short string of bits that serves as a type of “signature” for the computer code) can be computed and stored. Just before running the election, the hash is recomputed. Any change in the certified software will cause the two hashes to be distinct. This technique, however, may fall short of preventing all attacks on software integrity.
Computer viruses can infect a machine during an election. For this to happen, the machine must somehow interact with another electronic device. Thus, connection to the Internet or to wireless devices is usually disallowed. However, a voting session is typically initiated through the use of an activation card. A poll worker, upon verification of eligibility, sets the card to enable one voting session. After the session the voter returns the card to the poll worker for reuse. At least one DRE system has been shown to be vulnerable to infection using the activation card. An infected machine can be made to record votes not as they were cast.
The threat of DREs not recording the votes as cast has led some individuals and organizations to argue that a paper audit record must be produced for each cast ballot. DRE manufacturers responded by adding a printer capability to their DREs. The resulting systems produce both an electronic record and a paper record. However, problems in handling and monitoring the paper record, both by voters and by election officials, have led to much criticism of these hybrid systems. Many jurisdictions have discarded them in favour of optical scanning technology.
_
While DREs have many advantages including ease of operation, reduction of invalid votes cast and speeding up the counting, they also have some glaring disadvantages.
First, DREs are ‘black boxes’ in which it is impossible for voters to verify whether their votes have been recorded and counted correctly.
Second, as DREs suffer from the lack of transparency and verifiability, trusting the accuracy of their vote tallies calls for ‘a leap of faith’. It is true that small pre-election ‘mock polls’ are conducted in front of all-party representatives to ‘prove’ that the DREs are working properly. Such pre-election mock polls might protect against non-malicious malfunction of EVMs. But they afford very little protection against sophisticated attacks where the dishonest, look-alike CPU has been programmed to cheat only after several hours have passed or after the EVM has recorded hundreds of votes, or if it carries a malicious program (a Trojan) that is activated at a particular stage of the polling/counting process.
Third, with DREs, recounting is meaningless as it will simply yield the same total.
Fourth, there is the risk of the votes cast being permanently lost due to equipment malfunction.
There should be a provision whereby the votes are recorded in another way besides electronic storage and there is “retraceability” of the election result independently of the electronic count. In other words, there should be provision for an additional verifiable physical record of every vote cast.
_
DRE machines must have a voter-verifiable paper audit trails (sometimes called a voter-verified paper ballot). This is a paper ballot printed out by the voting machine, which the voter is allowed to look at and verify. He doesn’t take it home with him. Either he looks at it on the machine behind a glass screen, or he takes the paper and puts it into a ballot box. The point of this is twofold: it allows the voter to confirm that his vote was recorded in the manner he intended, and it provides the mechanism for a recount if there are problems with the machine. DREs with VVPATs are perceived to have an advantage over DREs without VVPATs, because paper trails provide greater transparency to the voter, which can engender greater trust. DRE voting without VVPATs, which is a form of “black box voting,” does not provide sufficient means for voters and stakeholders to verify votes have been accurately recorded. DREs with VVPAT provide election management bodies (EMBs) and those who provide oversight with the potential to audit the results or conduct a meaningful recount. However, DREs with VVPATs also introduce greater technological complexity into the process, which may result in greater challenges for EMBs in terms of reliability of the machine, training for staff and sustainability of the overall system.
DREs can be confusing for voters who are not familiar or comfortable with information technology (IT). However, in some contexts, voters may benefit from a streamlined presentation of ballots on DREs in complicated voting systems – with or without VVPAT – where a paper ballot design may lead to a significant number of spoilt and invalid ballots. It is important to note that ballot design may be a challenge no matter which voting system is used.
_
Direct-recording electronic (DRE) voting system used in Brazil:
Electronic voting machine is used in all Brazilian elections and plebiscites as seen in the figure below:
A direct-recording electronic (DRE) voting machine records votes by means of a ballot display provided with mechanical or electro-optical components that can be activated by the voter (typically buttons or a touchscreen); that processes data with computer software; and that records voting data and ballot images in memory components. After the election it produces a tabulation of the voting data stored in a removable memory component and as a printed copy. The system may also provide a means for transmitting individual ballots or vote totals to a central location for consolidating and reporting results from precincts at the central location. These systems use a precinct count method that tabulates ballots at the polling place. They typically tabulate ballots as they are cast and print the results after the close of polling.
_
Diebold AccuVote-TS:
The Diebold AccuVote machine uses a touch screen with a card reader that the voter gets after being authenticated by polling officials. Figure below shows Diebold AccuVote-TS system (Left) and Hart InterCivc eSlate system (Right)
Diebold’s voting systems are in use in 37 states in the U.S., and they are the second largest and the fastest growing vendor of electronic voting machines.
_
- Electronic Ballot Printers (EBPs):
EBPs are similar to DREs, in that the voter uses a DRE-type interface for the act of making voting choices. However, unlike DREs, an EBP does not store vote data. Instead, it prints out a paper receipt or produces a token containing the voting choice(s). The voter then takes this receipt or token and places it into the ballot box, which may be electronic and automatically count the vote.
EBPs are considered easier to understand and more user-friendly for the voter than DREs, as they split the actions of marking the voter’s choice and casting the ballot in the same way a voter marks and casts a ballot in traditional paper voting. The first machine (ballot printer) only marks the voter’s choice, but does not record the vote, while the second machine (ballot scanner or “electronic ballot box”) only records and tallies the votes. Like the DREs with a VVPAT, the voter can verify their vote, either on a printed paper ballot or by inserting the ballot token into another voting machine. There is the possibility of a recount of the paper receipt or token if the electronic results are challenged or audited. However, because they involve two separate machines, EBP systems may entail higher costs, require greater IT capacity from EMBs and encounter more challenges to ensuring sustainability than other systems.
_
- Optical Mark Recognition (OMR):
An optical scan voting system is an electronic voting system and uses an optical scanner to read marked paper ballots and tally the results. Optical scan systems use paper ballots, which are scanned and tabulated electronically, while DRE systems require you to vote using a machine. All optical scan systems work in basically the same way, and the only major differences are the type of mark you need to make on the ballot, and whether or not you scan your own ballot. States that use vote-by-mail systems use optical scan electronic voting, and absentee ballots are typically also cast using this technology. OMR counting machines combine aspects of paper ballot voting with electronic counting. The voter uses a pen or pencil to mark his or her choices (usually by filling in an oval or connecting an arrow) on a special machine-readable paper ballot. The ballot is then read by an OMR machine that tallies votes using the marks made by the voter. There are two methods used to tally votes using an OMR system. OMR systems can be either central count systems (where ballot papers are scanned and counted in special counting centers) or precinct count optical scanning (PCOS) systems (where scanning and counting happens in the polling station, directly as voters feed their ballot paper into the voting machine). In some optical scanning systems, the voter fills out a paper ballot and inserts it into an electronic scanning device. Scanners can reject improperly marked ballots, allowing the voter to start over, thereby reducing discarded votes. In other optical scanning systems voters compose their votes on a computer screen. Once a ballot is completed, the computer prints an optical scanning ballot. The voter verifies the ballot and then inserts it in another device that scans and tabulates the vote. Both these systems are considered electronic voting systems.
OMR systems provide greater ability for recounts than DREs without VVPAT. Generally, OMR systems cost less than DREs and may put less strain on EMBs in terms of sustainability of the systems. On the other hand, these systems entail significant focus on details such as ballot design, type of ink used, paper stock thickness and other factors that may inhibit the ability of OMR machines to accurately count votes. OMR machines are always used in a supervised, non-remote location.
Ballot marking device (BMD):
An electronic ballot marker (EBM) or ballot marking device (BMD) is a device that can aid voters in marking paper ballots. Typical ballot markers include a touch screen and a variety of assistive devices to serve the needs of voters with disabilities. A voter’s choices are usually presented on a screen in a similar manner to a DRE, or perhaps on a tablet. However, a BMD does not record the voter’s choices into its memory. Instead, it allows the voter to mark the choices on-screen and, when the voter is done, prints the ballot selections. The resulting printed paper ballot is then either hand counted or counted using an optical scan machine. BMDs are useful for people with disabilities, but can be used by any voter. Some systems produced print-outs with bar codes or QR-codes instead of a traditional paper ballot. Security experts have pointed out that there are risks associated with these types of systems since the bar code itself is not human readable.
Some BMDs count votes internally (as do DRE systems) and may save voter selection information. For any BMD that does count, save, or use cryptography or other techniques to make it difficult to insert fraudulent ballots prepared on other devices (before, during or after actual voting), any discrepancy between records stored within a BMD and physical ballots produced would provide clear evidence of malfunction or fraud and initiate an investigation to determine the source of the discrepancy and the invalid ballots, whether electronic or physical. Examples include: AutoMark and Populex.
_
There is a school of thought which considers Machine-readable Paper Ballots that are electronically counted using OMR technology superior to EVMs with VVPAT for the following reasons.
-1. First, paper ballots are considered the ‘gold standard’ of voting. That is why they are still in use in many advanced countries like the UK, Japan, Canada, and Singapore while others like Germany, Netherlands, and Ireland have reverted to paper ballots after experimenting with EVMs for some time. Machine-readable paper ballots retain all the advantages of paper ballots minus the delay in counting. Here, the primary ballots are in paper form and the secondary ballots are in electronic form whereas in EVMs with VVPAT, the primary ballots are in electronic form and the secondary ballots are in paper form. Paper is more secure than electronic memory and primary paper ballots are superior to secondary paper ballots.
-2. Second, the principle of secrecy of ballot is a sacred one that must not be compromised, even slightly. In the old system, paper ballots from different ballot boxes were mixed together, thoroughly shuffled and packed into bundles of 50 ballots each, and then counted. This succeeded in masking booth-wise voting trends which would otherwise be relied upon by political parties to (i) check the effectiveness of their campaign strategies (both legal and illegal), and (ii) target collective reprisals against voters from those booths where the party fared badly. But with EVMs, the information is freely available on ECI’s website as “Booth Level Data”! This is manna from heaven for political parties because it enables them to know exactly how many supporters and opponents they have in each booth and incentivises illegal activities such as bribing of voters or targeting of opponents. But in the case of machine-readable paper ballots, it is possible to mix them and shuffle them and pack them into bundles of 50 before counting them so that booth-wise voting trends are masked. And, since paper ballots are used, no digital time-series data are available for anybody to find out who voted for whom.
-3. Third, as the VVPAT unit is an electro-mechanical (printing) device, breakdowns are quite likely. In the recent past, on an average, about 15 per cent of the VVPAT units reportedly broke down on polling day in India. While replacements are made available, there have been several cases of polling stations going ahead with the polling without the VVPAT units where there was shortage of or undue delay in replacements. Even if the quality of VVPAT units supplied is improved and the staff trained properly in their use and the percentage of breakdowns on the polling day is reduced to, say, 5 per cent, that would still be an unsatisfactory state of affairs. The ECI will be faced with the dilemma of either putting the voters to hardship by ordering repolling in these polling stations where the VVPAT units had failed and couldn’t be replaced, or of ignoring these polling stations while selecting EVMs randomly for the purpose of hand counting of VVPAT slips. Both options are unsatisfactory, the second more so. There is the danger that potential attackers, operating in collusion with dishonest insiders, will ensure that the VVPATs sent to those polling stations which have the rigged EVMs do not work properly so that the VVPAT slips of these EVMs are not taken up for hand counting, thereby defeating the very purpose of introducing VVPAT. But in the case of machine-readable paper ballots that are electronically counted using OMR technology, there is no electro-mechanical device such as the VVPAT unit that can breakdown in a polling station and so the danger discussed above doesn’t exist.
_
- Internet Voting System:
In an Internet voting system, the voter casts his or her vote using a computer with access to the Internet. Internet voting generally takes place in an unsupervised, remote location, from any computer that has Internet access, such as a voter’s home or work. It can also take place in supervised, non-remote locations if, for example, electoral authorities provide Internet kiosks at polling stations.
Convenience and greater access are the two key benefits cited for a move to Internet voting. In terms of access, Internet voting is perceived to provide access to specific populations that may have difficulty in voting at polling stations, e.g. persons with disabilities and eligible voters living outside a country. However, Internet voting from unsupervised locations requires voting systems to place a greater emphasis on voter authentication to avoid impersonation, and also elicits concerns about the secrecy of the ballot. Internet voting also raises security concerns with regard to hacking into the system or other ways of corrupting data. Similar to DREs without VVPAT, Internet voting also raises questions about verifiability, may not allow recounts and presents challenges for adjudication of electoral complaints. Finally, transparency in Internet voting systems may be compromised to an even greater extent than with DREs. Such challenges are not beyond solution, but to date remain significant.
Note:
The general term voting machine (VM) is often used to refer to DRE and PCOS systems as well as to voting kiosks for Internet voting.
______
Vote-tabulation technologies:
Most voting systems (whether document ballot or non-document ballot) can be tabulated either at the place of voting or in another location.
Precinct-count voting system:
A precinct-count voting system is a voting system that tabulates ballots at the polling place. Generally, systems that hand count the ballots will tabulate only after the close of polling. Other voting systems typically tabulate the ballots as they are cast. In all systems, the vote totals are made public only after the close of polling. For DREs and some paper-based systems these systems provide electronic storage of the vote count and may transmit results to a central location over public telecommunication network. This system allows for voters to be notified of voting errors such as over voting and can prevent residual votes.
Central-count voting system:
A central count voting system is a voting system that tabulates ballots from multiple precincts at a central location. Central count systems are also commonly used to process absentee ballots. Voted ballots are typically placed into secure ballot boxes at the polling place. Stored ballots and/or Precinct Counts are transported or transmitted to a central counting location. The system produces a printed report of the vote count, and may produce a report stored on electronic media suitable for broadcasting, or release on the Internet. Central counting can be done by hand, and in some jurisdictions, central counting is done using the same type of voting machine deployed at polling places, but since the introduction of the Votomatic punched-card voting system and the Norden Electronic Vote Tallying System in the 1960s, high speed ballot tabulators have been in widespread use, particularly in large metropolitan jurisdictions. Today, commodity high-speed scanners sometimes serve this purpose, but special-purpose ballot scanners are also available that incorporate sorting mechanisms to separate tabulated ballots from those requiring human interpretation.
_____
Results Reporting:
- DREs and precinct optical scanners (small scanners that are used in a precinct) keep a running total of results throughout the voting period, although the tally is not made public until after the polls close. When the polls close, election officials can obtain results information relatively quickly.
- Central count optical scanners (larger scanners that are in a centralized location, and ballots are either submitted by mail or are brought to the location for counting) can delay election night reporting because the ballots must be transported, which takes time. Central count optical scanners typically count 200 to 500 ballots per minute. However, many jurisdictions that use central count scanners are permitted to begin preliminarily processing, but not tabulating, ballots that they receive ahead of the election. This is true in many vote-by-mail jurisdictions that receive a large number of ballots before Election Day.
_____
Electronic voting with or without independent physical evidence of the votes cast:
Many of today’s e-voting systems in controlled environments produce physical evidence of the vote cast in the form of paper receipts for the voters (often referred to as VVPAT). Voters can verify their vote on the receipt and then deposit the receipt in a ballot box. By manually re-counting the receipts, the results presented by the voting system can be independently verified. The results of an entire election can be verified by a well-designed manual recount of receipts from a random sample of polling stations.
Electronic voting systems in uncontrolled environments commonly do not produce physical evidence as these could be used for vote-selling. Additionally, as the voter would keep the receipt, a manual recount is not possible, which renders such receipts useless. However, some Internet voting systems utilize a return code system that allows voters to verify that their vote was received unaltered by the counting server.
If electronic voting systems provide no physical evidence of the votes cast, direct verification of results is not possible. The results produced by such a system can only be indirectly verified. Indirect verification relies exclusively on a strict certification process against agreed standards in combination with tight security measures that prevent any violation of the voting system’s integrity. In these circumstances it can be difficult to communicate the reliability and trustworthiness of the e-voting system in a transparent way to a critical or non-expert audience. This might become an insurmountable challenge in a context where the EMB does not enjoy the full trust of the electoral stakeholders.
Adding a paper trail makes e-voting systems more complex and expensive. Bearing in mind the fact that many voters do not check their receipts, as well as possible mistakes in the manual recount and the need to resolve discrepancies between the electronic count and the paper count, paper trails are not a perfect solution for guaranteeing accurate and transparent elections. Still, if implemented in conjunction with proper audit procedures and mandatory random sample recounts, they become an important tool that makes it easier to build stakeholders’ trust. Paper trails allow the verification of electronic election results and make it possible to identify any faults or manipulation in an observable and easily understandable process. The lack of a paper trail is often one of the first issues raised by opponents of electronic voting.
__
None of the above electronic voting systems is completely secure. Opinions differ widely on whether the posited threats are realistic enough to warrant forgoing the added functionalities of electronic voting in favour of the perceived security of nonelectronic voting systems. Cryptographers, on the other hand, have devised systems that allow voters to verify that their votes are counted as cast. Additionally, these systems do not enable the voter to prove to a third party how they voted (thus reducing the risks of vote selling and coercion). These cryptographic systems, called end-to-end (E2E) secure, are the preferred systems from a security point of view. Thus, there is considerable academic interest in fully developing these systems. On the other hand, some people argue against E2E systems on the grounds that their mathematical underpinnings are not comprehensible to the average voter.
______
______
The following 5 fundamental principles are mandatory for every democratic electronic voting solution, according to the council of Europe.
- Universal suffrage: all human beings have the right to vote and to stand for election, subject to certain conditions such as age and nationality.
- Equal suffrage: each voter has the same number of votes.
- Free suffrage: the voter has the right to form and to express his or her opinion in a free manner, without any coercion or undue influence.
- Secret suffrage: the voter has the right to vote secretly as an individual, and the state has the duty to protect that right.
- Direct suffrage: the ballots cast by the voters directly determine the person(s) elected.
_
These can be translated to the following requirements:
- Transparency/Integrity. To make sure that the general public, as well as other key stakeholders in the electoral process, have confidence in the e-voting solution.
- Ballot secrecy/privacy. To protect the secrecy of the vote at all stages of the voting process.
- Uniqueness. To ensure that every vote cast is counted and that each vote is counted only once.
- Voter eligibility. To ensure that only persons with the right to vote are able to cast a vote.
- Verifiability/auditing. Ideally, the voter can check if his vote is counted in the end result. If not, independent auditors should be able to check the integrity of the election result.
- Accessibility. To guarantee accessibility to as many voters as possible, especially with regard to persons with disabilities.
- Vote freedom / coercion resistance. To maintain the voters right to form and to express his or her opinion in a free manner, without any coercion or undue influence.
- Availability. To ensure that the voting solution is available to the voter during the election.
_
Traditional paper voting:
To be able to compare paper and e-voting solutions, let us first look at how paper voting satisfies the requirements for a voting solution.
- Transparency. A paper trail is present, the workings can be explained to every person. A person can be an observer at the voting and counting stage.
- Ballot secrecy. Eligibility is checked when entering the polling station, and no identifiable information is present on the ballot. Ballots are folded so they cannot be read and thrown in a box.
- Uniqueness. Only one ballot form is provided, but these may be replicated and smuggled in. The amount of double votes which can be cast without getting caught will be very low. Voting twice by visiting different polling stations should be impossible because of voter registration. Voting by proxy might enable an attacker to vote a limited amount of times for others, but requires explicit consent by those who vote by proxy.
- Voter eligibility. To ensure that only persons with the right to vote are able to cast a vote. As is the case with the previous requirement, this is checked by the voting staff.
- Verifiability. With paper voting, procedures are in place to verify the integrity of the voting procedure, and the paper trail allows for reliable verification in case of doubt.
- Accessibility. Persons with severe disabilities might have difficulty coming to the polling station or filling in the ballot with a pencil.
- Coercion resistance. You will not get any proof of what you voted. A person can however be forced to vote by proxy.
- Availability. Paper voting is not dependent on electricity or an internet connection. It is however not very available when there are no polling stations nearby. This might be a problem in rural areas.
__
Table below shows differences between paper ballots voting and electronic voting:
_
The strengths and weaknesses of various e-voting systems compared to paper-based equivalents:
The table below shows an overview of the typical strengths and weaknesses that different electronic voting solutions compared to paper-based equivalents. The classification into ‘strengths’ and ‘weaknesses’ is for the purpose of a rough overview only. Details vary depending on specifics of context and systems. Cases where these details are very important are classified as ‘mixed’; cases where electronic voting has little or no impact are classified as ‘neutral’.
_______
Comparison of various electronic voting systems in different countries:
In discussing the advantages and disadvantages of the various electronic voting systems it is useful to distinguish several overlapping typologies of systems. All typologies have various strengths and weaknesses, both when compared with each other and when compared to traditional paper-based voting. There is no such thing as a perfect electronic voting system and available systems continue to evolve with ongoing technological advances. It is therefore important to choose the right system for the right context by carefully weighing the advantages and disadvantages of all options. The last few years have brought a renewed focus on to the technology used in the voting process. The current voting system has many security holes, and it is difficult to prove even simple security properties about them.
The comparison between Indian EVM and computerized EVM (DRE America) is shown in the table below.
A voting system that can be proven correct has many concerns. There are some reasons for a government to use electronic systems are to increase elections activities and to reduce the elections expenses. Still there is some scope of work in electronic voting system because there is no way of identification by the electronic voting system whether the user is authentic or not and securing electronic voting machine from miscreants.
________
________
Biometric EVM:
Biometrics refers to an automated system that can identify an individual by measuring their physical and behavioral uniqueness or patterns, and comparing it to those on record. In other words, instead of requesting personal identification cards, magnetic cards, keys or passwords, biometrics can identify fingerprints, face, iris, palm prints, signature, DNA, or retinas of an individual for easy and convenient verification. With the boom in Internet-based business and the increased need for accurate verification when accessing accounts, biometrics is the simplest and most convenient the solution. Biometrics can also provide you with convenience and security, by enabling a machine to verify the individual by itself and to respond to the individual’s requests.
The objectives of biometric recognition are user convenience (e.g., money withdrawal without ATM card or PIN), better security (e.g., difficult to forge access), and higher efficiency (e.g., lower overhead for computer password maintenance). The tremendous success of fingerprint-based recognition technology in law enforcement applications, decreasing cost of fingerprint sensing devices, increasing availability of inexpensive computing power, and growing identity fraud/theft have all ushered in an era of fingerprint-based person recognition applications in commercial, civilian, and financial domains. So, the EVM has to be improved based on the current technologies viz, biometric system. Some previous work use fingerprint for the purpose of voter identification or authentication. As the fingerprint of every individual is unique, it helps in maximizing the accuracy. A database is created containing the fingerprint of all the voters in the constituency. Illegal votes and repetition of votes is checked for in this system. Hence if this system is employed the elections would be fair and free from rigging.
_
The comparison of Paper voting, Indian EVM, DRE (Diebold) and Biometric EVM is shown in the table below:
_____
_____
Electronic voting machine manufacturers:
- AccuPoll
- Advanced Voting Solutions, formerly Shoup Voting Machine Co.
- Bharat Electronics Limited (India)
- Dominion Voting Systems (Canada)
- Electronics Corporation of India Ltd
- ES&S (United States)
- Everyone Counts (United States)
- Hart InterCivic (United States)
- MicroVote
- Nedap (Netherlands)
- Premier Election Solutions (formerly Diebold Election Systems) (United States)
- Safevote
- Sequoia Voting Systems (United States)
- Scytl (Spain)
- Smartmatic
- VOTEX / TM Technologies Elections Inc. (Canada)
_______
_______
Voting systems design criteria:
The most common desirable attributes for an ‘ideal’ electronic voting system include following:
Authentication: Only authorized voters should be able to vote.
Uniqueness: No voter should be able to vote more than once.
Accuracy: Voting systems should record the votes correctly.
Integrity: Votes should not be able to be modified without detection.
Verifiability: Should be possible to verify that votes are correctly counted for in the final tally.
Auditability: There should be reliable and demonstrably authentic election records.
Reliability: Systems should work robustly, even in the face of numerous failures.
Secrecy: No one should be able to determine how any individual voted.
Non-coercibility: Voters should not be able to prove how they voted.
Flexibility: Equipment should allow for a variety of ballot question formats.
Convenience: Voters should be able to cast votes with minimal equipment and skills.
Certifiability: Systems should be testable against essential criteria.
Transparency: Voters should be able to possess a general understanding of the whole process.
Cost-effectiveness: Systems should be affordable and efficient.
_
Voting systems security technologies:
- Cryptography: Homomorphic encryption, digital signatures, blind signatures, Trusted Third Parties, digital certificates, etc.)
- Antiviral software
- Firewalls
- Biometrics
- Smart cards
______
Emerging Electronic Voting Standards:
Electoral standards based on public international law are well-elaborated in documents issued by intergovernmental organizations such as the United Nations; the African Union; the Commonwealth; the Council of Europe; including its European Commission for Democracy through Law (the Venice Commission); the European Union; the Organization of American States (OAS); the Organization for Security and Cooperation in Europe (OSCE); and other bodies. These sources illustrate a common understanding of the content of international electoral standards, drawing directly from the wording of Article 21 of the Universal Declaration of Human Rights, Article 25 of the International Covenant on Civil and Political Rights (ICCPR), other articles in those documents related to the exercise of rights that are essential to democratic elections, and other human rights treaties, declarations and instruments. A number of rulings by international tribunals concerning genuine elections and writings of highly-qualified legal experts advance electoral standards in harmony with those sources of law, and the generally-accepted practices of states conducting elections reflect them as well.
The core of these international electoral standards can be defined as the right of citizens, without discrimination, to take part in government and public affairs, directly or indirectly through freely chosen representatives, by exercising their right to vote and to be elected at genuine periodic elections, which shall be by universal and equal suffrage, held by secret ballot and guaranteeing the free expression of the will of the electors. This combines with the right to seek, receive and impart information (i.e., the freedom of expression) about the nature of electoral processes, forming the basis for electoral transparency.
These international electoral standards frame the conditions for using any tools to secure genuine elections, including electronic voting and counting. Because these new technologies for voting and counting fundamentally change the way many components of the electoral process are conducted, the standards demand corresponding new techniques to safeguard electoral integrity and earn public trust in their use. As a result, there have been initiatives in recent years to evolve these international electoral standards in order to cope with the challenges of using voting and counting technologies. The Council of Europe’s 2004 Recommendation on Legal, Operational and Technical Standards for electronic voting did much to set the agenda for this adoption of existing standards for electronic voting and counting technologies. The Council of Europe followed up this document with several other publications, including documents on transparency and certification of electronic voting systems. The OSCE’s Office for Democratic Institutions and Human Rights, the OAS, the Carter Center and NDI have approached the issue of standards for electronic voting and counting technologies from the perspective of observing or monitoring elections in which these technologies are used. IFES and International IDEA have also sought to provide guidelines and standards for the implementation of electronic voting and counting technologies by EMBs.
In analyzing the publications by the organizations listed above, it is clear that some trends are emerging in the recommendations about the conduct of elections using electronic voting and counting technologies. Common themes can be seen in the following areas:
_
- Accuracy. The goal of any voting system is to establish the intent of each individual voter, and translate those intents into a final tally. To the extent that a voting system fails to do this, it is undesirable. This characteristic also includes security: It should be impossible to change someone else’s vote, stuff ballots, destroy votes, or otherwise affect the accuracy of the final tally.
_
- Accessibility:
Electronic voting machines can be made fully accessible for persons with disabilities. Punched card and optical scan machines are not fully accessible for the blind or visually impaired, and lever machines can be difficult for voters with limited mobility and strength. Electronic machines can use headphones, sip and puff, foot pedals, joy sticks and other adaptive technology to provide the necessary accessibility.
Figure below shows a Hart eSlate DRE voting machine with jelly buttons for people with manual dexterity disabilities.
_
3.Transparency – as much of the process as possible should be transparent and verifiable. Effective access should be provided for party/candidate agents and observers in a manner that does not obstruct the electoral process.
_
- Public Confidence – closely related to and relying heavily upon transparency is the requirement that voters understand and have confidence in the electronic voting or counting technology being used. Public confidence requires that stakeholders are: involved in the processes of deciding whether to introduce electronic voting and counting technologies and considering the type of system to be introduced; provided information so they understand the technologies being used; given the opportunity to take part in simulations of the systems that take place; allowed to monitor testing, certification and auditing and review findings; and informed well in advance about the introduction, timeline and how to participate.
_
- Usability – electronic voting and counting technologies must be easy to understand and use. Stakeholders should be involved in the design of electronic voting and counting technologies and in public testing. Further, electronic voting and counting technologies should endeavor to maximize the accessibility of the voting system for persons with disabilities and minority language groups, and must not disenfranchise others. They must also afford voters the possibility to review and amend their vote before confirmation of their choice.
_
- System Certification – electronic voting and counting technologies must be certified by a qualified, independent body before their use and periodically thereafter. This ensures the use of such electronic technologies continues to meet the requirements of the electoral jurisdiction as well as the technical specifications for the system. Further, the certification process should be conducted in a transparent manner providing electoral stakeholders access to information on the process and earning public confidence.
_
- System Testing – any electronic voting or counting system should be subjected to a comprehensive range of testing before it is approved for use by an EMB. This testing should take place transparently and with access for electoral competitors and observers.
_
- System Security – the opportunities for systematic manipulation of the results mean that system security needs to be taken seriously. Security measures need to ensure that data cannot be lost in the event of a breakdown; only authorized voters can use an electronic voting or counting system; system configuration and results generated can be authenticated; and, only authorized persons are allowed to access electronic voting, counting and results management functionality, although party/candidate agents and observers should be able to monitor the integrity of that functionality. Any intervention that affects the system while electronic voting and/or counting is taking place should be carried out in teams of two, be reported on and be monitored by the electoral authority, party/candidate agents and observers. Attempts to hack into electronic voting and counting machines or the election management system into which results are received need to be detected, reported and protected against.
_
- Auditability and Recount – electronic voting and counting technologies must be auditable so it is possible to determine whether they operated correctly. It must be possible to conduct a recount. Such recounts must involve accurate and monitored manual recounts of votes cast electronically (e.g., with the paper record representing the basis for legal determination of the vote cast) and not merely be a repetition of the electronic result already provided.
Auditability:
The auditability of a system relates to two post-election procedures: post-election audits and recounts. Post-election audits verify that voting systems are accurately recording and counting votes. Not all states conduct post-election audits and the process varies in those that do, but typically a hand count of paper ballots from randomly selected precincts is compared to the totals reported by the DRE or optical scan system. If a recount is necessary, many states also conduct a hand recount of the paper records.
_
Election auditing in electronic voting:
Election audits are critical to ensuring the integrity of election outcomes and for raising voter confidence. Auditing can demonstrate the validity of an election outcome and provide an indication of errors in ballot tabulation. Effective auditing contributes to voting security by providing an answer to the question, “Can we trust the outcome of an election when the equipment (hardware and software) used to conduct the election may have vulnerabilities or when the process is subject to human error?”
For decades, traditional audits have been performed (and have been required by law) in many states. While election administrators have performed many types of post-election audits, such as process audits, the most widely known audits have been audits of cast ballots. Traditional ballot auditing requires that election results in some fixed percentage of precincts be reconfirmed by a hand count—though the details of actual implementation can reduce the value of the audit (election administrators should not, for example, always audit the same precincts).
Hand counting every ballot cast to be certain of the outcome is extremely time-consuming, and hand counts are susceptible to error or deliberate miscounting. The use of computerized voting machines provides flexibility and processing efficiencies. Nevertheless, computers are subject to programming errors, manipulation, and outside interference. Election audits have, therefore, become more important, as the performance of audits raises voter confidence in the reported outcomes of elections. The use of networked communication at various election stages has necessitated audits that address cybersecurity risks.
An evidence-based election would produce not only a reported (or initial) election outcome, but also evidence that the reported outcome is correct. This evidence may be examined in a “recount” or in a “post-election audit” to provide assurance that the reported outcome indeed is the result of a correct tabulation of cast ballots.
Voter-verifiable paper ballots provide a simple form of such evidence provided that many voters have verified their ballots. The ability of each voter to verify that a paper ballot correctly records his or her choices, before the ballot is cast, means that the collection of cast paper ballots forms a body of evidence that is not subject to manipulation by faulty hardware or software. These cast paper ballots may be recounted after the election or may be selectively examined by hand in a post-election audit. Such an evidence trail is generally preferred over electronic evidence like electronic cast-vote records or ballot images. Electronic evidence can be altered by compromised or faulty hardware or software.
Paper ballots are designed to provide a human-readable recording of a voter’s choices. The term “paper ballot’’ here refers to a “voter-verifiable paper ballot,” in the sense that voters have the opportunity to verify that their choices are correctly recorded before they cast their paper ballots. The voter may mark the ballot by hand, or the marked ballot may be produced by a voting machine. In the current context, the human-readable portion of the paper ballot is the official ballot of record that acts as the record of the voter’s expressed choices. Any human-readable, durable, tamper-evident medium such as cloth, cardstock, or plastic could be used instead of paper.
Experts have long recommended that all elections should be audited before the winner is certified to ensure the results are correct. This entails using statistical models to retrieve a small sample of paper ballots that are examined by hand to ensure the machines recorded and counted the votes correctly. If discrepancies are discovered the audit can be escalated to a full hand count and the hand count of the paper ballots becomes the official result.
Statistical auditing techniques available now (and some in development) are more efficient and effective than earlier techniques wherein a predetermined percentage of precincts were recounted by hand to confirm the accuracy of initial precinct tallies. The implementation of statistical auditing techniques may require the allocation of additional time between the end of voting and when the official results of the election are certified.
Risk-Limiting Auditing (RLA):
Auditing a fixed percentage of precincts may not provide adequate assurance with regard to the outcome of a close election. To address this weakness, a method of auditing known as risk-limiting auditing was developed. Risk-limiting audits (RLAs) operate dynamically by examining individual randomly selected paper ballots until sufficient statistical assurance is obtained. This statistical assurance ensures that the chance that an incorrect reported outcome escapes detection and correction is less than a predetermined risk limit.
A risk-limiting audit is a post-election audit that provides strong statistical evidence that the election outcome is correct, and has a high probability of correcting a wrong outcome. An RLA manually checks a sample of ballots, or voter-verifiable paper records, until there is sufficient evidence that the reported outcome is correct. A RLA could eventually lead to a full manual recount if there is not enough evidence to prove that the reported outcome is correct. A risk-limiting audit is a method to ensure that at the end of the canvass, the hardware, software, and procedures used to tally votes found the real winners. Risk-limiting audits do not guarantee that the electoral outcome is right, but they have a large chance of correcting the outcome if it is wrong. We need “risk-limiting” audits. Here you agree in advance the probability you’re willing to tolerate of an election outcome being manipulated and not detected. You then look at enough paper ballots so the odds of someone getting away with fraud are lower than the target percentage.
RLAs offer statistical efficiency. Auditing an election with tens of millions of ballots may require examining by hand as few as several hundred randomly selected paper ballots. RLA might determine that more ballots need to be examined, or even that a full hand recount should be performed, if the contest is close or the reported outcome incorrect. Because RLAs layer a security mechanism (the risk-limiting audit itself) on top of the traditional vote-casting process, RLAs can often be performed without the adoption of new vote-casting processes. RLAs were piloted state wide in Colorado in 2017 and are now being piloted by several other states.
The most efficient RLAs (comparison audits) make use of cast-vote records (CVRs) that electronically represent the contents of each paper ballot. A ballot-comparison audit operates by randomly selecting paper ballots from a list of all cast paper ballots on a ballot manifest and comparing the voter-verified human-readable contents of the selected paper ballots to the electronic records in the corresponding CVRs. When CVRs are not available (or cannot be linked to specific corresponding paper ballots), a ballot-polling audit may be used instead when margins are relatively large. Such an audit examines only randomly selected paper ballots (and no CVRs); however, many more paper ballots may need to be sampled and examined to achieve the same statistical assurance.
RLAs can establish high confidence in the accuracy of election results—even if the equipment that produced the original tallies is faulty. This confidence depends on two conditions: (1) that election administrators follow appropriate procedures to maintain the chain-of-custody and secure physical ballots—from the time ballots are received, either in-person or by mail, until auditing is complete; and (2) that the personnel conducting the audit are following appropriate auditing procedures and the equipment and software used to audit the election are independent of the equipment and software used to produce the initial tallies. In the latter case, this not only requires that the software be independent of the software used to tally votes, but also that the software’s specifications/algorithms, inputs, and outputs are transparent to permit members of the public to reproduce the software’s operation.
_
DREs don’t generate a paper ballot. The DRE architecture’s inability to provide for independent audits of its electronic records makes it a poor choice for an environment in which detecting errors and fraud is important. For auditability, they can be equipped with a voter-verifiable paper audit trail (VVPAT) that allows the voter to verify that his vote was recorded correctly. It is the VVPATs that are used for post-election audits and recounts. Many older DREs do not come with a VVPAT. However, some election technology vendors can retrofit equipment with VVPAT printers. VVPATs look like a rolling receipt behind glass where voter’s choices are indicated on paper. Studies show that most voters do not review their choices on the VVPAT, and therefore typically do not take that extra step of verifying that their vote was recorded correctly. Newer optical scan machines can also generate a digital cast ballot image that can be used for auditing, with the actual paper ballots used as backup. Some security experts have concerns with using a digital cast vote record as opposed to going to the actual paper record, however, pointing out that anything computerized has the potential to be hacked.
_
Figure below shows a Diebold Election Systems, Inc. model AccuVote-TSx DRE voting machine with VVPAT attachment.
_
Various technologies can be used to assure DRE voters that their votes were cast correctly, and allow officials to detect possible fraud or malfunction, and to provide a means to audit the tabulated results. Some systems include technologies such as cryptography (visual or mathematical), paper (kept by the voter or verified and left with election officials), audio verification, and dual recording or witness systems (other than with paper).
Dr. Rebecca Mercuri, the creator of the Voter Verified Paper Audit Trail (VVPAT) concept (as described in her Ph.D. dissertation in October 2000 on the basic voter verifiable ballot system), proposes to answer the auditability question by having the voting machine print a paper ballot or other paper facsimile that can be visually verified by the voter before being entered into a secure location. Subsequently, this is sometimes referred to as the “Mercuri method.” To be truly voter-verified, the record itself must be verified by the voter and able to be done without assistance, such as visually or audibly. If the voter must use a bar-code scanner or other electronic device to verify, then the record is not truly voter-verifiable, since it is actually the electronic device that is verifying the record for the voter. VVPAT is the form of Independent Verification most commonly found in elections in the United States and other countries such as Venezuela and India.
End-to-end auditable voting systems can provide the voter with a receipt that can be taken home. This receipt does not allow voters to prove to others how they voted, but it does allow them to verify that the system detected their vote correctly. End-to-end (E2E) systems include Punchscan, ThreeBallot and Prêt à Voter. Scantegrity is an add-on that extends current optical scan voting systems with an E2E layer. The city of Takoma Park, Maryland used Scantegrity II for its November, 2009 election.
Systems that allow the voter to prove how they voted are never used in U.S. public elections, and are outlawed by most state constitutions. The primary concerns with this solution are voter intimidation and vote selling.
An audit system can be used in measured random recounts to detect possible malfunction or fraud. With the VVPAT method, the paper ballot is often treated as the official ballot of record. In this scenario, the ballot is primary and the electronic records are used only for an initial count. In any subsequent recounts or challenges, the paper, not the electronic ballot, would be used for tabulation. Whenever a paper record serves as the legal ballot, that system will be subject to the same benefits and concerns as any paper ballot system.
_
Punchscan is an optical scan vote counting system invented by cryptographer David Chaum. Punchscan is designed to offer integrity, privacy, and transparency. The system is voter-verifiable, provides an end-to-end (E2E) audit mechanism, and issues a ballot receipt to each voter. The system won grand prize at the 2007 University Voting Systems Competition. The computer software which Punchscan incorporates is open-source; the source code was released on 2 November 2006 under a revised BSD licence. However, Punchscan is software independent; it draws its security from cryptographic functions instead of relying on software security like DRE voting machines. For this reason, Punchscan can be run on closed source operating systems, like Microsoft Windows, and still maintain unconditional integrity.
ThreeBallot is a voting protocol invented by Ron Rivest in 2006. ThreeBallot is an end-to-end (E2E) auditable voting system that can in principle be implemented on paper. The goal in its design was to provide some of the benefits of a cryptographic voting system without using cryptographic keys.
It may be difficult for a vote to be both verifiable and anonymous. ThreeBallot attempts to solve this problem by giving each voter three ballots: one verifiable, and two anonymous. The voter chooses which ballot is verifiable and keeps this secret; since the vote-counter does not know, there is a 1/3 chance of being discovered destroying or altering any single ballot. The voter is forced to make two of his three ballots cancel each other out, so that he can only vote once.
_
Independent verification systems:
Independent verification (IV) systems or Independent Dual Verification (IDV) are voting machines that produce at least two independent auditable records of votes where the second record is used to check the first. To be considered “independent” at least one of the records must not be editable by the voting machine and be directly verifiable by the voter. These systems must allow for the multiple records to be able to be cross-checked. The goal of an IV system is to increase the security, and maintain the integrity of the voting tally. The theory is that any corruption would need to corrupt two separate records to be undetected by an audit. IV systems can include some Voter Verified Paper Audit Trail (VVPAT) systems, End-to-end auditable voting systems, witness systems, and some optical scan voting systems.
_
Note:
When using paper ballots, it is the paper ballots themselves that are used for post-election audits and recounts. No additional paper trail is necessary. Paper ballots also allow election officials to examine ballots to review voter intent. Depending on the laws of the state, a stray mark or circle may be considered when determining a voter’s intent, especially in the case of a recount.
_
- Verifiability – it must also be possible to assure voters their votes are being counted as cast while also ensuring that secrecy of the vote is not compromised. This requires that electronic voting systems create an audit trail which is verifiable. It should provide the voter with a token or code with which to perform the verification. However, the token or code must not allow the voter to prove to others how they have cast their vote. The most common solution to this for in-person electronic voting machines is through the production of a VVPAT, and this solution is emerging as a standard in this regard. It should be noted that a VVPAT is not appropriate for unsupervised remote electronic voting (e.g. Internet voting, text message voting etc.) as there would be nothing to stop a voter from removing the paper record of the vote, and making vote buying and voter coercion possible.
_
- Mandatory Audit of Results – the existence of an audit trail for electronic voting and counting systems achieves little if it is not used to verify that electronic results and the audit trail deliver the same result. A mandatory audit of the results generated by electronic voting or counting technologies should be required by law and take place for a statistically significant random sample of ballots whether or not results are subject to a dispute.
_
- Secrecy of the Ballot – the use of electronic voting and counting technologies must comply with the need for secrecy of the ballot. This requirement is not a new standard, but it is one that is made more difficult by electronic voting and counting technologies. This is especially the case for remote electronic voting systems, where voters have to first identify themselves and vote electronically using the same interface.
Secret ballots are fundamental to democracy, and voting systems must be designed to facilitate voter anonymity.
_
- Accountability in Vendor Relations – the EMB needs to remain in control of the relationship with the vendor and ensure the relationship does not violate its own responsibility to be in charge of implementing the electoral process. Any role for the vendor must be clearly defined so the EMB remains in control of the process at all times and remains accountable, should a problem arise.
_
- Incremental Implementation – whenever electronic voting and counting technologies are introduced, they should be done so in an incremental manner and should start with less important elections. This will allow public understanding and trust to develop in the new system, and provide time to deal with problems and resistance.
_
- Scalability–Voting systems need to be able to handle very large elections. Nearly 120 million people voted in the US presidential election. About 800 million people voted in India’s 2014 national elections, and over 115 million in Brazil’s 2004 local elections. The complexity of an election is another issue. Unlike in many countries where the national election is a single vote for a person or a party, a United States voter is faced with dozens of individual election decisions: national, local, and everything in between.
_
- Speed — Voting systems should produce results quickly. This is particularly important in the United States, where people expect to learn the results of the day’s election before bedtime.
It is too early to say international standards are fully evolved concerning the use of electronic voting and counting technologies. Nevertheless, trends can be seen in emerging electoral standards concerning their adoption. As a means to maintain electoral integrity, these trends in emerging standards should be carefully considered when the adoption of any new technology is deliberated and employed.
