Dr Rajiv Desai
An Educational Blog
CYBERCRIME
CYBERCRIME:
____
This educational website was hacked by cyber-criminals on 7 February, 2017 and their threat note was posted on website as shown below:
____
Prologue:
Former Chief Justice of India R M Lodha received an email from his friend Justice B P Singh seeking immediate monetary help of Rs 100,000 for the treatment of his cousin. The email said Singh was unavailable over the phone and that was why he was emailing for help. This was not the first time they were emailing each other and an unsuspecting Justice Lodha immediately transferred the money in two transactions at the account number given in the email. Justice Lodha had the shock of his life when he later received a mail from Singh that his email was hacked and Justice Lodha was cheated of Rs 100,000 by a cybercriminal.
The world of internet today has become a parallel form of life and living. Public are now capable of doing things which were unimaginable few years ago. Internet as enabled the use of website communication, email and plenty of anytime, anywhere IT (information technology) solutions for the betterment of humankind. Technology is making tremendous advances against hunger, disease and wasteful uses of energy. But it also empowers organized crime and raises the specter of crippling cyber-attacks. The Internet deserves special attention in criminology as well as criminal law and policy, because of several characteristics: it is global, instantaneous, intrinsically transborder, digital, and enables automated information processing. Because of these characteristics, the Internet provides special opportunities to commit cybercrimes: crimes in which computer networks are the target or a substantial tool. Phishing, hacking, data theft, identity theft, online lottery, cyber-attacks, job frauds, banking frauds, cyberbullying, online blackmailing, morphing, revenge porn, child pornography, cyber grooming, cyberstalking, data diddling, software piracy, online radicalization — the web of cybercrimes is spreading across the world.
Cybercrime is highly complex, self-reinforcing, technologically advanced, geographically widespread, indiscriminate, relentless, undiminished, and unlikely to stop. It is just too easy and too rewarding, and the chances of being caught and punished are low. Cybercrime is a virtual crime with real damages. Cybercriminals at the high end are as technologically sophisticated as the most advanced IT companies, and, like them, have moved quickly to adopt cloud computing, artificial intelligence, Software-as-a-Service, and encryption. Cybercrime remains far too easy, since many technology users fail to take the most basic protective measures, and many technology products lack adequate defenses, while cybercriminals use both simple and advanced technology to identify targets, automate software creation and delivery, and monetization of what they steal. The problem of cybercrime crosses many technical, conceptual and institutional boundaries, and, due to its prevalence, has real and increasing social and economic impacts on all people. Cybercrime and data breaches are more devastating and detrimental to business than fire, floods and transit strikes. Society has reached a tipping point where digital security is converging with personal and physical security. Every facet of our society is now being targeted, and at every level.
Every second, 14 adults become the victim of some sort of cybercrime adding up to over a million victims every day, the report from Norton-maker Symantec said, with young men who access the web on their mobiles the most likely victims. But despite the large number of victims, people aren’t doing enough to stop it for themselves. Although 74 per cent of people say they’re aware of cybercrime, 41 per cent of them don’t have up-to-date security software and 61 per cent don’t use complex, regularly-changing passwords. Recently Cybersecurity Ventures predicted that cybercrime will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015. This represents the greatest transfer of economic wealth in history, risks the incentives for innovation and investment, and will be more profitable than the global trade of all major illegal drugs combined.
Crime exists since the beginning of human society, and cybercrime exists since the beginning of the digital society. Cybercriminal activity is one of the biggest challenges that humanity will face in coming decades. Cybercrime is the greatest threat to every company in the world, and one of the biggest problems with mankind. As the world is increasingly interconnected, everyone shares the responsibility of securing the growing cyberspace. To make the cyber world safe is the need of the hour. Putting up deterrent measures against cybercrime is essential in protecting critical infrastructure of the nation as well as for individuals.
______
______
Abbreviations, synonyms and key terms:
Anti-Malware—Software that prevents, detects and eliminates malicious programs on computing devices.
Antivirus—Software that prevents, detects and eliminates computer viruses.
Backdoor Trojan—A virus that enables remote control of an infected device, allowing virtually any command to be enacted by the attacker. Backdoor Trojans are often used to create botnets for criminal purposes.
Botnets—A group of Internet-connected devices configured to forward transmissions (such as spam or viruses) to other devices, despite their owners being unaware of it.
Cybercrime—Also known at computer crime or netcrime, cybercrime is loosely defined as any criminal activity that involves a computer and a network, whether in the commissioning of the crime or the target.
DoS— Denial of service attack is an attempt to interrupt or suspend host services of an Internet-connected machine causing network resources, servers, or websites to be unavailable or unable to function.
DDoS—Distributed denial of service attack. A DoS attack that occurs from multiple sources.
Malware—An overarching term describing hostile and/or intrusive software including (but not limited to) viruses, worms, Trojans, ransomware, spyware, adware, scareware, and other more, taking the form of executables, scripts, and active content.
Phishing—An attempt to acquire sensitive information like usernames, passwords, and credit card details for malicious purposes by masquerading as a trustworthy entity in a digital environment.
Rootkit—Trojans that conceal objects or activities in a device’s system, primarily to prevent other malicious programs from being detected and removed
Social Engineering—Non-technical malicious activity that exploits human interaction to subvert technical security policy, procedures, and programs, in order to gain access to secure devices and networks.
Trojan—Malicious, non-replicating programs that hide on a device as benign files and perform unauthorized actions on a device, such as deleting, blocking, modifying, or copying data, hindering performance, and more.
Zero-Day Vulnerability—a security gap in software that is unknown to its creators, which is hurriedly exploited before the software creator or vendor patches it.
SMB = Small and Medium-Sized Businesses. SMBs are defined as having less than 100 employees and between $5-$10 million in annual revenue. Such companies usually employ part-time workforce managing their clients, data and IT aspects.
SME = Small and Medium-Sized Enterprises. Also known as “mid-market”. SME’s are defined as having between 101-500 employees and between $10 million and $1 billion in annual revenue. This size organization has one or more full time employees dedicated to managing its data and IT infrastructure.
CSO = Chief Security Officer
CTO = Chief Technology Officer
CISO = Chief Information Security Officer
CIO = Chief Information Officer
CSIS = Center for Strategic and International Studies
DoS = Denial of service attacks
DDoS = Distributed Denial of Service attacks
ID = Identification
SQL = Structured Query Language
BEC = business email compromise
URI = uniform resource identifier
URL = uniform resource locator
APT = advanced persistent threat
VPN = virtual private network
IS = Information systems
IT = Information Technology = ICT = Information Communications Technology
IP = internet protocol; IP also means intellectual property
Cybercrime = cyber crime = cyber-crime
Cybersecurity = cyber security = cyber-security
Cyberattack = cyber attack = cyber-attack
_______
_______
Internet and cyberspace:
The term “networked environment” pertains to the human race being witness to and being part of one of the greatest scientific discoveries of this age: networked computers and the Internet. The first electronic general-purpose computer, the Electronic Numerical Integrator and Computer (ENIC), was built in 1946. This was bound into a network of computers that led to the early origins of the Internet in 1969.
The public was first introduced to the concepts of the Internet when a message was sent over the Advanced Research Projects Agency Network (ARPANET) from computer science Professor Leonard Kleinrock’s laboratory at the University of California, Los Angeles, after the second piece of network equipment was installed at Stanford Research Institute in 1969. The ARPANET, in particular, led to the development of protocols for internetworking, in which multiple separate networks could be joined together into a “network of networks”.
In 1982, the Internet protocol suite (TCP/IP) was standardized, and, consequently, the concept of a worldwide network of interconnected TCP/IP networks, called the Internet, was introduced. By the 1990s, millions of people were using their computers to “surf the web”, and this space came to be referred to as “cyberspace”.
According to Kerr (2003), there are “two dominant perspectives of the Internet”: on the one hand, the Internet is viewed as “a global meta-network that serves as an open platform for the transmission of information among end users that connect computers to the network;” on the other hand, the Internet is viewed “in terms of the applications it enables and the ways in which those applications affect end users”. It is the latter conception of the Internet “that leads to the conception of cyberspace as a sort of virtual reality” (or environment) whereby online activities take place.
_
Cyber and cyberspace:
Cyber- is derived from “cybernetic”, which comes from the Greek word κυβερνητικός meaning skilled in steering or governing. It is mainly used in the terms cyberspace, cyberlaw, cyberbullying, cybercrime, cyberwarfare, cyberterrorism, cybersex, and cyberdelic among others. Although it is more commonly used to describe policies and politics regarding computer systems and networks (as in the above cases), it is also widely used by many information technology industries. Cyber is now considered as a recent term in the internet era.
Cybercrime is one of the words frequently used by individuals in our contemporary Society. To understand the true meaning of cybercrime, there is the need to understand the slit meaning of Cyber and Crime. The term “Cyber” is a prefix used to describe an idea as part of the computer and Information age and “Crime” can be described as any activity that contravenes legal procedure mostly performed by individuals with a criminal motive.
In contemporary understandings, the term “Information and Communications Technology” (ICT) generally refers to computers, computer networks and systems, and disparate information distribution or delivery technologies such as land and submarine cables, satellites, the telephone, and even television. Today, these networks, technologies, and their delivery systems are increasingly referred to as “cyberspace”, the technological substrate of modern societies made up of several interconnected layers—physical, syntactic, semantic, and pragmatic, with the physical and pragmatic layers subject to certain sovereign governmental jurisdiction and controls. Framed by the use of electronics and the electromagnetic spectrum, cyberspace enables “the creation, storage, modification, exchange and exploitation of information via interdependent and interconnected networks using information communication technologies”. While the Internet is often conflated with cyberspace, it is just one part of the global technological substrate. And while it connects more than six billion devices, it is not a singular system, but rather involves many layers of distinct “functions” and “tasks”, the latter carried out by actors as distinct as private industry, technical institutions, States, or through multilateral governmental coordination.
_
Since the beginning of civilization, man has always been motivated by the need to make progress and better the existing technologies. This has led to tremendous development and progress which has been a launching pad for further development of all the significant advances made by mankind from the beginning till date. Probably the most important of them is the development of Internet. Internet is a global network of computers, all speaking the same language. Internet is believed to be full of anarchy and a system of law and regulation therein seems contradictory. However, Cyberspace is being governed by a system of law called Cyber law. Cyber law is a generic term which refers to all the legal and regulatory aspects of Internet.
The nature of the internet is quite paradoxical and even contradictory. On the one hand, it has been considered and described as the tool that provides an almost infinite capability for wide human interaction without borders and barriers and at any time of any day, a true and genuine open virtual market of ideas and information that can be shared instantly across the globe. On the other hand, in sharp contrast, the internet can also be exactly the opposite: an implacable and super-efficient tool giving multiple parties the ability to conduct 24/7 surveillance of people, places, movements, communications and exchanges. It can track the purchases of millions of consumers worldwide, producing vast information on lifestyle, eating and drinking habits, personal hygiene and sexual behaviors that can then be used against the citizen for employment, promotion, insurance, accidents investigations, criminal prosecution and, at times, extortion. It is used as a marketing, advertising, news filtering and propaganda machine to diffuse certain approved messages, indoctrinate, and control the mind of a people; and much more.
The Internet is one of the fastest-growing areas of technical infrastructure development. Today, information and communication technologies (ICTs) are omnipresent and the trend towards digitization is growing. The demand for Internet and computer connectivity has led to the integration of computer technology into products that have usually functioned without it, such as cars and buildings. Electricity supply, transportation infrastructure, military services and logistics – virtually all modern services depend on the use of ICTs. The influence of ICTs on society goes far beyond establishing basic information infrastructure. The availability of ICTs is a foundation for development in the creation, availability and use of network-based services. E-mails have displaced traditional letters; online web representation is nowadays more important for businesses than printed publicity materials; and Internet-based communication and phone services are growing faster than landline communications.
The availability of ICTs and new network-based services offer a number of advantages for society in general, especially for developing countries. ICT applications, such as e-government, e-commerce, e-education, e-health and e-environment, are seen as enablers for development, as they provide an efficient channel to deliver a wide range of basic services in remote and rural areas. ICT applications can facilitate the achievement of millennium development targets, reducing poverty and improving health and environmental conditions in developing countries. Given the right approach, context and implementation processes, investments in ICT applications and tools can result in productivity and quality improvements. In turn, ICT applications may release technical and human capacity and enable greater access to basic services. In this regard, online identity theft and the act of capturing another person’s credentials and/or personal information via the Internet with the intent to fraudulently reuse it for criminal purposes is now one of the main threats to further deployment of e-government and e-business services.
The costs of Internet services are often also much lower than comparable services outside the network. E-mail services are often available free of charge or cost very little compared to traditional postal services. The online encyclopedia Wikipedia can be used free of charge, as can hundreds of online hosting services. Lower costs are important, as they enable services to be used by many more users, including people with only limited income. Given the limited financial resources of many people in developing countries, the Internet enables them to use services they may not otherwise have access to outside the network.
_
Characteristics of Cyberspace:
Two of the key characteristics of cyberspace are the vast number of users and the borderless nature of the Internet, where an act in one continent permeates to other distant continents, sometimes within minutes. These characteristics also indicate that business can be conducted faster without physical travel or a physical presence, with quicker responses across vast distances, and possibly have an impact on a global audience.
While this technological advance introduced plentiful benefits to society, the downside was not far behind. The changes created by computing and networking have manifested a new environment in which people increasingly gather in cyberspace to interact socially and commercially, but these interactions also have provided an ideal opportune platform for the perpetration of crimes. The characteristics of cyberspace have not only provided a whole new class of targets for crime, but also have led to an increase in the number of cyber-savvy individuals with a ready means to commit crimes that have widespread impact.
As one commentator observes:
“Growth of cyber criminals is occurring on two axes: first, the number of people who are technologically savvy enough to commit cybercrimes is growing exponentially; second, a derivative market in cybercrime appears to be growing as ‘enablers’ — ‘persons who use their technical expertise to create and then sell to others easy-to-use tools’ — make it possible for non-technologically savvy people to engage in cybercrime.”
The Internet has been compared to an “unsafe highway”. This analogy “is an apt reminder of the inherent decentralized and open architecture of the Internet”. The omnipresent nature of the Internet makes it an ideal platform for business and social interactions, but also makes it highly vulnerable to those seeking to commit mischief or indulge in gross misuse of web technologies.
Troublemakers in cyberspace seek systems to infiltrate and misuse. Just for the heck of it, or as an intellectual challenge, there are some who try to hack into a computer to launch a worm or virus that could cripple a business organization or even disrupt an entire nation’s business for the day.
The need of the hour is for all Internet users — individuals and businesses alike — to gear up to the potential dangers of cyberspace and its ability to cause major security incidents. Developing measures to combat this threat is vitally important, because one thing is for sure: a poorly developed security system is a hopelessly inadequate safeguard against cyber-attacks, and lack of security measures poses a severe threat to the survivability and the profitability of the company’s business operations.
While the digital world brings enormous benefits, it is also vulnerable. The promise of today’s interconnected world is immeasurable. However, the benefits that stem from this promise, face real threats. These threats can have different origins – including criminal, politically motivated, terrorist or state-sponsored attacks as well as natural disasters and unintentional mistakes. We have to be aware of the increasing amount of opportunities to commit crime facilitated, enabled or amplified by the Internet. For many people, being online is no longer the exception but the norm, often without the individual being aware. This creates a broader attack surface and multiple areas of peoples’ lives for criminals to fraud.
Cyberspace radically undermines the relationship between legally significant (online) phenomena and physical location. The rise of the global computer network is destroying the link between geographical location and: (1) the power of local governments to assert control over online behaviour; (2) the effects of online behaviour on individuals or things; (3) the legitimacy of the efforts of a local sovereign to enforce rules applicable to global phenomena; and (4) the ability of physical location to give notice of which sets of rules apply.
Faced with their inability to control the flow of electrons across physical borders, some legislators strive to inject their boundaries into electronic mediums through filtering mechanisms and the establishment of electronic barriers. Others have been quick to assert the right to regulate all online trade insofar as it might adversely impact local citizens.
_
In 2011, at least 2.3 billion people, which is the equivalent of more than 1/3th of the world’s total population, had access to the Internet. There are 4.39 billion internet users in 2019. In 2016, there were 6.4 billion connected devices and this will reach 20.8 billion by 2020.
_
Risks of internet:
The Internet was created in the 1960s, but it only caught the attention of governments and criminologists in the mid-1990s when it became a large-scale medium for the general public. Before, the focus had been on computer-related crime. Now, the buzzword is cybercrime, stressing the fact that computer networks – ‘cyberspace’ – raised new questions for criminal law and policy. Perhaps the Internet even changes the nature of crime itself, as witnessed by the title of a seminal work by David Wall (2007), Cybercrime – The Transformation of Crime in the Information Age.
The Internet deserves special attention because of several characteristics. It is global and allows for real-time connections between people regardless of their location. Therefore, time, distance, and national borders are much less important than in traditional crime. The Internet, being a digital network, allows for processing data and information in automated ways, almost at the speed of light, and on an unprecedented scale. Because of these characteristics, the Internet provides special opportunities to commit crimes, which are usually called cybercrimes. Cybercrime can be defined as crime in which computer networks are the target or a substantial tool. Cybercrime deserves specific attention from a criminological perspective, because of the unique character of the Internet. ‘Routine activity theory (and, indeed, other ecologically oriented theories of crime causation) thus appears of limited utility in an environment that defies many of our taken-for-granted assumptions about how the socio-interactional setting of routine activities is configured’ (Yar, 2005, p. 425).
_
The introduction of ICTs into many aspects of everyday life has led to the development of the modern concept of the information society. This development of the information society offers great opportunities. Unhindered access to information can support democracy, as the flow of information is taken out of the control of state authorities (as has happened, for example, in Eastern Europe and North Africa). Technical developments have improved daily life – for example, online banking and shopping, the use of mobile data services and voice over Internet protocol (VoIP) telephony are just some examples of how far the integration of ICTs into our daily lives has advanced.
However, the growth of the information society is accompanied by new and serious threats. Essential services such as water and electricity supply now rely on ICTs. Cars, traffic control, elevators, air conditioning and telephones also depend on the smooth functioning of ICTs. Attacks against information infrastructure and Internet services now have the potential to harm society in new and critical ways.
Attacks against information infrastructure and Internet services have already taken place. Online fraud and hacking attacks are just some examples of computer-related crimes that are committed on a large scale every day. The financial damage caused by cybercrime is reported to be enormous. In 2003 alone, malicious software caused damages of up to USD 17 billion. By some estimates, revenues from cybercrime exceeded USD 100 billion in 2007, outstripping the illegal trade in drugs for the first time. Nearly 60 per cent of businesses in the United States believe that cybercrime is more costly to them than physical crime. These estimates clearly demonstrate the importance of protecting information infrastructures.
_
Invented in 1989, the World Wide Web is home to around 1.7 billion websites today. This unimaginable expansion has brought the world closer and shrunk it into a small global village. The internet is responsible for fast forwarding the world’s technological progress and advancing us hundreds of years ahead. However, as the world has made a shift from the physical to the digital landscape, security threats have also changed from physical to cyber. Cybercrimes have accounted for trillions of dollars in losses, as per Juniper research the amount in 2019 was $2 trillion. With such vulnerabilities revolving online, companies are investing heavily in cyber security and training employees, particularly regarding online scams and ransomware attacks. It is estimated that by 2027, global spending on cyber security will reach $10 billion. In this age of IoT, where there is no escaping the internet, it is very important to understand the importance of cyber security and more importantly, the types of cyber security threats around you!
__
__
With the opening of information systems to the global Internet and with their thorough infusion into the operation and management of business and government organizations and into the infrastructure of daily life across the world, information security issues have moved to the forefront of concerns about global well-being. Information systems security is responsible for the integrity and safety of system resources and activities. Most organizations in developed countries are dependent on the secure operation of their information systems. In fact, the very fabric of societies often depends on this security. Multiple infrastructural grids—including power, water supply, and health care—rely on it. Information systems are at the heart of intensive care units and air traffic control systems. Financial institutions could not survive a total failure of their information systems for longer than a day or two. Electronic funds transfer systems (EFTS) handle immense amounts of money that exist only as electronic signals sent over the networks or as spots on storage disks. Information systems are vulnerable to a number of threats and require strict controls, such as continuing countermeasures and regular audits to ensure that the system remains secure.
Although instances of computer crime and abuse receive extensive media attention, human error is estimated to cause greater losses in information systems operation. Disasters such as earthquakes, floods, and fires are the particular concern of disaster recovery planning, which is a part of a corporate business continuity plan. A contingency scheme is also necessary to cover the failure of servers, telecommunications networks, or software.
_
_
The internet was born around 1960’s where its access was limited to few scientists, researchers and the defense only. Initially the computer crime was only confined to making a physical damage to the computer and related infrastructure. Around 1980’s the trend changed from causing the physical damaging to computers to making a computer malfunction using a malicious code called virus. In 1996, when internet was launched for the public, it immediately became popular among the masses and they slowly became dependent on it to an extent that it has changed their lifestyle. The focus of the computer crime shifted from merely damaging the computer or destroying or manipulating data for personal benefit to financial crime. These computer attacks are increasing at a rapid phase. Every second around 25 computers became victim to cyber-attack and around 800 million individuals were affected by it till 2013. CERT-India has reported that around 308371 Indian websites were hacked till 2013.
A common man who is a user of computer, internet and cell phone is unaware of the traps set by clever criminals in the Cyberspace and the ways to get rid of them. Forging documents is one of the best examples of this kind of a cybercrime. Image morphing, circulation of defamatory comments and threats through mobile phones, taking photographs without consent and consistent blackmailing may be some other examples. With the rise in the internet users cybercriminals are also increasingly targeting cyber space to commit their illegal designs.
______
______
Cyber deviance:
There is an alarming trend of individuals behaving inappropriately with information technology in both organizational and personal settings. For example, in a work context individual are breaking repeatedly security protocols (Hovav et al. 2011) leading to the compromise of sensitive customer and important organizational data resources. Information systems (IS) researchers have studied the manners by which employees use, and misuse, information technology within organizations (Warkentin et al. 2009). Alternatively, in a non-work context, attention has been given to digital media piracy (Siponen et al. 2012) which continues to plague organizations. These examples illustrate some unacceptable behaviors exhibited by cyber citizens (Anderson et al. 2010) – both in the work and non-work settings.
Typically, the boundaries of acceptable and unacceptable cyber behavior are defined by government authorities, who develop laws around specific illegal online behaviors; and businesses, who detail inappropriate actions in their terms of service agreements. Past research has shown that even with detailed guidelines, employees continue to cause breaches in security (Harris 2012) and these actions are greatly influenced by the behaviors of their coworkers (Gallivan et al. 2005).
Alternatively, in a non-work environment, computer users operate within a precarious social and technological environment where the guidelines on appropriate behavior are vague (Nowak 2011). In such an ill-defined context, individuals tend to refer to accepted social norms as a guide, rather than try to understand the disparity between laws and policies (Morrison 1994).
_
Table below shows cyber deviance among college students in a study:
_
Research in criminology, sociology, and management, has focused on deviant behaviors with technology, termed cyber deviance. This term refers to inappropriate or criminal behavior in a digital context (Holt et al. 2010). Deviant activities often reflect the individual’s perverse behavior through email, news group messages, and chat room conversations. Technical solutions are only marginally effective as deviant cyber behavior continues to proliferate (Rogers et al. 2006). Research has examined individual factors, such as self-control, in order to explain cyber deviant behaviors (Hinduja et al. 2008). Social factors have begun to be examined through the use of social learning theory and social cognitive theory to explain the ways in which attitudes and beliefs influence cyber deviance (Jacobs et al. 2012). Although studies that examine the individual, social, and technical factors have provided insight into cyber deviance behavior, they have not considered such behavior as part of cyber citizenship, where individuals behave in an ethical and productive manner in online environments. Additionally, recent IS research has begun to explore alternative ways to influence social norms and attitudes on individual behaviors in online environments in order to create more conscientious cyber citizens (Anderson et al. 2010).
_
_
Cyber-deviance is a large umbrella capturing a wide range of behaviors from web surfing, time, and productivity theft to more serious forms of cyberbullying, virtual harassment, and disclosure of proprietary or sensitive information. Organizations are financially, legally, operationally, and morally motivated to mitigate workplace cyber-deviance, especially the types which also bear legal or societal costs. Yet it persists.
Weatherbee (2010) adapted Robinson and Bennett’s deviance typology for computer-mediated communications to: production cyber-deviance, property cyber-deviance, political cyber-deviance, and personal aggression (personal cyber-aggression).
- Political cyber-deviance is characterized by minor counterproductive work behaviors committed online at an interpersonal level. Example behaviors include: e-politics, playing zero-sum games, selective informing, blame shifting, and gossip (Weatherbee, 2010). Whistleblowing and cyber-smearing are other examples of political cyber-deviance, both of which may occur on social media, which may have wider social implications for the organization than more traditional forms of whistleblowing or smear campaigns (Workman, 2012). Whistleblowing occurs through stealing and exposing private information (Väyrynen, Hekkala & Liias, 2013). Another behavior which may be considered as political cyber-deviance from an organizational perspective (not societal perspective) is sending union organizing e-mails using a company supplied home-computer (Cole, 2002).
- Production cyber-deviance is the misuse of technology (Weatherbee, 2010), and violates the organizational norms regarding minimal quantity of production; it occurs when employees waste time using company resources. Cyberloafing, personal email, chain email, online banking, and online shopping are examples of production cyber-deviance (Weatherbee, 2010). Similar behaviors include: cyberslacking (Greengard, 2000), personal web usage (Mahatanankoon, Anandarajan & Igbaria, 2004), and non-work related computing (Pee, Woon & Kankanhalli, 2008). Cyberloafing (the most studied) is defined as the “voluntary act of employees using their companies’ internet access during office hours…for personal purposes” (Lim, 2002, p. 675), which consists of two dimensions: personal email and browsing the web. Additional dimensions have since been proposed to reflect the expanded use of the Internet and Web 2.0 activities (online videos, blogging: e.g., Anandarajan, Devine & Simmers, 2004).
- Property cyber-deviance is the damaging of company property or the theft and leaking of important company information using information technologies (Johnson, 2011). Examples are: online gambling, web pornography, software piracy, data diddling (the removal or alteration of data at time of entry), and hacking (Weatherbee, 2010). In addition, property cyber-deviance includes employee behaviors that harm the reputation of employers, such as blogs or social media posts from personal accounts, and intentionally using technology to provide poor customer service (excessive waiting or wrong phone transfers: Skarlicki, van Jaarsveld & Walker, 2008). Tampering with employers’ information technologies is another form of property cyber-deviance, like hacking into company databases to access user activity records in the company database to hide prohibited Internet activity, or even add inappropriate activity to the log of other employees (Barlow, Bean & Hott, 2003).
- Personal cyber-aggression consists of a range of behaviors, and is defined as computer-mediated communications that are “either used intentionally for the expression of aggression, or where it is used in such a way that it results in the perception of aggression by a focal target” (Weatherbee, 2010, p. 37). These behaviors are interpersonal; they target an individual or group of individuals. Personal cyberaggression includes a range of behaviors from low-intensity cyber-incivility, virtual harassment, to severe intensity cyber-bullying and cyberstalking (e.g., Barnes & Biros, 2007; D’Cruz & Noronha, 2013; Ford, 2013; Giumetti, McKibben, Hatfield, Schroeder & Kowalski, 2012). The terms vary across national borders; cyber-mobbing (Germany), virtual or cyber-bullying (Italy), and harassment via Internet or mobile phone (Spain) are used to describe the same behavior of ‘cyber-bullying’ (Nocentini, et al., 2010). Other example behaviors that constitute personal cyber-aggression are: cyber-aggression, e-harassment, identity theft (Weatherbee, 2010).
_
How to reduce youth participation in cyber deviance:
A study found that youth who have lower levels of self-control and more frequent association with deviant peers are more likely to take part in both on-line and off-line deviant activities. Strategies can focus on how to help youth to develop self-control and make good decisions when opportunities for engaging in wrongdoing are presented.
Parents need to closely monitor their children’s activities with peers in on-line (Mesch, 2009) and off-line settings (Hay, 2001). For instance, parental mediation techniques, particularly evaluative mediation that utilizes open discussion regarding Internet usage, evaluation of web content, and setting rules for Internet use and permitted and forbidden websites for children, can serve as a protective factor for children’s on-line misbehavior such as cyberbullying (Mesch, 2009). Further, prior research found that adolescents whose parents monitored and regulated their on-line activities were less likely to disclose personal information (e.g. full name, e-mail address, instant message name, school name) (Rosen, 2007; Rosen, Cheever, & Carrier, 2008).
Existing studies have used proxy measures of parental supervision such as location of computer use within the household. Research has shown that locating the computer in a public place (e.g. living room, kitchen), where visibility of detecting deviant activities is high, can be a helpful way to monitor youth misbehaviors (Bossler, Holt, & May, 2012; Marcum, 2008; Marcum, Higgins, & Ricketts, 2010a). It allows parents to better monitor the type of deviant activities in which youth engage using computers, and to intervene when they participate in deviant behaviors (Bocji, 2004). If the computer location was in a private location, it would be more challenging to monitor their activities since the visibility of detecting a deviant activity is low. Other preventative measures such as use of filtering or security software was shown to be ineffective measure to protect individuals from cybercrime victimization (Bossler & Holt, 2009; Bossler et al., 2012; Ngo & Paternoster, 2011).
With regard to on-line victimization, monitoring presence of a parent or guardian in the room during one’s Internet use influences the likelihood of receipt of sexually solicitation as well as non-sexual harassment (Marcum, Higgins, & Ricketts, 2010a; Marcum, Higgins, & Ricketts, 2010b). In addition, the study by Wolfe, Marcum, Higgins, & Ricketts (2014) found that two supervision-based routine activities, specifically school cell phone rules and family cell phone plan, to be significantly linked to receipt of sexually suggestive messages or images via texting. This study illustrated that adolescents whose cell phone contract is included in their family’s cell phone plan are less likely to received sexually explicit images or videos on their mobile phone, compared to those with cell phone contracts independent of their family’s plan. Yet, the study by Moore, Guntupalli, & Lee (2010) revealed that parental regulation of Internet use and on-line activities was not significantly linked to on-line harassment victimization.
Parents exert considerable influence on adolescents’ involvement in delinquent behaviors (Warr, 2002). Gottfredson and Hirschi (1990) assert that crime offers immediate, short-term benefits such as small monetary gain, brief sexual pleasure, or excitement. When opportunities for law-breaking are presented to individuals with low self-control, it is likely that they will be “unable to resist the easy, immediate gratification that crime and analogous behaviors seductively, and almost ubiquitously, present in everyday life” (Pratt & Cullen, 2000, p. 932). A person with low self-control is likely to be incapable of considering the long-term consequences and benefits associated with his or her acts. Given that ineffective parenting during early childhood contributes to low self-control (Gottfredson & Hirschi (1990), parents can serve as agents to develop self-control in youth but also influence their involvement in deviant activities.
Parents can educate their children about the costs and harms associated with deviant and criminal behaviors both off-line and on-line. Although individuals can recognize the costs as a result of participating in real world crime, it may be less apparent for cybercrime. Hinduja (2006) points out that unlike traditional street crime, two factors that may deter one’s participation in deviant behavior is absent with digital piracy. First, there is not a tangible loss or harm that is visible to potential and actual perpetrator of digital piracy. Secondly, with cybercrime, youth may not be fully aware of the legal punishment that may deter them from engaging in wrongdoings. This is particularly true for digital piracy. Using the bit-torrent technology and peer-to-peer file sharing, adolescents could easily download music, movie, or software files and share with peers via the Internet, and believe that there is no harm being done with this behavior (Higgins, 2004). Parents need to educate their children about seriousness of this behavior as well as consequences that one can suffer from intellectual property theft of digital goods. Parents also need to closely monitor their children’s on-line behaviors and consistently sanction them if they engage in misbehaviors (Gottfredson & Hirschi, 1990). Hinduja & Patchin (2012) make recommendations for parents and educators to immediately inform the perpetrators of on-line harassment about the consequences for harassing and bullying other off-line and on-line. Often, youth who engage in on-line harassment are unlikely to realize the costs and benefits of their actions.
Based on prior research examining cybercrime victimization, increasing awareness and educating youth about dangers associated with on-line harassment and other victimization (e.g. malware, identity theft) may have a deterrent impact on their future behaviors (Bossler & Holt, 2009, 2010; Bossler et al., 2012; Holt & Turner, 2012). Individual awareness and knowledge can play a role in reducing and preventing one’s involvement in cybercrime. Hence, developing and promoting programs that educate youth and children of the risks of engage in cyber deviance and associating with deviant peers on-line may help to decrease youth participation in cybercrime offending, as opposed to improving harsh punishments (Bossler & Holt, 2009; Bossler et al., 2012).
In addition to parents, teachers and school administrators can work together in create classroom structure that allows them to adequately monitor and regulate deviant use of computers, including socialization with deviant friends. They can also develop educational programs to educate the school youth concerning how their decisions to participate in deviant peer activities can negatively affect their lives in the short and long term. Helping youth to understand what constitutes appropriate behaviors when using the Internet can be an important aspect of educating the children to be responsible citizens in cyberspace (Fleming, Greentree, Cocotti-Muller, Elias, & Morrison, 2006). Through classroom activities and instructions, teachers and schools can address some of the key issues that youth are facing in cyberspace such as on-line safety and privacy, copyright protection and intellectual property theft, and responsible use of technology. Parents and teachers must work in tandem to raise awareness about the costs and dangers associated with criminal and deviant behaviors on-line.
Peers are influential in whether an individual approves of and participates in deviant activity (Akers, 1998). Peer associations provide the environment for youth to not only observe and imitate behavioral models but also reinforce beliefs and attitudes that support the behavior. With regards to deviance in the real world, parents and teachers attempt to disrupt the association with deviant peers by physically separating the youth from their peers in the classroom and other school settings (e.g. playground). Parents can also limit their physical interaction with deviant peers during after school hours as well as in the evenings and weekends. With the emergence of social media and other electronic communication, youth are able to socialize with peers on-line at any time and location. Based on the consistent finding that association with deviant peers increases the odds of all types of deviance, parents and teachers need to keep track of both off-line and on-line peer networks. Parents also need to monitor and regulate their use of social networking sites such as Facebook and Twitter in order to limit the opportunity to engage with deviant peers on-line. Research has shown that association with deviant peers and maintenance of social networking is a significant predictor of involvement in cybercrime (Bossler et al., 2012; Mesch, 2009). Specifically, parents could establish rules and guidelines, against socialization with deviant peers via the Internet and social media, by which they all abide. If they associate with deviant peers on-line, parents can apply sanctions for not complying with parental rules and guidelines. Hinduja & Patchin (2013) found that if a youth internalized that their deviant behavior will not go unpunished by parents or teachers, he or she is less likely to participate in cyberbullying. Further, teachers and school administrators can develop educational programs that promote the risks and consequences from “hanging out” with peers who engage in deviant or criminal activities on-line (Bossler & Holt, 2010). All of these aforementioned measures can be taken to discourage their association with deviant peers on-line. If associations with deviant peers on-line can be reduced, in turn, this can discourage youth participation in delinquent and criminal activity (Meldrum & Clark, 2013; Weerman et al., 2013). Policies should focus on effectively monitoring and limiting opportunities for virtual interaction with deviant peers.
Given that opportunities for youth to engage in cyber deviance and crime is ample, government, industry and parents can collaborate to produce strategies that protects children and youth from being involved in deviance on-line. The government could also closely cooperate with the Internet service providers (ISP) to identify those who engage in illegal behaviors such as digital piracy and hacking. If the perpetrators are minors, the ISPs can notify the parents or caregivers about their children’s wrongdoings. Through collaboration between law enforcement, industry, ISPs, and parents, efforts can be made to deter youth from beginning or continuing their participation in criminal activities on-line.
Because offenders are short-sighted and unable to consider the long-term consequences of their acts, intervention programs that aim to reduce the opportunities and rewards of deviant behavior can enhance the level of self-control. Gottfredson & Hirschi (1995) added that “programs that increase the difficulty, even minimally, with which crimes can be undertaken or that enhance the probability of immediate intervention will reduce crime” (p. 32). Considering the early exposure to technology at an increasingly earlier age, efforts to help youth to develop self-control and make good choices when faced with offending opportunities must be made early in life.
______
______
Introduction to cybercrime:
Crime is a relative phenomenon, universal in nature and essentially all societies from ancient to modern have been evidently demonstrating its presence. Each society have been providing its own description of criminal behavior and conduct made punishable by express will of the political community ruling over the society and it was always influenced by religious-social-political-economical values prevailing in the given society. Thus from time immemorial the behavior that attracts ‘penal liability’ was influenced and characterized by overall outcome of these standards. Medieval period had evidenced the eras of renaissance and restoration, which delivered new, and a fresh look to ‘crime’. The concepts like utilitarian, positive approach, analytical thinking, principles of natural justice, thoughts of lessie faire, hedonistic philosophy, and pain and pleasure theory were outcome of this period which helped to open new horizons for the study of crime. Later period paved the way for scientific & industrial revolution and rational way of interpretation dominated the thinking. Just as concept of crime has undergone change with the growth of Information Technology so the categories of criminals who engage in such crimes.
_
The continuing evolution and proliferation of computer technology has created a new class of threats — “cyberthreats” – that societies must confront. These cyberthreats can be broadly defined as using computer technology to engage in activity that can undermine a society’s ability to maintain internal or external order. Historically, societies have utilized a two-pronged strategy for maintaining the order they require to survive and prosper : They maintain internal order by articulating and enforcing a set of proscriptive rules (“criminal rules”) that prevent the members of a society from preying upon each other in ways that undermine order, e.g., by killing, robbing, committing arson, etc. Societies maintain external order by relying on military force (“war”) and, to an increasing extent, international agreements.
Computer technology erodes the empirical realities that generated and sustained this dichotomous approach to maintaining internal and external order. The traditional approach outlined above assumes societies occupy a territorially-defined physical reality in which threats are easily identified as being either “internal” (crime) or external (war). Computer-mediated communication erodes the validity of this assumption because it makes territory increasingly irrelevant. In the twenty-first century, those bent on undermining a society’s ability to maintain order can use the Internet to launch virtual attacks from almost anywhere in the world. And they can launch attacks that may not fit neatly into the internal-external threat dichotomy.
_
Cybercrime is a term used to broadly describe criminal activity in which computers or computer networks are a tool, a target, or a place of criminal activity and include everything from electronic cracking to denial of service attacks. It is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. The cybercrime can halt any railway where it is, it may misguide the planes on its flight by misguiding with wrong signals, it may cause any important military data to fall in the hands of foreign countries, and it may halt e-media and every system can collapse within a fraction of seconds.
The cybercrimes involve the use of cyberspace (i.e. computer, internet, World Wide Web etc.) and give rise to the criminal activities. Cyber criminals are becoming more sophisticated and are targeting consumers as well as public and private organizations. Cybercrimes arise due to the lack of cyber security.
Cybercrime is an emerging form of transnational crime, and one of the fastest growing. As the Internet has become an almost essential part of our lives, providing information and communication all over the world, so criminals have taken advantage. With some four billion users worldwide, cyberspace is the ideal place for criminals because they can remain anonymous and gain access to all forms of personal information we knowingly, or unwittingly, store online. Threats to Internet safety have spiked dramatically in recent years, and cybercrime now affects about 1 billion victims globally.
Cybercrime exists in many forms, the most common being identity-related offences. This occurs by phishing (deceiving Internet users into giving their personal information), malware (unintentionally-installed software that collects personal information) and hacking (illegally accessing someone’s computer remotely). Criminals tend to use these methods to steal credit card information and money. Furthermore, the Internet has also becoming a place for crimes related to copyright and intellectual property rights and also offences such as child pornography and abuse material.
Cybercrime has grown easier as technology advances, and perpetrators no longer require great skills or techniques to be a threat. For example, software tools that allow the user to locate open ports or override password protection can be bought easily online. What has not grown easier, unfortunately, is the ability to find those responsible. With the anonymity that cyberspace provides, it is difficult for law enforcement to profile and locate the criminals. What is known, however, is that more than three quarters of cybercrime acts today are linked to organized criminal activity.
Cybercrime has rapidly grown into a business that may exceed three trillion US dollars a year. Without proper regulation, and insufficient capacity in many countries, combating cybercrime has proven difficult. A global effort is needed to provide better protection and firmer regulations because so far cyber criminals have hidden within legal loopholes in countries with less regulation. Perpetrators and their victims can be located anywhere, but the effects are seen across societies, highlighting the need for an urgent and robust international response.
_
Cybercrime constitutes any and all criminal activities carried out by means of computers or the Internet. While it has been around for quite some time, cybercrime continues to grow in scope and sophistication, to the tune of $600 billion in 2018 alone according to one study. As consumers increasingly allow technology into their personal lives, this technology stores and builds on troves of private data. Consider, for example, the information available in some popular everyday objects:
-Personal health data, sleep schedules, and geolocations from wearable health trackers
-Shopping history, account information, and passive conversations picked up on voice-controlled devices
-Private conversations on social media accounts
-Browsing history, photos, website passwords, and account information on cellphones
Your entire life, from the intimate to the mundane, is becoming increasingly digital, and your digital information may be uniquely accessible to a worldwide audience of potential perpetrators. The more this digitization becomes ubiquitous and standard, the more you may be prone to disregarding the inherent risks as society as a whole is lulled into complacency. In fact, a Pew Research study determined that many Internet users cannot correctly answer more than half the questions on a cybersecurity quiz.
_
The 2006 Computer Crime and Security Survey, conducted by the Computer Security Institute in conjunction with the U.S. Federal Bureau of Investigation’s International Computer Crime Squad [CSI/FBI 2006], showed an alarmingly high number of businesses reporting difficulties with computer and Internet fraud.