________
Security Requirements of an Electronic Voting System:
Electronic voting is more complicated than other electronic transactions such as e-commerce. Many of the security requirements required for an electronic voting scheme are not necessarily needed in other electronic transactions. Moreover, electronic voting has conflicting security requirements which are difficult to resolve, for example verifiability and receipt-freeness. Most security requirements for electronic voting also apply to traditional paper-based voting. However, universal verifiability is not satisfied in traditional paper-based schemes.
The main security requirements in an electronic voting scheme are following:
- Coercion Resistance: a coercion resistant scheme prevents a coercer from forcing voters to reveal their ballot.
- Receipt freeness: this property ensures that a voter doesn’t get any information that could be used to prove to anyone how he voted. This requirement helps to check vote buying and selling.
- Individual verifiability: this property implies that a voter is able to confirm that their vote was cast as intended.
- Universal Verifiability: in a universal verifiable scheme, anyone can confirm that votes have been recorded as cast and counted as cast.
- Privacy: This requires that the identity of the voter is not revealed. Thus, from a vote cast, it should be impossible to identify the voter. This is closely linked with, but different from, anonymity which is the unlinkability between the voter’s identity and the vote cast. This requirement gives electronic voting the ballot secrecy achieved using ballot boxes in traditional paper-based elections.
In my view, privacy, anonymity and secrecy of voting are the same in electronic voting.
- Democracy: An electronic voting scheme should ensure only eligible voters can vote and they cannot cast multiple votes.
- Robustness: A robust scheme should be resilient to external attacks such as denial of service attacks; should prevent inclusion of votes by corrupt parties for abstained voters; and should be able to recover from any faulty behavior due to collusion by malicious parties.
_____
Security controls in electronic voting system:
In conducting elections, officials must be able to assure the public that the confidentiality of the ballot is maintained and fraud prevented. In providing this assurance, the people, processes, and technology involved in the election system all play a role: the security procedures and practices that jurisdictions implement, the security awareness and training of the election workers who execute them, and the security features provided by the systems.
Election officials are responsible for establishing and managing privacy and security procedures to protect against threats to the integrity of elections. These security threats include potential modification or loss of electronic voting data; loss, theft, or modification of physical ballots; and unauthorized access to software and electronic equipment. Physical access controls are required for securing voting equipment, vote tabulation equipment, and ballots; software access controls (such as passwords and firewalls) are required to limit the number of people who can access and operate voting devices, election management software, and vote tabulation software. In addition, election processes are designed to ensure privacy by protecting the confidentiality of the vote: physical screens are used around voting stations, and poll workers are present to prevent voters from being watched or coerced while voting.
Examples of security controls that are embedded in the technology include the following:
- Access controls. Election workers may have to enter user names and passwords to access voting systems and software, so that only authorized users can make modifications. On election day, voters may need to provide a smart card or token to DRE units.
- Encryption. To protect the confidentiality of the vote, DREs use encryption technology to scramble the votes cast so that the votes are not stored in the same order in which they were cast. In addition, if vote totals are electronically transmitted, encryption is used to protect the vote count from compromise by scrambling it before it is transmitted over telephone wires and unscrambling it once it is received.
- Physical controls. Hardware locks and seals protect against unauthorized access to the voting device once it has been prepared for the election (e.g., once the vote counter is reset, the unit is tested, and ballots are prepared).
- Audit trails. Audit trails provide documentary evidence to recreate election day activity, such as the number of ballots cast (by each ballot configuration or type) and candidate vote totals for each contest. Audit trails are used for verification purposes, particularly in the event that a recount is demanded. With optical scan systems, the paper ballots provide an audit trail. Since not all DREs provide a paper record of the votes, election officials may rely on the information that is collected by the DRE’s electronic memory. Part of the debate over the assurance of integrity that DREs provide revolves around the reliability of this information.
- Redundant storage. Redundant storage media in DREs provide backup storage of votes cast or vote counts to facilitate recovery of voter data in the event of power or system failure.
The particular features offered by DRE and optical scan equipment differ by vendor make and model as well as the nature of the technology. DREs generally offer most of the features, but there is debate about the adequacy of the access controls and the audit trails that this technology provides. If DREs use tokens or smart cards to authenticate voters, these tokens must also be physically protected and may require software security protection. For optical scan systems, redundant storage media may not be required, but software and physical access controls may be associated with tabulation equipment and software, and if vote tallies are transmitted electronically, encryption may also be used. In addition, since these systems use paper ballots, the audit trail is clearer, but physical access to ballots after they are cast must be controlled. The physical and process controls used to protect paper ballots include ballot boxes as well as the procedures implemented to protect the boxes if they need to be transported, to tabulate ballots, and to store counted ballots for later auditing and possible recounts.
_____
_____
Testing and certification of electronic voting:
The six stages of testing electronic voting machines are:
- Manufacturer
- Federal
- State
- Acceptance
- Logic and Accuracy
- Parallel
_
Labs examine and test the systems according to standards developed in 1990 and rewritten in 2002. But the standards, which are currently being rewritten again, have been problematic, since they demand little in the way of security and contain loopholes that allow parts of voting systems to slip past certifiers without being tested. The labs generally test the machines for functionality but don’t thoroughly examine them for rogue software that could alter votes.
Once machines are tested, voting vendors constantly update the software. Until now, procedures for tracking and securing certified software have been extremely poor, so no one could ensure that the software tested was the same, unaltered, software used in elections. California encountered this problem when officials discovered that Diebold Election Systems installed uncertified software on its machines in 17 of the state’s counties. The National Institute of Standards and Technology recently installed a new voting software library to address this problem, but it’s unclear whether it will work in practice. The library will store checksums, which are measures used to protect the integrity of data, for certified software. Election officials can then compare their software against stored versions to ensure that it wasn’t altered. But election officials plan to use the library only when an election dispute arises, not as a matter of course before elections.
The “independent testing labs,” or ITAs, that test voting systems are not completely independent of the companies that make voting equipment. The ITAs are private, for-profit labs that receive money from voting vendors to test their systems, giving the vendors control over such parts of the testing process as who gets to view the test results. This lack of transparency means that state officials who buy voting machines seldom know about problems that occurred with machines during testing. Until now there has been no oversight of the testing labs and no clearinghouse for tracking problems with voting systems.
_
One method for verifying voting machine accuracy is Parallel Testing, the process of using an independent set of results compared to the original machine results. Parallel testing can be done prior to or during an election. During an election, one form of parallel testing is the VVPAT. Voter-verified paper audit trail (VVPAT) or verified paper record (VPR) is a method of providing feedback to voters using a ballotless voting system. A VVPAT is intended as an independent verification system for voting machines designed to allow voters to verify that their vote was cast correctly, to detect possible election fraud or malfunction, and to provide a means to audit the stored electronic results. This method is only effective if statistically significant numbers of voters verify that their intended vote matches both the electronic and paper votes.
On election day, a statistically significant number of voting machines can be randomly selected from polling locations and used for testing. This can be used to detect potential fraud or malfunction unless manipulated software would only start to cheat after a certain event like a voter pressing a special key combination (or a machine might cheat only if someone doesn’t perform the combination, which requires more insider access but fewer voters).
Another form of testing is Logic & Accuracy Testing (L&A), pre-election testing of voting machines using test votes to determine if they are functioning correctly.
Another method to ensure the integrity of electronic voting machines is independent software verification and certification. Once a software is certified, code signing can ensure the software certified is identical to that which is used on election day. Some argue certification would be more effective if voting machine software was publicly available or open source.
Certification and testing processes conducted publicly and with oversight from interested parties can promote transparency in the election process. The integrity of those conducting testing can be questioned.
Testing and certification can prevent voting machines from being a black box where voters cannot be sure that counting inside is done as intended.
One method that people have argued would help prevent these machines from being tampered with would be for the companies that produce the machines to share the source code, which displays and captures the ballots, with computer scientists. This would allow external sources to make sure that the machines are working correctly.
____
____
Cost of DRE/optical scan in U.S.:
To determine the cost of an election system, the original purchase price is only one element. Additionally, costs for transportation, printing and maintenance must be considered. Costs vary widely depending on the number of units requested, which vendor is chosen, whether or not maintenance is included, etc. Recently, jurisdictions have also taken advantage of financing options available from vendors, so costs can be spread out over a number of years. Generally, buying DRE units is more expensive than buying optical scan systems. For a broad picture, consider the comparison that was made in 2001 of the costs of purchasing new voting equipment for local election jurisdictions based on three types of equipment: central-count optical scan equipment, precinct-count optical scan equipment, and touchscreen DRE units. Based on equipment cost information available in August 2001, it was estimated that purchasing optical scan equipment that counted ballots at a central location would cost about $191 million. Purchasing an optical scan counter for each precinct that could notify voters of errors on their ballots would cost about $1.3 billion. Purchasing touchscreen DRE units for each precinct, including at least one unit per precinct that could accommodate blind, deaf, and paraplegic voters, would cost about $3 billion. For a given jurisdiction, the particular cost involved will depend on the requirements of the jurisdiction, as well as the particular equipment chosen. Voting equipment costs vary among types of voting equipment and among different manufacturers and models of the same type of equipment. For example, in 2001, DRE touchscreen unit costs ranged from $575 to $4,500. Similarly, unit costs for precinct-count optical scan equipment ranged from $4,500 to $7,500. Among other things, these differences can be attributed to differences in what is included in the unit cost as well as differences in the characteristics of the equipment. In addition to the equipment unit cost, an additional cost for jurisdictions is the software that operates the equipment, prepares the ballots, and tallies the votes (and in some cases, prepares the election results reports). For decisions on whether to invest in new voting equipment, both initial capital costs (i.e., cost to acquire the equipment) and long-term support costs (i.e., operation and maintenance costs) are relevant. Moreover, these collective costs (i.e., life-cycle costs) need to be viewed in the context of the benefits the equipment will provide over its useful life. It is advisable to link these benefits directly to the performance characteristics of the equipment and the needs of the jurisdiction.
_______
_______
Internet voting (online voting):
_
_
Definition of online voting:
Generally, online voting refers to the process of casting a ballot via an internet connection. It is commonly associated as being one type of electronic voting – a general term used to refer to many different types of voting that use information and communications technology in part or all of the voting process, which includes identifying the voter, the casting of the vote, and the counting of the vote. In their 2011 Handbook on electronic voting the International Institute for Democracy and Electoral Assistance (IDEA) defines electronic voting as “systems where the recording, casting or counting of votes in political elections and referendums involves information and communication technologies” (2011:6). A definition of internet voting provided by the US Public Policy Council of the Association of Computing Machinery (2010) explains that it is “returning an electronic form or voted ballot over the internet using email, a web application or an internet-based fax or phone (e.g. the iPhone).” The difference between these two definitions is the presence of an internet connection, characterized by the transmission of a ballot and other aspects of the voting process that take place online. For the purposes of this article internet voting is defined as systems where obtaining ballots, casting votes or counting votes in political elections and referendums uses an internet connection.
There are different types of online voting that can be distinguished by whether they occur in a supervised (controlled) or unsupervised (uncontrolled) environment. Alvarez and Hall (2003) point to four types of internet voting. Two of these, precinct internet voting and polling place internet voting involve voting online at a polling station, the former occurs at an individual’s designated polling location whereas the later takes places at any polling place. These options offer more control for election officials and less accessibility and convenience for potential voters. Next, there is kiosk internet voting which denotes voting by internet from a computer at a location that is controlled by election officials, but is not an official polling place. Kiosks are typically located in public places that are considered high-traffic areas such as a mall, library, or local government office. Finally, remote internet voting is the term most people associate with voting online. This method involves casting a ballot via the internet from a remote location, such as home, work or perhaps overseas. Remote online voting could occur on a number of devices such as a desktop computer, laptop, tablet or iPad, or mobile phone connected to the internet. This final online voting option offers election administrators the least control but provides the greatest potential accessibility and convenience for electors.
_
When people think of being able to vote online, they do not envision having to attend a traditional polling station and learn how to navigate new voting technology, but rather assume they will be able to vote from a remote location of their choosing using a personal device. Although online voting, internet voting and I-voting are the same, colloquially these terms refer to remote online voting. However, it should be pointed out that remote online voting from home or work would have to be offered in combination with online voting from central locations such as libraries or community government offices to ensure access and assistance with technical aspects.
______
Why online voting could be a good option for you:
Vote at anytime from anywhere
Poll open over six days
No leaving home/work
Avoid polling station
Boost participation
Timesaver
Work long hours
Away from home
Dependents at home
Using Internet anyway
Disabled/ill
Effortless/simple
Less physical infrastructure
More rich ballots
Fast and easy votes tally
______
Benefits, Drawbacks and Risks Associated with Internet Voting:
Benefits:
Proponents of Internet voting, make a number of arguments in favour of its implementation. These are related to technology, social issues and election administration.
First, internet voting has the potential to make the voting process easier and more accessible for electors. This is especially true for remote Internet voting and telephone voting given that ballots can be cast from any computer with an Internet connection or any working telephone. These latter methods substantially lower the cost of voting for many electors by creating many more access points from which they are able to vote. There is the potential to eliminate long line-ups at polling stations and better address accessibility issues for persons with disabilities, those suffering from illness, those serving in the military or living abroad, those away on personal travel, snowbirds and other groups of citizens such as single parents who may find it difficult to visit a traditional polling station. Additionally, remote methods of Internet voting, and in some cases kiosk Internet voting, afford electors the opportunity of being able to vote at any time, a feature that further enables electors’ ability to cast a ballot. With regard to special populations of electors, Internet (especially remote) and telephone voting may also be methods of engaging those voters who are considered the hardest to reach, particularly young people aged 18 to 30. These electors are most familiar with the technology, are the most frequent reported users and would likely benefit the most from the extension of remote types of electronic voting. Remote Internet and telephone voting seem to be especially useful ways of engaging young people away at university and who are not registered to vote in that particular constituency.
Second, Internet and telephone voting could allow greater secrecy for special populations of electors with disabilities (including visually or hearing impaired). By voting electronically and therefore unassisted, these electors are afforded a greater degree of anonymity when casting a ballot. Enabling secrecy for these groups enhances the equality of the vote.
Third, enhancing accessibility and creating more participatory opportunities for electors holds promise to positively impact voter turnout. Generally, the academic literature addressing electronic voting and turnout decline presents inconclusive results concerning whether the extension of on-line voting has a positive effect on electoral participation. In most cases where polling place voting machines that relied on the Internet for operation were used turnout did not increase. However, cases in which remote methods were implemented have produced mixed results. Though some areas, such as the UK, have not consistently noted increases, others, such as Estonia and Geneva as well as the Canadian municipalities, do report some instances of increased turnout. The length of time remote Internet voting options remain in place appears to be related to increases in both its use and in voter turnout.
Fourth, related to administration, Internet and telephone voting are claimed to produce faster and more accurate election results. Internet and telephone voting systems are said to deliver a faster official ballot tabulation process and are alleged to be more accurate than other types of machine counting (such as punching cards) which are sometimes criticized for error.
Fifth, over the long term all types of Internet voting have the potential to be less expensive to operate and execute than traditional paper ballots which require setting up and staffing polls. However, the start-up costs for machines or kiosks can be very high.
Finally, all types of Internet voting and telephone voting have the potential to improve the overall quality of ballots cast by reducing or eliminating ballot errors and by creating better informed electors. There can be no ballot errors, and, depending on the system, no spoiled ballots because the computer will not permit it. However, if the legal structure in a jurisdiction requires the option to spoil a ballot or allows for protest votes, a button can be added in some programs to give electors the option to cast a protest vote (or decline to vote). Furthermore, depending on the architecture of the Internet voting system, there is the possibility for additional information to be displayed regarding candidates and their policy positions in conjunction with the on-line vote. This would provide voters with basic information about the candidates and party platforms, and therefore better informing them to vote.
Drawbacks and Risks:
Those opposed to, or skeptical of, internet voting point to several drawbacks and perceived risks that are associated with types of Internet voting and telephone voting methods.
The most prominently cited risk relates to security. Threats of computer viruses or hacker-orchestrated ‘denial of service’ attacks are most commonly mentioned as problems that could compromise an election and public confidence in electronic voting. This concern is most prevalent with regard to the security of personal computers. In light of this, the maintenance of ballot secrecy is presented as an issue when using computers that are unprotected, located in public places, or which may be susceptible to virus attacks. Other potential technical problems or issues include power outages or malfunctions in Internet connectivity as well as the possibility of servers shutting down or crashing. The reliable recording and storage of votes is also an important consideration.
Second, problems with access are raised. The material on remote Internet voting discusses the potential for a “digital divide”, which can occur in two ways. There is a digital divide between those who have home computers with Internet connections and those who do not. Second, there may be a digital divide between those who have faster access and those who have slower connections and hence lower quality access. People with higher incomes are more likely to be able to afford access. Furthermore, access is often less expensive and of higher quality in urban areas. Those with lower incomes and who live in rural areas are at a disadvantage. Therefore, the extension of Internet voting has the potential to create divides with respect to many socio-economic variables, namely income, education, gender, geography and race and ethnicity. These potential divides could be problematic for participation and representation.
Third, it is said that remote Internet and telephone voting present greater opportunity for fraud and coercion or vote-buying. Fraud occurs when someone votes on another’s behalf without their permission, whereas coercion or vote-buying takes place when a voter is pressured by others to vote in a way that he or she would not have otherwise. Both present problems for ballot integrity since it is important that every vote cast be tallied as the voter intended. There is additional opportunity for fraud in internet voting systems if voter notification cards, which contain unique passwords required to cast a ballot, are intercepted. In the case of ballots not cast in person it is more challenging to verify a voter’s identity. Remote voter authentication can be a problem since it may be difficult to confirm that the person voting is actually who he or she claims to be. While digital signatures and passwords can help, they are not foolproof and could potentially be shared.
Fourth, the issue of voter education is cited as a concern. A lot of time and money must be invested to ensure that the public is aware that internet voting is an option and that voters are able to understand and use the on-line system to cast a ballot. Without correct marketing and advertising it will be difficult to engage electors.
Fifth, privatization is a concern when electoral administrators cede control to a hired firm. Contracting elections out to private companies to run the electronic operations has negative implications for some people, and hence has the potential to negatively impact public confidence and trust in government and elections.
Finally, perhaps the most significant social concern is the threat of disintegration of social capital or civic life. The proliferation of electronic election services has the power, some say, to alter the nature of electoral participation by causing more electors to vote alone instead of at a polling place with others. This threatens to erode civic life, local social networks and groups related to elections (see Putnam, 2000).
_
While above paragraph provides a general treatment of the major advantages and drawbacks to Internet and telephone voting, there are pros and cons which are unique to each particular internet method. These are presented in table below. It also includes instances where these methods have been trialed or implemented.
_
Benefits and Drawbacks of Various Internet Voting Methods:
| System Type | Benefits | Drawbacks and Risks | Where Method Has Been or Was Used |
| Remote Internet voting |
|
|
|
| Kiosk Internet voting |
|
|
|
| Polling place Internet voting |
|
|
|
| Precinct Internet voting |
|
|
|
| Telephone voting |
|
|
|
____
____
Security vulnerabilities of online voting:
A list of common security threats associated with online voting systems that are not present in traditional paper voting at the polls where ballots are counted by hand can be found in table below.
| Threat | Description |
| Vote Selling and Coercion | The unsupervised nature of internet voting means that others can observe electors while voting, and their vote choice could be unduly influenced. |
| Prevention of Phishing | Online avenues that seek to misdirect voters into visiting misleading or malicious websites, or visiting legitimate websites that are vulnerable to loading malicious third-party content. |
| Automation bias | Habituation and lack of knowledge about the goals and purpose of common web security technologies can lead users to place an undue reliance on technological protections and underestimate the significance of warnings or errors. For example, not noticing when the green padlock icon is missing, or clicking through browser security warnings). |
| Denial of Service | Occurs when a server is flooded with connection requests from numerous computers or devices. These types of attacks can be mitigated; however, they do occasionally cause significant disruptions. For example, a denial of service attack in 2015 caused Canadian government websites to be inaccessible for several hours. |
| Client-side Malware/Spyware | Malicious software on a voter’s computer with the intention of altering and/or surveilling ballot selections. |
| Server penetrations | Compromising or attacking the server running the internet voting portion of the election. An attack could be the result of any combination of undisclosed software vulnerabilities, misconfigurations, or human error that would allow a remote attacker to gain access to voter data. An example of a server penetration is IP theft. |
| Insider Influence | Risk that insiders (e.g., election officials, vendors or other technical personnel) can view or modify vote choices on the server, making it vital for there to be strong mechanisms to prevent undetected changes to votes. |
| State-level Actors | A sophisticated and undetected attack by a state-level actor where an election outcome is changed. |
Such security vulnerabilities and possible breaches have the potential to negatively affect public trust in elections. If an election, or part of an election, was compromised because results were delayed or tampered with, there could be a loss of public faith in electoral institutions and processes. It is difficult to predict this impact. At the Online Voting Roundtable some experts suggested that a security breach in a binding election might not affect public trust too much since Canadians have come to expect a certain degree of risk in anything carried out online (e.g. banking). In the United States, for example, according to Gallup levels of public trust in elections already reached a low of 28% in May 2016 before allegations of Russian hacking, and were not much higher in 2011 (Zuesse, 2016). Furthermore, despite the US intelligence community’s assertion that Russia is responsible for the 2016 election-related hacks, nearly half of Americans say we cannot be sure since the intelligence community was wrong that weapons of mass destruction were in Iraq (Bordelon, 2016). To promote public faith in elections if remote online voting is introduced (or any other electronic-based vote casting or counting technology) there needs to be strong transparency and scrutiny of the process, especially if an outcome is challenged.
_______
Auditability of online voting:
Auditability of voting must be maintained with online voting. Those who can audit an online voting system may be different than persons who could assess a paper-based scheme given that technical knowledge may be required. A critical part of system auditability, which can present additional challenges to ballot secrecy, is the verifiability of the vote. The issue of verification has been present in computer science and engineering debates for some time (Gritzalis, 2002) but emerged in practical online voting debates sometime after the first few phases of initial deployments around the world probably because as the number of online voters increased so did the associated risk. The idea behind verifiability is to act as a mechanism to ensure the accuracy of the election outcome (Benaloh et al., 2014; US Vote Foundation, 2015). From the outside an election might appear to have been properly conducted and produced an accurate outcome, but there is the possibility that errors and fraud could go undetected. To mitigate this online voting systems can be made verifiable. There are two types of verifiability – individual verifiability and universal verifiability. The former is based on a voter being able to ensure their ballot was cast as intended and recorded correctly. Universal verifiability or end-to-end verification (E2E) is considered to be the gold standard in terms of verifying election outcomes. Like individual verifiability it is based on the principle of confirming that a voter’s ballot was cast as intended and that votes are tallied as cast, meaning that “any member of the public can verify that every recorded vote is correctly included in the tally” (Benaloh et al., 2014: 2).
______
Public Attitudes towards online voting:
Implementation of online voting would not be possible without a culture of support from citizens. It is important that the public retain a strong sense of confidence and trust in the electoral process and be generally supportive of the notion of electronic voting.
Elections Canada survey data offers important insights regarding the Canadian publics’ expressed likelihood to vote by Internet. Overall, the data shows that there is a moderate increase in the proportion of respondents who report being likely to make use of Internet voting over time. While in 2000, for example, 47 percent of respondents report being likely to vote on-line, in 2008, interest rose to 54 percent of respondents. We also see that respondents’ reported likelihood to use on-line voting either increases over time or remains consistent for all age groups. In fact, aside from those electors over the age of 54, a majority of respondents in all age groups indicate that they would be likely to make use of on-line voting if the service were available. Except in 2008, where the numbers are virtually identical, non-voters responding to election surveys are more inclined than voters to say that they would be more likely to vote on-line in the future. In fact, a greater proportion of respondents aged 18 to 34 reports being likely to make use of on-line voting than having voted. This suggests that some non-voting electors may be encouraged to participate through Internet voting. Overall, the figures suggest that the extension of Internet voting may be a useful way of appealing to younger electors as well as encouraging some non-voters to participate in the electoral process.4 It also highlights that older electors are less likely to make use of on-line voting.
Another important consideration with respect to public attitudes is the rationale provided by electors for not voting. If the extension of Internet voting is to encourage participation then it should address one or more of the reasons respondents cite for not casting a ballot. Elections Canada survey data reveals that among the general population in all survey years, time constraints or accessibility issues are mentioned most commonly to account for respondents not voting. For example, three of the top four reasons respondents provided as rationales for not voting in 2008 include being too busy (16 percent), traveling or holidays (16 percent) and their work or school schedule (11 percent). In 2006 by comparison, 27 percent of respondents reported not voting because their work or school-related obligations prevented them from casting a ballot. In 2004, two of the top four reasons mentioned for not voting were being too busy with work (12 percent), or personal and family life (11 percent). Twenty-seven percent of respondents rationalized not voting in the federal election in 2000 by citing a lack of time or work obligations. In addition, reasons for not voting, such as illness, absence from the country or constituency, and missing registration information (including poll location), could potentially be remedied with an available remote Internet voting option.
______
Case studies of electronic voting:
I-voting: Estonia:
Estonia is one of the few countries that makes extensive use of I-voting. Introduced in 2005 for local elections, the system has been used ever since and is an increasingly popular way of voting. During the 2015 Parliamentary Elections, 30.5% of votes cast were I-votes. It is interesting to note that the voter turnout has slightly increased (61.9% in 2007, 63.5% in 2011, 64.2% in 2015). This supports the often-heard statement that I-voting helps increase voter participation. However, research conducted in Switzerland concludes that “internet voting does not attract new voters or young voters and it has a substitution effect as it replaces postal voting”. Additional research will be required in order to draw stronger conclusions on how internet voting changes voter participation.
_
The system:
The architecture of the Estonian I-voting system is as follows. Citizens that want to cast their vote use their web browser to connect to a government website and download a program. This program guides the voter through the voting process, allowing the voter to pick the candidate of his choice. The vote is now encrypted with the election key, a public key that is stored in the application and is different for every election. This way, all votes are encrypted and may only be decrypted on a machine that possesses the private election key. Some random data is added to the vote prior to encryption, to make sure no two identical votes result in an identical ciphertext. Omitting this random data would allow an attacker to obtain the contents of the vote by comparing the ciphertext of the vote to all possible encryptions of valid votes. The random data is stored on the client machine for some time, as it is required for vote verification. The vote now needs to be signed by the voter. This is done with a USB smartcard reader and an Estonian National ID card. This card contains a chip that stores two RSA keys, one for encryption, one for signing, and is widely used for online banking and government services. The RSA keys cannot be extracted and in order to be able to use the card for signatures or encryption, the voter must first enter a pin. The downloaded voting program asks for this pin and then asks the smartcard to sign the (already encrypted) vote. The encrypted, signed vote is now sent to the election servers. Upon reception, the election server sends back a unique, unguessable token. The voting program confirms that the vote was submitted, and displays a QR code based on the random data used for the encryption step together with the random token received from the voting server. Using a smartphone app, the voter may scan this QR code. The app then sends the token to the voting server, which responds by sending the encrypted vote. The app now checks if the intended vote plus the encryption randomness indeed encrypts to the same ciphertext as received from the voting server. This verification mechanism is possible for up to 30 minutes, in order to limit the possibility of coercion by others asking for ’proof’ that a voter did indeed vote for a specific candidate. After reception of the vote by the system, the vote is temporarily stored on the Vote Forwarding Server. This server is the only one of the infrastructures that is directly accessible from the internet and verifies voter eligibility before forwarding the vote to the Vote Storage Server. All votes are collected here until the I-voting phase ends. At that time, when it is no longer possible to cast a vote, all votes that are stored on the vote are once more verified and then the signatures are stripped from the votes. The resulting set of anonymous, encrypted votes are burned onto DVDs. The DVDs are then transferred to the Vote Counting Server, an air-gapped machine that contains the election private key. This private key is now used to decrypt and count every vote. The result is the sum of the votes for each candidate.
_
Design risks:
The design of the Estonian I-voting solution has several conceptual shortcomings. These shortcomings are important, as they are very difficult or impossible to mitigate without redesigning important parts of the system.
- Assumes voter’s computer is trustworthy
This is a dangerous assumption, as many computers are infected with some kind of malware. For high-stakes elections, an attacker may be able to attack and infect a large number of computer systems, allowing him to change a vote cast from an infected machine to any candidate of the attacker’s choosing. Of course, the smartphone-based verification app serves to mitigate the risk of this kind of attacks. However, smartphones are frequently connected to their owners’ computers, and an attacker could choose to only modify a vote if an associated smartphone has also been infected. This is not very practical, though, as the attacker will want to modify as many votes as possible in order to maximize his influence in the outcome of the elections.
A more interesting approach would be to take advantage of the fact that verification is only possible for up to 30 minutes. An attacker could let the user cast his vote, and if after 30 minutes the smartcard is still connected, cast another vote for a candidate specified by the attacker. The user could successfully validate that his vote was cast (as it was indeed properly received by the system), but will not be aware of the fact that his previous vote has been overridden by a new vote cast by the attacker.
- Assumes voter can securely download the voting application
An attacker controlling any part of the network between the voter and the application download server would be able to intercept and modify any HTTP request/response pair. The download of the application itself is done over HTTPS, which is supposed to provide confidentiality and, more importantly, integrity. However, if an attacker can intercept one of the earlier HTTP requests, he can manipulate the traffic in order to trick the client into downloading the application over an unencrypted socket and provide the user with an infected or patched voting application.
Another possibility would be for an attacker to obtain a valid certificate for the download server’s domain, which should not be possible unless the attacker can convince a certificate authority to cooperate. In this case, the attacker can provide the expected secure HTTPS connection while still tricking the user into downloading a modified application. It is not a simple task to convince (or exploit) a certificate authority in order to obtain a certificate, but for state-level or very well-funded adversaries this is certainly a scenario to consider.
- Assumes the counting server is trustworthy
While the counting server is air-gapped and located in a locked rack in the data center, the server is an obvious security risk. If an attacker could in any way tamper with the machine, there is no guarantee that the election results do indeed correspond with the votes cast by the users. There are many ways to tamper with a machine, as malware may be introduced at any point from manufacturing to the moment the votes are being counted. Additionally, some malware may be extremely difficult to detect, such as BIOS-based malware or advanced rootkits.
_
Procedural risks:
Part of the security of the Estonian I-voting system relies on procedures, intended to make unauthorized interference impossible. The Internet Voting Committee published extensive procedures, that cover many of the steps and possible events that might occur during the election process. However, there are flaws in the specified procedures, that are discussed below.
- Unclear and/or incomplete procedures
It was found that some procedures were unclear and/or incomplete. An example of this is that the server racks in the data center are equipped with tamper-evident seals. Although even the added value of these seals is questionable, as they can be defeated with widely available tools, there was another problem: there was no procedure for how to act if a seal would be found damaged. One might argue that if a situation occurs for which there is no procedure, the integrity of the election can no longer be guaranteed. Also, some procedures seemed to be specified or changed during the actual election period. An example is that observers were initially allowed to bring cellphones into the data center, but this changed and was no longer allowed days after the election period started. This suggests that some procedures were not sufficiently thought out.
- Leakage of secrets through Youtube videos
In an effort to increase the transparency and verifiability of the deployment and configuration of the infrastructure, videos are recorded whenever the system administrators interact with the trusted parts of the system. These videos are then published on Youtube, allowing anyone to verify that the interactions with the system are performed according to protocol and in an honest way. While this is a great idea to mitigate the risk of manipulation by malicious insiders, it also is a security risk, as secret information may unintentionally be recorded and published. Drew Springall et al. found that there are indeed multiple recordings that contain secret information. In figure below (a), we see how the root password is being typed in. By carefully analysing the keystrokes, an attacker could either obtain the exact password or at least reduce the search space to a few possibilities per character. Figure below (b) shows how a note on the wall shows the password for the local WiFi network.
- Use of untrusted computers for sensitive operations
Another example is where the voting application is being compiled. Close inspection shows that the machine used to build the application contains software like BS Player FREE and a link to PokerStars.ee. This kind of software is not appropriate for a machine that is being used to compile important software, as the presence of malware cannot be excluded.
- Occasional deviation from protocol
On several occasions, the election staff deviated from protocol. For example, when attempting to burn the encrypted votes to DVD on the Vote Storage Server, there was a technical issue. Instead of resolving the issue in order to be able to burn the votes to DVD according to protocol, a staff member decided to use his personal USB flash drive in order to transfer the votes to the counting server. This is a severe breach of protocol, as the flash drive contained personal documents and was absolutely not guaranteed to be free from malware. More importantly, a flash drive may be crafted by an attacker to exploit some vulnerability on the counting server.
_
Does Estonian I-voting system meet the requirements of electronic voting?
Transparency– Some parts are not open source, some procedures are not on video and one has to trust the counting server.
Ballot secrecy– Signatures are separated from the votes before counting. Vote contents are only determined afterwards, ensuring anonymity.
Uniqueness — Voters are allowed to vote multiple times. The backend will check for duplicate votes, only the most recent vote is taken into account. Voting twice will invalidate the first vote.
Voter eligibility –The national ID card is used for authentication, and voter eligibility is checked properly.
Verifiability — No independent auditing is done during the election period. Important parts of the system are based on trust. Additionally, deviations from protocol make verification even harder.
Accessibility — The system is easy to use and does not require physical presence of the voter at a polling station.
Coercion resistance — Although somewhat mitigated by the possibility to vote again, voting from a remote, uncontrolled environment is inherently sensitive to coercion.
Availability — A DOS attack has been found, that may disrupt the possibility for electronic voting. However, the impact on the democratic process would be limited as citizens could still go vote in person the day after I-voting ends.
______
______
Challenges and security concerns in using electronic voting:
Electronic voting systems play a vital role in elections, but they are only one component in a multidimensional process. The people, processes, and technology that make up these various dimensions all contribute to the success of the overall election process. From a national perspective, this overall process involves many levels of government, including thousands of jurisdictions with widely varying characteristics and requirements. For example, the size of a jurisdiction and the languages spoken by voters are significant variables in local election processes, as is the performance of the particular voting system used.
An electronic voting system, like other automated information systems, can be judged on several bases, including how well its design provides for security, accuracy, ease of use, and efficiency, as well as its cost. For example, direct recording electronic systems offer advantages in ease of use because they can have features that accommodate voters with various disabilities, and they protect against common voter errors, such as overvoting (voting for more candidates than is permissible); a disadvantage of such systems is their capital cost and frequent lack of an independent paper audit trail. Advantages of optical scan voting equipment (another type of electronic voting system) include capital cost and the enhanced security associated with having a paper audit trail; disadvantages include lower ease of use, such as their limited ability to accommodate voters with disabilities.
One important determinant of voting system performance is how it is designed and developed, including the testing that determines whether the developed system performs as designed. In the design and development process, a critical factor is the quality of the specified system requirements as embodied in applicable standards or guidance. For voting technology, these voluntary standards have historically been problematic. A second determinant of performance is how the system is implemented. In implementing a system, it is critical to have people with the requisite knowledge and skills to operate it according to well-defined and understood processes. In the upcoming national elections and beyond, the challenges confronting local jurisdictions in using electronic voting systems are similar to those facing any technology user. These challenges include both immediate and more long-term challenges, as shown below:
__
Weighing the Benefits and Challenges:
The increasing adoption of these new technologies in some regions comes in part from the recognition that technology may offer benefits over traditional methods of voting and counting. Such benefits may include:
-eliminating the cost and logistics involved with paper ballots;
-improved voter identification mechanisms;
-improved accessibility to voting;
-easy conduct of complex elections; increase in voter turnout;
-eliminating invalid ballots;
-faster, more accurate and standardized counting of ballots; and
-prevention of certain forms of fraud.
However, the use of new technologies brings new challenges. These challenges may include:
- lack of transparency;
- negative impact on confidence in the process;
- confusion for the illiterate or uneducated voters on process;
- need to conduct widespread voter education, how to use it and its impact on the process;
- difficulties in auditing results;
- secrecy of the ballot;
- security of the voting and counting process;
- cost of introducing and maintaining the technology over the lifecycle of the equipment;
- potentially losing control over the process to outside technology vendors; recruitment of staff with specialized IT skills;
- added complexity in the electoral process and the ability of the EMB to deal adequately with this complexity; and
- consequences in the event of equipment or system malfunction.
In addition to these challenges, it is also vitally important that electronic voting and counting systems are implemented in such a way as to not violate core electoral standards.
The challenges need to be carefully considered and balanced against anticipated benefits when deciding whether to use such technologies for elections. The relevance of each of these possible advantages and disadvantages will vary from country to country, as will the challenges and issues presented by the existing system being used for elections. Therefore, there is no one answer on the appropriateness of using election technologies. Rather, each electoral jurisdiction will need to fully assess possible advantages and disadvantages to see whether using such technologies is beneficial.
Because the decisions on these matters will profoundly affect voters’ confidence in electoral results, the assessment should be made through a broadly consultative process and be based on equally broad consensus. Without such inclusive and transparent deliberations, suspicions that often exist in competitive political environments may undermine the decision to use electronic voting or counting systems, and erode the legitimacy of the electoral process.
____
Design challenges for ECI and manufacturers of EVM in India:
When the ECI delegated ECIL and BEL to design an electronic voting machine, a number of challenges particular to the Indian context, had to be considered. This includes the cost of those machines, power supply, natural hazards, illiteracy, technological illiteracy and booth capture.
Due to the huge number of machines employed all over the country and due to a limited budget, the ECI wanted to keep costs as low as possible. Through the eyes of the economic research team this goal has been achieved successfully: compared to other nations such as the USA, Indian voting machines are much more inexpensive. Each machine comes at a price of Rs. 8670 plus taxes from the manufacturer (ECIL, 2012-13), which translates to 104.76 Euros (at exchange rate of 1 Euro = 82.8 INR, 2014).
The geography of India poses challenges, since many polling stations across the country are in remote areas without electricity supply. In past elections the polling officials have made amazing efforts to make voting possible in even the most remote villages in the Himalayan Mountains or the deserts of Rajasthan. Their means of transportation include boats, elephants, camels and ferries and sometimes the polling teams are trekking through many kilometers of jungle. There are areas where you have to walk for 6 days to reach the polling station. Due to those obstacles Indian EVMs are entirely operating on battery power and are stand-alone machines, not connected to any network. Compared to the old paper ballot boxes, EVMs are lighter, which also makes transportation easier. So generally, EVMs are a relief for the ECI.
Extreme temperatures – from the freezing Himalayan mountain to boiling heat in the jungle and deserts – and other environmental hazards like dust and pollution, pose further challenges for EVM design and operation. Sometimes it rains so hard that the roads to the polling centers are not motor able and the only way is travelling on elephant back. EVMs must withstand those extreme conditions and have the capacity to absorb external shocks. Often EVMs are stored for extended periods in facilities that lack climate control. The Expert Committee of the ECI wrote in one of their reports about dangers from “attack by vermin, rats, fungus” that might cause malfunction. In the eyes of the government these kinds of challenges are successfully addressed in the EVM design: The government of India has stated they are robust enough “to withstand rough handling and variable climatic conditions”.
The total adult literacy rate in India in 2008-2012 was about 62.8 per cent (UNICEF, 2014). Hence the machines need to be easy to use and not require written instructions. Political parties and candidates use graphical symbols in their campaigns, which are then found on the ballot unit (BU). The Presiding Officer will have a card-board replica of the ballot unit with him, to demonstrate to the illiterate voters how to vote. Illiterate people find it easier to press a button than putting stamp on a paper. Hence in technical terms electronic voting does not pose any problems for the illiterate.
On the other hand there are still people in India who are unfamiliar with technology and there have been reports of people from tribes who felt intimidated by the machines. Moreover blind voters have also been taking into consideration and the machines are made braille compatible. The problem of booth capture as such cannot be prevented with the EVMs. However, the machine cannot register more than 5 votes in a minute or 300 votes in an hour whereas a ballot box could be stuffed with any number of ballot papers.
______
______
Technical Challenges of electronic voting:
- Design Flaws:
An important decision when defining a strategy for e-Voting is whether to use open-source or proprietary software. This is particularly relevant to the question of trust. Many companies use proprietary e-Voting software, which has the disadvantage that in most cases, the source code is not available to the rights holder. The security analysis of the source code of Diebold AccuVote-TS 4.3.1 has been analyzed. It is one of the first electronic machine paperless voting systems used in a large market share. It is based on Windows CE and is developed in C++. The analysis shows that this voting system is far below even the most minimal security standards applicable in other contexts. Several problems including unauthorized privilege escalation, incorrect use of cryptography, vulnerabilities to network threats, and poor development process software were identified. It is suggested that the best solutions are systems with an “audit trail voter verifiable,” where an e-Voting system might print a ballot that can be read and verified by the voter as he votes.
- Spoofing:
The website may look exactly like a voting site in the state, but redirect the browser of the voter to a malicious Web server. There are many ways that an attacker could spoof a legitimate site vote. One way might be to send emails to users tell users to click on a link, which then set up a voting site were false adversary could collect the credentials of the user, to steal the vote, and then use it to vote differently. An attacker could also establish a connection to the legitimate server, feed the user a fake web page, acting as a man in the middle, transfer, and control all tracks between the user and the web server.
- Malicious Payload:
Malicious payload is a threat to the security of the personal computer of the voter. The malicious payload is software or configuration to damage and could be a virus, worm, Trojan horse or a remote-control program that is perhaps the greatest threat in a scenario of voting. If a malicious program is installed on the computer of the voter, it could change the secret ballot. The owner of the computer may not be aware of even have one installed because these programs can be difficult to detect (run in stealth mode) malware. Malware of this kind have increased in sophistication and automation in recent years in a way that they can do more damage, more likely to succeed and to dress better. Even if a system of Internet voting has strict protocols for encryption and authentication, malicious code can do its damage before the other security features are applied to the data.
- Attacks:
E-Voting technology can speed the counting of ballots and provide better accessibility for disabled voters. However, e-Voting could also facilitate electoral fraud. Internet based voting systems require strong safeguards against hacking attacks, viruses and Trojans. Software continues to get complex and can never be bug free. A virus or network attack can also be mounted during the verification process and result in false positive verifications. Network attacks may be met by cryptographic key exchange and distributed back-end databases. Information dispersal algorithms and verifiable secret sharing schemes may be used to maintain system fairness such that no single server stores all the cast ballots and the partitions are distributed over independent servers. Threats could be, for example internal vendor, election officials. Alternatively, they can be external, such as individuals, organizations and funded, states, parties, criminals, terrorists, many of whom cannot even be prosecuted.
Voting systems based on the Internet are vulnerable to attack by three main points; the server, the client and the communication infrastructure. Penetration attacks target the client or server directly while DoS attacks target service and interrupt the communication link between the two. The penetration attacks involve the use of a distribution mechanism for carrying a malicious payload to the target host in the form of a Trojan horse program or a remote control. Once executed, it can spy on the ballots, prevent voters from casting ballots, or worse, change the ballot according to his instructions. Remote control software can compromise the secrecy and integrity of the ballot by those who monitor the activity of the host.
-Physical Attacks:
Many physical attacks can be made on the e-Voting system to sabotage the election. Vandalism of e-Voting systems makes it unusable for Election Day. Saboteur can remove network connections and pull the plug on e-Voting systems causing lost votes. Attackers can remove hard disks or smart cards to replace falsified data. E-Voting machines could be stolen by attackers discover information confidential voting on users.
-Overloading Attacks:
(a) Denial-of-Service (DoS) Attack:
Distributed Denial-of- Service (DDoS) attack is an attack on a computer system or a network in which a simple auto-mated request is repeated at a very high frequency, with the aim of overloading the connecting lines of the system or the calculation of capabilities. These attacks are detectable and may require the postponement of the election. EMB should therefore check what security measures were put in place to protect systems against such attacks. DoS attacks are performed by automatically sending a flood of messages on a website, server, or on a channel similar to crash or reduce the quality because it cannot handle all the traffic generated. Using a DoS attack distributed (DDoS), attackers can cause routers to crash or electoral servers being flooded, or it is possible to attack a large number of hosts such demographically targeted to stop the operation of the election. This can be a major threat to Internet voting if such voting takes place in one day. It is important to have additional bandwidth to handle the traffic and some voting systems.