Of the organizations who acknowledged financial losses due to computer breaches, many could not quantify the losses.
65% detected computer viruses
48% reported between one and five security incidents in the year
42 % reported incidents that originated from sources within the organization;
32% of the respondents experienced incidents of unauthorized use of their computer systems during the last year;
47% reported theft of laptop computers and mobile devices.
_
Cybercrime is a worldwide problem that’s costing countries billions of dollars. According to crime-research.org, as early as 2003 the United States was already leading the world in percentage of cyber-attacks at 35.4 percent, followed by South Korea at 12.8 percent. Countries with high rates of computer piracy, such as Russia, have reacted slowly to cybercrime. As a result, many hackers and other cyber criminals can flourish in countries with few Internet crime laws while attacking richer countries through their computer because it lacks rules and codes of a central authority which governs it and as such internet has no geographical demarcation.
_
Understanding the concept of cybercrime:
Generally speaking, computers play four roles in crimes: They serve as objects, subjects, tools, and symbols. Computers are the objects of crime when they are sabotaged or stolen. There are numerous cases of computers being shot, blown up, burned, beaten with blunt instruments, kicked, crushed and contaminated. The damage may be intentional, as in the case of an irate taxpayer who shot a computer four times through the window of the local tax office. Or unintentional, as in the case of a couple who engaged in sexual intercourse while sitting on computer destroys information, or at least makes it unavailable. Computers play the role of subjects when they are the environment in which technologies commit crimes. Computer virus attacks fall into this category. When automated crimes take place, computers will be the subjects of attacks. The third role of computers in crime is as tools-enabling criminals to produce false information or plan and control crimes. Finally, computers are also used as symbols to deceive victims. In a $ 50 million securities-investment fraud case in Florida, a stock broker deceived his victims by falsely claiming that he possessed a giant computer and secret software to engage in high-profit arbitrage. In reality, the man had only a desktop computer that he used to print false investment statements. He deceived new investors by paying false profits to early investors with money invested by the new ones.
When speaking about cybercrime, we usually speak about two major categories of offences: In one, a computer connected to a network is the target of the offence; this is the case of attacks on network confidentiality, integrity and availability. The other category consists of traditional offences- such as theft, fraud, and forgery- which are committed with the assistance of computers connected to a network. Cybercrime ranges from computer fraud, theft and forgery- to infringements of privacy, the propagation of harmful content, the falsification of prostitution, and organized crime. In many instances, specific pieces of legislation contain definitions of terms. However legislators don’t always do a good job of defining terms. Sometimes they don’t define them at all, leaving it up to law enforcement agencies to guess, until the courts ultimately make a decision. One of the biggest criticisms to the definition of computer crime by the U.S Department of Justice (DOJ) is of its overly broad concept. The (DOJ) defines computer crime as ‘any violation of criminal law that involved the knowledge of computer technology for its perpetration, investigation, or prosecution’. Under this definition, virtually any crime could be classified as a computer crime, simply because a detective searched a computer data base as part of conducting an investigation.
One of the factors that make a hard-and-fast definition of cybercrime difficult is the jurisdictional dilemma. Laws in different jurisdictions define terms differently, and it is important for law enforcement officers who investigate crimes, as well as network administrators who want to become involved in prosecuting cybercrime that are committed against networks, to become familiar with the applicable laws.
Also, one of the major problems with adequately defining cybercrime is the lack of concrete statistical data on these offences. In fact, reporting crimes is voluntary. This means that the figures are almost certainly much lower than the actual occurrence of networked-related crime.
In many cases, crimes that legislators would call cybercrimes are just the ‘same old stuff’, except that a computer network is somehow involved. The computer network gives criminals a new way to commit the same old crimes. Existing statutes that prohibit these acts can be applied to people who use a computer to commit them as well as to those who commit them without the use of a computer or network.
In other cases, the crime is unique and came into existence with the advent of the network. Hacking into computer systems is an example; while it might be linked to breaking and entering a home or business building, the elements that comprise unauthorized computer access and physical breaking and entering are different.
____
Traditional Crime has long ago moved Online:
Money laundering
Child pornography/Sexual Exploitation of Children
Sale and trafficking of illegal drugs
Prostitution
Internet fraud/Credit Card Fraud
Illegal gambling
Hate propaganda/racism crimes
Intellectual Property Theft/Piracy
Harassment/Stalking
Threats/Extortion
Identity Theft
And many, many more…
_
New Forms of Criminality (thanks to computers/cyberspace):
Crimes directed against a computer or a computer network itself
Unauthorized use of computer system
Hacking
Denial of service attacks (DoS)
Virus/Malware transmission
Phishing
Botnet “Armies” and attacks
Terrorist Use of the Internet
Crime in Virtual Worlds
______
______
Definitions of cybercrime:
Most U.S states have statutes pertaining to computer crime. These statutes are generally enforced by state and local police and might contain their own definitions of terms. Texas Penal Code’s Computer Crime section, defines only one offence – Breach of Computer Security- as ‘A person commits an offence if the person knowingly accesses a computer, computer network, or computer system without the effective consent of the owner’. California Penal Code, on the other hand, defines a list of eight acts that constitute computer crime, including altering, damaging, deleting, or otherwise using computer data to execute a scheme to defraud, deceiving, extorting, or wrongfully controlling or obtaining money, property, or data using computer services without permission, disrupting computer services, assisting another in unlawfully accessing a computer, or introducing contaminates into a system or network. Thus, the definition of cybercrime under state law differs, depending on the state.
_
One common definition describes cybercrime as any activity in which computers or networks are a tool, a target or a place of criminal activity. There are several difficulties with this broad definition. It would, for example, cover traditional crimes such as murder, if perchance the offender used a keyboard to hit and kill the victim.
Some definitions try to take objectives or intentions into account and define cybercrime more precisely, such as “computer-mediated activities which are either illegal or considered illicit by certain parties and which can be conducted through global electronic networks”. These more refined descriptions exclude cases where physical hardware is used to commit regular crimes, but they risk excluding crimes that are considered as cybercrime in international agreements such as the Commonwealth Model Law on Computer and Computer-related Crime or the Council of Europe Convention on Cybercrime. For example, a person who produces USB devices containing malicious software that destroys data on computers when the device is connected commits a crime as defined by Article 4 of the Convention on Cybercrime. However, since the act of deleting data using a physical device to copy malicious code has not been committed through global electronic networks, it would not qualify as cybercrime under the narrow definition above. Such acts would only qualify as cybercrime under a definition based on a broader description, including acts such as illegal data interference.
The variety of approaches, as well as the related problems, demonstrates that there are considerable difficulties in defining the terms “computer crime” and “cybercrime”. The term “cybercrime” is used to describe a range of offences including traditional computer crimes, as well as network crimes. As these crimes differ in many ways, there is no single criterion that could include all acts mentioned in the different regional and international legal approaches to address the issue, whilst excluding traditional crimes that are just facilitated by using hardware. The fact that there is no single definition of “cybercrime” need not be important, as long as the term is not used as a legal term.
_
There is no internationally accepted definition of cybercrime, however, it is understood as a crime in which a computer is either the object of the crime – for example, through hacking, phishing or spamming – or in which a computer is used as a tool to commit an offence, such as child pornography or hate crimes.
Let us look to international organizations to provide a standard definition of cybercrime.
At the Tenth United Nations Congress on the Prevention of Crime and Treatment of Offenders, in a workshop devoted to the issues of crimes related to computer networks, cybercrime was broken into two categories and defined thus:
(a) Cybercrime in a narrow sense: Any illegal behaviour directed by means of electronic operations that targets the security of computers systems and the data processed by them.
(b) Cybercrime in a border sense: Any illegal behaviour committed by means of, or in relation to, a computer system or network, including such crimes as illegal possession and offering or disturbing information by means of a computer system or network.
These definitions, although not completely definitive, do give us a good starting point-on that has some international recognition and agreement – for determining just what we mean by term cybercrime. Cybercrime, by these definitions, involves computers and networks. In cybercrime, the “cyber” component usually refers to perpetrating qualitatively new offences enabled by information technology or integrating cyberspace into more traditional activities.
_
There are at present a large number of terms used to describe crime involving computers:
Such terms include
-computer‐related crime,
-computer crime,
-internet crime,
-e‐crime,
-high‐tech crime,
-online crime,
-electronic crime,
-computer misconduct and
-cybercrime.
_
The USA Department of Justice defines computer crime as “any violations of criminal law that involve a knowledge of computer technology for their perpetration, investigation or prosecution”.
The UK Association of Chief Police Officers (ACPO) has defined e‐crime as the “use of networked computers, telephony or internet technology to commit or facilitate the commission of crime”
Symantec Corporation defines cybercrime broadly as: “any crime that is committed using a computer or network or hardware device”.
The Australian Centre for Police Research (ACPR) defines e-crimes (cybercrime) as: “offences where a computer is used as a tool in the commission of an offence, as the target of an offence, or used as a storage device in the commission of an offence”
The Council of Europe Convention on Cybercrime defines cybercrime as a wide range of malicious activities, including the illegal interception of data, system interferences that compromise network integrity and availability, and copyright infringements.
_
There are three broad categories of cyber-crime.
The first category is defined where the computer is the tool of the crime. This category includes crimes that law enforcement has been fighting in the physical world but now is seeing with increasing frequency on the Internet. Some of these crimes include child pornography, criminal harassment, fraud, intellectual property violations and the sale of illegal substances and goods.
The second category is defined where the computer is the object of the crime. Cyber-crime consists of specific crimes dealing with computers and networks. These are new crimes that are specifically related to computer technology and the Internet. For example, hacking or unauthorized use of computer systems, defacing websites, creation and malicious dissemination of computer viruses.
The third category is “computer-supported crime” which covers the use of computers by criminals for communication and document or data storage.
Hence computer crime or cybercrime is divided into three categories:
- The use of computer as a target of criminal activity (e.g. hacking, dissemination of viruses)
- The use of computer as a tool or instrument used to commit a criminal activity (e.g. online fraud)
- The use of computer as incidental to the crime (e.g. data storage for criminal activity)
_
Another classification is espoused by Gordon and Ford. They classified cybercrime into Type I and Type II offenses using a continuous scale. Type I cybercrime, they said, is crime which is more technical in nature (e.g. hacking) while Type II cybercrime is crime that relies more on human contact rather than technology (e.g. online gambling). However, these authors state that ‘there are likely to be very few events which are purely Type I or Type II; these types represent either end of a continuum’ (Gordon & Ford, 2006 Gordon, S. & Ford, R. (2006). Cybercrime really presents a continuum ranging from crime which is almost entirely technological in nature and crime which is really, at its core, entirely people-related. A traditional investigator may be more capable of investigating crimes that are more people-centric than technological; similarly, computer security experts are more likely to focus their efforts on issues they see as technological. However, artificial intelligence and developments in robotics are quickly changing the technological landscape. One could argue that these phenomena could give rise to a ‘Type III’ cybercrime perpetrated by instruments capable of self-learning.
_
McGuire and Dowling (2013 McGuire, M., & Dowling, S. (2013). Cybercrime: A review of the evidence: Summary of key findings and implications. Home Office Research Report. London: also developed a useful classification tool. They classify cybercrime into ‘cyber-enabled’ crime and ‘cyber-dependent’ crime.
| Crimes that target networks or devices | Crimes using devices to participate in criminal activities |
| Viruses | Phishing Emails |
| Malware | Cyberstalking |
| DoS Attacks | Identity Theft |
Cyber-enabled crimes are traditional crimes facilitated by the use of computers. The range of ‘cyber-enabled’ crimes is myriad – from white-collar crime, such as fraudulent financial transactions, identity theft, and the theft of electronic information for commercial gain, to drug-trafficking, aberrant voyeuristic activities, harassment, stalking or other threatening behaviors. While these have always been deemed criminal activities, they are now so much easier to pursue with a computer.
Cyber-dependent crimes are those crimes that cannot exist without the cyber technology. A cybercriminal can inflict massive commercial damage using the internet. In fact, it is now easier and safer for a criminal to disrupt a business by destroying its database through malware than by throwing a Molotov cocktail through its front door. Cyber-dependent criminality was acutely felt across the world in May 2015 when Cryptowall 3.0 ransomware began attacking businesses. Using an exploit kit capable of attacking software vulnerabilities, Cryptowall 3.0 searched for files on the victims’ computers, encrypted these documents, deleted the originals, and then alerted the victims that they needed to pay thousands of dollars in ransom money in order to get their files back. It has been estimated that these attacks infected hundreds of thousands of computers across the world, and caused close to USD325 million damage.
Another modern manifestation of cyber-dependent crime is the work of the ‘hacktivist,’ someone who protests against an organization’s actions or policies. Perhaps the most memorable is the 2010 Anonymous hacktivist attack on Mastercard, Visa and PayPal in retribution for their ceasing to transact donations to the WikiLeaks group. Anonymous encouraged the spread of Distributed Denial of Service (DDoS) attacks which bombarded the trio’s websites with requests. A DDoS attack is when one attempts to make an online service unavailable by overwhelming it with traffic from multiple sources, causing it to collapse. Damage from this specific cybercrime was considerable. For PayPal alone, damage was estimated at USD5.5 million. Cyber-dependent crimes can be set up easily and cheaply using tools that may be readily available online.
_
Cybercrime, or computer-oriented crime, is a crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target. Halder and Jaishankar (2011) defines cybercrime as: “Offences that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm, or loss, to the victim directly or indirectly, using modern telecommunication networks such as Internet (networks including chat rooms, emails, notice boards and groups) and mobile phones (Bluetooth/SMS/MMS)”. Cybercrime may threaten a person or a nation’s security and financial health. Issues surrounding these types of crimes have become high-profile, particularly those surrounding hacking, copyright infringement, unwarranted mass-surveillance, sextortion, child pornography, and child grooming. Internationally, both governmental and non-state actors engage in cybercrimes, including espionage, financial theft, and other cross-border crimes. Cybercrimes crossing international borders and involving the actions of at least one nation-state is sometimes referred to as cyberwarfare.
Debarati Halder and K. Jaishankar further define cybercrime from the perspective of gender and defined ‘cybercrime against women’ as “Crimes targeted against women with a motive to intentionally harm the victim psychologically and physically, using modern telecommunication networks such as internet and mobile phones”.
_
On the website of the European Commission, it is mentioned that cybercrime can be classified in three broad definitions:
- Crimes specific to the Internet, such as attacks against information systems or phishing (e.g. fake bank websites to solicit passwords enabling access to victims’ bank accounts).
- Online fraud and forgery. Large-scale fraud can be committed online through instruments such as identity theft, phishing, spam and malicious code.
- Illegal online content, including child sexual abuse material, incitement to racial hatred, incitement to terrorist acts and glorification of violence, terrorism, racism and xenophobia.
_
Wall (2001) subdivides cybercrime into four established legal categories:
- Cyber-trespass or hacking/cracking: crossing boundaries into other people’s property and/or causing damage, e.g. hacking, defacement, viruses
- Cyber-deceptions and thefts: stealing (money, property), e.g. credit card fraud, intellectual property violations (a.k.a. piracy)
- Cyber-pornography: activities that breach laws on obscenity and decency
- Cyber-violence: doing psychological harm to, or inciting physical harm against others, thereby breaching laws pertaining to the protection of the person, e.g. hate speech, stalking
In addition to the above, Yar (2006) has added a new type of activity which is “crime against the state,” describing it as encompassing those activities that breach laws which protect the integrity of the nation’s infrastructure, like terrorism, espionage and disclosure of official secrets.
This classification is helpful in relating cybercrime to existing conceptions of proscribed and harmful acts, however it does little in the way of isolating what might be qualitatively different or new about such offences and their commission when considered from a perspective that looks beyond a limited legalistic framework.
_
Robert Taylor categorizes four general types of cybercrime by the computer’s relationship to the crime:
- Computer as the Target: theft of intellectual property, theft of marketing information (e.g., customer list, pricing data, or marketing plan), and blackmail based on information gained from computerized files (e.g., medical information, personal history, or sexual preference).
- Computer as the Instrumentality of the Crime: fraudulent use of automated teller machine (ATM) cards and accounts, theft of money from accrual, conversion, or transfer accounts, credit card fraud, fraud from computer transaction (stock transfer, sales, or billing), and telecommunications fraud.
- Computer is Incidental to Other Crimes: money laundering and unlawful banking transactions, organized crime records or books, and bookmaking.
- Crime Associated with the Prevalence of Computers: software piracy/ counterfeiting, copyright violation of computer programs, counterfeit equipment, black market computer equipment and programs, and theft of technological equipment.
______
Typology of cybercrime:
The Council of Europe taxonomy of cybercrime offences is depicted in figure below:
The term “cybercrime” is used to cover a wide variety of criminal conduct. As recognized crimes include a broad range of different offences, it is difficult to develop a typology or classification system for cybercrime. One approach can be found in the Convention on Cybercrime, which distinguishes between four different types of offences:
- offences against the confidentiality, integrity and availability of computer data and systems;
- computer-related offences;
- content-related offences; and
- copyright-related offences.
This typology is not wholly consistent, as it is not based on a sole criterion to differentiate between categories. Three categories focus on the object of legal protection: “offences against the confidentiality, integrity and availability of computer data and systems”; content-related offences; and copyright-related offences. The fourth category of “computer-related offences” does not focus on the object of legal protection, but on the method used to commit the crime. This inconsistency leads to some overlap between categories. In addition, some terms that are used to describe criminal acts such as “cyberterrorism” or “phishing” cover acts that fall within several categories. Nonetheless, the four categories can serve as a useful basis for discussing the phenomena of cybercrime.
____
Another Typology of cybercrime:
In terms of cybercrime, we may often associate it with various forms of Internet attacks, such as hacking, Trojans, malware (keyloggers), botnet, Denial-of-Service (DoS), spoofing, phishing, and vishing. Though cybercrime encompasses a broad range of illegal activities, it can be generally divided into five categories:
- Intrusive Offences
Illegal Access: “Hacking” is one of the major forms of offences that refers to unlawful access to a computer system.
Data Espionage: Offenders can intercept communications between users (such as e-mails) by targeting communication infrastructure such as fixed lines or wireless, and any Internet service (e.g., e-mail servers, chat or VoIP communications).
Data Interference: Offenders can violate the integrity of data and interfere with them by deleting, suppressing, or altering data and restricting access to them.
- Content-related offences
Pornographic Material (Child-Pornography): Sexually related content was among the first content to be commercially distributed over the Internet.
Racism, Hate Speech, Glorification of Violence: Radical groups use mass communication systems such as the Internet to spread propaganda.
Religious Offences: A growing number of websites present material that is in some countries covered by provisions related to religious offences, e.g., anti-religious written statements.
Spam: Offenders send out bulk mails by unidentified source and the mail server often contains useless advertisements and pictures.
- Copyright and trademark-related offences
Common copyright offences: cyber copyright infringement of software, music or films.
Trademark violations: A well-known aspect of global trade. The most serious offences include phishing and domain or name-related offences, such as cybersquatting.
- Computer-related offences
Fraud: online auction fraud, advance fee fraud, credit card fraud, Internet banking
Forgery: manipulation of digital documents.
Identity theft: It refers to stealing private information including Social Security Numbers (SSN), passport numbers, Date of birth, addresses, phone numbers, and passwords for non-financial and financial accounts.
- Combination offences
Cyberterrorism: The main purposes of it are propaganda, information gathering, preparation of real-world attacks, publication of training material, communication, terrorist financing and attacks against critical infrastructure.
Cyberwarfare: It describes the use of ICTs in conducting warfare using the Internet.
Cyber-laundering: Conducting crime through the use of virtual currencies, online casinos etc.
_____
Cybercrimes can be categorized as follows:
- Data Crime
-Data Interception
-Data Modification
-Data Theft
- Network Crime
-Network Interferences
-Network Sabotage
- Access Crime
-Unauthorized Access
-Virus Dissemination
- Related Crimes
-Aiding and Abetting Cyber Crimes
-Computer-Related Forgery and Fraud
-Content-Related Crimes
______
Categories of cybercrimes based on targets:
Cybercrimes are broadly categorized into four categories, namely crime against
1.Individual
2.Property
3.Government
4.Society at large
Each category can use a variety of methods and the methods used vary from one criminal to another.
- Cybercrimes against Individual:
- Harassment via E-Mails: It is very common type of harassment through sending letters, attachments of files & folders i.e. via e-mails. At present harassment is common as usage of social sites i.e. Facebook, Twitter etc. increasing day by day.
- Cyber-Stalking: It means expressed or implied a physical threat that creates fear through the use to computer technology such as internet, e-mail, phones, text messages, webcam, websites or videos.
- Dissemination of Obscene Material: It includes Indecent exposure/ Pornography (basically child pornography), hosting of web site containing these prohibited materials. These obscene matters may cause harm to the mind of the adolescent and tend to deprave or corrupt their mind.
- Defamation: It is an act of imputing any person with intent to lower down the dignity of the person by hacking his mail account and sending some mails with using vulgar language to unknown persons mail account.
- Hacking: It means unauthorized control/access over computer system and act of hacking completely destroys the whole data as well as computer programs. Hackers usually hacks telecommunication and mobile network.
- Cracking: It is amongst the gravest cybercrimes known till date. It is a dreadful feeling to know that a stranger has broken into your computer systems without your knowledge and consent and has tampered with precious confidential data and information.
- E-Mail Spoofing: A spoofed e-mail may be said to be one, which misrepresents its origin. It shows its origin to be different from which actually it originates.
- SMS Spoofing: SMS spoofing is a technology which uses the short message service (SMS), available on most mobile phones and personal digital assistants, to set who the message appears to come from by replacing the originating mobile number (Sender ID) with alphanumeric text.
- Carding: It means false ATM cards i.e. Debit and Credit cards used by criminals for their monetary benefits through withdrawing money from the victim’s bank account malafidely. There is always unauthorized use of ATM cards in this type of cybercrimes.
- Cheating & Fraud: It means the person who is doing the act of cybercrime i.e. stealing password and data storage has done it with having guilty mind which leads to fraud and cheating.
- Child Pornography: It involves the use of computer networks to create, distribute, or access materials that sexually exploit underage children.
- Assault by Threat: refers to threatening a person with fear for their lives or lives of their families through the use of a computer network i.e. E-mail, videos or phones.
- Cybercrimes Against Property:
- Intellectual Property Crimes: Intellectual property consists of a bundle of rights. Any unlawful act by which the owner is deprived completely or partially of his rights is an offence. The common form of IPR violation may be said to be software piracy, infringement of copyright, trademark, patents, designs and service mark violation, theft of computer source code, etc.
- Cyber Squatting: It means where two persons claim for the same Domain Name either by claiming that they had registered the name first on by right of using it before the other or using something similar to that previously.
- Cyber Vandalism: Vandalism means deliberately destroying or damaging property of another. It may include within its purview any kind of physical harm done to the computer of any person. These acts may take the form of the theft of a computer, some part of a computer or a peripheral attached to the computer.
- Hacking Computer System: This is unauthorized access/control over the computer. Due to the hacking activity there will be loss of data as well as computer. Research indicates that these attacks were not mainly intended for financial gain but also to diminish the reputation of particular person or company.
- Transmitting Virus: Viruses are programs that attach themselves to a computer or a file and then circulate themselves to other files and to other computers on a network. They usually affect the data on a computer, either by altering or deleting it. Worm attacks plays major role in affecting the computerize system of the individuals.
- Cyber Trespass: It means to access someone’s computer without the right authorization of the owner and does not disturb, alter, misuse, or damage data or system by using wireless internet connection.
- Internet Time Thefts: Basically, Internet time theft comes under hacking. It is the use by an unauthorised person, of the Internet hours paid for by another person. The person who gets access to someone else’s ISP user ID and password, either by hacking or by gaining access to it by illegal means, uses it to access the Internet without the other person’s knowledge. You can identify time theft if your Internet time has to be recharged often, despite infrequent usage.
- Cybercrimes Against Government:
- Cyber Terrorism: Cyber terrorism is a major burning issue in the domestic as well as global concern. The common form of these terrorist attacks on the Internet is by distributed denial of service attacks, hate websites and hate e-mails, attacks on sensitive computer networks etc. Cyber terrorism activities endanger the sovereignty and integrity of the nation.
- Cyber Warfare: It refers to politically motivated hacking to conduct sabotage and espionage. It is a form of information warfare sometimes seen as analogous to conventional warfare although this analogy is controversial for both its accuracy and its political motivation.
- Distribution of pirated software: It means distributing pirated software from one computer to another intending to destroy the data and official records of the government.
- Possession of Unauthorized Information: It is very easy to access any information by the terrorists with the aid of internet and to possess that information for political, religious, social, ideological objectives.
- Cybercrimes Against Society at large:
- Cyber Trafficking: It may be trafficking in drugs, human beings, arms weapons etc. which affects large number of persons. Trafficking in the cyberspace is a crime.
- Online Gambling: Online fraud and cheating is one of the most lucrative businesses that are growing today in the cyber space. There are many cases that have come to light are those pertaining to credit card crimes, contractual crimes, offering jobs, etc.
- Financial Crimes: This type of offence is common as there is rapid growth in the users of networking sites and phone networking where culprit will try to attack by sending bogus mails or messages through internet. E.g. Using credit cards by obtaining password illegally.
- Forgery: It means to deceive large number of persons by sending threatening mails as online business transactions are becoming the habitual need of today’s life style.
_______
Common Cybercrime activities are as follows:
- Hacking and related activities
- Viruses and other malicious programs
- Fraud and Theft
- Gambling, Pornography and other offences against morality
- Child pornography and other offences against minors
- Stalking, Harassment, Hate speech
- Other offences against persons
- Cyberterrorism
_
_____
_____
Cybercrime in developing world:
Developing countries lack the capacity to combat cyber-attacks and other forms of cybercrime. It is therefore not surprising that victimization rates are higher in countries with lower levels of development. Criminals also exploit countries’ legal loopholes and weak security measures to perpetrate cybercrimes. The lack of cooperation between developed and developing countries can also result in “safe havens” for those committing cybercrimes.
_
State of Cybercrime:
In a recent US State of Cybercrime Survey, three out of four respondents detected a security event during the past 12 months. Many organizations report that they are suffering from technology debt, estimated to exceed one trillion dollars. This means that companies are effectively spending IT budgets on emerging business technologies while allowing IT infrastructure to age into obsolescence until they cannot provide effective security functions.
Common security deficiencies have been found in organizations most susceptible cybercrime:
-Reactive or unplanned cybersecurity spending
-No assessments of the security capabilities of their third-party providers
-Lack of understanding and/or assessment of supply-chain risks
-Inadequate or nonexistent mobile device management and security
-Insider threats and risk not adequately addressed
-Lack of thorough employee security and awareness training
Cybercrime is increasing at a geometric rate. There’s roughly 900 phishing attempts detected per financial institution, and more than 9,000 attempts detected per technology company per year on average. Phishing sites are mimicking all the major technology players as well. Google, Apple, Facebook, and Yahoo, are all phishing targets, as well as Dropbox, where insidious phishing sites could actually dupe users into uploading their files to cybercriminals.
On average, 85,000 malicious IPs are launched every day, bringing the average reputation score of all URLs worldwide to 65 percent. It is a worldwide endeavor, with large concentrations in the United States, Russia, and throughout Asia. The result is that in one year, users have a 30% chance of falling for a zero-day phishing attack.
Cybercrime is not restricted to the desktop alone; Mobile devices have proliferated in recent years, and with them viruses, malware, and phishing scams. Because of its open marketplace, the Android platform is home to a variety of malware in particular. In a recent survey, 72% of all apps for the OS were regarded as suspicious, unwanted, or malicious, with Trojans making up the majority of threats.
External cybercrime is bad enough, but many experts agree that internal attacks pose as great or greater risk to businesses and organizations, due to the sensitive information gained from employment. Insider risk can be mitigated with robust employee awareness and security training; however, the tragic reality is that a vast amount of organizations do not conduct this training at all. Insider cybercrime risk typically has precursors with IT policy violations; awareness and scrutiny of these trends can help prevent crimes that would otherwise go unnoticed until after the fact.
Why does this behavior among organizations persist? Data suggests that many decision makers at organizations do not have a full understanding of the extent or seriousness of threats, do not believe they are at risk, or have become desensitized to the warnings. Over the course of one year, businesses that have fallen victim to cybercrime tend to take security more seriously, and with good reason. Businesses with more than one thousand employees also take cybercrime more seriously and have more processes in place to mitigate risk internally as well as externally.
_____
Global risks:
Cybercrime has been a topic of great interest over the last ten years and is currently considered one of the most serious threats worldwide. Every aspect of daily life, both private and work related, is now highly computerized. All the world’s economies use the same basic infrastructure, the same software, hardware, and standards – with billions of connected devices.
According to a recent survey by the World Economic Forum (WEF), risks from cyber space are considered as among the greatest perceived risks in terms of impact and likelihood of occurrence, as can be seen in figure below.
Figure above shows The Global Risks Landscape in 2014
The report also shows that if businesses and governments do not develop adequate defense policies, and if they do not do so quickly, the economic losses caused by cyber-attacks could be up to 3,000 billion dollars by 2020.
The WEF has often highlighted the interdependence of IT systems, introducing new vulnerabilities and flaws with unpredictable consequences and emphasizing the macroeconomic impact of IT risks in terms of growth of GDP. In its latest report the WEF emphasizes the delicacy of this cybercrime, explaining that if not addressed promptly and taken into account by all stakeholders (governments, businesses and civil society), it could lead to serious consequences and to a scenario in which the Internet could suffer the mistrust of users, no longer be a free resource and research tool, and no longer be used for ecommerce. Despite all of this, there is still no shared legal definition that determines cybercrime in a consistent and exhaustive manner – due mainly to differences in the laws of various countries.
_____
Where is the crime scene?
Most cases go undetected as multinational internet giants and social media companies refuse to share information with the police. In most cases, it takes a lot of time just to get the information as the police and cyber cell officials need to trace the IP addresses and get hold of the devices (laptops, computers, mobile phones etc), involved in the crime. In most cases, the IPs are located in some other country. Technology evolution and innovation make it more challenging to detect cybercrimes. Information sharing between countries and within the country needs to be strengthened. The low detection of cybercrimes is also due to lack of technical knowledge among the police staff and that there should be more training centers and courses so that they can upgrade themselves.
_____
Global ranking:
Do you know that over the last ten years Cyber Crime rose 19 times? After, U.S.A and China, India ranked third in Malicious Activity. Internet Subscribers in India crossed 462 million by June 2016.
_____
Cybercrimes are now a Booming Mode of Income:
I am not trying to advocate choosing cybercrime as your career interest, but these statistics are shocking!
Did you know that the individual earning of crooks from different types of cybercrimes is 10-15% higher than other traditional crimes? In fact, the highest earnings can go up to $167000 per month while mid-level earners can make nearly $75000 per month! Some cyber conmen rake in nearly half a million dollars in a year by simply trafficking embezzled data!
Furthermore, the annual revenues from cybercrime will leave you shocked! Illegal online markets churn out the highest revenues for cyber conmen, amounting to nearly $860 billion. Likewise, data trading and ransomware generate an annual revenue of nearly $160 billion and $1 billion respectively!!!
_____
How cybercrime works:
Cyber criminals use a number of attack vectors to carry out their cyberattacks and are constantly seeking new methods and techniques for achieving their goals, while avoiding detection and arrest.
Here are common types of attacks Cyber criminals have been known to use:
- Distributed DoS attacks are often used to shut down systems and networks. This type of attack uses a network’s own communications protocol against it by overwhelming its ability to respond to connection requests. DoS attacks are sometimes carried out simply for malicious reasons but they may also be used to distract the victim organization from some other attack or exploit carried out at the same time.
- Infecting systems and networks with malware is used to damage the system or harm users by, for example, damaging the system, software or data stored on the system. Ransomware attacks are similar, but the malware acts by encrypting or shutting down victim systems until a ransom is paid.
- Phishing campaigns are used to infiltrate corporate networks by sending fraudulent email to users in an organization, enticing them to download attachments or click on links that then spread viruses or malware to their systems and through their systems to their company’s networks.
- Credentials attacks, where the cybercriminal aims to steal or guess user IDs and passwords for the victim’s systems or personal accounts, can be carried out through the use of brute force attacks by installing key sniffer software or by exploiting vulnerabilities in software or hardware that can expose the victim’s credentials.
- Cyber criminals may also attempt to hijack a website to change or delete content or to access or modify databases without authorization. For example, an attacker may use an SQL injection exploit to insert malicious code into a website, which can then be used to exploit vulnerabilities in the website’s database, enabling a hacker to access and tamper with records or gain unauthorized access to data, such as customer passwords, credit card numbers, personally identifiable information (PII), trade secrets, intellectual property and other sensitive information.
Cyber criminals often carry out their activities using malware and other types of software, but social engineering is often an important component for executing most types of cybercrime. Phishing email is an important component to many types of cybercrime, but especially so for targeted attacks, like business email compromise (BEC), in which the attacker attempts to impersonate, via email, a business owner in order to convince employees to pay out bogus invoices.
_____
Cybercrime is a complex issue. Some of the main challenges to improving understanding of cybercrime include:
- lack of recording mechanisms that accurately distinguish between online and offline crime;
- under-reporting of cybercrime from the public and businesses and a lack of awareness that some cyber incidents are actually crimes (although not all are);
- inconsistencies in the measurement and definition of cybercrime within the relevant research;
- information from industry sources often lacks transparency and comparability;
- few methodologically sound surveys of victims exist;
- cybercrime can be undertaken on a large scale, potentially resulting in a relationship between victims and offenders that is very different to ‘offline’ crime; and
- cybercrime is global in nature, it is not constrained by national boundaries.
______
______
Vulnerability:
A vulnerability is a weakness in design, implementation, operation or internal control. Most of the vulnerabilities that have been discovered are documented in the Common Vulnerabilities and Exposures (CVE) database. An exploitable vulnerability is one for which at least one working attack or “exploit” exists. Vulnerabilities are often hunted or exploited with the aid of automated tools or manually using customized scripts.
Technical vulnerabilities:
Every company has its own vulnerabilities, both technical and human, which when identified, can be exploited by cyber criminals. In most cases, the attack techniques used are widely known and often simple and are aimed at the company’s weak spots: code errors, failure to install security patches for programs or systems used by the victim, failure to update antivirus and anti-malware, the incorrect configuration or failure of devices and corporate networks, or the use of repetitive passwords or passwords which are too simple. These are all vulnerabilities that could be easily erased with proper preparation by technical management and a greater knowledge of best practices by all users of the systems at risk. These simple practices make it more difficult to obtain the result desired by the attackers.
Human vulnerabilities:
The human factor is undoubtedly a key factor in the entire system of corporate security. In fact, very often the first breach in the security of a system is achieved not by technical means, but simply by taking advantage of aspects of standard human behavior: distraction, superficiality, negligence, altruism, confidence, and curiosity – which are the basis of many types of attacks. Attacks such as phishing, pharming, fraud, identity theft or theft of sensitive data, are based on the probability that the operator on the other side of the PC may be prompted to click on a suggested link, led by simple curiosity, because he believes he knows the sender of the email or because he is convinced they can solve problems with his credit card. The social engineering technique is more complex because it uses the phone, email, information released on social networks, and direct physical contact, to get the necessary information directly from the target, in order to commit the attack using technological tools. It is therefore necessary to understand the mindset of the attacker, his attitude, his motivations, and how he collects information about the target – basically hacker profiling and the ethics that motivate them.
In July 2014, Goldman Sachs asked Google for the removal of a confidential email containing classified company information and customer data, which was sent in human error from a contractor of the investment bank to a wrong email address (gmail.com instead of gs.com, which is the Goldman Sachs corporate domain). This is an example of an extremely basic error that risked compromising sensitive data and consequently high-profile business relationships. A recent study reveals that 80% of IT Professional respondents see employees as the weakest link in the IT security chain and paint a picture of the SME sector as being flooded with cyber threats.
_____
_____
Cybercrime threats:
A resource (both physical and logical), called an asset, can have one or more vulnerabilities that can be exploited by a threat agent in a threat action. As a result, the confidentiality, integrity or availability of resources may be compromised. Potentially, the damage may extend to resources in addition to the one initially identified as vulnerable, including further resources of the organization, and the resources of other involved parties (customers, suppliers).
The attack can be active when it attempts to alter system resources or affect their operation: so it compromises integrity or availability. A “passive attack” attempts to learn or make use of information from the system but does not affect system resources: so it compromises confidentiality.
A threat is a potential for violation of security, which exists when there is a circumstance, capability, action or event that could breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability. A threat can be either “intentional” (i.e., intelligent; e.g., an individual cracker or a criminal organization) or “accidental” (e.g., the possibility of a computer malfunctioning, or the possibility of an “act of God” such as an earthquake, a fire, or a tornado).
_
Figure below shows G8 taxonomy of threats
_
Similar to conventional crime, economic benefits, power, revenge, adventure, ideology and lust are the core driving forces of cybercrime. Major threats caused by those motivations can be categorized as following:
- Economic security, reputation and social trust are severely challenged by cyber fraud, counterfeiting, impersonation and concealment of identity, extortion, electronic money laundering, copyright infringement and tax evasion.
- Public interest and national security is threatened by dissemination of offensive material e.g., pornographic, defamatory or inflammatory/intrusive communication— cyber stalking/harassment, Child pornography and pedophilia, electronic vandalism/terrorism.
- Privacy, domestic and even diplomatic information security are harmed by unauthorized access and misuse of ICT, denial of services, and illegal interception of communication.
- Domestic, as well as international security are threatened by cybercrime due to its transnational characteristic. No single country can really handle this big issue on their own. It is imperative for us to collaborate and defend cybercrime on a global scale.
_
In its report Threat Landscapes 2013, The European Union for Network and Information Security Agency (ENISA), identifies 16 major IT security threats, highlighting what has been the trend for the past year. The following chart, drawn from the report, summarizes the main threats directly involving SMEs, such as mobile and cloud. As you can see, with the exception of botnets and spam, which have remained at the same level of the previous year, all other threats are increasing in almost all the most sensitive areas.
Table above shows Summary of the main trends relating to cyber threats
_
The word ‘breach’ has been used more in an information technology context in the last few years more than it had ever been in the previous 20 year before that. It is estimated that 1 billion records were compromised in 2014 (Gelmato, 2015) and at the cost of per compromise estimated to be between 52 to 87 US dollars (Verizon, 2015), the impact of these bridges to the global economy is alarmingly large. Further, a Verizon report highlighted that “organised crime became the most frequently seen threat actor for Web App Attacks”, raising the concern that cybercriminal attacks are becoming more organised and systemic. In a hyperconnected world, the ability to adequately protect data and information has been touted as an important component of risk management.
While technology has been a key enabler to better and more productive living, it does bring its fair share of challenges as increasingly sophisticated cyber threats become a key concern in this connected world. A recent report released by Fire-Eye suggested that hackers, most likely from China, have been spying on government and business targets in the region for over a decade (Hamzah, 2015). Such threats which are less known in the past have made way in headlines in recent years and months, a stark reminder of the cyber threats in this global connected community. Gartner predicted that more than 25% of global firms will adopt big data analytics for at least one security and fraud detection case, up from 8% currently. Every CIO and CISO wakes up each day knowing that if they don’t get security right and breaches are suffered, their program can be perceived to be ineffective, and their citizens may suffer direct harm.
_
Figure below is a graphical illustration of Threat Actors and Attacker Determination.
_
The participants use a variety of techniques to achieve their end objectives as shown in figure below which summarises the techniques and the vulnerabilities that the threat actors focus on. The root cause from studying the corporate challenges is the attitude that we adopt in addressing the issue. Each of the challenges is usually addressed individually instead of abstracting them to uncover that there is a fundamental flaw. The silo approach to “fix it” has also caused a deterioration in the way incidents are being managed thus, to use the common idiom meaning that, often we miss the forest for the trees.
_
Figure above summary of techniques and vulnerabilities focused by threat actions
_
Cyberattacks are committed for a variety of reasons including financial fraud, information theft, activist causes, to deny service, disrupt critical infrastructure and vital services of government or an organization.
The six common sources of cyber threats are as follows:
- Nation states
- Cyber criminals
- Hacktivists
- Insiders and service providers
- Developers of substandard products and services
- Poor configuration of cloud services like S3 buckets
_
Source of Cyberthreat Feared Most (By Percentage)
Disgruntled Ex-employees 24%
Rogue Hacktivist Groups 21%
Lone-wolf Dorm Hackers 19%
Competitors Targeting Corporate IP 18%
State-sponsored Hackers 18%
Source: AppRiver Cyberthreat Index for Business (Q1 2019).
_
The FBI has noted three primary categories of cyber threat actors:
[1] Organized crime groups that are primarily threatening the financial services sector, and they are expanding the scope of their attacks;
[2] state sponsors-foreign governments that are interested in pilfering data, including intellectual property and research and development data from major manufacturers, government agencies, and defence contractors; and
[3] increasingly there are terrorist groups who want to impact the same way they did on 9/11 by flying planes into buildings. They are seeking to use the network to challenge nations by looking at critical infrastructure to disrupt or harm the viability of our way of life
_
Cybercrime as an international threat:
Globally, risks of various kinds have become more and more important due to the intensification of globalization. In this scenario, cybercrime is an even more dangerous threat. The consequences of the new risks have become international, and are potentially devastating and unpredictable. Global interconnectedness makes any national economic production system vulnerable. As we have seen, cybercrime is a phenomenon that affects all the countries of the world – especially the most industrialized and computerized. There are hundreds of different sources that provide data about the scale of cybercrime, but the statistics are insufficient and fragmented. However, when conducting an analysis, of a major report from the field, the data is very discouraging.