(b) Ping of Death:
The ping of death relies on a flaw in some Transmission Control Protocol, Internet Protocol (TCP/IP) stack implementations. The attack relates to the handling of unusually and illegally large ping packets. Remote systems receiving such packets can crash as the memory allocated for storing packets over flows. The attack does not affect all systems in the same way, some systems will crash, and others will remain unaffected.
(c) Packet Flooding:
Packet flooding exploits the fact that establishing a connection with the TCP protocol involves a three phase’s handshake between the systems. In a packet flooding attack, an attacking host sends many packets and does not respond with an acknowledgement to the receiving host. As the receiving host is waiting for more and more acknowledgements, the buffer queue will fill up. Ultimately, the receiving machine can no longer accept legitimate connections.
-Receipt Attacks:
(a) Trash Attack:
The idea of the trash attack is that if voters throw away their (paper) receipt, then authorities who find these receipts could conclude that these voters will not check their receipts on the bulletin board, and hence, ballots of such voters can safely be modified.
(b) Clash Attack; the simple idea behind the shock attack, is as follows. Voting machines are trying to provide different voters with the same reception, where the name of the attack. Accordingly, the authorities can safely replace the ballots news on the scoreboard; therefore, manipulate the election without being detected. It has been shown that, surprisingly, many e-Voting systems that have been designed to provide the verifiability between systems that have been used in real elections are vulnerable to this attack, under realistic assumptions of trust in machines and authorities vote. It must be noted that the shock attack can work even if the voters and election observers know exactly how and what the electorate voted. So confront attacks are different and more subtle than the known ballot stuffing attacks (see, for example, attacks ballot stuffing). This attack does not seem to have attracted much attention in the literature.
-Man-in-the-Middle Attack:
Fraud in the form of fake servers must also be taken into account. Some server may pretend to be the official server by tampering with the DNS or by using a name very similar to that of the official server (Man-in-the-Middle). To protect the system against Man-in-the-Middle attacks, a digital signature may be applied to the ballot to ensure verification of the voter submitting the ballot. However, it is of utmost importance that the confidentiality of the vote is not threatened.
-Viruses
A computer virus is a computer program that can reproduce itself and may cause undesired effects in computers where it is active. To do its malicious work, the virus needs executing. Usually viruses are located together with other code that is likely, will be executed by a user. As long as the virus is active on the computer, it can copy itself to other files or disks when they are used (Technology Corner, 1999). Viruses made could destroy voting systems that use ICT. This could compromise the availability at election time forcing governments and institutions to perform re-elections.
-Worms
A worm is a type of virus that does not change any existing program or file to spread itself. Instead, it makes copies of itself within an infected computer and spreads to become active on other systems. It is intentionally destructive, overwriting portions of the files with random data (Technology Corner, 1999). This damage is non-repairable, so files may need reinstallation or restoring from a backup. Worms could overwrite files and change results of votes if programmed to do so, brining the integrity of the votes into question.
-Trojan Horses
Trojan horses are pieces of computer code that download to a computer while connected to the Internet. They may be harmless, but it could possibly delete or modify an important file from the computer, plant a harmful virus, or even steal users’ passwords (Technology Corner, 1999). This makes all sorts of fraudulent schemes possible. Once inside a computer the Trojan horse can access passwords, screen names and other personal information and then distribute this confidential data to the attacker. Trojan horse represents an immense threat to systems confidentially and integrity of information of voting systems that use ICT.
______
Insider Threat:
According to Schneier, 2009 “Insiders are especially pernicious attackers because they’re trusted. They have access because they’re supposed to have access. They have opportunity, and an understanding of the system, because they use it or they designed, built, or installed it. They’re already inside the security system, making them much harder to defend against.” The UK Cyber strategy also notes that “Computer systems, networks and applications all rely upon people for their development, delivery, operation and protection and the likely success of an attack is increased when a so-called ‘insider’ is involved”. The insider threat is a well-documented issue and one of the biggest threats to organizations. About 53% of attacks on organization have been deliberate actions or negligence by staff. 54% of IT staff feel it is difficult to detect insider threats while 33% of organization have no formal response plan (Cole, 2014). Attackers have realized that it is difficult to attack secure networks, so they find easier routes, like targeting individuals that work in organizations. An example is the 2011 attack on RSA secureID where phishing emails with an attachment that contained malware was sent to a group of unsuspecting employees who downloaded the files allowing the attackers to gain access to the network.
In e-voting literature, the insider threat and how it could mar an election is not often considered. Instead some schemes assume electoral officials can be trusted to carry out vital functions such as authentication (Springall, et al., 2014) of voters or transfer of sensitive information from one entity (i.e. a server) to another (Culnane, Ryan, Steve, & Vanessa, 2015). This could have been done more securely by technology. This trust in human procedures and processes over technology is an assumption in the I-voting scheme and prêta-voter. In an analysis of the electoral process in Estonia (Springall, et al., 2014), researchers recorded various lapses in procedures which introduced vulnerabilities that could be exploited. The financial benefits for malicious insiders is enough incentive for them to either aid an attack or look the other way when this happens.
With vulnerable electoral officials, it is important to ensure that the technical security employed in voting schemes should reduce threats posed by insiders. Hence, auditability of the process and verifiability of votes cast should be satisfied for a voting scheme to be credible.
_____
Cyberthreat and Foreign Government Influence:
Cyber threat and cyber warfare have become a serious issue that organizations and governments are dealing with. There have been various reported cases of state sponsored attacks like the alleged North Korean attack on Sony or alleged United States attack on Iranian nuclear enrichment plant (Langner, 2001). Increasingly we continue to see allegations of foreign government influence in the democratic processes of other nations. In addition to the current controversy surrounding recent elections in the USA, it has been alleged that Russia carried out a state sponsored Distributed Denial of Service (DDoS) attack on Estonia in 2007. In Hong Kong, the largest and most sophisticated ever DDoS attack hit an online democracy poll that canvassed opinions for future elections in the country. Also, in Ukraine a virus that was meant to delete votes during the presidential elections hit their Central Election Authority.
In Washington DC, an Internet voting system was designed to allow oversea absentee voters cast their votes, this was a pilot project and it was tested as a mock election in 2010. Some researchers (Wolchok, Wustrow, Isabel, & Halderman, 2012) attacked this system and gained full access within 48 hours, changing every vote and revealing almost all secret ballots. These Cyber-attacks have created a completely different threat environment that did not exist before, and now that nations are pushing for e-voting this should be considered when designing e-voting schemes.
In the literature, many schemes don’t consider the threat of a cyber-attack. In the I-voting scheme used in Estonia, lapses where shown in the electoral process and architecture that could create avenue for a cyber-attack (Springall, et al., 2014). The implicit trust placed on voters’ computers in some Internet voting schemes clearly shows that cyber threat was not considered in their design.
______
______
Security concerns of electronic voting:
During the 2016 presidential election, America’s election infrastructure was targeted by a foreign government. According to assessments by members of the U.S. Intelligence Community, actors sponsored by the Russian government “obtained and maintained access to elements of multiple US state or local electoral boards.” While the full extent and impact of these activities is not known and our understanding of these events is evolving, there is little doubt that these efforts represented an assault on the American system of representative democracy. The 2016 Russian probes of the U.S. voting infrastructure also were accompanied by directed social media campaigns spreading disinformation that sought to divide the American electorate and undermine confidence in democratic institutions. As former Central Intelligence Agency and National Security Agency Director Michael Hayden observed that these efforts represented part of a sustained campaign to discredit Western countries and institutions and specifically “Western democratic processes and the American election.” The Russian campaign represents an unsettling development that adds greatly to the technical and operational challenges facing election administrators. The vulnerability of election systems to cyberattacks became a growing concern during the campaign leading up to the 2016 presidential election. That threat caused so much concern that, in the fall of 2016, the federal government took the unusual step of issuing a joint statement from the U.S. Department of Homeland Security (DHS) and the Office of the Director of National Intelligence (ODNI) urging state and local governments to be “vigilant and seek cybersecurity assistance from DHS.” In late December 2016, as the extent of Russian activities became apparent, President Barack Obama invoked sanctions against Russia for its efforts to disrupt the presidential election. In early January 2017, then-DHS Secretary Jeh Johnson observed that, “Given the vital role elections play in this country, it is clear that certain systems and assets of election infrastructure meet the definition of critical infrastructure, in fact and in law.” In early 2017, the nation’s election systems were given critical infrastructure status.
Since the 2000 election, election infrastructure has been a focus of attention due to concerns about aging and insecure voting equipment, inadequate poll worker training, insufficient numbers of voting machines and pollbooks, deficient voter registration information systems, and inadequate verification procedures for votes cast. Long before concerns about Russian interference surfaced, state and local election administrators had been forced to reevaluate and modernize the operation of voting systems in the wake of incidents such as the “hanging chad” debacle in the 2000 presidential election and long lines that occurred in some jurisdictions in the 2004, 2008, and 2012 elections. In advance of the 2016 election, as they had in the past, officials worked aggressively to ensure that the 2016 national election would run smoothly and without disruptions and that election systems—including public election websites, voter registration systems, voting systems, vote tabulation systems, election night reporting systems, and auditing systems—would meet the challenges of a national election.
Today, long-standing concerns about outdated and insecure voting systems and newer developments such as cyberattacks, the designation of election systems as critical infrastructure, and allegations of widespread voter fraud, have combined to focus attention on U.S. election systems and operations. The issues highlighted add urgency to a careful reexamination of the conduct of elections in the United States and demonstrate a need to carefully consider tradeoffs with respect to access and cybersecurity.
_
It has been demonstrated that as voting systems become more complex and include software, different methods of election fraud become possible. Others also challenge the use of electronic voting from a theoretical point of view, arguing that humans are not equipped for verifying operations occurring within an electronic machine and that because people cannot verify these operations, the operations cannot be trusted. Furthermore, some computing experts have argued for the broader notion that people cannot trust any programming they did not author.
Critics of electronic voting, including security analyst Bruce Schneier, note that “computer security experts are unanimous on what to do (some voting experts disagree, but it is the computer security experts who need to be listened to; the problems here are with the computer, not with the fact that the computer is being used in a voting application)… DRE machines must have a voter-verifiable paper audit trails… Software used on DRE machines must be open to public scrutiny” to ensure the accuracy of the voting system. Verifiable ballots are necessary because computers can and do malfunction, and because voting machines can be compromised.
Many insecurities have been found in commercial voting machines, such as using a default administration password. Cases have also been reported of machines making unpredictable, inconsistent errors. Key issues with electronic voting are therefore the openness of a system to public examination from outside experts, the creation of an authenticatable paper record of votes cast and a chain of custody for records. There has been contention, especially in the United States, that electronic voting, especially DRE voting, could facilitate electoral fraud and may not be fully auditable. In addition, electronic voting has been criticised as unnecessary and expensive to introduce. While countries like India continue to use electronic voting, several countries have cancelled e-voting systems or decided against a large-scale rollout, notably the Netherlands, Ireland, Germany and the United Kingdom due to issues in reliability of EVMs.
_____
The question we should try to answer is not “is this product secure”, but it is rather “is there a chance for a secure-enough e-voting system?”
There are two categories of requirements from a voting system to make it considered trustworthy:
- The system shall be robust (“secure”), and
- The system shall be verifiable by the public.
Meeting the first requirement is “just” very hard. Meeting the second requirement is discouragingly challenging even at the conceptual level.
_____
There are many layers between the application software that implements an electoral function and the transistors inside the computers that ultimately carry out computations. These layers include the election application itself (e.g., for voter registration or vote tabulation); the user interface; the application runtime system; the operating system (e.g., Linux or Windows); the system bootloader (e.g., BIOS or UEFI); the microprocessor firmware (e.g., Intel Management Engine); disk drive firmware; system-on—chip firmware; and the microprocessor’s microcode. For this reason, it is difficult to know for certain whether a system has been compromised by malware. One might inspect the application-layer software and confirm that it is present on the system’s hard drive, but any one of the layers listed above, if hacked, may substitute a fraudulent application layer (e.g., vote-counting software) at the time that the application is supposed to run. As a result, there is no technical mechanism that can ensure that every layer in the system is unaltered and thus no technical mechanism that can ensure that a computer application will produce accurate results. This has several important implications for election systems:
- all digital information—such as ballot definitions, voter choice records, vote tallies, or voter registration lists—is subject to malicious alteration;
- there is no technical mechanism currently available that can ensure that a computer application—such as one used to record or count votes—will produce accurate results;
- testing alone cannot ensure that systems have not been compromised; and
- any computer system used for elections—such as a voting machine or e-pollbook—can be rendered inoperable.
Election systems are especially vulnerable when they are connected to the Internet, telephone network, or another wide-area network. Systems that utilize network connections for their functions include voter registration systems, e-pollbooks, and post-election canvassing/reporting systems.
Even when systems are not directly connected to networks, they are vulnerable to attack through physical or wireless access. They also are vulnerable whenever data transferred to them originates from another computer system that is itself vulnerable. For example, to attack a voting machine that receives data only through hand-carried removable media bearing “ballot definition files,” an attacker might create a ballot definition file that takes advantage of a flaw in the software that reads a ballot definition file or displays a ballot. Such an attacker need not be physically present with that removable media—entry through a network-connected computer that creates the removable storage media may suffice (the removable storage media is used to transmit the ballot definition file).
Achieving stronger defenses against cyberattacks involves: (1) adopting state-of-the-art technologies and best practices more widely; and (2) developing new knowledge about cybersecurity. The first defense is primarily nontechnical and involves economic, organizational, and behavioral factors. The second defense requires research to develop new technologies and approaches.
_
Factors that Exacerbate Cybersecurity Concerns:
- A highly decentralized elections system. Because the U.S. elections system is highly decentralized, responsibility for cybersecurity often falls to the county or municipal level where expertise and resources may be quite limited.
- Aging systems. Because U.S. elections frequently make use of hardware and software that are aging—in some cases to the point that they would generally be considered obsolete—cybersecurity risk is increased because (1) such systems may fall well behind the current state of the art in cybersecurity measures; and (2) software or the operating system used to run it may no longer be receiving security updates.
- Changing threat. Traditionally, the goal has been to secure against election fraud by corrupt candidates or their supporters who may attempt to favor a particular candidate by altering or destroying votes or tampering with the vote tally. The 2016 U.S. election vividly illustrated that hostile state actors can also pose a threat. These actors often possess more sophisticated capabilities and can apply greater resources to the conduct of such operations. Moreover, they may have other goals than shifting the outcome for a particular candidate. If their goal is to disrupt an election or undermine confidence in its outcome, they may need only to achieve DoS against e-pollbooks or leave behind traces of interference like malicious software or evidence of tampering with voter registration lists or other records. Even failed attempts at interference could, if detected, cast doubt on the validity of election results absent robust mechanisms to detect and recover from such attacks.
_____
Risks of E-voting:
Electronic voting has spread throughout the U.S. and the world without sufficient attention to reliability, security, or transparency. Today’s e-voting systems use proprietary code, and vendors have often asserted the confidentiality of this code when independent reviews of certified systems were requested. This confidentiality conflicts with the transparency required for public elections. In order to provide an independent assessment of the voting systems certified for use in California, Secretary of State Debra Bowen initiated a top-to-bottom review of those e-voting systems. She asked us to recruit a team of experts and gave us access to all the equipment, source code, and technical information that the Secretary of State’s office had.
The results showed that the systems appeared not to be designed or implemented with security in mind. The design and implementation ignored basic security principles, and they found serious security vulnerabilities in all three vendors’ systems. The security flaws were systemic and surprisingly similar across the three systems.
For example, malicious code could exploit vulnerabilities in the voting software to spread virally from machine to machine. As a result, when the voting machines return results to election central to count the votes, a virus could infect the county’s election management systems. At the next election, the infected election management systems could then infect every voting machine in the county. This virus could be introduced at several points in the process. An attacker could tamper with an e-voting machine while it is stored unattended overnight in a polling place. For some of the systems, a voter could introduce malicious code in under a minute, while voting. Many flaws resulted from elementary mistakes such as straightforward buffer overrun vulnerabilities and flawed cryptography. One piece of voting software appends a three-letter suffix to a password and sends this “encrypted’’ result over the network. Another has encryption keys hard-coded in the source code, meaning the keys are the same for all machines using that software—an obvious security flaw. One of the manufacturers used its own name as a hard-wired password. The public reports had to be written carefully to convey the depth of the problem without providing a “road map” for attackers.
______
Tampering with electronic voting machines:
All voting systems face threats of some form of electoral fraud. The types of threats that affect voting machines vary. Research at Argonne National Laboratories revealed that a single individual with physical access to a machine, such as a Diebold Accuvote TS, can install inexpensive, readily-available electronic components to manipulate its functions.
Other examples include:
-Tampering with the software of a voting machine to add malicious code that alters vote totals or favors a candidate in any way. Multiple groups have demonstrated this possibility.
– Private companies manufacture these machines. Many companies will not allow public access or review of the machines source code, claiming fear of exposing trade secrets.
– Tampering with the hardware of the voting machine to alter vote totals or favor any candidate.
– Some of these machines require a smart card to activate the machine and vote. However, a fraudulent smart card could attempt to gain access to voting multiple times or be pre-loaded with negative votes to favor one candidate over another, as has been demonstrated.
– Abusing the administrative access to the machine by election officials might also allow individuals to vote multiple times.
– Election results that are sent directly over the internet from a county count center to the state count center can be vulnerable to a man-in-the-middle attack, where they are diverted to an intermediate website where the man in the middle flips the votes in favour of a certain candidate and then immediately forwards them on to the state count center. All votes sent over the internet violate the chain of custody and hence should be avoided by driving or flying memory cards in locked metal containers from county count centers to the state count center. For purposes of getting quick preliminary statewide results on election night, encrypted votes can be sent over the internet, but final official results should be tabulated the next day only after the actual memory cards arrive in secure metal containers and are counted.
______
Chain of custody:
Chain of custody is about establishing who has had their hands on some important piece of physical evidence that must not be tampered with. This could be evidence in a court case, or it could be evidence of voter intent, i.e. a marked ballot. If you can’t firmly establish that only authorized, trusted parties have handled a ballot from the moment that it left the voter’s hands and entered the lock-box, then you can’t be certain that nobody tampered with that ballot to change its vote. If at any point ballots are left either unattended or unsecured, then it’s possible that someone could have tampered with them. The mere existence of that possibility precludes the establishment of a certain chain-of-custody—the two are mutually exclusive. If the state can’t demonstrate a secure chain of custody for the ballots in an election, then the public can’t have the level of confidence in the integrity of that election that it deserves to be able to have.
In the context of an election, a strong chain of custody means safeguarding the ballots, as well as the election-related software and hardware used. The public should be confident that the ballots and election machines are secure from the moment of their creation until the tally is finalized at the Board of Elections. Machines must be kept under literal lock and key, given that computer scientists have demonstrated that they can install a new chip into a voting machine, and alter its software, in about a minute. When software is first installed, a “hash” can be applied —essentially, a digital fingerprint that changes if the software has been altered. This is just one example of many protections that security experts with technical expertise can implement.
______
______
CIA Security Triangle in Electronic Voting System:
What is the CIA triad? No, CIA in this case is not referring to the Central Intelligence Agency. CIA refers to Confidentiality, Integrity and Availability. Confidentiality of information, integrity of information and availability of information. Many security measures are designed to protect one or more facets of the CIA triad.
_
Confidentiality, Integrity, and Availability are three sides of the famous CIA security triangle as shown in the figure below:
_
Confidentiality:
When we talk about confidentiality of information, we are talking about protecting the information from disclosure to unauthorized parties. Information has value, especially in today’s world. Bank account statements, personal information, credit card numbers, trade secrets, government documents. Everyone has information they wish to keep a secret. Protecting such information is a very major part of information security. Protection of confidentiality against illegitimate users and attackers is vital factor for e-voting systems as they store voters’ authentication information, casted votes, passwords, and encryption/decryption keys inside and also may transmit them online. Two of e-voting systems critical confidentiality approaches are preserving ballot secrecy and banning voters’ coercion. A very key component of protecting information confidentiality would be encryption. Encryption ensures that only the right people (people who knows the key) can read the information. Encryption is very widespread in today’s environment and can be found in almost every major protocol in use. A very prominent example will be SSL/TLS, a security protocol for communications over the internet that has been used in conjunction with a large number of internet protocols to ensure security. Other ways to ensure information confidentiality include enforcing file permissions and access control list to restrict access to sensitive information. Access control also helps to grant access only to legitimate users.
Integrity:
Integrity of information refers to protecting information from being modified by unauthorized parties. Information only has value if it is correct. Information that has been tampered with could prove costly. For example, if you were sending an online money transfer for $1000, but the information was tampered in such a way that you actually sent $10,000, it could prove to be very costly for you. Integrity falls into two categories of data and software integrity. Data integrity is preserving integrity of ballot information and audit records. Software integrity is ensuring that only genuine software is running on the system components. As with data confidentiality, cryptography plays a very major role in ensuring data integrity. Most important method to protect integrity is utilizing cryptographic techniques like SSL, TSL, MAC, or digital signature. Commonly used methods to protect data integrity includes hashing the data you receive and comparing it with the hash of the original message. However, this means that the hash of the original data must be provided to you in a secure fashion. More convenient methods would be to use existing schemes such as GPG to digitally sign the data.
Availability:
Availability of information refers to ensuring that authorized parties are able to access the information when needed. Information only has value if the right people can access it at the right times. Denying access to information has become a very common attack nowadays. Almost every week you can find news about high profile websites being taken down by DDoS attacks. The primary aim of DDoS attacks is to deny users of the website access to the resources of the website. Such downtime can be very costly. Other factors that could lead to lack of availability to important information may include accidents such as power outages or natural disasters such as floods. Proportion of time that e-voting system must be partially or fully functional is called availability. Due to problems like overloading resources, malfunctions, or attacks the systems might become unavailable. How does one ensure data availability? Backup is key. Regularly doing off-site backups can limit the damage caused by damage to hard drives or natural disasters. For information services that is highly critical, redundancy might be appropriate. Having a off-site location ready to restore services in case anything happens to your primary data centers will heavily reduce the downtime in case of anything happens. Most important factors for preserving system availability are capability of failure resiliency and DoS attack counter measures.
There is no comprehensive solution against denial of service attacks but following points will help to detect, prevent, and recover from attacks.
Redundancy and over-provisioning: duplication of resources to be used at attack time is called redundancy, and over-provisioning is devoting higher capacity severs and infrastructure to keep system functionality if DoS attack happens.
Availability active attack detection: process of availability detection is easy and voters will lose their access if DoS attack happens. Best protection is early detection and fast reaction.
Active attack defense: the most common DoS defense is over-provisioning and second choice is filtering sent attack packets.
_
The above paragraph shows that CIA triad is a very fundamental concept in security of e-voting system. Often, ensuring that the three facets of the CIA triad is protected is an important step in designing any secure system. Other factors besides the three facets of the CIA triad are also very important in certain scenarios, such as non-repudiation and authentication.
_
Authentication:
Authentication is a security service, designed to establish the validity of transmission, message, or originator, or a means of verifying and individuals authorisations to receive certain categories of information (Maconachy, et al, 2001) In the context of voting, authentication provides the means in which to identify an eligible a voter. This would conventionally be a polling card and a form of ID card that would verify the eligible voter. Any voting systems incorporating ICT should be capable of identifying eligible voters and distinguishing between non-voters. Such a system might use a social security number or passport number as means of identification. To enhance the authentication processes the voting public may receive a polling card days before election with number, this number corresponds with the social security number or passport number. This number generated by using a hash function algorithm (Kurose 2004 p-615).
Non-repudiation:
Non-repudiation provides, the assurance the sender of the data provided with proof of delivery and the recipient is provided with proof of the sender s identity, so that neither can deny having processed the data (Maconachy, et al, 2001). In the context of voting, non-repudiation will mean that there is evidence of a voting transaction; this can be a polling slip as form of evidence. An electronic voting system using ICT, would have to use digital signatures to achieve the same goals of non-repudiation that a polling slip could offer. Generating digital signatures would involve the use public and private key cryptography with checksum algorithms (Kurose 2004 p-610).
_
Voter Trust Model:
Figure above illustrates the five areas of security discussed in above paragraphs, three CIA plus authentication and non-repudiation. Together these five areas of security combine to provide a barrier of trust surrounding the voter. If any area of security in figure above is compromised, it will lead to lack of trust on the voter’s behalf. This model helps identify the security requirements for an electronic voting system that will ultimately lead to full trustworthy voting system.
____
____
Security vulnerability of DRE voting machine:
There are a great number of concerns regarding the DREs such as:
– Voters have no way to verify that their votes were recorded correctly.
– There is no way to publicly count the votes.
– Meaningful recounts are impossible.
– Certification process does not work, as we see on the example of Diebold.
– Other vendors do not expose their machines for public scrutiny.
– DREs are vulnerable to undetectable rigging.
_
The 2000 presidential election and the consequential actions of Congress and the states are dramatically changing the American election process. The Help America Vote Act (HAVA) passed by Congress in 2002 mandates reform of the election processes of all states. HAVA provides funding to replace obsolete voting technologies such as punch cards and lever machines with more modern technologies such as precinct based optical scanners and direct recording electronic (DRE) voting machines. While HAVA includes a requirement that all voting systems must provide a manual audit capacity, its definition of that requirement is ambiguous, and there are conflicting interpretations of its meaning. Many elections officials have concluded that HAVA does not require a paper record of each ballot, verified by the voter at the time the ballot is cast. As a result, over 100,000 paperless DRE voting machines have already been deployed which lack the ability to produce a voter-verified paper ballot.
There are three major objections to entrusting American elections to these machines:
- Software errors are unavoidable
- Without a voter-verified paper ballot it is impossible to perform meaningful recounts
- The opportunities for fraud exist on a greater scale than ever before
- Software Errors:
No one knows how to write bug-free software. This fact is not in dispute. The more complex the software, the more difficult it is to find and fix bugs. Election software is very complex because of the wide variety of ballot types used across the nation, and it will contain errors, regardless of the skill and dedication of the engineers who design it and the programmers who code it. Computer glitches are not uncommon. All of us who use computers know this. Undoubtedly, software errors will cause problems in future elections, just as they have in past elections. Here are three of the many examples of computer errors reported in newspapers in recent elections:
- Cateret County, North Carolina, November 2004: software problems caused 4,438 electronic ballots to be lost and never recovered. The vendor acknowledged responsibility for the loss.
- Fairfax County, Virginia, November 2003: testing ordered by a judge revealed the several voting machines subtracted one in every hundred votes for the candidate who lost her seat on the school board.
- Broward County, Florida, January 2004: 134 electronic ballots were blank in a one-race election held on DRE voting machines in which the margin of victory was 12 votes. Florida law required a manual recount of the ballots, but that recount was impossible because there were no physical ballots to recount.
These and many other reports of computer problems present us with an obvious question: how many election results were compromised by unnoticed computer errors and malfunctions? Of course, we have no way of knowing. These reported cases were detected, but it is only reasonable to assume that were other undetected errors, and we will never know how many.
- Impossibility of Meaningful Recounts:
Trusting our votes to a wholly electronic process of recording and storage leaves us completely without recourse if that electronic process fails – and history shows that the process fails all too frequently. DRE voting machines do allow voters to inspect and correct their choices on the touch screen’s final summary display prior to casting their vote. But, DREs do not provide voters any method for inspecting how their vote is stored inside the DRE’s electronic memory. Thus, the electronic ballot records stored in those memory circuits are completely invisible to and unverified by the voter; they are also alterable. Yet it is the contents of that invisible, impermanent, and unverified computer memory that are used to total up the votes. Without voter-verified paper records that accurately reflect the voters’ choices, it is simply impossible to perform a meaningful recount. While most DRE voting machines can print a paper record of the votes cast, this report is not generated until after the polls have closed, and is nothing more than a printout of the electronic records. If the electronic record is inaccurate, then the printed report will also be inaccurate. Such a printout is not voter verified and does not provide an audit trail appropriate for a meaningful recount.
Consider this scenario, not unlike events that have occurred in past elections: A voter marks the appropriate locations on the voting machine’s touch screen, reviews the choices, and gives the command to cast the ballot. Due to a software problem or malfunction, the computer records the ballot incorrectly, or not at all. The voter leaves the booth, and at the end of the day, the poll worker prints out the ballot images. The voter’s votes are incorrectly tallied and the printed ballot image is incorrect, but this error goes undetected because the voter is not there to view the printed version. But because the printed version of the ballot images all match the electronic records (as they must, since one is simply a copy of the other), elections officials proudly report that they have successfully conducted yet another flawless election.
- Opportunities for Grand-Scale Fraud:
Election fraud is not unknown in previous American elections, and it is not unexpected in future elections. However, the opportunities for fraud provided by electronic voting machines surpass all the opportunities available previously. For example, a corrupt insider, working for one of the vendors of widely-used voting machines, could hide malicious code in the software. That vendor could then unwittingly distribute that malicious code to thousands of machines across the nation and alter the election results in every state where those machines are used. Existing testing and certification procedures for DREs are voluntary and currently insufficient to guarantee that this type of tampering will be detected. Elections officials are usually not computer security experts and most do not fully appreciate the security vulnerabilities of DRE voting machines.
Concerns about fraud are not simply speculation. A 2003 study by Johns Hopkins and Rice University computer experts revealed hundreds of security flaws in the software of a leading manufacturer. Two separate studies commissioned by Maryland (the SAIC and RABA reports) confirmed many of those findings and identified additional vulnerabilities. An Ohio study of the four major voting machines has shown them all to have serious security vulnerabilities. That study prompted the Ohio Secretary of State to delay the installation of DRE voting machines in that state until after the 2004 election.
_
In July 2003, computer scientists from Johns Hopkins and Rice Universities released a security analysis of software purportedly from a direct recording electronic (DRE) touchscreen voting machine of a major voting-system vendor. The study drew public attention to a long-simmering controversy about whether current DREs are vulnerable to tampering that could influence the outcome of an election.
This security concern appears to stem largely from three factors:
- Malicious computer code, or malware, can often be written in such a way that it is very difficult to detect.
- DRE software is moderately complex, and it is generally accepted that the more complex a piece of software is, the more difficult it can be to detect unauthorized modifications.
- Most manufacturers of DREs treat their software code as proprietary information and therefore not available for public scrutiny. Consequently, it is not possible for experts not associated with the companies to determine how vulnerable the code is to tampering.
With DREs, unlike document-ballot systems, the voter sees only a representation of the ballot; votes are registered electronically. Some computer security experts believe that this and other features of DREs make them more vulnerable to tampering than other kinds of voting systems, especially through the use of malicious computer code. While there are some differences of opinion among experts about the extent and seriousness of those security concerns, there appears to be an emerging consensus that in general, current DREs do not adhere sufficiently to currently accepted security principles for computer systems, especially given the central importance of voting systems to the functioning of democratic government. Others caution, however, that there are no demonstrated cases of computer tampering in public elections, and any major changes that might be made to improve security could have unanticipated negative effects of their own. Several proposals have been made to improve the security of DREs and other computer-assisted voting systems. They include (1) ensuring that accepted security protocols are followed appropriately, (2) improving security standards and certification of voting systems, (3) use of opensource computer code, and (4) improvements in verifiability and transparency.
Much of the current debate has focused on which such proposals should be implemented and through what means — in particular, whether federal involvement is necessary.
_
How each voter votes is a private matter. But how those votes are counted is everyone’s business. When voters cast their ballots, they must be able to verify that their choices have been accurately and permanently recorded on that ballot. They must also be ensured that their ballots cannot be altered or deleted after they have verified them, and that their voter-verified paper ballots are available for a meaningful recount, including manual recounts where required by law. Accordingly, a reasonable solution to the problem with electronic voting is to pass legislation requiring all DRE voting machines to provide a voter-verified paper ballot that is saved in a ballot box for use in recounts and audits.
______
The Diebold E-Voting System-security flaws:
During an analysis of the source code of the Diebold e-voting system, based on Version 4.3.1, several security flaws were unveiled in the code, that allow several different parties means to launch an attack against the Diebold system and its integrity while in use.
- Impersonation
Using a copy of Diebold under control of a malicious user, with an inside worker at the polling station could access the PPP dial-up information, which is stored in plaintext in the registry of each client machine. Using the phone number, username and password details obtained, and the voting terminal ID either of the compromised machine or from another source, could log into the central server to submit incorrect voting tallies, and at least temporarily upsetting the voting process
- Denial of Service
Due to the centralized design of the Diebold system, a central single point of failure is present, meaning that if the main server (and any backup servers) are brought down with a traditional denial-of-service attack, then the start of an election could at least be delayed if terminals are unable to download their ballot definition files.
- Tampering
Due to the lack of security on the configuration of the polling machines themselves, i.e. the definition file is stored as plaintext ASCII, unencrypted and without any form of checksum or tamper logging, voting machines can be surreptitiously altered by anybody with physical access to the machine, or network access to the drive it is stored on. Also, if the file is transmitted over a network to the voting terminal, the design is subject to a man-in-the-middle attack, who could receive the correct definition file, and pass on an altered one to the voting terminals.
Also, because Diebold is supported by the Windows operating system, anybody with network permissions to the drive on the network, or exploiting a security hole in the operating system, could also alter this file. This gives another point of compromise for attackers, rather than just relying on the security of the software itself, we must rely on the security of the Operating System.
- Tracking Voters
Diebold fails to ensure anonymity of voters, by recording votes in its database in the order that they were cast. Anybody who is able to access the list of votes would be able to watch voters and record the order that they entered the polling booth, hence be able to associate each voter with their respective vote after the election has closed.
- “Encryption” and Key Management
Diebold uses single DES, which is insubstantial and easy to break by brute force. Although this could easily be solved by upgrading the encryption, the more worrying aspect is that the source code shows the key management consists of a single, statically-coded key. This means anybody with access to the source can unencrypt any information encrypted by the Diebold system. From the CVS logs, it also shows this key has been in use since the original versions of Diebold, to the current (as of 2002) AccuVote-TS 4.3.1 system. #define DESKEY ((des_key*)”F2654hD4″)
- Unsafe Coding
C++ is an “unsafe” language, as it is vulnerable to buffer overflows, unlike languages such as Java. Because the Diebold system has been coded in C++, although the developers show thoughtfulness towards the prevention of buffer overflows, it is extremely difficult to prove the code is without issues in such a language. The system also makes use of a 3rd-party add-on for audio, called ‘fmod’. This means trust is placed in outside developers who would now be able to add possibly malicious code to the Diebold system while bypassing any internal code audit process.
- Coding Process
Because each programmer has authority to commit code to any part of the Diebold system, it is possible for any one of them to introduce malicious code into the system.
- Gems Database
All voting information taken in by the Diebold system is recorded in the GEMS database. This database is stored in Microsoft Access format, and is not password protected from external access (though contains password-protection within the program itself, this password is stored in the database).
The system uses a well-documented default password of “gemsuser”, and if the password has been changed, a malicious user can easily copy the encrypted password from another install and override the password in the victim install using Microsoft Access. Also, the “tamper” log in the system only monitors activity generated from the Diebold software, so such vulnerabilities such as changing the password via Access remain undetectable with the current design.
______
______
Hacking:
There’s more than one way to hack an election:
Here are the systems at risk in the election process:
-Voter registration systems
-Voter registration databases (which the voter registration process produces)
-Voter records at polling places (known as poll books, which exist in both printed and electronic versions)
-Voting machines (which capture the votes)
-Vote tabulation (when the votes are tallied)
_
Hacking of American electronic voting system:
Although election officials often claim American computerized election system is too “decentralized” to allow an outcome-altering cyber-attack, it is, in fact, centralized in one very important way: just two vendors, Elections Systems & Software, LLC, and Dominion Voting, account for about 80 percent of US election equipment. A third company, Hart Intercivic accounts for another 11 percent. The enormous reach of these three vendors creates an obvious vulnerability and potential target for a corrupt insider or outside hacker intent on wreaking havoc.
These vendors supply three main types of equipment that voters use at the polls: optical or digital scanners for counting hand-marked paper ballots, direct record electronic (usually touchscreen) voting machines, and ballot-marking devices that generate computer-marked paper ballots or “summary cards” to be counted on scanners.
Contrary to popular belief, all such equipment can be hacked via the Internet because all such equipment must receive programming before each election from memory cards or USB sticks prepared on the county’s election management system, which connects to the Internet. Thus, if an election management system is infected with malware, the malware can spread from that system to the memory cards and USB sticks, which then would transfer it to all voting machines, scanners, and ballot-marking devices in the county.
Malicious actors could also attack election management systems via the remote access software that some vendors have installed in these systems. The memory cards or USB sticks used to transfer the pre-election programming from the election management system to the voting machines, scanners, and ballot-marking devices constitute another potential attack vector. In theory, the person who distributes those cards or USB sticks to the precincts could swap them out for cards containing a vote-flipping program. Memory cards are also used in the reverse direction—to transfer precinct tallies from the voting machines and scanners to the election management system’s central tabulator, which aggregates those tallies. Problems can occur during this process, too.
Further complicating matters, some jurisdictions transfer results from the precincts to the central tabulators via cellular modems. ES&S has recently installed such cellular modems in Wisconsin, Florida, and Rhode Island. Michigan and Illinois transfer results via cellular modem as well. According to Computer Science Professor Andrew Appel of Princeton University, these cellular modems could enable a malicious actor to intercept and “alter vote totals as they are uploaded” by setting up a nearby cell phone tower (similar to the Stingray system used by many police departments). After precinct tallies are sent by memory card or modem to the central tabulators, a memory card or flash drive transfers the aggregated totals from the central tabulators to online reporting systems, creating another hacking opportunity. Central scanners, which are used to count absentee ballots and paper ballots from polling places that lack precinct-based scanners, are also vulnerable. As troubling, voting machines themselves can be compromised within seven minutes of direct access, with little more than a screwdriver and a new ROM chip.
Vote flipping aside, malicious or benign actors can also cause electronic failure that prevents the machines from working at all. The potential impact of electronic failure is far greater with touchscreen systems, whether for voting machines or ballot-marking devices, than with hand-marked paper ballots counted on scanners because, when touchscreens fail, voters may have no means of voting whatsoever.
_
Election hacking raises visions of a hooded figure on a laptop remotely tapping into a voter machine to artificially boost tallies. But in truth, most remote attacks on individual machines are tricky because many devices aren’t directly linked to an internet connection. However, in-person manipulation is possible. Some machines are vulnerable, due to accessible ports where a hacker could plug a laptop or smartphone to add fake votes. The Sequoia AVC Edge machines feature a yellow “Activate” button on the back that can allow user to enter multiple ballots at a time. Nevada has employed these systems statewide, while Louisiana did the same with early voting without backup paper records. It’s the technical equivalent to stuffing a voter box. You can tap that as many times, for as many votes as you want to give the person. To exploit the tactics, a perpetrator would need access to a voter machine for an extended period of time, which is possible given background checks for election officials and poll workers aren’t a national requirement.
Another target is the facility or database where votes are counted. You have to look at attacks at the intermediate stages, where there are computers tabulating results from around a state or a county. Some counties use devices that collect and calculate results at once, such as the AccuVote TS and TSX voting machines. But the software for these popular machines lack basic cybersecurity, like encryption or strong passwords.
Harri Hursti, a Finnish computer programmer, famously exposed this vulnerability among voting machines in Leon County, Florida, as part of a series of studies on digital election infrastructure. He showed the “Hursti Hack” — tampering with the machine’s memory cards in person or over a remote internet connection — could add or subtract hundreds of votes for a candidate. Some experts believe this tactic may have been partially responsible for the voting irregularities witnessed in Florida during the 2000 election.
Security experts have focused their worries mainly on other possible threats — such as hacking of voter-registration databases, which could wreak havoc on checking in voters and cause longer lines at the polls — but experts also voice concerns that results could be vulnerable nonetheless, if gaps in the system go unanticipated. The biggest cyber breaches to influence recent events may have occurred months ago and involved voter registration data. Over the summer, cyber assailants launched separate attacks on the voter registration databases in Arizona and Illinois. The Arizona breach compromised the personal information of 3 million voters, though investigator did not find evidence that the hackers removed the data. However, perpetrators in Illinois did escape with the names, addresses and contact details for 200,000 voters in Illinois. The FBI’s Cyber Division issued an alert stating foreign hackers had infiltrated state election systems, though their bulletin did not specifically mention the incidents in Arizona and Illinois.
Luckily, ballot stuffing is improbable, even with electronic voting because “every jurisdiction conducts reconciliation procedures to ensure that the number of voters who signed in to vote squares with the number of votes tallied.” This safeguard means the election will ultimately hinge on counted votes. So, hacks that switch or delete selections at polling stations without paper records represent the most insidious manipulation, because those votes would be lost.
At 2018 year’s DEFCON hacker conference, where hackers test their skills on out-of-use voting machines brought in by conference organizers, hackers succeeded in cracking — to various extents — several models currently in use. One hacker, already familiar with the machine, gained full administrative-level access to a Premier (formerly Diebold) AccuVote TSX in about 30 seconds.
______
Can Russia hack American elections?
The history of what appears to be Russian government abuse of the Internet traces back to a cyberattack on Estonia in April 2007 and an attack during the Russio-Georgian war in August 2008. There was a degree of plausible deniability in the Estonian case, but the close coordination of the Russian cyberattack against Georgia with military action makes Russian denials ring hollow.
How vulnerable are American elections?
Compared to a decade ago, the fraction of votes counted on paperless machines had declined, but they are still in use statewide in Georgia, South Carolina and Louisiana, and in widespread use in Pennsylvania, Texas and a handful of other states. Laboratory experiments show that many of these machines can be hacked, it is not rocket science.
Can Russians hack these electronic voting machines in America?
Very difficult. Why?
- First, there are over 5000 local election jurisdictions in the United States, mostly county election offices. In many cases, each election jurisdiction makes its own purchasing decision. Even when they buy from the same vendor, they run things differently.
- Second, voting machines in the precinct are not connected to the Internet while the polls are open. Where attacks from the Internet may be possible, they are indirect — you have to attack the county election office computers first, then install complex attack software there to actually attack the machines, and you must do this month ahead of the election.
- Third, the oldest paperless DRE machines cannot be attacked even if you infiltrate the county’s computers because they don’t use flash memory. Software changes on those early machines require physical access to pull and replace chips. You can’t do that from St. Petersburg or Moscow.
Suppose a crook wanted to hack the election by actually hacking DRE machines. First, they would have to find jurisdictions in a swing state that had vulnerable systems, then develop an attack on the election office computers in that jurisdiction, and finally use that attack to install the attack software, all without being detected. That’s a lot of work. There’s no point in attacking anywhere but a swing state, because if you attack states with a wide margin and change enough votes to change the outcome, someone will notice.
_
The recent allegations that Russia interfered with the U.S. elections has led countries to assume that hacking emails is the same as hacking an electronic voting platform. This is false —the U.S. voting system wasn’t hacked. The accusations that someone hacked the email accounts of senior Democrats to release embarrassing ones to help sway the U.S. election has made the rest of the world assess the threat of cyber-attacks on democracy. When election technology is properly designed, cyber-attacks, such as the ones allegedly perpetrated by the Russians against the U.S. Democratic Party’s email servers, are not a significant risk. Modern, automated voting platforms have a series of highly secure countermeasures in place to prevent being hacked that email services and other web-based applications don’t have.
Firstly, voting machines (unlike emails) are only online for one to two minutes at a time to transmit data, making it much harder, if not impossible, for hackers to break into them.
Secondly, votes are transmitted over secure private channels not accessible to the public, with secured authentication of both senders and receivers. Votes are digitally signed and asymmetrically encrypted with algorithms. In other words, modern, automated voting platforms have a series of highly secure countermeasures in place, which emails and databases don’t have.
Even the U.S. elections, today under so much scrutiny, serve to demonstrate how reliable election technology is. Despite using technology that was at least 10 years old, no significant incidents occurred in the 2016 elections. The machines used to vote and count the votes worked properly, and recounts only served to prove it. To this day, no one has provided any credible evidence proving the results were altered.
______
Barcode receipts:
Cybersecurity experts are critical of those who want to switch to a new kind of electronic voting machine that prints a barcode receipt. Experts say those machines can still be hacked and the printed barcodes are useless because humans can’t read barcodes. The idea behind barcodes is it allows the vendor to charge for technology to read the barcodes and it adds no actual value to the voting process. What you’re being asked to do is to verify that the ballot is being counted is being cast, but you have to be able to read the ballot to do that. We can’t read barcodes, we can’t read QR codes. It becomes an unusable receipt.
_____
Integrity of Electronic Voting Systems and Use of Cryptography:
In recent years, electronic voting systems have been deployed in all U.S. elections. Despite the fact that cryptographic integrity checks are used in most such systems, several reports have documented serious security vulnerabilities of electronic voting terminals. The security analysis of the AccuVote TSx voting terminal — used by more than 12 million voters in over 350 jurisdictions in the U.S. — demonstrates certain new integrity vulnerabilities that are present in the system. Two attacks were demonstrated based on these vulnerabilities: one attack swaps the votes of two candidates and another erases the name of one candidate from the slate. These attacks do not require modification of the operating system of the voting terminal (as was the case in a number of previous attacks) and are able to circumvent the cryptographic integrity checks implemented in the terminal. The attacks can be launched in a matter of minutes and require only a computer with the capability to mount a PCMCIA card file system (a default capability in most current operating systems). The attacks were discovered through direct experimentation with the voting terminal and without access to any internal documentation or the source code from the manufacturer.
An electronic voting system is a complex distributed system comprised of several types of devices, including (i) election management systems, (ii) electronic voting terminals, such as optical scan terminals, direct entry electronic terminals, and/or enhanced-access terminals for people with disabilities, (iii) voter-assist terminals, such as ballot marking devices, (iv) removable memory devices, such as memory cards, universal serial bus drives, compact flash drives, etc., (v) means of communication, including removable media, telephone and data networks.
Electronic voting terminals are complex computing devices that include sophisticated hardware and software. The behavior of any given voting terminal depends on the software/firmware pre-installed on the terminal, software/firmware installed as an upgrade, and software and data installed for the purposes of an election via removable media. Any such installation, including the installation of election-specific software and data via removable media, can completely change the behavior of the terminal. In particular, incorrect, incomplete, or even arbitrary precinct election results can be reported by a terminal due to errors or malicious interference.
Removable memory devices serve to deliver election configuration to electronic voting terminals and to convey the results to central tabulation. Such devices have proved to be a major source of vulnerabilities in electronic voting systems. The cards connect the election management system and the voting terminals into a large distributed system. Inadequate security measures (electromechanical, software, cryptographic, and physical custody) can allow errors, introduced inadvertently or as the result of deliberate tampering, to propagate through the entire system. Such errors can create broad tampering risks and lead, in extreme cases, to massive failures. Every component of such distributed electronic system is susceptible to attacks, both external attacks and insider attacks.
Although vendors improved their use of cryptography, the mere application of cryptographic mechanisms such as (i) hash checking for software integrity, (ii) encryption for confidentiality of election related data, and (iii) digital signatures for integrity of election data, does not guarantee in itself that the desired properties are achieved. Use of good tools must go hand-in-hand with good use of tools. In particular, severe security deficiencies have been reported in electronic voting terminals despite the use of cryptography. In this way, superficial uses of cryptography can lead to a false sense of security. Worse, cryptography can prevent meaningful independent technological audits of voting equipment when encryption obfuscates the auditable data. A vendor may provide its own test and audit tools, but relying on the self-test and selfaudit features is problematic as one should never trust self-auditing software (cf. relying on a corporate entity to perform self-audit).
______
______
Security of the Internet Voting System:
As technology continues to permeate every facet of life, individuals are continuously faced with decisions that test the balance between convenience and privacy. Voter privacy is of utmost concern when considering the voting systems that are used; especially where we utilize secret ballots. The benefit of the secret ballot is that it ensures that there is no undue pressure once the voter is voting and that there can be no retaliation against the voter for the vote they cast. As a fundamental principle, it is essential to ensure that no one can link the actual vote that is cast to the voter, but in practice this causes unique concerns that require addressing to implement an internet voting system.
Still a new technology, internet voting, and its functional implementation faces substantial barriers. Denial of service, advanced persistent threats, malware, insider attacks, compromised credentials, all of these threats faced by voting systems are not unique, they are threats encountered in all information systems. What is unique is that while many companies assume a certain amount of loss from fraud as part of doing business on-line, for voting systems, this is not an acceptable assumption. Vulnerabilities exposed in electronic systems can compromise democracy and wield considerable political power. Therefore, these threats need to be adequately addressed while still maintaining the privacy of the voter to ensure the confidentiality, integrity, and availability of the voting system.
The risks to internet voting include all of the dangers typically associated with on-line transactions. For those planning on voting by internet, a denial-of-service attack could be the difference between the opportunity to vote or not voting in the election. Likewise, a successful shell-injection attack, insider attack, client-side injection, improper session handling, poor authentication and authorization, etc. leaves internet voting vulnerable to a loss of confidentiality or the essence of the secret ballot. These attacks could also lead to a loss of integrity with votes being changed or additional votes being added; for instance, false votes cast for individuals who registered themselves, but did not actually login to vote.
There are, of course, ways to mitigate these risks, but no system will be without vulnerabilities and thus there is an inherent risk to moving towards internet voting. Internet voting, though, is not a thing of the future as there are several countries and U.S. states that have begun to adopt internet voting.
The concern for voter privacy is still a challenge, even for secure systems. That’s because most audit techniques involve going through logs and determining who performed which tasks. In the case of voting, that would mean keeping detailed logs that include who specifically voted for which candidates. While this is ideal for a more secure application, it is far from ideal when considered against the need to have a secret ballot. Therefore, along with securing the system, it must also be designed to allow for anonymous votes.
Fortunately, there are already proposed solutions to this problem. One solution is that once the server receives a vote, it stores it securely until the time when all votes are counted and it stores sequentially in the order that they are cast. Whenever a vote is cast by the voter, the vote is encrypted with the public key of the electoral committee. Similarly, the votes can be decrypted with the corresponding private key. So long as the votes are not decrypted prior to shuffling them, the privacy of the voters would be maintained.
By following the best practices and designing systems that meet minimum baseline requirements that have already been established and proven to be effective, the security of on-line voting can be maintained. Internet voting may very well prove to be the future of democracy, but it is not there yet. Internet voting solutions must be subject to public scrutiny and address the inherent security issues that threaten voter privacy and the integrity of the voting system if it will ever stand a chance at success.
_____
_____
End-to-end-verifiability:
In recent years there has been increased interest in providing voters with an opportunity to verify that their votes have been accurately cast, counted, and tabulated. This presents a challenge due to the necessity of preserving the secrecy of the ballot. However, building upon cryptographic methods initially developed by computer scientist and cryptographer David Lee Chaum, researchers have developed an approach called end-to-end (E2E) verifiability. This approach enables voters and other members of the public to audit the integrity of an election without relying on hardware, software, or personnel associated with elections.
An election is E2E-verifiable (E2E-V) if it achieves three goals: 1) voters can obtain assurance that their selections have been properly recorded; 2) any individual can verify that his or her ballots have been included in vote tallies; and 3) members of the public can verify that the final tally is the correct result for the set of ballots collected. E2E-verifiability enables not only detection of external threats, but also detection of internal threats including errors or tampering by election officials, corrupted equipment, or compromises originating with equipment vendors.
E2E-V voting systems adopt certain properties, encrypt ballot data, and permit verification of data throughout the voting process. In an election context, “end-to-end” refers to the flow of ballot data through the entirety of the voting process and to the idea that the data may be verified at multiple stages in the voting process. The phrase should not, however, be interpreted to mean that verification must occur at particular stages of the process. E2E-verifiability is a property that may be achieved in an election—rather than a particular methodology. Systems with various characteristics have been designed to produce E2E-V elections.
In practice, an E2E-V voting system might work as follows:
Upon marking a ballot, the voter would obtain a receipt which is a “cryptographically-masked” copy of the voter’s selections (the voter’s choices would thus not be visible in a way that would enable vote-selling or coercion). The receipt could be machine-issued or derived from the process of marking a pre-printed paper ballot.
There are several methods to test whether the encryption process is working properly. In one scenario, voters might be allowed to “spoil” one or more ballots after receipts have been produced. Voters could subsequently verify that receipts issued for spoiled ballots accurately reflect selections made. Because voting systems cannot predict whether a voter will spoil a ballot, a voting system must correctly encrypt all receipts, as only a small fraction of voters would need to verify that spoiled ballots have been properly encrypted to reveal systematic erroneous behavior by a voting system. After polls close, copies of all voter receipts would be posted to a public electronic bulletin board in order to allow voters to confirm that their votes have been properly recorded. If the voter’s unique receipt was not posted, the voter could file a protest and use the receipt as evidence for correcting the posting error.
All voter receipts would be processed using a series of cryptographic computations that would yield the results of the particular election. The algorithms and parameters for the cryptographic operations would be posted on a website to enable voters to verify that their votes were tallied as recorded and to allow other observers to verify that the tally is correct. When E2E-verifiability is used with paper ballots, conventional recounts and risk-limiting audits are possible as additional means of verification.
E2E-verifiablility adds complexity to the election process, and the effective wide-scale deployment of E2E-verifiability will require a broad understanding of the underlying cryptographic methods by election officials and the general public. It may initially be challenging to understand the tools that could be employed to make E2E-verifiability possible. Further, with E2E-V systems, it is possible that the encryption of voter receipts could be compromised. While such decryption would not affect the integrity of an election, it could compromise voter anonymity.
E2E-V methods seem to be necessary for secure voting via the Internet, but the methods are, in and of themselves, insufficient to address all of the security issues associated with Internet voting. Electronic versions of ballots may be subject to Internet-based (or other) attacks that might, for example, delete electronic ballots or otherwise replace or modify electronic election records. With E2E-V systems—as with any voting system—a bad actor could simply claim that his or her vote was not accurately captured. Such claims could eventually be discounted by security experts following the E2E-V trail of evidence. However, with sufficient numbers of bad actors acting simultaneously, confidence in an election outcome could be eroded before all the necessary independent verifications could take place.
_
End-to-end-verifiable (E2E-V) voting systems share the following security properties:
-Integrity. Once a voter successfully enters his or her ballot into an E2E-V system, it cannot be undetectably lost or modified in any way, even in the presence of computer bugs or malicious logic.
-Counting Accuracy. Ballots cannot be miscounted without the miscount being detectable.
-Public Verifiability. E2E-V systems provide outputs and publish sufficient verification data to permit any voter to verify that his or her ballot was not lost or modified and that votes were properly tabulated. Verification data provides cryptographic proof that ballot integrity was preserved and tabulation was correct. Anyone may run a verification program on the verification data to confirm the accuracy of the data.
-Transparency. Mathematical principles underlying the E2E-V security guarantees are open and public. The specifications for verification programs are publicly documented, and voters and observers are free to create and execute their own verification programs.
_
The emerging approach to voting systems is verifiability (US Vote Foundation, 2015). At the outset of remote online voting trials no voting systems had verifiability but some systems have introduced it to improve security and protect electoral integrity. Norway was the first country to try universally verifiable voting, though after two trials in selected municipalities in local and national elections, pilots have now been terminated as the current government regards online voting and the secret ballot as incompatible (Government of Norway, 2014). Currently, some systems use individual verifiability and are preparing to launch versions that enable universal verifiability (e.g., Estonia in 2017 and by 2018 in Switzerland). While technical experts state that individual verifiability is important, there is near “universal” consensus that an E2E verifiable system is necessary for electoral integrity and proper auditability. The idea of universal verifiability is premised on having evidence-based results or proof for the voter that their vote made it into the ballot box as they intended, and that anyone can establish that the votes were tallied correctly.
In practice, the two principles of being able to verify votes are cast as intended and tallied as cast take place in three phases or steps whereby voters can check that their ballot was cast an intended, recorded as cast and tallied as cast:
- Cast as intended – at the time of voting, voters are provided with evidence, often in the form or a receipt or code, that their encrypted ballot reflects their voting choice.
- Recorded as cast – voters can check that the encrypted ballot has been included correctly by seeing the encrypted code they cast on a public list, which shows the encrypted votes that have been cast.
- Tallied as recorded – “any member of the public can check that all the published encrypted votes are correctly included in the tally, without knowing how any individual voted” (Benaloh et al., 2014).
The first and second steps often involve providing the voter with a code/ “receipt” upon finalizing the casting of their ballot, which they can use to carry out this check. The third step relies on mathematical proofs, and either mixes the ballots by removing voters’ personal information and decrypting the votes, or uses something called “homomorphic encryption” which allows for the votes to be tallied without decrypting them to verify the tally is correct (Benaloh et al., 2014). The key to this third element is being able to ensure the election results were tabulated correctly without revealing any additional information about the votes or voters.
_
End-to-end verifiable voting systems:
End-to-end auditable or end-to-end voter verifiable (E2E) systems are voting systems with stringent integrity properties and strong tamper resistance. E2E systems often employ cryptographic methods to craft receipts that allow voters to verify that their votes were counted as cast, without revealing which candidates were voted for. As such, these systems are sometimes referred to as receipt-based systems. A researcher has argued that end-to-end auditability and receipt-freeness (the voter cannot prove how he voted) should be considered to be orthogonal properties. Other researchers have shown that these properties can co-exist, and these properties are combined in the 2005 Voluntary Voting System Guidelines promulgated by the Election Assistance Commission.
In 2004, David Chaum proposed a solution that allows a voter to verify that the vote is cast appropriately and that the vote is accurately counted using visual cryptography. After the voter selects their candidates, a DRE machine prints out a specially formatted version of the ballot on two transparencies. When the layers are stacked, they show the human-readable vote. However, each transparency is encrypted with a form of visual cryptography so that it alone does not reveal any information unless it is decrypted. The voter selects one layer to destroy at the poll. The DRE retains an electronic copy of the other layer and gives the physical copy as a receipt to allow the voter to confirm that the electronic ballot was not later changed. The system guards against changes to the voter’s ballot and uses a mix-net decryption procedure to ensure that each vote is accurately counted. Sastry, Karloff and Wagner pointed out that there are issues with both of the Chaum and VoteHere cryptographic solutions.
Chaum’s team subsequently developed Punchscan, which has stronger security properties and uses simpler paper ballots. The paper ballots are voted on and then a privacy-preserving portion of the ballot is scanned by an optical scanner.
The Prêt à Voter system, invented by Peter Ryan, uses a shuffled candidate order and a traditional mix network. As in Punchscan, the votes are made on paper ballots and a portion of the ballot is scanned.
The Scratch and Vote system, invented by Ben Adida, uses a scratch-off surface to hide cryptographic information that can be used to verify the correct printing of the ballot.
The ThreeBallot voting protocol, invented by Ron Rivest, was designed to provide some of the benefits of a cryptographic voting system without using cryptography. It can in principle be implemented on paper although the presented version requires an electronic verifier.
The Scantegrity and Scantegrity II systems provide E2E properties, however instead of being a replacement of the entire voting system, as is the case in all the preceding examples, it works as an add-on for existing optical scan voting systems. Scantegrity II employs invisible ink and was developed by a team that included Chaum, Rivest, and Ryan.
The STAR-vote system under development for Travis County, Texas is another way to combine an E2E system with conventionally auditable paper ballots, produced in this case by a ballot marking device.
_
End-to-end-verifiable (E2E-V) technologies can be used in a variety of voting scenarios. In its 2015 report, the U.S. Vote Foundation asserted that any possible future Internet voting system should utilize E2E-verification, but the report stated that this should not even be attempted before greater experience has been garnered with E2E-V systems deployed and used within in-person voting scenarios. E2E-V voting mitigates some of the vulnerabilities in Internet voting. However, advances in prevention of malware and DoS attacks need to be realized before any Internet voting should be undertaken in public elections—even if E2E-V.
Note:
- All Internet voting schemes (including those that are E2E-V) are vulnerable to DoS attacks.
- The Internet is not currently a suitable medium for the transmission of marked ballots, as Internet-based voting systems in which votes are cast on remote computers or other electronic devices and submitted electronically cannot be made adequately secure today.
- E2E-verifiability may mitigate many of the threats associated with Internet voting.
- Conducting secure and credible Internet elections will require substantial scientific advances.
_____
_____
Blockchains in internet voting:
Blockchains are a cryptographic technology that have been around for more than 40 years but have attracted recent interest given the fascination with Bitcoin. Scholarly literature points out that defining blockchain is challenging and a firm definition is “far from clear” (Mattila, 2016). A Berkeley Engineering Sutardja Center for Entrepreneurship & Technology Technical Report (2015) provides a simple definition and explains that blockchain refers to:
A blockchain is essentially a distributed database of records or public ledger of all transactions or digital events that have been executed and shared among participating parties. Each transaction in the public ledger is verified by consensus of a majority of the participants in the system. And, once entered, information can never be erased. The blockchain contains a certain and verifiable record of every single transaction ever made. Bitcoin, the decentralized peer-to-peer digital currency, is the most popular example that uses blockchain technology.
There is a simple analogy that explains the value of blockchain technology: stealing a cookie for a cookie jar is easy if the jar is secluded, however, stealing a cookie from a market that is observed by thousands of people is more difficult (Crosby et al., 2015).
The characteristics of blockchain are seen as useful in instances where a transparent and irreversible transaction record is required (Bracamonte, Yamasaki and Okada, 2016). Specifically, elements such as distributed verification, decentralization, transparency and irreversible transactions are qualities of blockchain that have been identified as useful to contribute to the criteria online of voting systems such as uniqueness of the vote, verifiability and auditability and vote integrity, among others.
_
Blockchains are a technology meant to achieve an unalterable, decentralized, public, append-only log of transactions, without any single authority in a position to change the log. In an election context, the “transactions” would be the casting of ballots. A blockchain could therefore act as a virtual electronic ballot box. Blockchains may be managed publicly or by a restricted set of managers. Several companies provide, or are attempting to build, voting systems around blockchains.
There is a lot of enthusiasm surrounding the potential of blockchain to revolutionize online voting. Many assert that blockchain is the “missing link for transparent, verifiable election systems” (Nasser et al., 2016) and point to its potential to detect tampering of any kind. Yet among the technical experts there was unanimous agreement that while blockchain is very useful and can contribute to improving or perhaps eventually solving some issues with online voting, it is by no means a panacea that will magically address problems or concerns with the technology. A recent study by Nasser et al., (2016) further emphasizes this point, by stating: “blockchains are a useful augmentation to verifiable voting in some circumstances and may introduce interesting ways of voting in non-traditional settings; but on the other hand, blockchains are not a panacea”.
_
Here are some examples of how blockchain can contribute to improved online voting:
-The Bitcoin network can prevent double spending of assets. Using a transaction to represent a vote for a specific candidate could protect the uniqueness of the vote.
-Open source approaches to online voting are often favoured because they enhance transparency. A Bitcoin’s code is open source and everything that comes through the system is traceable, making it highly transparent.
-Having a verifiable audit trail is recommended to ensure votes are cast as intended. Some argue having a paper receipt is the ideal audit trail for electronic voting. Bitcoin blockchain keeps a record of all transactions with the ability to view and track them. This could enable verifiability by allowing voters to check the transaction record to verify their vote. As explained, below, however, the transaction record presently reveals too much information for binding elections.
-Once a transaction is recorded in the Bitcoin blockchain it is considered irreversible. Applied to voting, once a voting transaction was added to the blockchain and confirmed it would be difficult to modify or delete voting records (Bracamonte, Yamasaki and Okada, 2016).
_
A recent paper on blockchains and voting explains how a blockchain voting system operates:
Voters register a Bitcoin address with the election authority (EA). The EA publishes a list of addresses but does not list which address belongs to which voter. Each candidate also specifies a Bitcoin address. Voters then cast a ballot by sending a small payment to their selected candidate. Any deviation from the voting rules (e.g., one vote per voter) can be seen by inspecting the blockchain, and the tally is visible by inspecting the candidate’s received payments.
The primary benefit of this approach is that votes are cast on a global network of computers that is decentralized, and not affiliated with election authorities so the system is distributed and independent. By contrast, a key disadvantage is that the registration authority is privy to information about the voting transactions that could breach voter privacy. Ballot secrecy can also be compromised since the time each vote is cast is tracked on the ledger, which could allow for tracking or possibilities for fraud such as vote selling and voter coercion or intimidation. Another disadvantage is that “votes can be seen as they come in” which enables transparency but also tallies by particular candidates. Third, the ability to carry out voting transactions can be done more simply in other systems than through a standard Bitcoin transaction (Nasser et al., 2016). Finally, instead of passwords, blockchains require something stronger called a cryptographic key, which would be stored on a voter’s computer. Kept on a computer the key would be vulnerable to being lost or stolen by malware. While this is not an exhaustive list of drawbacks of bitcoin-based voting systems it raises questions about the usefulness of this approach for voting.
A final consideration is the complexity of such a system. One issue with most electronic or online voting systems is their complexity, which can make it difficult for the average voter to understand how things work. The blockchain approach seems additionally complicated which would provide less transparency for the voter.
In addition to the operational issues, at this point blockchain is not able to address a number of security concerns.
An open letter on blockchains written by a group of computer scientists identifies the issues and security threats blockchain cannot address now, or in the foreseeable future, as seen in the table below:
Technical issues blockchains cannot solve in internet voting:
| Transparency |
|
| Authentication |
|
| Verification |
|
| Security |
|
_
The use of blockchains in an election scenario would do little to address the major security requirements of voting, such as voter verifiability. The security contributions offered by blockchains are better obtained by other means. In the particular case of Internet voting, blockchain methods do not redress the security issues associated with Internet voting.
A final issue raised in expert consultations that is unique to blockchains, specifically cryptocurrencies, is the proof-of-work the system uses which relies upon people donating computer power for a financial incentive and ensures that no one individual can take control of the blockchain. This set-up is premised on the fact that there is more collective good than there is bad. However, if those with malicious intent gained control of more than 50% of the total computing power, they would have the ability to change the transaction history. Lack of the financial bitcoin incentive, and possible competing interests over the outcome of an election, raises concerns about control of the blockchain.
Overall, blockchains are a useful technology that can contribute toward enabling a secure voting solution and improving parts of online voting systems, but there is much they cannot address and they are not the silver bullet to delivering issue-free online voting (Kiniry et al., 2016). There is also a lot we do not know about blockchain that future research and development can help to understand and apply.
_
While the notion of using a blockchain as an immutable ballot box may seem promising, blockchain technology does little to solve the fundamental security issues of elections, and indeed, blockchains introduce additional security vulnerabilities. In particular, if malware on a voter’s device alters a vote before it ever reaches a blockchain, the immutability of the blockchain fails to provide the desired integrity, and the voter may never know of the alteration.
Blockchains are decentralized, but elections are inherently centralized. Although blockchains can be effective for decentralized applications, public elections are inherently centralized—requiring election administrators define the contents of ballots, identify the list of eligible voters, and establish the duration of voting. They are responsible for resolving balloting issues, managing vote tabulation, and announcing results. Secure voting requires that these operations be performed verifiably, not that they be performed in a decentralized manner. While it is true that blockchains offer observability and immutability, in a centralized election scenario, observability and immutability may be achieved more simply by other means. Election officials need only, for example, post digitally signed versions of relevant election-related reports for public observation and download.
Ballots stored on a blockchain are electronic. While paper ballots are directly verifiable by voters, electronic ballots (i.e., ballots on a blockchain) can be more difficult to verify. Software is required to examine postings on blockchain. If such software is corrupted, then verifiability may be illusory. Software independence is not, therefore, achieved through posting ballots on a blockchain: as ballots are represented electronically, software independence may be more difficult to achieve.
The blockchain abstraction, once implemented, provides added points of attack for malicious actors. For example, blockchain “miners” or “stakeholders” (those who add items to the blockchain) have discretionary control over what items are added. Miners/stakeholders might collude to suppress votes from certain populations or regions. Furthermore, blockchain protocols generally yield results that are a consensus of the miners/stakeholders. This consensus may not represent the consensus of the voting public. Miners/stakeholders with sufficient power might also cause confusion and uncertainty about the state of a blockchain by raising doubts about whether a consensus has been reached.
Blockchains do not provide the anonymity often ascribed to them. In the particular context of elections, voters need to be authorized as eligible to vote and as not having cast more than one ballot in the particular election. Blockchains do not offer means for providing the necessary authorization.
Blockchains do not provide ballot secrecy. If a blockchain is used, then cast ballots must be encrypted or otherwise anonymized to prevent coercion and vote-selling. While E2E-V voting methods may provide the necessary cryptographic tools for this, ordinary blockchain methods do not.
It may be possible to employ blockchains within an election system by addressing the security issues associated with blockchains through the use of additional mechanisms (such as, for example, those provided by E2E-verifiability), but the credit for addressing such problems would lie with the additional mechanisms, not with the use of blockchains.
Scalability:
Another of those unknowns is scaling a blockchain system up to cater for what could be hundreds of millions of votes being processed. When Bitcoin reached a value of almost $20,000, transactions became a lot slower due to the number of people attempting to buy and sell the cryptocurrency. If this happens with voting, it’s going to cause problems — because election results are needed within hours. There’s a statistic on bitcoin transactions that can only handle seven a second. If you do that in an election, it might be possible in a voting context if you’ve got thousands rather than millions. But if you’re talking about millions of votes — take the Brexit referendum with 35 million votes cast: if you could only verify those at seven a second, it’d take fifty-five days to get everything worked out.
One area where blockchain can improve elections is in transparency, not only because the ledgers can easily be viewed, but also because the startups providing the technology have an opportunity to publish open-source code showing how the system works — and that it can be trusted.
_____
_____
Countries using Electronic Voting:
Electronic voting systems are used in countries throughout the world, but adoption of this technology has been somewhat scattershot. A few countries have tested electronic voting and adopted it, others have tried it out and abandoned it, and some continue to test it or have plans for further testing in the future. Only a small handful of countries use electronic voting technology on an ongoing basis, and even fewer use it nationwide as the sole voting method.
- Countries that use electronic voting nationwide:
Brazil, Estonia, India, Venezuela
- Countries that use electronic voting in some areas:
Canada, United States, Peru, Argentina
- Countries where electronic voting has been tested:
Bhutan, United Kingdom, Italy, Norway, Kazakhstan, Australia, Nepal, Philippines, Australia, Guatemala, Costa Rica, Ecuador, Russia, Mongolia, Nepal, Bangladesh, Indonesia, Finland, Somalia (Somaliland), Switzerland
- Countries where electronic voting has been discontinued:
Belgium, France, Netherlands, Germany, Paraguay, Japan
There are about 120 countries in the world that practice democracy. Of all those democratic countries, only about 25 have experimented with or used electronic voting to elect their governments. So, electronic voting is not the dominant choice of the world for recording and/or counting votes in elections. The countries that have used electronic voting include small nations like Estonia to the oldest democracy, the United States of America. It is very interesting to note that different trends are seen in different regions. Parts of Europe and North America can be seen as moving away from the use of electronic voting, while South America and Asia show increasing interest in using electronic voting technologies. No other country in the world has used electronic voting in as large a scale as India has. Since India is currently the second largest population in the world and therefore by default becomes the largest national population to vote in a democratic process, any use of electronic voting machines on a pan Indian scale would make it the largest instance of electronic voting.
_
Table below shows status of electronic voting in various countries:
_
_
Comparison among electronic voting systems of various countries:
The above table provides an overview of the experiences of various countries using electronic voting. The comparative focus is on the adoption of electronic voting systems adopted at the international level.
_____
Electronic Voting in Developing Countries:
The developing world has been reported to have significant interests in voting technology and the rate of e-voting implementation has been faster therein than in developed countries. In countries such as Nigeria, e-voting has been considered a necessity and as the only solution for credible elections. Nigeria has set its eyes on e-voting since 2011 and, undeterred by the problems found during its implementation, seems determined to proceed with the technology. In Nigeria, the traditional voting system was believed to have allowed significant irregularities and a lower level of probity, accountability and transparency, and have overseen corruptions, oppressive acts and administrative failures. Similar enthusiasm has been shown in India, where e-voting was assumed to be significantly more reliable than paper ballot. In contrast, e-voting in Brazil is often seen from a different perspective, placing more concerns in the social aspects of its implementation. Although Brazil’s e-voting election in 2000 was considered a success, issues of the lack of public trust and confidence in the system have been raised. E-voting has failed to improve public involvement in politics and the delivery of public services despite the vast investments made to generate public trust in the system. Critiques have also been raised over the government decision to employ the technology, given that millions of Brazilians still suffered from poverty and illiteracy. The decision has been seen as market-driven and lacked adequacy in terms of information and communication technologies strategy. Such a dispersed way of perceiving the technology might have been caused by a lack of theoretical common ground, departing from an insufficient literature review that focused specifically on e-voting in developing countries.
___________
Electronic voting in the united states:
The US is the oldest modern democracy in the world. It is in its 25th decade of democracy but the country does not have a uniform voting system. Several states continue to use ballot papers, while others have shifted to electronic voting. Some experimented with the electronic voting system but returned to the ballot papers in the face of apprehensions.
Five states in the U.S. — Louisiana, Georgia, South Carolina, New Jersey, and Delaware — run their elections using direct recording electronic machines (DREs), which provide no paper trail of the votes.
A critical point in electronic voting experiment in the US has been that its voting machines are connected to a server and operate using the internet. This makes them vulnerable to cyberattacks. This mode of DRE functioning has been questioned several times and has even forced some countries to do away with electronic voting. But, incidentally, they have generally not thought of introducing non-networked standalone EVMs – as used in India – to use in elections in their countries.
_
Voting in the United States is an extremely complex topic, because it’s handled at the state and local level. Some areas still use paper ballots that are counted by hand, but most use some type of electronic assistance in the counting and casting of ballots. Some of these electronic voting systems have a paper trail as a hedge against tampering, and others don’t. Some systems also transmit voting data over the internet in some way, while others rely on election workers and volunteers to physically transport voting machines, and the data they contain, once voting has closed.
Figure above shows main types of electronic voting systems that are in use, or have been used in the past, in the United States.
_______
_______
Electronic voting machine (EVM) of India:
_
India is the world’s largest democracy. The protected right conceded by the Indian constitution to its whole national is Right to Vote. It’s extremely troublesome and tedious utilizing the paper ballot system for the purpose of elections, remembering this, paperless Direct Recording Electronic (DRE) voting machines were developed and commonly known as Electronic Voting Machine (EVM). The massive scale of voting in India creates a strong case for EVM use. Over 60% of the more than 800 million registered Indian voters cast their vote in the last general elections in 2014. Using paper ballots for Indian parliamentary elections requires some 8,000 tons of paper, equivalent to cutting down 120,000 full grown trees. There are other cost inefficiencies, namely recurring expenditures on printing, storage, transportation, counting and security of ballot papers. A second issue is the frequency of electoral violations such as booth capturing, voter intimidation, and vote buying. According to a South Asia Monitor report, 70% of polling booths in Bihar were declared sensitive or hypersensitive — a euphemism for areas prone to violence. Despite the measures introduced by the election commission of India (ECI), poor and illiterate voters, women and the elderly still remained at risk from violence and vote capture. The ECI had discussed electronic voting since 1977 mostly for efficiency reasons. In 1999, Goa became the first state to introduce EVMs in its legislative assembly elections. Other states introduced EVMs through 2008. How does the EVM work? First, election officials check a voter’s ID card and signature. Then they press the ballot button allowing one vote. Inside the polling cubicle, the voter presses the key next to the candidate of choice. A red lamp signals to the voters that the vote is cast. At the same time, election officials are alerted that voting is complete. By default, EVMs in India only allow five votes per minute. This is a key feature that sets apart Indian EVMs and radically decreases the probability of booth capturing and false ballots. Moreover, once recorded, it is difficult to tamper with EVM data. The electronic process is also more efficient. It reduces human error and increases speed while counting votes. A study found that these factors directly impact election outcomes.
__
The advantages of the EVM over the traditional ballot paper/ballot box system are –
-It eliminates the possibility of invalid and doubtful votes which, in many cases, are the root causes of controversies and election petitions.
-It makes the process of counting of votes much faster than the conventional system.
-It reduces to a great extent the quantity of paper used thus saving a large number of trees making the process eco-friendly.
-It reduces cost of printing (almost nil) as only one sheet of ballot paper is required for each Polling Station.
-It reduces transportation cost related to transporting conventional ballot papers and the ballot boxes in which ballot papers are.
___
Design and technology:
An EVM consists of two units, control unit (CU) and balloting unit (BU). The two units are joined by a five-meter cable. Balloting unit facilitates voting by voter via labelled buttons while control unit controls the ballot units, stores voting counts and displays the results on 7 segment LED displays. The controller used in EVMs has its operating program etched permanently in silicon at the time of manufacturing by the manufacturer. No one (including the manufacturer) can change the program once the controller is manufactured. It leverages advances in technology to strengthen security, verifiability and traceability. The security features include authentication based on Public Key Cryptography (PKC), laser marked unique serial numbers, tamper resistant and tamper detection features. EVMs are manufactured by Bharat Electronics Limited (BEL), Bangalore and Electronics Corporation of India Limited (ECIL), Hyderabad, and powered by an ordinary 6-volt alkaline battery. This design enables the use of EVMs throughout the country without interruptions because several parts of India do not have power supply and/or erratic power supply.
An EVM can record a maximum of 3840 votes and can cater to a maximum of 64 candidates. There is provision for 16 candidates in a single balloting unit and up to a maximum of 4 units can be connected in parallel. The conventional ballot paper/box method of polling is used if the number of candidates exceeds 64. It is not possible to vote more than once by pressing the button again and again. As soon as a particular button on the balloting unit is pressed, the vote is recorded for that particular candidate and the machine gets locked. Even if one presses that button further or any other button, no further vote will be recorded. This way the EVMs ensure the principle of “one person, one vote”. The lifespan of an EVM is 15 years & even more and votes recorded in the Control Unit can be stored up-to its lifetime until it is cleared. If the Court orders a recount, the Control Unit can be reactivated by fixing the battery and it will display the result stored in its memory.
_
The EVMs were devised and designed by Election Commission of India in collaboration with two Public Sector undertakings viz., Bharat Electronics Limited, Bangalore and Electronics Corporation of India Limited, Hyderabad. There are number of variants available for the EVMs. Time-to-time, it has evolved and has become more robust. In case of pre-2006 (M1) and post-2006 EVMs (M2), 4 Balloting Units can be cascaded together to accommodate up to a maximum of 64 candidates (including NOTA), which can be used with one Control Unit. In case of upgraded post-2006 EVMs (M3), 24 Balloting Units can be cascaded together catering to 384 candidates (including NOTA) which can be used with one Control Unit.
Evolution of the machine:
With each iteration, new security features and in-built mechanisms have been incorporated.
A look at the three models:
M1
Manufactured: 1989-2006
Last used: 2014 general elections
Not compatible with VVPAT
M2
Manufactured: 2006-2012
In use
Encryption, time-stamping of key press
M3
Manufactured: 2013 onwards
In use; replacing significant number of older models by end of 2018
Stops functioning if tampered with and has self-diagnostics.
The original M1 was non-hackable. The M2 EVMs were upgraded further to incorporate to enable transfer of the message from Ballot Unit (BUs) to Control Unit (CUs) in an encrypted form making the message non-readable. The new M3 EVM machines will have Tamper Detection to make an EVM inoperative the moment anyone tries to open the machine and a Self-diagnostic feature to checks the EVM fully, every time it is switched on to detect any change in its hardware or software.
___
Ballot Unit:
Ballot unit is used by voters for casting their votes.
_
_
Control Unit:
The Control Unit is the main unit which stores all data and controls the functioning of EVM. The program which controls the functioning of the control unit is burnt into a microchip on a “one-time programmable basis”. Once burnt it cannot be read, copied out or altered. The EVMs use dynamic coding to enhance security of data transmitted from ballot unit to control unit. The new EVMs have also got real time clock and date-time stamping facility which enables them to record the exact time and date whenever a key is pressed. After the voting is completed and the close button is pressed, the machine does not accept any data or record any vote. The display system of the control unit shows the total number of votes polled in a polling station and the candidate-wise votes polled in the machine when the ‘result’ button is pressed by the counting staff in the presence of counting agents at the counting center. The control unit can also detect any physical tampering made with the connecting cable and indicate the same in the display unit. India’s EVM is a standalone device not connected to any network.
__
Do the Indian EVMs use foreign technology?
EVMs are being produced indigenously by two PSUs. The Software Program Code is written in-house, by these two companies and is not outsourced, so as to maintain the highest levels of security. India only uses microchips from manufacturers in US or Japan as India does not have the capability of producing microchips within the country. The software code is written in India and converted into machine code and only then given to the chip manufacturer in US or Japan. Every microchip has an identification number and the producers have their digital signatures on them. So, the question of their replacement does not arise at all because microchips are subjects to functional tests with regard to the software.
_
What are the different levels of checks?
- First Level Checking: BEL/ECIL engineers certify originality of components after technical and physical examination of each EVM, undertaken in front of representatives of political parties.
- Polling Stations: EVMs are randomised twice while being allocated to an Assembly and then to a polling booth and then Mock Polling is conducted in front of polling agents and representatives of each political party on the poll day before polls begin. After Poll, EVMs are sealed and polling agents put their sign on the seal.
- Strong Rooms: Candidates or their representatives can put their own seals on the strong rooms where polled EVMs are stored after the poll. These strong rooms are guarded 24×7.
- Counting Centers: The polled EVMs are brought to the Counting Centers and Unique IDs of the seals and CU are shown to reps of candidates before start of counting.
_
Can anybody tamper with the EVMs?
Utmost care has been taken to make the EVM tamper proof. The programming of the microprocessor chip used in EVMs is burnt into the chip. The fused program can neither be altered nor overwritten. Any attempt to burn additional or substitute code on the chip would destroy its existing program and render it unusable/useless. The microchip used in EVMs is a one-time programmable/ masked chip, which can neither be read nor overwritten. Hence, the program used in the EVMs cannot be reprogrammed in a particular manner. Furthermore, the EVMs are stand-alone machines which are not accessible remotely from any network, nor are connected with any external devices and there is no operating system used in these machines. There is, therefore, absolutely no chance of programming the EVMs in a particular way to select any particular candidate or political party. As an additional precautionary measure, the machines prepared for a poll are physically sealed in the presence of candidates or their agents and kept in secure strong rooms guarded by Central Police Force which can also be watched by the representatives of the candidates. The storage places for these pre-poll or polled EVMs can be accessed only by following a stringent procedure set by the Commission ensuring complete transparency.
_
What is a procedure followed to seal the EVM?
Physical sealing of different segments of an EVM is done to prevent access to the buttons controlling various process of the poll. This is done in several stages. Sealing of ballot screen of the ballot unit and the candidate set section of the control unit are done under the supervision of Returning Officer in the presence of the candidates or their agents to prevent tampering with the alignment of the ballot paper and making unwanted changes in the candidate buttons that are actually required for a particular poll. Similarly, if the result section is not sealed, anyone can see the result of a particular polling station before it is taken up for counting at the counting centre on the specified date. The candidates or their agents are invited by the election authorities to put their signatures on the tags/paper seals along with the seals of the Returning/Presiding Officers.
_
Is it possible to use EVM in simultaneous election for Parliament and State Legislative Assembly?
Yes, simultaneous election for Parliamentary and State Legislative Assembly can be conducted through EVMs. Two separate EVMs –one for the Parliamentary election and the other for the Assembly election are used in such a situation.
_
Whether the EVMs can reveal the data that who voted for whom?
The ECI-EVMs have the facility to reveal that who voted for whom by using a device called ‘decoder’ which when attached to the EVM can print out statement of voting data showing the order in which the voters voted and to whom (i.e. the serial number pertaining to the particular candidate in the Ballot paper) they voted. But these decoders are never allowed to be put to use as revealing of any such information will violate the secrecy of voting provided under the law. Only on the orders of competent courts, such information can be printed and shown.
_
Voter Verifiable Paper Audit Trail (VVPAT):
Voter Verifiable Paper Audit Trail is an independent system attached with the Electronic Voting Machines that allows the voters to verify that their votes are cast as intended. When a vote is cast, a slip is printed on the VVPAT printer containing the serial number, name and symbol of the candidate and remains exposed through a transparent window for 7 seconds. Thereafter, this printed slip automatically gets cut and falls in sealed drop box of the VVPAT. VVPAT consists of a Printer and a VVPAT Status Display Unit (VSDU). VVPAT runs on a power pack (Battery) of 22.5 volts. Control Unit and VSDU are kept with the Presiding Officer/Polling Officer and Balloting Unit and Printer are kept in the voting compartment.
On 8 October 2013, Supreme Court of India delivered its verdict on Subramanian Swamy’s PIL, that Election Commission of India will use VVPAT along with EVMs in a phased manner and the full completion should be achieved by 2019. The Court’s exact words: “From the materials placed by both the sides, we are satisfied that the “paper trail” is an indispensable requirement of free and fair elections. The confidence of the voters in the EVMs can be achieved only with the introduction of the “paper trail”. EVMs with VVPAT system ensure the accuracy of the voting system. With an intent to have fullest transparency in the system and to restore the confidence of the voters, it is necessary to set up EVMs with VVPAT system because vote is nothing but an act of expression which has immense importance in democratic system.”
The paper trail should put to rest all doubts in the minds of voters and political parties. Since 2015, state polls have been held using paper trails. In these elections paper slips generated by some 1,500 machines were counted and tallied with the votes in the voting machines. There was not one mismatch. In June 2018, Election Commission of India decided that all VVPATs will have a built-in-hood to prevent it from excess light and heat.
_
Cost:
The cost per EVM was ₹5,500 (equivalent to ₹42,000 or US$580 in 2017) at the time the machines were purchased in 1989–90. The cost was estimated to be ₹10,500 (equivalent to ₹12,000 or US$170 in 2017) per unit as per an additional order issued in 2014. Even though the initial investment was heavy, it has since been expected to save costs of production and printing of millions of ballot papers, their transportation and storage, substantial reduction in the counting staff and the remuneration paid to them. RTI queries revealed that from 1989-90 till May 15, 2017, the Election Commission procured a total of 1,005,662 BUs and 928,049 CUs from BEL, plus another 1,014,644 BUs and 934,031 CUs from ECIL.
_
Overseas usage of Indian EVMs:
Nepal, Bhutan, Namibia and Kenya have purchased India-manufactured EVMs. Fiji was expected to use Indian EVMs in its elections in 2014. In 2013, the Election Commission of Namibia acquired 1700 control units and 3500 ballot units from India’s Bharat Electronics Limited; these units were to be used in the regional and presidential elections in 2014. Several other Asian and African countries are reportedly interested in using them as well.
____
EVM malfunction:
Various Malfunctioning of EVM seen during several elections:
-EVM could not start
-EVM got jammed and did not open on counting day
-EVM stopped functioning during the poll/in between the polling process
-When button of one candidate pressed, light on another candidate got flashed [discussed later on]
-Polling staff was not at all updated or aware about the security measures.
A large number of complaints about malfunctioning of electronic voting machines (EVMs) were received but the Election Commission dismissed them as “exaggerated,” claiming that the “severe heat conditions” had interfered with the machines. However, they were quickly replaced with the ones in reserve. There was no denying the heat: in fact, in Palghar and Bhandara-Gondiya, bedsheets, table-cloth and fans were used to protect the EVMs from the searing heat, harsh light and dust. The sensors of these EVMs are extremely sensitive to heat, light and dust. All Voter Verifiable Paper Audit Trail (VVPAT) machines will henceforth have a built-in hood to ensure that they are not exposed to excess light and heat. This is part of the corrective measures initiated by the Election Commission of India after several VVPATs malfunctioned during the recent Gondiya and Kairana bypolls, triggering strong reactions from different quarters.
_____
Advantages of Indian EVM:
Electronic Voting Machines (EVMs) have revolutionised the Indian election process. The advantages of electronic voting machines is simplicity of the procedure, the ease of tabulation of ballots into results and the faster and more accurate results. It`s easy to see the utility of the machine— it eliminates invalid votes, ends booth capturing, and makes counting easier and faster. It is tamper-proof, error-free and easy to operate.