In a recent report drawn up on the basis of interviews among 250 industry experts and business executives, the World Economic Forum warns that over the next six years cyber-attacks could cause economic losses of up to 3 trillion dollars if we are unable to act effectively in order to fight this threat. That could, according to the same study, also lead to a slowdown in the use of innovative technology solutions in the coming years. As many as 78% of companies surveyed, in fact, had postponed the use of solutions such as cloud computing for fear of being a victim of a hacker attack and suffer the loss of sensitive data. According the WEF study, the adoption of proactive actions by companies and governments would not only lead to a limitation in the number of attacks, but could also lead to generation of economic value in terms of technological innovation – which in turn would generate a profit to the global economy of between 9 and 21 trillion dollars in a decade.
The annual cost of the damage inflicted by cybercrime is difficult to estimate for several reasons: companies do not always share information as they often do not realize they have been attacked until months or years later, and in some cases it can be difficult to estimate the actual loss suffered. In this type of crime, the fact that there is no legislation at the international level should be taken into consideration. It is also difficult to define which actions are considered offenses in different nation states in order to draft reliable international estimates.
In addition, numerous reports drawn up by private IT security companies all suffer the limitation of not being able to take advantage of the full data compiled at the level of the individual nation state. Only an official report drawn up by a government body could provide more details on the final statistics. In any case, these reports by IT security companies give an indication of the severity and the trends recorded in recent years regarding cybercrime. All reports, in fact, point out that the risk of cyber-attacks is constantly increasing and that the impact on the global economy is increasingly worrying, and this should be enough to encourage SMEs, civil society and governments to take this threat more seriously and to cooperate in order to limit damage.
According to Kaspersky, the impact of cybercrime on the global economy is sadly destined to multiply over time, with the most feared attacks being those to critical infrastructure. What is also worrying is the significant increase in crimes against businesses, such as fraud or identity theft.
The more conservative estimates of McAfee and CISCO assess the gap of the annual cost of cybercrime to the global economy at between 375 and 575 billion dollars a year, potentially even a trillion dollars – but still growing steadily due to the large and easy returns compared with very low risks for criminals. McAfee also noted that companies tend to underestimate the severity of cyber risks and their growth rates.
One of the most extensive studies on the impact of cybercrime on users, the Norton Cybercrime Report 2012, estimates that each year cybercrime directly affects, on average, over 500 million people. Given their greater level of computerization, more industrialized nations suffer the most losses, but the situation is expected to increase in less developed countries as they increase their computerization. The United States, China, Japan, and Germany, alone, have registered 200 billion dollars of annual losses.
______
______
Cybercrime Targets:
Cybercrime targets of a company includes:
- Customer data
- Employee data
- Intellectual property
- Third and fourth party vendors
- Product quality and safety
- Contract terms and pricing
- Strategic planning
- Financial data
_
Just as the modes of cybercrimes are many, so are its targets. But the most common among them are listed below.
- Online Banking: Ever since online banking came into existence; hackers have been after them hoping to make some easy money online by breaking into their websites. To give an example, almost 2.5 Million Pounds were stolen from nearly 9000 customer accounts of UK’s TESCO Bank when hackers broke into it. Therefore online banks remain the most preferred target for hackers.
- E-Commerce Websites: Next come E-Commerce websites which deal with customer online transactions frequently. Here hackers are after the payment card information of customers who make purchases from these E-Commerce websites. This payment card information, once stolen will be used by hackers for their own benefit.
- POS Systems or Terminals: POS systems used by various industries like retail stores, hospitals, restaurants etc., also a much-favored target among cyber criminals. The POS-System hacking of Target retail chain of stores back in December 2013 by using a POS-malware called Backoff malware is something which cannot be forgotten that easily. It is through these attacks that BackOff malware gained popularity and the dangers they pose are threatening the IT security landscape even today. So much so that BackOff malware has become synonymous with POS malware.
- Websites without SSL Protection: Hackers love websites with security vulnerabilities. Because they can be broken into or hacked easily. Therefore any website which does not have SSL Encryption or Protection becomes the target of hackers. Because websites without SSL Certificates can be easily impersonated by hackers.
- Those with Online Reputation: Enterprises, governments, universities and almost any organization which has an online reputation can become the target of cyber criminals who may bear a personal grudge against them. Or for the simple reason, that defaming such personalities gives them a high.
______
Systems at risk of cybercrime:
The growth in the number of computer systems and the increasing reliance upon them by individuals, businesses, industries and governments means that there are an increasing number of systems at risk.
- Financial systems
The computer systems of financial regulators and financial institutions like the U.S. Securities and Exchange Commission, SWIFT, investment banks, and commercial banks are prominent hacking targets for cyber criminals interested in manipulating markets and making illicit gains. Web sites and apps that accept or store credit card numbers, brokerage accounts, and bank account information are also prominent hacking targets, because of the potential for immediate financial gain from transferring money, making purchases, or selling the information on the black market. In-store payment systems and ATMs have also been tampered with in order to gather customer account data and PINs.
- Utilities and industrial equipment
Computers control functions at many utilities, including coordination of telecommunications, the power grid, nuclear power plants, and valve opening and closing in water and gas networks. The Internet is a potential attack vector for such machines if connected, but the Stuxnet worm demonstrated that even equipment controlled by computers not connected to the Internet can be vulnerable. In 2014, the Computer Emergency Readiness Team, a division of the Department of Homeland Security, investigated 79 hacking incidents at energy companies. Vulnerabilities in smart meters (many of which use local radio or cellular communications) can cause problems with billing fraud.
- Aviation
The aviation industry is very reliant on a series of complex systems which could be attacked. A simple power outage at one airport can cause repercussions worldwide, much of the system relies on radio transmissions which could be disrupted, and controlling aircraft over oceans is especially dangerous because radar surveillance only extends 175 to 225 miles offshore. There is also potential for attack from within an aircraft. The consequences of a successful attack range from loss of confidentiality to loss of system integrity, air traffic control outages, loss of aircraft, and even loss of life.
- Consumer devices
Desktop computers and laptops are commonly targeted to gather passwords or financial account information, or to construct a botnet to attack another target. Smartphones, tablet computers, smart watches, and other mobile devices such as quantified self-devices like activity trackers have sensors such as cameras, microphones, GPS receivers, compasses, and accelerometers which could be exploited, and may collect personal information, including sensitive health information. Wi-Fi, Bluetooth, and cell phone networks on any of these devices could be used as attack vectors, and sensors might be remotely activated after a successful breach. The increasing number of home automation devices such as the Nest thermostat are also potential targets.
- Large corporations
Large corporations are common targets. In many cases attacks are aimed at financial gain through identity theft and involve data breaches. Examples include loss of millions of clients’ credit card details by Home Depot, Staples, Target Corporation, and the most recent breach of Equifax.
Some cyberattacks are ordered by foreign governments, which engage in cyberwarfare with the intent to spread their propaganda, sabotage, or spy on their targets. Many people believe the Russian government played a major role in the US presidential election of 2016 by using Twitter and Facebook to affect the results of the election.
Medical records have been targeted in general identify theft, health insurance fraud, and impersonating patients to obtain prescription drugs for recreational purposes or resale. Although cyber threats continue to increase, 62% of all organizations did not increase security training for their business in 2015.
Not all attacks are financially motivated however; for example security firm HBGary Federal suffered a serious series of attacks in 2011 from hacktivist group Anonymous in retaliation for the firm’s CEO claiming to have infiltrated their group, and in the Sony Pictures attack of 2014 the motive appears to have been to embarrass with data leaks, and cripple the company by wiping workstations and servers.
- Automobiles
Vehicles are increasingly computerized, with engine timing, cruise control, anti-lock brakes, seat belt tensioners, door locks, airbags and advanced driver-assistance systems on many models. Additionally, connected cars may use Wi-Fi and Bluetooth to communicate with onboard consumer devices and the cell phone network. Self-driving cars are expected to be even more complex.
All of these systems carry some security risk, and such issues have gained wide attention. Simple examples of risk include a malicious compact disc being used as an attack vector, and the car’s onboard microphones being used for eavesdropping. However, if access is gained to a car’s internal controller area network, the danger is much greater – and in a widely publicized 2015 test, hackers remotely carjacked a vehicle from 10 miles away and drove it into a ditch.
- Government
Government and military computer systems are commonly attacked by activists and foreign powers. Local and regional government infrastructure such as traffic light controls, police and intelligence agency communications, personnel records, student records, and financial systems are also potential targets as they are now all largely computerized. Passports and government ID cards that control access to facilities which use RFID can be vulnerable to cloning.
- Internet of things and physical vulnerabilities
The Internet of things (IoT) is the network of physical objects such as devices, vehicles, and buildings that are embedded with electronics, software, sensors, and network connectivity that enables them to collect and exchange data – and concerns have been raised that this is being developed without appropriate consideration of the security challenges involved.
While the IoT creates opportunities for more direct integration of the physical world into computer-based systems, it also provides opportunities for misuse. In particular, as the Internet of Things spreads widely, cyber-attacks are likely to become an increasingly physical (rather than simply virtual) threat. If a front door’s lock is connected to the Internet, and can be locked/unlocked from a phone, then a criminal could enter the home at the press of a button from a stolen or hacked phone. People could stand to lose much more than their credit card numbers in a world controlled by IoT-enabled devices. Thieves have also used electronic means to circumvent non-Internet-connected hotel door locks.
- Medical systems
Medical devices have either been successfully attacked or had potentially deadly vulnerabilities demonstrated, including both in-hospital diagnostic equipment and implanted devices including pacemakers and insulin pumps. There are many reports of hospitals and hospital organizations getting hacked, including ransomware attacks, Windows XP exploits, viruses, and data breaches of sensitive data stored on hospital servers. On 28 December 2016 the US Food and Drug Administration released its recommendations for how medical device manufacturers should maintain the security of Internet-connected devices – but no structure for enforcement.
- Energy sector
In distributed generation systems, the risk of a cyber-attack is real. An attack could cause a loss of power in a large area for a long period of time, and such an attack could have just as severe consequences as a natural disaster.
______
Crimeware:
The software used in Cybercrime is sometimes referred to as crimeware. Like Cybercrime itself, the term crimeware covers a broad spectrum. However, it is important to remember that not all software used in the commission of a computer-based or computer-facilitated crime can be legitimately termed crimeware. For example, while an IM client may be used in the commission of a Cybercrime, the IM application software itself is not considered crimeware. FTP clients may be used in the commission of crimes; however, they are not considered crimeware. Crimeware does, however, include programs which may be classified as bots, keystroke loggers, spyware, backdoors and Trojan horses. Additionally, some cybercrime may involve both crimeware and legitimate programs.
Examples of different cybercrime by examining the software used in each case:
| Example | Software | Crimeware |
| Phishing | Mail client | No |
| Identity Theft | Keylogger, Trojan | Yes |
| Cyberstalking | Email Client, Messenger Clients | No |
| DDoS | Bots | Yes |
| Cyberterrorism (communication) | Steganography, Encryption, Chat Software | No |
______
______
Cyberattack:
In computers and computer networks an attack is any attempt to expose, alter, disable, destroy, steal or gain unauthorized access to or make unauthorized use of an asset. A cyberattack is any type of offensive maneuver that targets computer information systems, infrastructures, computer networks, or personal computer devices. An attacker is a person or process that attempts to access data, functions or other restricted areas of the system without authorization, potentially with malicious intent. Depending on context, cyberattacks can be part of cyberwarfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, society or organizations, and it may originate from an anonymous source. A cyberattack may steal, alter, or destroy a specified target by hacking into a susceptible system. Cyberattacks can range from installing spyware on a personal computer to attempting to destroy the infrastructure of entire nations. Legal experts are seeking to limit the use of the term to incidents causing physical damage, distinguishing it from the more routine data breaches and broader hacking activities. Cyberattacks have become increasingly sophisticated and dangerous.
_
In May 2000, the Internet Engineering Task Force defined cyberattack in RFC 2828 as:
an assault on system security that derives from an intelligent threat, i.e., an intelligent act that is a deliberate attempt (especially in the sense of a method or technique) to evade security services and violate the security policy of a system.
CNSS Instruction No. 4009 define a cyberattack as:
An attack, via cyberspace, targeting an enterprise’s use of cyberspace for the purpose of disrupting, disabling, destroying, or maliciously controlling a computing environment/infrastructure; or destroying the integrity of the data or stealing controlled information.
_
A cyberattack is a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization. Usually, the attacker seeks some type of benefit from disrupting the victim’s network. Cyberattacks hit businesses every day. Former Cisco CEO John Chambers once said, “There are two types of companies: those that have been hacked, and those who don’t yet know they have been hacked.” According to the Cisco Annual Cybersecurity Report, the total volume of events has increased almost fourfold between January 2016 and October 2017. Cybercrime has increased every year as people try to benefit from vulnerable business systems. Often, attackers are looking for ransom: 53 percent of cyberattacks resulted in damages of $500,000 or more. Cyberthreats can also be launched with ulterior motives. Some attackers look to obliterate systems and data as a form of “hacktivism.” The 5 most cyber-attacked industries in 2016 — healthcare, manufacturing, financial services, government, and transportation — have remained largely the same today, although the rank order has been changing.
_
Types of cyberattack:
An attack can be active or passive.
An “active attack” attempts to alter system resources or affect their operation.
A “passive attack” attempts to learn or make use of information from the system but does not affect system resources (e.g., wiretapping).
An attack can be perpetrated by an insider or from outside the organization;
An “inside attack” is an attack initiated by an entity inside the security perimeter (an “insider”), i.e., an entity that is authorized to access system resources but uses them in a way not approved by those who granted the authorization.
An “outside attack” is initiated from outside the perimeter, by an unauthorized or illegitimate user of the system (an “outsider”). In the Internet, potential outside attackers range from amateur pranksters to organized criminals, international terrorists, and hostile governments.
Attacks are broken down into two categories: syntactic attacks and semantic attacks.
Syntactic attacks are straightforward; it is considered malicious software which includes viruses, worms, and Trojan horses.
Semantic attack is the modification and dissemination of correct and incorrect information. Information modified could have been done without the use of computers even though new opportunities can be found by using them. To set someone into the wrong direction or to cover your tracks, the dissemination of incorrect information can be utilized.
_
| Cyberviolence | Cyberpeddler | Cybertrespass | Cybersquatting |
| Denial of service/distributed denial of service | Keylogger and social engineering | Traffic analysis, eavesdropping, snooping, password attacks, SQL injection, salami attack, and data diddling | Session hijacking |
Table above shows classification of cyberattacks on the basis of cybercrime techniques.
_
How cyberattacks work:
An attack, particularly if carried out by a skilled adversary, may consist of repeated stages. Understanding the types of attack, and the stages involved, will help you to better defend yourself.
It’s useful to group attacks into two types: targeted and un-targeted.
Un-targeted cyberattacks:
In un-targeted attacks, attackers indiscriminately target as many devices, services or users as possible. They do not care about who the victim is as there will be a number of machines or services with vulnerabilities. To do this, they use techniques that take advantage of the openness of the Internet, which include:
phishing – sending emails to large numbers of people asking for sensitive information (such as bank details) or encouraging them to visit a fake website
water holing – setting up a fake website or compromising a legitimate one in order to exploit visiting users
ransomware – which could include disseminating disk encrypting extortion malware
scanning – attacking wide swathes of the Internet at random
Targeted cyberattacks:
In a targeted attack, your organisation is singled out because the attacker has a specific interest in your business, or has been paid to target you. The groundwork for the attack could take months so that they can find the best route to deliver their exploit directly to your systems (or users). A targeted attack is often more damaging than an un-targeted one because it has been specifically tailored to attack your systems, processes or personnel, in the office and sometimes at home.
Targeted attacks may include:
spear-phishing – sending emails to targeted individuals that could contain an attachment with malicious software, or a link that downloads malicious software
deploying a botnet – to deliver a DDoS (Distributed Denial of Service) attack
subverting the supply chain – to attack equipment or software being delivered to the organisation
Stages of an attack:
Regardless of whether an attack is targeted or un-targeted, or the attacker is using commodity or bespoke tools, cyberattacks have a number of stages in common. An attack, particularly if it is carried out by a persistent adversary, may consist of repeated stages. The attacker is effectively probing your defences for weaknesses that, if exploitable, will take them closer to their ultimate goal. Understanding these stages will help you to better defend yourself.
The four main stages present in most cyberattacks:
Survey – investigating and analysing available information about the target in order to identify potential vulnerabilities
Delivery – getting to the point in a system where a vulnerability can be exploited
Breach – exploiting the vulnerability/vulnerabilities to gain some form of unauthorised access
Affect – carrying out activities within a system that achieve the attacker’s goal
Determined and undetected attackers continue until they have achieved their end goals, which may can include:
-retrieving information they would otherwise not be able to access, such as intellectual property or commercially sensitive information
-making changes for their own benefit, such as creating payments into a bank account they control
-disrupting normal business operation, such as overloading the organisation’s internet connection so they cannot communicate externally, or deleting the whole operating system from users’ computers
After achieving their objectives, the more capable attacker will exit, carefully removing any evidence of their presence. Or they could create an access route for future visits by them, or for others they have sold the access to. Equally, some attackers will want to seriously damage your system or make as much ‘noise’ as possible to advertise their success.
_
In an ever-changing digital landscape, it is vital to keep pace with the impact of cyber trends. Cyberattacks are changing due to:
- Evolving targets: Information theft is the most expensive and fastest rising consequence of cybercrime. But data is not the only target. Core systems, such as industrial controls, are being hacked in a dangerous trend to disrupt and destroy.
- Evolving impact: While data remains a target, theft is not always the outcome. A new wave of cyberattacks sees data no longer simply being copied but being destroyed—or even changed in an attempt to breed distrust. Attacking data integrity—or preventing data toxicity—is the next frontier.
- Evolving techniques: Cyber criminals are adapting their attack methods. They are targeting the human layer—the weakest link in cyber defense—through increased ransomware and phishing and social engineering attacks as a path to entry. An interesting development is when nation-states and their associated attack groups use these types of techniques to attack commercial businesses. Attempts are being made to categorize attacks from these sources as ‘acts of war’ in an attempt to limit cybersecurity insurance settlements.
_
Remote access attacks:
Remote access attack is any malicious attack that targets any computer other than the computer the attacker is currently logged on to. For example, the attacker can log on to a system but actually attack any computer or server on the same network. Remote attacks are growing in number, as well as becoming more sophisticated. One of the main types of remote access attack in 2018 was cryptojacking, which targeted cryptocurrency owners. Another popular type of attack threatened perimeter devices.
Remote access attacks are among the most common attack vectors in a connected home. Hackers target computers, smartphones, internet protocol (IP) cameras and network attached storage (NAS) devices, since these tools usually need to have ports open and forwarded to external networks or the internet.
Vulnerabilities in home automation and the Internet of Things:
The consumer Internet of Things (IoT) industry is expected to grow to more than seven billion devices by the end of 2020, according to Gartner. Many consumers do not see IoT devices as a vulnerability, because a significant portion of them do not have a user interface. This could lead to issues understanding what kind of data the device collects or manages. However, IoT devices are not only collecting valuable user data. They could become an entry point for an attacker or tool to launch a distributed denial-of-service (DDoS) attack. IoT devices are not secure by design, because putting a focus on security would significantly increase manufacturing and maintenance expenses.
About 46% of all attack types that these devices experience are remote access attempts and 39% are used for detecting behavioural patterns. With the exponential growth of connected devices at home, these threats are likely to increase.
_
Here are the biggest cyber-attacks in recent history:
WannaCry:
WannaCry was a ransomware attack that spread rapidly in May of 2017. Like all ransomware, it took over infected computers and encrypted the contents of their hard drives, then demanded a payment in Bitcoin in order to decrypt them. The malware took particular root in computers at facilities run by the United Kingdom’s NHS. Malware isn’t anything new, though. What made WannaCry significant and scary was the means it used to propagate: it exploited a vulnerability in Microsoft Windows using code that had been secretly developed by the United States National Security Agency. Called EternalBlue, the exploit had been stolen and leaked by a hacking group called the Shadow Brokers. Microsoft had already patched the vulnerability a few weeks before, but many systems hadn’t upgraded. Microsoft was furious that the U.S. government had built a weapon to exploit the vulnerability rather than share information about the hole with the infosec community.
NotPetya:
Petya was just another piece of ransomware when it started circulating via phishing spam in 2016; its main claim to fame was that it encrypted the master boot record of infected machines, making it devilishly difficult for users to get access to their files.
Then, abruptly in June of 2017, a much more virulent version of the malware started spreading. It was different enough from the original that it was dubbed NotPetya; it originally propagated via compromised Ukrainian accounting software and spread via the same EternalBlue exploit that WannaCry used. NotPetya is widely believed to be a cyberattack from Russia against Ukraine, though Russia denies it, opening up a possible era of states using weaponized malware.
Ethereum:
While this one might not have been as high-profile as some of the others on this list, it deserves a spot here due to the sheer amount of money involved. Ether is a Bitcoin-style cryptocurrency, and $7.4 million in Ether was stolen from the Ethereum app platform in a manner of minutes in July 2017. Then, just weeks later came a $32 million heist. The whole incident raised questions about the security of blockchain-based currencies.
Equifax:
The credit rating agency announced in July of 2017 that “criminals exploited a U.S. website application vulnerability to gain access to certain files,” getting personal information for nearly 150 million people. The subsequent fallout enraged people further, especially when the site Equifax set up where people could see if their information had been compromised seemed primarily designed to sell Equifax services.
Yahoo (revised):
This massive hack of Yahoo’s email system gets an honorable mention because it actually happened way back in 2013 — but the severity of it, with all 3 billion Yahoo email addresses affected, only became clear in October 2017. Stolen information included passwords and backup email addresses, encrypted using outdated, easy-to-crack techniques, which is the sort of information attackers can use to breach other accounts. In addition to the effect on the account owners, the breach could spawn a revisiting of the deal by which Verizon bought Yahoo, even though that deal had already closed.
GitHub:
On February 28, 2018, the version control hosting service GitHub was hit with a massive denial of service attack, with 1.35 TB per second of traffic hitting the popular site. Although GitHub was only knocked offline intermittently and managed to beat the attack back entirely after less than 20 minutes, the sheer scale of the assault was worrying; it outpaced the huge attack on Dyn in late 2016, which peaked at 1.2 TB per second.
More troubling still was the infrastructure that drove the attack. While the Dyn attack was the product of the Mirai botnet, which required malware to infest thousands of IoT devices, the GitHub attack exploited servers running the Memcached memory caching system, which can return very large chunks of data in response to simple requests.
_
Cyberattacks continue to grow in sophistication, with attackers using an ever-expanding variety of tactics. This includes social engineering, malware and ransomware (used for Petya, WannaCry and NotPetya). In 2018, the cybercrime economy was estimated to be worth $1.5 trillion, according to a study commissioned by Bromium. Cyberattacks cost organisations billions of dollars and can cause serious damage. Impacted organisations stand to lose sensitive data, and face fines and reputational damage.
_
Cyberwarfare and cyberterrorism (vide infra):
Cyberwarfare refers to the use of cyberattacks — like computer viruses and hacking — by one country to disrupt the vital computer systems of another, with the aim of creating damage, death and destruction. Cyberterrorism, on the other hand, is “the use of computer network tools to shut down critical national infrastructures (such as energy, transportation, government operations) or to coerce or intimidate a government or civilian population”. That means the end result of both cyberwarfare and cyberterrorism is the same, to damage critical infrastructures and computer systems linked together within the confines of cyberspace. Three factors contribute to why cyber-attacks are launched against a state or an individual: the fear factor, spectacularity factor, and vulnerability factor.
Within cyberwarfare, the individual must recognize the state actors involved in committing these cyber-attacks against one another. The two predominant players are the age-old comparison of East versus West, China’s cyber capabilities compared to United States’ capabilities. There are many other state and non-state actors involved in cyberwarfare, such as Russia, Iran, Iraq, and Al Qaeda.
_
Traditionally, most cyber-attacks have been carried out by criminal organizations, with the majority of incidents failing to register on an enterprise risk scale of businesses that faced significant setbacks. In 2017, this dynamic changed with the WannaCry and NotPetya incidents. These two attacks affected organizations in more than 150 countries, prompted business interruption and other losses estimated at well over USD 300 million by some companies, brought reputational damage, and resulted in loss of customer data. In December 2017, the U.S. government took a rare step and attributed the WannaCry attack to hackers backed by North Korea. WannaCry and NotPetya exposed a systemic risk and affected a broad cross-section of businesses without specific targeting, demonstrating the potential for escalation in the threat of cyber terrorism.
______
______
Deep web and dark web:
Deep web:
The deep web, invisible web, or hidden web are parts of the World Wide Web whose contents are not indexed by standard web search-engines. The opposite term to the deep web is the “surface web”, which is accessible to anyone/everyone using the Internet. Computer-scientist Michael K. Bergman is credited with coining the term deep web in 2001 as a search-indexing term. The content of the deep web is hidden behind HTTP forms and includes many very common uses such as web mail, online banking, private or otherwise restricted access social-media pages and profiles, some web forums that require registration for viewing content, and services that users must pay for, and which are protected by paywalls, such as video on demand and some online magazines and newspapers. The content of the deep web can be located and accessed by a direct URL or IP address, but may require a password or other security access to get past public-website pages. According to app developer and cofounder of TBG Labs Harsha Halvi, the deep web makes up as much as about 65- 75% of the world wide web.
Dark web:
Dark Net (or Darknet) is the part of the Internet purposefully not open to public view, or hidden networks whose architecture is superimposed on that of the Internet. Darknet is a network built over internet where term dark web refers to websites on a darknet. The dark web is the World Wide Web content that exists on darknets, overlay networks that use the Internet but require specific software, configurations, or authorization to access. The dark web forms a small part of the deep web, the part of the Web not indexed by web search engines, although sometimes the term deep web is mistakenly used to refer specifically to the dark web. The dark web is a part of the deep web, the non-indexed part of the world wide web that cannot be accessed by standard search engines such as Google and requires encrypted networks such as Tor browser. Dark web are pages on servers that cannot be accessed by a search engine (or indeed, a user) without an appropriately permissioned account. Large scale illegal activity are happens in dark web.
The darknets which hosts the dark web include small, friend-to-friend peer-to-peer networks, as well as large, popular networks like Tor, Freenet, I2P, and Riffle operated by public organizations and individuals. Users of the dark web refer to the regular web as Clearnet due to its unencrypted nature. The Tor dark web may be referred to as onionland, a reference to the network’s top-level domain suffix .onion and the traffic anonymization technique of onion routing.
The Internet is multi-layered, there is the surface layer that anyone can get to but then there are deeper layers that are much harder to find, the Deep Web, and then there is a segment of deep web, the Dark Web where illegal activities occur on a daily basis. An increasing number of cyber criminals are using the dark web — the encrypted part of the internet that cannot be tracked — to shop for software that helps them remain anonymous while carrying out their crimes. The most significant feature of this world is that the identity of its users is hidden and cannot be tracked, which is why several illicit products such as weapons and drugs are available here. Cyber criminals, too, appear to be shopping here. Many tools that can be used to commit cyber frauds are available on the dark web. Bitcoin transactions are the preferred mode of payment for purchases on the dark web as they cannot be traced.
_
The Dark Web allows users to remain anonymous through encryption. This is attractive to anyone involved in illegal activity, such as child pornography, sex trafficking, illicit drugs, or counterfeit goods. But it also may be useful for anyone living in an authoritarian state wishing to communicate with the outside world, as well as providing a safe space for whistleblowers. So while it’s not illegal to visit the Dark Web, it provides access to illegal activities.
Web sites that exist on the Dark Web are encrypted (and thus difficult to track), most commonly through the Tor encryption tool. Therefore, most Dark Web users access those sites using the Tor browser. There are other encryption tools and corresponding browsers such as I2P (these are not universal, by design) and you have to know the exact URL in order to access the site. There’s no “Google” for the Dark Web because that kind of indexing would provide a breadcrumb trail for investigators.
Another layer of anonymity involves the way payments are processed. Silk Road, for example, only accepted payment via Bitcoin, which is an unregulated cryptocurrency. As with the Dark Web generally, there’s nothing illegal about using Bitcoin. But the anonymity of Bitcoin payments is attractive to those making illegal transactions.
_
Cybercriminals have become reliant on the Tor network to maintain anonymity. Tor, short for The Onion Router, allows users to browse the internet anonymously by encrypting their traffic and then routing it through multiple random relays on its way to its destination. This process makes it nearly impossible for law enforcement agencies to track users or determine the identities of visitors to certain sites. While Tor can be used to anonymously browse ordinary sites like Wikipedia or YouTube, its greatest advantage to cybercriminals comes in its ability to access special “dot.onion” addresses on the dark web, which serves as the home for most internet black markets.
As of June 2017, Europol found that the Tor network had more than 2.2 million users and hosted almost 60,000 unique onion domains. Researchers disagree over how much of the traffic on Tor is illicit, but one recent study has estimated that approximately 57% of onion sites hosted illegal content. Though some law enforcement actions have managed to exploit vulnerabilities in Tor to take down sites hosting child pornography, Tor is still considered to be highly resilient to law enforcement efforts. Most of the successes in shutting down dark net marketplaces in the past were the result of police exploiting mistakes made by site administrators, not through the compromise of Tor itself.
_
How Dark Web crimes are investigated:
Because of the anonymous nature of the Dark Web, investigators have their work cut out for them. One of the main ways to catch criminals is by going undercover online, which can sometimes lead to real-life connections when, for example, an officer posing as a seller obtains the buyer’s mailing address. Also, the target of an investigation may slip up and reveal personally identifying information. In fact, an investigator with the Internal Revenue Service found an incriminating comment by Silk Road’s Ulbricht along with his email address, which would lead to his eventual arrest.
Since many of the transactions conducted via the Dark Web are completed by the U.S. Postal Service, police sometimes are able to match online clues with surveillance footage, handwriting analysis, and other clues. They may even find fingerprints on the package, potentially revealing the sender’s identity. Following the money also can be effective, even though the anonymous nature of Bitcoin makes that much more difficult. Still, the Department of Homeland Security has a dedicated task force focused on tracking money laundering via cryptocurrencies.
Other approaches involve the use of sophisticated technology and hacking techniques. For example, the FBI used malware to go after child pornography site Playpen. The software caused users who clicked on the forum to reveal their real IP addresses, which were then sent to investigators. Another hacking technique exploited a vulnerability in the Tor browser, allowing investigators to see the IP addresses of Dark Web marketplaces and users.
_____
_____
How Cybercrime is changing:
- More First-Timers
Investigations into the dark web illegal trading have revealed that most traders involved in the act had little or no prior records. Many Individuals involved directly or indirectly in the cyber felonies are often new to the dark web, and unlikely to have a previous felony or even a misdemeanour history. In 2017 a study by Alec Fullerton showed that many students across campuses started turning to the dark web for buying and selling of drugs and narcotics.
- Better Phishing Techniques
Cybercriminals are evolving their phishing techniques and are using more targeted approach to lure their preys in handing over sensitive and compromisable information. They do not rely anymore on the basic tactics for social engineering like made-up & misspelled URLs, or Nigerian Princes’ leaving the inheritance to us. They now do a deep research on the target victim and use advance Malware and Trojans to get their information, including sensitive data like social security numbers, insurance details and banking credentials.
- Rise of Hacktivists and Cyber Vigilantes
Cyber vigilantes are standing up against cybercriminals and scammers trying to bring them to justice in their own ways, like scam baiting, public shaming, DDoS attacks, etc. Whereas, ‘Hacktivists’, a blend of hacking and activism, target government agencies to paralyze them, release compromisable data in the cyberspace, as a protest against them for a political or social cause. Efforts of cyber vigilantism & hacktivism are expected to significantly increase in the next few years. While debating the moral cause behind hacktivism and vigilantism remains a separate discussion, the fact still remains that these intrusions often put cybersecurity at risk and may even jeopardize the security of the whole nation itself.
- Fighting Cyber Crime is getting Harder
Encryption and anonymization on the internet are a new normal. It is becoming harder for law enforcement agencies to fight cybercriminals with new and advanced anonymization techniques. Anonymization is as effective as encryption because it allows any available data to be non-attributable to a user. Such data flow limits a law enforcement agency’s capability to track and detect the culprits.
- Difficulty in bringing justice to Cybercrimes
Determining the level of the penalty based on a cybercrime is a challenge in itself; there is a lack of a universal cybercrime law structure that helps levy penalties, fines and jail time. Considering the fact that cybercrimes are often global, it is certainly a challenge to track and bring justice to a hacker on the opposite side of the world as there no cyber-borders between countries.
- Rise in Organized Cybercrime
A vast majority of data breaches are often a result of organized crime. Cybergangs have been more disciplined in their crime lately and are now being referred to as organized crime syndicates and groups. In the past 30 years, cybercrime has evolved from what was an orthodox structure to a modern and more organized style of selling – “Fraud as a Service” (FaaS). Many Hacker groups are now so sophisticated that they are at par with many states in their capabilities in system intrusion and penetration.
- Ease of Payment for Cybercrimes
Cryptocurrency and internet money have enabled a whole new world of anonymous payments without a paper trail. Payments in cash and kind often leave an array of breadcrumbs for authorities to sniff, even after being extremely careful. Collecting, storing or laundering money from criminal proceedings is a challenge that many convicts have failed at. However, with the introduction of cryptocurrencies like Bitcoin, hackers are now more motivated to commit cybercrimes with a belief that they will remain incognito. Cryptocurrencies are anonymous and unregulated which makes the transactions easy for cybercriminals and thus, can do so hiding in plain sight.
- Massive increase in Digital Sphere
Use of digital technologies has rapidly increased around the globe and is still on the rise. Everyone and every device connected to the internet is a potential target for cybercrimes. A direct correlation can be observed with rise in Internet of Things (IoT) devices and ease of cybercrime. For example, in 2016 Mirai Botnet attacked the insecure IoT and left much of the internet inaccessible on the US east coast. As the digital sphere has increased, the opportunity for cybercrime has also increased to a great extent.
- State-Sponsored Cyber Attacks
In recent years, State-sponsored cyber-attacks have increased dramatically; building cyber-armies and cyber defense capabilities have become a quintessential national security strategy. More than 20 countries display impressive offensive & defensive cyber capabilities. For example, in 2015, US alleged China breached several databases of the US Office of Personnel Management, stealing Social Security Numbers of more than 21 million people interviewed for government background checks. In 2014, North Korea attacked Sony Pictures Entertainment, and stole gigabytes of data and later posted the compromised data online. The most recent was that of the alleged politically-motivated ‘NotPetya malware’ attack against Ukraine by Russia in 2016. The world of cybercrime is changing dynamically with cyber proxy wars among nations.
- Lack of Government interest in Average Cybercrimes
Recent cyber-attacks have been exceptionally bad to companies, incurring hundreds of millions of dollars in losses. Still, governments around the globe haven’t made great strides in securing digital assets of their citizens. It almost seems like cybersecurity has been put on the backburner by some governments while prioritizing other tasks. Not considering cybersecurity to be a national issue could potentially be devastating a strategy.
Along with the changing world, the nature of crimes has also transformed and become virtual. Acts of stealing, extorting, blackmail, illegal trading, etc. have now become, hacking, ransomware, online blackmailing and dark web trading. There is a great need be secure in this virtually threatening world, cybersecurity best practices should be a top priority for any Individual or firm, to secure and maintain their digital assets.
______
Cybercrime is increasing:
For many reasons, there are no reliable statistics on cybercrime. Cybercrime is a vast area and covers innumerable crimes and no common statistics system exists. Because of the difficulties arising when trying to define and identify cybercrime, cross-national comparative statistics on cybercrime are much rarer than for other crime types.
The increasing ubiquity of global connectivity presents a serious risk that rates of cybercrime will increase and are increasing. A range of cybercrime acts are increasing, such as computer-related fraud and identity theft, computer-related production, distribution or possession of child pornography, phishing attempts and illegal access to computer systems, including hacking.
Criminological theories and socio-economic approaches offer several possible explanations for the growth of cybercrime. The increasing use of the Internet and ICT create new opportunities for offenders and facilitates the growth of crime. Another underlying development that contributes to driving cybercrime levels is the emergence of global connectivity in the context of world economic and demographic transformations. Socio-economic factors may play an important role in increases in cybercrime. Pressure on private sector enterprises to cut spending and to reduce staffing levels can lead to reductions in security and to opportunities for exploitation of ICT weaknesses.
This is a significant increase in cybercrime over few years. CSIS believes that five trends help explain this. The first is state-sponsored bank robbery, followed by ransomware, Cybercrime-as-a-Service, an increased reliance on anonymization services (such as Tor and digital currencies), and, finally, the prevalence of the theft of personal information and the theft of intellectual property (IP).
______
______
History and evolution of cybercrime:
Computers, computer networks and the Internet were created for the creation, storage and transfer of government and corporate information, information that is very valuable to the right people. The creation of a digitized methods may have pushed mankind into the 21st century but it did the same thing for criminals. They want what we have and the harder we make it for them to find, retrieve and utilize the more they will want to take it. If not for personal gains then just because they can.
_
The first recorded cybercrime took place in the year 1820! That is not surprising considering the fact that the abacus, which is thought to be the earliest form of a computer, has been around since 3500 B.C. in India, Japan and China. The era of modern computers, however, began with the analytical engine of Charles Babbage. In 1820, JosephMarie Jacquard, a textile manufacturer in France, produced the loom. This device allowed the repetition of a series of steps in the weaving of special fabrics. This resulted in a fear amongst Jacquard’s employees that their traditional employment and livelihood were being threatened. They committed acts of sabotage to discourage Jacquard from further use of the new technology. This is the first recorded cybercrime! The first spam email took place in 1976 when it was sent out over the ARPAnet. The first virus was installed on an Apple computer in 1982 when a high school student, Rich skrenta, developed the EIK Cloner.
_
In the late 70s, first ever computer virus “Creeper” was created that targeted a telephone company to make free long-distance calls. That was the first encounter of any cybercrime that resulted in the launch of a first antivirus called “Reaper.” Internet Technology becomes popular and familiar in 2000’s; people and organizations started using the internet for making money. It’s very difficult to crack down on cyber criminals as they didn’t use their actual location but located virtually. They attack anonymously and also impersonate people to receive money. Cyber-attacks that started from the single Creeper virus has now reached to a huge collection of viruses and malware. There are many cases in the history that changed the world of hacking. The virus that changed the modern day cybercrime “Morris Worm” was one of the first computer worms distributed via the Internet in 1988. It was first to gain media attention.
The graph above shows that how cyberattacks have changed over the years. Now the most widely used attacks are ransomware, point of sale attacks, Botnets, Phishing attacks, Cyber Warfare and network traveling worms. These attacks are widespread nowadays and affecting millions of people around the world.
_
The 1960s
In the 1960s, the introduction of transistor-based computer systems, which were smaller and less expensive than vacuum-tube based machines, led to an increase in the use of computer technology. At this early stage, offences focused on physical damage to computer systems and stored data. Such incidents were reported, for example, in Canada, where in 1969 a student riot caused a fire that destroyed computer data hosted at the university. In the mid 1960s, the United States started a debate on the creation of a central data-storage authority for all ministries. Within this context, possible criminal abuse of databases and the related risks to privacy were discussed.
The 1970s
In the 1970s, the use of computer systems and computer data increased further. At the end of the decade, an estimated number of 100,000 mainframe computers were operating in the United States. With falling prices, computer technology was more widely used within administration and business, and by the public. The 1970s were characterized by a shift from the traditional property crimes against computer systems that had dominated the 1960s, to new forms of crime. While physical damage continued to be a relevant form of criminal abuse against computer systems, new forms of computer crime were recognized. They included the illegal use of computer systems and the manipulation of electronic data. The shift from manual to computer-operated transactions led to another new form of crime – computer-related fraud. Already at this time, multimillion-dollar losses were caused by computer-related fraud. Computer-related fraud, in particular, was a real challenge, and law enforcement agencies were investigating more and more cases. As the application of existing legislation in computer-crime cases led to difficulties, a debate about legal solutions started in different parts of the world. The United States discussed a draft bill designed specifically to address cybercrime. Interpol discussed the phenomena and possibilities for legal response.
The 1980s
In the 1980s, personal computers became more and more popular. With this development, the number of computer systems and hence the number of potential targets for criminals again increased. For the first time, the targets included a broad range of critical infrastructure. One of the side effects of the spread of computer systems was an increasing interest in software, resulting in the emergence of the first forms of software piracy and crimes related to patents. The interconnection of computer systems brought about new types of offence. Networks enabled offenders to enter a computer system without being present at the crime scene. In addition, the possibility of distributing software through networks enabled offenders to spread malicious software, and more and more computer viruses were discovered. Countries started the process of updating their legislation so as to meet the requirements of a changing criminal environment. International organizations also got involved in the process. OECD and the Council of Europe set up study groups to analyse the phenomena and evaluate possibilities for legal response.
The 1990s
The introduction of the graphical interface (“WWW”) in the 1990s that was followed by a rapid growth in the number of Internet users led to new challenges. Information legally made available in one country was available globally – even in countries where the publication of such information was criminalized. Another concern associated with online services that turned out to be especially challenging in the investigation of transnational crime was the speed of information exchange. Finally, the distribution of child pornography moved from physical exchange of books and tapes to online distribution through websites and Internet services. While computer crimes were in general local crimes, the Internet turned electronic crimes into transnational crime. As a result, the international community tackled the issue more intensively. UN General Assembly Resolution 45/121 adopted in 1990 and the manual for the prevention and control of computer-related crimes issued in 1994 are just two examples.
The 21st Century
As in each preceding decade, new trends in computer crime and cybercrime continued to be discovered in the 21st century. The first decade of the new millennium was dominated by new, highly sophisticated methods of committing crimes, such as “phishing”, and “botnet attacks”, and the emerging use of technology that is more difficult for law enforcement to handle and investigate, such as “voice-over-IP (VoIP) communication” and “cloud computing”. It is not only the methods that changed, but also the impact. As offenders became able to automate attacks, the number of offences increased. Countries and regional and international organizations have responded to the growing challenges and given response to cybercrime high priority.