- EVMs reduce the time in casting votes.
- EVMs also reduce the time taken to count votes and declare results.
- Claims were made earlier that the systems could be tampered with and the security could be breached, but this has not been proved.
- EVMs save paper.
- These machines are powered by batteries and do not rely on electricity which ensures uninterrupted voting.
- EVMs can accommodate 64 candidates in a single constituency.
- Votes can be stored for up to 10 years.
- The program of EVMs cannot be changed and have a sealed security chip, therefore votes cannot be rigged without damaging the program. This prevents fraud.
- Only one vote can be cast per person as the machine will register only the first button pressed.
- EVMs restrict 5 votes for every minute.
- NOTA was introduced recently at EVMs for voters to cast their vote even if they are not in favor of any of the candidates or parties. NOTA votes are counted and indicates that the elector is not happy with any of the candidates.
_
Limitations of Indian EVM:
- If your preferred language is English, then you might face a little difficulty. You should be familiar with the candidates symbol you wish to vote for. The names of the candidates will be placed alphabetically in the respective language of the state. Therefore, in Maharashtra, the names appear in Marathi, in Karnataka, the names appear in Kannada, and so on.
- Each ballot unit can accommodate only 16 candidates. Therefore, ballot units may be linked together to accommodate more. A total of 4 ballot units can be linked to accommodate 64 candidates from a single constituency. Any number above this will have to be added by the old manual voting method.
- EVMs can record 3840 votes. Although, this number is not much of a limitation as the number of voters at a polling station is generally lower.
- A candidate can know how many people from a polling station voted for him. This is a significant issue particularly if lopsided votes for/against a candidate are cast in individual polling stations and the winning candidate might show favoritism or hold grudge on specific areas. Bharat Electronics Limited, Bengaluru, and Electronics Corporation of India Limited, Hyderabad, developed the totaliser. Totaliser is an interface, which is connected to main control units of a cluster of 14 EVMs (hence, in 14 polling stations), and the consolidated result of votes cast for each candidate in that group of EVMs can be obtained by pressing the result button in the totaliser, but without disclosing the votes polled by a candidate polling-station-wise.
Note:
The control units do not electronically transmit their results back to the Election Commission, even though a simple and unconditionally secure protocol for doing this exists. The Indian EVMs are purposely designed as stand-alone units to prevent any intrusion during electronic transmission of results. Instead, the EVMs are collected in counting booths and tallied on the assigned counting day(s) in the presence of polling agents of the candidates.
_______
The EVM Controversy in India:
In India, the Election Commissioners are very eminent persons whose capability, sincerity, neutrality and integrity are beyond question. They have been trying their best to conduct free and fair elections and have introduced far-reaching electoral reforms. They are held in high esteem by political parties and citizens alike. But like election administrators around the world, they have been criticised for underestimating the gravity of electronic security issues. The ECI, for its part, has been consistently claiming that its EVMs, security protocol and administrative safeguards are time-tested, robust, secure and tamper-proof. According to them, Indian EVMs are unique and any comparisons with the EVMs used elsewhere in the world are misplaced. Notwithstanding the ECI’s claims, at various points in time, the entire spectrum of political parties in India have expressed their reservations about the integrity of its EVMs. Elections are the bedrock of democracy. Confidence in the integrity of EVMs is important for voters to trust the outcomes of elections and the legitimacy of governments formed as a result of them. If the concerns about EVM security become widespread, that confidence could be eroded whether or not those concerns are well-founded. The ECI cannot allow that to happen and must retain an open mind that some of the concerns may be true and take expeditious steps to resolve the issues.
___
Computer tampering is unauthorized access to programs, data, or the computer, and it uses the access for fraudulent purposes or to damage another computer, data or program. Tampering means alteration in the software program written either on existing microchips of Control Unit (CU) or introducing malicious software program by inserting new microchips in CU and also making keys – pressed in Ballot Unit (BU) not record faithfully in the Control Unit.
_
The Penrose Conditions:
In his book “Shadows of the Mind” (1994), Roger Penrose, the globally renowned British mathematician and authority on Artificial Intelligence, visualised the hi-tech rigging of an election as follows. The date of a long-awaited election approaches. Numerous opinion polls are held over a period of several weeks. To a very consistent degree, the ruling party trails by three or four per cent but all the polls taken together have a much smaller margin of error, of less than two per cent. Polling day arrives and passes, the polls being held with electronic voting machines. When the votes are counted, the result is a complete surprise to almost everyone. The ruling party is back with a comfortable majority, having achieved its target of eight per cent over its nearest rivals. Yet the result is false. The vote-rigging has been achieved by a highly subtle means, namely, a computer virus. The virus was cleverly programmed to steal votes from other parties and give the ruling party precisely the majority it needs. The virus does more than just steal votes; it self-destructs, leaving no record whatsoever. In the 24 years since Roger Penrose wrote, such a scenario has already become a reality.
Penrose wrote that for such an electoral fraud to succeed, two conditions are necessary:
(i) The voting machine is programmable. That is because a virus can infect only a programmable computer.
(ii) The vote-counting process is not checked by humans at any stage.
It follows from Penrose’s first condition that an ideal Electronic Voting Machine (EVM) should be a stand-alone, non-networked machine with a Central Processing Unit (CPU) whose software is ‘burned’ into it and cannot be programmed after manufacture or manipulated in any manner. Indian EVMs answer to this successful description. They are more like calculators than computers and are not connected to any network (wired or wireless) including the Internet, and if they retain their physical integrity, they cannot be hacked.
But what if dishonest insiders and criminals get physical access to the EVMs and replace the EVM’s nonhackable CPU with a look-alike but hackable CPU that can be programmed to count votes dishonestly together with an embedded Bluetooth device that allows it to be remote controlled? What if this replacement is done at the manufacturing stage itself for a certain percentage of machines?
The probability of successful tampering may be low but it is non-zero. It is therefore important to analyse the security protocol and administrative safeguards that the Election Commission of India (ECI) has put in place and see if they are adequate to prevent such physical tampering of EVMs.
It follows from Penrose’s second condition that relying entirely on machine counting without any physical check by humans, at least in part, may leave the system vulnerable to attacks that can go undetected. So, in case of electronic voting, there should be provision for an additional verifiable record of every vote cast in the form of ‘paper print-outs’ which should then be hand counted and tallied with the machine total for at least a sample of the EVMs deployed. This is what the EVMs fitted with Voter Verified Paper Audit Trail (VVPAT) seek to achieve. If vote stealing has been done by replacing the non-hackable CPU of an EVM with a look-alike but hackable CPU, then such fraud can be detected by the hand counting of VVPAT paper slips for a sample of the EVMs. It follows that VVPAT is an absolute imperative and any discussion should center on the statistically significant sample size of EVMs for which hand counting of paper slips should be done.
_
Regardless of the assertions that EVM rigging isn’t possible, some argue that the doubts over them can erode public faith in the electoral process. It is viewed as particularly important that voting stays simple and transparent in a country that is home to the largest illiterate population in the world. “Electronics are never transparent. The poor man has always got this doubt in his mind,” said Arun Mehta, a technologist who in the late 1980s became one of the first in India to research and speak publicly about the vulnerabilities of EVMs. “The process needs to be sufficiently transparent so that the poor man who’s wasting his daily wage to go and vote should have confidence in the process.” These issues will assume even greater importance as India heads for its next parliamentary election in 2019.
_
Is EVM Software safe?
The electronic voting machines are safe and secure only if the source code used in the EVMs is genuine. The EVM manufacturers, the BEL and ECIL, have shared the ‘top secret’ EVM software program with two foreign companies, Microchip (USA) and Renesas (Japan) to copy it onto microcontrollers used in EVMs. This process could have been done securely in-house by the Indian manufacturers. Worse, when the foreign companies deliver microcontrollers fused with software code to the EVM manufacturers, the EVM manufacturers cannot “read back” their contents as they are either OTP-ROM (one-time programmable read-only memory) or masked chips. Also the software given to foreign companies is not even made available with the Election Commission, ostensibly for security reasons. Adopting an open standards policy by making the software public and allowing parties to test the software installed in the EVMs would have offered better protection.
_
Is EVM hardware safe?
The danger for EVM manipulations is not just from its software. Even the hardware isn’t safe. Dr. Alex Halderman, professor of computer science in the University of Michigan says, “EVMs used in the West require software attacks as they are sophisticated voting machines and their hardware cannot be replaced cheaply. In contrast, the Indian EVMs can easily be replaced either in part or as wholesale units.” One crucial part that can be faked is microcontrollers used in the EVMs in which the software is copied. EVM manufacturers have greatly facilitated fraud by using generic microcontrollers rather than more secure ASIC or FPGA microcontrollers. Not just only microcontrollers, mother boards (cards which contain microcontrollers) and entire EVMs can be replaced. Neither the Election Commission nor the manufacturers have undertaken any hardware or software audit till date. As a result, such manipulation attempts would go undetected.
_
Is EVM hackable?
The Indian EVMs can be hacked both before and after elections to alter election results. Apart from manipulating the EVM software and replacing many hardware parts discussed above, Indian EVMs can be hacked in many ways.
-Each EVM contains two EEPROMs inside the Control Unit in which the voting data is stored. They are completely unsecured and the data inside EEPROMs can be manipulated from an external source. It is very easy to read (data from) the EEPROMs and manipulate them. Electrically Erasable Programmable Read-Only Memory (EEPROM) is a type of non-volatile memory used in computers and other electronic devices to store small amounts of data. EEPROM can be erased and reprogrammed through the application of electrical charge.
-The second and the most deadly way to hack Indian EVMs is by inserting a chip with Trojan inside the display section of the Control unit. This requires access to the EVM for just two minutes and these replacement units can be made for a few hundred rupees. Bypassing completely all inbuilt securities, this chip would manipulate the results and give out “fixed” results on the EVM screen.
_
Insider threat:
Unlike in the traditional ballot system where only the election officials were the “insiders”, electronic voting machine regime has spawned a long chain of insiders, all of whom are outside the ambit and control of the Election Commission of India. There is every possibility that some of these “insiders” are involved in murky activities in fixing elections. The “insiders” include the public sector manufacturers of India’s electronic voting machines namely, the Bharat Electronics Limited (BEL) and Electronics Corporation of India (ECIL), the foreign companies supplying microcontrollers, private players (some of which are allegedly owned by some political leaders) for carrying out checking and maintenance of electronic voting machines during elections.
_
Storage and Counting are Concerns:
The EVMs are stored at the district headquarters or in a decentralized manner in different locations. Election Commission’s concern for EVM safety becomes apparent only during elections, whereas security experts say that voting machines must remain in a secure environment throughout their life cycle. There could be many malpractices associated with electronic counting. “Everybody watches polling closely. Nobody watches counting as closely,” says Bev Harris, an American activist.
_____
Vulnerability of Indian EVM:
In 2010, a team led by J. Alex Halderman, Professor of Computer Science, University of Michigan, US, managed to get hold of an Indian EVM unofficially and published a paper titled “Security Analysis of India’s Electronic Voting Machines”. This was the first, independent, rigorous assessment of the security risks associated with Indian EVMs. It described the EVM’s design and operation in detail, and evaluated its security in light of relevant election procedures. It pointed out many vulnerabilities that the ECI’s “Technical Experts Committee” had failed to do. According to the paper, while the simple hardware design and the minimal software of Indian EVMs made certain software-based attacks less likely than in their counterpart Direct Recording EVMs in the West (DREs), they made a different set of highly dangerous attacks far easier. Such attacks which can steal votes and violate the secrecy of the ballot can be carried out by dishonest election insiders or other criminals with only brief physical access to the machines. The authors also demonstrated two such attacks.
- Dishonest Display Attack
The dishonest display adds a separate, hidden microcontroller that sends its own signals to the 7-segment LEDs to show fraudulent vote totals.
- Clip-on Memory Manipulator Attack
This attack uses new hardware to alter the internal state of the machine. Unlike the first category, which replaced hardware components with dishonest look-alikes, this category involves only the temporary application of new hardware. The attack prototyped is a device that clips directly to the EEPROM memory chips used to record votes inside the EVM. This small device fits discreetly in a shirt pocket. It facilitates two kinds of attacks: stealing votes and violating ballot secrecy.
The first attack is vote stealing. Any time between the start of polling and the public count, dishonest election insiders or other criminals could use the clip-on device to change the votes recorded in the EVM. In India, counting sometimes takes place weeks after voting, so criminals could wait for an opportunity to tamper with the machines while they are in storage. Another variation of this attack is an electronic version of the booth capture attack. In normal operation, the EVM limits the rate of voting to no more than 5 per minute. However, this device bypasses the software restrictions of the EVM, so an attacker is able to again forcibly take control of an EVM and stuff the electronic “ballot box” with any number of votes.
The second kind of attack is to violate ballot secrecy. Internally, the EVM records votes in the order in which they were cast, and this device can be used to extract these records. An attacker who observed the order in which voters used the machine could then determine which candidate each voter selected.
In order to mitigate these threats, the researchers suggest moving to a voting system that provides greater transparency, such as paper ballots, precinct count optical scan, or a voter verified paper audit trail, since, in any of these systems, skeptical voters could, in principle, observe the physical counting process to gain confidence that the outcome is fair.
But Election Commission of India points out that for such tampering of the EVMs, one needs physical access to EVMs, and pretty high tech skills are required. Given that EVMs are stored under strict security which can be monitored by candidates or their agents all the time, it is impossible to gain physical access to the machines. Physical tampering to hack EVM is easily detectable. Plus, to impact the results of an election, hundreds to thousands of machines will be needed to tamper with, which is almost impossible given the hi-tech and time-consuming nature of the tampering process.
_____
Unthinking implementation of VVPAT:
Ideally, the controversy over EVMs should have been laid to rest once the Supreme Court had ordered the implementation of EVMs with VVPAT in 2013. If this has not happened, it is partly due to the inordinate delay in procurement of VVPAT units and partly due to the ECI’s questionable action of prescribing a minuscule sample of EVMs for hand-counting of VVPAT slips. After some initial press reports stating that VVPAT slips may be counted in respect of 10 per cent or 5 per cent of the EVMs, the ECI threw a bombshell by ordering the hand counting of VVPAT slips only for one randomly chosen polling station (i.e. one EVM) per Assembly Constituency in the Assembly Elections for Gujarat and Himachal Pradesh held in December 2017 and Karnataka in May 2018. This worked out to just 182 out of 50,128 polling stations (or 0.36 per cent of the EVMs) in Gujarat; to just 68 out of 7,521 polling stations (or 0.90 per cent of the EVMs) in Himachal Pradesh; and to just 224 out of 56,696 polling stations (or 0.40 per cent of the EVMs) in Karnataka. Such a low percentage defeats the very purpose of introducing VVPAT and is fraught with all the risks of conducting elections with paperless EVMs.
Statistically Unsound:
Consider a hypothetical example where 4 Assembly Constituencies P, Q, R and S have 50, 100, 200 and 300 polling stations in them respectively. The ECI’s action of prescribing a uniform sample size of “one polling station (EVM) per Assembly Constituency” cannot obviously be correct for all the 4 constituencies. Since the number of polling stations in an Assembly Constituency varies widely from State to State and even within a State, the sample size should clearly be different for different Assembly Constituencies and bear a relation to the number of polling stations in the constituency.
In fact, there cannot even be a uniform per centage for sample size for all Assembly Constituencies as per standard statistical sampling theory. If ‘N’ is the Population Size and ‘n’ the Sample Size, then the smaller the value of N, the greater will be the value of n/N (i.e. the Sample Size relative to the Population Size). Thus, smaller States and smaller constituencies will have relatively larger Sample Sizes when expressed as a fraction of Population Sizes.
There are ready reckoners based on standard statistical sampling theory which can tell us as to what would be the Margin of Error for the chosen Sample Size for a given Population Size and a given Confidence Level. Taking the total number of polling stations in the State as the Population Size and the total number of EVMs taken up for hand counting of paper slips (which is equal to the number of Assembly Constituencies in the State) as Sample Size, and assuming Confidence Levels of 95 per cent and 99 per cent, Table below shows the resulting Margins of Error for the ECI-prescribed sample size in respect of Gujarat, Himachal Pradesh and Karnataka.
Margins of Error for ECI-prescribed Sample Size:
There was a “100 percent match” in the random vote count on EVMs and paper trail slips carried out by the Election Commission in 182 Gujarat polling stations in 2017. However, since only one EVM per constituency was audited with VVPAT, the margin of error is 7 to 10 %.
It is evident that the ECI-prescribed sample size for hand-counting of VVPAT slips is far too small leading to very high margins of error which are unacceptable in a democracy. It is open to legal challenge on this score. The ECI seems to have chosen the sample size arbitrarily when, in fact, its selection should have been grounded in standard statistical sampling theory. It is suggested that the ECI should choose the Population Size (N), the Confidence Level and the Margin of Error in such a way that the resulting Sample Size (n) is reasonable (neither too small nor too large), statistically sound and administratively viable.
Currently, VVPAT slips in one polling station per constituency are tallied with EVM results. However, most political parties have been demanding that this number should be increased by 10% to 30%. The ECI is aiming at 100% VVPAT coverage ahead of the 2019 Lok Sabha polls and the ECI would decide on the percentage of VVPAT counting in a ‘scientific’ manner and would arrive at a formula after consulting technical experts to minimise error. Formulas ranging from 5% to 15% VVPAT auditing were closely considered with 5% count finding favour as statistically sound and representative enough to audit the accuracy of the voting system. However, the plan never reached implementation stage.
_
Transparent use of statistical methods can help detect rigged electronic voting machines:
Tallying the results from VVPAT with aggregate count from respective EVMs is the best way to test whether or not EVMs have been tampered with. About 1.8 million EVMs are used across 543 Lok Sabha constituencies. Tallying all VVPAT counts with EVMs counts would defeat the very purpose of shifting from paper ballots to EVMs.
Suitable modifications can be made to account for differences in sizes of constituencies while deciding on the required proportion of tallying VVPAT with EVMs.
Now, to come to the question of how checking just a few EVMs can successfully detect any potential EVM tampering. The concept of probability is useful here.
Suppose a box contains 95 red balls along with five blue balls. The probability that a randomly drawn (i.e. drawn without any bias) ball will be red, is just the proportion of red balls in the box, which is 95/100. Once this ball has been taken out, the probability of drawing another red ball would be 94/99. Suppose the first nine drawn balls are all red. The box now contains 91 balls, of which 86 are red. The chance of drawing a red ball in the 10th draw will be 86/91.
Probability theory tells us that the chances of drawing 10 red balls in succession would be the product of these fractions. This number comes out to be 58.4%. What is the probability that there would be at least one blue ball in the first 10 draws from the box? It is 41.6%, which is the difference between 100% and probability of drawing all 10 red balls.
Now assume that the box contains all the EVMs in an election. The blue balls can be considered as tampered EVMs (if at all) and the red balls might correspond to the EVMs which are not tampered. Let us assume that we want a 95% probability, which is a widely accepted level in many sampling procedures, of getting a potentially rigged EVM in tallying VVPAT count with EVMs.
Let us take four different possibilities of level of potential rigging into account at the constituency level: 25%, 10%, 5% and 0.5%. We assume an equal distribution of 1.8 million EVMs across 543 constituencies. Tallying 11, 29, 58 and 534 VVPATs per constituency would allow us to find a rigged EVM with 95% probability for each of these four scenarios. You can see that as the level of EVM rigging falls, you need larger size of random sample to detect rigging.
Suitable modifications can be made to account for differences in sizes of constituencies while deciding on the required proportion of tallying VVPAT with EVMs. It is reasonable to assume that any acts of EVM rigging would be done in a large scale than just at the booth levels. Provided the process is carried out in a transparent and democratic manner, it could help dispel all fears of EVM tampering and facilitate smooth conduct of elections in our country.
______
______
Election Commission’s response to criticisms of EVM:
The independent Election Commission of India says ‘it completely reaffirms its faith in the infallibility of the EVMs these are fully tamper-proof as ever’. It adds ‘baseless, speculative and wild allegations are being made which deserve to be rejected’. There is an old saying the ‘winner takes it all and the loser cries foul!’ The results in various elections have made many of the losers of the polls cry foul that it is the technology that failed them and not that their poll promises were rejected by the people. According to the ECI, in 2014 national parliamentary elections, a whopping 1.4 million individual electronic voting machines were used in 930,000 polling stations spread across the country and these parliamentary polls have been smoothly conducted using the EVMs.
- In 2009, ECI invited skeptics to demonstrate the alleged fallibility of EVMs, using 100 randomly sourced machines from 10 states. The outcome was that none of the persons who were given opportunity could demonstrate that ECI-EVM could be tampered in any of the 100 machines put on display.
- ECI said that EVMs can neither be reprogrammed nor controlled by the external device. The source code is so designed that it allows the voter to cast the vote only once. The next vote can be recorded only after the Presiding Officer enables the ballot on the Control Unit. In between, the machine becomes dead to any signal from outside.
- The Commission said that the comparison between EVMs in India and abroad, where they have failed, are both misplaced and misguided. This is because most of the systems used in other countries are PC based and running on the operating system. Hence they are vulnerable to hacking. But EVMs in India are the standalone machine without being part of any input. The software in the chip is one time programmable and is burnt into the chip at the time of manufacture. Nothing can be written on the chip after manufacture. Thus there is a fundamental difference between EVMs in India and abroad. Unlike voting machines in some countries which are connected to a network, Indian EVMs are standalone. Tampering an EVM through the hardware port or through a Wi-Fi connection is not possible as there is no frequency receiver or wireless decoder in the EVM machine.
What if the chip inside the EVM is replaced or a Bluetooth device is inserted within the EVM?
This would mean that the institutional safeguards to protect the EVM (sealing and hardware checks, among others) are breached to fit a device within the EVM and to manipulate it from outside. In M3 machines, this is also technologically ruled out, as they shut down in the event of tampering.
- Can EVMs be manipulated by chip manufacturers?
The EVMs are produced indigenously by two PSUs – Bharat Electronics Ltd. and Electronics Corporation of India Ltd. – where the software program for the chip is written and converted into machine code before being given to the microchip manufacturer. The chips with digital signatures are subjected to functional tests on the embedded software. EVMs are randomly assigned to polling booths across States and candidates are alphabetically listed on ballot sheets (inserted onto the EVM’s ballot unit). For EVMs to be manipulated at the manufacturing level, it is assumed that there is some trojan present in the EVM already that will lead to votes being transferred to a particular party. This is impossible as there is no prior way in which the order of the candidate can be known besides the location where the EVMs will be used. In addition, VVPAT machines now display the voter’s choice, thereby bringing an extra layer of verification.
- Can Trojan Horse be incorporated into the chip in CU?
No.
Trojan horse is a destructive program that masquerades as a benign application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. Sequence of voting in EVM eliminates the possibility of injection of Trojan Horse. The stringent security measures by ECI make it impossible to introduce Trojan Horse in the field. Once a ballot key is pressed in CU, the CU enables BU for registering the vote and waits for the key pressing in the BU. During this period, all keys in the CU become Inactive till the entire sequence of casting of that vote is complete. Once any of the keys (candidates vote button) is pressed by a voter in BU, the BU transmits the key information to CU. The CU gets the data and acknowledges it by glowing the corresponding LED lamps in BU. After the enabling of ballot in CU, only the first key pressed is sensed and accepted by CU. After this, even if a voter keeps on pressing the other buttons that is of no use as there will not be any communication between CU and BU as the result of those subsequent key presses, nor will BU register any key press. To put it in other words, there can be only one valid key press (the first key press) for every ballot enabled using CU. Once a valid key press (voting process) is complete, until another ballot enabling key press is made there will not be any activity between the CU and the BU. Hence, sending of any malicious signal, by way of so called a sequenced key press, is impossible in the Electronic Voting Machines being used in India. Results cannot be altered by activating a Trojan Horse through a sequence of key presses. ECI-EVMs cannot be physically tampered with nor their components be changed without anyone noticing.
- Why tampering of EVMs is impossible or very difficult?
The machine is electronically protected to prevent any tampering/manipulation. The program (software) used in these machines is burnt into a One Time Programmable (OTP)/Masked chip so that it cannot be altered or tampered with. Further these machines are not networked either by wire or by wireless to any other machine or system. Therefore, there is no possibility of its data corruption. The software of EVMs is developed in-house by a selected group of Engineers in BEL (Defense Ministry PSU) and ECIL (Atomic Energy Ministry’s PSU) independently from each other. A select software development group of 2-3 engineers designs the source code and this work is not sub-contracted. After completion of software design, testing and evaluation of the software is carried out by an independent testing group as per the software requirements specifications (SRS). This ensures that the software has really been written as per the requirements laid down for its intended use only. After successful completion of such evaluation, machine code of the source program code is given to the micro controller manufacturer for writing in the micro controllers. From this machine code, the source code cannot be read. Source code is never handed over to anyone outside the software group of PSUs.
Micro controller manufacturer initially provides engineering samples to PSUs for evaluation. These samples are assembled into the EVM, evaluated and verified for functionality at great length. Bulk production clearance by PSU is given to micro controller manufacturer only after successful completion of this verification.
The source code for the EVM is stored under controlled conditions at all times. Checks and balances are in place to ensure that it is accessible to authorized personnel only. During production in the factory, functional testing is done by production group as per the laid down Quality plan and performance test procedures. The software is so designed that it allows a voter to cast the vote only once. The vote can be recorded by an elector from the ballot unit only after the Presiding Officer enables the ballot on the Control Unit. The machine does not receive any signal from outside at any time. The next vote can be recorded only after the Presiding Officer enables the ballot on the Control Unit. In between, the machine becomes dead to any signal from outside (except from the Control Unit). Samples of EVMs from production batches are regularly checked for functionality by Quality Assurance Group, which is an independent unit within the PSUs.
The control unit contains the main circuit board. The centerpiece is the EVM’s CPU, a Renesas H8/3644-series microcontroller driven by an 8.8672 MHz crystal oscillator. The CPU is custom manufactured with the election software permanently recorded in an internal mask ROM [ROM is the permanent part of a computer’s memory. The information stored there can be read but not changed. ROM is an abbreviation for ‘read-only memory’.]. This prevents the software from being electronically reprogrammed. Also on the main circuit board are the switches for the buttons on the face of the device, a buzzer, two EEPROM chips used for non-volatile storage of vote data, the display board connector, and the connector for the ballot unit. There are nearly 1.4 million EVMs in use throughout the country, and it is impossible to get physical access to thousands of EVMs at poll time to affect election outcome. Every microchip has an identification number embedded into memory and the producers have their digital signatures on them. So, the question of their replacement does not arise at all because microchips are subjected to functional tests with regard to the software. Any attempt to replace microchip is detectable and can make EVM inoperative. Thus, both changing existing program or introducing new one are detectable making EVM inoperative.
The voting data is recorded on a simple imported chip which has a small and simple software that is burnt directly onto the chip itself and each vote as it is cast is recorded directly on the chip. The machines are so robust that unless the chips themselves get destroyed the data can be recovered even if the batteries die out or even if the power is accidentally cut off.
The chip fabricator has no idea where the chip will be ultimately used from Gandhinagar to Guwahati. There is a double randomisation process which makes it impossible for any person to know which machine will be used in what constituency, this is done to safeguard that machines are not pre-programmed to cast ballots in favour of a particular candidate. EVMs are randomised by computer software twice. Once for allocation of machines to assembly constituencies and second to polling stations in the presence of candidates’, this means no one really knows which machine would go to what location and hence pre-programming can be ruled out as a way of tampering. Even the final placement of the list of candidates on the balloting unit is not known till the last day of withdrawal of nomination before elections, so tampering with machines is virtually an impossible task. The candidate names are placed in an alphabetical order giving it even more variability. On counting day the machines are removed from the strong room where they are kept under twenty four hour armed guard and the votes polled are displayed sequentially in the presence of the observers of candidates.
Certain additional features were introduced in 2006 in ECI-EVMs such as dynamic coding between Ballot Unit (BU) and Control Unit (CU), installation of real time clock, installation of full display system and date and time stamping of every key-pressing in EVM. Technical Evaluation Committee in 2006 has concluded that any tampering of CU by coded signals by wireless or outside or Bluetooth or WiFi is ruled out as CU does not have high frequency receiver and data decoder. CU accepts only specially encrypted and dynamically coded data from BU. Data from any outside source cannot be accepted by CU.
- What are the latest technological features to make ECI-EVMs tamper proof?
On the recommendations of the Technical Evaluation Committee in 2006, M2 model of EVMs produced after 2006 and up-to 2012 incorporated dynamic coding of key codes thereby enabling transfer of the key press message from Ballot Unit (BUs) to Control Unit (CUs), in an encrypted form as an additional security feature. It also contains Real time setting of each key press so that sequencing of key presses including so called malicious sequenced key presses can be detected and wrapped. The ECI-EVMs use some of the most sophisticated technological features like one time programmable (OTP) microcontrollers, dynamic coding of key codes, date and time stamping of each and every key press, advanced encryption technology and EVM-tracking software to handle EVM logistics, among others to make the machine 100% tamper proof. In addition to these, new model M3 EVMs also have tamper detection and self-diagnostics as added features. The new M3 EVM machines have Tamper Detection to make an EVM inoperative the moment anyone tries to open the machine. There is also a Self-diagnostic feature to check the EVM fully, every time it is switched on to detect any changes in its hardware or software. Since, software is based on OTP the program cannot be altered, re-written or Re-read. Thus, making EVM tamper proof. If anyone makes tamper attempt, the machine will become inoperative.
- Why have Developed Nations like the US and European Union not adopted EVMs and some have discontinued?
Some countries have experimented with electronic voting in the past. The problem faced with the machines in these countries was that they were computer controlled and connected to the network, which in turn, made them prone to hacking and hence totally defeating the purpose. Moreover, there were not adequate security measures and safeguards in their corresponding laws regulations for security, safety and protection. In some countries, Courts struck down the use of EVMs on legal grounds only. Indian EVM is stand-alone whereas, USA, The Netherlands, Ireland & Germany had direct recording machines. India has introduced paper audit trail, though partly. Others did not have audit trail. Source code is closed during polling in all of the above countries. India also has closed source burnt into memory and is OTP. Indian EVMs are stand-alone devices not connected to any network, thus making it impossible for anyone to tamper with over 1.4 million machines in India individually. EVMs are most suited for India, looking at the country’s past poll violence and other electoral malpractices like rigging, booth capturing etc. during the polls.
Contrary argument:
It is true that ECI’s (paperless) EVMs are stand-alone, non-networked machines that are not connected to the Internet at any point of time and cannot therefore be hacked. But then, the paperless EVMs (or DREs) used all over the world are also “stand-alone” machines like Indian EVMs and are not part of any network though they may differ in certain other features. As German software expert Dr.Ulrich Weisner, who won the case against EVMs in Germany leading to their ban, observed:
“(EVMs)…banned in the Netherlands, Ireland and Germany are not networked…they were similar to the Indian EVMs and worked stand-alone with no connection to Internet or other networks during the election and counting phase. The lack of the network connection was one of the (invalid) reasons given by the vendor and by authorities in the three countries why the machines could not be hacked. The vendor also claimed that his devices were not real computers but ‘special purpose devices’ which were designed to only count votes and could not be used for any other purpose….It is common sense that someone who has sufficient access to open the Indian EVMs and replace the software or hardware can implement virtually any functionality, including vote stealing functionality, that is only activated under certain circumstances and would not be spotted in tests.”
_____
Flip side of EVMs:
The ECI is largely correct when it claims that the software (‘firmware’) of its EVMs cannot be manipulated in any manner. The greater the lines of code, the greater the scope for manipulation. The software of Indian EVMs is minimal, and it is One Time Programmable (OTP) that is ‘burned’ into the EVM’s CPU and cannot be re-written after manufacture. But this design also has certain disadvantages.
The flip side of the minimalist software is that it does not attempt to cryptographically protect the voting data stored in the electronic memory of the EVM’s Control Unit which are therefore unsecured. Even though some of the world’s best brains develop the software of Microsoft, Apple and Google, there are still several bugs and security issues in their software which are corrected (and new features added) by software updates that are automatically downloaded via the Internet and installed. The flip side of OTP software and EVMs not being part of any network including the internet is that bugs and security issues cannot be fixed and new features cannot be added until a new generation of EVMs is developed. These bugs may cause occasional (non-malicious) equipment malfunction such as flipping of votes, loss of votes, wrong totalling etc. which can change election outcomes just as EVM tampering can and which cannot be detected and corrected without VVPAT.
Attackers might try to substitute look-alike CPUs containing software that counts the votes dishonestly. Other than the firmware, the CPUs are a commodity part, so obtaining and programming identical hardware would be straightforward. The EVM designers could have made such attacks more difficult by building a cryptographic mechanism for identifying the original CPUs such as a challenge-response protocol based on a secret contained in the original firmware.
Is this EVM fraud?
Despite claims to the contrary by the Election Commission of India (ECI), a concrete instance of an electronic voting machine (EVM) “malfunction” in Maharashtra has been conclusively established, information obtained under RTI revealed. The “EVM fraud” concerns the recently held elections to Buldhana Zilla Parishad from Lonar, at a polling station in Sultanpur village of the district, said RTI activist Anil Galgali. “Everytime the voter pressed a symbol of Coconut, allotted to a candidate, the LED lamp of the Bharatiya Janata Party (BJP)’s Lotus used to flash. This was reported to the District Collector by the Returning Officer (RO) in his inquiry report and furnished under an RTI query. The election was cancelled in that booth after the reports of various election officials were sent to the Collector, the polling station was closed, the “malfunctioning” machine was sealed and a standby unit was put into operation. This case purports to be an ‘EVM fraud’. It was brought to notice by a voter, confirmed by many other voters, the RO and other officials also reconfirmed it and sent a report to the Collector.
My view:
The above mentioned purported EVM fraud was not deliberate fraud but inadvertent EVM malfunction; the equipment malfunction can cause flipping of votes, loss of votes, wrong totaling just as EVM tampering can. The sensors in touch screen devices can be knocked out of alignment by shock and vibration that may occur during transport and such touch screen machines can misinterpret a voter’s intent. Computer errors and malfunctions are possible and should not be seen as tampering or rigging. To alter election outcome by EVM fraud, you need to have similar flipping of votes in hundreds of EVM machines simultaneously at the time of poll. Out of thousands of EVM, if one EVM shows flipping of vote, loss of votes or wrong totalling, it could be machine failure rather than deliberate tampering by humans. Of course, such malfunction should be prevented or corrected before polling, and best way to confirm voter’s intent is by VVPAT. Also, there should be a cryptographic mechanism for identifying the original CPUs and cryptographic protection of stored voting data.
______
______
Prototyping of Indian Electronic Voting Machine, 2017 paper:
-A step towards ASIC (Application-Specific Integrated Circuit) in voting:
In this paper the Indian Electronic Voting Machine’s Protocol for voting is implemented on a field programmable gate array. The ASIC based design is known to be faster than a microcontroller-based design. Furthermore the use of an ASIC based design will make the Electronic Voting Machine a more reliable and tamper resistant machine. The new Voter-verified paper audit trail (VVPAT) system could also be interfaced with the ASIC based design. The protocol of Indian Electronic Voting Machine has been successfully implemented on a Basys 2 board using Verilog HDL. The FPGA based implementation gets half the job done for ASIC based EVM. The tool used for simulation and implementation is Xilinx ISE Design Suite with ISim as a Simulator.
_____
Mobile voting in India:
Many Indian leaders have questioned EVM; they are asking Election Commission to revert to Paper Ballot. Nobody is stating how the paper ballot is better than EVM. Mobile voting is several generations advanced technology over EVMs (e-Voting) and paper ballot. Right2Vote Infotech Private Limited has built the most advanced and ‘made for India’ Mobile Verified Voting Platform. The platform uses Aadhaar for verification. This is India’s opportunity to jump directly from EVMs to Mobile Voting.
- mVoting completely eliminates the need for setting up booths across the country.
- A voter can vote from anywhere directly from his mobile.
- This is very useful specially for NRIs, in-country migrants, college students, traveling professionals, married females and others who are located at a place other than their city of registration.
- This will ensure much higher voter turnout.
- Aadhaar based mVerification (Mobile Verification) ensures better verification without any human intervention.
- Aadhaar also provides a universal government database and eliminates the requirement of each central and state Election Commission to maintain their voter database.
- It also eliminates the requirement from a citizen to register separately for voter ID card.
______
______
Pros and cons of electronic voting:
_
Pros of Electronic Voting:
- Voter verified paper audit trails.
This component of the system ensures accurate casting, tabulation, and reporting of all votes. It allows voters to verify the accuracy of their votes as well as provides election authorities with a hardcopy of electorate’s choices which can be used for recounting votes when election results are questioned or when the need to manually count the votes arises.
- Faster results can build trust.
For large countries where population is widely dispersed, such as Brazil, India and the Philippines, the faster the votes are counted, the better. Faster results mean that people can get the results of the election within hours. This can help build their confidence on the reliability of the election as a result.
- Increase voter turnout.
The introduction of electronic voting machines has led to increase in voter turnout in many countries, like the Philippines which recent election held on May 9, 2016 recorded a historic 81.62% voter turnout.
- Reduce human error.
Manually tallying votes can result to human error. Electronic voting machines eliminated this problem by. They have the process auditable, transparent and secure.
- Reduce invalid and bogus votes.
Clear user guidance prevents formal errors such as illegible answers, missing signatures, incorrectly completed forms or invalid lists in the voting and election process. Bogus voting has been greatly reduced by the use of EVMs.
- E-voting is secure.
Votes are only transmitted and saved in encrypted and anonymized form. Sophisticated algorithms prevent votes from being manipulated without being detected.
- Accessibility.
It is argued that e-voting is more accessible than paper voting for the visual impaired. They can bring headphones and the buttons can be given tactile feedback. People with disabilities can vote or take part in elections online without the help of a third party. Swiss citizens living both in Switzerland and abroad can participate in votes and elections irrespective of their place of residence.
_
Figure below shows strengths of electronic voting:
________
Cons of electronic voting:
All fully-electronic (touch screen, DRE, internet) voting systems are subject to the limitations and risks of computer technology. This includes the inability to detect the presence of hardware and/or software that could be used, deliberately or inadvertently, to alter election outcomes. According to Rebecca Mercuri, PhD, president, Notable Software, democratic elections require independent verification that all balloting choices have been recorded as intended and vote totals have been reliably and indisputably created from the same material examined by the voters.
- Manufacturers’ political ties may negatively affect electorates’ confidence on the election results.
While vendors’ non-partisanship is assured, their connection to a certain politician or political party may erode people’s confidence in the election results.
- Malicious software programming.
The voting machine’s code can be secretly altered, and testing may not detect them if the malicious codes were intentionally introduced and concealed. Any computer software is basically generated from software programming and coding. And all these software could be tampered with by a computer programmer who knows the source code. Testing electronic voting systems for security problems, especially if they were intentionally introduced and concealed, is basically impossible. If malicious coding is inserted by programmers into commercial software that are triggered by obscure combinations of commands and keystrokes via the computer keyboard, then election results can change completely.
- Scalability of attacks.
It is easier to do large scale attacks, because often the same systems and software is being used across a country. In order to influence paper voting counts, an attacker will have to manipulate many different polling stations. This also brings us to the amount of people committing fraud: for e-voting fraud, one or a small group of attackers may be able to change the outcome of an election, while when considering paper elections, in general a larger group is needed.
- Less transparency.
The e-voting process is a lot less transparent, especially for non-technical people. Advanced knowledge of cryptography is required for people to be able to prove that their vote was taken into account in the election results, and that all the votes were counted correctly. Only few researchers will comprehend this, while the rest of the population will have to trust a system they cannot understand.
- Usage on untrusted and unmanaged client systems.
I-voting solutions generally assume that the client systems can be trusted. This assumption does not hold, since many home computers are unsafe. For example, existing botnets could have a significant impact on election results.
- Vulnerability to hacking.
According to the Congressional Research Service of Election Reform and Electronic Voting Systems, vendors and election jurisdictions generally state that they do not transmit election results from precincts via the internet, but they may transmit them via a direct modem connection or Virtual Private Network (VPN). However, even this approach may be subject to attack via the internet, especially if encryption and verification are not sufficient. That is because telephone transmission systems are themselves increasingly connected to the internet and computers to which the receiving server may be connected, such as through a local area network (LAN), may have internet connections. In other words although election results are not transmitted through the internet to avoid online hackers, transmission via direct modem is not guaranteed safe either, especially when encryption and verification systems are not sufficient because telephone transmission systems themselves are connected to the internet.
- Susceptibility to fraud.
Fraud comes in degrees and increments. A malicious voting system created and distributed by one vendor to hundreds of thousands of polling booths, can systematically falsify millions of votes. Although some may believe that tampering with an electronic voting machine is extremely hard to do, computer scientists have tampered with machines to prove that it is quite easily done. However, if people have access to the machines, and know how to work them, they can take the memory card out of the machine, which stores the votes, and in place they put their own memory card with a virus that can tamper with the votes. Stuffing a ballot box works at a retail level. A tamperer, however malicious and skilled, can stuff only as many ballots as might plausibly be cast at the polling place, but a faulty and corrupted voting system (malicious DRE software) could affect far more votes.
- Accuracy in capturing voters’ intent:
If a touch screen is used in the elections, the sensors in touch screen devices can be knocked out of alignment by shock and vibration that may occur during transport. Unless these sensors are realigned at the polling place prior to the start of voting, touch screen machines can misinterpret a voter’s intent. For example, a voter might touch the part of the screen identified with candidate X, but candidate Y’s would light up instead.
- Physical security of machines.
Regarding physical hardware controls, many of the DRE (direct recording electronic voting machine) models under examination contained weaknesses in controls designed to protect the system. According to the USA Government Accountability office, all the locks on a particular DRE model were easily picked, and were all controlled by the same keys. Also a particular model of DRE was linked together with others to form a rudimentary network. If one of these machines were accidentally or intentionally unplugged from the others, voting functions on the other machines in the network would be disrupted. In addition, reviewers found that switches used to turn a DRE system on or off, as well as those used to close the polls on a particular DRE terminal, were not protected.
- Secure storage of cast votes.
The votes that are cast using the electronic voting machines, are stored in a safe storage or space in the
computer machine memory. But, Doug Jones, PhD, Professor of Computer Science at University of Iowa explained in his book, Secure Electronic Voting, ‘For over a decade, all direct recording electronic machines have been required to contain redundant storage, but this redundant storage is not an independent record of the votes, because it is created by the same software that created the original record. As a result, the multiple files are of limited use to check the correctness of the software.’
- Errors in internet voting:
Recently endorsing a wider implementation of the internet voting system, the NSW Electoral Commission claimed it would “reduce systemic errors in current voting processes”, including informal votes, lost ballot papers and transposition and counting errors. While it was well-received by eligible voters, 43 of around 43,000 votes cast via iVote were recorded by the system as ‘N’ “due to a javascript error”. That represents an error rate of 0.1 per cent, the same rate as the recent WA Senate lost ballot fiasco, where 1370 votes were lost in a state of 1.4 million enrolled voters. “NSW iVote had about the same failure rate as Western Australia’s but it didn’t get anywhere as much attention as the WA vote because the [NSW] election was a landslide,” Vanessa Teague, a cryptographer at the University of Melbourne says. “This assumption that persists that computers will solve either the accidental error problem or the deliberate manipulation problem is completely untrue.”
_
Figure below shows weaknesses of electronic voting:
______
______
Impact of electronic voting:
_____
Impact on voting turnout:
One of the core arguments in support of electronic voting is to increase democratic participation. This is a noble pursuit and an aim that should be encouraged, but when e-voting has been trialed, it has not delivered that outcome. A 2016 study of online voting in two Swiss cantons found that it had no effect on turnout. A paper on “remote electronic voting and turnout in the Estonian 2007 parliamentary elections” showed that rather than eliminating inequalities, e-voting might have enhanced the digital divide between higher and lower socioeconomic classes. People who lived greater distances from polling areas voted at higher levels with this service now available. The 2007 Estonian elections yielded a higher voter turnout from those who lived in higher income regions and who received formal education. Norway ran electronic voting trials in 2011. Research was conducted looking at the hard numbers of voter turnout in the trials areas, and also the experience of voters in those trials. Internet voting did not have a significant impact on turnout. The vast majority of those who voted online would have voted anyway. Analysis of Estonia’s eight elections since 2005 where electronic voting has been available show that electronic voting has not attracted a new demographic to vote. A 2018 study published by Auckland University of Technology said online voting was “superficially attractive” but international evidence suggested it was not a silver bullet for reversing declining voter turnout. Elections in Switzerland and Belgium suggested online voting could have a “novelty effect” that gave a short-term boost to voter turnout, but evidence of a wider impact on voter turnout was “inconsistent”.
The distinction – why people vote not how people vote – is what makes all the difference. It should be remembered that Scotland’s independence referendum had the highest turnout of any UK election or referendum since universal suffrage was reached. That wasn’t because there was a new kind of method to vote, it was everything else: the significance of the vote, the closeness of the vote, and the nature of the debate having a relevance to people across Scotland.
________
Impact on election outcomes:
The use of electronic voting in elections remains a contentious issue. A 2017 study of Brazil found no systematic difference in vote choices between online and offline electorates. Some countries such as Netherlands and Germany have stopped using it after it was shown to be unreliable, while the Indian Election commission recommends it. The involvement of numerous stakeholders including companies that manufacture these machines as well as political parties that stand to gain from rigging complicates this further. It has further been argued political parties that have more support from the less fortunate—who are unfamiliar with the Internet—may suffer in the elections due to e-voting, which tends to increase voting in the upper/middle class. It is unsure as to whether narrowing the digital divide would promote equal voting opportunities for people across various social, economic and ethnic backgrounds. A group of researchers studying the recent Estonian elections describe massive operational lapses in security from transferring election results on personal thumb drives to posting network credentials on the wall in view of the public. The researchers concluded that these systems are insecure in their current implementation, and due to the rise of nation state interest in influencing elections, should be discontinued.
_
The Impact of Electronic Voting Machines on Electoral Frauds, Democracy, and Development, 2017 study:
Free and fair elections are cornerstones of democracy. In India, electronic voting machines (EVMs) were introduced with the objective of reducing electoral fraud. Authors exploit the phased roll-out of the EVMs in state assembly elections to study its impact on electoral fraud, democracy, and development. Their main findings are: (i) Introductions of EVMs led to a significant decline in electoral frauds, particularly in politically sensitive states which were subjected to frequent re-polls due to electoral rigging. (ii) It strengthened the weaker and the vulnerable sections of the society (women and the scheduled castes and tribe) who were now more likely to cast their vote. (iii) It made the electoral process more competitive whereby the winning margin and the vote share of the winning party declined. (iv) Using the luminosity data, they find that EVMs led to an increase in the provision of electricity. (v) Lastly, they find evidence that EVMs resulted in significant decline in crimes, such as murder and rape (violence against women).
Using Indian state assembly elections data from 1976 to 2007 and the variations in the use of EVMs, authors find that introduction of EVMs led to a significant decline in electoral fraud (Debnath, Kapoor and Ravi 2016). Constituencies where polling booths were captured and ballot boxes were stuffed resulted in higher voter turnout. After the introduction of EVMs, authors find that there was a significant decline in the total number of valid votes and voter turnout, particularly in those states that were prone to electoral fraud and where politicians faced criminal charges. On an average, their estimates suggest that the introduction of EVMs led to a 3.5% decline in voter turnout. However, these results can also be explained by voters’ negative preference toward EVMs. Voters may not like the EVMs, or it may cause the formation of long lines in polling booths due to the upper limit on the maximum votes per minute. To allay these concerns, they analyse the data from post-poll surveys conducted by an independent agency. Interestingly, they find that the ability of vulnerable citizens (illiterates, females, scheduled castes and tribes) to cast their vote improved significantly after the introduction of the EVMs. Furthermore, voters were less likely to report that they did not cast their vote due to fear of violence or vote capture, or were prevented from voting. Together these results provide strong evidence that EVMs resulted in a very significant decline in electoral fraud. Additionally, authors also find that EVMs led to a virtual elimination of rejected votes.
Voting technology susceptible to fraud may enable the political elite to capture the democratic process. EVMs in India strengthened electoral process making rigging difficult. Therefore, EVMs may affect political competitiveness reflected in the vote share of the incumbents and their chances of re-election. Authors find that overall incumbent party’s vote share decreases by 8.5% after the introduction of EVMs. This decline was much larger in the states where the ECI was more likely to issue re-poll orders. In the states of Andhra Pradesh, Bihar, and Jharkhand, where the re-poll orders were the highest in the 2004 Parliamentary elections, the incumbent party’s vote share declined by additional 9.8% and their re-election chances also plummeted. Electricity is one of the key issues during state elections, and its provision is primarily under state control. State-level corporations in India are the largest producers of electricity and are responsible for its transmission and distribution. Politicians wield considerable power over the state distribution companies and exercise them to control and manipulate provision of electricity to tilt election outcome in their favor (Baskaran et al. 2014). As a result provision of electricity improves with election cycles. Furthermore, transmission losses also peak just before the state assembly elections (Min and Golden 2014). Given the close relationship between elections and electricity, authors explore the relationship between use of EVMs and provision of electricity. Using annual satellite nighttime lights images for the period 1992-2007 and assembly constituency maps they construct a proxy measure of electricity provision. Their results suggest that constituencies using EVMs had better provision of electricity than their counterparts using paper ballots. Furthermore, provision of electricity improved over time, and the effect is strongest for the year just before the subsequent election. These results imply that the change in voting technology led to strengthening of the democracy by making elections more competitive, which in turn had an impact on promoting development by increased provision of electricity.
Maintaining law and order is a fundamental responsibility of the state. In a democracy, where political representatives are elected by the people, it is expected that these political representatives ensure the security of the citizens by maintaining law and order. However, in a rigged electoral system, politicians fail to provide security to common people because they depend on criminal elements in the electoral process. Politicians, therefore, end up supporting and protecting criminals instead of being able to prevent them. Given that introduction of EVMs in elections was motivated to reduce electoral fraud, authors find it critical to extend their analysis to the effect EVMs might have on law and order within a constituency. They assembled district level data on crimes from the National Crime Records Bureau. Their analysis suggests a very strong link between the introduction of EVMs and decline in crime. In particular, they find a significant decline in crime related to murder and rape. Furthermore, it is noteworthy that this effect is stronger in states where large proportion of legislators have criminal records.
__
Winners and Losers of the Ballot: Electronic vs. Traditional Paper Voting Systems in Brazil, a 2018 study:
What are the effects of voting technology on candidates’ vote shares?
Are the effects different for viable and nonviable candidates?
Put differently, are the consequences of voting technology different for candidates with and without the resources to be electorally competitive? Why?
This article leverages the gradual introduction of electronic voting in Brazil to address these questions. Before the introduction of electronic voting in 1998, Brazilian voters cast their votes with paper ballots. Under the traditional paper ballot system, they selected their preferred presidential and gubernatorial candidates from a predetermined list; voters were not required to write out manually the names or electoral numbers of their preferred candidates. Under this system, voters cast their votes using what we call information-inclusive ballots. However, with the introduction of electronic voting technologies, Brazilians were no longer presented with presidential and gubernatorial candidate options from which to choose. Instead, they were required to input the electoral number associated with their preferred candidate in an electronic machine. Thus, voters using electronic voting technologies to cast their votes used ballots that did not list the competing candidates. This study estimates the effects of voting technology on viable and nonviable candidates’ vote shares.
Many countries have adopted and experimented with different types of voting systems in recent years as more information has come to light about the functioning and effects of these systems. Electronic voting is one such system that has emerged as a consistent contender in debates over optimal voting systems (Katz et al. 2011). Proponents of electronic voting argue that it improves vote counting, decreases fraud, and facilitates the act of voting for voters. However, some studies suggest that achieving these objectives comes at the expense of electoral fairness and neutrality. This article profitably advances understanding of the effects of voting systems by studying the relationship between voting systems and viable and nonviable candidates’ vote shares. Authors exploited the causal leverage afforded by the gradual introduction of electronic voting in Brazil. They found that the type of voting system used has implications for viable and nonviable candidates’ vote shares and that electronic voting produces electorally biased results. Specifically, the shift away from traditional paper ballots and the introduction of electronic voting increased viable candidates’ vote shares and decreased nonviable candidates’ vote shares. Authors posit that this result can be attributed to disparities in viable and nonviable candidates’ abilities to effectively campaign and entrench their electoral numbers in the minds of voters. This study finds that the introduction of electronic voting concentrated vote shares among viable candidates and thus exhibited electoral bias. Authors posit that this result occurred because viable candidates were better able to communicate the information that electronic voters needed to cast valid ballots than were their nonviable counterparts.
______
______
Documented problems with electronic voting:
As older voting equipment has been replaced with newer electronic voting systems over the last few years, the debate has shifted from hanging chads and butterfly ballots to vulnerabilities associated with DREs. Problems with these devices in recent elections have arisen in various states. Additionally, questions are being raised about the security of DREs. Critics suggest that their use could compromise the integrity of the election process and that these devices need auditing mechanisms, such as receipt printers that would provide a paper audit trail and allow voters to confirm their choices. Among these critics are computer scientists, citizens groups, and legislators.
_____
Major Media Articles reveal Major Electronic Voting Machine Problems:
- MSNBC – A 2011 article titled “It only takes $26 to hack a voting machine” states, “Researchers from the Argonne National Laboratory in Illinois have developed a hack that, for about $26 and an 8th-grade science education, can remotely manipulate the electronic voting machines used by millions of voters all across the U.S. The electronic hacking tool consists of a $1.29 microprocessor and a circuit board that costs about $8. Together with the $15 remote control, which enabled the researchers to modify votes from up to a half-mile away, the whole hack runs about $26.”
- Christian Science Monitor – A 2015 article states, “Computer security experts have warned for years that some voting machines are vulnerable to attack. In Virginia, the state Board of Elections decided to impose an immediate ban on touchscreen voting machines used in 20 percent of the state’s precincts. When state auditors investigated [they found that] while using their smartphones, they were able to connect to the voting machines’ wireless network, which is used to tally votes. Other state investigators easily guessed the system’s passwords — in one case, it was ‘abcde’ — and were then able to change the vote counts remotely without detection.”
- Washington Post – An article titled “A Single Person Could Swing an Election” describes the test of a team of cybersecurity experts. The article states, “The experts … concluded in a report issued yesterday that it would take only one person, with a sophisticated technical knowledge and timely access to the software that runs the voting machines, to change the outcome.”
- Christian Science Monitor – An 2012 article is titled “Could e-voting machines in Election 2012 be hacked? Yes.” It shows how easy it continues to be for voting machines to be manipulated. The article states, “Rapid advances in the development of cyberweapons and malicious software mean that electronic-voting machines used in the 2012 election could be hacked, potentially tipping the presidential election or a number of other races. For a savvy hacker, the time and access needed to infect a machine is so small that it could be done while in a voting booth.”
- Miami Herald – An article titled “CIA expert: Electronic voting not secure” presents the troubling results of CIA cybersecurity expert Steve Stigall. “Computerized electoral systems can be manipulated at five stages, from altering voter registration lists to posting results. Stigall said voting equipment connected to the Internet could be hacked, and machines that weren’t connected could be compromised wirelessly. The [Election Assistance] Commission has been criticized for giving states more than $1 billion to buy electronic equipment without first setting performance standards. Numerous computer-security experts have concluded that U.S. systems can be hacked.”
- MSNBC – A 2009 MSNBC article describes five county officials, including the circuit court judge, the county clerk, and election officers, who were accused of blatant election corruption. “These alleged criminal actions affected the outcome of federal, local, and state primary and general elections in 2002, 2004, and 2006. Clay County Circuit Court Judge Russell Cletus Maricle, 65, and school superintendent Douglas C. Adams, 57… caused election officers to commit acts of extortion, mail fraud, and bribery. Clay County Clerk, Freddy Thompson, 45, allegedly … instructed officers how to change votes at the voting machine.”
- Six DRE units used in two North Carolina counties lost 436 ballots cast in early voting for the 2002 general election because of a software problem, according to a February 9, 2004, report in Wired News. The manufacturer said that problems with the firmware of its touchscreen machines led to the lost ballots. The state was trying out the machines in early voting to determine if it wanted to switch from the optical scan machines it already owned to the new touchscreen systems.
- According to a January 2004 report in Wired News, blank ballots were recorded for 134 voters who signed in and cast ballots in Broward County, Florida. These votes represented about 1.3 percent of the more than 10,000 people who voted in the race for a state house representative.
- USA Today reported that four California counties suffered from problems with DREs in a March 2004 election, including miscounted ballots, delayed polling place openings, and incorrect ballots. In San Diego County, about one-third of the county’s polling places did not open on time because of battery problems caused by a faulty power switch.
- In at least 20 states, according to the Associated Press, legislation has been introduced requiring a paper record of every vote cast. Following the problems in California, the California Secretary of State banned the use of more than 14,000 touchscreen DREs and conditionally decertified 28,000 others in 2004. According to a New York Times article, he also recommended that the state Attorney General consider taking civil and criminal action against the manufacturer for “fraudulent actions.” The decision followed the recommendations of the state’s Voting Systems and Procedures Panel, which urged the Secretary of State to prohibit the four counties that experienced difficulties from using their touchscreen units in the November 2004 election, according to an Associated Press article. The panel reported that the manufacturer did not obtain federal approval of the model used in the four affected counties and installed software that had not been approved by the Secretary of State. It also noted that problems with the systems prevented an unspecified number of voters from casting ballots.
_____
Computer scientists from Johns Hopkins and Rice Universities released a security analysis of software from a DRE of a major vendor, concluding that the code had serious security flaws that could permit tampering. Other computer scientists, while agreeing that the code contained security flaws, criticized the study for not recognizing how standard election procedures can mitigate these weaknesses. Following the Johns Hopkins and Rice study, Maryland contracted with both SAIC and RABA Technologies to study the same DRE equipment. The SAIC study found that the equipment, as implemented in Maryland, poses a security risk. Similarly, RABA identified vulnerabilities associated with the equipment. An earlier Caltech/MIT study noted that despite security strengths of the election process in the United States, current trends in electronic voting are weakening those strengths and introducing risks; according to this study, properly designed and implemented electronic voting systems could actually improve, rather than diminish, security. The Premier Election Solutions (formerly Diebold Election Systems) AccuVote-TSx voting system was studied by a group of Princeton University computer scientists in 2006. Their results showed that the AccuVote-TSx was insecure and could be “installed with vote-stealing software in under a minute.” The scientists also said that machines can transmit computer viruses from one to another during normal pre- and post-election activity.
______
Documented problems with electronic voting nation-wise:
- Australia
- iVote is a remote electronic voting system in New South Wales that allows eligible voters a chance to vote over the Internet. However, during the New South Wales state election in 2015, there were several reports that over 66,000 electronic votes could have been compromised. Although the iVote website is secure, security specialist believe that a third party website was able to attack the system. This was the first time a major vulnerability was discovered in the middle of an ongoing poll.
- Canada
- The New Democratic Party leadership election, 2012 was conducted partially online, with party members who were not in attendance at the convention hall able to cast their leadership vote online. However, for part of the day the online voting server was affected by a denial-of-service attack, delaying the completion and tabulation of results.
- In the 2018 Ontario municipal elections, over 150 municipalities in the Canadian province of Ontario conducted their elections primarily online, with physical polling stations either abandoned entirely or limited to only a few central polling stations for voters who could not or did not want to vote online. On election day, however, 51 of those municipalities, all of which had selected Dominion Voting Systems as their online voting contractor, were affected by a technical failure. According to Dominion, the company’s colocation center provider imposed a bandwidth cap, without authorization from or consultation with Dominion, due to the massive increase in voting traffic in the early evening, thus making it impossible for many voters to get through to the server between 5:00 and 7:30 p.m. All of the affected municipalities extended voting for at least a few hours to compensate for the outage; several, including Pembroke, Waterloo, Prince Edward County and Greater Sudbury, opted to extend voting for a full 24 hours into the evening of October 23.
- India
- In April 2017, Eighteen EVM machines in Dholpur, Rajasthan were found to be registering votes for the wrong person. Votes being given to one party were wrongly being registered for another political party, BJP instead.
- In the April 2017 elections in Bhind (Madhya Pradesh), electronic machines were found rigged, thus registering votes to the Bharatiya Janta Party (BJP) even when the voter voted for other parties. 18 officials were suspended due to this, however the results were not declared incorrect.
- Omesh Saigal, an IIT alumnus and IAS officer, demonstrated that the 2009 elections in India when Congress Party of India came back to power might be rigged. This forced the election commission to review the current EVMs.
- Finland
- In Finland, the Supreme Administrative Court declared invalid the results of a pilot electronic vote in three municipalities, and ordered a rerun of the municipal elections (Karkkila, Kauniainen and Vihti). The system had a usability problem where the messages were ambiguous on whether the vote had been cast. In a total of 232 cases (2% of votes), voters had logged in, selected their vote but not confirmed it, and left the booth; the votes were not recorded. Following the failure of the pilot election, the Finnish government has abandoned plans to continue electronic voting based on voting machines. In the memo it was concluded, that the voting machine is not developed any more, and Finnish government will follow the development of different electronic voting systems worldwide.
- Netherlands
- On October 30, 2006, the Dutch Minister of the Interior withdrew the license of 1187 voting machines from manufacturer Sdu NV, about 10% of the total number to be used, because it was proven by the General Intelligence and Security Service that one could eavesdrop on voting from up to 40 meters using Van Eck phreaking. National elections are to be held 24 days after this decision. The decision was forced by the Dutch grass roots organisation Wij vertrouwen stemcomputers niet (“We do not trust voting computers”).
- United States
- Fairfax County, Virginia, November 4, 2003. Some voters complained that they would cast their vote for a particular candidate and the indicator of that vote would go off shortly after.
- In Napa County, California, March 2, 2004, an improperly calibrated marksense scanner overlooked 6,692 absentee ballot votes.
- Instances of faulty technology and security issues surrounding these machines were documented on August 1, 2001, in the Brennan Center at New York University Law School. NY University Law School released a report with more than 60 examples of e-voting machine failures in 26 states in 2004 and 2006. Examples included Spanish language ballots that were cast by voters but not counted in Sacramento in 2004.
- In 2010, graduate students from the University of Michigan hacked into the District of Columbia online voting systems during an online voting mock test run and changed all the cast ballots to cater to their preferred candidates. This voting system was being tested for military voters and overseas citizens, allowing them to vote on the Web, and was scheduled to run later that year. It only took the hackers, a team of computer scientists, thirty-six hours to find the list of the government’s passwords and break into the system.
Problems in the United States general elections, 2006:
- During early voting in Miami, Hollywood and Fort Lauderdale, Florida, in October 2006 three votes intended to be recorded for Democratic candidates were displaying as cast for Republican. Election officials attributed it to calibration errors in the touch screen of the voting system.
- In Pennsylvania, a computer programming error forced some to cast paper ballots. In Indiana, 175 precincts also resorted to paper. Counties in those states also extended poll hours to make up for delays.
- Cuyahoga County, Ohio: The Diebold computer server froze and stopped counting votes then the printers jammed so paper copies could not be retrieved for many votes and there was no way to be sure of the accuracy of the votes when the votes were being counted.
- Waldenburg, Arkansas: The touch screen computer tallied zero votes for one mayoral candidate who confirmed that he certainly voted for himself and therefore there would be a minimum of one vote; this is a case of disappearing votes on touchscreen machines.
- Sarasota, Florida: There was an 18,000-person “undervote” in a congressional election. The subsequent investigation found that the undervote was not caused by software error. Poor ballot design was widely acknowledged as the cause of the undervote.
2008 United States elections:
- Virginia, Tennessee, and Texas: Touch screen voting machines flipped votes in early voting trials.
- Humboldt County, California: A security flaw erased 197 votes from the computer database.
_____
_____
Why countries banned electronic voting:
_
It was supposed to be the most modern election in Africa. Kenyan authorities, hoping to avoid the chaos of the 2007 election, decided that this time in 2013 the country would use a tamper-proof, state-of-the-art electronic voting system where voter IDs would be checked on hand-held devices and results transmitted to Nairobi through text messages. But everything that could go wrong did. The biometric identification kits to scan people’s thumbs broke down; a server meant to take in results from 33,400 voting centers sent via SMS became overloaded; and some election operators forgot the passwords and PIN numbers for the software. Polling centers went back to hand counting ballots and results were delayed almost a week, until March 9 when Uhuru Kenyatta’s win was announced. And every day before that people feared a repeat of 2007 when results were delayed and violence erupted, killing 1,200 people. Kenya’s troubled electronic voting experiment is part of a strange dichotomy where electronic voting is on the way out in most Western countries, but taking hold in emerging economies, possibly to their detriment. In the US and Western Europe, more states have been opting out of electronic voting systems and returning to paper out of worries over the number of glitches, and the inability to verify that electronic votes or the software on machines have not been manipulated.
_
Here is a list of countries that have banned or monitored the use of DREs.
- Germany
The DREs have been prone to hacking and are declared as unfit for political use. In Germany, Electronic Voting Machines (DREs) have been termed as unconstitutional and has been banned. [vide infra]
- Netherlands
The Netherlands is another country that has questioned the use of DREs. The country banned the use of DREs stating that they lack transparency. This decision was taken by the Dutch council in 2008 after people questioned the authenticity of the voting machines. Dutch TV carried a story where one change the EPROM of the Nedap voting machine changed the output making people question its credibility.
- Ireland
Ireland spent millions of dollars on the installation of DREs and to use them during the political elections. However, after spending more than 51 million pounds for three years, Ireland went forwards and scrapped the electronic voting system citing it to lack of trust and transparency in the voting machine.
- England
England has had various pilots for the electronic voting system to be used. However, these pilots have never led to the use of DREs in the country. England is one of the few countries that has stayed away from the modern methods in political elections, and the government plans to continue on the same path. In January 2016, the UK Parliament revealed that it has no plans to introduce electronic voting for statutory elections, either using electronic voting in polling booths or remotely via the internet
- France
Electronic voting was used in a national presidential primary in 2007. While the country has chosen to vote via the internet, DREs have not been used in France. Elections in France utilised remote Internet voting for the first time in 2003, and this idea was made a custom in 2009 as people chose the internet voting system over paper.
- Italy
In 2006, Italy used Nedap Voting machines in the national elections. The pilot project involved 3000 electors and four polling stations. However, after the pilot project was completed, the country chose to go back to paper as it is easy to manage and cheaper.
While these countries have banned or refrained from using DREs, there are others who have taken a systematic approach and backed the use of DREs with paper ballots. In various parts of the United States of America as well as in Venezuela DREs are used on a large scale but are backed by paper trails of the votes. This simple step helps the government to regularize and check the authenticity of votes and avoid any discrepancies.
____
Why Electronic Voting Banned in Germany in 2009?
The German Constitutional Court upheld the argument that the use of the NEDAP voting machines was unconstitutional. The Court noted that, under the constitution, elections are required to be public in nature and that all essential steps of an election are subject to the possibility of public scrutiny unless other constitutional interests justify an exception. The basis for the German court ruling was the principle that “all essential steps in the elections are subject to public examinability.” In a republic, elections are a matter for the entire people and a joint concern of all citizens. Consequently, the monitoring of the election procedure must also be a matter for and a task of the citizen. Each citizen must be able to comprehend and verify the central steps in the elections. When electronic voting machines are deployed, it must be possible for the citizen to check the essential steps in the election act and in the ascertainment of the results reliably and without special expert knowledge. In other words, electronic voting machines are computers that, like all computers, are essentially opaque to citizens who do not have “special expert knowledge” about computers. And any kind of computing system would fail the basic test of whether any ordinary citizen (without expert knowledge) could examine the system to see whether it is operating correctly.
______
______
Research on electronic voting:
_
Bingo Voting: Secure and Coercion-Free Voting Using a Trusted Random Number Generator: a 2007 paper:
It is debatable if current direct-recording electronic voting machines can sufficiently be trusted for a use in elections. Reports about malfunctions and possible ways of manipulation abound. Voting schemes have to fulfill seemingly contradictory requirements: On one hand the election process should be verifiable to prevent electoral fraud and on the other hand each vote should be deniable to avoid coercion and vote buying. This work presents a new verifiable and coercion-free voting scheme Bingo Voting, which is based on a trusted random number generator.
Bingo voting is an electronic voting scheme for transparent, secure, end-to-end auditable elections. It was introduced in 2007 by Jens-Matthias Bohli, Jörn Müller-Quade, and Stefan Röhrich at the Institute of Cryptography and Security (IKS) of the Karlsruhe Institute of Technology (KIT). Random numbers are used to record votes. Central to the scheme is the use of trusted random number generating devices in the voting booths alongside the electronic voting machines. Also crucial are its paper receipts which, while not revealing how a vote was cast, and so inhibiting vote buying and intimidation, still allow voters to check that their vote was correctly counted. The scheme allows the correctness of an election result to be verifiably proved relying only on the integrity of the in-booth random number generators (hence “trusted”); the proof of correctness does not rely on, still less need to prove, the integrity of the electronic voting machines themselves. No particular demands are placed on voters, and no ballot papers are used. One special requirement, however, to prevent fraudulent challenges to the election result, is the use of unforgeable paper for the receipts.
__
Electronic Voting Protocol Using Identity-Based Cryptography, a 2015 paper:
Electronic voting protocols proposed to date meet their properties based on Public Key Cryptography (PKC), which offers high flexibility through key agreement protocols and authentication mechanisms. However, when PKC is used, it is necessary to implement Certification Authority (CA) to provide certificates which bind public keys to entities and enable verification of such public key bindings. Consequently, the components of the protocol increase notably. An alternative is to use Identity-Based Encryption (IBE). With this kind of cryptography, it is possible to have all the benefits offered by PKC, without neither the need of certificates nor all the core components of a Public Key Infrastructure (PKI). Considering the aforementioned, in this paper authors propose an electronic voting protocol, which meets the privacy and robustness properties by using bilinear maps.
In this paper authors present a protocol that is based on blind signatures and secret sharing techniques, using blind signatures and encryption schemes as the main construction blocks. The main difference with protocols proposed to date is that its functionality is based on bilinear maps and secret sharing schemes, which are used jointly with their respective properties to meet expectations of privacy and robustness. Bilinear maps develop high cost operations which can be addressed by using cryptoaccelerators to efficiently develop this sort of operations. As a result, authors eliminate the need of implementing a Public Key Infrastructure (PKI). In addition the proposed protocol is based on the difficulty of solving the Computational Diffie-Hellman Problem (CDHP) and the Bilinear Diffie-Hellman Problem (BDHP); due to its construction it can be found on supersingular elliptic curves or hyperelliptic curves over finite fields; as a consequence no algorithm exists as yet capable of solving such problems in polynomial time.
According to what was mentioned above, it is easy to see that proposed protocol highlights the balance between security and efficiency. In other words, from the security point of view, the proposed protocol is based on the difficulty of solving the Computational Diffie-Hellman Problem (CDHP) and the Bilinear Diffie-Hellman Problem (BDHP). From the efficiency point of view, authors eliminate the need of implementing the components of a Public Key Infrastructure (PKI) and leave as consideration the development of cryptographic operations by using cryptoaccelerators.
The protocol presented here could be used, for instance, in a voting system based on Direct Recording Electronic (DRE) systems, which provides authentication of the voter’s identity based on official documents presented to the electoral authority. Moreover, the voter’s receipt could be used to meet requirements of verifiability and accuracy. Thus, in order to verify if the votes were recorded and counted, the receipt should appear on a bulletin board in which it is displayed together with the final tally. If any voter does not find his/her hash value on the bulletin board, he/she can register a complaint with election officials.
_
An approach to Electronic Voting System using UIDAI: a 2014 paper:
Unique Identification Authority of India (UIDAI) is a government agency in New Delhi that serves as the issuing authority for Aadhaar unique identification numbers (UIDs) and cards. Casting a vote and counting votes both by electronic means constitutes Electronic Voting System. Creating an electronic voting system requires the use of robust voting mechanism that is relatively complex to design. In this paper authors present a concept of electronic voting system which ensures authentication, authorization and accounting. Approach collects information from UIDAI and uses this information in validating electorate, casting electorate vote during electronic voting procedure. Only necessary information is collected from UIDAI that has some significance in authentication, authorization and accounting. The approach addresses issues such as voter frauds, voting accuracy, reliable voting, time delays, increasing electorate participation providing user friendly interface etc., thus providing a framework for fair elections.
_
Biometrically secured electronic voting machine, a 2017 paper:
Voting is one of the fundamental rights of every citizen of a democratic country. By utilizing the right of the voting, people elect their most suitable leader who will lead them. In this modern era where technology is being used in every aspect of life, election is a place to apply the best technology. Because biometric identifiers cannot be easily misplaced, forged, or shared, they are considered more reliable for person recognition than traditional token or knowledge-based methods. So, the Electronic voting system has to be improved based on the current technologies viz., biometric system. In this project, authors have developed a system which will be suitable for elections in countries like Bangladesh. The usual system for voting in Bangladesh is ballot paper-based voting system, where voting is sometimes unfair. In this proposed system authors have used Arduino and Finger Print Scanner that can identify each voter, count votes and can prevent fake votes. The proposed system is more digital, technology-based and secured system.
_
A Novel Hybrid Biometric Electronic Voting System: Integrating Finger Print and Face Recognition, a 2018 paper:
A novel hybrid design based electronic voting system is proposed, implemented and analyzed. The proposed system uses two voter verification techniques to give better results in comparison to single identification based systems. Finger print and facial recognition based methods are used for voter identification. Cross verification of a voter during an election process provides better accuracy than single parameter identification method. The facial recognition system uses Viola-Jones algorithm along with rectangular Haar feature selection method for detection and extraction of features to develop a biometric template and for feature extraction during the voting process. Cascaded machine learning based classifiers are used for comparing the features for identity verification using GPCA (Generalized Principle Component Analysis) and K-NN (K-Nearest Neighbor). It is accomplished through comparing the Eigen-vectors of the extracted features with the biometric template pre-stored in the election regulatory body database. The results of the proposed system show that the proposed cascaded design-based system performs better than the systems using other classifiers or separate schemes i.e. facial or finger print based schemes. The proposed system will be highly useful for real time applications due to the reason that it has 91% accuracy under nominal light in terms of facial recognition. with bags of paper votes. The central station compiles and publishes the names of winners and losers through television and radio stations. This method is useful only if the whole process is completed in a transparent way. However, there are some drawbacks to this system. These include higher expenses, longer time to complete the voting process, fraudulent practices by the authorities administering elections as well as malpractices by the voters. These challenges result in manipulated election results.
_
Secure voting system through SMS and using smart phone application, a 2017 paper:
Mobile voting system is used to cast their votes in secure manner. Previously the votes were casted through the traditional methods of polling booths, punch cards, lever voting, optical voting machine, which are now replaced through some electronic mediums. All of these consumes more time to cast their votes. The proposed system is developed to select their candidate through smart phone application. This process consists of three steps: online registration of voter, vote casting of voter and display of results, through the concept of SMS (short messaging service). It provides more efficiency for voters to cast their vote from anywhere, at any time through internet. The important aspect of this is to provide more security till the core, since every vote counts and each of the votes are to be remained confidential. This prevents voters to cast their vote more than once with the use of OTP (one-time password) for every sign in and login. It also reduces the paper work and eliminates the manual counting process. Here the security is provided through the RSA encryption algorithm.
_
An RFID based smart EVM system for reducing electoral frauds:
This paper describes the design, operation of smart EVM to improve the election process by avoiding the electoral fraud and to ensure safety, security, reliability, guarantee and transparency and smooth conduct of elections in the country as the voting is of crucial importance in the society where people determine its government. This paper talks about an innovative approach for voting process where the device communicates with the RFID tag which is embed in the voter ID card. When the voter scans his card, his/her data is being checked in the system after which the system generates an OTP and sends the message to the user’s mobile (voter). The voter inserts the password and if the password is confirmed then the person is allowed to vote and this process is repeated for every person.
_____
The Need for an Ecological View in E-Voting Research:
Khan et al. suggested that the success of computer-based systems implementations should be attributed to the simultaneous configuration of technical, organizational, and social aspects of the systems. The technical aspect concerns how technology and business processes transform inputs to outputs; while the organizational and social system emphasizes the needs for understanding people’s attitudes, skills and values, as well as the relationships among them within an organizational structure. This conception sees information technology not as a mere tool which is readily, un-problematically applicable in any given context for any specific purpose, but rather as a complex socio-technical agent whose correlative interactions with other social agents are significant in order to understand how the technology works.
Technology has only a small effect in shaping human intention and choices, hence the impacts associated with e-voting initiatives, for instance, can be attributed to human agency shaped by social context. It does not mean that technical solutions for e-voting systems can be ignored, rather the emphasis is on how social and organizational aspects should be seen just as decisive, if not more, to e-voting success. It has been reported that the use of technology in elections might have failed to improve public participation due to socio-technical gaps.
Al Shammari et al. identified three dimensions of disparities lingering in e-voting implementations. First is the technological gap caused by incompatibility between systems components – both hardware and software. Next is the social gap occurring between social policies and human behavior which represents moral discrepancies among users, between users and social values, and between democratic culture and election protocols. E-voting indeed conveys different significance for different actors, and their use of the technology may depart from different agendas. The last dimension is the socio-technical gap caused by disparities between social and computer policies. For e-voting systems therefore, the social world and the technology used therein cannot be seen as separate, rather, they co-constitute each other.
The causes of failures to implement electoral information technology are associated not only with the technological aspects of the systems, but also with the organizational context in which they are used. Although one of the main objectives of utilizing technology in elections is to improve democracy through increases in voter turnouts, in practice e-voting is seldom seen as a social utility. Adoptions are often driven simply by over-acknowledgement of technological possibilities and for the sake of bureaucratic convenience, as a result of unsatisfactory experiences from the use of traditional paper-based systems. In some cases, failures may originate from the scarcity of resources and the overreliance of governments on the private sector due to the lack of IT expertise.
The decision on whether or not a country should implement e-voting can never be detached from the political implications that precede and may follow. The question is what drives governments to initiate the adoption of a system that arguably is not better than the one it replaces? What motivates government to tolerate “social trade-offs” to ensure public acceptance of the technology even though it may put democratic practices in the hands of near-monopolist private sectors? E-voting, therefore, needs to be seen from a broader, ecological point-of-view that goes beyond the technology and includes social and organizational perspectives and interrelationships amongst them.
______
______
Discussion:
_
Electronic voting and democracy:
Literature has shown that countries with strong democratic traditions, such as the United States and Canada, are not yet using electronic voting systems intensively, due to the concern for and emphasis on security. It has revealed that there is no such thing as an error-free computer system, let alone an electronic voting system, and that existing technology does not offer the conditions necessary for a reliable, accurate and secure electronic voting system. Literature has shown that countries with strong democratic traditions are not yet using electronic voting systems intensively, given citizens’ and policy makers’ concerns about the security of such systems. To date, commercially available technology requires an infrastructure that poses complex technical challenges for reliability and security. Despite our technological process, e-voting technology does not yet provide a completely “secure e-transaction environment”. Some authors claim that e-voting will never be error-free and that it is nice in theory, but that in practice, the risks are too large.
Given the lack of security of e-voting systems, what are the risks of e-voting to democracy when the systems are introduced? Can more fragile, less mature democracies such as those in Latin America, be reinforced and advanced with the adoption of e-voting systems? Indeed, what are the implications for emerging democracies when elections engage millions of poor people, many of whom live well-below the poverty line? What are the implications of this costly ‘technological imperative’ upon the policy priorities of their governments? The contradictions are apparent: most countries in the developed world have held off adopting e-voting systems given their concerns about security and their knowledge of the implications of insecure systems for democracy.
However, costly technological systems are being imposed on citizens in less developed countries, where questions about voting abnormalities can go far beyond the scandal of hanging or ‘dimpled’ chads discovered and heatedly contested in the 2000 Presidential Election in the United States. Which criteria or benefits justify a full-scale electronic election, when the costs – budgetary, democratic and other – are so high? What are the implications when a public network project is conceived and implemented in the interests of corporate actors without consideration for the needs and interests of millions of illiterate people unaccustomed to even traditional voting methods, let alone electronic systems? In what ways, if at all, might an e-voting strategy be conceived which serves the democratic vision of citizens in less developed countries? These and many other questions have not been posed, let alone addressed.
Democracy depends on healthy and educated citizenship; if technology can further policy objectives around education, health and well-being, then indeed, the investment in innovation can be defended in a less developed country. However, when a market-driven approach dominates, the adoption of technology for technology’s sake, without due consideration and strategic efforts to mitigate the foreseen and unintended side effects of technological adoption, then there is an obligation to question the motivation for such an initiative, to assess the implications of the adoption of technology, and to push for public dialogue about the relevance and appropriateness of the current course of action.
_______
Public Confidence in Electronic Voting Technologies:
Allowing domestic observation groups, political party agents, and the public to have access to the electoral process, including those aspects that are automated, is a critical means of promoting public confidence. In addition, it is often helpful for electoral management bodies and legislators to include all stakeholders (e.g., civil society organizations, political parties, and voters) in the selection and introduction of new electoral technologies. This should include training for voters, political party agents, domestic observers, and others on the technologies, covering how to use them and how to assess indications of possible technology failure.
- Accessibility
To ensure that voters are not disenfranchised by the introduction of electronic voting technologies, election management bodies should take steps to check that all qualified voters are able to cast their ballots. This includes those who are disabled, illiterate, or do not speak the majority language of the country. Observers should consider the provisions in place to protect the right of these voters to cast ballots, including ballot design (e.g., in minority languages) or availability of ballots in larger type sizes, the availability of electronic voting machines for disabled voters, and any provisions to ensure that illiterate or disabled voters are able to cast and verify their votes.
- Election Day Procedures
Electronic voting technologies should offer voters the same options as manual voting, including, but not limited to, casting blank ballots and cancelling their votes. If a voter verified paper trail (VVPT) is used, a voter should be able to cancel his or her vote should the paper receipt not reflect the ballot cast on the machine. Steps also should be taken by the electoral management body to ensure that the secrecy of the vote is protected, that a vote cannot be traced back to a specific voter, and that voters are not able to remove evidence of how they voted from the polling place.
- Contingency Planning
Election management bodies should have clear and consistent rules in place in case of machine failure, whether resulting from power outages or other issues. These rules should be clearly communicated to all poll workers and technicians as well as observers and party agents, and poll workers should receive training on what to do in such instances. Any machine failures should be clearly documented. Documented chain-of-custody procedures should be in place to ensure that machines are secure from tampering once removed from the polling station either at the end of polling or in case of machine failure. Any replacement equipment should be subject to the same testing and certification processes as equipment initially installed in the polling place.
- Ballot Counting and Recount and Complaint Procedures
The use of electronic voting technologies, particularly those that do not produce a VVPAT, poses unique challenges to the observation of ballot counting. Regardless of whether the machines produce a VVPAT, election results should be printed at the station level prior to transmission to the central tabulating computer, allowing the public and observers, at the very least, to conduct a comparative assessment of the results at the precinct level with the final official results. Specific procedures should be in place, and clearly conveyed to all stakeholders, for instances of discrepancies in the results, that is, when posted precinct-level results do not match final precinct results or when VVPT counts do not match the vote count produced by the machine. In addition, the grounds and procedures for a recount should be communicated to all stakeholders, including when a recount can be requested, who is responsible for the cost of the recount, whether the recount includes manually recounting paper ballot receipts and/or conducting a voting machine recount electronically, whether the results of a recount can be used as grounds for a legal challenge to the election results, and what constitutes the “ballot of record” in cases of discrepancy between electronic and paper results.
_
The Psychology of Electronic Voting:
The public must trust that elections are fairly conducted in order for a democratic government to be considered legitimate. If the public perceives elections to be unfair, the foundation of the government is weakened. Whether electronic voting systems are fair may not even matter; it is the public perception that is crucial. At the moment, the latest electronic voting systems in use (particularly DRE systems, which according to Election Data Services, serves as the voting equipment available for 38 percent of the U.S. registered voters) are receiving a great deal of scrutiny and criticism. Citizens, private companies and elected officials are spending more time carefully examining these systems and the implications of their use. Because our democracy depends upon the public believing in fair elections, these systems must be shown to be as secure and reliable as other voting methods. That is probably much easier said than done. Reports of lost data, corrupted files, bribed officials, vendor partisanship, unsecured information and other scandals have been in the news several times since 2000. While these reports likely create an unrealistic expectation of unreliability, they are legitimate causes for concern. It will be the responsibility of the states and vendors to determine the best means of creating public trust. Some of these methods will likely include more stringent tests, careful discussions about the balance of proprietary information against the need for source code validation, and discussions on the balance between voter anonymity and the need for a reliable audit system.
In practice, public debate over electronic voting has devolved into an argument over the technical security of voting systems and whether or not a paper trail to facilitate election auditing is or is not desirable from a public policy perspective. While these issues are important, there is a broad range of end-to-end issues, from the point of capturing the voter’s intent to assuring an accurate final tabulation of votes. Consideration of electronic voting cannot be divorced from these issues, which frame such consideration and embed it in a larger context. Furthermore, these issues are themselves embedded in a larger electoral system that includes voter registration databases, election planning and administration, procurement of election systems, and so on. Put differently, challenges to election quality cannot be tied to just one potential problem whose solution would result in a near-perfect election process, but rather are the result of the cumulative impact of many potential failures large and small, including human error, equipment failures, procedural miscues, and so on. Thus, issues of the security or accuracy or usability of electronic vote systems have to be examined in the context of the entire electoral process.
_____
Electronic Voting – unsolvable problems:
Elections have to satisfy three conditions, they must be:
- Secure: Your vote has to be secure, steps must be taken to make sure that it can’t be tampered with; but also
- Anonymous: Your vote can’t be traced back to you, protecting you against coercion; but also
- Verifiable: It has to be shown that one person cast this one vote, and didn’t cast another to be counted, but also continue to be secure and anonymous.
All voting systems should be subjected to this test, whether pencil and paper, electronic kiosk or online voting. Balancing these three conditions is an incredibly difficult task. What makes it even more difficult is the additional requirement that the methods used to achieve these conditions need to be reasonably understandable to the population.
Open Rights Group’s research in this area has shown how difficult it is for electronic voting to achieve this.
In 2007, Open Rights Group were technical observers for electronic voting trials in England. E-voting systems in some constituencies were found to be running software known to be vulnerable, risking the security and anonymity of the vote. What’s more, votes were downloaded and counted by the suppliers of e-voting systems, without any candidate, agent or observer able to examine the process, undermining verifiability of the process.
In 2014 Open Rights Group participated in a peer-reviewed independent report on the security of e-voting in Estonia. The research discovered two fundamental vulnerabilities, targeting individual’s machines and the servers used to count the votes, that would allow for votes to be changed at scale potentially affecting the outcome of the election.
Some may argue that these points on the secure systems are moot, that the opportunities provided by blockchain and advanced cryptographic solutions have set all of that aside. But those arguments fail to take into account the other necessary condition for a vote: the process must be reasonably understandable for the public. Democratic processes need to be understood by more than a handful of advanced cryptographic experts. It must be trusted by all of us, and most important of all it needs to be indisputable in an understandable way for the most skeptical of us. If a solution can’t do this, it leaves us in a very precarious position.
The key to democracy is not in the winning and taking power, it is in the counting, the losing and the acceptance of that result. The only solution for securing electronic voting against the conditions of security, anonymity, and verifiability appears to be through using advanced security and cryptographic tools. But the problem with that is by using advanced security and cryptographic tools, most people can’t understand the process. That lack of understanding can be exploited leading voters to distrust the outcome of an election. And there it is: the unsolvable problem with electronic voting. Democracy is difficult. Relying purely on technology is not going to make it any easier or, as we’ve seen, more attractive to new generations. Electronic voting isn’t a solution to the problems in the consultation. In fact, it is likely to bring more profound problems.
_____
Problems with audit of electronic voting:
An audit of an election conducted with electronic voting systems with VVPAT starts with a count of the votes on the voter-verified paper ballots, after which all discrepancies between the electronic and VVPAT tallies are reconciled.