_
Figure below is showing various stages of cyberattack evolution from year 1980 to the year 2000+
_____
_____
Methods and Types of cybercrimes:
Now I will discuss common methods (techniques) of cybercrimes in brief:
_
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks:
DoS (denial of service) is a very common attack that disrupts the availability of the network and its resources. An attacker can attack his/her target directly or indirectly or both. In direct attack, the attacker generates huge traffic by using his/her own computer system, and in indirect attack, the attacker uses bots (a system that is hacked by an attacker and is under his/her control) to generate huge traffic for his/her target. A large variant of the DoS attack is DDoS (distributed denial-of-service) attack in which a number of bots or even a server can be used to make an attack on the target to disrupt his/her network services. DoS/DDoS attack can disrupt the network bandwidth, system resources, and application resources.
Unlike attacks that are designed to enable the attacker to gain or increase access, denial-of-service doesn’t provide direct benefits for attackers. For some of them, it’s enough to have the satisfaction of service denial. However, if the attacked resource belongs to a business competitor, then the benefit to the attacker may be real enough. Another purpose of a DoS attack can be to take a system offline so that a different kind of attack can be launched. There are different types of DoS and DDoS attacks; the most common are TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack and botnets.
The consequences of a DoS attack are the following:
(i) Slow network performance
(ii) Unavailability of network services
_
Botnets:
Botnets are the millions of systems infected with malware under hacker control in order to carry out DDoS attacks. These bots or zombie systems are used to carry out attacks against the target systems, often overwhelming the target system’s bandwidth and processing capabilities. These DDoS attacks are difficult to trace because botnets are located in differing geographic locations.
_____
Hacking:
Hacking means unauthorized access to another computer system. It is the most popular and commonly known Cybercrime. Hackers will break into networks and computers system for multiple purposes like data theft, fraud, destruction of data, causing damage to computer system for mere pleasure or personal satisfaction.
Hacking is the basic act of the criminals who later on tread on to the other computer related crimes and frauds.
Hacking is the act of illegally accessing a system in order to achieve a high degree of knowledge and gain information regarding both the operation and the data it contains, in order to adapt it to the hacker’s needs. The term hacking has acquired numerous identities during the period in which the cyber world has developed, gaining both negative and positive connotations. The use of techniques and methods of hacking – with the goal of making a gain – are direct and material, indirect (by stealing information in order to resell the item or product), or with the purpose of damaging the victim company (called cracking). In our imagination, the hacker is a curious and solitary person motivated by challenge and personal interests, but the reality is different. The figure of the hacker is now groups of organized criminals who, through hacking, pursue economic motives for profit.
_
| Hacking | In the context of cybercrime, hacking is an umbrella term that applies to a variety of human activities that interfere with the proper operation of computer systems and networks. Most legal systems, however, do not use the term hacking due to its ambiguity. A list of more specific hacking behaviours is criminalised instead. The U.S. Computer Fraud and Abuse Act defines a number of criminal offenses related to hacking that include: | |
| • | computer espionage | |
| • | computer trespassing with the aim to obtain data | |
| • | computer trespassing that interferes with the intended computer use | |
| • | damaging a protected computer by various means including malware | |
| • | threatening to damage a protected computer | |
| • | trafficking in passwords and other hacking tools. | |
| The Council of Europe Convention on Cybercrime (2001) similarly defines a list of five offenses related to hacking: | ||
| • | unauthorised access to computer systems and networks | |
| • | unauthorised interception of transmitted or displayed data | |
| • | unauthorised data interference, such as data deletion, alteration, suppression, deterioration, etc. | |
| • | unauthorised hindering of system operation (denial of service) | |
| • | making or possessing hacking tools, such as malware, remote access exploits, databases of stolen passwords, etc.
The key requirement of the above criminal offenses is the absence of authorisation and – in some cases – the dishonest intent or attempt to bypass security controls. It is perfectly legal, for example, to attempt hacking into a computer system with proper authorisation to test system security. This form of security testing is called penetration testing. The term white hat hacker applies to individuals that perform authorised hacking for benign purposes. The term black hat hacker refers to criminal hackers. |
|
_____
Man-in-the-middle (MitM) attack:
A MitM attack occurs when a hacker inserts itself between the communications of a client and a server. Here are some common types of man-in-the-middle attacks:
Session hijacking:
In this type of MitM attack, an attacker hijacks a session between a trusted client and network server. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client.
IP Spoofing:
IP spoofing is used by an attacker to convince a system that it is communicating with a known, trusted entity and provide the attacker with access to the system. The attacker sends a packet with the IP source address of a known, trusted host instead of its own IP source address to a target host. The target host might accept the packet and act upon it.
E- mail spoofing:
E-mail is the short form for ‘electronic mail’. The electronic mail system over the internet can carry messages, letters, pictures, sounds, or anything that can be created and stored in a computer. Data can be sent as electronic mail to any other computer connected to the internet. E-mail spoofing is a technique commonly used to hide the origin of an e mail message. The result is that, although the e-mail appears to have come from a particular address it comes actually from other sources.
Replay:
A replay attack occurs when an attacker intercepts and saves old messages and then tries to send them later, impersonating one of the participants. This type can be easily countered with session timestamps or nonce (a random number or a string that changes with time).
Currently, there is no single technology or configuration to prevent all MitM attacks. Generally, encryption and digital certificates provide an effective safeguard against MitM attacks, assuring both the confidentiality and integrity of communications. But a man-in-the-middle attack can be injected into the middle of communications in such a way that encryption will not help.
_____
Social engineering:
Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
Social engineering attacks happen in one or more steps. A perpetrator first investigates the intended victim to gather necessary background information, such as potential points of entry and weak security protocols, needed to proceed with the attack. Then, the attacker moves to gain the victim’s trust and provide stimuli for subsequent actions that break security practices, such as revealing sensitive information or granting access to critical resources.
_
Social Engineering Attack Lifecycle:
What makes social engineering especially dangerous is that it relies on human error, rather than vulnerabilities in software and operating systems. Mistakes made by legitimate users are much less predictable, making them harder to identify and thwart than a malware-based intrusion.
_
Social engineering attack techniques:
Social engineering attacks come in many different forms and can be performed anywhere where human interaction is involved. The following are the five most common forms of digital social engineering assaults.
- Baiting
As its name implies, baiting attacks use a false promise to pique a victim’s greed or curiosity. They lure users into a trap that steals their personal information or inflicts their systems with malware. The most reviled form of baiting uses physical media to disperse malware. For example, attackers leave the bait—typically malware-infected flash drives—in conspicuous areas where potential victims are certain to see them (e.g., bathrooms, elevators, the parking lot of a targeted company). The bait has an authentic look to it, such as a label presenting it as the company’s payroll list. Victims pick up the bait out of curiosity and insert it into a work or home computer, resulting in automatic malware installation on the system. Baiting scams don’t necessarily have to be carried out in the physical world. Online forms of baiting consist of enticing ads that lead to malicious sites or that encourage users to download a malware-infected application.
- Scareware
Scareware involves victims being bombarded with false alarms and fictitious threats. Users are deceived to think their system is infected with malware, prompting them to install software that has no real benefit (other than for the perpetrator) or is malware itself. Scareware is also referred to as deception software, rogue scanner software and fraudware. A common scareware example is the legitimate-looking popup banners appearing in your browser while surfing the web, displaying such text such as, “Your computer may be infected with harmful spyware programs.” It either offers to install the tool (often malware-infected) for you, or will direct you to a malicious site where your computer becomes infected. Scareware is also distributed via spam email that doles out bogus warnings, or makes offers for users to buy worthless/harmful services.
- Pretexting
Here an attacker obtains information through a series of cleverly crafted lies. The scam is often initiated by a perpetrator pretending to need sensitive information from a victim so as to perform a critical task. The attacker usually starts by establishing trust with their victim by impersonating co-workers, police, bank and tax officials, or other persons who have right-to-know authority. The pretexter asks questions that are ostensibly required to confirm the victim’s identity, through which they gather important personal data.
All sorts of pertinent information and records is gathered using this scam, such as social security numbers, personal addresses and phone numbers, phone records, staff vacation dates, bank records and even security information related to a physical plant.
- Phishing
As one of the most popular social engineering attack types, phishing scams are email and text message campaigns aimed at creating a sense of urgency, curiosity or fear in victims. It then prods them into revealing sensitive information, clicking on links to malicious websites, or opening attachments that contain malware. An example is an email sent to users of an online service that alerts them of a policy violation requiring immediate action on their part, such as a required password change. It includes a link to an illegitimate website—nearly identical in appearance to its legitimate version—prompting the unsuspecting user to enter their current credentials and new password. Upon form submittal the information is sent to the attacker. Given that identical, or near-identical, messages are sent to all users in phishing campaigns, detecting and blocking them are much easier for mail servers having access to threat sharing platforms.
Phishing is a technique of extracting confidential information such as credit card numbers and username password combos by masquerading as a legitimate enterprise. Phishing is typically carried out by email spoofing. You’ve probably received email containing links to legitimate appearing websites. You probably found it suspicious and didn’t click the link.
The malware would have installed itself on your computer and stolen private information. Cyber-criminals use social engineering to trick you into downloading malware off the internet or make you fill in your personal information under false pretences. A phishing scam in an email message can be evaded by keeping certain things in mind.
-Look for spelling mistakes in the text. Cyber-criminals are not known for their grammar and spelling.
-Hover your cursor over the hyperlinked URL but don’t click. Check if the address matches with the one written in the message.
-Watch out for fake threats. Did you receive a message saying “Your email account will be closed if you don’t reply to this email”? They might trick you by threatening that your security has been compromised.
-Attackers use the names and logos of well-known web sites to deceive you. The graphics and the web addresses used in the email are strikingly similar to the legitimate ones, but they lead you to phony sites.
-Most viruses, Trojan horses, and worms are activated when you open an attachment or click a link contained in an email message. If your email client allows scripting, then it is possible to get a virus by simply opening a message. It’s best to limit what HTML is available in your email messages. The safest way to view email messages is in plain text.
Not all phishing is done via email or web sites.
Vishing (voice phishing) involves calls to victims using fake identity fooling you into considering the call to be from a trusted organisation. They may claim to be from a bank asking you to dial a number (provided by VoIP service and owned by attacker) and enter your account details. Once you do that, your account security is compromised. Treat all unsolicited phone calls with scepticism and never provide any personal information. Many banks have issued pre-emptive warnings informing their users of phishing scams and the do’s and don’ts regarding your account information.
- Spear phishing
This is a more targeted version of the phishing scam whereby an attacker chooses specific individuals or enterprises. They then tailor their messages based on characteristics, job positions, and contacts belonging to their victims to make their attack less conspicuous. Spear phishing requires much more effort on behalf of the perpetrator and may take weeks and months to pull off. They’re much harder to detect and have better success rates if done skilfully. A spear phishing scenario might involve an attacker who, in impersonating an organization’s IT consultant, sends an email to one or more employees. It’s worded and signed exactly as the consultant normally does, thereby deceiving recipients into thinking it’s an authentic message. The message prompts recipients to change their password and provides them with a link that redirects them to a malicious page where the attacker now captures their credentials.
Social engineering prevention:
Social engineers manipulate human feelings, such as curiosity or fear, to carry out schemes and draw victims into their traps. Therefore, be wary whenever you feel alarmed by an email, attracted to an offer displayed on a website, or when you come across stray digital media lying about. Being alert can help you protect yourself against most social engineering attacks taking place in the digital realm. Moreover, the following tips can help improve your vigilance in relation to social engineering hacks.
-Don’t open emails and attachments from suspicious sources – If you don’t know the sender in question, you don’t need to answer an email. Even if you do know them and are suspicious about their message, cross-check and confirm the news from other sources, such as via telephone or directly from a service provider’s site. Remember that email addresses are spoofed all of the time; even an email purportedly coming from a trusted source may have actually been initiated by an attacker.
-Use multifactor authentication – One of the most valuable pieces of information attackers seek are user credentials. Using multifactor authentication helps ensure your account’s protection in the event of system compromise.
-Be wary of tempting offers – If an offer sounds too enticing, think twice before accepting it as fact. Googling the topic can help you quickly determine whether you’re dealing with a legitimate offer or a trap.
-Keep your antivirus/antimalware software updated – Make sure automatic updates are engaged, or make it a habit to download the latest signatures first thing each day. Periodically check to make sure that the updates have been applied, and scan your system for possible infections.
______
SQL injection attack:
Structured Query Language (SQL) is a standard computer language for relational database management and data manipulation. SQL is used to query, insert, update and modify data. SQL injection has become a common issue with database-driven websites. It occurs when a malefactor executes a SQL query to the database via the input data from the client to server. SQL commands are inserted into data-plane input (for example, instead of the login or password) in order to run predefined SQL commands. A successful SQL injection exploit can read sensitive data from the database, modify (insert, update or delete) database data, execute administration operations (such as shutdown) on the database, recover the content of a given file, and, in some cases, issue commands to the operating system.
The vulnerability to this type of cyber security attack depends on the fact that SQL makes no real distinction between the control and data planes. Therefore, SQL injections work mostly if a website uses dynamic SQL. Additionally, SQL injection is very common with PHP and ASP applications due to the prevalence of older functional interfaces. J2EE and ASP.NET applications are less likely to have easily exploited SQL injections because of the nature of the programmatic interfaces available.
In order to protect yourself from a SQL injection attacks, apply least privilege model of permissions in your databases. Stick to stored procedures (make sure that these procedures don’t include any dynamic SQL) and prepared statements (parameterized queries). The code that is executed against the database must be strong enough to prevent injection attacks. In addition, validate input data against a white list at the application level.
______
Cross-site scripting (XSS) attack
XSS attacks use third-party web resources to run scripts in the victim’s web browser or scriptable application. Specifically, the attacker injects a payload with malicious JavaScript into a website’s database. When the victim requests a page from the website, the website transmits the page, with the attacker’s payload as part of the HTML body, to the victim’s browser, which executes the malicious script. For example, it might send the victim’s cookie to the attacker’s server, and the attacker can extract it and use it for session hijacking. The most dangerous consequences occur when XSS is used to exploit additional vulnerabilities. These vulnerabilities can enable an attacker to not only steal cookies, but also log key strokes, capture screenshots, discover and collect network information, and remotely access and control the victim’s machine.
While XSS can be taken advantage of within VBScript, ActiveX and Flash, the most widely abused is JavaScript — primarily because JavaScript is supported widely on the web. To defend against XSS attacks, developers can sanitize data input by users in an HTTP request before reflecting it back. Make sure all data is validated, filtered or escaped before echoing anything back to the user, such as the values of query parameters during searches. Convert special characters such as ?, &, /, <, > and spaces to their respective HTML or URL encoded equivalents. Give users the option to disable client-side scripts.
______
Eavesdropping attack:
Eavesdropping attacks occur through the interception of network traffic. By eavesdropping, an attacker can obtain passwords, credit card numbers and other confidential information that a user might be sending over the network. Eavesdropping can be passive or active:
Passive eavesdropping — A hacker detects the information by listening to the message transmission in the network.
Active eavesdropping — A hacker actively grabs the information by disguising himself as friendly unit and by sending queries to transmitters. This is called probing, scanning or tampering.
Detecting passive eavesdropping attacks is often more important than spotting active ones, since active attacks requires the attacker to gain knowledge of the friendly units by conducting passive eavesdropping before.
Data encryption is the best countermeasure for eavesdropping.
______
Birthday attack:
Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software or digital signature. A message processed by a hash function produces a message digest (MD) of fixed length, independent of the length of the input message; this MD uniquely characterizes the message. The birthday attack refers to the probability of finding two random messages that generate the same MD when processed by a hash function. If an attacker calculates same MD for his message as the user has, he can safely replace the user’s message with his, and the receiver will not be able to detect the replacement even if he compares MDs.
______
Malware attack:
Malware means malicious software. Malware is any software intentionally designed to cause damage to a computer, server, client, or computer network. By contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug. Malicious software can be described as unwanted software that is installed in your system without your consent. It can attach itself to legitimate code and propagate; it can lurk in useful applications or replicate itself across the Internet. Malware includes computer viruses, worms, Trojan horses, ransomware, spyware and other malicious programs. A Virus is a malicious executable code attached to another executable file. The virus spreads when an infected file is passed from system to system. Viruses can be harmless or they can modify or delete data. Opening a file can trigger a virus. Once a program virus is active, it will infect other programs on the computer.
Here are some of the most common types of malware:
Macro viruses — These viruses infect applications such as Microsoft Word or Excel. Macro viruses attach to an application’s initialization sequence. When the application is opened, the virus executes instructions before transferring control to the application. The virus replicates itself and attaches to other code in the computer system.
File infectors — File infector viruses usually attach themselves to executable code, such as .exe files. The virus is installed when the code is loaded. Another version of a file infector associates itself with a file by creating a virus file with the same name, but an .exe extension. Therefore, when the file is opened, the virus code will be executed.
System or boot-record infectors — A boot-record virus attaches to the master boot record on hard disks. When the system is started, it will look at the boot sector and load the virus into memory, where it can propagate to other disks and computers.
Polymorphic viruses — These viruses conceal themselves through varying cycles of encryption and decryption. The encrypted virus and an associated mutation engine are initially decrypted by a decryption program. The virus proceeds to infect an area of code. The mutation engine then develops a new decryption routine and the virus encrypts the mutation engine and a copy of the virus with an algorithm corresponding to the new decryption routine. The encrypted package of mutation engine and virus is attached to new code, and the process repeats. Such viruses are difficult to detect but have a high level of entropy because of the many modifications of their source code. Anti-virus software or free tools like Process Hacker can use this feature to detect them.
Stealth viruses — Stealth viruses take over system functions to conceal themselves. They do this by compromising malware detection software so that the software will report an infected area as being uninfected. These viruses conceal any increase in the size of an infected file or changes to the file’s date and time of last modification.
Trojans — A Trojan or a Trojan horse is a program that hides in a useful program and usually has a malicious function. A major difference between viruses and Trojans is that Trojans do not self-replicate. In addition to launching attacks on a system, a Trojan can establish a back door that can be exploited by attackers. For example, a Trojan can be programmed to open a high-numbered port so the hacker can use it to listen and then perform an attack.
Logic bombs — A logic bomb is a type of malicious software that is appended to an application and is triggered by a specific occurrence, such as a logical condition or a specific date and time.
Worms — Worms differ from viruses in that they do not attach to a host file, but are self-contained programs that propagate across networks and computers. Worms are commonly spread through email attachments; opening the attachment activates the worm program. A typical worm exploit involves the worm sending a copy of itself to every contact in an infected computer’s email address In addition to conducting malicious activities, a worm spreading across the internet and overloading email servers can result in denial-of-service attacks against nodes on the network.
Droppers — A dropper is a program used to install viruses on computers. In many instances, the dropper is not infected with malicious code and, therefore might not be detected by virus-scanning software. A dropper can also connect to the internet and download updates to virus software that is resident on a compromised system.
Ransomware — Ransomware is a type of malware that blocks access to the victim’s data and threatens to publish or delete it unless a ransom is paid. While some simple computer ransomware can lock the system in a way that is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, which encrypts the victim’s files in a way that makes them nearly impossible to recover without the decryption key.
Adware — Adware is a software application used by companies for marketing purposes; advertising banners are displayed while any program is running. Adware can be automatically downloaded to your system while browsing any website and can be viewed through pop-up windows or through a bar that appears on the computer screen automatically.
Spyware — Spyware is a type of program that is installed to collect information about users, their computers or their browsing habits. It tracks everything you do without your knowledge and sends the data to a remote user. It also can download and install other malicious programs from the internet. Spyware works like adware but is usually a separate program that is installed unknowingly when you install another freeware application.
Backdoors – A backdoor bypasses the usual authentication used to access a system. The purpose of the backdoor is to grant the cyber criminals future access to the system even if the organization fixes the original vulnerability used to attack the system.
Rootkits –A rootkit modifies the OS to make a backdoor. Attackers then use the backdoor to access the computer distantly. Most rootkits take advantage of software vulnerabilities to modify system files.
Keyloggers –Keylogger records everything the user types on his/her computer system to obtain passwords and other sensitive information and send them to the source of the keylogging program.
_
Below a simple diagram shows how malware can propagate:
The malicious code or virus is inserted into the chain of command so that when the infected program is run, the viral code is also executed (or in some cases, runs instead of the legitimate program). Viruses are usually seen as extraneous code attached to a host program, but this isn’t always the case. Sometimes, the environment is manipulated so that calling a legitimate uninfected program calls the viral program. The viral program may also be executed before any other program is run. This can virtually infect every executable file on the computer, even though none of those files’ code was actually tampered with. Viruses that follow this modus operandi include “cluster” or “FAT” (File Allocation Table) viruses, which redirect system pointers to infected files, associate viruses and viruses that modify the Windows Registry directory entries so that their own code is executed before any other legitimate program.
Computer viruses usually spread via removable media or the internet. A flash disk, CD-ROM, magnetic tape or other storage device that has been in an infected computer infects all future computers in which it’s used. Your computer can also contract viruses from sinister email attachments, rogue web sites or infected software. And these disseminate to every other computer on your network.
All computer viruses cause direct or indirect economic damages. Based on this, there are two categories of viruses:
1) Those that only disseminate and don’t cause intentional damage
2) Those which are programmed to cause damage.
However, even by disseminating, they take up plenty of memory space, and time and resources that are spent on the clean-up job. Direct economic damages are caused when viruses alter the information during digital transmission. Considerable expenses are incurred by individuals, firms and authorities for developing and implementing the anti-virus tools to protect computer systems.
_
Drive-by attack
Drive-by download attacks are a common method of spreading malware. Hackers look for insecure websites and plant a malicious script into HTTP or PHP code on one of the pages. This script might install malware directly onto the computer of someone who visits the site, or it might re-direct the victim to a site controlled by the hackers. Drive-by downloads can happen when visiting a website or viewing an email message or a pop-up window. Unlike many other types of cyber security attacks, a drive-by doesn’t rely on a user to do anything to actively enable the attack — you don’t have to click a download button or open a malicious email attachment to become infected. A drive-by download can take advantage of an app, operating system or web browser that contains security flaws due to unsuccessful updates or lack of updates.
To protect yourself from drive-by attacks, you need to keep your browsers and operating systems up to date and avoid websites that might contain malicious code. Stick to the sites you normally use — although keep in mind that even these sites can be hacked. Don’t keep too many unnecessary programs and apps on your device. The more plug-ins you have, the more vulnerabilities there are that can be exploited by drive-by attacks.
_
Memory Scraping malware:
This has been around for a long time, but is more aggressively targeting data such as credit card records, passwords, PIN’s, keys, as of late. The reason they are successful is that they get around PCI/ GLBA/ HIPAA/ ETC security requirements that data must be encrypted while in transit and at rest. Data in transit is decrypted on the system and often stored in memory during the lifetime of a process, or at least during a decryption routine. Depending on how a process cleans up after itself, it may stay resident even after the fact. The data is encrypted on the hard disk, but again, the RAM likely maintains the cleartext version of the data. Browsers are notorious for leaving things sitting around in memory during web sessions. The RAM Scraping malware also targets encryption keys in memory to decrypt anything for session data to encrypted files. As emerging security threat, we are seeing RAM scraping more commonly now as attackers focus on client-side attacks, shifting away from server-side attacks. Browsers are often misconfigured, allowing malware to get onto a user’s system, stealing credit card data and passwords.
______
Password attack
Because passwords are the most commonly used mechanism to authenticate users to an information system, obtaining passwords is a common and effective attack approach. Access to a person’s password can be obtained by looking around the person’s desk, ‘‘sniffing’’ the connection to the network to acquire unencrypted passwords, using social engineering, gaining access to a password database or outright guessing. The last approach can be done in either a random or systematic manner:
Brute-force password guessing means using a random approach by trying different passwords and hoping that one work Some logic can be applied by trying passwords related to the person’s name, job title, hobbies or similar items.
In a dictionary attack, a dictionary of common passwords is used to attempt to gain access to a user’s computer and network. One approach is to copy an encrypted file that contains the passwords, apply the same encryption to a dictionary of commonly used passwords, and compare the results.
In order to protect yourself from dictionary or brute-force attacks, you need to implement an account lockout policy that will lock the account after a few invalid password attempts. You can follow these account lockout best practices in order to set it up correctly.
_______
Web jacking:
Web jacking derives its name from “hijacking”. Here, the hacker takes control of a web site fraudulently. He may change the content of the original site or even redirect the user to another fake similar looking page controlled by him. The owner of the web site has no more control and the attacker may use the web site for his own selfish interests. Cases have been reported where the attacker has asked for ransom, and even posted obscene material on the site.
The web jacking method attack may be used to create a clone of the web site, and present the victim with the new link saying that the site has moved. Unlike usual phishing methods, when you hover your cursor over the link provided, the URL presented will be the original one, and not the attacker’s site. But when you click on the new link, it opens and is quickly replaced with the malicious web server. The name on the address bar will be slightly different from the original website that can trick the user into thinking it’s a legitimate site. For example, “gmail” may direct you to “gmai1”. Notice the one in place of ‘L’. It can be easily overlooked.
Obviously not gmail.com, but still enough people click
Web jacking can also be done by sending a counterfeit message to the registrar controlling the domain name registration, under a false identity asking him to connect a domain name to the webjacker’s IP address, thus sending unsuspecting consumers who enter that particular domain name to a website controlled by the webjacker. The purpose of this attack is to try to harvest the credentials, usernames, passwords and account numbers of users by using a fake web page with a valid link which opens when the user is redirected to it after opening the legitimate site.
_______
Salami Attacks
Salami attacks are a series of minor data security attacks that together result in a larger attack. Example of this attack is a deduction of very small amount of money from bank account which is not noticeable. But when these deductions of very small amount from various numbers of accounts in the bank become a huge amount, it can damage the infrastructure of the bank.
______
Data Diddling Attacks
Data diddling is an illegal or unauthorized data alteration. For example, account executives can change the employee time sheet information of employees before entering to the HR payroll application.
______
Cryptojacking — Cryptojacking is a specialized attack that involves getting someone else’s computer to do the work of generating cryptocurrency for you (a process called mining in crypto lingo). The attackers will either install malware on the victim’s computer to perform the necessary calculations, or sometimes run the code in JavaScript that executes in the victim’s browser.
_______
Zero-day exploit:
A zero-day exploit hits after a network vulnerability is announced but before a patch or solution is implemented. Attackers target the disclosed vulnerability during this window of time. Zero-day vulnerability threat detection requires constant awareness.
_______
DNS Tunneling:
DNS tunneling utilizes the DNS protocol to communicate non-DNS traffic over port 53. It sends HTTP and other protocol traffic over DNS. There are various, legitimate reasons to utilize DNS tunneling. However, there are also malicious reasons to use DNS Tunneling VPN services. They can be used to disguise outbound traffic as DNS, concealing data that is typically shared through an internet connection. For malicious use, DNS requests are manipulated to exfiltrate data from a compromised system to the attacker’s infrastructure. It can also be used for command and control callbacks from the attacker’s infrastructure to a compromised system.
_______
Morphing
Morphing is editing the original picture by unauthorised user to use it for porn sites or blackmailing for financial/sexual gains.
The change smoothly from one image to another by small gradual steps using computer animation techniques. Morphing is a special effect in motion pictures and animations that changes one image or shape into another through technological means or as part of a fantasy or surreal sequence.
______
Software piracy:
Now-a-days software piracy is in great boom. Everyone use pirated software’s as they are made available easily and free of cost, whereas original software’s comes with price tag. Illegal copying of genuine software’s and selling it in cheap cost or for free is software piracy. Pirated software’s can be downloaded from internet, are available in CD/DVD also. As the movie is release, its copy made and sold without the consent of the movie maker. Retail revenue losses are increasing worldwide due to this crime.
______
Utilizing artificial intelligence for cybercrime:
Most of the biggest industries already use machine learning (ML) and artificial intelligence (AI) to automate their processes and improve overall performance. Cybersecurity and cybercrime are no exception. AI is often considered to be a dual-use technology – while more cybersecurity companies are implementing AI-driven algorithms to prevent threats, hackers are also taking the opportunity to become more effective. As cybersecurity strategies increase in innovation and effectiveness through the application of AI and ML, criminals will not only be able to adjust their own innovations with minimal effort, but also reduce the amount of time required to monitor and manage live exploits. The majority of AI qualities serve malicious purposes. AI systems are cheap, scalable, automated, anonymous and they provide physical and psychological distance for the attacker, diminishing the immediate morality around cybercrime.
- Artificial intelligence for cybersecurity evasion. Cybercriminals are using various evasion methods to avoid detection, and AI helps to optimize different elements of this process.
- Artificial intelligence in phishing. AI could help to create content that can pass through typical cybersecurity filters, such as email messages that are indistinguishable from those written by humans.
- Artificial intelligence in social engineering. While social engineering is one of the most popular hacking techniques, it takes a lot of time to implement properly. AI could help in not only collecting information, but also by writing emails or calling potential victims.
With new advances in AI-driven technology, utilizing AI in cyber-attacks will become an even more popular and dangerous trend.
_
Zero-day exploits have been expensive, primarily because of the time, effort, and expertise involved in uncovering them. This will change as AI and machine learning (ML) are combined with the technique known as “fuzzing” to better discover zero-day vulnerabilities and related exploits. Fuzzing has traditionally been a sophisticated technique confined to lab environments that is used by professional threat researchers with specialized skills to discover vulnerabilities in hardware and software interfaces and applications. As a result, using fuzzing to discover zero-day vulnerabilities has traditionally been beyond the scope of most cyber-criminals. As ML models are applied to this process, however, it will become more efficient – and more accessible as an attack vector. Cyber-criminals will begin to leverage machine learning to develop automated fuzzing programs to accelerate the process of discovering zero-day vulnerabilities, leading to an increase of these attacks. Once that is in place, we also expect zero-day mining-as-a-service to be made available by the cybercrime economy – a strategy that will completely change how organizations need to approach security.
_
AI poisoning:
The high-level process used by machine learning is called inference. Inference refers to the machine-learning engine making a decision based on the training that it has already received. The easiest way to perform a machine-learning poisoning attack would probably be to overwrite the existing training data with poisoned data, thereby causing a breakdown of the inference process. Cybercriminals will figure out ways to poison AI inference capabilities of endpoint security technologies as a way to bypass security controls. As we move AI processing closer to the edge for other applications, attackers will find ways to poison AI inference models to wreak havoc on models – potentially causing a “return to zero” for AI models over time.
______
Cybercrime Tactics:
Cybercriminals utilize both static and dynamic methods to commit their crimes as seen in the figure below:
______
______
Now I will discuss common types of cybercrimes in brief:
_
Cyberviolence:
Hundreds of millions of people currently use the Internet to enhance their lives and those of others. Yet a growing segment of the online population abuses the Internet for antisocial purposes, to stalk, harass and prey on other users, often with distressing effects. Internet-mediated aggression is a global phenomenon, and, disturbingly, it is on the rise, lending prima facie credence to the dystopian view that computer-mediated communication exacerbates bad behavior. To make matters worse, the tide of online violence is rising at a time when the Internet has moved from being a luxury to a necessity of daily life for educated people throughout the industrialized world. ‘Cyber violence’ thus stands to have negative impacts on a very large scale.
_
Cyberviolence is the use of computer systems to cause, facilitate, or threaten violence against individuals that results in, or is likely to result in, physical, sexual, psychological or economic harm or suffering and may include the exploitation of the individual’s circumstances, characteristics or vulnerabilities.
What distinguishes cyber violence from traditional off-line forms of violence is that in the former case, some significant portion of the behavior takes place online, although it might then carry over into offline contexts. Cyber violence thus may, but need not, have a physical component, and much of the harm caused by cyber violence—as indeed by offline violence—is psychological and/or emotional (which is not to say less real or destructive). Finally, cyber violence may be targeted at individuals or groups, the latter being more characteristic targets of cyber violence than of offline, physical violence, due to the ease with which a single perpetrator can gather information about and make contact with large numbers of people on the Internet. This is another aspect of online violence that can cause it to have widespread effects.
_
One obstacle to taking effective action against cyber violence is that it tends to be viewed as less serious, less “real” than violence in the off-line world. This is due in part to the relative novelty of the phenomenon (and of cyberspace as a whole); cyber violence does not conform to our familiar prototype of violence in a number of respects. As shown in table below, violence can be situated along a continuum from more to less prototypical.
Dimensions of violence:
| More prototypical violence <—————————————-> Less prototypical violence | |
|
Off-line |
Online |
| Physical | Virtual |
| Action | Symbols |
| Intentional harm | Harm not intended |
| Targeted against an individual | Untargeted, diffuse |
| Perpetrator is socially marginal | Perpetrator is an average person |
A prototype is a mental representation of a complex concept in terms of its default or “most typical” realization. When we think of violence, we typically think of off-line behavior before we think of the Internet; we think of physical aggression before we think of deception or mental cruelty; and we think of action before we think of symbolic behavior via words or images. Our prototype probably also involves an intentional perpetrator—non-intentional harm is usually characterized by other terms, such as ‘accident’—with a specific target or targets, although untargeted violence (known by terms such as ‘rampage’ and ‘mayhem’ when it occurs offline) is also possible. Last but not least, we expect perpetrators of violence to be socially marginal types—possibly with a history of violent or criminal behavior—rather than average, well-adjusted individuals (cf. ‘white collar crime’, which often goes undetected because of this assumption). Cyber violence is less prototypical than physical violence in where and how it takes place, in allowing perpetrators to deny their intent to harm more easily, and in enabling “normal” people to perpetrate widely-targeted harm, without requiring that the perpetrator be in an extreme emotional state (or risk his or her life) to carry it out. Because cyber violence differs from our prototypical associations of violence, it may be difficult at first to recognize it for what it is, and accordingly, harder to resist and punish it. Thus a necessary first step in fighting cyber violence is to identify and name its manifestations.
_
Types of cyberviolence:
In practice, acts of cyberviolence may involve different types of harassment, violation of privacy, sexual abuse and sexual exploitation and bias offences against social groups or communities. Cyberviolence may also involve direct threats or physical violence as well as different forms of cybercrime. There is not yet a stable lexicon or typology of offences considered to be cyberviolence, and many of the examples of types of cyberviolence are interconnected or overlapping or consist of a combination of acts. Not all of forms or instances of cyberviolence are equally severe and not all of them necessarily require a criminal law solution but may be addressed by a graded approach and a combination of preventive, educational, protective and other measures.
Various types of cyberviolence are depicted in the figure below:
_
_
Gender based cyber violence:
Many women and girls who are victims of cyber violence choose to minimize their online presence, which hurts digital inclusion, freedom of speech, and other human rights valued in democratic societies.
_
We live in the era of information and communication technologies (ICTs), which allow people around the world to connect, network, and exchange ideas in a way that was not possible before. This opens endless opportunities for communication, as well new dangers and challenges. Just like in the real world, the internet can be unsafe for women and young girls. Cyber violence against women and girls (CVAWG) is a fairly new phenomenon that is becoming more and more pervasive. It can take a variety of forms, including sending aggressive or threatening emails, text messages, or instant messages; sharing personal photos and videos without consent; internet trolling; hacking; cyberstalking; and others.
Violence is related to gender. Research has shown that men are disproportionately the perpetrators, and women disproportionately the victims, of violence in the physical world (Cyber-stalking.net, 2002). Cyber violence shows a similar pattern. Women were the victims in 84% of online harassment cases, and men the perpetrators in 64% of cases reported to the organization Working to Halt Online Abuse in 2000-2001 (WHO@, 2002). For many female Internet users, online harassment is a fact of life. One out of five adult female Internet users reported having been harassed online as of 1994 (Brail, 1994), and as many as one out of three female children reported having been harassed online in 2001 alone (Thomas, 2002). Among children, girls are targeted at almost twice the rate of boys (Finkelhor et al., 2000). A new report released in 2015 by the United Nations Broadband Commission reveals that almost three quarters of women online have been exposed to some form of cyber violence, and urges governments and industry to work harder and more effectively together to better protect the growing number of women and girls who are victims of online threats and harassment.
Males are also victims of violence (particularly of violence perpetrated by other males), and females also commit acts of violence, both online and offline. However, to ignore the larger gender pattern associated with violence is to miss a basic insight into the social reality of violence as a means of control and intimidation. That is, it tends to be perpetrated downward along a power hierarchy, thereby reinforcing societal gender asymmetries.
_
Cyber-harassment:
Cyber-harassment is perhaps the broadest form of cyberviolence and involves a persistent and repeated course of conduct targeted at a specific person that is designed to and that causes severe emotional distress and often the fear of physical harm. Cyber-harassment is often accomplished by a “storm of abuse”. Harassers terrorize victims by threatening violence. Offenders post defamatory falsehoods to cause the victim embarrassment or worse among friends, family or co-workers. Offenders impersonate victims in online ads, and suggest – falsely – that their victims are interested in sex with strangers. Sometimes, harassers manipulate search engines to ensure the prominence of the lies in searches of victims’ names. Harassers invade victims’ privacy by posting their sensitive information, such as nude images or national identity numbers. Or harassers may use technology to knock people offline. Cyber-harassment in popular discourse may be described as or related to “revenge porn” or “sextortion.”
Cyber-harassment is often targeted at women and girls and termed “cyber violence against women and girls” (CVAWG or Cyber VAWG) involving:
-Unwanted sexually explicit emails or other messages;
-Offensive advances in social media and other platforms;
-Threat of physical or sexual violence;
-Hate speech meaning language that denigrates, insults, threatens or targets an individual based on her identity (gender) and/or other traits (such as sexual orientation or disability).
Cyber-harassment thus involves a range of conduct, including for example “cyberbullying” and “revenge porn”.
_
Cyber Stalking:
Cyber stalking is a new form of internet crime of our society when a person is pursued or followed online. A cyber stalker doesn’t physically follow his victim; he does it virtually by following his online activity to harvest information about the stake and harass him or her and make threats using verbal intimidation. The behavior includes false accusation, threats and harassment of as victim through e-mail, chat message or web pages. It is a wilful conduct that actually causes a victim to feel terrorized, frightened, intimidated or molested. Normally majority of cyber stalkers are men and the majority of victims are women.
In order to prevent cyber stalking, the netizens should avoid disclosing any information pertaining to one while chatting. Girls should avoid sending any photographs online participatory to strangers and chat friends as there has been incidence of misuse of the photograph for morphing.
_
When children are involved in cyber stalking it is called cyber bullying.
Cyber bullying:
Cyber bullying occurs when children including teenagers are tormented threatened, harassed, humiliated, embraced or otherwise targeted by other children using the internet, interactive and digital technologies or mobile phones. It has to have a minor on both sides or at least should have been instigated by a minor against another minor. The methods used are limited only by child’s imagination and access to technology. Cyber bullying is usually not a onetime communication unless it voices death threats or credible threats of serious bodily harm. Cyber bullying may arise to the level of a cyber harassment charge, or if the child is young enough it may result in the charge of juvenile delinquency. In order to safeguard children from cyber bullying parents should be more involved in their children’s online activities, the parents should also be aware of major changes in a child’s behavior.
_
Revenge porn:
“Revenge porn” is a term in popular discourse that centres on the sexually explicit portrayal of one or more persons that is distributed without the subject’s consent. The phenomenon predominantly involves a partner in an intimate relationship disseminating the material in order to humiliate or intimidate the victim. The phenomenon, emerged as early as the 1980s (being a regular feature in Hustler magazine) and was linked to “amateur pornography”, before transforming into sexually explicit videos disseminated over the Internet (such as the amateur porn aggregator Xtube in 2008). “Revenge porn” is a crime that has been recognised by several regulations at local and national levels and has involved civil suits and criminal offences in various countries, although not always in the same manner. One legal formulation criminalises the unlawful (meaning non-consensual) disclosure, distribution, dissemination or promotion of intimate images or videos.
_
Sextortion
Sextortion is a term in popular discourse that encompasses activities that (a) involve manipulation or coercion to perform sexual activities for the benefit of the aggressor and/or to create sexually explicit images of the victim and (b) the traditional crime of extortion. Although the crime may include the threat to disseminate such images or videos once they have been created, it is just as common that the coercion may involve the threat to hurt the victim’s family or friends if sexual activity is not undertaken and recorded or transmitted to the aggressor. The aggressor’s motivation may also be revenge, humiliation or monetary gain. It is often carried out remotely over computer networks and may involve recording images or live streaming video (i.e., using a Web cam). Perpetrators are often current, former or would-be romantic or sexual partners. There are cases of sextortion, however, where the perpetrator is a stranger and a serial aggressor with victims in dozens of countries. Offenders often use a variety of computer skills including hacking, creation of multiple false identities on social media sites, interception of private communications and so forth. In this regard, sextortion has been a component of the more severe forms of cyberbullying and has also been an element in some forms of cyberstalking and cyber harassment. “Sextortion” often entails the non-consensual distribution of intimate images, even if that distribution is only between the offender and the victim, rather than broad dissemination.
_
Child pornography:
Child pornography is, a) producing child pornography; b) offering or making available child pornography; c) distributing or transmitting child pornography; d) procuring child pornography for oneself or for another person; e) possessing child pornography; f) knowingly obtaining access, through information and communication technologies, to child pornography.
“Child pornography” means any material that visually depicts a child engaged in real or simulated sexually explicit conduct or any depiction of a child’s sexual organs for primarily sexual purposes.
The Internet has become a prime channel for the distribution of child pornography. In the 1970s and 1980s, offenders engaging in the exchange of child pornography faced serious threats. At that time, the commercial child pornography market focused mainly on Europe and the US and the material was locally produced, expensive and difficult to obtain. Approaches to buy or sell child pornography entailed a number of risks that no longer – or at least not to a degree – exist today. In the past, producers did not have the capability to develop photography and films. They were dependent on services offered by businesses, which increased the chances of law-enforcement agents identifying child pornography through reports from businesses handling the development. The availability of video cameras changed this situation for the first time. But the risks were not only related to production. Getting access to child pornography was similarly fraught with risks for the offender. Orders were placed by responding to advertisements in newspapers. Means of communication between seller and collector, and hence the market itself, were limited. Until the mid-1990s, child pornography was primarily transported through postal services, and successful investigations led to the detection of a significant number of offenders. In the view of experts, law enforcement was at that time able to meet the challenges.
The situation changes dramatically with the availability of Internet-based data-exchange applications. While in the past, law enforcement was confronted with analogue material, today the vast majority of discovered material is digital. Since the mid-1990s, offenders have increasingly used network services for the distribution of such material. The resulting problems in terms of detecting and investigating child-pornography cases have been acknowledged. The Internet is today the main channel for trading regular pornography as well as child pornography.
Several reasons for the shift from analogue to digital distribution can be identified. The Internet gives less technically skilled users the impression they can act invisibly from others. If the offender does not employ anonymous communication technology, this impression is erroneous. But the fact that using sophisticated means of anonymous communication can hinder the identification of the offender is a matter of concern in respect of the exchange of child pornography online. In addition, this development has been supported by the decreasing price of technical devices and services used for the production and trading of child pornography, such as recording equipment and hosting services. Since websites and Internet services are open to around four billion Internet users, the number of potential customers has also expanded. There are concerns that the fact that access is easier attracts people who would not have taken the risk of being caught trying to obtain child pornography outside the Internet. With the shift from analogue to digital media, an increasing number of child-pornography images discovered through investigations were reported. Another aspect that probably supported this development is the fact that digital information can in general be duplicated without a loss of quality. While in the past consumers of child pornography wishing to duplicate and trade the material were hindered by the loss in quality from reproduction, today a downloaded file can become the source for further duplications. One of the consequences of this development is that, even when the offender who produced the material in the first place is arrested and his files are confiscated, it becomes difficult to “remove” files once they have been traded over the Internet.
In contrast to differing views on adult pornography, child pornography is broadly condemned and offences related to child pornography are widely recognized as criminal acts. International organizations are engaged in the fight against online child pornography, with several international legal initiatives, including: the 1989 United Nations Convention on the Rights of the Child; the 2003 European Union Council Framework Decision on combating the sexual exploitation of children and child pornography; and the 2007 Council of Europe Convention on the Protection of Children against Sexual Exploitation and Sexual Abuse, among others.
Sadly, these initiatives seeking to control the network distribution of pornography have proved little deterrent to perpetrators, who use the Internet to communicate and exchange child pornography. An increase in bandwidth has supported the exchange of movies and picture archives.
Research into the behaviour of child pornography offenders shows that 15 per cent of arrested people with Internet-related child pornography in their possession had more than 1000 pictures on their computer; 80 per cent had pictures of children aged between 6 and 12 years on their computer; 19 per cent had pictures of children younger than the age of 3; and 21 per cent had pictures depicting violence.
The sale of child pornography is highly profitable, with collectors willing to pay great amounts for movies and pictures depicting children in a sexual context. Search engines find such material quickly. Most material is exchanged in password-protected closed forums, which regular users and law enforcement agencies can rarely access. Undercover operations are thus vital in the fight against child pornography.
Two key factors in the use of ICTs for the exchange of child pornography act as obstacles to the investigation of these crimes:
- The use of virtual currencies and anonymous payment
Cash payment enables buyers of certain goods to hide their identity, so cash is dominant in many criminal businesses. The demand for anonymous payments has led to the development of virtual payment systems and virtual currencies enabling anonymous payment. Virtual currencies may not require identification and validation, preventing law-enforcement agencies from tracing money flows back to offenders.
- The use of encryption technology
Perpetrators are increasingly encrypting their messages. Law-enforcement agencies note that offenders are using encryption technology to protect information stored on their hard disks, seriously hindering criminal investigations.
_______
Swatting:
“Swatting” is an example of how computer systems can be misused for many types of conduct with violent impact on victims. Swatting is a criminal harassment tactic of deceiving an emergency service (via such means as hoaxing an emergency services dispatcher) into sending a police and emergency service response team to another person’s address. It is the use of telephones and often computer systems to deceive an emergency service in order to send law enforcement to a specific location based on a false report. The name comes from the acronym “S.W.A.T.” (Special Weapons and Tactics) which are law enforcement units that have specialized training and may employ military-style equipment. False reports include reporting homicides in someone else’s home, bomb threats, and kidnapping. “Swatting” may fall under a variety of criminal statutes such as uttering death threats, conspiracy to commit device fraud, obstruction of justice, and public mischief. These are not merely prank phone calls: perpetrators typically use caller ID spoofing and social engineering and some demonstrate the sophisticated use of computer systems and software to make it appear calls are coming from different locations (sometimes in different countries from the offender’s point of origin). Swatting may be terrifying and dangerous to the victims, who have been killed by responding law enforcement or who have suffered physical injuries such as bullet wounds and heart attacks.
______
Bitcoin abuse:
The expansion of cybercrime has been enabled by the easy availability of tools like Bitcoin and Tor, which have allowed cybercriminals to conceal their identities while paying for services through a digital medium that significantly complicates law enforcement tracking efforts. Bitcoin has long been the favored currency for darknet marketplaces, with cybercriminals taking advantage of its pseudonymous nature and decentralized organization to conduct illicit transactions, demand payments from victims, and launder the proceeds from their crimes. Cybercriminals benefit from the fact that no personally identifying information is linked to the use and exchange of Bitcoin, allowing criminals to operate with near impunity despite the fact that all Bitcoin transactions are publicly recorded.
Bitcoin users can only be identified if their accounts become linked to their real identity, something most criminals are careful to avoid. However, linking an account with identifying information is a necessary component of converting Bitcoin into real-world currencies through banks or exchanges, creating a vulnerability for criminals. To address this, a number of services have been established in recent years that allow cybercriminals to launder their Bitcoins and withdraw them through unregulated exchanges to avoid being caught. Bitcoin laundering can occur through the process of “tumbling,” or “mixing,” where multiple users pool both clean and dirty Bitcoins together, letting a program execute a series of exchanges between the members that eventually gives the users back their money in randomized coins. Cybercriminals can also utilize unregulated cryptocurrency exchanges that obscure customer information, like in the case of the recently shut down BTC-e exchange, thought to be responsible for 95% of all ransomware cash outs.
Despite these services, there are still instances in which cybercriminal using Bitcoins can be identified, either through IP address mapping or accidental leaks by web trackers. As a result, a number of attempts have been made at developing a truly anonymous cryptocurrency that could provide greater security to cybercriminals. The three most popular today are Dash, Monero, and Zcash. Dash uses a technique known as “coinjoin” to integrate mixing into the operation of the currency and to provide protection for senders and recipients. Monero is even more secure, using “stealth addresses” that hide the amount of every purchase and mix each transaction with more than a hundred others to anonymize the senders. Zcash, the most advanced of the three, using a process called zero-knowledge proofs to allow two users to exchange information without ever revealing identities, completely shielding details of the transaction from all involved. Monero has been the most widely implemented of the three, with about 2% of all transactions on former top market AlphaBay using the coin in late 2016. According to Europol, a Monero based ransomware kit has already appeared in the wild, raising the possibility that cybercriminals may soon begin to use these anonymous cryptocurrencies for more than just exchanging services in darknet markets.
______
Intellectual Property (IP) Theft:
Intellectual property theft involves robbing people or companies of their ideas, inventions, and creative expressions—known as “intellectual property”—which can include everything from trade secrets and proprietary products to movies, music, and software. It is a growing threat—especially with the rise of digital technologies and Internet file sharing networks. The most important area for the cost of cybercrime is in the theft of intellectual property and business confidential information. Internet connectivity has opened a vast terrain for cybercrime, and IP theft goes well beyond traditional areas of interest to governments, such as military technologies. One way to measure the cost of intellectual property theft is to look for competing products that take market share from the rightful owners. If hackers steal intellectual property, such as product designs, from a small or medium size enterprise, it can be a fatal experience. For big companies, it can be an unexpected source of revenue lost as competing products enter the market. The theft of intellectual property accounts for at least a quarter of the cost of cybercrime and, when it involves military technology, creates risks to national security as well. These losses can often be invisible to the victim. They still have access to the IP that has been copied by the criminals and may attribute a decline in revenue to growing competition rather than theft.
China is the focus of IP theft concerns. There is a general consensus that Chinese hackers, often associated with the People’s Liberation Army (PLA,) led until recently in the theft of intellectual property. Before 2015, China was responsible for half of the cyberespionage against the US involving the theft of IP and commercially valuable information, according to US government sources.
_______
Identity Theft:
Surveys routinely show identity theft as one of the top concerns of internet users, not surprisingly, given the size of breaches that routinely make the news. But Bureau of Justice Statistics (BJS) reports in 2012 and 2014 suggest that the actual losses from identity theft remain small. The BJS report found 16.6 million people had experienced some form of identity theft in 2012, resulting losses of about $25 billion. That averages out to $1500 per incident, a painful but not crippling amount for most people. Only 14% of victims suffered out-of-pocket losses, and of those victims, about half lost $99 or less.
So why is identity theft such a concern? DOJ found that it was the most expensive kind of property crime the in US, costing $10 billion more than the losses attributed to all other property crime. Second, two-thirds of victims had no idea how or when they had been hacked. Identity theft creates a sense of helpless. An invisible crime that affects millions is something to worry about. Not all identity theft is cyber-related, but the real victims, however, are the banks and credit card companies that bear the bulk of the losses.
The breach of credit reporting agency Equifax exposed the personal data of 143 million US consumers in September 2017. The Equifax breach cost the company nearly $90 million in the first four months after discovery. Equifax incurred a one-time charge related to the cybersecurity incident of $87.5 million, and its net income fell 27% in the third quarter.
Identity theft and credit card fraud:
Identity theft occurs when someone steals your identity and pretends to be you to access resources such as credit cards, bank accounts and other benefits in your name.
“Credit card fraud “is a wide ranging term for crimes involving identity theft where the criminal uses your credit card to fund his transactions.
_______
Racism, hate speech, glorification of violence:
Radical groups use mass communication systems such as the Internet to spread propaganda. The number of websites offering racist content and hate speech has risen in recent years – a study in 2005 suggested a rise of 25 per cent in the number of webpages promoting racial hatred, violence and xenophobia between 2004 and 2005. In 2006, over 6 000 such websites existed on the Internet.
Internet distribution offers several advantages for offenders, including lower distribution costs, nonspecialist equipment and a global audience. Examples of incitement-to-hatred websites include websites presenting instructions on how to build bombs. Besides propaganda, the Internet is used to sell certain goods, e.g. Nazi-related items such as flags with symbols, uniforms and books, readily available on auction platforms and specialized web-shops. The Internet is also used to send e-mails and newsletters and distribute video clips and television shows through popular archives such as YouTube.
Not all countries criminalize these offences. In some countries, such content may be protected by principles of freedom of speech. Opinions differ as to how far the principle of freedom of expression applies with regard to certain topics, often hindering international investigations. One example of conflict of laws is the case involving the service provider Yahoo! in 2001, when a French court ordered Yahoo! (based in the US) to block the access of French users to Nazi-related material. Based on the First Amendment of the United States Constitution, the sale of such material is legal under United States law. Following the First Amendment, a US court decided that the French order was unenforceable against Yahoo! in the United States.
The disparities between countries on these issues were evident during the drafting of the Council of Europe Convention on Cybercrime. The Convention on Cybercrime seeks to harmonize cybercrime-related laws to ensure that international investigations are not hindered by conflicts of laws. Not all parties engaged in negotiations could agree on a common position on the criminalization of the dissemination of xenophobic material, so this entire topic was excluded from the Convention on Cybercrime and instead addressed in a separate First Protocol. Otherwise, some countries (including the United States) might have been unable to sign the Convention on Cybercrime.
_______
Religious offences:
A growing number of websites present material that is in some countries covered by provisions related to religious offences, e.g. anti-religious written statements. Although some material documents objective facts and trends (e.g. decreasing church attendance in Europe), this information may be considered illegal in some jurisdictions. Other examples include the defamation of religions or the publication of cartoons.
The Internet offers advantages for those who wish to debate or deal critically with a subject – people can leave comments, post material or write articles without having to disclose their identity. Many discussion groups are based on the principle of freedom of speech. Freedom of speech is a key driver behind the Internet’s success, with portals that are used specifically for user-generated content. Whilst it is vital to protect this principle, even in the most liberal countries the application of principles of freedom of speech is governed by conditions and laws.
The differing legal standards on illegal content reflect the challenges of regulating content. Even where the publication of content is covered by provisions relating to freedom of speech in the country where the content is available, this material can be accessed from countries with stricter regulations. The “cartoon dispute” in 2005 demonstrated the potential for conflict. The publication of twelve editorial cartoons in the Danish newspaper Jyllands-Posten led to widespread protests across the Muslim world.
As with illegal content, the availability of certain information or material is a criminal offence in some countries. The protection of different religions and religious symbols differs from country to country. Some countries criminalize the use of derogatory remarks in respect of the Holy Prophet or the defiling of copies of the Holy Quran, while other countries may adopt a more liberal approach and may not criminalize such acts.
_____
Internet homicide:
Internet homicide refers to killing in which victim and perpetrator met online, in some cases having known each other previously only through the Internet. Also Internet killer is an appellation found in media reports for a person who broadcasts the crime of murder online or who murders a victim met through the Internet. The first known murder of a victim met online was in 1996. Depending on the venue used, other terms used in the media are Internet chat room killer, Craigslist killer, Facebook serial killer. Internet homicide can also be part of an Internet suicide pact or consensual homicide. Some commentators believe that reports on these homicides have overemphasized their connection to the Internet.
_____
Selling Fakes Online:
The Internet has opened up a wealth of possibilities for new businesses. Its speed, connectivity, and anonymity make it possible to sell nearly anything to anyone at any time. Unfortunately, that can include the sale of fake products as well — everything from counterfeit purses or shoes, to knockoff clothes, and even fake medications. Counterfeiters sometimes steal the designs or trademarks of others in order to dupe customers into buying fake products. Although selling fakes online can be big business, it’s a common online scam. Depending on the kind of fake products a scammer may try to sell, different sets of laws, governing agencies, and penalties may apply.
_____
Drug trafficking:
Darknet markets are used to buy and sell recreational drugs online. Some drug traffickers use encrypted messaging tools to communicate with drug mules. The dark web site Silk Road was a major online marketplace for drugs before it was shut down by law enforcement (then reopened under new management, and then shut down by law enforcement again). After Silk Road 2.0 went down, Silk Road 3 Reloaded emerged. However, it was just an older marketplace named Diabolus Market, that used the name for more exposure from the brand’s previous success.
_____
Spam and steganography:
The email, has spawned one of the greatest nuisances of our time, “spam”. Conservative estimates are that 100 million people receive at least one spam email. It is also estimated that somewhere between 50 percent and 70 percent of all email messages are spam. Some argue that spam e-mail are “unsolicited advertisements for products or services”. While this may sound like a nice catchy definition of spam, it is also somewhat misleading. Spam can be a lot more than merely an advertisement for products and services. It’s eminently possible to receive spam mail that actually doesn’t advertise either a product or service. For this reason, an alternative is needed and none better can be found than “An unsolicited e-mail from which the sender is attempting to gain an advantage (commercial or otherwise) and which the recipient neither asked for nor wanted”. Spam is a nuisance against all users of the Internet since it wastes both the storage and network capacities of ISPs, as well as often simply being offensive. Yet, despite various attempts to legislate it out of existence, it remains unclear how spam can be eliminated without violating the freedom of speech in a liberal democratic polity. Unlike junk mail, which has a postage cost associated with it, spam is nearly free for perpetrators—it typically costs the same to send 10 messages as it does to send 10 million. Spam becomes cybercrime when it is used to spread computer viruses, trojan horses or other malicious software. The objective may be identity theft, or worse (e.g., advance fee fraud). Tricking users into clicking on malicious links is the most common method for cyber-criminals to spread malware. Email spam was the most common method for cybercriminals to spread malware in 2018. Roughly 69 percent of spam emails attempt to trick users into visiting a malicious URL. Malicious attachments were used in the remaining 31 percent of spam.
One of the most significant problems in shutting down spammers involves their use of other individuals’ personal computers. Typically, numerous machines connected to the Internet are first infected with a virus or Trojan horse that gives the spammer secret control. Such machines are known as zombie computers, and networks of them, often involving thousands of infected computers, can be activated to flood the Internet with spam or to institute DoS attacks. While the former may be almost benign, including solicitations to purchase legitimate goods, DoS attacks have been deployed in efforts to blackmail Web sites by threatening to shut them down. Cyber experts estimate that the United States accounts for about one-fourth of the 4–8 million zombie computers in the world and is the origin of nearly one-third of all spam.
E-mail also serves as an instrument for both traditional criminals and terrorists. While libertarians laud the use of cryptography to ensure privacy in communications, criminals and terrorists may also use cryptographic means to conceal their plans. Law-enforcement officials report that some terrorist groups embed instructions and information in images via a process known as steganography, a sophisticated method of hiding information in plain sight. Even recognizing that something is concealed in this fashion often requires considerable amounts of computing power; actually decoding the information is nearly impossible if one does not have the key to separate the hidden data.
_____
Cyberextortion:
Cyberextortion occurs when a website, e-mail server, or computer system is subjected to or threatened with repeated denial of service or other attacks by malicious hackers. These hackers demand money in return for promising to stop the attacks and to offer “protection”. According to the Federal Bureau of Investigation, cybercrime extortionists are increasingly attacking corporate websites and networks, crippling their ability to operate and demanding payments to restore their service. More than 20 cases are reported each month to the FBI and many go unreported in order to keep the victim’s name out of the public domain. Perpetrators typically use a distributed denial-of-service attack. However, other cyberextortion techniques exist such as doxing extortion and bug poaching. An example of cyberextortion was the attack on Sony Pictures of 2014.
_______
Cyber-laundering:
The Internet is transforming money-laundering. For larger amounts, traditional money-laundering techniques still offer a number of advantages, but the Internet offers several advantages. Online financial services offer the option of enacting multiple, worldwide financial transactions very quickly. The Internet has helped overcome the dependence on physical monetary transactions. Wire transfers replaced the transport of hard cash as the original first step in suppressing physical dependence on money, but stricter regulations to detect suspicious wire transfers have forced offenders to develop new techniques.
_______
Cyber-terrorism:
Cyber terrorism is the convergence of cyberspace and terrorism. It refers to unlawful attacks and threads of attacks against computers, networks and the information stored therein that are carried out to coerce a country’s government or citizens in furtherance of political or social objectives. There is not a consensus on one definition of cyber-terrorism but they all focus on that it invokes fear. A 2008 NATO document defines cyber-terrorism as: “a cyber-attack using or exploiting computer or communication networks to cause sufficient destruction to generate fear or intimidate a society into an ideological goal.” Another definition from the National Information Protection Center (NIPC) that exists within the Department of Homeland Security (DHS) is: “a criminal act perpetrated through computers resulting in violence, death and/or destruction, and creating terror for the purpose of coercing a government to change its policies.” The similarities between these definitions is that cyber-terrorism’s motive is to invoke fear to intimidate a society into changing for the purpose of an ideological goal. The difference between cyber-crime and cyber-terrorism is distinct in the “motive” of the cyber-attack by the attacker. Cyber-crime is different in that its motive is for personal gain.
The nature of cyberterrorism covers conduct involving computer or Internet technology that:
-is motivated by a political, religious or ideological cause
-is intended to intimidate a government or a section of the public to varying degrees
-seriously interferes with infrastructure
_
Figure below shows distribution of cyber-attacks across cultural, social, economic and political motivations: 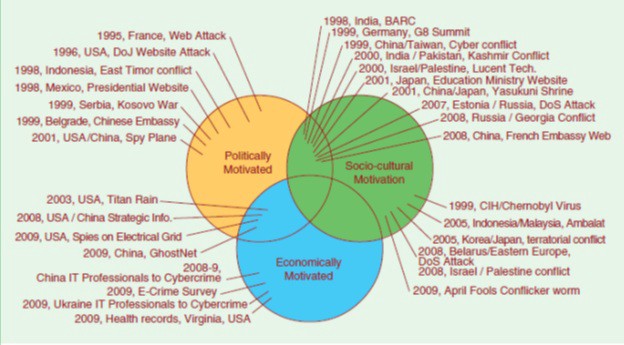
_
Terrorist use of the Internet:
It is known that terrorists use ICTs and the Internet for:
- propaganda
- information gathering
- preparation of real-world attacks
- publication of training material
- communication
- terrorist financing
- attacks against critical infrastructures.
The cyber terrorism attacks and threats includes interfering and disrupting information and transportation systems, emergency services and government services, communication networks, infrastructure systems, banking and fiancé system.
_
Figure below shows factors involved in cyberterrorism:
Cyberterrorism involves the idea that terrorists could cause massive loss of life, worldwide economic chaos and environmental damage by hacking into critical infrastructure systems.
_
Examples of cyberterrorism include:
- Global terror networks disrupting major websites to create public nuisances/inconveniences or to stop traffic to websites that publish content the hackers disagree with.
- International cyberterrorists accessing and disabling or modifying the signals that control military technology.
- Cyberterrorists targeting critical infrastructure systems, for example, to disable a water treatment plant, cause a regional power outage, or disrupt a pipeline, oil refinery or fracking operation. This type of cyberattack could disrupt major cities, cause a public health crisis, endanger the public safety of millions of people as well as cause massive panic and fatalities.
_
Methods of cyberterrorism:
Cyberterrorism operations can use many different attack methods, including:
- An advanced persistent threat (APT) is a prolonged and targeted cyberattack in which an intruder gains access to a network and remains undetected for long period of time. The intention of an APT attack is usually to monitor network activity and steal data rather than to cause damage to the network or organization. To gain access, APT groups often use advanced attack methods, including advanced exploits of zero-day vulnerabilities, as well as highly-targeted spear phishing and other social engineering techniques. To maintain access to the targeted network without being discovered, threat actors use advanced methods, including continuously rewriting malicious code to avoid detection and other sophisticated evasion techniques. Some APTs are so complex that they require full-time administrators to maintain the compromised systems and software in the targeted network. APT attacks target organizations in sectors with high-value information, such as national defense, manufacturing and the financial industry.
- Viruses, computer worms and malware targeting control systems can affect water supplies, transportation systems, power grids, critical infrastructure and military systems and may be used to further cyberterrorist goals.
- DoS attacks, cybersecurity events that occur when attackers take action to prevent legitimate users from accessing targeted computer systems, devices or other network resources.
- Hacking and theft of critical data from institutions, governments and businesses.
- Ransomware that holds computer systems hostage until the victims pay ransom.
- Phishing attacks, attempts by cybercriminals to collect information from victims through email, which they can then use to access systems or steal the victims’ identities.
Cyberterrorist attackers can use virtually any attack method used by cybercriminals to further their political or social goals.
_
Professional hackers to cyberterrorists:
Professional hackers, either working on their own or employed by government agencies or the military, can find computer systems with vulnerabilities lacking the appropriate security software. Once those vulnerabilities are found, they can infect systems with malicious code and then remotely control the system or computer by sending commands to view content or to disrupt other computers. There needs to be a pre-existing system flaw within the computer such as no antivirus protection or faulty system configuration for the viral code to work.
Many professional hackers will promote themselves to cyberterrorists, where a new set of rules govern their actions. Cyberterrorists have premeditated plans and their attacks are not born of rage. They need to develop their plans step-by-step and acquire the appropriate software to carry out an attack. They usually have political agendas, targeting political structures. Cyberterrorists are hackers with a political motivation, their attacks can impact political structure through this corruption and destruction. They also target civilians, civilian interests and civilian installations. Cyberterrorists attack persons or property and cause enough harm to generate fear.
______
Cyberwarfare
Cyberwarfare is the use of technology to attack a nation, causing comparable harm to actual warfare. Cyberwarfare does not imply scale, protraction or violence which are typically associated with the term ‘war’. Cyberwarfare may not meet the typical definition of the term war, however, many states including the United States, United Kingdom, Russia, India, China, Israel, Iran, and North Korea have active cyber operations for offensive and defensive operations. As states explore the use of cyber operations and combine capabilities the likelihood of physical confrontation and violence playing out as a result of, or part of, a cyber operation is increased.
Cyberwarfare is an extension of policy by actions taken in cyberspace by state actors (or by non-state actors with significant state direction or support) that constitute a serious threat to another state’s security, or an action of the same nature taken in response to a serious threat to a state’s security (actual or perceived). The former US National Coordinator for Security, Infrastructure Protection and Counter-terrorism, Richard A. Clarke, defines cyberwarfare as “actions by a nation-state to penetrate another nation’s computers or networks for the purposes of causing damage or disruption.”
There are a number of reasons nations undertake offensive cyber operations. Sandro Gaycken, a cyber security expert and adviser to NATO, advocates that states take cyber warfare seriously as they are viewed as an attractive activity by many nations, in times of war and peace. Offensive cyber operations offer a large variety of cheap and risk-free options to weaken other countries and strengthen their own positions. Considered from a long-term, geostrategic perspective, cyber offensive operations can cripple whole economies, change political views, agitate conflicts within or among states, reduce their military efficiency and equalize the capacities of high-tech nations to that of low-tech nations, and use access to critical infrastructures to blackmail them.
_____
Figure below summarizes various cybercrimes and their techniques:
______
______
Cybercrime statistics:
A new study by Norton reveals the staggering prevalence of cybercrime. About 65 per cent of Internet users globally, and 73 per cent of US Web surfers have fallen victim to cybercrimes, including computer viruses, online credit card fraud and identity theft. As the most victimised nations, America ranks third, after China (83 per cent) & Brazil and India (76 per cent).
Another study found when surveying 6.2 billion files, including ones that contained health records and financial information that about 1 in 5 were completely open for global access. What makes it worse is that companies are also perpetuating this. About 2 in 5 companies will have over 1000 files open for anyone to see, including files with sensitive information.
_
There are several difficulties associated with determining the global threat of cybercrime on the basis of crime statistics.
First of all, crime statistics are generally created at the national level and do not reflect the international scope of the issue. Even though it would theoretically be possible to combine the available data, such an approach would not yield reliable information because of variations in legislation and recording practices. Combining and comparing national crime statistics requires a certain degree of compatibility that is missing when it comes to cybercrime. Even if cybercrime data are recorded, they are not necessarily listed as a separate figure. Furthermore, statistics only list crimes that are detected and reported. Especially with regard to cybercrime, there are concerns that the number of unreported cases is significant. Businesses may fear that negative publicity could damage their reputation. If a company announces that hackers have accessed their server, customers may lose faith. The full costs and consequences could be greater than the losses caused by the hacking attack. On the other hand, if offenders are not reported and prosecuted, they may go on to re-offend. Victims may not believe that law-enforcement agencies will be able to identify offenders. Comparing the large number of cybercrimes with the few successful investigations, they may see little point in reporting offences. As automation of attacks enables cybercriminals to pursue a strategy of reaping large profits from many attacks targeting small amounts (e.g. as is the case with advance fee fraud), the possible impact of unreported crimes could be significant. For only small amounts, victims may prefer not to go through time-consuming reporting procedures. Reported cases are often the ones that involve very large amounts.
In summary, statistical information is useful to draw attention to the continuing and growing importance of the issue, and it is necessary to point out that one of the major challenges related to cybercrime is the lack of reliable information on the extent of the problem, as well as on arrests, prosecutions and convictions. As already stated, crime statistics often do not list offences separately, and available statistics on the impact of cybercrime are in general unable to provide reliable information about the scale or extent of offences at a level sufficient for policy-makers. Without such data, it is difficult to quantify the impact of cybercrime on society and to develop strategies to address the issue. Nevertheless, the statistics can serve as a basis for determining trends, which can be found by comparing results over several years, and serve as guidance with regard to the process of reporting cybercrime.
_
Microsoft Research says cybercrime Surveys are useless:
A study by Microsoft Research finds that many of these surveys are as rife with catastrophic statistical errors as to make their conclusions almost useless. Cybercrime surveys are “so compromised and biased that no faith whatever can be placed in their findings,” said the paper’s authors, Microsoft researchers Cormac Herley and Dinei Florêncio.
A number of issues that negatively impact cybercrime surveys, among them: finding survey populations that represent the general public, the relative rarity of cybercrime incidents, especially when balanced of against the huge volume of legitimate online activity, and the effect of so-called “outlier” incidents that can create catastrophic statistical errors, Microsoft said.
_
Prevalence and perceptions of cybercrime:
The exact prevalence of cybercrime is unknown. Convictions for cybercrimes are still relatively rare (compared to other crimes), although that does not mean cybercrime is not prevalent. There is supposed to be a high ‘dark number’ of undetected, unreported, uninvestigated, or unresolved cybercrimes, due to the invisibility and complexity of digital traces and a general reluctance of business victims to report for fear of reputation damage. Crime victim surveys have only recently begun to include questions on Internet crime, often limited to fraud and illegal or offensive content; they tend to exclude malware and other ‘core’ cybercrimes since these are difficult to recognise by average computer users. Many statistics are published of computer-security incidents, notably of viruses and other malware and phishing attempts. However, these often come from security companies with an interest of selling, e.g., anti-virus software, and should therefore be taken with a (large) pinch of salt. Another complicating factor is the ‘mythology’ of cybercrime fed by popular images in movies and novels, with a stereotypical hacker as the archetypical cybercriminal (Wall, 2008a; Wall, 2008b; cf. Jewkes & Yar, 2010, pp. 104-166). Such popular perceptions can be far removed from reality. Nevertheless, the overall trend in the literature is to suppose that (many) more cybercrimes must occur than is empirically established, even if research efforts fail to shed light on the ‘dark number’. David Wall (2007) warns against the conundrum of our beliefs about cybercrime’s prevalence: ‘we are shocked by cybercrime, but also expect to be shocked by it because we expect it to be there, but – confusingly – we appear to be shocked if we are not shocked (if we don’t find it!).’
_
Cyber Attack Surface:
The World Wide Web was invented in 1989. The first-ever website went live in 1991. Today there are more than 1.7 billion websites. There were 3.8 billion Internet users in 2017 (51% of the world’s population of 7 billion), up from 2 billion in 2015. Cybersecurity Ventures predicts that there will be 6 billion Internet users by 2022 (75% of the projected world population of 8 billion) — and more than 7.5 billion Internet users by 2030 (90% of the projected world population of 8.5 billion, 6 years of age and older). Like street crime, which historically grew in relation to population growth, we are witnessing a similar evolution of cybercrime. It’s not just about more sophisticated weaponry, it’s as much about the growing number of human and digital targets.
Microsoft helps frame digital growth with its estimate that data volumes online will be 50 times greater in 2020 than they were in 2016. ‘The Big Data Bang’ is an IoT world that will explode from 2 billion objects (smart devices which communicate wirelessly) in 2006 to a projected 200 billion by 2020, according to Intel. Gartner forecasts that more than half a billion wearable devices will be sold worldwide in 2021, up from roughly 310 million in 2017. Wearables includes smartwatches, head-mounted displays, body-worn cameras, Bluetooth headsets, and fitness monitors.
Despite promises from biometrics developers of a future with no more passwords — which may in fact come to pass at one point in the far out future — a 2017 report finds that the world will need to cyber protect 300 billion passwords globally by 2020.
There are 111 billion lines of new software code being produced each year — which introduces a massive number of vulnerabilities that can be exploited.
The world’s digital content is expected to grow from 4 billion terabytes (4 zetabytes) in 2015 to 96 zetabytes by 2020.
The far corners of the Deep Web — known as the Dark Web — is intentionally hidden and used to conceal and promote heinous criminal activities. Some estimates put the size of the Deep Web (which is not indexed or accessible by search engines) at as much as 5,000 times larger than the surface web, and growing at a rate that defies quantification, according to one report.
_
Police recorded cybercrime rate:
Police-recorded crime statistics do not represent a sound basis for cross-national comparisons. About 75% of the countries view their systems of police statistics as insufficient for recording cybercrime. Police-recorded cybercrime rates are associated with levels of country development and specialized police capacity, more than underlying crime rates.
Figure above shows most common cybercrime acts encountered by national police (UNODC).
There is evidence suggesting that cybercrime incidents are very rarely reported. This is especially the case when the criminal activity is directed towards companies: any report might be perceived as a security problem and lead to competition disadvantages.
Police data is under-reported for various reasons: fear of negative publicity, lack of incentive, perception that the police response will be ineffectual, no prospect of restitutionary damages and victims not realizing that they have been victimized.
_
Many countries have strategies and approaches to increase the reporting of cybercrime, as shown in figure below.
_
Global cybercrime statistics of first decade of 21st century:
Hacking:
-In 2008, Verizon observed the compromise of over 180 million business records due to hacking.
Malware:
-Symantec has detected a total of approximately 2.6 million different malware programs, 60 per cent of which were detected in 2008.
Malware infections via legitimate websites:
-A 2007 study of 4.5 million web pages by Google found that one out of every ten websites contain malware.
Botnets:
-McAfee estimates that nearly 40 million computers were recruited to botnets in the first three quarters of 2009.
-The Internet Society of Australia submitted that estimates of the number of bot computers range from five percent of all computers connected to the Internet (over 20 million) to twenty-five per cent of all computers connected to the Internet (over 250 million).
DDoS attacks:
-Telstra submitted that the size of the largest DDoS attacks increased a hundredfold between 2001 and 2007, from 0.4 gigabits per second to 40 gigabits per second.
Cybercrime industry:
-Verizon reports that 91 per cent of the data breaches it observed in 2008 were linked to organised criminal networks.
Phishing and spam:
-In the year 2008, Symantec observed 349.6 billion spam messages across the Internet.
-Symantec claim that in 2008 approximately 90 per cent of spam was sent via botnets.
-The Anti-Phishing Working Group, an international consortium of organisations against phishing, identified over 210 thousand unique phishing websites in the first half of 2009.
_
The Anti-Phishing Working Group (APWG) recorded more than 1.2 million attacks in 2016, many linked to ransomware. This number may be low, since the FBI estimated there were 4,000 ransomware attacks every day in 2016. The Privacy Rights Clearing House estimates there were 4.8 billion records lost as a result of data breaches in 2016, with hacking responsible for about 60% of these.
Table below shows Estimated daily cybercrime activity
| Cybercrime | Estimated Daily Activity |
| Malicious scans | 80 billion |
| New malware | 300,000 |
| Phishing | 33,000 |
| Ransomware | 4,000 |
| Records lost to hacking | 780,000 |
_
The FBI received 467,361 internet and cyber-crime complaints in 2019, which the agency estimates have caused losses of more than $3.5 billion, the bureau wrote in its yearly internet crime report released recently. The FBI said that almost half of the reported losses — an estimated $1.77 billion — came from reports of BEC (Business Email Compromise), also known as EAC (Email Account Compromise) crimes.
BEC/EAC is a sophisticated scam targeting businesses and individuals performing wire transfer payments. At its heart, BEC relies on the oldest trick in the con artist’s handbook: deception. A typical BEC scam happens after hackers either compromise or spoof an email account for a legitimate person/company. They use this email account to send fake invoices or business contractors. These are sent to employees in the same company, or upstream/downstream business partners. The idea is to trick counterparts into wiring money into the wrong bank accounts. BEC scams are popular because they’re (1) dead simple to execute, and (2) don’t require advanced coding skills or complex malware.
According to the FBI’s 2019 Internet Crime Report, BEC scams were, by a considerable margin, the most damaging and effective type of cyber-crime in 2019. Only 23,775 BEC victim accounted for $1.77 billion in losses for victims, which is on average $75,000 per complaint. In comparison, phishing/smishing/vishing accounted for $500 in losses per complaint, while ransomware averaged $4,400.
_
Cybercrime Statistics of 2019:
- The cybercrime industry generated at least $1.5 trillion in revenue in 2018 (and that’s a conservative estimate!)
- Social media-enabled cybercrimes generate $3.25+ billion in global revenue per year
- $76 billion of the cybercrime economy involves Bitcoin
- 4.1 billion records were exposed via data breaches in 2019
- 85% of organizations reported experiencing phishing and social engineering attacks
- An average of 300,000 cybercrime-related complaints are received each year by the FBI
- Seniors over age 60 are the preferred victims of cybercrime against individuals
- More than 25% of malware attacks targeted banks and financial services in 2018
- Cybercrime damages are anticipated to cost $6 trillion per year by 2021.
- Cybercrime costs $2.9 million to the global economy every minute
- Up to 40% of social media sites have some form of turn-key hacking tools or services available for purchase
- The data of 1.3+ billion social networking users has been compromised within the past 5 years
- There are over 903 million malware in 2019.
- The average time to identify a data breach is 196 days.
- 45% of all companies hit by ransomware pay the demanded amount.
- Almost every second call to a mobile phone is a scam.
- Antivirus and anti-malware systems detect over 10,000 different malicious files every day.
- Over 540 million Facebook users’ data was exposed in 2019.
- More than two-thirds of all DDoS attacks originate from China.
- A hack occurs every 39 seconds
- Hackers earn around $30,000 per job, whilst their managers can make up to $2 million
- 60% of fraud goes through mobile devices, 80% of which are generated from mobile apps
- It is estimated that 1 out of every 50 emails contain malicious content.
- It is estimated that 91% of cyber-attacks of any form start with phishing emails.
- About 0.80% of the world’s GDP is lost to cybercrime. The total global cost of all the data breaches in 2019 amounts to $2.1 trillion.
- The total global impact of cybercrime has jumped to $3 trillion in 2015, making it more lucrative than the global trade in marijuana, cocaine and heroin combined.
_
But it’s not only big money corporations that are being attacked. Civil society groups, journalists and NGOs are the new targets of massive digital attacks. Several techniques are now used to infiltrate these groups, from government surveillance, online bullying, data theft and fake news. Citizen Lab recently released a report titled, Tainted Leaks, showing how civil society groups and journalists critical of the Russian government, were cyber-attacked using techniques like phishing, to steal or alter information they work with. Another report, Reckless Exploit, reveals how up to 10 Mexican journalists and human rights defenders were attacked with advanced spying software, for working on a range of issues that included corruption allegations against the Mexican President, and human rights abuses by the government.
_
China and Russia are Biggest Cyber Offenders:
A study attributes more than 200 cyberattacks to the two countries over the past 12 years. According to a recent report produced by the Center for Strategic and International Studies (CSIS), a think tank based in Washington, 2018 was an active year for cyberattacks, with more than 100 significant incidents occurring in the past year. Looking at publicly available data on cyber-espionage and warfare but excluding cybercrime, the CSIS study reveals that China and Russia have been the largest source of attacks in cyberspace since 2006. In December of 2018 alone, four major incidents were reported involving China, while three involved Russia.
From 2006 to 2018, China was involved in 108 cyber incidents with losses of more than $1 million each, compromising communications across Europe, conducting cyber-espionage spying on 12 countries and stealing information from hundreds of millions of customers of a U.S. hotel chain, according to the CSIS report. Another study labeled China as the biggest state sponsor of cyberattacks on the West.
Russia has been responsible for 98 major cyber incidents since 2006 with losses of more than $1 million each, the CSIS report said, and is accused of hacking Ukraine’s government, NATO operations, the Czech security service and the German Parliament.
The CSIS report examined data on China, North Korea, Iran, India, Russia, the United Kingdom, the United States, Germany, Australia, Japan, South Korea, Ukraine, Israel and France, with the rest of the world listed as a separate category. The study named the rest of the world as the third-worst offender, with 67 incidents. Next in the ranking came Iran with 44 incidents, and North Korea with 38. India was listed as guilty of 16 important cyber incidents from 2006 to 2018, while the U.S. was accused of nine.
Just two countries were identified as having not been the source of cyberattacks in the past 12 years: Japan and Australia.
__
Cybercrimes in India:
India is the largest market for internet users after China. China has 854 million internet users and India has 560 million internet users in 2019. India’s rapid and uncontrolled digitization combined with a young digital population and an inadequate response mechanism make cyber-attacks easy to carry out. Frauds involving theft of small amounts of money, social media bullying, lottery scams and sexual harassment are some of the motives behind attacks. For every 500 cybercrimes that take place, only 50 are reported to the police and just one gets registered as FIR (first information report). A lack of awareness among the population causes many cyber incidents to be left unreported. In cases where it is reported, the infrastructure and process to tackle the crime is often inefficient. In the IT capital of the country, Bangalore, one police officer was reported to handle as many as five thousand investigations, most involving password theft. India stands 11th in the world for cybercrime, constituting 3% of the global cybercrime. In India hacking has witnessed 37% increase.
A Symantec report published in January 2019 reveals that globally India is the third least honest country on the Internet. The report reveals that over half of Indian adults have lied online. This means half of the Indian adults have lied on their social and professional networking sites as well as on other platforms. Clearly when of the hundreds of millions of Indian adults online, half have created profiles that contain lies or profiles that are completely false, many, including employers, must have been duped in one way or another.
The statistics are grim. Symantec reveals that 76% of Indians have been victims of some form of cybercrime and 60% have been victimised because of computer viruses and malware. A tiny minority, only 8% do not believe they will fall victim to cybercrime. Clearly, the overwhelming majority of Indians considers cybercrime a significant threat. In India, only 10% of people feel very safe online. Not only do many Indians believe they will fall prey to cybercriminals, the majority, approximately 57%, believe cybercriminals will never be brought to justice. The Symantec report reveals that over the last 5 years, there has been a 457% increase in cybercrime in India. India ranks third with respect to the number of cybercriminals living in the country and third in the number of cybercrime victims.
India ranks 23rd out of 165 nations in the United Nation’s Global Cybersecurity Index in terms of its commitment to cybersecurity. The UN classified India under the “maturing” category implying the country is in the process of developing a complex cyber security program.