The electronic record and the printed record are both viewed as fallible and subject to subversion. A hacker can hack into a computer and corrupt data. A counterfeiter can print up counterfeit ballots and swap them for the real ones. Many vendors and some scientists believe that an audit trail of electronically recorded ballots can be made secure (possibly through encryption or other mechanisms), but no such systems have yet been validated through rigorous mathematical proofs, nor can they be independently confirmed for correctness by non-technical poll workers, election officials or ordinary citizens.
Also, surprise random counts of small percentages of VVPAT do not prove e-vote accuracy. If a surprise random check of a small percentage of transactions could ensure the accuracy of a computer system, no bank or other company would ever spend the time and money to perform a complete audit.
Yet the idea of counting only a small “statistically significant” percentage of the VVPAT appeals to many — it acknowledges the limited resources that we allocate for elections; it enables our election bodies to avoid the time and expense of counting all the VVPAT. For example, a bill in the New York state legislature would require counting 3% of the VVPAT. The bill does not require an audit or reconciliation of discrepancies, does not require 100% accuracy, and does not require the public to be informed of any discrepancies discovered.
Problems with counting only 3% of the VVPAT include:
- If observers can watch the count of 3% of the ballots cast, then the election has 3% legitimacy. Moreover, statistical significance may be an inappropriate consideration. Each different ballot design involves different computer programming for vote recording and vote counting. There is no reason to believe that if ballots are counted correctly in one district, they would be counted correctly in other districts where the ballot design is different, requires different programming, and can generate different errors.
- Some types of computer errors and fraud may not show up in small samples. These include:
-Intermittent errors or fraud triggered by particular combinations of votes and/or particular ballot designs.
-Legally “insignificant” vote switches per machine. A study by Yale students showed that with a single statewide system, centralized manipulation is facilitated and can swing elections with one or two vote switches per machine. This is why, when computers are used, 100% accuracy must be mandated.
- Creation of two classes of voters. 3% of voters would cast ballots that were confirmed to be tallied correctly. 97% of voters would cast ballots that were not.
- Mandate for unverified elections. The requirement for only 3% of the VVPAT to be counted puts the burden on candidates and voters to struggle in the courts for the right to verify an election in a timely manner before certification of outcomes.
- Electronic voting and vote tabulating systems should not be treated as exceptions to professional Information Technology standards, which require 100% audit, 100% accuracy.
- The idea that counting 3% of the VVPAT is sufficient to prove integrity of 100% of computer operations is based on several false premises:
-Computers are accurate and secure unless proven otherwise.
-If one computer is proven accurate, hundreds of other similar computers are also accurate.
-Elections are like a court of law where a piece of technology, or an unobserved procedure, should be assumed accurate until proven inaccurate.
-False premises, such as “if the chief election official of a jurisdiction trusts the computers, the computers are trustworthy,” have been used to evade the routine auditing to which all commercial systems are subject.
- Computer systems are merely tools created by people, and are always error-prone and vulnerable to manipulation by insiders. 100% audits, including reconciliation of discrepancies to achieve 100% accuracy, have been the only way to achieve accuracy of operation. In the Information Technology world, one common definition of computer security is “the results of normal operation have been proved correct by independent audit.” Most people understand that 100% audits with 100% accuracy are needed to prevent or detect financial fraud, but don’t apply this understanding to computer systems used for voting and vote tabulation. Obviously, audits are needed in both worlds for the same reason. If you find an error on your bank statement, and a bank officer says, “our records are never perfect, and we didn’t audit your account this month because our 3% random check said we were accurate enough,” that would be unacceptable. It should be unacceptable in elections. However, if all 100% votes cast electronically are verified with VVPAT and counted manually, then it becomes traditional manual ballot paper counting making e-voting meaningless. The better alternative would be use of precinct-based optical scan or mark-sense tabulators instead of DREs. In this simple and cost-effective system, voters fill out paper ballots which are then counted electronically by a tabulator at the precinct, similar to the technology used to score standardized tests. Optical scan machines have been in use for decades, and provide a voter-verified audit trail by default. Tabulators can detect overvotes at the poll so that the voter can be given the opportunity to correct a spoiled ballot.
One unspoken argument is that elections cannot be held to routine Information Technology standards – because in real life election bodies cannot perform computer audits. They lack not only the intention or will, but the legal mandate, expertise, staff, and funding. That is why any law that allows use of e-vote equipment must mandate and fund training of elections staff prior to use, require vendors to provide thorough training on their equipment, and ban vendor service contracts.
_
Procedures other than auditing cannot ensure election integrity:
A variety of activities can reduce the number of errors and discrepancies than may occur during elections, but these activities cannot ensure election integrity.
- Hardware and software testing. Such testing, if accompanied by correction of all errors that are found, can reduce the number of discrepancies and computer errors found during an audit. Due to certification requirements and the length of time required for certification, however, such errors are likely to remain uncorrected. (Certification can take a year or more.)
- Use of open source software. Open source software is software that is posted publicly for technologists worldwide to read. When errors are found they are discussed on the internet and suggestions for correction are made. Again, however, due to certification requirements and the length of time required for certification, such errors are likely to remain uncorrected.
- Reading and examination of software. If reading and examining software could eliminate errors, no company would ever perform continuous audits. Professor Aviel Rubin, the computer security expert who headed the Johns Hopkins team that wrote the first report revealing the insecurity of Diebold software, has stated publicly that no examination of software of the size and complexity of voting systems can guarantee that the software does not contain fraudulent parts.
- Escrow copies of software. The idea of keeping copies of software in escrow has many flaws. First, it assumes that the escrow copy has no errors or backdoors in it. Second, it assumes that if software in an election system is changed once, it cannot be changed back to the original escrowed version. Neither assumption is true. Comparing software escrowed one day to what is in the computer on another day will reveal only very sloppily performed fraud.
_____
I-voting no way to run a democracy:
Internet voting is risky due to its sociological and technological problems. Absentee balloting does not provide the safeguards of freedom from coercion and vote selling that are afforded via local precincts. Internet voting creates additional problems due to the inability of service providers to assure that websites are not spoofed, denial of service attacks do not occur, balloting is recorded accurately and anonymously, and votes are only cast by the authorized voter themselves. The government’s website warned that “it is the citizen’s responsibility to maintain the latest anti-virus software for their computer” in order to assure safety, yet they failed to acknowledge the fact that anti-virus software can only protect against known malware (new ones appear constantly, and could occur during an election season) and server-based attacks are still possible. Certainly citizens overseas should have an opportunity to vote, but perhaps this could be handled by setting up remote balloting precincts at the Embassies, or by creating bi-partisan poll-worker teams on military bases.
If you do online banking, you get feedback that the money is deposited into your account. You can check that. If there is a problem, you can complain to the bank and have it investigated. When you buy something online and the package doesn’t show up, you can contact the seller and say, ‘Where’s my package?’ Bank fraud happens and packages don’t arrive so having these processes to detect and deal with the problem is essential. We don’t even think about it because we know where to go.
But imagine the vote as a transaction in an online setting: You cast your ballot with a ‘submit’ button; you receive confirmation you’ve done so but there is no evidence after the fact that your vote – or every submitted ballot – is included in the final count. I am not saying hackers will definitely hack an election. I am not saying we don’t trust the election commission to be faithful in its execution of an election. That’s not the issue. The issue is, they are required to run a transparent election. Without transparency and an ability to trust the system, things will not bode well for our confidence in the democratic system. Simply stated, there is no way to optimize internet voting. You cannot overcome voting as a cybersecurity concern. People have this notion that hand-counted paper ballots are simple in a naïve way, when in fact, they are simple in an elegant way, in the optimal way. We don’t know how to do it better and still get the same kind of guarantee.
There are three requirements for robust political elections: security, anonymity and verifiability. Meeting those three requirements is a very difficult problem quite unlike other transactions. Online banking suffers problems but refunds are possible after checking your bank statement. You can’t ‘refund’ a vote and ‘vote statements’ can’t be provided to check your vote was correctly recorded as that would enable vote selling and coercion. All that paper in standard ballots may seem old fashioned, but it leaves a trail that votes cast, that PCs and phones can’t do. There’s a fundamental conflict between verification and keeping votes anonymous. Paper ballots do this very neatly but computers find this hard because they leave audit trails.
Switching to I-voting is not necessarily a bad idea. The reasons are legitimate. Whether it is an effort to improve accessibility or boost voter turnout or an effort to reduce cost and human resources, I-voting ultimately doesn’t deliver any result towards these noble pursuits. What does it mean to increase participation if the system itself isn’t trustworthy? Better voter turnout is meaningless if you’re not confident in the process. It’s not that paper ballots are perfect and completely un-hackable but the guarantees they provide are so much greater than the online system. It seems kind of crazy to want to give all that up just so we can have some convenience. You can’t give up the transparency of a democratic election, otherwise what the heck are we doing an election for?
According to Chris Culnane, a University of Melbourne cryptographer and part of the team that developed the Electronically Assisted Voting system that was used in the 2014 Victorian election:
‘Such systems are possible, but they are at the pinnacle of security and cryptography, they are trying to achieve the holy trinity of data security (confidentiality, integrity, and availability) in a system that is deployed for a short time with very high load and must be accessible and easy to use by both the public and the electoral commission…They are not going to be able to buy something off the shelf and it is just going to work.’
A chain of horrors:
The common practice of emailing ballots is like breakdancing in a minefield of security threats. Hackers can intercept the data on its way to polling authorities, changing votes in a way that no one can trace. Or malware, some form of which is on up to a third of all computers, can surreptitiously alter what voters type in. It can also plant yet more malware in the PDF or JPEG files that voters email in. This could lead to the ultimate nightmare scenario. An election worker clicks on an infected attachment, which spreads malware across the network at a county or state election office. It then infects the configuration files that are loaded, via memory cards, onto all voting machines and scanners for every election. Even if those machines aren’t online, the bug still gets in. Without fanfare, one email has swung an election. Even short of such a meltdown, just tampering with the relatively small number of online votes could be enough to flip the polls in the close races that are becoming more common around the world.
Going back to paper from online voting:
Virginia ultimately decided to abandon online voting altogether–despite having a large number of residents serving in the military. The federal government originally pushed for online voting to help service members stationed far from home cast ballots, and they are still the main group using those services in the U.S. But even many states with online voting are trying to cut back. Some states have taken proactive steps to further limit the population that qualifies for online voting or have restricted or prohibited it completely. The return to paper is happening in other countries, too. In 2017, France dropped its plans to let citizens living abroad vote online for legislative elections. Everyone who has tried, with the exception of Estonia, has subsequently backed away because they’ve seen the risks and they’ve seen how bad the software was… and therefore the problems they got into. The Baltic nation’s system is tied to the Estonian ID card, a state-issued smart card for secure online authentication and encryption. That somewhat reduces the risk, compared to the U.S.
And no other technologies will completely close the security gap. Blockchain is no magic bullet. The trendy encrypted ledger technology could help, by making it harder to change votes once they have been cast. But it wouldn’t stop spyware on people’s computers from manipulating the votes before they get written to the ledger, nor would it help with the fraught process of verifying that the person casting the vote is who they say they are. Similar weaknesses exist for end-to-end encryption between voters and election authorities.
No cybersecurity expert is willing to endorse any sort of platform or tool as secure for online voting. In fact, online voting is such a dangerous idea that computer scientists and security experts are nearly unanimous in opposition to it. No Internet technology is safe, secure or reliable for voting, find the National Academies of Sciences, Engineering, and Medicine. Paper ballots that can be tallied by hand are the most secure way to conduct an election, according to a report from the US National Academies of Sciences, Engineering, and Medicine. The report calls for all US elections to be conducted using such ballots by the 2020 presidential election. The report says it is safe to count that paper ballots with a machine using an optical scanner, but the analysis also stipulates that recounts and audits should be conducted by hand. It also recommends the immediate removal of voting machines that do not allow manual auditing.
________
Computer scientists versus election administrators:
In his celebrated essay “Two Cultures” (1959), the British writer C.P. Snow had lamented the cultural divide that separates two great areas of human intellectual activity, “the sciences” and “the arts.” He wanted that practitioners in both areas should build bridges, to further the progress of human knowledge and to benefit society. A similar cultural divide exists between “election administrators” and “computer scientists” around the world regarding the electronic security of DREs or paperless EVMs; they just can’t see eye to eye. The controversy over DREs dates back to the early 2000s and is world-wide.
According to election administrators, it may be possible to modify an isolated DRE in a laboratory but that does not prove anything. The question is whether any tampering is feasible involving a large number of machines under real election conditions with the security protocol and various administrative safeguards in place. They think that computer scientists have no practical experience of conducting elections and that they exaggerate the security concerns and that the “omnipotent hacker” is a myth perpetuated by novels and movies. They believe that there is “safety in numbers” and physically tampering with a large number of EVMs is difficult because there are so many of them.
On the other hand, computer scientists think that election administrators are status quoists who are clueless about Information Technology and the vulnerability of paperless EVMs to a range of hardware and software attacks and the evolving nature of the threats. With DREs, frauds may be undetectable and those who have been declared the losers are left with no recourse to verify results. Computer scientists think that election administrators harbour a secret fear that the legitimacy of the election process would be undermined if such attacks are proved and so they resort to “security through obscurity” by not making the hardware and software of the EVMs available for testing for vulnerabilities by external electronic security experts. A standing joke among computer scientists is that election administrators simply don’t want others to know just how bad their hardware and software are!
Both election administrators and computer scientists would do well to take C.P. Snow’s advice and build bridges in the interest of developing a sound and secure electronic voting system.
Ethical hacking of EVMs:
Ethical hacking is a common practice in the software industry. Google, Apple, Microsoft, Facebook and Twitter invite hackers to find flaws in their code and offer attractive rewards (called ‘bug bounties’) to those who find them. The US government has done likewise with programs like “Hack the Pentagon”. But election administrators and EVM manufacturers (both government-owned and private) around the world have been reluctant to submit their machines to such ethical hacking.
The annual “DEFCON Computer Security Conference”, which is the largest and longest-running conference of its kind, invites hackers from all over the world to Las Vegas, US, to display their skills. In the aftermath of fears that Russians had used hacking techniques to influence the 2016 US Presidential election, about 30 EVMs were made available in a ‘Voting Village’ to professional hackers for the first time in the 25th DEFCON Conference held in July 2017. Some of the EVM models had been in use in US elections till recently while others are still in use. The hackers were allowed to probe, deconstruct and even open the equipment over a period of three days in order to understand how they work and how they could be compromised by attackers. The results were sobering. By the end of the conference, every piece of equipment in the Voting Village was effectively breached in some manner. Participants with little prior knowledge and only limited tools and resources showed that they could undermine the confidentiality, integrity, and availability of these systems. Moreover, a closer physical examination of the machines highlighted several supply chain vulnerabilities. Many machines were found to use cheap generic chips (CPUs) that could be bought over the counter instead of specially customised chips that would be difficult for hackers to lay hands on. There were multiple cases of foreign-manufactured internal parts including hardware developed in China. The hackers documented the various vulnerabilities of the EVMs in the form of a report. The ‘Voting Village’ concept will be a regular feature of DEFCON Conferences hereafter and this should keep the EVM manufacturers in US (all of whom are in the private sector) on their toes.
In 2018 DEFCON Conference the Voting Village featured nearly four dozen machines, and again, their vulnerabilities were on full display. On the second day of DEFCON 2018, J. Alex Halderman, a computer-science professor at the University of Michigan, stood by the door of the Voting Village, encouraging everyone who came through to cast a vote for either George Washington or Benedict Arnold in a mock election he was running using a common ES&S-owned touch-screen voting machine, the AccuVote-TSX. The AccuVote is most studied electronic voting machine in the country, Halderman explained, as people pressed their fingers to the screen and watched it register their vote. The vote ticked up and up for Arnold. The election was rigged. Halderman had infected the machine—which was not connected to the Internet—with software that registered every vote for Washington as a vote for his rival. Because the AccuVote is a Direct-Recording Electronic device (D.R.E.), which provides no physical record of votes cast, there was no way to know what the real tally had been. Later in the day, Halderman told an audience how he’d put the fix in for Arnold by adding some lines of code to the external media card that is used to set up the AccuVote for an election. It was a quick, simple, and undetectable modification.
I advise Election Commission of India (ECI) to send Indian EVMs to the next DEFCON Conference for scrutiny by ethical hackers!
_______
Arguments against electronic voting:
Voting has progressed in technology from traditional days when voters dropped votes marked on a shell, shard of pottery, or card into a box to the current days where voting is controlled by electronics and the processes leading to the vote remain unseen to the human eye. Despite the change in method of voting, the basic facets of good voting tactics remain the same: ensuring one vote per voter, maintaining voter anonymity, accuracy of vote, security of the system, and prevention of fraud.
This is where the problem lies in many arguments against electronic voting – opponents do not feel that the voting basics can be maintained in an electronic voting system. The arguments have been divided into 3 general categories of complaints: issues with the technology, vast possibilities of fraud, and protection of voters and their votes. As Bruce Schneier describes it, technology adds more steps to the process and thus increases the possibility of error with each additional step, all of which are largely unseen by the voter. Put Murphy’s Law of ‘whatever can go wrong, will go wrong’ into play, and one can surmise that technology will most likely falter. Not only does the technology create more errors in the electronic workings, but the voters can also commit mistakes due to confusion with the user interface. The terminology is confusing, different machines produce different interfaces, and even the audio guides to help the disabled may prove more confusing than helpful.
With the advent of electronic machine voting also comes the higher possibilities of fraudulent machines and practices. First of all, the technology is “black box software,” meaning that the public is not allowed access into the software that controls the voting machines. Although companies protect their software to protect against fraud, this also leaves the public with no idea of how the voting software works. It would be simple for the company to manipulate the software to produce fraudulent results. Also, the vendors who market the machines are in competition with each other, and there is no guarantee that they are producing the machines in the best interest of the voters and the accuracy of the ballots. Lastly, vote accuracy is also an issue, because voters have no way of confirming there vote, and there is also no way of conducting a recount with direct-recording electronic (DRE) voting. With DRE, there is no paper trail, no verification, and thus no scrutiny of the processes. Voter anonymity is also a problem. Voters have to provide much of their personal information to the systems for voter verification, and with that comes the problem of keeping voter information safe and keeping voters anonymous. The cons against electronic voting laid out here are only some of the arguments against electronic voting. However, they are a good reflection of the ethical and technical concerns related to the issue of electronic voting.
______
______
Electronic voting may not be 100% secure but neither is traditional voting:
You must start from a base: no voting system is 100% secure. Neither traditional nor electronic. Ballot stuffing is a practice as old as elections themselves and it refers to one of the multiple techniques used throughout history to tamper with election results: submitting multiple ballots per person. There is also the personation technique, deceased voters who come back to life for one day to vote; and electoral registration fraud, voters registering illegally in a constituency that does not correspond to them. That is not to speak of the buses that pick-up people from the villages to take them to the capital to vote, the party obviously covering the expense.
Paper ballot is a cumbersome process requires a voter to first unfold the ballot paper, mark his preference, fold it again, go to the place where the ballot box is kept and drop it in the box. Paper ballots have inherent problems – their printing, storage and transportation involve huge expenditure; millions of ballot boxes are needed for each election, and there are logistics issues with their safe storage between elections. There were instances when the number of invalid votes (marked incorrectly by illiterate voters) exceeded the winning margin. Marked, unmarked, wrongly marked or multi-marked ballot papers are subjected to the decision of the returning officer. Also, the counting of ballot papers could take a full day or more.
The Netherlands, pioneer in implementing electronic voting (a legal provision being put in place in 1965), decided to go back to using ballot papers in 2008, two years after the publication of a study that revealed a serious security problem in the system. In 2009, following a long legal battle, the German Federal Constitutional Court ruled electronic voting unconstitutional, as it considered that it did not allow citizens without technical knowledge to supervise the election process. In the same year, Ireland scrapped the online voting system. Finland halted its program in 2010, after invalidating the results of the first pilot test, which was carried out in 2008. The United Kingdom carried out more than thirty pilot tests between 2002 and 2007, but none of them returned sufficient guarantees for authorities. The Electoral Commission suspended the implementation of electronic voting in 2008. In Spain, the surprise political party that was successful in the European elections, Podemos, is using an electronic voting system to make internal decisions. It is called Agora Voting and involves three phases: One, the party’s responsibility is to make sure that the person voting is who they say they are; the second and third, registration and counting of the votes, are the shared responsibility of the so-called “voting authorities” (independent observers who certify that no personal interests contaminate the process). All of the software used is free software and after voting, each voter can check the integrity of the vote using an identifier. In this case, the largest crack in the system is in the Podemos registration or membership system, which only asks for a national identity card number and phone number. Both of these things, as already proved, can be faked.
To sum up, as Eduardo Robles, cofounder of Agora Voting, said, there is not a big difference between the traditional voting system and the electronic. “Can ballot papers get lost? Of course, but it is very difficult because they are kept guarded. Can ballot boxes be tampered with? Yes.” And the same happens with the virtual ones. Security mechanisms improve very quickly but so do the techniques used by the attacker. While there is interest in changing the results, ballot stuffing will continue to evolve.
_______
Why is paper ballot system still prevalent in the U.S.? Security.
The US Election Assistance Commission Chairman Tom Hicks saying that the “primary reasons” paper ballots are used in most states are “security and voter preference”. E-voting is not highly preferred because of the cost it comes with: the need for new voting machines, upgrades, are “greatly restricted by budget”. Another argument is that politicians would not go for e-voting over the dearly-known paper ballot ritual, which has been “accurately modeled from decades of polling and analysis”. But here’s the deal: considering that Americans use electronic gadgets for banking, educational purposes and even security, this logic may not stand tall for long. Though it has been around for quite some time now.
Today, a reliable method of voting that is widely used and avoids many of the problems of paper while preserving some of its advantages is a hybrid of paper and machine in which voters mark a machine-readable form and then it is scanned and the results recorded. This avoids most difficulties (but not all) with hand-filled out ballots, takes advantage of the fact that the scanner/tabulation computer doesn’t get tired and can be more accurate, and provides a paper trail for auditing. Because these machines are seldom networked, they are less likely to be disrupted or corrupted, but they do require that someone program the system to record the results and that the results be captured in a systematic and secure way.
_____
_____
Can anyone hack Indian EVM?
There are two ways by which an electronic device can be hacked: wired and wireless. In order to hack a machine, the best way is to establish a wired link with its control unit, which is the brain of the device. In technical terms, it is called the microprocessor, which is an electronic board with some circuit elements that can do basic mathematical operations based on the given input. The information fed to the system is processed by the control unit and the output is sent to the memory of the system, which can be read or retrieved at a later stage. Hacking a device through a wired connection essentially means designing another electronic device, which is able to send a specific pattern of information that its brain can read and interpret. In a demonstration at the University of Michigan, scientists used this kind of hacking in the context of an EVM, where they used a specifically designed chip that was physically plugged into its control unit. There is an alternative way, in which you artificially change the processor to show that it is hacked. This technique was demonstrated by the Aam Admi Party in the Delhi Assembly last year.
In wireless hacking, you do not need a physical connection with the device, but you still need a basic understanding of the control unit or the target device and its operational instructions. In order to hack a device using a wireless link, the device needs to have a radio receiver which comprises an electronic circuit and an antenna. The Election Commission claims that EVMs do not have any such circuit element. Let us assume that someone has designed a special kind of electronic circuit, technically called a transceiver, which is ultra-small and is artificially inserted in an EVM, so that it gets hooked to its control unit. In that case, one would need millions of such specifically designed transceiver sets, plugged into the control unit of each EVM. Now, such advanced electronic devices are extremely complex and cannot be bought from a shop at the end of your street. There are only around half a dozen companies in the world with the expertise to design and fabricate such a device at the chip level. The designers would need access to the actual circuit board of the EVM in order to design the electronic interface. The design of a single device at the chip level can cost a couple of million dollars. The overall cost of getting such devices in millions would cost hundreds of millions of dollars. This is not the end of the story. One would also need a specifically designed antenna, which interfaces with the transceiver circuit. Now, there is a twist here — in principle, transceiver circuits can be miniaturised, but the antenna cannot. The physical dimensions of smallest GSM antenna that we can think of are in the range of 1 cm × 2cm × 0.5 cm, which roughly corresponds to the dimension of our mobile phone antenna. Now, we would need millions of such antennas along with the transceiver circuits, hooked on to the target EVMs to enable large scale wireless hacking. In principle, a miniaturised transceiver can remain hidden from our eyes but the antenna would always remain visible due to its size. If one were to use lower frequencies, let us say 100 MHz, the antenna size would increase by a factor of 10. That is why we need huge antennas for our TV sets or dish antennas.
Considering all this, large-scale deployment of such a technology would be a huge project in itself, where the Election Commission, EVM manufacturers as well as chip-making companies would be involved. As mentioned earlier, it is almost impossible to hide the antenna, which will always stick out of the system in order to ensure a seamless wireless link.
To sum up, Indian EVMs cannot be hacked on large scale to alter election outcome. Solitary EVM can be hacked if physical access is provided by breach in security.
Pitfalls of paper ballot voting in India:
Paper-based voting is even more susceptible to being hacked through booth capturing, artificial manipulation of ballots, change of ballot paper, and many different ways. In the current age, where printers and computers are readily available, it would take a couple of hours to duplicate ballot papers, print them and dispatch them with miscreants to the specific voting booths. Western countries that have refused to opt for EVMs are small, have a small number of voters, and have strong policing systems that prevent manual hacking and manipulation of ballots. Also in India, there is strong possibility of ink thrown in ballot boxes, ballot stuffing and invalid votes in which it is impossible to figure out which candidate’s name has been stamped.
______
______
Moral of the story:
_
- The right to vote freely for the candidate of one’s choice is of the essence of a democratic society. Every voter’s vote is entitled to be counted once. It must be correctly counted and reported. Voting procedures play a significant role in the conduct of free and fair elections in a democracy. It converts voters’ preferences into a political mandate which in turn forms the basis for policymaking. The key to democracy is not in the winning and taking power, it is in the counting, the losing and the acceptance of that result.
_
- The basic facets of good voting tactics remain the same no matter traditional paper ballot voting or electronic voting: i.e. ensuring one vote per voter, maintaining voter anonymity, accuracy of vote, security of the system, and prevention of fraud.
_
- Electoral fraud not only undermines public trust in democratic institutions by electing political leaders that have the greatest capacity to organize electoral fraud but it also adversely affects the provision of public goods. In India, the largest democracy with more than 800 million registered voters and a complex multi-party system, electoral fraud has been one of the leading causes of concern. Among various forms of electoral violation, such as multiple voting, vote buying, and voter intimidation; booth capturing is a major concern. In several constituencies under the paper ballot system in India, polling booths would be captured, and ballot boxes would be stuffed. Voting systems cannot prevent all forms of electoral fraud since there is always a financial incentive to cheat the system due to socio-economic challenges. However, design of voting systems should take these threats into account and leverage on security wherever possible to ensure that any deliberate attempt to circumvent people’s mandate is detected.
_
- Without trust in voting system, our democracy could crumble. Therefore, it is of critical importance that we safeguard our democracy by ensuring that voting systems work properly and those responsible for operating our elections must demonstrate to the public that their votes are indeed being captured and counted as they intended, and the outcomes are correct. It is patently unfair that once you get to the ballot box, the ballot itself fails you because voting system is compromised. The ultimate goal of electoral reform by implementing an electronic voting solution—is a credible electoral process that enjoys a high level of public trust and confidence in the new system. The public must trust that elections are fairly conducted in order for a democratic government to be considered legitimate. If the public perceives elections to be unfair, the foundation of the government is weakened. Whether electronic voting systems are fair may not even matter; it is the public perception that is crucial.
_
- Paper ballots with manual counting system has transparency, verifiability and accountability. Most countries still use paper ballots which are counted by hand after the voting period ends. This obviously has drawbacks: paper is wasted, invalid votes, manual vote counting takes time and is potentially more error-prone than electronic vote counting, not to mention electoral frauds. The primary reason for expanding the use of technology in the electoral process is the desire to overcome the limitations of conventional voting systems. The main reason for finding alternative to paper ballot and manual counting is exclusion of so-called invalid votes. An invalid vote is a vote which doesn’t count towards the final election result as voter’s intention cannot be clearly determined. It is these invalid and doubtful votes which, in many cases, are the root causes of controversies and election petitions. There were instances when the number of invalid votes exceeded the winning margin and invalid votes could have affected even the final formation of the government. In any physical ballot involving marks on paper, there will be marks that are on the borderline between acceptable and unacceptable votes, and vote counting rules that allow selective counting of marginal marks lie at the heart of a broad class of election rigging. This is eliminated by electronic voting. Other reasons for electronic voting include faster tallying times, providing ease to voters with disabilities, and increasing voter turnouts.
_
- Electronic voting system is a voting system in which the election data is recorded, stored and processed primarily as digital information. Electronic voting system is where the recording, casting or counting of votes in political elections and referendums involves information and communication technologies. Electronic voting system uses electronic methods to record and/or count votes. It is possible to have electronic voting without electronic counting and electronic counting without electronic voting. It is also possible to have voting and counting on entirely different devices, whereby a voting machine is used to produce tokens with the ballot choices made and a separate counting device tallies the votes recorded on these tokens. In common usage the term ‘electronic voting’ refers to DRE (direct recording electronic) voting systems most often utilizing touch-screens as well as electronic panels with push buttons or pointing devices to record votes directly in electronic memory. DRE machines are also known as electronic voting machines (EVMs). Other electronic voting systems include punch card systems, optical scan voting systems, electronic ballot printers and Internet voting.
_
- A worthy electronic voting system must comply with a set of standards established by regulatory bodies, and must meet requirements like security, accuracy, integrity, swiftness, privacy, auditability, accessibility, cost-effectiveness, scalability and ecological sustainability.
_
- The terminology of electronic voting is nascent, and a crucial distinction lies between the various different ways in which voters can vote electronically. Internet voting (I-voting) is defined as systems where obtaining ballots, casting votes or counting votes in political elections and referendums uses an internet connection. Internet voting contain an additional module for authenticating voters based on an electronic poll book or electoral register. When considering electronic voting solutions, a clear distinction can be made between what is commonly referred to as I-voting or internet voting and a more traditional form of electronic voting that employs controlled voting booths where the actual vote is cast on an electronic device (e-voting) i.e. non-internet electronic voting. Although online voting, internet voting and I-voting are the same, colloquially these terms refer to remote online voting which involves casting electronic ballot via the internet from a remote location, such as home, work or perhaps overseas. Remote online voting could occur on a number of devices such as a desktop computer, laptop, tablet or iPad, or mobile phone connected to the internet.
_
- Electronic voting can be conducted either in controlled or in uncontrolled environments. Electronic voting in controlled environments happens when the casting of votes takes place in polling stations, polling kiosks or other locations under the supervision of staff appointed by the electoral management body (EMB). Electronic voting in uncontrolled environments happens without any supervision and from voting devices that cannot be controlled by the election administration. This can be from home, on the voter’s personal computer, or potentially anywhere on mobile or public devices.
_
- Because biometric identifiers cannot be easily misplaced, forged, or shared, they are considered more reliable for person recognition than traditional token or knowledge-based methods. So, electronic voting system has to be improved based on the current technologies viz., biometric system. Fingerprint can be used for the purpose of voter identification or authentication. As the fingerprint of every individual is unique, it helps in maximizing the accuracy. A database is created containing the fingerprint of all the voters in the constituency. Illegal votes and repetition of votes is checked for in this system.
_
- Most voting systems have as their cornerstone, the secrecy of the vote, forestalling attempts to influence the voter by intimidation, blackmailing, and vote buying. On the other hand, everyone knows who they voted for, but one cannot check that the eventual accounting of the votes was not tampered with because, in the simple case, one would be revealing his vote. There is a fundamental conflict between verification and keeping votes anonymous. Paper ballots do this very neatly but computers find this hard because they leave audit trails. Virtually every information and communication technology (ICT) application is built in a way that allows verification of its proper functioning by observing the application’s outputs. Electronic voting systems are fundamentally different. Due to the requirement to protect the secrecy of the vote, they have to avoid any connection between the voter’s identity and the vote cast. This is in itself a challenge as standard ICT systems are inherently built for tracking and monitoring transactions that happen on them. More importantly, breaking the link between voter and vote means that the examination of an electronic voting system after an election cannot prove directly that every vote was indeed counted and tallied as cast. That is why indirect proofs of the validity of the electronic results, such as paper trails or system certification, in combination with stringent quality control and security procedures, are exceptionally important in electronic voting. Without such mechanisms, manipulated or incorrect results produced by an electronic voting system could remain undetected for a long time. From the outside electronic voting might appear to have been properly conducted and produced an accurate outcome, but there is a possibility that errors and fraud could go undetected. To mitigate this, electronic voting systems must be made verifiable. There are two types of verifiability – individual verifiability and universal verifiability. Individual verifiability means a voter is able to ensure that their ballot was cast as intended and recorded correctly. Universal verifiability means any member of the public can verify that every recorded vote is correctly included in the tally. VVPAT (Voter Verified Paper Audit Trail) is prototype of individual verifiability. End-to-end cryptographic verification (E2E-V) is prototype of universal verifiability. Traditional paper ballot voting has individual verifiability but no universal verifiability.
_
- Verifiable ballots are necessary because computers can and do malfunction, and because voting machines can be compromised. Relying entirely on machine counting without any physical check by humans, may leave the system vulnerable to attacks that can go undetected. So, in case of electronic voting, there should be provision for an additional verifiable record of every vote cast in the form of ‘paper print-outs’ which should then be hand counted and tallied with the machine total. This is what the EVMs fitted with Voter Verified Paper Audit Trail (VVPAT) seek to achieve. All Electronic voting machines must have a voter-verifiable paper audit trails (VVPAT). This is a paper ballot printed out by the voting machine, which the voter is allowed to look at and verify. He doesn’t take it home with him. VVPAT slip automatically gets cut and falls in sealed drop box. The point of this is twofold: it allows the voter to confirm that his vote was recorded in the manner he intended, and it provides the mechanism for a recount if there are problems with the machine. Experts have long recommended that all elections should be audited before the winner is certified to ensure the results are correct. This entails using statistical models to retrieve a small sample of paper ballots (VVPAT) that are examined by hand to ensure the machines recorded and counted the votes correctly. If discrepancies are discovered, the audit can be escalated to a full hand count and the hand count of the paper ballots becomes the official result. By manually re-counting the VVPAT, the results presented by the voting system can be independently verified. Tallying the results from VVPAT with aggregate count from respective EVMs is the best way to test whether or not EVMs have been tampered with. The results of an entire election can be verified by a well-designed manual recount of VVPAT from a random sample of polling stations. As the level of EVM rigging falls, you need larger size of random sample to detect rigging. This factor as well as the size of constituency must be taken into account while deciding the statistically significant sample size of EVMs for which hand counting of paper slips should be done. However, studies show that the majority of voters fail to detect mismatches between their electronic ballot and the paper trail leading to uncertainty regarding the value of this process of VVPAT. Also, if VVPAT is available, a voter should be able to cancel his or her vote should the paper receipt not reflect the ballot cast on the machine.
_
- One must understand that random counts of small percentages of VVPAT do not prove electronic voting accuracy. Ideally all 100% votes cast electronically must be verified with VVPAT count, but then it becomes traditional ballot paper counting making electronic voting meaningless. About 1.8 million EVMs are used across 543 parliamentary constituencies in India. Tallying all VVPAT counts with EVMs counts would defeat the very purpose of shifting from traditional paper ballots to EVMs.
_
- The main reason for the difficulty in implementing a secure electronic voting system is the conflict between the principles of accuracy and secrecy in the electoral process. In e-commerce systems, a buyer can always get a receipt to document his purchase. Conversely, due to fundamental voting regulations, providing documentation of a vote is forbidden, which means that the voter has no choice but to trust that a system records his vote as cast, counts it as recorded, and is secure and private enough to ensure that no one will be able to view or change his ballot. To resolve this conflict and to eliminate the need for the infamous chain of custody, cryptographers have suggested a protocol known as end-to-end (E2E) cryptographic voting. The goal behind the end-to-end concept is to provide voters with confidence in the integrity of election results, regardless of the software used and without the need to blindly trust election officials. All that must be accomplished without enabling the voters to prove to others how they voted. Generally, end-to-end systems provide the voter with some kind of assurance that his vote was recorded-as-intended (ballot casting assurance) in the form of encrypted proof receipts. Additionally, such systems publish all the encrypted proofs so that the public may verify the integrity of the election as a whole (universal verifiability). E2E-verifiablility adds complexity to the election process, and the effective wide-scale deployment of E2E-verifiability will require a broad understanding of the underlying cryptographic methods by election officials and the general public.
_
- Electronic voting machines and ballot tabulators are computers, and like all computers they are susceptible to software bugs, programming errors and hacking which could corrupt the vote count. Elections could be hacked or rigged by “insiders” such as vendors or election workers; anyone able to access the voting machines or the systems that program machines and tally the election results. Voting systems may also be hacked or rigged remotely over the Internet by hackers anywhere in the world. Cyber experts have repeatedly proven that the testing and certification process for basic functionality and accessibility cannot be relied on to ensure voting system security. Elections officials are usually not computer security experts and most do not fully appreciate the security vulnerabilities of electronic voting machines.
_
- Software used on electronic voting machines must be open to public scrutiny. Security experts have demanded that voting machine source code should be publicly available for inspection. Any expert who wants to analyse and understand an electronic voting system needs to have access to its programming source code. This has two functions: it allows any expert to examine the software and find bugs, which can then be corrected to improve security; and it increases public confidence in the voting process because when the software is public, no one can insinuate that the voting system has unfairness built into the code.
_
- Most voting machines (DREs) are not directly connected to the Internet, but this does not ensure they cannot be remotely hacked. Before each election, each voting machine must receive programming information about the candidates and contests in that election, via an election management system (EMS). The EMS is typically hosted on regular desktop or laptop computers which can potentially be used for other, non-election related, Internet-connected activities. This means the device that hosts the EMS may be exposed to the Internet and serve as a pathway for a hacker to attack the EMS and infect the voting machines with malicious software that can corrupt the vote count. Furthermore, many voting machines have built-in wireless capability which will expose the voting machines to the Internet when transmitting election results.
_
- There appears to be an emerging consensus that in general, current American DREs do not adhere sufficiently to currently accepted security principles for computer systems, especially given the central importance of voting systems to the functioning of democratic government.
_
- Denial of service, advanced persistent threats, malware, insider attacks, compromised credentials, all of these threats faced by electronic voting systems are not unique, they are threats encountered in all information communication systems. However, for voting systems, this is absolutely unacceptable as vulnerabilities exposed in electronic systems can compromise democracy and wield considerable political power. Therefore, these threats need to be adequately addressed while still maintaining the confidentiality, integrity, and availability of the voting system.
_
- Convenience and greater access are the two key benefits of Internet voting while concerns are about secrecy, security and verifiability of voting. No cybersecurity expert is willing to endorse any sort of platform or tool as secure for online voting. In fact, online voting is such a dangerous idea that computer scientists and security experts are nearly unanimous in opposition to it. Currently, no known technology can guarantee the secrecy, security, and verifiability of a marked ballot transmitted over the Internet. Blockchain methods do not redress the security issues associated with Internet voting. End-to-end verifiable (E2E-V) voting mitigates some of the vulnerabilities in Internet voting, but cannot prevent malware and DoS attacks. The Internet is not currently a suitable medium for electronic voting. Conducting secure and credible Internet elections will require substantial scientific advances. It may be decades before we’re able to secure online systems to the same level we expect from voting in polling places today. E2E-V is suitable for non-internet electronic voting.
_
- There are about 120 countries in the world that practice democracy. Of all these democratic countries, only about 25 have experimented with or used electronic voting to elect their governments. So, electronic voting is not the dominant choice of the world for recording and/or counting votes in elections. Parts of Europe and North America can be seen as moving away from the use of electronic voting, while South America and Asia show increasing interest in using electronic voting technologies. Paper ballots are considered the ‘gold standard’ of voting. That is why they are still in use in many advanced countries like the UK, Japan, Canada, and Singapore while others like Germany, Netherlands, and Ireland have reverted to paper ballots after experimenting with EVMs for some time.
_
- According to German constitution, all essential steps in the elections are subject to public examinability. Since ordinary citizen (without expert knowledge) cannot examine the electronic voting system to see whether it is operating correctly or not, ordinary citizens cannot check the essential steps in the election. Electronic voting machines are computers that, like all computers, are essentially opaque to citizens who do not have “special expert knowledge” about computers. Therefore, German Constitutional Court banned electronic voting. Germans have a point. The election process must be reasonably understandable for the public. There are three requirements for robust political elections: security, anonymity and verifiability, and it can be achieved in electronic voting only through using advanced security and cryptographic tools. But the problem with that is by using advanced security and cryptographic tools, most people can’t understand the process. Democratic processes need to be understood by more than a handful of cryptographic experts. It must be trusted by all voters and trust without understanding the complexities of electronic voting amount to blind faith which can be shattered easily. If not carefully planned and designed, the introduction of electronic voting can undermine confidence in the whole electoral process.
_
- One of the core arguments in support of electronic voting is to increase democratic participation but it has not delivered that outcome. The distinction – why people vote not how people vote – is what makes all the difference.
_
- Electronic voting should be seen not only from technological point of view but also from social and organizational perspectives and interrelationships amongst them.
_
- What are the effects of voting technology on candidates’ vote shares? Does electronic voting come at the expense of electoral fairness and neutrality as compared to paper ballot voting? There are hardly any studies that compares electoral fairness and neutrality between paper ballot voting and electronic voting. One Brazilian study showed that resourceful candidates were able to garner more votes than non-resourceful candidates in electronic voting election as compared to paper ballot election because resourceful candidates were better able to communicate the information that electronic voters needed to cast valid ballots than their non-resourceful counterparts. On the other hand, one Indian study showed that EVMs strengthened the democracy in India by making elections more competitive, by significant decline in electoral fraud, by significant decline in crime rates and by increased voter turnout in weaker and vulnerable sections of the society (illiterates, women and the scheduled castes and tribe).
_
- No other country in the world has used electronic voting in as large a scale as India has. Over 60% of the more than 800 million registered Indian voters cast their vote in the last general elections in 2014 using EVMs. Using paper ballots for Indian parliamentary elections requires some 8,000 tons of paper, equivalent to cutting down 120,000 full grown trees. Thus electronic voting in India is highly environment friendly.
_
- An ideal Electronic Voting Machine (EVM) should be a stand-alone, non-networked machine with a Central Processing Unit (CPU) whose software is ‘burned’ into it and cannot be programmed after manufacture or manipulated in any manner. Indian EVM is answer to this successful description. They are more like calculators than computers and are not connected to any network (wired or wireless) and if they retain their physical integrity, they cannot be hacked. It is imperative that documented chain-of-custody procedures should be in place to ensure that machines are secure from tampering once removed from the polling station either at the end of polling or in case of machine failure, and also when they are stored in-between elections.
_
- The results in various elections in India have made many of the losers of the polls cry foul that it is the technology that failed them and not that their poll promises were rejected by the people.
_
- Is any device, electronic or not, tamper-proof? The answer, of course, is no, it is not. Given enough technical, logistical and human resources, one can tamper with any device. This is as true of a laptop as it is of a “black box” flight recorder or the Indian electronic voting machine (EVM). Whether one should worry about a device being tamper-proof depends not on the theoretical feasibility of tampering but on the practical realities of pulling it off without detection — and the gains to be had by such tampering.
Tampering of Indian EVMs is very difficult because:
-1. For tampering of the EVMs, one needs physical access to EVMs, and pretty high-tech skills are required. Given that EVMs are stored under strict security which can be monitored by candidates or their agents, it is very difficult to gain physical access to the machines. Physical tampering to hack EVM is easily detectable. Additionally, since no EVM is connected to another EVM by any means, to impact the results of an election, hundreds to thousands of machines will be needed to tamper with, which is almost impossible given the hi-tech and time-consuming nature of the tampering process. In M3 machines, this is also technologically ruled out, as they shut down in the event of tampering.