______
______
Characteristics of cybercrime:
_
The unique characteristics of cybercrime:
- Organized
Developments in technology have proved to be a catalyst in the world of cybercrime, making efforts organized, sophisticated and borderless. Law enforcement agencies must collaborate across borders to take down networks comprised of dozens of individuals. The image of a lone hacker behind a computer is no longer accurate. These criminal networks are compared to corporations due to their levels of organization and collaboration. Elaborate methods and processes are employed to accomplish significant heists and data breaches. Roles are spread across the globe to fulfill the needs of an operation.
The dark web makes cybercrime ubiquitous because it is not indexed by public search engines. While not all content is dangerous per se, it is a breeding ground for criminal collaboration and the exchange of illicit and illegal services. Products such as compromised financial credentials can be purchased from user-friendly sites that provide reviews and ratings. The dark web has proved to be a major cornerstone in the increasingly organized world of cybercrime.
- Sophisticated
Encryption and cryptocurrency are two innovations that have led to the increased complexity and efficiency of cybercrime attacks. Cryptocurrency, like bitcoin, simplifies paying and receiving ransoms, which has fueled ransomware attacks. These attacks lock down a computer through encryption and demand money in return. The level of sophistication allows for the scale of cyber-attacks to reach massive volumes of affected individuals and organizations.
- Interconnected
The internet has no borders. A recent ransomware attack entrapped 200,000 victims from 150 countries within 24 hours. Malicious software can spread across borders and industries due to the connective nature of the internet. Cybercrime now crosses into the physical world as the internet of things expands and connects devices and services: security cameras, pacemakers, smart devices, smart homes, self-driving cars, the electrical grid, water systems and more.
The Internet deserves special attention in criminology as well as criminal law and policy, because of several characteristics: it is global, instantaneous, intrinsically transborder, digital, and enables automated information processing. Because of these characteristics, the Internet provides special opportunities to commit cybercrimes: crimes in which computer networks are the target or a substantial tool.
- Internationality
The virtual world does not feature any frontiers and the different legal systems apply according to the territorial competences of law enforcement agencies. The borderless nature of cybercrime makes it possible to commit crimes against government, business and citizens in one nation from almost anywhere around the world. Compared to other, more traditional crime types, criminals who use the Internet for hacking computers, stealing data and emptying bank accounts are not hindered by logistic constraints, such as travelling and transporting the looted goods. There is hardly any identifiable link between the criminals and the crime scenes.
These crimes transcend jurisdictional boundaries, often involving multiple victims from different communities, states and countries. The geographic location of a victim is not a primary concern for perpetrators who target victims over the Internet.
As cybercrimes make geographical boundaries insignificant, combating cybercrime calls for international harmonization of laws and crossborder regulation, along with mandatory global prosecution procedures; however, such is not the case, nor is it feasible in the near future. Regulation is usually fragmented, and countries differ on definitions of cybercrime, leave alone the types of crime and punishment.
Cybercriminals exploit this situation by coming up with new tools and discovering new vulnerabilities to attack targets. Moreover, the targets of cybercrime have evolved from personal targets to financially sound targets such as business enterprises that can be held to ransom and made to pay big monies.
- The scalability
The scalability results from the ease to replicate crimes on a massive scale due to the standardization of software and the possibility to reach millions of computers without any logistical constraints.
- Anonymity and pseudonymity
Perpetrators feel very safe and can easily hide their real identity on the Internet. Physical contact between victim and perpetrator is not necessary to become a victim or for a crime to be committed.
The Internet also provides a source for repeated, long-term victimization of a victim that can last for years, often without the victim’s knowledge. For example, once a victim’s picture is displayed on the Internet, it can remain there forever. Images can stay on the Internet indefinitely without damage to the quality of the image.
Many victims of Internet crimes do not disclose their victimization or even realize that they have been victims of a crime. For example, whereas children who experience physical or sexual abuse may disclose the abuse to a friend, teacher, parent, many victims of Internet crimes remain anonymous until pictures or images are discovered by law enforcement during an investigation.
The presumed anonymity of Internet activities often provides a false sense of security and secrecy for both the perpetrator and the victim. There are different technologies and forums that criminal actors can take advantage of in order to anonymize themselves and facilitate criminal activity. The ease to hide comes from the use of hacked computers, stolen identities and from techniques to re-route traffic through numerous nodes while obfuscating the origin. Operating from or via countries in which the regime has limited competence or ambition to prevent and fight cybercrime is an effective way to hide. For example, the anonymity of the Internet is frequently misused for child sexual exploitation. Child abuse material is offered and exchanged via anonymous networks, but also through peer-to-peer networks and peer groups on social media.
Darknets offering a high degree of anonymity are increasingly hosting hidden services devoted to traditional types of crimes, like for example drug trade, selling stolen goods, weapons, compromised credit card details, forged documents, fake ID’s and trafficking of human beings.
- Asymmetry
Authors of internet crimes are mostly ahead of police and justice authorities by developing new modi operandi. Criminal entrepreneurs can operate relatively efficiently due to the innovation enabled by the Internet. This results in a strife between criminal developers and those who try to foil them. It is really hard protecting yourself against unknown vulnerabilities, which makes it hard to stay ahead of criminal actors. The law enforcement already had some limited success in penetrating technologies to identify and capture criminals, and/or has taken advantage of sloppy use of these technologies to find those who hide behind them.
However, the speed and capacity of cybercriminals to develop and guard what, how and where they do it in cyberspace should not be underestimated. Law enforcement experiences have already shown that cybercriminals are efficient in learning from police operations and responding to these with improved software security and encryption, and mechanisms for conducting criminal activity.
- Low marginal cost of online activity
The effort and resources required to commit a cybercrime are substantially less than for traditional crimes. In general, effort refers to the combination of mental energy and time necessary to implement the attack. If the demand for attack resources as greater, the target becomes less attractive. In contrast, like with cybercrimes, computers provide most of the effort and resources, by virtue of their tremendous speed of processing, rendering cyber targets attractive.
- Nature of criminal cooperation
The nature of criminal cooperation via the internet has resulted in networks of criminals that amplify each other’s criminal services. This applies in the area of cybercrime, but also other types of crime. A complete underground economy has developed, where all kinds of criminal products and services are traded such as drugs, weapons, stolen payment credentials, child abuse etc. As mentioned earlier, this is facilitated by anonymous payment systems, such as virtual currencies and hidden market places where the criminal services are offered. Especially for cybercrime this underground economy has a multiplying effect, because any kind of cybercrime can be procured by anyone even without any technical skills or instruments: password cracking, hacking, malware testing and many more.
_
Govil mentioned the following characteristics shown in figure below.
These characteristics make traditional law enforcement strategies, particular strategies based on identifying and apprehending perpetrators after they commit online crime, less effective and more expensive.
However, other characteristics of cyberspace provide at the same time new opportunities to control illegal acts. Unlike the physical world, in cyberspace certain readily identifiable third parties – such as Internet service providers, telecommunication providers, and victims themselves – have exclusive or shared technical control over the infrastructure through which most illegal online behavior is carried out. The characteristics provide new opportunities for innovative policy approaches to controlling undesirable behavior; including the use of technical architecture as a regulatory mechanism, the use of novel authorization and surveillance regimes to prevent or deter undesirable activity, and the use of data and activity logging to enhance persistence and recoverability of evidence, amongst others.
_____
_____
Differences between cybercrime and traditional crime:
Crime is a social and economic phenomenon and is as old as the human society. Crime or an offence is “a legal wrong that can be followed by criminal proceedings which may result into punishment.”
- The hallmark of criminality is that, it is breach of the criminal law.
- A crime may be said to be any conduct accompanied by act or omission prohibited by law and consequential breach of which is visited by penal consequences.
_
Is Cybercrime a new form of crime?
Some people suggest that the advent of ‘virtual crimes’ marks the establishment of a new and distinctive social environment with its own ontological and epistemological structures, interactional forms, roles and rules, limits and possibilities. Other people see ‘cybercrime’ as a case of familiar criminal activities pursued with some new tools and techniques. Grabosky suggested that cybercrime was simply a case of ‘old wine in new bottles’. If this was the case, cybercrime could be fruitfully explained, analysed and understood in terms of established criminological classifications.
Like traditional crime, cybercrime has different facets and occurs in a wide variety of scenarios and environments. Apparently, there is no distinction between cyber and conventional crime. However, on a deep introspection we may say that there exists a fine line of demarcation between the conventional and cybercrime, which is appreciable. The demarcation lies in the involvement of the medium in cases of cybercrime. The sine qua non for cybercrime is that there should be an involvement, at any stage, of the virtual cyber medium.
On the other hand, combating cybercrime requires a different approach from the one traditionally taken in respect of most crimes, because of severity of cybercrime and the extent to which it has a greater potential for harm than traditional crime. In contrast to the off-line world where criminals need to be physically present at the crime scene and can commit one offence at a time, criminals in cyberspace do not need to be close to the crime scene, they do not have to travel to the target country, and can attack a large number of victims globally with a minimum of effort and risk through hiding their identity. The information capabilities of the Internet change the nature of crime, as they provide cyber criminals with simple, cost effective and repeatable means of conducting rapid global-scale attacks, while remaining anonymous and/or unreachable for law enforcement. Cybercrime opens new doors to criminals where they have the power to defraud entire institutions in ways that would not have been possible traditionally. Housing billions of gigabytes of sensitive information and valuable data, the Internet is very appealing to criminal organizations, who can act anonymously (and so remain more unpunished). Finally, one of the differences between cybercrime and traditional crime is the evidence of the offenses: traditional criminals usually leave traces of a crime, through fingerprints, physical evidences. On the other hand, cybercriminals rely on the Internet via which they commit their crimes, and leaves little evidence.
_
_
Similarities between traditional crime techniques and cybercrime techniques:
| Traditional Techniques | Internet | Cybercrime |
| Theft: Breaking and entering with the intention of stealing | Hacking: Infiltration into a device or a communication network by means of unauthorized access. | |
| Fraud: Obtaining by all means of communication financial data and information from a person with the intention of committing a crime | Phishing: A computer trick that sends spam messages to the victim in order to obtain data and financial information of a person for criminal purposes. | |
| Blackmail and Abuse: Illegal or abusive use of position in order to obtain undue benefits, bribery, power or influence | Internet Blackmail and Abuse: Illegal access via data networks to control various personal, industrial and/or governmental databases, or blocking and altering them. The aim is to blackmail the victim in order to obtain money or satisfy other requirements. | |
| Fraud: Deception, fraud, bad faith act in order to make a profit by harming another person’s rights. | Internet fraud: Creating a profile similar to the victim by illegally obtaining information about him/her and using that information to commit crimes of fraud and deceit, usually to get material benefits | |
| Identity Theft: The personification or representation of another person using personal data and its history to gain access, information or favors / benefits | Identity Theft: Creating a profile similar to the victim by illegally obtaining information about her and using those information to commit crimes of fraud and deceit. Usually to get material benefits | |
| Children abuse and exploitation: Child abuse and exploitation with indecent purposes, the most common cases are child pornography and sexual abuse | Children abuse and exploitation: Facilitate abuse (usually sexual) and their exploitation through modern communication devices. |
_
Simply put, cybercrime is a crime committed using the means of technology and the internet. Although we talk about cybercrime as a separate entity to traditional crime, it is carried out by the same types of criminals for the same type of reasons. These hackers are professional thieves, criminal gangs, disgruntled employees, professional competitor, activists, disillusioned youth and state adversaries. They have the same motivations as traditional criminals such as boredom and vandalism, ideological or political support, malice or revenge, monetary gain through extortion or sale of illegally obtained data, terrorism or notoriety and sensationalism. The methods that cyber criminals use to gather data and perform an attack is comparable to physical ‘traditional’ crimes. For example, let’s compare how a criminal gang might go about breaking into a bank to steal money against how a cyber-criminal gang might go about breaking into a computer network to steal data.
So apart from the use of technology what is the difference between cybercrime and traditional crime?
- The Scale
Attacks can be conducted on a scale not possible in the physical world. A traditional bank robber may only be able to hit one or two banks a week, a cyber-attack can target 100’s if not 1000’s of sites at once.
- The Reach
Attacks can be performed from anywhere in the world; they can be performed anonymously and within jurisdictions where the consequences of those actions may not, or cannot, be addressed by the criminal justice system. Attackers are also able to extract far more data digitally than would ever be possible in the physical world. For example, 1 gigabyte of data is approximately 4,500 paperback books. Think of how many gigabytes of data is held on a system, hackers can extract this within a matter of minutes.
- The Speed
Attacks are conducted at machine speed; a criminal can write a piece of code that can target multiple sites in minutes.
- Perception and Media Effect
There is another part of the cyber threat to be considered, the public and media perception of cybercrime. When large financial institutions have been hacked the media has often wholly apportioned blame to the organisations rather than the criminals, this would not be the case in a physical bank robbery.
_
With regard to the penalty phase of cybercrime versus physical crime, there appears to be an apparent disparity. As in most white-collar crime, the judicial system is generally more lenient during sentencing due to the lack of physical threat or harm. Normally, value is a consideration during the penalty phase of white-collar crime, whereby the total value of goods stolen impacts sentencing. If a person with a handgun steals a thousand dollars from a store clerk and shoots the clerk in the shoulder, but an 18-year old hacker steals $10,000 from a bank in Utah, would 15-year sentences for both crimes be sufficient for the public to perceive that justice has been served? Ultimately, there will almost always be a disparity in sentencing between violent and white-collar crime due to the threat of violence and harm to the person versus the value of the theft. However, as cybercrimes become more trans-national and values increase exponentially, the international community, judicial systems, and public outcry will begin to change perceptions and more than likely adjust sentencing parameters to align with local and international perceptions.
_
Risk factors for traditional crime and cybercrime:
Personal and situational risk factors such as low self-control, risky life-styles or routine activities, substance abuse and socioeconomic status are associated with both offending and victimisation risks for traditional crimes (e.g., Berg & Felson, 2016; Jennings et al., 2012; Rokven et al., 2016). People, who spend more time with delinquent friends and/or in places where crimes take place, are more at risk of being victimised and also have more criminal opportunities (e.g., Jensen & Brownfield, 1986; Lauritsen et al., 1991; Rokven et al., 2016; Sampson & Lauritsen, 1990; Schreck, Wright, & Miller, 2002).
Cybercrimes tend to be committed in a different context than traditional crimes, which may lead to different risk factors for both offending and victimisation. The relationship between traditional offending and victimisation is the strongest for violent crimes, which per definition require physical interaction between victims and offenders (Berg & Felson, 2016; Lauritsen & Laub, 2007). In the case of cybercrime there is no physical convergence in space and time of offenders and victims (e.g., Bossler & Holt, 2009; Holt & Bossler, 2008; Yar, 2005a). Nevertheless, previous research suggests that victims and offenders eventually interact with one another in order for cybercrime to occur, even if it occurs asynchronously. This may account for the association identified between cybercrime offending and the increased risk of victimisation, as well as common risk factors for both experiences, including low self-control, routine activities and socio-demographic characteristics (e.g., Bossler & Holt, 2009; Holt & Bossler, 2014; Ngo & Paternoster, 2011; Wolfe et al., 2008).
Research examining the association between cybercrime offending and victimisation has largely focused on forms of cybercrime that do not require technical expertise or are not dependent on technology, such as fraud (Ngo & Paternoster, 2011) and bullying (Holt & Bossler, 2008). New and more technical cyber-dependent crimes, like cyber-trespass (Wall, 2001), have received less attention from researchers. For instance, research on malware victimisation found individuals with malicious software infections were more likely to engage in online deviance, mainly piracy or viewing pornography (e.g., Bossler & Holt, 2009; Choi, 2008; Wolfe et al., 2008). When comparing online harassment victimisation with hacking victimisation, Van Wilsem (2013) found that online offending was related to harassment victimisation but not to hacking victimisation.
Considering the common risk factors associated with cybercrime victimisation and offending, it is imperative to understand their underlying theoretical relationships. The primary risk factor identified across multiple studies of cybercrime is low self-control, though it has greater explanatory power for less technical forms of cybercrime (Holt & Bossler, 2014). Some forms of cybercrime are simple to complete, provide immediate gratification for the individual, and present multiple opportunities for offending, such as digital piracy (Holt & Bossler, 2014). These same conditions may increase an individual’s risk of victimisation as savvy offenders may target those who are online more frequently and engage in risky activities like downloading pirated materials (Bossler & Holt, 2010). Empirical studies on low self-control show mixed results. Van Wilsem (2013) found that low self-control was positively related to hacking victimisation, while Bossler and Holt (2010) found that low self-control was neither related to hacking nor to malware victimisation. Holtfreter, Reisig, and Pratt (2008) found that although targeting of scam victims is random, the personal characteristics and behaviour of the victim influenced who responded to a scam. As a result, low self-control may play a role in the risk of victimisation regardless of the targeted nature of victimisation.
With respect to offending, it has been argued that advanced types of hacking and other technical cyber-dependent crimes require more self-control. Offenders must learn the skills needed in order to commit the act, such as manipulation of computer hardware and software via malicious software (Bossler & Burruss, 2011). They must also have the patience to plan and execute the offence properly and cover their tracks (e.g., Holt & Kilger, 2008). In contrast, some research has found that offenders who learn from friends do not need high self-control to be able to commit these crimes (Bossler & Burruss, 2011; Holt, Bossler, et al., 2012).
As a second risk factor, online routine activities enable the digital convergence of offenders and victims and may be associated with a cybercrime victim-offender overlap. Individual involvement in routine activities that increase exposure to motivated offenders may disproportionately increase the risk of victimisation. To that end, several studies have found time spent in specific activities, like time spent using email or social media, increases individual risks of interpersonal victimisation such as online harassment (Bossler & Holt, 2009; Holt & Bossler, 2008; Leukfeldt, 2014). In a recent study, based on a large representative sample, online communication, or use of forums or social networks increased hacking victimisation (Leukfeldt & Yar, 2016). Time spent using the internet, targeted and untargeted browsing, online shopping, downloading and gaming were all related to malware victimisation (Leukfeldt & Yar, 2016).
Studies that relate offending to life-style or routine activity measures are virtually non-existent for serious forms of cybercrime, such as complex hacks and the use of malicious software. Nevertheless, studies have shown that spending time on social networks or online forums can provide offenders with the knowledge or social contacts to commit cybercrime (e.g., Holt, Strumsky, Smirnova, & Kilger, 2012; Hutchings, 2014). In addition, online gaming environments can increase opportunities and motivation for hacking, but could consequently also increase the risk for victimisation. An example is hacking into gaming accounts to steal virtual objects or credits (Blackburn, Kourtellis, Skvoretz, Ripeanu, & Iamnitchi, 2014; Hu, Xu, & Yayla, 2013). Kerstens and Jansen (2016) also found that spending more time online results in a higher likelihood of being a victim-offender. This suggests that although there is no physical convergence of offenders and victims, the digital convergence of actors in online spaces can increase the risk of cybercrime victimisation.
Studies of cybercrime victimisation include online routine activities only, while studies of traditional crime only include offline daily routine activities like work or school, and nightlife activities like going out and being with friends (Lauritsen et al., 1991). The absence of measures may lead to model misspecification as online activity could increase the risk of offline crimes like fraud (Holtfreter et al., 2008). At the same time, traditional crimes might decrease because individuals spend more time online (Tcherni et al., 2016). Consequently, both online and offline activities must be included in any analyses of cybercrime and traditional crime to more accurately assess the influence of behaviours on the risk of offending and victimisation (Leukfeldt & Yar, 2016).
In addition to the opportunities and risks created by routine activities, a person’s technological skill could influence their opportunities for cybercrime offending as well as victimisation risks. Individuals with greater technical expertise, acquired through social relationships and personal experience, may directly and indirectly increase a person’s ability to engage in cyber-dependent crimes (Bossler & Burruss, 2011; Chua & Holt, 2016; Holt, Bossler, et al., 2012; Holt & Kilger, 2008).
Technological capacity may also serve as a protective factor against cybercrime victimisation, as it is thought technically proficient individuals can identify when their computer may have been compromised or utilise appropriate resources to secure their system. Most studies, however, find no relationship between IT skills and malware infections (e.g., Bossler & Holt, 2009; Ngo & Paternoster, 2011), though some have found the opposite (e.g., Van Wilsem, 2013). These contradictory findings may stem from differences in technology use as a function of IT-skills, which may increase the risk for victimisation. Leukfeldt and Yar (2016) found that although computer knowledge in general was not related to hacking or malware victimisation, operating system and browser type were related to malware victimisation and risk awareness was negatively related to hacking victimisation.
In addition, the link between socio-demographic factors that explain traditional offending and victimisation and cybercrime is mixed. Previous research suggests that cybercrime offending, especially of more cyber-dependent crimes, occurs in higher social classes (e.g., Pontell & Rosoff, 2009) and victimisation occurs more often among higher educated people (e.g., Leukfeldt & Yar, 2016).
_
Convergence of cybercrime and traditional crime:
It’s easy to forget that cybercrime is a relatively new term that didn’t exist 30 years ago. Today, excluding some violent crimes, it appears that almost every conceivable crime can have a cyber element to it. Cybercrime can be described as any illegal activity that is dependent on a computer or network-connected device. But as devices are increasingly network connected, could we see a blurring of the line between traditional crime and cybercrime?
-Internet of Things
The concept of connecting any device with an on and off switch to the Internet is known as the Internet of Things (IoT). Connectivity, convenience, automation – these are some of the benefits that the IoT will bring. However, these benefits provide opportunities for miscreants to commit crimes which have a physical impact – not just the information security and financial impact we often associate with cybercrime.
That’s exactly what happened in Lappeenranta, Finland. Attackers caused heating systems to go offline by targeting them with a Distributed Denial of Service (DDoS) attack, leaving residents to face the sub-zero temperatures typical for that time of year.
In Germany in 2014, attackers infiltrated the corporate network of a steel mill, and used the access to pivot into the production network, enabling them to manipulate the facility’s control systems. The attack led to failures in equipment, and caused a blast furnace to explode.
In both of the above cases, the result was sabotage. Although no ransom demands were reported, the two cases highlight the opportunities that the IoT will bring to criminals. For some companies, cybercrime will not just be about data and financial theft. They will also have to consider the physical impact of cybercrime – in addition to the existing physical risks associate with day to day operations. The insurance industry is already struggling to comprehensively quantify cyber risks; the physical considerations presented by the IoT will create further challenges for the industry.
-Traditional Crimes
Sometimes criminals use cyber methods to enhance the modus operandi of existing operations. Increasing digitalisation and globalisation is creating more opportunities for this to happen; blurring the lines between traditional crime and cybercrime.
The search for new ways to get drugs out of a port in Belgium port led a group of drug smugglers to recruit hackers in 2011. Together, the alliance hatched a plan which included the hacking of the port’s computer networks. Sometime later, after the breach was discovered, and their plan foiled, the group broke into the premises and plugged remote access devices into computers. The group sought to infiltrate the port’s systems to steal release codes which enabled containers to be collected by authorised personnel. The objective was to gain access to cocaine and heroin, which the smugglers had hidden amongst legitimate goods prior to the departure of the container ships. Police were first alerted when entire containers began to disappear mysteriously.
There are plenty of examples of traditional crimes being facilitated by cyber methods. From human traffickers breaching airport systems with the help of immigration officers, to the shift from postal to email-based advance fee fraud by West African fraudsters. The hidden web, and in particular, Tor and other darknets currently provide the largest markets for the trade in illicit goods and services. Such darknet sites are increasingly replacing the ‘man in the pub’ and the drug dealer on the corner.
____
____
Causes of cybercrime:
_
Humans tend to engage in criminal enterprises when the rate of return on investment is high and the risk of loss is low. This calculation is made every day on the part of cybercriminals, and they have concluded it is profitable to continue committing fraud, stealing financial information and hacking into networks worldwide. Also, one of the main causes of rapid increase in the cases of cybercrimes is our dependency on cyberspace, even for the most basic things like shopping, making payment, ordering food, etc. and where there is such uncontrollable dependency, some people out there are definitely going to take advantage of it.
__
Computers are vulnerable and reasons for the vulnerability of computers are as follows:
- Easy to access – The problem behind safeguarding a computer system from unauthorized access is that there are many possibilities of breach due to the complex technology. Hackers can steal access codes, retina images, advanced voice recorders etc. that can fool biometric systems easily and bypass firewalls can be utilized to get past many security systems.
- Capacity to store data in comparatively small space – The computer has the unique characteristic of storing data in a very small space. This makes it a lot easier for the people to steal data from any other storage and use it for own profit.
- Complex – The computers run on operating systems and these operating systems are programmed of millions of codes. The human mind is imperfect, so they can do mistakes at any stage. The cybercriminals take advantage of these gaps.
- Negligence – Negligence is one of the characteristics of human conduct. So, there may be a possibility that protecting the computer system we may make any negligence which provides a cyber-criminal the access and control over the computer system.
- Loss of evidence – The data related to the crime can be easily destroyed. So, loss of evidence has become a very common & obvious problem which paralyzes the system behind the investigation of cyber-crime.
___
Motives for cybercrime:
There are many reasons why people commit a cybercrime: recognition, quick money, to fight a cause (one thinks) he believes in, low marginal costs of online activity due to global reach, official investigation and criminal prosecution is rare, no concrete regulatory measure, lack of reporting and standards, difficulty in identification, limited media coverage and corporate cybercrimes are done collectively and not by individual persons.
- Money
Anyone who makes a financial profit from the crime – whether it is a bank employee who uses his computer access to divert funds from someone else’s account to his own, an outsider who hacks into a company database to steal identities that he can sell to other criminals, or a professional “hacker for hire” who is paid by one company to steal the trade secrets of another. Almost anyone can be motivated by money – they are young, old, male, female, those from all socio-economic classes.
- Emotion
The most destructive cybercriminals often act out of emotion, whether anger/rage, revenge, “love” or despair. This category includes spurned lovers or spouses/ex-spouses (cyber-stalking, terroristic threats, email harassment, unauthorized access), disgruntled or fired employees (defacement of company web sites, denial of service attacks, stealing or destroying company data, exposure of confidential company information), dissatisfied customers, feuding neighbors, students angry about a bad grade, and so forth. This can even be someone who gets mad over a heated discussion on a web board or in a social networking group.
- Sexual impulses
Although this is related to emotion, this category is slightly different and includes some of the most violent of cybercriminals: serial rapists, sexual sadists (even serial killers) and pedophiles. Child pornographers can fit into this category or they may be merely exploiting the sexual impulses of others for profit, in which case they belong in the “money” category.
- Politics or religion
This category is also closely related to the “emotions” category, since people get very emotional about their political and religious beliefs and are willing to commit heinous crimes in the name of those beliefs. This is the most common motivator for cyberterrorists, but motivates many lesser crimes, as well.
- Just for fun
This motivation applies to teenagers (or even younger) and others who may hack into networks, share copyrighted music/movies, deface websites and so forth – not out of malicious intent or any financial benefit, but simply “just because they can”. They may do it to prove their skills to their peers or to themselves, they may simply be curious, or they just may see it as a game. Although they do not intentionally do harm, their actions can cost companies money, cause individuals grief and tie up valuable law enforcement resources.
_______
_______
Cybercriminals’ profiles, categories and characteristics:
Cybercrime offenders no longer require complex skills or techniques, due to the advent and ready availability of malware toolkits. While some perpetrators may have completed advanced education, (especially in the computer science field) many known perpetrators do not have any specialized education. More than 80% of cybercrime acts are estimated to originate in some form of organized activity, with cybercrime black markets established on a cycle of malware creation, computer infection, botnet management, data sale, and ‘cashing out’ of financial information. Cybercrime often requires a high degree of organization to implement and may lend itself to small criminal groups, ad hoc networks or organized crime on a larger scale. The typology of perpetrators and active criminal groups mostly reflect patterns in the conventional world.
The demographic nature of perpetrators mirrors conventional crime in that young males are the majority, although the age profile is increasingly showing older individuals, particularly concerning child pornography offences. Different studies suggest that cybercrime perpetrators are most commonly aged between 18 and 30 years old. Other studies can differ somewhat, and indicate older perpetrator age groups. Nevertheless cybercrime perpetrators overall may be younger than criminal offenders in general. Cybercrime perpetrators are also mainly male.
The profile of persons engaged in the computer-related production, distribution or possession of child pornography is different to that of cybercrime offenders in general. They are male and ranged in age from 15 to 73 years, with an average age of 41 years. Online offenders are more likely to be unemployed and marginally younger than offline offenders, but links nonetheless may exist. A part of online child pornography offenders, may also be involved in ‘offline’ abuse of children.
_
The typical cybercriminal:
What does profiling tell us about the “typical” cybercriminal – the person who uses computers and networks to commit crimes? There are always exceptions, but most cybercriminals display some or most of the following characteristics:
- Some measure of technical knowledge (ranging from “script kiddies” who use others’ malicious code to very talented hackers).
- Disregard for the law or rationalizations about why particular laws are invalid or should not apply to them.
- High tolerance for risk or need for “thrill factor.”
- “Control freak” nature, enjoyment in manipulating or “outsmarting” others.
- A motive for committing the crime – monetary gain, strong emotions, political or religious beliefs, sexual impulses, or even just boredom or the desire for “a little fun.”
That still leaves us with a very broad description, but we can use that last characteristic to narrow it down further. This is especially important since motive is generally considered to be an important element in building a criminal case (along with means and opportunity).
__
Signs of a possible white-collar cybercriminal include:
- Refusal to take time off from work or let anyone else help with his/her job, lest they uncover what’s been going on.
- Attempts to avoid formal audits.
- A lifestyle far above what would be expected on the person’s salary with no good explanation for the extra income.
- Large cash transactions.
- Multiple bank accounts in different banks, especially banks in different cities or counties.
__
Categories of cybercriminals:
In the Journal of Alternative Perspectives in the Social Sciences, 4 categories of cybercriminals are described.
- Children and adolescents between the 6 – 18 years: The simple reason for this type of delinquent behavior pattern in children is seen mostly due to the inquisitiveness to learn, know and explore things. Other reasons may be to prove themselves, to be outstanding amongst other children in their group. Furthermore the reasons may be psychological. In most literature you can find in this category the ‘script-kiddies’.
- Organised hackers: These kinds of hackers are mostly organised to reach certain objectives together. The reason may be to accomplish political bias, fundamentalism, etc.
- Professional hackers / crackers: The work of professional hackers or crackers, is motivated by the color of money. These kinds of hackers are mostly hired to hack the site of rivals to receive credible, reliable and valuable information.
- Discontented employees: Those people have been either sacked by their employer or are dissatisfied with their employer. They normally hack the system of their employer to get some revenge.
__
Marcus Rogers identified 8 types of cyber-criminals, distinguished by their skill levels and motivations.
- Novice
- Limited computer and programming skills.
- Rely on toolkits to conduct their attacks.
- Can cause extensive damage to systems. since they don’t understand how the attack works.
- Looking for media attention.
- Coders
- Acts as mentors to the newbies. Write the scripts and automated tools that others use.
- Motivated by a sense of power and prestige.
- Dangerous – have hidden agendas, us Trojan horses.
- Cyber-punks
- Capable of writing their own software.
- Have an understanding of the systems they are attacking.
- Many are engaged in credit card number theft and telecommunications fraud.
- Have a tendency to brag about their exploits.
- Old guard hackers
- Appear to have no criminal intent.
- Alarming disrespect for personal property.
- Appear to be interested in the intellectual endeavor.
- Internals
- Disgruntled employees or ex-employees
- May be involved in technology-related jobs.
- Aided by privileges they have or had been assigned as part of their job function.
- Pose largest security problem.
- Petty thieves
- Include employees, contractors, consultants.
- Computer literate.
- Opportunistic: take advantage of poor internal security.
- Motivated by greed or necessity to pay off other habits, such as drugs or gambling.
- Professional criminals
- Specialize in corporate espionage.
- Guns for hire.
- Highly motivated, highly trained, have access to state-of-the-art equipment.
- Information warriors/cyber-terrorists
- Increase in activity since the fall of many Eastern Bloc intelligence agencies.
- Well-funded.
- Mix political rhetoric with criminal activity. Political activist.
- Possible emerging category.
- Engage in hacktivism.
__
Common Types of Cyber Criminals:
- Identity Thieves
Identity thieves are cyber criminals who try to gain access to their victims’ personal information – name, address, phone number, place of employment, bank account, credit card information and social security number. They use this information to make financial transactions while impersonating their victims. Identity theft is one of the oldest cybercrimes, gaining prominence during the early years of the Internet. Initially, these cyber criminals leveraged basic hacking techniques, such as modifying data and leveraging basic identity fraud to uncover the desired information. Today, the practice has progressed in scope and technique due to advances in computing, and now, many identity thieves can hack into a government or corporate database to steal a high-volume of identities and personal information. This expansion of strategy has resulted in major losses for companies and consumers, with recent studies indicating that approximately $112 billion has been stolen by identity thieves over the past six years.
- Internet Stalkers
Internet stalkers are individuals who maliciously monitor the online activity of their victims to terrorize and/or acquire personal information. This form of cybercrime is conducted through the use of social networking platforms and malware, which are able to track an individual’s computer activity with very little detection. The motives for such attacks can differ depending on the cybercriminal, but many internet stalkers seek to acquire important information that they can use for bribery, slander, or both. Businesses should be aware of internet stalkers, as well as the strategies that they utilize, in case their employees are ever victims of this cyberattack. If left unaddressed, internet stalkers could cause emotional distress to the team or even obtain data for blackmail.
- Phishing Scammers
Phishers are cyber criminals who attempt to get a hold of personal or sensitive information through victims’ computers. This is often done via phishing websites that are designed to copycat small-business, corporate or government websites. Unsuspecting computer users often fall prey to such activities by unknowingly providing personal information including home addresses, social security numbers, and even bank passwords. Once such information is obtained, phishers either use the information themselves for identity fraud scams or sell it in the dark web. It’s important for businesses to constantly be aware of phishing scams, particularly scams that may be trying to copycat their own business site. Such sites can tarnish the company’s reputation and brand, which could potentially lead to a decrease in earnings.
- Cyber Terrorists
The key difference between an act of cyberterrorism and a regular cyberattack is that within an act of cyber terrorism, hackers are politically motivated, as opposed to just seeking financial gain.
______
Different types of hackers:
There are three classes of hackers-white hat hackers, black hat hackers, and grey hat hackers.
White Hat Hackers
White Hackers use their hacking skills for good reasons and do no harm to the computer system. So they are referred as ethical hackers.
Black Hat Hackers
A black hat hacker is a person who gains unauthorized access to a computer system with a malicious intention. The black hat hackers use their computer knowledge for private gain. They cause damage to the system after intrusion. They may steal, modify or erase data or insert viruses which damages the system.
Grey Hat Hackers
A Grey Hat Hackers is a skilled hacker who sometimes acts legally, sometimes in good will and sometimes not. They are hybrids between white hat and black hat hackers. They usually do not hack for personal gain nor have malicious intentions, but may or may not occasionally commit crimes during the course of their technological exploits.
____
According to a study performed by Shirley (2003), a specialist in psychology of the University of San Francisco, the majority of teenagers who hack and invade computer systems are doing it for fun rather than with the aim of causing harm. Shirley McGuire mentioned that quite often parents cannot understand the motivation of the teenage hackers. She performed an anonymous experiment, questioning more than 4,800 students in the area of San Diego. Her results were presented at the American Psychological Association conference:
- 38% of teenagers were involved in software piracy;
- 18% of all youngsters confessed of entering and using the information stored on other personal computer or website;
- 13% of all the participants mentioned they performed changes in computer systems or computer files.
_____
Types and characteristics of cyber-offenders:
Even though hackers are now generally seen to wear grey to black-coloured hats, there are still distinct differences between subgroups of hackers, and moreover, the stereotypical hacker is far from the only cybercriminal on the block. Some characteristics can be given of cybercrime offenders, although it should be stressed from the start that, similar to prevalence data, little empirical knowledge is available of offenders (with the exception of a few special types, such as cyberstalkers and child pornographers) (Van der Hulst & Neve, 2008). Nevertheless, based on literature study and theory, some tentative insights can be provided.
On average, cybercriminals tend to be male, white, and young, but the variation in offender groups is rising. Cybercriminals are, again generally speaking, also expected to be to some extent technical savvy, have a disregard for the law or a feeling of being above or beyond the law, have an active fantasy life, be a control freak or risk-taking, and have strong – if differing – motivations (Cross, 2008).
But types of cybercriminals differ, depending on their aims, methods, or skills. Hackers are for example characterised according to their skill as ‘gurus’, ‘wizards’, or ‘samurai’ (whitish hats with great skills) or, conversely, as newbies, ‘cluebies’, or ‘script kiddies’ (whitish to blackish hats with no or low expertise) (Wall, 2007). The most extensive and most interesting typology is the ‘hacker circumplex’, in which Rogers (2006) distributes nine hacker types in a circle consisting of four quadrants of different motives:
- revenge (against persons, organisations, countries, or continents);
- financial gain;
- curiosity (knowledge, sensation, intellectual challenge);
- fame (media attention, boasting, popular hero).
As Van der Hulst and Neve (2008) note, however, this model is still a hypothesis needing to be empirically tested. Moreover, some other types of motivations may also play a role, such as ‘for fun’, sexual drive, or political motives. Van der Hulst and Neve (2008), based on a literature review, distinguish between three basic offender types associated with the different motivations:
- young male criminals, who hack for fun, curiosity, or peer respect;
- ideological hackers, who are intelligent and eager to learn, some of whom are obsessive, antisocial, or have a minority complex;
- financially-motivated hackers, from various backgrounds.
The FBI (Icove et al., 1995) has developed a ‘Computer Crime Adversarial Matrix’ – which may be outdated since it is over 25 years old – that distinguishes between ‘group’ and ‘individualist’ (black-hat) hackers. Group hackers function in peer groups, with a distinct (anti-)subculture and maintaining international contacts; they belong to the above type 1 or type 2. Individualist hackers are loners who share expert information with other hackers and keep records; they belong to the above type 2 or type 3. The FBI’s Matrix also comprises of espionage perpetrators from foreign intelligence services, and fraudsters.
Leukfeldt (2010) investigated whether online fraud perpetrators differ from offline fraudsters. He concludes that there are more similarities between the two than would be expected on the basis of the Internet’s opportunity structure; many personal and socio-economic characteristics are the same. However, e-fraudsters do start committing online fraud earlier in their criminal careers, and they have less records for drugs. These differences might be explained by the fact that offline scams, unlike e-fraud, require social skills usually acquired later in life, and perhaps drug addicts who need money fast stick to direct yielding offline scams.
A category that merits special attention are insiders, since a substantial proportion of cybercrime is committed by people within an organisation. Individuals who threaten vital infrastructures (motivated by revenge, financial gain, or espionage) tend to be introverted, computer-dependent, socially isolated, vulnerable to ethical ‘flexibility’, have a sense of entitlement and anger at authority, reduced loyalty to employers, and lack empathy (Shaw et al., 1998). Insider cybercriminals can be distinguished according to their different activities: espionage (generally by ‘spies’ high in the management hierarchy), sabotage (usually motivated by personal revenge), theft (often committed by younger persons lower in the hierarchy), and abuse (minor forms of misuse by employees, which cumulatively cause damage to the company) (Nykodym et al., 2005). It is hypothesized that computer addiction (possibly in the form of Internet Addiction Disorder or Pathological Computer Use) is a risk factor for insider cybercrime (Nykodym et al., 2008).
______
Individual explanations of cyber violence:
A few psychological studies have begun examining the characteristics of individuals who engage in cyber aggression and violence, which include both traditional criminal risk factors (i.e., externalizing traits) and potentially new risk factors (i.e., internalizing traits).
- Low self-control or impulsivity
Gottfredson and Hirschi’s (1990) self-control theory argues that individuals with low self-control will find crime appealing because they are unable to see the consequences of their actions. This theory maps onto the concept of impulsivity in psychology, which is highly correlated with criminal behavior (Krueger, Markon, Patrick, Benning, & Kramer, 2007), and is well established as one of the strongest predictors of both juvenile and adult offending (White et al., 1994).
In the online context, low self-control is often presented as a risk factor either for piracy (i.e., online copyright infringement) offending (Higgins, Wolfe, & Marcum, 2008) or hacking (i.e., illegal access to computer networks) victimization (Bossler & Buruss, 2011; Bossler & Holt, 2010). Indeed, in the context of hacking victimization, Wilsem (2013) concludes, “Low self-control can be expected to go together with risky online behavior” (p. 441). Only a couple of studies have examined whether low self-control has a relationship with cyber aggression and violence. A survey study of nearly 500 undergraduate students found that low self-control predicted online deviance, which included harassing or threatening posts and illegal hacking (Donner, Marcum, Jennings, Higgins, & Banfield, 2014). An additional study of over 25,000 youth in 25 different countries ages 9–16 found associations between online and offline bullying and low self-control, with stronger direct effects on cyberbullying (compared to traditional bullying; Vazsonyi, Machackova, Sevcikova, Smahel, & Cerna, 2012). The small amount of empirical literature available does suggest the relationship between low self-control/impulsivity and violence applies to the cyber world as well, thus may be an important risk factor for cyber aggression and violence.
- Psychopathic and Machiavellian traits
Psychopathic traits (i.e., charming, manipulative, emotionally sallow, callous, deceitful) are highly predictive of criminal and violent activity across a wide range of settings and individuals (Hare, 2003). A handful of studies have begun examining whether these traits are markers for cyber aggressors as well. Although the small collection of empirical evidence is somewhat mixed, the literature supports psychopathic or Machiavellian traits as another potential risk factor for cyber violence.