-2. For EVMs to be manipulated at the manufacturing level, it is assumed that there is some trojan present in the EVM already that will lead to votes being transferred to a particular party. This is impossible as there is no prior way in which the order of the candidate can be known besides the location where the EVMs will be used. There is a double randomization process which makes it impossible for any person to know which machine will be used in what constituency, this is done to safeguard that machines are not pre-programmed to cast ballots in favour of a particular candidate.
-3. VVPAT machines now display the voter’s choice, thereby bringing an extra layer of verification.
-4. Any tampering of control unit by coded signals by wireless, Bluetooth or WiFi is ruled out as control unit does not have frequency receiver and data decoder. These EVMs do not have any frequency receiver or decoder for data for wireless or any external hardware port for connection to any other non-EVM accessory or device. Hence no tampering is possible either through hardware port or through Wireless, Wi-Fi or Bluetooth device because control unit accepts only encrypted and dynamically coded data from ballot unit. No other kind of data can be accepted by control unit.
_
- Computer errors and malfunctions are possible and should not be seen as tampering or rigging. Out of thousands of EVMs, if one EVM shows flipping of vote, loss of votes or wrong totaling, it could be machine failure rather than deliberate tampering by humans. Non-malicious equipment malfunction can cause flipping of votes, loss of votes, wrong totaling similar to EVM tampering. The sensors in touch screen devices can be knocked out of alignment by shock and vibration that may occur during transport and such touch screen machines can misinterpret a voter’s intent. These malfunctions should be prevented or corrected before polling and the best way to confirm voter’s intent is by VVPAT. Also, there should be a cryptographic mechanism for identifying the original CPUs and cryptographic protection of stored voting data.
_
- The better alternative to EVM/DRE with VVPAT would be use of optical scan voting system which uses optical scanner to read marked paper ballots and tally the results. Scanners can reject improperly marked ballots, allowing the voter to start over, thereby reducing invalid votes. There is a school of thought which considers Machine-readable Paper Ballots that are electronically counted using OMR (optical mark recognition) technology superior to EVMs with VVPAT because machine-readable paper ballots retain all the advantages of paper ballots minus the delay in counting. Here, the primary ballots are in paper form and the secondary ballots are in electronic form whereas in EVMs with VVPAT, the primary ballots are in electronic form and the secondary ballots are in paper form. Paper is more secure than electronic memory and primary paper ballots are superior to secondary paper ballots.
_
- There are many layers between the application software that implements an electoral function and the transistors inside the computers that ultimately carry out computations. There is no technical mechanism that can ensure that every layer in the system is unaltered and thus no technical mechanism exists that can ensure that a computer application will produce accurate results. Electronic voting systems are especially vulnerable when they are connected to the Internet. Even when systems are not connected to networks, they are vulnerable to attack through physical or wireless access. Computer scientists think that DRE/EVMs are vulnerable to range of hardware and software attacks, and frauds may be undetectable, and those who have been declared the losers are left with no recourse to verify results. Election administrators think that computer scientists exaggerate the security concerns and that the “omnipotent hacker” is a myth perpetuated by novels and movies. They believe that there is “safety in numbers” and physically tampering with a large number of DRE/EVMs is very difficult because there are so many of them. Both election administrators and computer scientists are advised to build bridges in the interest of developing a sound and secure electronic voting system.
_
- Paper ballots that can be tallied by hand are the most secure way to conduct an election notwithstanding electoral frauds and invalid votes. Paper ballots form a body of evidence that is not subject to manipulation by faulty software or hardware and that can be used to audit and verify the results of an election. It is safe to count paper ballots with a machine using an optical scanner, but recounts and audits should be conducted by hand. Electronic voting machines that do not allow manual auditing (without VVPAT) must be banned. No procedure other than risk-limiting auditing can ensure election integrity in electronic voting.
______
Dr. Rajiv Desai. MD.
February 3, 2019
______
Postscript:
There is fundamental conflict between vote secrecy and vote verification. Paper ballots resolve this conflict but computers find it difficult. Although paper ballots are gold standard of voting, for a country like India with more than 800 million registered voters, millions of invalid votes and history of booth capturing and ballot stuffing, M3 EVMs with VVPAT is a better option than paper ballots. EVMs can be trusted but not Indian leaders and their henchmen.
______


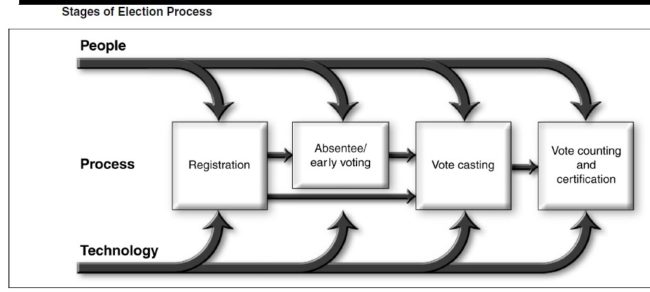
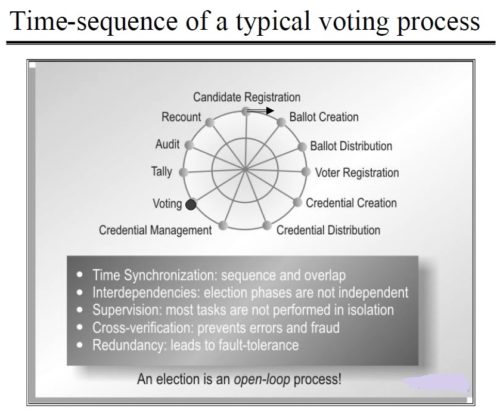

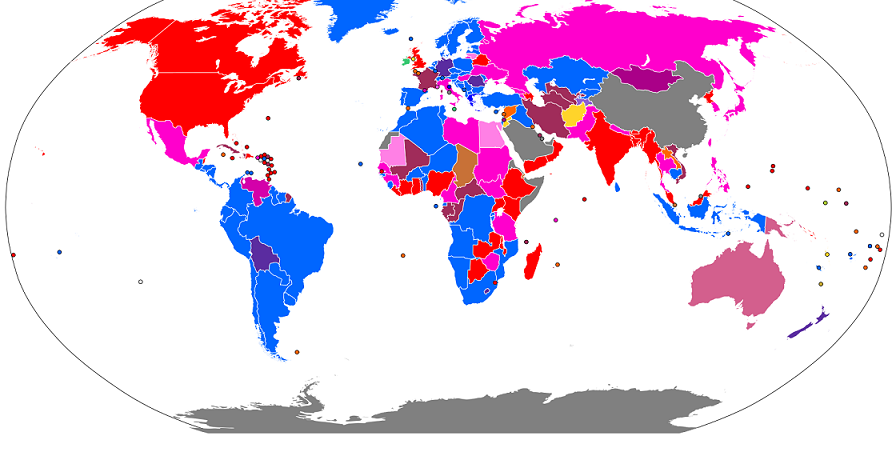
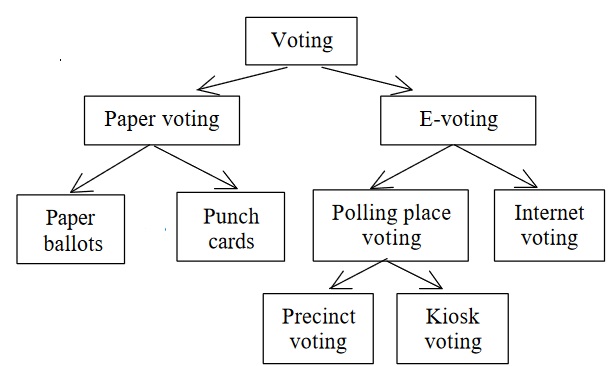
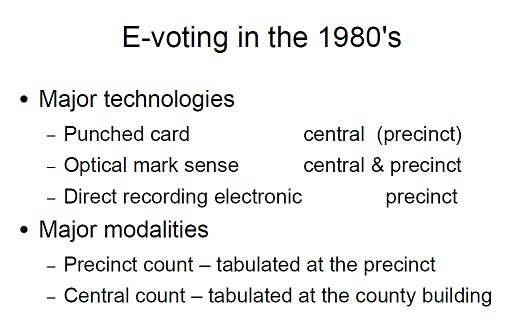
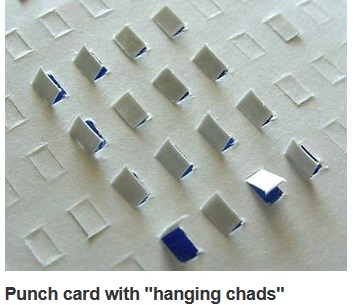

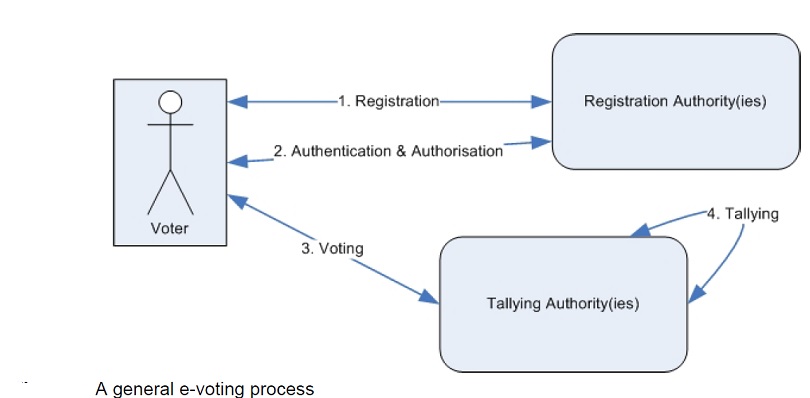
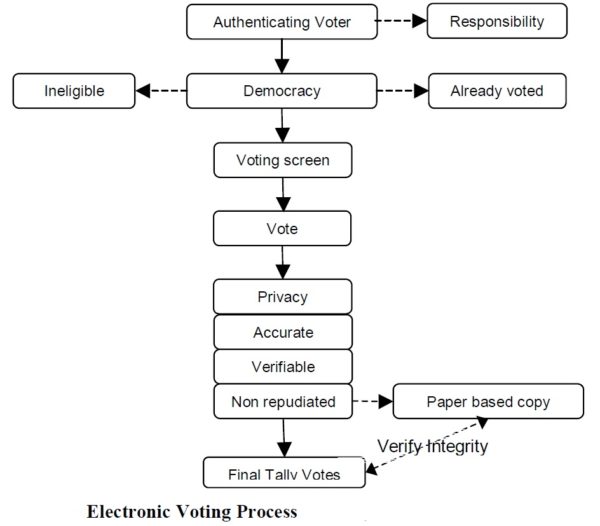
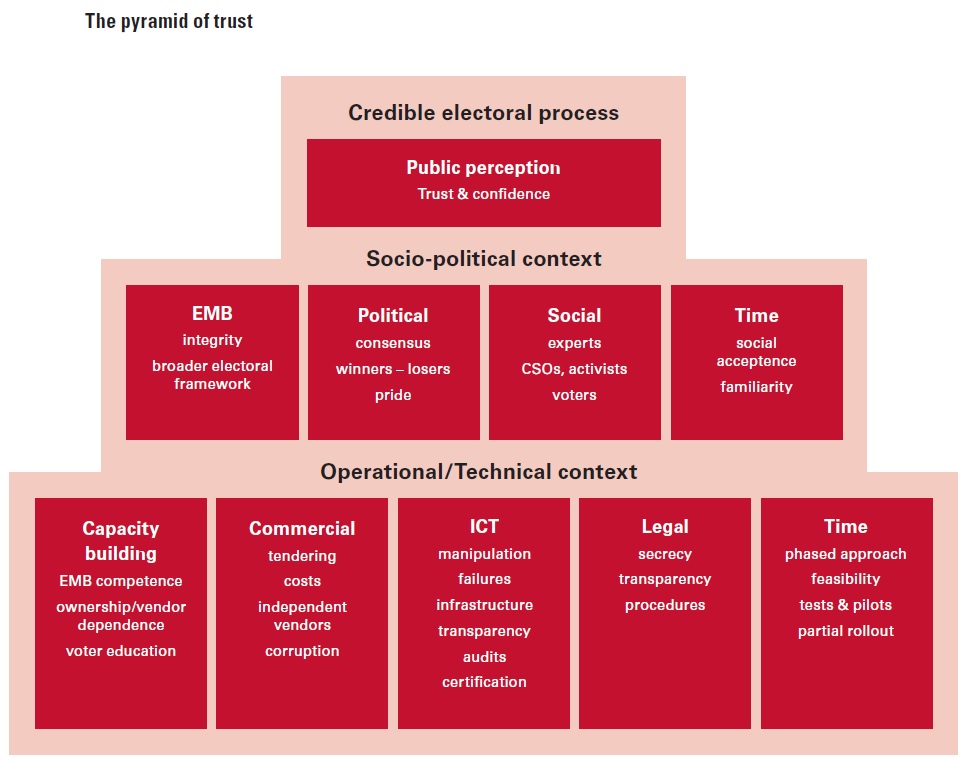
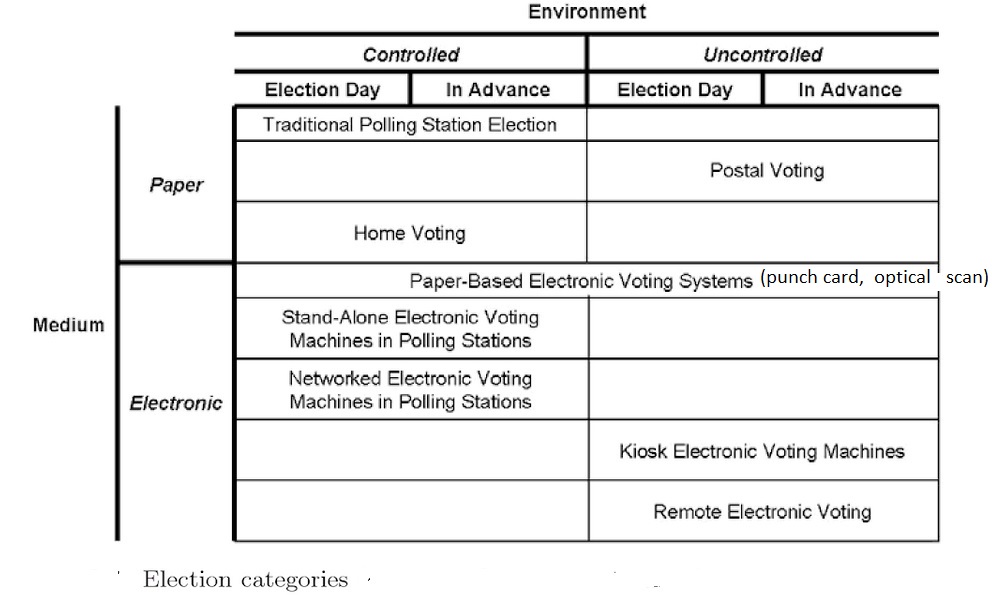
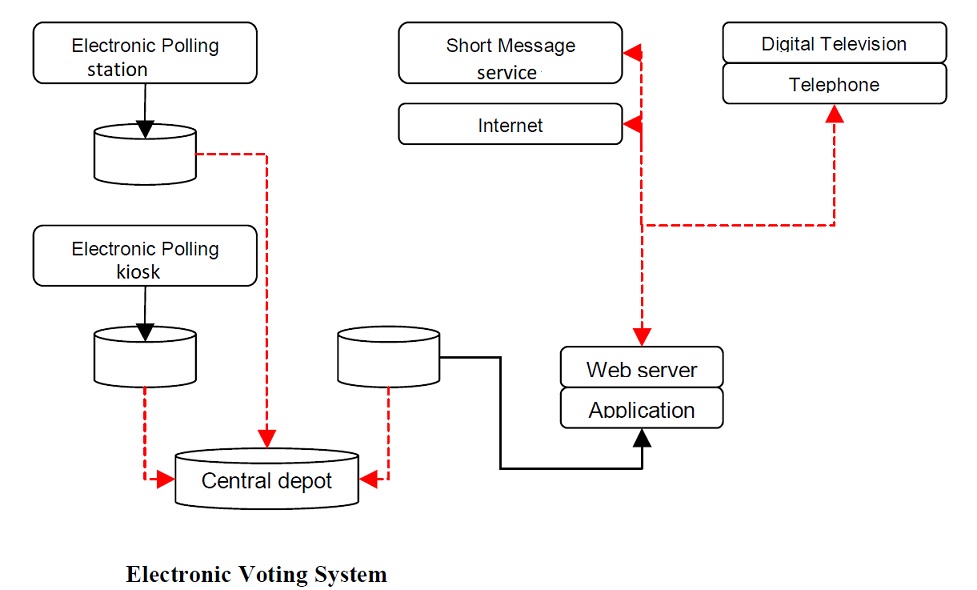

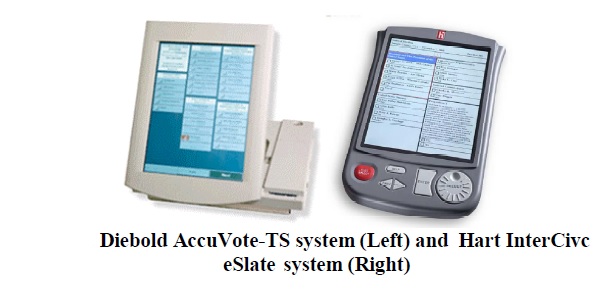

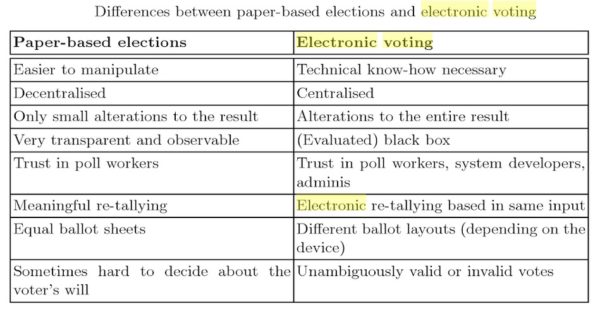
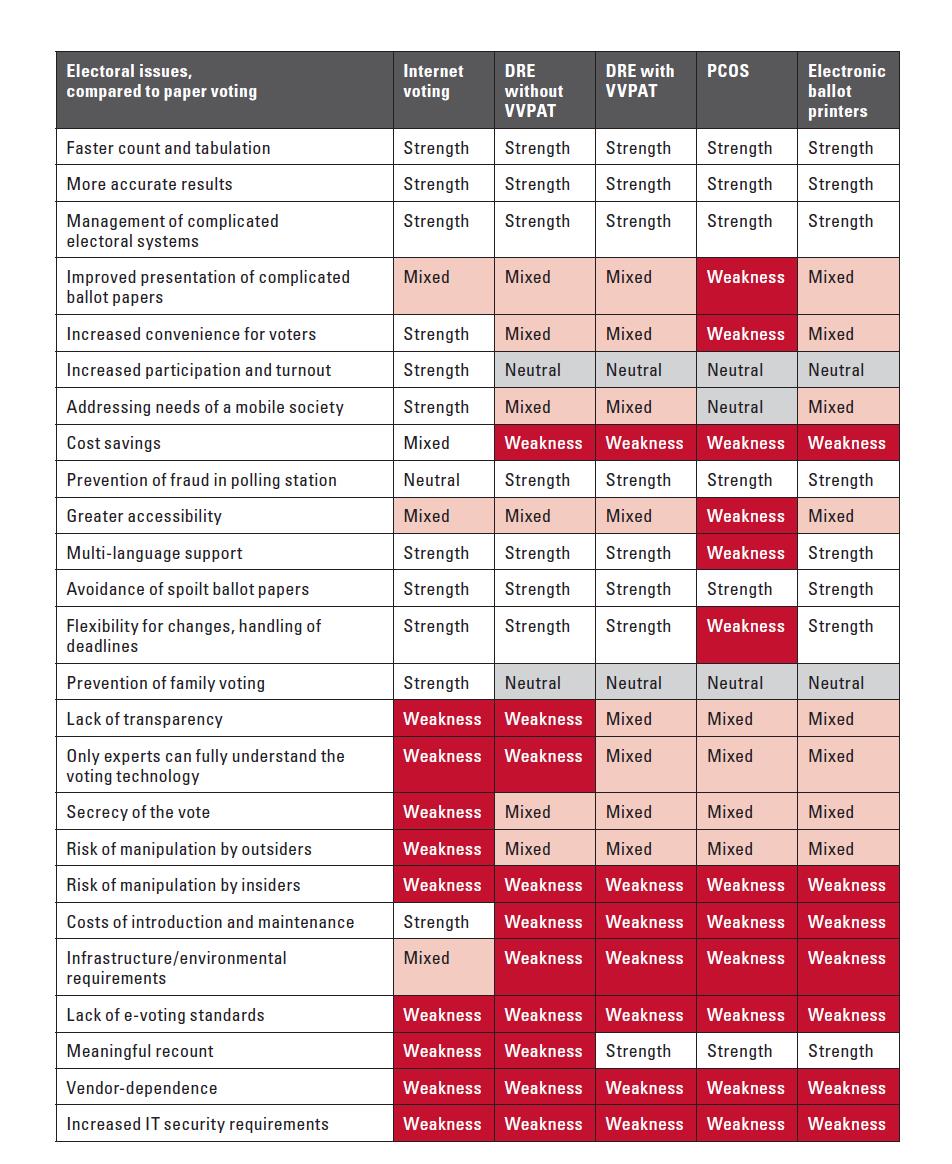
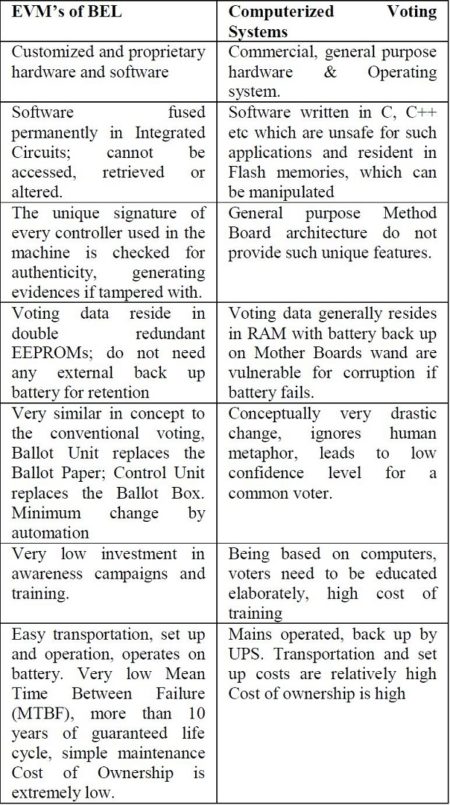
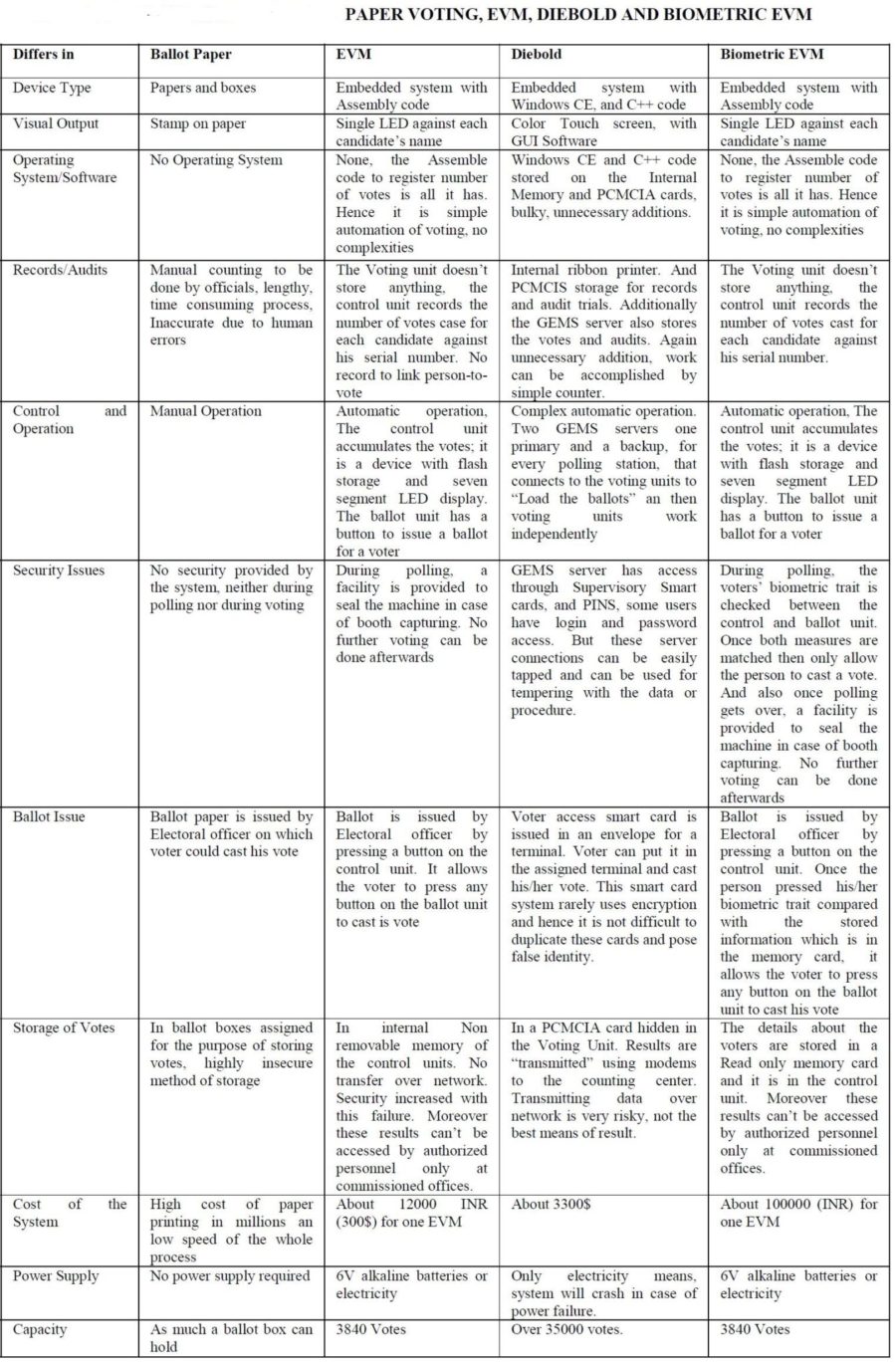

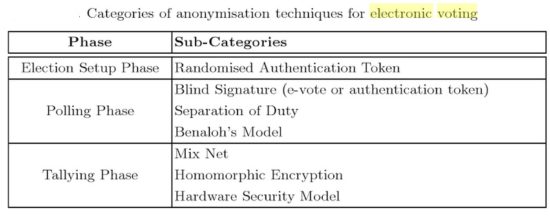
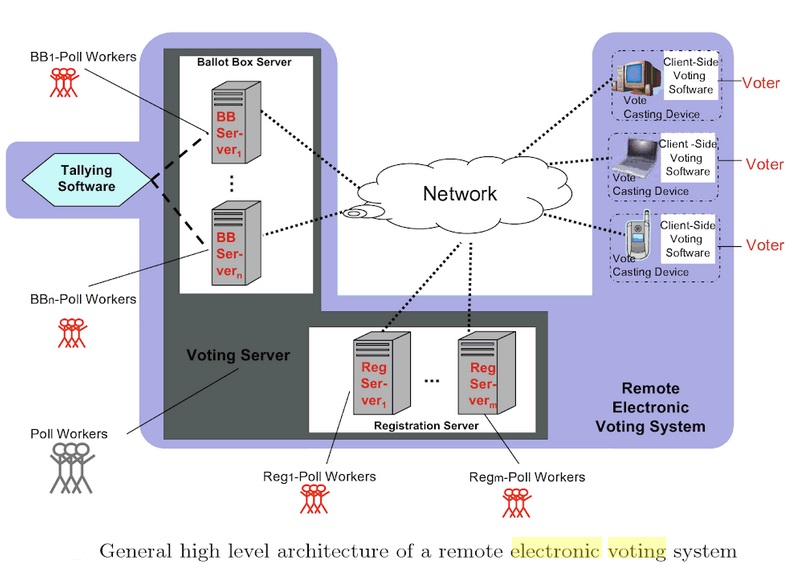
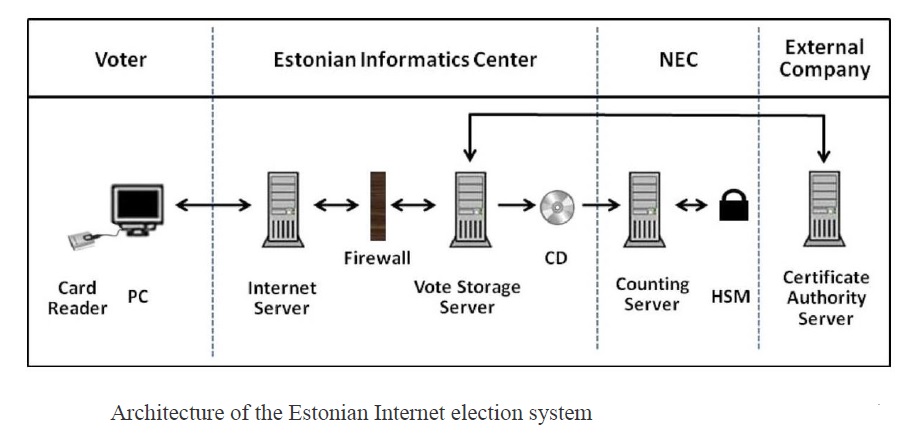

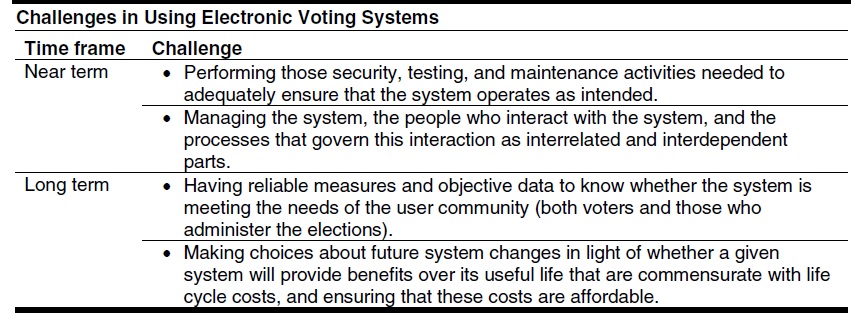

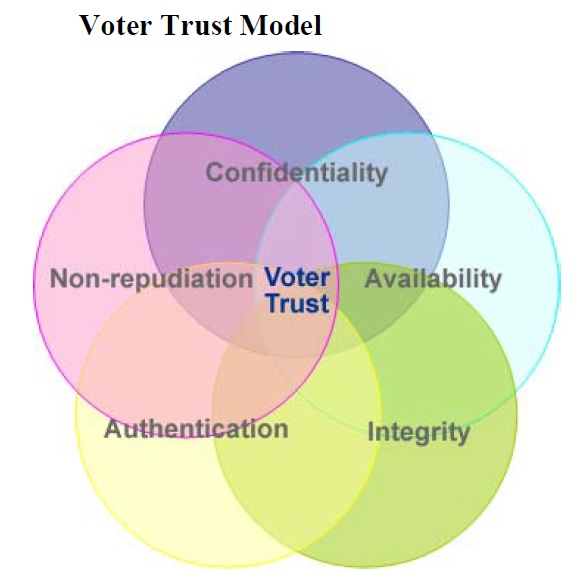
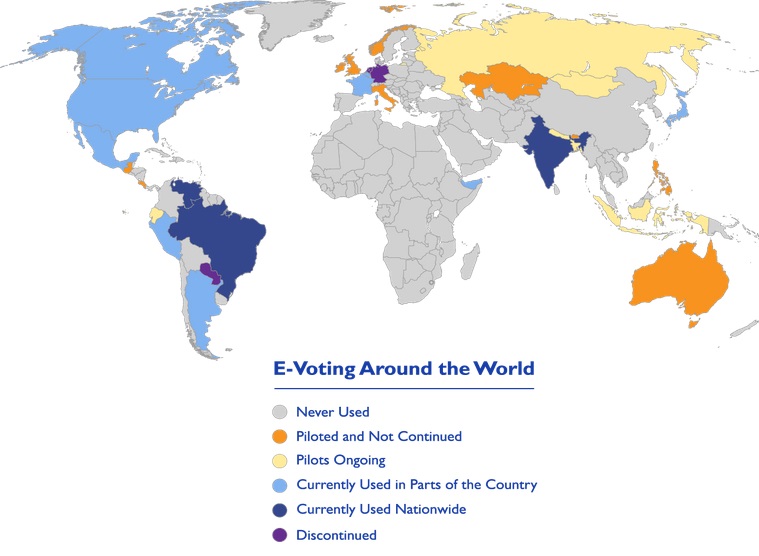
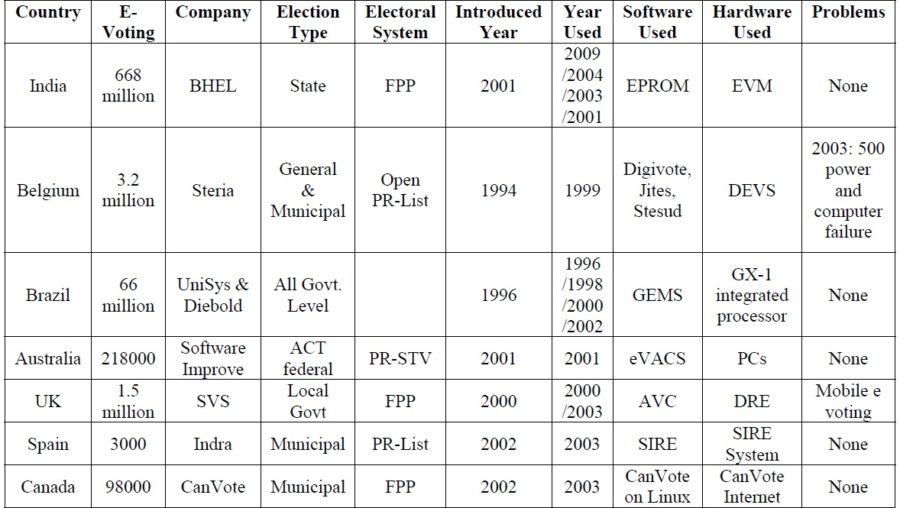
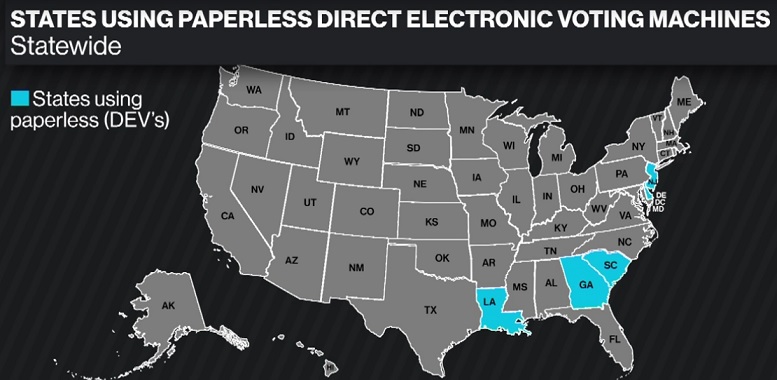
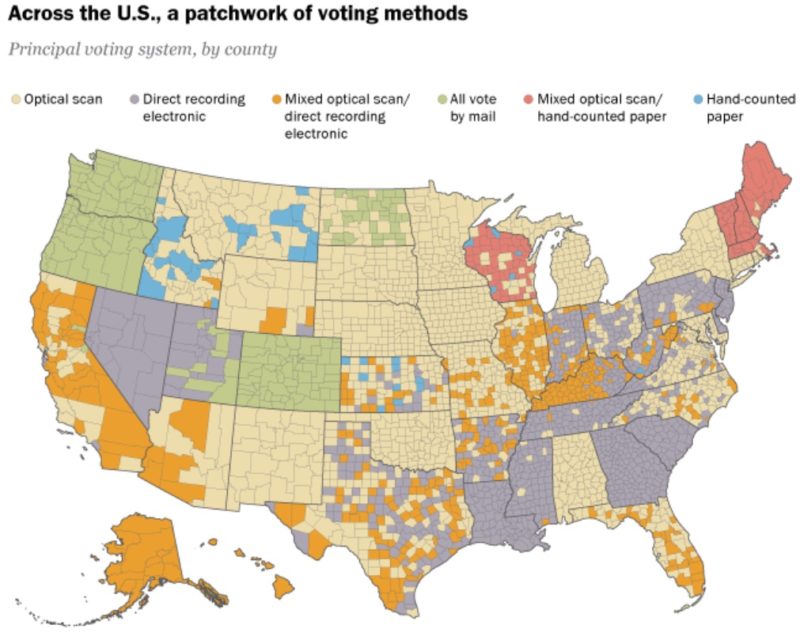

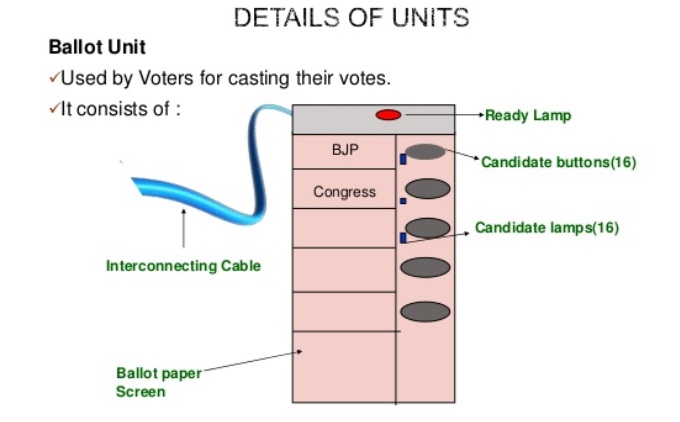
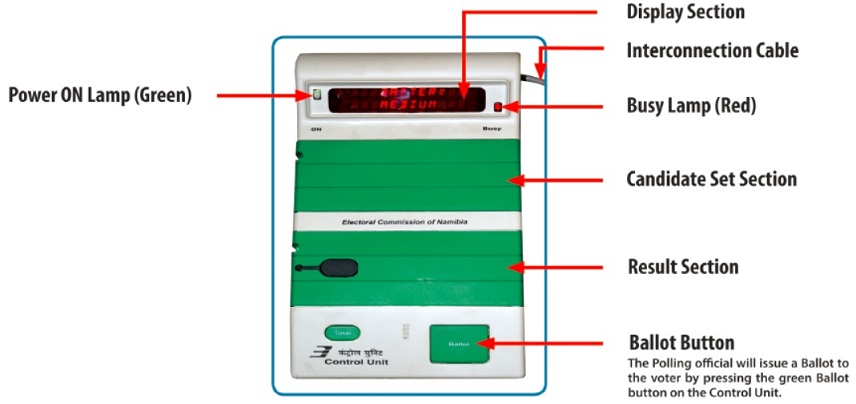

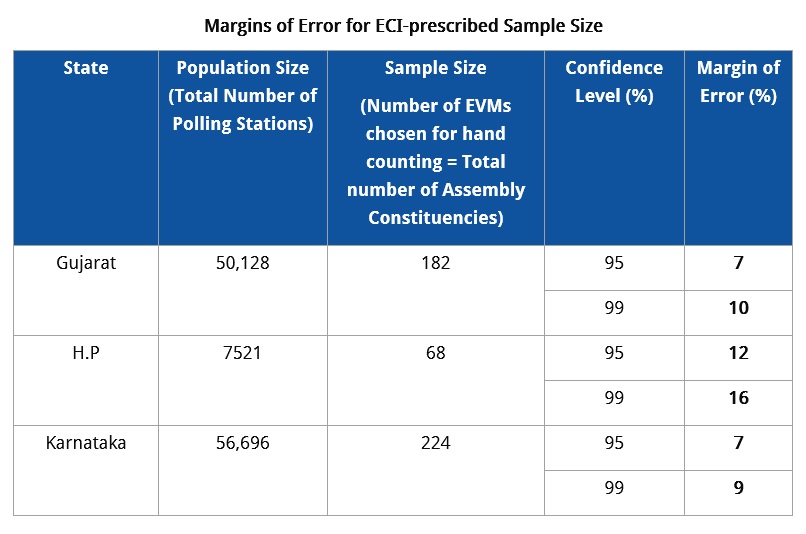

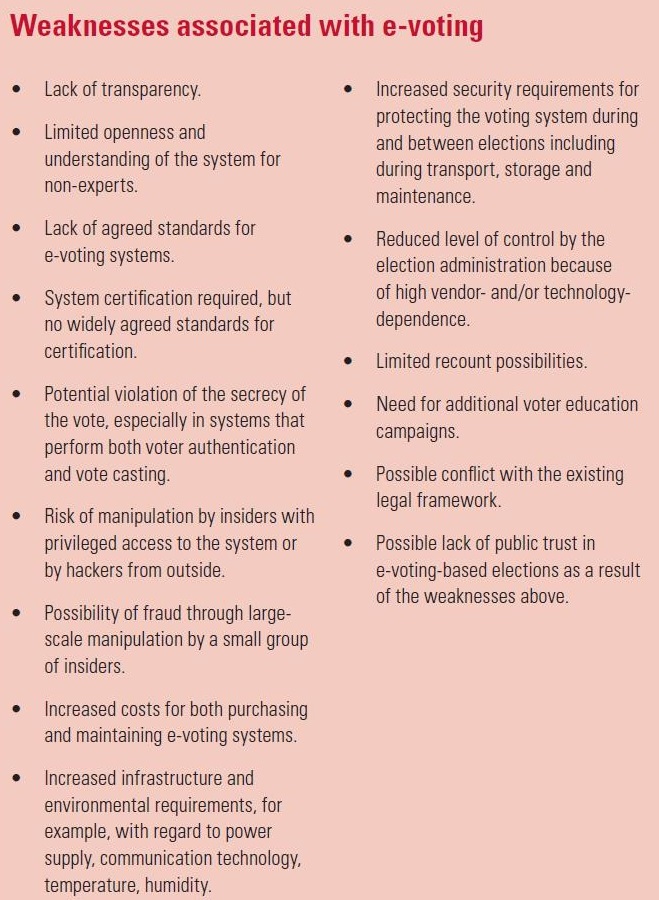
Robin here — I’ve tried fiat on-ramp and the wide token selection impressed me. The dashboard gives a complete view of my holdings.
I think the admin of this website is actually working hard in support of his web site, as here every data is quality based data.|
A great post without any doubt.
I seriously love your blog.. Great colors & theme. Did you build this site yourself? Please reply back as I’m trying to create my own website and would like to learn where you got this from or exactly what the theme is called. Thanks.
I really liked your post.Thanks Again. Keep writing.
I do trust all the ideas you’ve presented in your post. They are very convincing and can definitely work. Nonetheless, the posts are too brief for newbies. Could you please extend them a bit from subsequent time? Thank you for the post.|
You presented the truths in a straightforward yet effective manner that resonated with visitors.
The one you should have yet didn’t know about!
It’s my first time here.I found this post from google search.It’s very useful and very informative for everyone Thanks for sharing this.Keep it up.เกมยิงปลา
To uncover the greatest bonuses, you require to delve into the
details.
my web blog: 카지노사이트
excellent points altogether, you simply gained a brand new reader. What would you suggest about your post that you made a few days ago? Any positive?
I am not positive where you’re getting your info, however good topic. I must spend some time studying more or understanding more. Thanks for fantastic information I was searching for this information for my mission.
Enjoyed every bit of your post.Much thanks again. Keep writing.
Thanks a lot for the blog post. Will read on…
Very good post.Really thank you! Will read on…
Thanks so much for the blog.Really looking forward to read more. Great.
Thank you for your blog article.Really looking forward to read more. Really Great.
Hey, thanks for the blog post.Really thank you! Awesome.
I value the article. Will read on…
I love this post, I visit here often and a fan of it.
Keep up the good work.
Also visit my webpage USA
Good write-up. I absolutely love this site.
Stick with it!
This is very interesting, You’re a very skilled blogger. I have joined your feed and look forward to seeking more of your great post. Also, I’ve shared your web site in my social networks!