In one of first studies of personality characteristics of online trolls, for example, Buckels et al. (2014) examined the relationship between trolling and self-reported sadistic traits, psychopathic traits, and Machiavellian traits (i.e., cynical, emotionally detached, manipulative; Abell & Brewer, 2014). Study one collected online data from 418 U.S. residents, of whom 5.6% reported enjoying trolling behavior online. These individuals scored significantly higher on all measures of sadism, psychopathy, and Machiavellianism. A second, larger study collected online data from 188 Canadian college students and an additional 418 U.S. residents. Again, results showed a significant relationship between self-reported enjoyment of trolling and sadism, psychopathy and Machiavellianism. Further analysis demonstrated that sadism, specifically, was uniquely related to trolling behavior (as opposed to other, non-aggressive online activities such as chatting or debating).
In one of the only other studies of trolling behavior, Shachaf and Hara (2010) conducted qualitative interviews over email with a small sample of five Wikipedia trolls (who engage in harmful or threatening cyber aggression on Wikipedia). Consistent with Buckels et al.’s (2014) work, these interviews indicated that trolls were motivated by boredom, attention seeking, and revenge—and also found pleasure from causing damage to the Wikipedia community (potentially indicating sadistic or psychopathic traits). Abell and Brewer (2014) examined how Machiavellian traits influence social networking behavior among men and women (N = 243) using a series of self-report questionnaires. In this study, women (but not men) who were high in Machiavellianism were more likely to engage in relational aggression with a friend via social media.
One specific trait of psychopathy is a lack of empathy (Hare, 2003), which is the inability to experience the emotions of another person or to comprehend the emotions of another person (Jolliffee & Farrington, 2006). A lack of empathy has been examined in the context of cyberbullying in two European studies. In one study involving online surveys of over 2000 students in Germany, cyberbullies reported significantly less empathy for victims than non-bullies (Steffgen, Konig, Pfetsch, & Melzer, 2011). However, Sticca, Ruggieri, Alsaker, and Perren (2013) surveyed 835 junior high school students in Switzerland, following-up six months later. They found that a lack of empathetic concern did not predict cyberbullying over and above traditional bullying, rule breaking, and frequency of online communication.
- Internalizing traits
Externalizing traits such as low self-control, impulsivity, psychopathy, and lack of empathy also are strong risk factors for individuals who engage in traditional (i.e., in person) forms of aggression and violence. However, online aggression is distinct from traditional forms of aggression in that the aggressors are invisible to their victims, and often anonymous. This unique form of violence and aggression may, therefore, attract individuals with a distinct set of internalizing traits such as depression or shyness.
For example, a study of nearly 400 youth in grades 8–10 in Canada, found symptoms of depression and suicidal ideation were predicted by involvement in cyberbullying (Bonanno & Hymel, 2013). Participating as a cyberbully accounted for a small, but significant amount of the variance in depression and accounted for a larger amount of the variance in suicidality. An additional survey in 2007 of nearly 2000 middle school students found that cyberbullies were more likely to experience suicidal ideation and attempt suicide than students who had not been involved in online aggression (Hinduja & Patchin, 2010).
Beyond depression and suicidality, a study of over 400 University students in Turkey examined the relationship between “problematic internet use” and narcissism, shyness, loneliness, aggression, and self-perception (Odaci & Çelik, 2013). The results of this self-report study demonstrate only aggression and shyness were significantly correlated with problematic Internet use. Although the examination of internalizing traits as predictors of those who engage in cyber-aggression is a relatively new area of study, these preliminary findings highlight these traits as potentially important selection criteria.
_
Group and environmental explanations of cyber violence:
In addition to individual-level externalizing and internalizing traits, certain group processes and environmental factors may also facilitate cyber violence. Prior research has generally drawn upon popular criminological theories to account for this.
- Social control and social learning theories
The role of parents and peers is critical in the development and facilitation of traditional forms of aggression and violence (e.g., Akers, 1998). In a recent review of the literature, Ang (2015) found that poor emotional bonds with parents and a lack of parental monitoring related specifically to cyber aggression as well. Holt et al. (2010) argue social learning theory may apply specifically to cyber aggression through the association with delinquent peers. Exposure to violence in the media is also associated with concurrent reports of serious violent behavior (Ybarra et al., 2008).
Hinduja and Patchin (2007) examined 4400 sixth to twelfth grade students, and also found that cyber bullying was related the perceived likelihood of being punished by adults. Additionally, this study found that perceptions of peer behavior (i.e., whether or not one’s peers were cyberbullying as well) were related to cyber aggression. This finding is consistent with a recent survey of 850 middle school students, which found that weak attachments to peers was associated with both traditional and cyber bullying (Burton, Florell, & Wygant, 2012). Another study of relationship cyber aggression in 600 adolescents found that insecure maternal attachments and insecure partner attachments were related to partner-directed cyber aggression (Wright, 2015), again emphasizing the importance of peer and family relationships as selection criteria.
- Routine activities and “digital drift”
Offending via social networking sites is most commonly associated with routine activity or lifestyle theories of crime (Bossler & Holt, 2009; Holt & Bossler, 2009; Leukfeldt, 2014; Moule et al., 2013; Ngo & Paternoster, 2011; Pratt, Holtfreter, & Reisig, 2010; Pyrooz et al., 2015; Reyns, 2013; Reyns, Henson, & Fisher, 2011; Van Wilsem, 2011; Yar, 2005). As first conceptualized by Cohen and Felson (1979), routine activity theory states crime results from the spatial and temporal convergence of motivated offenders and suitable targets in the absence of capable guardianship (i.e., formal or informal social controls). Routine activity theory has intuitive appeal for explaining crime online, not least because connecting to the online world has become so routine, or habitual for society (David-Ferdon & Hertz, 2007; Huesmann, 2007). Still, routine activity theory perhaps has more to say about victimization than offending (Sampson & Lauritsen, 1990). People explore new technologies because of the freedom these technologies bring, but new technologies make people vulnerable to online violence. Williams and Guerra (2007) observe, “The Internet has become a new arena for social interactions, allowing children and youth to say and do things with a certain degree of anonymity and limited oversight by adult monitors” (p. S15). Limited oversight speaks to the absence of capable guardianship online.
Guan and Subrahmanyam (2009) looked into the link of online addiction in youth with the likelihood of being harassed, bullied, and sexually exploited and concluded that those who spend more time on the internet are more likely to be approached by online predators. Overall, the more youth are online, the greater chance there is to become a victim of cyberbullying considering the background, type of contact, and relationships formed. As an extension of this line of inquiry, Goldsmith and Brewer (2015) draw on Matza (1964) to advance the theory of “digital drift,” which accounts for the arbitrary and capricious nature of some cyber violence. Goldsmith and Brewer point to lone wolf terrorism and pedophilia as examples of a new “criminal interaction order” “that is encounter based and that can engage with the Internet as a source as well as facilitator of encounters” that result in criminal outcomes (p. 126). Such a perspective speaks to the “great seduction” (Keen, 2008, p.11) of the Internet and what Katz (1998), p. 53) referred to as “sneaky thrills” of offending.
- Anonymity and conformity
Anonymity may contribute to online aggression and violence beyond a lack of guardianship, due to the “deindividuation” process. People experience reduced inhibition and personal responsibility in situations when they are more anonymous (Zimbardo, 2007). For example, a study of violence in Northern Ireland found a significant relationship between wearing a mask to disguise one’s identity and increased aggression (Silke, 2001). The degree of anonymity on social media, with an associated lack of accountability, encourages unconstrained commenting (Lee, 2006), which in turn may contribute to the aggressive nature of users’ comments (Thelwall & Sud, 2011). New apps, such as ‘Yik Yak’, allow users in the same physical area to post anonymous messages to each other. These anonymous group conversation on Yik Yak have turned so threatening and aggressive on college campuses that many Universities are asking their students to avoid the app altogether (Mahler, 2015).
Another important social process that may take place on social media is conformity, which is changing one’s behavior because of direct or indirect group pressure, either real or imagined (Asch, 1951), as was famously demonstrated by the Stanford prison experiment in the 1970s (Haney, Banks, & Zimbardo, 1978). For example, a study of over 1200 elementary school students that examined bullying found that the strongest influence on behavior came from class context and group norms, as opposed to individual attitudes (Salmivalli & Voeten, 2004). Social media expands the peer networks of adolescents, exposing them to new group norms in an online context. Although this phenomenon has not yet been empirically studied, social media may contribute to cyber violence by expanding peer networks that normalize aggressive or violent online behaviors.
_______
Top 5 countries with maximum number of hackers
China
Unsurprisingly, China the most populous country in the world has the largest number of hackers in the world. Various estimates state that 41% of the world’s cyber-attacks have their origin in China. Rumours also go that, the hacking network in China has national backing.
United States of America
In the second position, the USA accounts for approx. 10% of the world’s attack traffic. One of the many infamous groups from here is Anonymous.
Turkey
Next to the USA is Turkey. It has a share of around 4.7% in global cyber-attack traffic. However recent years show a rapid increase in their activities.
Russia
The recent news of Russia meddling in the US elections have brought public attention to this country. Although only about 4.3% of global attack traffic generates from Russia, still it is capable of a lot more. In fact, they are able to target some of the most secure networks in the world.
Taiwan
In spite of the small size of the nation, Taiwan accents for more than 3.7 per cent of the world’s hacking traffic. Likewise, this small island is known as a hub for hackers.
____
IT Professionals and cybercrimes:
Since Cybercrime is all about computers and Networks (Internet), many types of IT professionals are quite prominently active in the same, which include but are not restricted to:
- Network Engineers
- Cyber Security Software Professionals
- Cyber Forensic Experts
- IT Governance Professionals
- Certified Internet Security Auditors
- Ethical Hackers
_____
Autism and cybercrime:
Having interviewed cyber-dependent criminals, the NCA’s intelligence assessment (2017) identified that perpetrators are likely to be teenage males who are unlikely to be involved in traditional crime and also that autism spectrum disorder appears to be more prevalent amongst cyber-dependent criminals than the general populace—though this remains unproven. No socio-demographic bias has yet been identified amongst cyber-dependent offenders or those on the periphery of criminality.
This apparent relationship between cyber-dependent crime and autism is echoed in a survey of six international law enforcement agencies’ (UK; USA; Australia; New Zealand; Germany; the Netherlands; Denmark) experiences and contact with autistic cybercriminals (Ledingham and Mills 2015), which indicated that some autistic individuals commit cyber-dependent offences. Offences committed included: hacking; creating coding to enable a crime to be committed; creating, deploying or managing a bot or bot-net; and malware (Ledingham and Mills 2015). This was a small-scale study, limiting the generalisability of findings, but it does indicate a presence of autistic offenders within cyber-dependent crime populations, although the link between autism and cyber-dependent crime remains largely speculative as cyber-dependent criminality may be evidenced within a wide range of populations. Further clarification of any relationship between autism and cyber-dependent crime is required before any conclusions can be inferred.
With respect to cyber-dependent crime, some members of both autistic and high autistic-like trait groups will have developed advanced digital skills that are likely to be required to commit cyber-dependent crime. Indeed a specific relationship between ‘autism and the technical mind’ has been previously speculated by Baron-Cohen (2012; see also Wei et al. 2013). Moreover, computer science students and those employed in technology are two of the groups who typically possess higher levels of autistic-like traits (Baron-Cohen et al. 2001; Billington et al. 2007; Ruzich et al. 2015b). These relationships are potentially significant, as cyber-dependent criminal activity requires an advanced level of cyber-related skills (such as proficiency in programming in Java, C/C++, disassemblers, and assembly language and programming knowledge of scripting languages [PHP, Python, Perl, or Shell]; Insights 2018). Thus, there may be an association between autistic-like traits and the potential to develop the advanced digital skills required for cyber-dependent crime.
Cyber-enabled crime is an online variant of traditional crimes (such as fraud) and shares common motivations such as financial gain, whereas the motivations for cyber-dependent crime can be based around a sense of challenge in hacking into a system or enhanced reputation and credibility within hacker communities (NCA 2017). This may be pertinent for the relationship between cyber-dependent crime specifically and autism or autistic-like traits, since cyber-dependent criminals typically have not engaged in traditional crime (NCA 2017) and autism has been associated with generally being law abiding and low rates of criminality (Blackmore et al. 2017; Ghaziuddin et al. 1991; Heeramun et al. 2017; Howlin 2007; Murrie et al. 2002; Wing 1981; Woodbury-Smith et al. 2005a, 2006). In addition, several studies have suggested that autistic internet-users can demonstrate a preference for mediating social processes online, such as preferring to use social media over face-to-face interaction to share interests (Brosnan and Gavin 2015; Gillespie-Lynch et al. 2014; van der Aa et al. 2016). This may be significant, as it has been suggested that social relationships developed online are key to progressing into cyber-dependent crime, with forum interaction and reputation development being key drivers of cyber-dependent criminality (NCA 2017).
A 2019 study found increased risk of committing cyber-dependent crime was associated with higher autistic-like traits. However a diagnosis of autism was associated with a decreased risk of committing cyber-dependent crime. Around 40% of the association between autistic-like traits and cyber-dependent crime was mediated by advanced digital skills.
______
______
Cybercrime victims’ profiles, typology and traits:
- Are victims of cybercrime a specific group of people?
- Are there reasons why these individuals are becoming victims of cybercrime?
Establishing whether victims of cybercrime are a specific group of people will help to target preventative methods and resources. Through a victim information database researchers can investigate the characteristics of the victims to develop our understanding of who they are and determine if specific groups of people are more vulnerable to cyber-attacks and the reasons why. The first step is to identify and explore the demographics (i.e. age, gender, location), socio-demographics (i.e. education, employment, income), attitudes (i.e. to cybercrime, risk, self-protection) and technological characteristics (i.e. technology skill set, technology used, day to day technology brands, internet) of the victims to build a complete profile.
Following this information the common characteristics of the victims can be identified. For example, it may become apparent that the majority of victims were of the age 25 to 30, if this was the case preventative methods could be targeted to this age group such as educating them on how to stay safe online. Or, it may be the case that the majority of victims were found to be in full time employment and earning over £50,000 or were start-up companies with less than 50 employees. In each case preventative methods need to be, in part, targeted to the victims found most at risk. With improvements to data collection statistical analysis can be performed to establish which characteristics of cybercrime victims are statistically significant. Researching the reasons why these characteristics have left people vulnerable to cyber-attacks will aid the development of preventative methods and evidence base on cybercrime.
_
Typology of Victims:
There has been some speculation about the typology of fraud victims. Much of the work has focused on personal fraud, in general. For example, Titus and Gover believe that victims of fraud are more likely to be cooperative, greedy, gullible/uncritical, careless, susceptible to flattery, easily intimidated, risk takers, generous, hold respect for authority, and are good citizens. Fischer et al. found in their survey research that scam victims or near scam victims were more affected by the high values offered in scams and displayed a high degree of trust in the scammers. They also found some support for the notion that some kind of enduring personality trait might increase susceptibility to persuasion. Similarly, a susceptibility to persuasion scale has been developed with the intention to predict likelihood of becoming scammed. This scale includes the following items: premeditation, consistency, sensation seeking, self-control, social influence, similarity, risk preferences, attitudes toward advertising, need for cognition, and uniqueness. A 2017 study found 5 personality traits of cybercrime victims i.e., extraversion, agreeableness, conscientiousness, emotional stability, and openness to experience.
Millennials are the most impacted group of people by cybercrime. This is potentially because they are the most technologically savvy group. In any case, around 53 percent of millennials experienced cybercrime in 2015.
___
Cybercrime Victim Apprehensions:
The victims of cybercrime can feel that nowhere will ever be safe and that they could always be confronted with the perpetrator once again. They also have a need for redress. This emerged from research into the consequences of online crime and the needs of its victims. The research was carried out by the NSCR and commissioned by the WODC. Online offences differ from ‘conventional’ offences in the scale and duration of their consequences, and through their relationship with offline criminality.
- Victims fear the consequences long after the offence
Images can be posted online, for example, during sexting, threatening or stalking. Such images can be widely disseminated at an enormous rate, becoming visible to a practically unlimited group of people. This spread can also continue indefinitely. Nude images and other materials can move around online and then suddenly, and unpredictably, turn up again. Victims can be terrified that this will happen long after the original offence, even if the perpetrator has been successfully convicted. When offences such as stalking, threats and intimidation are carried out online, their consequences are aggravated. Sometimes these offences are first committed in the physical world, the perpetrator then continuing them through the internet. This gives victims the idea that nowhere is safe for them.
- Financial damage and feelings of shame
The financial losses incurred by the victims of cybercrime can be anything from a few hundred dollars to over two hundred thousand dollars. The psychological damage caused by these losses can be considerable, especially in cases in which the perpetrator first began a romantic relation with the victim online and then went on to blackmail them. Besides the financial consequences, the victim can experience feelings of shame and guilt, as well as grief over the loss of what they had taken to be a genuine love relationship.
Another possible side effect is large-scale ‘victim blaming’ in which the social environment and even complete strangers can harass, insult, or blame the victim. The victim may then feel that their only option is to withdraw from online society altogether. These negative consequences are exacerbated if it turns out that the police are not actively trying to find the perpetrator, or if officers at the police station make disparaging or critical remarks.
- Victims and experts are concerned about police facilities and capacity
According to both victims and experts, the police are inadequately equipped to fight online crime. They claim that police officers do not receive adequate training and consider this type of criminality is too complex and widespread to tackle. They are also concerned about inadequate police capacity. Victims have cited cases of frustration arising from the fact that they were not even given the opportunity to make an official report.
Identifying victims’ needs:
Victims of online fraud have a need for redress: the NSCR study showed that they want to see the perpetrator punished and they want financial compensation. They have a need for clear information on what can be expected from the police and the courts. And they have a need for remediation; for instance, having images removed from the internet as quickly as possible.
____
The 2017 Norton Cyber Security Insights Report throws light on victim traits:
When it comes to cyber security, consumers are overconfident in their security prowess, leaving them vulnerable and enabling cybercriminals to continue attacks.
- 978 million people in 20 countries were affected by cybercrime in 2017.
The most common cybercrimes experienced by consumers or someone they know include:
-Having a device infected by a virus or other security threat (53%)
-Experiencing debit or credit card fraud (38%)
-Having an account password compromised (34%)
-Encountering unauthorized access to or hacking of an email or social media account (34%)
-Making a purchase online that turned out to be a scam (33%)
-Clicking on a fraudulent email or providing sensitive (personal/financial) information in response to a fraudulent email (32%)
As a result, consumers who were victims of cybercrime globally lost $172 billion – an average of $142 per victim – and nearly 24 hours globally (or almost three full work days) dealing with the aftermath.
Cyber security concerns do not always seem to translate to good behaviors as many consumers put themselves at risk in their day-to-day lives. This leads us to a startling cybercrime confession: those who emphasize the importance of online security, generally contradict themselves through their actions, and as a result, are more likely to fall victim to cybercrime.
Cybercrime victims share three common traits:
- Overconfident in Cybersecurity Prowess: Consumers who’ve fallen victim to cybercrime, emphasize the importance of online security more than non-victims, yet they’re more likely to contradict their efforts through simple missteps. While 44% of consumers have personally experienced cybercrime, 39% of cybercrime victims globally report gaining trust in their ability to hold and protect their personal information and data and 33% believe they’re at a low risk of becoming a cybercrime victim.
- Favor Multiple Devices: Consumers who adopt the newest technologies and own the most devices are also more likely to be victims of cybercrime. More than one third (37%) own a gaming console and smart device, compared to 28% of non-victims. They’re also almost twice as likely to own a connected home device than non-victims.
- Dismiss the Basics: They practice new security techniques such as fingerprint ID (44%), facial recognition (13%), pattern matching (22%), personal VPN (16%), voice ID (10%) and two-factor authentication (13%). Yet, 20% of cybercrime victims globally use the same password across all online accounts and 58% shared at least one device or account password with others. By comparison, only 17% of non-cybercrime victims use the same password across all online accounts and 37% share their passwords with others.
______
How a personality trait puts you at risk for cybercrime, a 2018 study:
Impulse online shopping, downloading music and compulsive email use are all signs of a certain personality trait that make you a target for malware attacks. New research examines the behaviors — both obvious and subtle — that lead someone to fall victim to cybercrime involving Trojans, viruses, and malware.
“People who show signs of low self-control are the ones we found more susceptible to malware attacks,” said Tomas Holt, professor of criminal justice and lead author of the research. “An individual’s characteristics are critical in studying how cybercrime perseveres, particularly the person’s impulsiveness and the activities that they engage in while online that have the greatest impact on their risk.”
Low self-control, Holt explained, comes in many forms. This type of person shows signs of short-sightedness, negligence, physical versus verbal behavior and an inability to delay gratification.
“Self-control is an idea that’s been looked at heavily in criminology in terms of its connection to committing crimes,” Holt said. “But we find a correlation between low self-control and victimization; people with this trait put themselves in situations where they are near others who are motivated to break the law.”
The research, published in Social Science Computer Review, assessed the self-control of nearly 6,000 survey participants, as well as their computers’ behavior that could indicate malware and infection. To measure victimization, Holt and his team asked participants a series of questions about how they might react in certain situations. For computer behavior, they asked about their computer having slower processing, crashing, unexpected pop-ups and the homepage changing on their web browser.
“The internet has omnipresent risks,” Holt said. “In an online space, there is constant opportunity for people with low self-control to get what they want, whether that is pirated movies or deals on consumer goods.”
As Holt explained, hackers and cybercriminals know that people with low self-control are the ones who will be scouring the internet for what they want — or think they want — which is how they know what sites, files or methods to attack.
Understanding the psychological side of self-control and the types of people whose computers become infected with malware — and who likely spread it to others — is critical in fighting cybercrime, Holt said. What people do online matters, and the behavioral factors at play are entirely related to risks.
Computer scientists, Holt said, approach malware prevention and education from a technical standpoint; they look for new software solutions to block infections or messaging about the infections themselves. This is important, but it is also essential to address the psychological side of messaging to those with low self-control and impulsive behaviors.
“There are human aspects of cybercrime that we don’t touch because we focus on the technical side to fix it,” he said. “But if we can understand the human side, we might find solutions that are more effective for policy and intervention.”
_____
_____
Cybercrime and Teens:
Today’s teens form part of Gen Z, young people who were born and raised in the new technology era, who cannot envisage an offline world with no access to the Internet or social media. From an early age, they have juggled with computers, tablets and smartphones, accessories they use in their daily lives. There is evidence to show that cybercrime is increasingly attracting and engaging with the teen population. A study by the National Crime Agency (NCA) in the UK reveals that 61% of computer hackers identified in that country begin their activity before the age of 16. In 2015, the Australian Bureau of Statistics and Crime Investigation reported that cyber-fraud crimes committed by under-18s had risen by 26% in the previous two years and by 84% in the previous three. In a recent survey conducted by an online security firm, roughly 1 out of every 6 adolescents in the US and 1 out of every 4 in the UK disclosed that they had attempted some kind of Internet “hacking”.
Today, fewer skills than ever are required to commit a cybercrime, as you do not need to be a computer or programming expert to know how to hack. A variety of low-cost hackers’ tools are available for users online. There are hundreds of tutorials and digital manuals that explain step by step how to access computers or steal passwords and, all of the above, in environments, social media and websites linked to teen-oriented content. Today, you do not have to live or be brought up in the criminal underworld or in a poor neighborhood to witness or take part in the cybercrime business. Typical adolescent hacker is extremely intelligent young person, probably slightly vulnerable, socially awkward and withdrawn, and very keen in understanding how computers work.
_
What circumstances or determining factors drive some young people to get involved in criminal activities on the Internet?
Criminological theoretical frameworks view hacking as a criminal act, exploring the ‘how’, ‘who’ and ‘why’ of cybercrime as is the case with other forms of criminal behaviour. Seminal theories such as Routine Activity Theory, General Theory of Crime, Theory of Reasoned Action, General Deterrence Theory and Neutralization provide a series of critical insights into explaining why adolescents might engage in hacking behaviour.
Routine Activity Theory (RAT) explains the three necessary conditions for crime to occur in everyday life: a capable and willing offender, a suitable target perceived by the offender as vulnerable/attractive, and the absence of guardians. These three factors converge in time and space explaining criminal behaviour. Additionally, when considering Routine Activity Theory environmental aspects can be explored in terms of a geographical approach to criminality. Considering cyberspace as an environment and the web as a domain, may have explanatory value, notably NATO now officially recognises cyberspace a warfare domain.
General Theory of Crime postulates that social bonds and self-control regulates engagement in anti-social behaviour and criminality, therefore the ability to forge antisocial bonds along with a lack of regulation in cyberspace may influence youth engagement in acts of online criminality and deviance.
The Theory of Reasoned Action postulates behavioural intentions as precursors to acts and the expectation of behaviours leading to specific outcomes; however, it has been established that behaviour can alter in cyber contexts in terms of escalation and amplification.
General Deterrence Theory states that individuals can be dissuaded from committing antisocial acts through the use of countermeasures, which include disincentives and sanctions. Combined, these latter two theories have emerged in research into hacking where preliminary analysis of action and mapping of potential outcomes as well as perceived norms and the likelihood of punishment were critical in the offender’s decision to engage in the anti-social acts.
Neutralisation argues that often offenders will deny the status of their victim as a ‘worthy’ victim, that is, not recognising that they have been harmed or wronged. Alternatively, the offender may convince themselves that the victim ‘deserved’ what happened to them. This process of neutralisation may be strengthened in the mind of the offender given the anonymity afforded by cyberspace.
_
Let us look at a traditional criminology theory, A General Theory of Crime, by Gottfredson and Hirschi. This theory upholds that people who are more likely to commit a crime are those with low self-control, in other words, individuals who cannot control their impulses or alter their emotions or thoughts to curb undesirable behaviors. Having low self-control means that the person is unable to delay their rewards, that they have no patience and act impulsively to get whatever they want. On most occasions, this means getting involved in criminal conduct. This low self-control is typical in teenagers who, at their age, do not have the necessary brain structures in place to generate self-control; they do not have the emotional maturity that enables them to control their impulses, withstand peer pressure and calculate the risks of any dangerous decisions.
This is echoed in countless studies that evidence how young people who score worse on self-control scales are, to a greater extent, usually related not only to criminal behaviors but also to cybercrime. Teenagers are at a developmental and identity building stage, for which they use different strategies, including peer comparison. This comparison has a materialistic bias, where the possession and purchase of material items and belongings are used as a measure of happiness, success and satisfaction in life. The pressure for possessions, usually items of value, obviously represents an economic cost, which is not within everyone’s reach through “legal” channels. If this is coupled with low self-control, which is usually present at these ages, the outcome is that some teenagers try and obtain these possessions via unlawful means. One example of this may be the pressure that some young people feel to own the latest model of Smartphone, an item which nowadays not only represents a mere technological device, but it is also an “essential” element for interaction, communication and everyday relationships from a young person’s perspective.
This peer comparison leads us to another theory that also attempts to explain criminal behavior in adolescents, Akers’ Social Learning Theory, according to which criminal behavior is learnt like any other. A teenager, through the identity building we mentioned earlier, feels more influenced by their peers than by adults, using as a benchmark and imitating the behavior they see in their equals. If their group of equals carries out, justifies and reinforces criminal conduct, the adolescent will be more likely to imitate and develop these types of behaviors, especially if the results of these acts mean more benefits than punishment.
This peer pressure is also extremely powerful in adolescence, from which it is very difficult for someone in need of the approval of their companions to escape. Many criminal phenomena, such as gangs, mobs or juvenile organizations, can be explained from this perspective.
On the top of it, internet provides anonymity, encryption and low risk.
_
What can go wrong for teen cybercriminal?
A permanent criminal record could affect education and future career prospects, as well as potential future overseas travel. Consequences vary from country to country, but young people who get involved in cybercrime could face the following:
- A visit and a warning from the police, as well as a penalty fine
- Arrest and a prison sentence for serious offences
- Their computers being seized and/or being prevented from accessing the internet
__
Advice for teachers:
- Talk – If you are worried about one of your students, speak to them about what they are doing, try and point out the difference between harmless exploration/curiosity online and illegal online activity. Tell them about the consequences of cybercrime for the offender and for the victim. Try mentoring them and showing them positive ways to use their skills. If you are very concerned, you should consider alerting the students’ parents.
- Deter- The best way to help to deter tech-savvy and talented students from getting involved in entry level cybercrimes is to offer them constructive and positive alternatives.
- Report – If you believe that your school is the victim of a cybercrime attack or that a student is engaging in cybercriminal activities, you should report it to the school and to the local police.
_
Warning signs for parents:
Some of the indicators that your child may be at risk of becoming involved in cybercrime include:
- They spend most of their time online and are often secretive about their activities;
- They are excessively interested in coding;
- They seem to gain an additional income from their online activities, but they do not talk about how they do it;
- Your home network’s monthly data allowance is often met;
- They socialize more in the online world than offline
Many children will have an active interest in coding and programming, spend a lot of time online and have independent learning materials. These are all signs of a healthy and positive interest in computing and the development of those extremely valuable skills should be encouraged – but in a lawful way.
_
Effects of cybercrime on teen victim:
- Personal
Relationship breaks down
Frustration
- Social/ cultural
Break social harmony
Isolated from the society
Grow different subculture
- Economical
Financial loss
Loss of time
Reduce productivity
_____
_____
Cybercrime on social media:
The rise of social networking has created an atmosphere for increased cybercrime:
In 2013, the stock market lost more than $130 billion in value thanks to one event. No, it wasn’t a global crisis. A war hadn’t broken out. And, there were no changes to fiscal or monetary policies. Instead, the dip was attributed to a single source: social media. Hackers gained control of the Twitter account of the Associated Press and posted an erroneous ”news story” that a bomb had been detonated in the White House in Washington, D.C. The fake story caused the Dow to drop 150 points, roughly equivalent to $136 billion, though it eventually rebounded. This is one example of how social networks are used for mischievous purposes, and there are plenty of others. Criminals on fake Instagram accounts posted photos of supposed lottery winners, offering to share their bounty with anyone who followed their account. Once the account grew to a sizable following, the account owners sold the account and all of its followers to someone else. On Twitter, cybercriminals often post malicious URLs that look legitimate in hopes of getting users to click – and subsequently infect their devices. The growing use of social media, now estimated to be more than three billion users worldwide, provides fertile ground for hackers looking to commit cybercrime. Cybercrime is an easy way to target people because it requires only a computer, an internet connection, and criminal intent. The evidence of how simple it is to commit cybercrimes is in the number of victims estimated to have been targeted in 2017: nearly one billion people!
_
From the available evidence it is clear there are some striking trends in the use of social media platforms in crime:
- Social media-enabled crimes are generating global revenues of at least $3.25bn for the global cybercrime economy annually
- Crimes involving social media grew more than 300-fold between 2015-2017 in the US, while UK police data shows social media-enabled crime quadrupled between 2013 and 2018
- Over 1.3 billion social media users have had their data compromised within the last five years and between 45-50% of the illicit trading of data from 2017 to 2018 could be associated with breaches of social media platforms, like LinkedIn and Facebook
- Social media platforms contain up to 20% more methods by which malware can be delivered to users – e.g. through updates or shares, add-ons, plug-ins etc. – than comparable sources, such as ecommerce, media or culture-orientated websites
- Around 30-40% of social media infections come from infected ads
- Around 30-40% of the social media platforms had accounts offering some form of hacking service
- Offers for botnet and booter hires are found on Facebook, Instagram, Twitter and several other sites. Prices were fairly stable, with an average cost of around $10 for a month or $25 for a lifetime rental
In addition to ‘direct’ revenue, cybercriminals have many other ways to use social media for revenue generation, such as malware and hacking services, intellectual copyright theft involving fake brands and illegal drug sales (such as cocaine, MDMA and heroin), to name a few. Revenues from these activities have not been included in the above estimate since available data is not robust enough to make any kind of reliable inferences. It is, however, safe to assume that the total level of criminal revenues from social media is likely to be much higher.
FBI data has suggested a 300-fold rise in reports of crimes involving social media between 2015-2017. This striking increase is no doubt partly explained by the greater likelihood of victims reporting such crime or law enforcement categorising it in this way. Nonetheless, significant rises are corroborated in other, more localised, police data, with some forces reporting that social media-enabled crime quadrupled between 2013-2018.
_
Why social media platforms are so desired by cyber criminals?
Given the rapid pace of growth and the near ubiquity of social media cybercrime on the Internet, the inevitable question becomes: Why have cyber criminals chosen to focus on social media platforms like Facebook, Twitter, Instagram, and YouTube? One easy answer is that these sites make it very easy to share and pass on just about anything – and that includes malware. In fact, the security researchers found that social media platforms, on average, have 20 percent more methods to scam and rip off consumers than other websites. These methods include adverts, sharing buttons and plug-ins. Plus, the fact that most people have hundreds, if not thousands, of connections on these social media platforms make it very convenient to distribute malware to a wide audience with surprisingly few negative consequences.
_
Cybercrime can be associated with three key features of social media that cybercriminals are learning to exploit:
- Amplification
In a world where two-thirds of American adults get their news from social media, social platforms now provide the most obvious available springboard for disseminating social engineering strategies. Indeed, by placing almost anything on social media platforms – whether that be commercial products, fake news or political messages – the reach is amplified to produce what is often an exponential expansion of an individuals’ networks of influence.
- Persuasion
‘Talking louder’ may reach more ears, but it doesn’t guarantee the message will get across. By its very nature, social media is a domain where popularity is a highly valued currency. Marketers now routinely distinguish between two versions of amplification – ‘reach’ (the number of unique individuals who view a page) and ‘impressions’ (the total number of times content is displayed to people). But social media campaigns are also concerned with ‘engagement’ – the extent to which individuals respond to content. For example, by liking, commenting or posting further content. Cybercriminals have learned these lessons and are becoming far more accomplished at building upon the amplificatory power of social media to develop ways of engaging their victims – that is, to catch their attention and make them more malleable to exploitation. In fact, they appear to be much better than marketers at engagement given that they are so often successful at transforming mere engagement into persuasion. For example, by persuading victims to not only look at ‘interesting’ apps but to follow them or download content.
Social media users appear to be highly susceptible to persuasion, with recent psychological research suggesting that habitual users of social media platforms like Facebook are up to 40% more likely to click on links that lead to phishing or spam-based infections than infrequent or nonusers. Regular users are also more likely to respond to friend-based attacks (i.e. to click on links in messages from ‘friends’) compared to infrequent visitors to social media sites or non-users.
Persuasion is clearly more profitable for cybercriminals than engagement, in that it can result in directing behaviour or opinion beyond the immediate confines of a platform — in everything from changing voting intentions, or agreeing to act as a money mule.
- Contagion
The phrase ‘gone viral’ is now a common term of reference when discussing an idea or trend that suddenly acquired huge popularity. However, its origins within cybercriminality are perhaps not as well appreciated as they should be. The computer virus is the archetypical example of how content can spread extremely rapidly, often exponentially, through a given medium. It should be no surprise then that contemporary platform-focused cybercriminals are just as aware as marketers that once a certain tipping point in the cycle of amplification and persuasion is reached, they will be able to reap significantly more benefits from an illicit endeavour.
_
Various Types and Techniques of Cybercrime on Social Media:
- Reconnaissance:
Reconnaissance is an attack precursor that, when conducted passively on social media platforms, is difficult to detect. When individuals overshare personal and private information on social media networks, it can be collated and analyzed to allow a profile of their behavior to be compiled. After gathering information about locations, hobbies, and relationships, a threat actor can begin to piece together a potential victim’s life and use this to craft convincing lures, such as malicious links sent from a profile impersonating someone they know, as well as gain knowledge that may allow them to authenticate to other services such as email or banking websites. For example, how many people use a child or pet’s name in their passwords or password reset questions? How many use their year of birth? These seemingly innocuous details when shared alone aren’t that valuable, but when combined into a full profile, can provide the keys to unlock further parts of their digital life. Knowing the value that these tidbits of personal information have to threat actors, shrewd social media users limit the amount of personal data they publicly share to reduce its intelligence value to potential attackers.
- Fake Profiles:
Using a fake social media profile, cybercriminals can mimic a legitimate profile and carry out attacks both on a large scale (e.g. fake public figure profiles used to distribute mass-malware or phishing campaigns to millions of victims), and a smaller ‘targeted’ scale. This attack is often preempted with a reconnaissance phase. These attacks can also be conducted against organizations by using fake profiles that mimic key individuals within that target organization.
- Social Engineering:
Social engineering attacks usually involve some type of psychological manipulation of unsuspecting users or employees into sharing confidential or sensitive data. Commonly, social engineering attacks occur via email or other communication that invokes urgency, fear, or similar emotions in the target, prompting the target to reveal sensitive information, click a malicious link, or open a malicious file. Attacks have been increasingly successful because the attackers are creating more legitimate looking emails and with the prevalence of social media, an attacker can look up everything they need to know about a person and their interests. Armed with this information gleaned from social media, they can craft an email tailored to that person, and email them directly, which increases the chances of that person clicking.
- Fake News:
Although not a cybercrime, fake news has been a hot topic in the last few years. Troll Farms attempt to subvert and influence public perceptions using social media platforms. The 2016 U.S. presidential elections is the most high profile target of this tactic. Kathleen Hall Jamieson, a professor of communications at the University of Pennsylvania notes in her book “Cyberwar: How Russian Hackers and Trolls Helped Elect a President—What We Don’t, Can’t, and Do Know,” that Russian trolls created social-media posts with the intent of winning support for Trump from churchgoers and military families. Russian trolls pretended to have the same religious convictions as targeted users. The U.S. Justice Department, in connection with the Mueller probe, released an indictment of thirteen Russians working at the Internet Research Agency, a troll farm in St. Petersburg. The operatives were described as working day and night waging “information warfare against the United States of America.”
- Malicious Content:
Typically, malicious links are used to lure a victim into clicking through to a payload that is hosted on third-party sites rather than the malicious content being directly available from the social media platform. One-click exploits such as those used for account takeover could easily be distributed via social media and, when clicked, could exploit the victim.
- Profile Hacking
Profile hacking happens when, as a user, you are not able to log in to your account. Someone has complete control of your account and has changed all the credentials. Facebook is the most hacked social networking site and it generally happens because of the following reasons:
- Not logging out from the account
- Sharing passwords or having passwords that are easily predicted
- Hacking the email with which you login to your Facebook account
- Logging in through Facebook options for apps
- Photo Morphing
Photo morphing is a special effect that allows a person to morph or change one image or shape into another without any difficulty. Up to 2017, there are roughly around 3.2 Billion images shared every day. It is easy for a hacker to use your images, morph it and then use it for porn sites or blackmailing for financial/sexual gains. You can’t stop anyone from morphing. If your images are publicly available, people can easily access them and make use of them to morph. Every popular male and female celebrity are probably photo-shopped and used by most porn sites to satisfy sexual fantasies. You never know, when someone take your photographs and use them.
- Offer and Shopping Scams
You would often come across messages, post which would say ‘Click on the link to claim the offer’ or ‘spin the wheel to win.’ These offers would generally ask you to forward the message to another 20 people once you have registered in order to get the code or coupon. You won’t get coupons but the host would get your personal information.
- Romance and Dating Scams
There are people out there who would connect to you on social media, interact with you, and persuade you to move to a different form of communication through various excuses. Once they realize that you are falling for them, they would send you small gifts to show you that it’s same on either side. After a point the romantic period would start declining and they would start asking for monetary help in the form of recharge, booking flight tickets to meet and the list only grows. There are also extreme cases where a guy promises to marry the girl and before the marriage runs away with all her money. It is basically a trick/scam which would begin with romantic intensions to build goodwill and later commit fraud. The other form of romance scam is where the person who you fall in love with will ask you to strip naked in front of cam. He is more likely to chat with you on skype and you might be so much in love with the person opposite that you wouldn’t mind doing him/her a favor. This is the last time he/ she would chat with you and then you will start receiving blackmail calls. Many people try to take an offline scam to online where they record videos of girls in compromising positions for porn sites.
The romance scam is of particular concern given the numbers of victims reported worldwide. The online dating romance scam is an Advance Fee Fraud, typically conducted by international criminal groups via online dating sites and social networking sites. Criminals pretend to initiate a relationship with the intention to defraud their victims of large sums of money. Scammers create fake profiles on dating sites and social networking sites with stolen photographs (e.g., attractive models, army officers) and a made-up identity. They develop an online relationship with the victim off the site, “grooming” the victim (developing a hyper-personal relationship with the victim) until they feel that the victim is ready to part with their money. This scam has been found to cause a “double hit”–a financial loss and the loss of a relationship. Whitty and Buchanan found that for some victims the loss of the relationship was more upsetting than their financial losses, with some victims describing their loss as the equivalent of experiencing a death of a loved one.
- Link Baiting
Link bait happens when the content of your website or pages gets linked to other sites because they want to and not because they have asked you. A few instances where link bait has been showcased are-
- Your photo just got leaked on internet, check here:
- Look what people are talking about you:
- This video of yours is going viral. To know more click here:
When clicking on any of these links, there are chances where you are likely to send the same message to the people from your profile. This link would be sent from your name and would make people think that you are the one doing it.
- Information Theft
Informational theft occurs when an imposter identifies key pieces of personally identifiable information like social security, driving license number in order to impersonate someone else. Many people tend to store passwords or bank details on their email. Many people try to have very private conversation on Facebook or Instagram messengers. Businesswomen are also more likely to be at the risk of information theft especially with respect to her organization. Women bloggers these days are faced by plagiarism of various types. When they try to open their business page on Facebook for the first time, there are chances that their competitors would already have promoted bad things to bring down their reputation.
- Cyber Bullying
Posting any kind of humiliating content on the social media or sending vulgar messages online, or threatening to commit any act of violence, or stalking by means of calls, messages or threatening of child pornography is called as cyberbullying.
_
Worryingly for businesses, research shows that employees can spend over three hours per working week browsing social media sites. The same research showed up to 77% of employees say they use social media in the workplace, regardless of whether there are policies in place for how this should be used. Business itself is equally implicated in the growing dependence upon social media platforms. It has been estimated that circa 73% of businesses use a Facebook account for work purposes, 64% use LinkedIn and 56% use Twitter.
Social media has been a thorn in the side of enterprise security for some time now. Up to 1 in 5 businesses have been infected with malware originating from social media and 1 in 8 have experienced a security breach as a result of a social media-directed cyberattack. While in the early days, companies tried to ban its use, social media has become such a powerful tool for enterprise – particularly for marketing and HR – that preventing its use is simply not practical.
Social media is a huge blindspot in enterprise defences. It is enabling rapid infection across huge user bases, as well as providing easy access to would-be hackers to get the tools and services they need to launch attacks. Quite frankly, it’s worrying. This backdoor access to enterprise systems is putting customer data and business IP at risk on a daily basis. And, at the moment, enterprises and individuals are simply not geared up to deal with it.
_
Social media-enabled attacks against businesses and enterprises are as follows:
- Social media platforms are being used as a trojan horse by hackers to enter the enterprise. Cybercriminals can use simple hacks to reach millions of users, globally, with very little effort on their part: social media is in effect a global distribution center for malware. One in five organisations have now been infected with malware distributed via social media. Research found that up to 40% of malware infections identified were connected to malvertising. A further 30% came from malicious plug-ins and apps. Employees casually clicking on malicious content spread by cybercriminals are unwittingly acting as trojan horses, giving hackers backdoor access to high value assets.
- Social media is enabling the spread of cryptomining malware. Four of the top five global websites hosting cryptomining code are social media platforms. Something as innocuous as clicking on a YouTube advert can result in cryptomining malware installing onto devices and hijacking them to mine cryptocurrency, increasing power consumption, and potentially using cryptojacking payloads for even more nefarious purposes in the future. The brilliance of this – from a hackers’ perspective – is that a lot of victims won’t even know they have been hit, meaning that hackers can go undetected for a long time. But the increased performance strain on the CPU or GPU will accelerate the deterioration of enterprise equipment and drain IT resources, causing significant rising costs in relation to computing power.
- Social media is making it even easier for would-be attackers to get the tools and expertise they need to launch their assaults. There is widespread availability of hacking services, hacking tutorials and the tools needed to aid hacking efforts, like exploits and botnet hire. The boundary between social platforms and Dark Web equivalents is becoming blurred, with tools and services freely available, or acting as an entry point for more extensive shopping facilities on the Dark Web.
Ultimately, hackers know your weak spot – your employees – and they know how to manipulate them through trusted connections. Cybercriminals know that they likely won’t get caught. It’s a numbers game. And social media puts the odds of finding someone who will click on their malware firmly in cybercriminals’ favour. Only with a thorough understanding of the scope of the problem and deploying advanced capabilities, including containment, to defend ourselves can we start to tip the balance. If we carry on as we are, then we are just sitting ducks.
______
______
Cybercrime in banking sector:
Why are banks such a lucrative target for cybercrime?
The answer is simple, cyber criminals go where the money is, and banks have more money than most other organisations. Banks are being targeted over and over again because all the reserves in the form of cash are held with the banks. The software used for detecting frauds in most cases is either outdated or very time consuming. And the number of cases solved by the cyber cell has remained consistently low.
Almost 80 per cent of cases in cybercrime division are related to revealing ATM passwords, OTPs and details of bank account, Chennai police commissioner AK Viswanathan said recently. “Fraudsters take advantage of our fear or desire to con us into falling prey. We are either scared that our bank account will be blocked or we want a loan approval without any verification,” he said. The department is in need of a technology to identify and block fraudsters from conning people. “In spite of several warnings from bank and police, still hundreds of people come to cybercrime wing to lodge complaint. While we might think people with no proper information are falling prey to banking frauds, it is actually well-educated and people who know about the situation who fall victims to such fraudsters,” he said.
_
Banks remain the favorite target of skilled cybercriminals. Cybercrime imposes a heavy cost on financial institutions as they struggle to combat fraud and outright theft. One report says that banks spend three times as much on cybersecurity as non-financial institutions, and there is agreement among bank regulators around the work that cybercrime poses a “systematic” risk to financial stability. To understand why financial cybercrime is such a problem, we need to look at three countries in particular.
The combination of massive budgets, access to talent, and protection from law enforcement make nation states the most dangerous source of cybercrime. The three countries—Russia, North Korea, and Iran—are the most active in hacking financial institutions. China remains the most active in espionage. Iran’s goals are coercive effect, as evidenced by the Iranian distributed denial-of-service (DDoS) attack on leading US banks. For cybercrime, the two most important states are Russia and North Korea. They hack banks to make money. A former NSA Deputy Director said publicly that “nation states are robbing banks,” and they’re doing it with computers. He was referring to the 2015 to 2016 cybercrime campaign that targeted dozens of banks in the SWIFT network.
As major international financial institutions invest in defense, better fraud prevention, and transaction authentication, the most sophisticated nation-states and organized crime groups have begun targeting the “seams” between well-defended networks, exploiting weak points in the global financial network to pull off massive heists. The North Korean campaign to steal money through the SWIFT network is a prime example. Recognizing the difficulty of pulling off large-scale thefts from a single major western bank, the RGB targeted smaller, less sophisticated banks in developing countries like Bangladesh, Vietnam, and Ecuador. After compromising these banks’ systems, they then used the victim banks’ credentials to send what looked like legitimate SWIFT fund transfer requests to larger banks in other countries. These requests at first appeared legitimate to the receiving banks, since they were sent from legitimate partner banks through the established channels, so in some cases the money was transferred.
Russia leads overall in cybercrime, reflecting the skill of its hacker community and its disdain for western law enforcement. The complex and close relationship between the Russian state and Russian organized crime means that Russia provides a sanctuary for the most advanced cybercriminals, whose attention focuses on the financial sector. The best cybercriminals in the world live in Russia, and, as long as they do not travel to countries where they could be arrested, they are largely immune from prosecution. For example, one of the cybercriminals who hacked Yahoo at the behest of Russian intelligence services, compromising millions of accounts and transferred the PII to the Russian government, also used the stolen data for spam and credit card fraud for personal benefit.
_
Major Cybersecurity Threats in Banking Sector:
- Unencrypted Data – The majority of data breaches happen due to improper encryption and stolen data immediately accessible after being stolen.
- New automation technology without Security – CCTV cameras, connected devices, and toys can all be turned into bots if they are unprotected. It is important to understand that more than just computer, hard drive data can be used for cybercrime.
- Unprotected Third-Party Services – The Internet is a universal connector, therefore the unprotected third-party services can open the door for cyber attackers to access data. Therefore cybersecurity should be given priority when you connect services, rather than an afterthought.
- Unsecured Mobile banking – in recent times as mobile banking popularity has increased, has given an opportunity to hackers to access its data due to less complicated security systems on mobile devices. Encryption must increase the mobile space for banks and customers data to remain safe.
- A constantly changing threat landscape – The cyber threat landscape has changed over the past few years. Now Criminals have stopped going after low-value monetary amounts and shifted to high-value payment platforms. The number of breaches affecting the financial sector had led to an increase in fraudulent activities.
- False Positives – Tone of the biggest issue for banks in its anti-money laundering (AML) monitoring systems is “false positives”. It means pointing out issues that are not actually fraudulent activities, which takes up valuable time for an analyst.
- The Big Breach – It’s the big breach that keeps banks awake at night. Huge volumes of valuable financial data are under increasing pressure to keep customer data safe from hackers and fraudsters.
- New Forms of Hacking – Nowadays hackers do not only just delete consumer data, whereas they change or hold its hostage for later use. Every time hackers are using new ways to exploit financial service.
- Ignoring a Potential Breach – This failure of the system to alert to a potential breach is a major part of a modern cybersecurity strategy and would keep any CISO worth their salt up at night.
- Customers’ Accounts – Customer accounts can be the most vulnerable point of entry to a bank’s systems. The hackers used stolen privileged credentials to steal from their account.
- Ruthless Adversaries – The threat shouldn’t be considered a technology problem but more like organized crime. They are like ruthless operations that work outside of a regulatory system. They are even quicker than the system and are more pragmatic. That’s a really tough problem banking industry has to deal with, so one needs to stop thinking about this as a technology problem.
_
Major threats to banks are depicted in the figure below:
While there are numerous threats aimed at bank systems and their customers, one of the biggest threats, and often one of the hardest to detect, is that of malicious, careless and compromised users. These employees, contractors and partners are already inside the banks secure perimeter and have legitimate access to its sensitive data and IT systems.
When insiders abuse their privileged access or are compromised by external attackers, the valuable data is easily exposed. As banks continue to expand online and mobile access, they also expand the attack surface. As such, they must be vigilant against DDoS attacks and web application attacks such as credential stuffing. We have seen numerous high-profile breaches against major financial services institutions, and the volume and complexity of the attacks are on the rise. Criminals can send phishing emails or set up fake websites that dupe consumers into giving away sensitive financial data. They can also leverage information from social media sites to socially engineer their way into accounts via customer service.
_
Fraud detection:
Nowadays, the banking industry is facing an acute problem of fraud. The problem is global, and no country is fully protected. Fraudsters have become experts in hijacking online sessions: they steal client credentials and use malware to swindle funds from unaware account holders. In his book “Future Crimes” Marc Goodman explains that “criminals are often the first to exploit emergent technologies and turn their complexity against their users”. One of these options is the use of data analysis software which, in most cases, guarantees impeccable fraud detection. Modern systems allow fraud examiners to analyze business data and check how well the internal control system is operating.
As a result, they can designate transactions that denote fraudulent activity or the elevated risk of fraud. There is a spectrum of analysis measures that can be applied to tackle fraud. It ranges from contextual situations for a singular fraud investigation to a repeatable analysis of financial processes susceptible to criminal activity in the first place. If the risk of fraud is really high, financial and banking institutions can employ a constant or continual approach to fraud detection. It works particularly well in situations where preventive controls are not practicable or efficient. The majority of modern financial service companies have increased management requirements for information as the audit adjustment is moving from the conventional cyclical approach to a risk-based and longstanding model.
To disclose fraudulent activity, a lot of banks use special transaction monitoring systems. By and large, they represent domestically produced software which demands an operator intervention. However, traditional security systems can function well for detecting individual point-of-sale, real-time fraud. But that is only the tip of an iceberg.
There is a list of analytical techniques used to detect fraud. The most effective among them are:
1) Classification: to find patterns among various data elements
2) Statistical parameters calculation (standard deviation, averages, etc.): to detect outliers that could reveal fraud.
3) Numbers stratification: to disclose unordinary (redundantly high or low) entries.
4) Joining random diverse sources: to denote matching values (such as names addresses and account numbers) where they shouldn’t exist.
5) Duplicate testing: to note duplicate transactions such as claims, payments or financial report items
6) Gap testing: to find out any missing items in a serial data where there should be none
7) Entry dates validation: to estimate inappropriate or suspicious items or postings or information entry
8) Numeric values summation: to identify control sums which may have been falsified
__
Is secure banking an unrealistic goal?
Even though banks are a popular target for hackers, they also are among the most sophisticated enterprises in the world from a security perspective. This is largely because security and online banking go hand-in-hand.
Consumers want the confidence that their financial information will be protected, regardless of how it’s accessed. The banks have reputation, brand and highly sensitive personal data to protect, and in the main, they take that very seriously. What we don’t hear about are the numerous attempts to breach banking systems that are successfully prevented. This is down to the investments that the banks have made in systems and processes to defend their customer’s personal data.
_
Report by Positive Technologies:
The findings obtained by Positive Technologies’ experts in penetration testing illustrate the planning methodology for attacks and the vulnerabilities cyber gangs exploited.
Deeper Penetration Test Findings:
- 100% of banks, were found to have vulnerabilities in web applications, insufficient network security, and server configuration flaws.
- At 58% of banks there were found deficiencies in user account and password management.
- At 22% of banks, experts successfully breached the network perimeter in external penetration testing.
- 75% of banks are vulnerable to social engineering attacks.
- At 100% of banks, full control over infrastructure was obtained.
- At 58% of banks, experts obtained access to banking systems.
What specifically were the weaknesses that made it possible for more than half of the banks tested to have their banking systems penetrated?
- Insufficient protection against recovery of credentials from OS memory.
- Dictionary passwords.
- Sensitive data stored in cleartext.
- SQL injection.
- Use of reversible coding.
- Credentials stored in application source code.
- Reuse of credentials for multiple resources.
- Insufficient protection of root account.
Network Perimeter Vulnerabilities:
The main vulnerabilities and flaws in security mechanisms common on the bank network perimeter can be divided into four categories: vulnerabilities in web applications, insufficient network security, server configuration flaws, and deficiencies in user account and password management software. On average, an attacker who has penetrated the bank’s internal network needs to only exploit those four flaws to gain access to the banks’ electronic crown jewels.
The report concludes with four points:
1.Remember that if an attack is detected and stopped in time, intruders can be thwarted. Preventing losses is possible at any stage as long as appropriate protective measures are taken.
2.Email attachments should be checked in an isolated environment (sandbox), instead of relying solely on endpoint antivirus solutions.
3.It is critical to configure notifications from protection systems and react to notifications immediately.
4.Security events must be monitored by an internal or external security operations center (SOC) with use of security information and event management (SIEM) solutions, which significantly facilitate and improve processing of information security events.
_
Famous Banking Services Hackings:
- Attack on Six American Banks (2012)
In 2012, six major American banks (Bank of America, JPMorgan Chase, Citigroup, U.S. Bank, Wells Fargo, and PNC) were targets in a wave of computer attacks by a group claiming Middle Eastern ties. The attacks caused internet blackouts and delays in online banking, resulting in frustrated customers who could not access their accounts or pay bills online. These were DDoS attacks, where the hackers overwhelmed the bank websites to the point of shutdown. The attacks also utilized botnets, networks of infected computers that do the bidding of criminals. Sometimes, botnets are referred to as “zombie computers” that obey the commands of a “master botnet.” Unfortunately, these can be rented through black markets or lent out by criminals or governments.
- JPMorgan (2014)
In summer of 2014, in the largest security breach of an American bank to date, the names, addresses, phone numbers, and email addresses of around 83 million accounts were compromised by hackers. Ironically, JPMorgan spends around $250 million on computer security every year. The 2014 breach was not the result of a sophisticated scheme. The attack did not use a zero day attack, the novel software bug that sells for millions in the black market. It also did not utilize malware that hackers in North Korea employed in their cyberattack of Sony. Rather, the source of the issue was basic: The bank did not employ two-factor authentication, which is an additional layer of security when users sign in to access data or an application. JPMorgan’s security team neglected to upgrade one of its network servers with the dual password scheme—that’s all it took.
- SWIFT Payment System (2016)
In February 2016, the Society for Worldwide Interbank Financial Telecommunication (SWIFT), an international consortium of over 11,000 banks that facilitates cross-border transfers, was hacked. The Bangladesh Bank, a user in the SWIFT network, was hacked in the amount of $81 million. Only a small proportion was recovered before the Federal Reserve Bank of New York blocked in 30 other transactions that might have transferred an additional $850 million. These attacks show that payment networks are only as trustworthy as their weakest link. Many in the industry were not surprised by the attack. According to Justin Clarke-Salt, co-founder of Gotham Digital Science, a cybersecurity company, the attacks exploited a weakness in the system: that not every institution protects access to SWIFT in the same way. After all, “Attackers often attack people who are easier to attack…So far from what we know has been publicly reported, they have very much targeted smaller financial institutions. This is probably because they have less sophisticated controls.”
_
Some measure to counter cybercrime against banks:
Education to Customer
Training of Bank Employees
Strong Encryption-Decryption Methods
Physical and Personnel Security
Cooperation among Nations to avert Cybercrime
_
Why Cyber Security is important in banking:
Cybersecurity has been of great importance in the financial sector. It becomes all the more necessary since the very foundation of banking lies in nurturing trust and credibility. Here are some reasons why cybersecurity is important in banking and why it should matter to you:
- Everyone seems to be going cashless, using digital money, e. debit cards and credit cards. In this context, it becomes very important to ensure that all measures of cybersecurity are in place, to protect your data and your privacy.
- Data breaches can make it difficult to trust financial institutions. For banks, that’s a serious problem. A weak cybersecurity system can amount to data breaches that could easily cause their customer base to take its money elsewhere.
- You often tend to lose time and money when a bank’s data is breached. Recovering from the same can be time-consuming and stressful. It would involve cancelling cards, checking statements, and keeping your eyes open for complications.
- Your private data in the wrong hands can do great harm. Even if the cards are cancelled, and fraud is immediately taken care of, your data is sensitive and could reveal a lot of information that could be used against you.
- Banks need to be on their guard more than most businesses. That’s the cost of holding onto the kind of valuable personal data that banks do. Your data with the bank can be breached if not protected from cybercrime threats.
______
______
Cybercrime in business:
The companies are potentially exposed to serious technological as well as financial risks. The reasons for this are certain characteristics of cybercrime, such as the ease of access to powerful technology, the anonymity of the criminal, and the fleeting nature of the evidence. These elements, which provide armor for a perfect crime, are available to the cybercriminal and ensure that the cybercriminal escapes unharmed. Given that the use of technology in today’s business environment brings new risks to the fore, using old solutions might not be the answer. New risks require new measures. There are unique problems related to digital information and transactions, such as storage and intellectual property issues, that must be considered. Therefore, although the new technology allows individuals to engage in international business activity as never before, it also expands the scale and scope of the associated risks. Technology tools mean that computing power, connectivity, and speed can spread viruses, compromise systems, and compound errors in seconds, potentially affecting interconnected parties, increasing business costs to rectify such mishaps, and hitting a larger target than even envisaged. Cybercriminals never stop devising new techniques. New tools mean new vulnerabilities, and the preventive measures to overcome these vulnerabilities fail to keep pace with cybercriminals’ ability to devise new techniques. The reporting of this type of crime is often inadequate. This is partly because some crimes go unnoticed and partly because the victims (economic operators and companies) are wary about reporting cybercrimes for fear of getting a bad reputation and of their future business prospects being affected by public exposure of their vulnerabilities. Companies must factor these risks into their business risk margins and take abundant precautions to fight against these vulnerabilities. Any form of crime is socially harmful; combating cybercrime is not just a matter of creating security measures through the medium itself, but also requires the establishment of preventive measures in the legal sphere to address the situation.
Many business organizations are leaving themselves vulnerable to cybercrime based on a false sense of security — perhaps even complacency — driven by non-agile security tools and processes. Many are failing to recognize cybercrimes in their [information technology] environments and misallocating limited resources to lesser threats. For example, many organizations focus heavily on foiling hackers and blocking pornography, leaving major cybercrimes undetected and unaddressed. This has generated significant risk exposure, including exposure to financial losses, regulatory issues, data breach liabilities, damage to brand, and loss of client and public confidence.
_
Most Common Threats to Businesses:
A recent collective analysis distributed at the initiative of the French National Gendarmerie has identified the forms of cybercrime that are most likely to target businesses.
These threats are:
(1) Denial of service/blocked access/paralysis/unavailability;
(2) Loss or theft of strategic data/unfair competition;
(3) Misinformation/defamation/damaged image;
(4) Intrusions/economic fraud/embezzlement;
(5) Cyber-extortion/demand for ransom;
(6) Theft of personal data managed by a business;
(7) Threats to vital infrastructures;
(8) Propagation of malware through social networks/web navigation;
(9) Misuse; and
(10) Falsification of documents.
_
Below is an example of CryptoLocker’s screen alerting the victim of encryption of all data and asking for a ransom for the return of said data within a set time.
Figure above shows image of the warning screen of CryptoLocker ransomware
_
Impact of cybercrime on businesses:
The impact of cybercrime on businesses goes beyond financial integrity (Ringwelski). They include; Revenue loss, Time wastage, Damage to business reputation and Reduction in productivity.
The amount of revenue loss that results from cybercrimes is phenomenal. Cybercrime cost U.S. businesses U.S.$3.8 million annually (Messmer,2010). A study by Ponemon Institute and duly sponsored by ArcSight which was conducted over a period of seven months and covered 45 organizations revealed that a lot of revenue is lost by business enterprises due to cybercrime (Ponemon Institute, 2010). The revenue loss was attributed to the cost spent by both government and business enterprises in coping with the various attacks.
A lot of time is wasted by the IT staff of a given firm in handling of cybercrime incidents. This tends to distract them from working on the productive organizational activities. lot of time is wasted in handling of breaches and other cybercrime related events.
Firms whose securities have been breached suffer a lot of reputational damage as well as possible law suits from customers whose personal and private data have landed on the hands of the hackers. The consequence of this is loss of confidence and hence loss of business.
Cybercrime often results in moves that are aimed at counteracting the events. This negatively affects the productivity of employees.
There are other ways that cyber-crime affects companies and their customers:
The Cost of Protection:
Companies that want to protect themselves from online thieves have to pull out their wallets to do it. There are costs in identifying risks, building new and safer operating procedures, and buying protective software and hardware. For businesses with complex or sensitive operations, this often involves hiring a cyber-security consultant to develop a customized solution. Not only are the upfront costs of protection expensive, but the systems must be tested and monitored regularly to ensure that they are still effective against emerging cyber-attacks. These costs are often passed on to the customer through higher prices of goods and services.
Lost Sales:
Cyber-crime isn’t just for thieves anymore. A new subculture has emerged in the past few years: the cyber-activist. These are the online equivalents of protesters who chain themselves to buildings or trees. Their purpose is to shut down a company’s online operations to send a message about the company’s business practices. In the past two years, major corporations, such as PayPal and MasterCard, have been attacked in this way.
In December 2010, the PayPal website was attacked by dozens of people claiming to be part of the group, Anonymous. They attempted to perpetrate a denial of service attack in retaliation for PayPal shutting down payment services to WikiLeaks. More than a dozen hackers were arrested in that crime. While PayPal did not experience a full shutdown, many other businesses aren’t so lucky. A denial of service attack results in fewer sales as customers cannot access the company’s online store. It can even result in less revenue in the long-term if some customers decide to no longer do business with a company vulnerable to attack.
Changing Methods of Doing Business:
Cyber-crime can impact businesses in more than just financial ways. Companies have to rethink how they collect and store information to ensure that sensitive information isn’t vulnerable. Many companies have stopped storing customers’ financial and personal information, such as credit card numbers, social security numbers and birth dates. Some companies have shut down their online stores out of concern that they cannot adequately protect against cyber-theft. Customers are also more interested in knowing how the businesses they deal with handle security issues and they are more likely to patronize businesses that are upfront and vocal about the protections they have installed. (To learn more, read Identity Theft.)
_
_
According to cyber edge group 2016, companies have several barriers that prevent them from establishing effective defenses against cyber-attacks:
- Low security awareness among employees
- Too much data to analyze
- Lack of skilled personnel
- Lack of budget
- Lack of management support/awareness
- Poor integration/interoperability between security solutions
- Lack of effective solutions available in the market
- Inability to justify additional investment
- Too many false positives
Implementing defense mechanisms would greatly reduce successful cyber-attacks, however, attackers continually develop more powerful software that cannot be identified by security systems or even break existing security codes, thereby diminishing the possibility of prevention of cybercrime, and makes necessary the appearance of enforcement to punish the criminal conduct perpetrated.
_
Why are SMBs vulnerable to cyberattacks?
SMBs are vulnerable to the same threats as larger ones, but often lack the resources to fully implement network security. Small businesses, in particular, bear the brunt of 43% of cyberattacks and this percentage will only increase. There are multiple factors contributing to this. Small businesses are less likely to have dedicated cyber security resources to protect their businesses and more likely to be reliant on outsourced suppliers and software for their IT needs, which introduces possible supply chain vulnerabilities, as well as infrastructure configuration weaknesses. They are also less likely to have an adequate cyber security budget, resulting in weakened security coverage. Additionally, SMBs may lack the expertise to make informed policy and configuration changes in response to emerging threats.
One of the most important security measures for SMBs to take is properly securing remote access to their networks. While convenient, remote access mechanisms often lack adequate security to defend against attackers scanning the Internet. If you connect to a terminal server or office PC, protect that connection with a VPN. Make sure that multi-factor authentication is enabled on web portals.
Encrypting mobile devices that store company data, such as laptops, even if not required by regulatory compliance obligations is recommended. Knowing that a machine is encrypted means that the cost of a lost or stolen laptop is just replacing the laptop, rather than a potential release of corporate data.
To protect SMBs from cybercriminals:
- Train your employees
- Set up and implement stringent security policies
- Monitor the network.
- Ensure perimeter security and access restrictions
_____
While it may not be possible to completely eradicate cybercrime, businesses can reduce their exposure to it by maintaining an effective cybersecurity strategy using a defense in depth approach to securing systems, networks and data.
Some steps for resisting cybercrime include:
- develop clear policies and procedures for the business and employees;
- outline the security measures that are in place about how to protect systems and corporate data;
- use two-factor authentication apps or physical security keys: Activate two-factor authentication on every online account when possible;
- verbally verify the authenticity of requests to send money by talking to a financial manager;
- create intrusion detection system rules that flag emails with extensions that are similar to company emails
- carefully scrutinize all email requests for transfer of funds to determine if the requests are out of the ordinary.
- create a cybersecurity incident response management plans to support these policies and procedures;
- continually train employees on cybersecurity policies and procedures and what to do in the event of security breaches;
- keep websites, endpoint devices and systems current with all software release updates or patches; and
- back up data and information regularly to reduce the damage in case of a ransomware attack or data breach.
______
______
Organized cybercrime:
Important questions in the literature are to what extent cybercriminals are organised – a counterintuitive proposition for those who hold the stereotypical view of the loner hacker nerd – and whether traditional organised crime is transferring to the Internet. Again, too few data are available to say anything definitive about these questions; indeed, assertions without cited supportive evidence are quickly transformed into hearsay and anecdote which are in turn recycled within other authors’ assertions concerning cybercriminal activity.
Nevertheless, the literature does offer hypotheses based on anecdotal evidence. There seems a trend towards increasing diversification and specialisation of tasks, in which hackers, virus writers, and spammers focus on their own special expertise, while collaborating to commit a wider range of cybercrimes (Van der Hulst & Neve, 2008, p. 80). Wall (2007, pp. 41, 43) observes a specialised division of labour with ‘deskilling’ and ‘reskilling’ of tasks in automated attacks, and he asserts (2007, p. 155) that ‘the new generation of cybercrime is becoming much more organized at a higher level than its predecessors’. A distinct ‘underground’ criminal subculture is emerging, in which cybercrime tools and knowledge are shared and traded, and task-specific expertise is rented and hired for one-off operations. This may also include hiring students or expert ICT personnel from regular businesses; Van der Hulst and Neve (2008, pp. 126, 148) assert that ‘in some cases Dutchmen are also members of organised (Eastern European) criminal networks acting as service performers’. The high unemployment of cryptologists and ICT experts in Eastern Europe is hypothesized to be a risk factor for organised cyberfraud (Bekkers et al, 2005, p. 109).
Whether the organisation of cybercriminals is similar to traditional organised crime, is debatable. Brenner (2002) argues, based on the characteristics of offline organised crime and the online environment, that cybercrime will not develop the organised-crime models of the gang or the Mafia, but instead ‘will almost certainly emphasize lateral relationships, networks instead of hierarchies’ in a fluid, ‘swarming’ model ‘in which individuals coalesce for a limited period of time in order to conduct a specifically defined task or set of tasks’ (Brenner, 2002, p. 50). As McCusker (2006, p. 265) points out, however, offline organised crime nowadays also comprises horizontal networks of cell-like crews, so that the difference between offline and online organised crime may be less poignant than Brenner suggests.
McCusker (2006) investigated whether current forms of organised cybercrime derive from cybercrime that has organised itself, or from organised crime that has moved online. He concludes overall that cybercrime is perpetrated by ‘criminal individuals and/or groups online who are organised rather than traditional organised crime groups who are online’ (p. 273). However, he also observes that both underground communities can benefit from combining efforts, because of an overlap in skills and motivation (p. 266). In any case, organised crime groups will be willing to pay cybercriminals for information to facilitate their (offline) activities, and they will also employ the Internet’s opportunities to launder money or hide their traces. Whether organised crime will eventually mutate into full-fledge organised cybercrime depends ultimately on the opportunity structure of offline crime as compared to the opportunities of online crime (McCusker, 2006, p. 273).
_
Cybercriminals often work in organized groups. Some cybercriminal roles are:
- Programmers: Write code or programs used by cybercriminal organization
- Distributors: Distribute and sell stolen data and goods from associated cybercriminals
- IT experts: Maintain a cybercriminal organization’s IT infrastructure, such as servers, encryption technologies and databases
- Hackers: Exploit systems, applications and network vulnerabilities
- Fraudsters: Create and deploy schemes like spam and phishing
- System hosts and providers: Host sites and servers that possess illegal contents
- Cashiers: Provide account names to cybercriminals and control drop accounts
- Money mules: Manage bank account wire transfers
- Tellers: Transfer and launder illegal money via digital and foreign exchange methods
- Leaders: Often connected to big bosses of large criminal organizations. Assemble and direct cybercriminal teams, and usually lack technical knowledge.
Clearly, there is much overlap between roles, but as cybercrime becomes a greater issue, more specialization is being seen as organized crime gets in the picture. For example, hackers were once more often than not hobbyists who broke into systems for personal gratification. While white-hat hacking hasn’t disappeared, it’s much more common now to see hackers as professionals who sell their services to the highest bidder.
_
According to a United Nations Office on Drugs and Crime study on cybercrime, upwards of 80 per cent of cybercrime acts are estimated to originate in some form of organized activity. This is established on a cycle of malware creation, computer infection, botnet management, harvesting of personal and financial data, data sale, and “cashing out” of financial information. An interesting observation is that they also found during the course of their study that cybercrime perpetrators no longer require complex skills or techniques.
Take the example of a Russian group that attacked one of the best-known banks in New York via data networks in 1994. Operating from St. Petersburg, the group succeeded in causing the American bank to transfer more than US $10,000,000 to foreign accounts. A number of the perpetrators were arrested, and some of them possessed fake Greek and Israeli passports. The high quality of the forging could have been produced only in Russia, by members of the former Russian secret service, the KGB. A recent example is the cyber-heist on a fuel distribution firm in North Carolina, where the firm lost more than US $800,000.
These examples clearly reflect how cybercrime has now evolved into “organized cybercrime”, with far-reaching effects and insurmountable costs. Today’s cyber criminals have evolved to make their crimes more profitable; they have specialties, they are masters in their chosen field, they have networks, and they organize their crimes. In this scenario, it is imperative that businesses recognize this very serious threat.
Given that organized crime has traditionally selected particular industries as targets for infiltration, it is essential that the corporate sector consider both general cybercrime and large-scale organized cybercrime when formulating its policies on risk management and risk margins.
The primary objective of organized crime is to generate a profit; as such, it is a business that is operated by criminal means. Criminal organizations are always on the lookout for new means and opportunities to perpetrate criminal exploitation. The Internet and the ever-increasing growth of electronic commerce provide organized crime groups with tremendous new opportunities.
Another reason why cyberspace is a potentially welcome area for organized criminals is because organized crime groups often operate out of safe havens. The transnational nature of the Internet therefore perfectly fits their modus operandi. There are no borders defining the commitment of cybercrimes, which makes policing problematic and makes “large-scale investigations slow and tedious at best, and impossible at worst”.
_
_
The structure of cybercriminal market:
The cybercriminal market usually comprises a set of “services” and “products”, used for various illegal actions in cyberspace. These “products” and “services” are offered to users of dedicated online communities, most of which are closed to outsiders.
The “products” include:
- Software designed to gain unauthorized access to a computer or a mobile device, in order to steal data from an infected device or money from a victim’s account (the Trojans);
- Software designed to take advantage of vulnerabilities in the software installed on a victim’s computer (exploits);
- Databases of stolen credit card data and other valuable information;
- Internet traffic (a certain number of visits to a customer-selected site by users with a specific profile.)
Tools of the Trade:
- Wireless networking technology poses the biggest problem, as an unsecured network can be hacked from someone outside using a simple radio antenna, PDA or cell phone.
- Password Crackers (Software designed to decrypt passwords, so they can gain access)
- Network Scanning software that looks for open ports to gain access to a network (software or hardware based)
- Illegitimate Websites (fake URLs), to lure you into giving information over the web or even hack an un-patched (updated)system
- SPAM (used to get email lists to possibly cause more damage)
The “services” include:
- Spam distribution;
- Organization of DDoS attacks (overloading sites with requests in order to make them unavailable to legitimate users);
- Testing malware for antivirus detection;
- “Packing” of malware (changing malicious software with the help of special software (packers) so that it is not detected by antivirus software);
- Renting out exploit packs;
- Renting out dedicated servers;
- VPN (providing anonymous access to web resources, protection of the data exchange);
- Renting out abuse-resistant hosting (hosting that does not respond to complaints about malicious content, and therefore does not disable the server);
- Renting out botnets;
- Evaluation of the stolen credit card data;
- Services to validate the data (fake calls, fake document scans);
- Promotion of malicious and advertising sites in search results (Black SEO);
- Mediation of transactions for the acquisition of “products” and “services”;
- Withdrawal of money and cashing.
Payments for such “products” and “services” on the cybercriminal market are generally made via an e-payment system such as WebMoney, Perfect Money, Bitcoin and others.
All of these “products” and “services” are bought and sold in various combinations in order to enable various types of crime. According to Kaspersky Lab experts, the theft of money is currently the most widespread type of crime.
_
Line between Illicit and Legitimate E-Commerce is blurring:
The cybercrime ecosystem has evolved to welcome both new actors and new scrutiny. The threat of prosecution has pushed most cybercrime activities onto the darknet, where the anonymity of Tor and Bitcoin protects the bad guys from being easily identified. Trust is rare in these communities, so some markets are implementing escrow payments to make high-risk transactions easier; some sellers even offer support services and money-back guarantees on their work and products.
The markets have also become fractured, as the pro criminals restrict themselves to highly selective discussion boards to limit the threat from police and fraudsters. Nevertheless, a burgeoning cybercrime market has sprung from these hidden places to offer everything from product development to technical support, distribution, quality assurance, and even help desks.
Many cybercriminals rely on the Tor network to stay hidden. Tor — The Onion Router — allows users to cruise the Internet anonymously by encrypting their activities and then routing it through multiple random relays on its way to its destination. This circuitous process renders it nearly impossible for law enforcement to track users or determine the identities of visitors to certain black-market sites.
There is now a sophisticated and self-sufficient digital underground economy in which data is the illicit commodity. Stolen personal and financial data – used, for example, to gain access to existing bank accounts and credit cards, or to fraudulently establish new lines of credit – has a monetary value. This drives a range of criminal activities, including phishing (the act of attempting to acquire information such as usernames, passwords, and credit card details and sometimes, indirectly, money, by masquerading as a trustworthy entity in an electronic communication), pharming (the fraudulent practice of directing Internet users to a bogus Web site that mimics the appearance of a legitimate one), malware distribution and the hacking of corporate databases, and is supported by a fully-fledged infrastructure of malicious code writers, specialist web hosts and individuals able to lease networks of many thousands of compromised computers to carry out automated attacks.
_
A study found no mob bosses in cybercrime world yet: There is no ‘Tony Soprano mob boss type’ who is ordering cybercrime against financial institutions globally, say researchers, adding that there are no such thing as organized crime mafias to date. Cybercrime groups function and work together to cause an estimated $445-600 billion of harm globally per year. “Certainly, there are different nation states and groups engaging in cybercrime, but the ones causing the most damage are loose groups of individuals who come together to do one thing, do it really well – for a period of time – then disappear,” explained Thomas Holt, professor of criminal justice at Michigan State University. Holt said that organized cybercrime networks are made up of hackers coming together because of functional skills that allow them to collaborate to commit the specific crime. “So, if someone has specific expertise in password encryption and another can code in a specific programming language, they work together because they can be more effective – and cause greater disruption – together than alone,” said Holt, the co-author of the study. Holt and lead author ER Leukfeldt, researcher at the Netherlands Institute for the Study of Crime and Law Enforcement, reviewed 18 cases from which individuals were prosecuted for cases related to phishing. “We found that these cybercriminals work in organisations, but those organisations differ depending on the offense,” Holt said. “They may have relationships with each other, but they’re not multi-year, multi-generation, sophisticated groups that you associate with other organised crime networks,” he noted in the journal International Journal of Offender Therapy and Comparative Criminology. The research also debunked common misconceptions that sophisticated organized criminal networks – such as the Russian mafia – are the ones creating cybercrime.
______
Cybercrime-as-a-Service (CaaS):
Over the last 20 years, we have seen cybercrime become professionalized and sophisticated. Cybercrime is a business with flourishing markets offering a range of tools and services for the criminally inclined. From products like exploit kits and custom malware to services like botnet rentals and ransomware distribution, the diversity and volume of cybercrime offerings has never been greater. The result of this has been a simultaneous broadening and deepening of the cybercrime threat. New tools and platforms are more accessible than ever before to those without advanced technical skills, enabling a flood of new actors to engage in cybercrime activities. At the same time, experienced criminals are able to focus on developing more specialized skill sets, confident in their ability to find others within the thriving darknet ecosystem who can complement their services, and with whom they could collaborate to develop new tools of unprecedented sophistication.
_
The terms “Attack-as-a-Service,” “Malware-as-a-Service,” and “Fraud-as-a-Service” are used to qualify models of sale in which cybercriminals sell or rent their colleagues hacking service and malicious code, to conduct illegal activities. The concept is revolutionary, the black market offers entire infrastructures to service malware (e.g. bullet-proof hosting or rent compromised machines belonging to huge botnets), and outsourcing and partnerships services, including software development, hacking services, and, of course, customer support.
The majority of these services are presented in the underground economy, based on a subscription or flat-rate fee model, making them convenient and attractive. The principal cost of arranging criminal activities are shared between all customers. This way, service providers could increase their earnings, and clients benefit from a sensible reduction of their expenditure, with the knowledge needed to manage illegal businesses.
These services are characterized by their ease of use and a strong customer orientation. They typically have a user-friendly administration console and dashboard for the control of profit.
The diffusion of the cloud computing paradigm has brought numerous advantages to IT industry, but also new opportunities for cyber criminals. The term “Attack-as-a-Service” is referred to as the capability of criminal organizations to offer hacking services. The majority of cases exploit cloud-based architectures. Cyber criminals offer entire botnet and control infrastructures, hosted on cloud architectures for lease or sale. Compromised machines could be used to steal information from the victims (e.g. banking credentials, sensitive information) or to launch massive DDoS attacks against specific targets.
The prices for attacks on commission are widely variable. Some services are totally free, such as a subscription for IMDDOS. Meanwhile, it costs between $150 and $400 to crack e-mail passwords in less than 48 hours.
_
Trend Micro published a fascinating report on the Russian underground, one of the most active cybercriminal communities, proposing interesting considerations on principal products and services available on the black market and their prices. The study showed data collected during the analysis of online forums and services attended by Russian hackers such as carding-cc.com, antichat.ru, xeka.ru, and carding-cc.com. Online it is possible to acquire all the necessary resources to conduct a cyber-attack or to realize a sophisticated fraud without having particular skills. The list of criminal activities is long, as is the range of products and services offered to the buyers for relative cheap prices. The following is a list of the principal “articles” sold in the underground ranked by popularity and the number of requests:
- Programming services and software sales
- Hacking services
- Dedicated server sales and bulletproof-hosting services
- Spam and flooding services, including call and SMS flooding services
- Download sales
- DDoS services
- Traffic sales
- File encryption services
- Trojan sales
- Exploit writing services and sales
Cyber criminals have discovered the possibility to provide malicious services renting tools, botnet architectures and cloud infrastructures providing computational resources on demand. The innovation is represented by the possibility to offer also an efficient “customer care” to support customers in their initiatives and social networks platform to manage the community of clients and communicate with them rapidly. The business model is consolidated and adopted by various criminal organizations.
_
One of the most interesting studies proposed regarding cybercrime offers was presented by Fortinet in December 2012. The report produced by the security firm describes the model of “Crime-as-a-Service” in particular, providing a detailed price list for principal hacking services offered in “Attacks-as-a-Service,” with some interesting data:
- Consulting services such as botnet setup, $350-$400
- Infection/spreading services, under $100 per a thousand installs
- Botnets and rental, Direct Denial of Service (DDoS), $535 for 5 hours a day for one week, email spam, $40 per 20,000 emails, and Web spam, $2 per thirty posts.
- Blackhat Search Engine Optimization (SEO), $80 for 20,000 spammed backlinks.
- Inter-Carrier money exchange and mule services, 25% commission.
- CAPTCHA breaking, $1 per a thousand CAPTCHAs, done by recruited humans.
- Crimeware upgrade modules: Using Zeus modules as an example, they range anywhere from $500 to $10,000.
The above deliverables are provided using different modalities, such as renting, buying or leasing to respond to the client’s needs. No doubt, despite different terms adopted to describe similar practices, the models behind them appear to be winning.
_
Cybercrime site selling hacking tool taken down in 2019:
A website which sold a hacking tool purchased by cyber criminals in 124 countries and gave full remote control of victims’ computers has been taken down following an international investigation. 14,500 people across the world purchased the Imminent Monitor Remote Access Trojan (IM RAT) from https://imminentmethods.net for as little as $25USD.
Once covertly installed on a victim’s computer, IM RAT allowed the hacker full access to the infected device, enabling them to disable anti-virus software, steal data or passwords, record key strokes and watch victims via their webcams.
The international operation was led by the Australian Federal Police (AFP) with the North West Regional Organised Crime Unit (NWROCU) leading the UK investigation with UK activity coordinated and supported by the National Crime Agency (NCA).
The illicit use of IM RAT is akin to a cyber burglary, with criminals stealing data, including images and movies, secretly turning on web cams, monitoring key strokes and listening in to people’s conversations via computer microphones.
Cyber Crime is not an anonymous victimless crime as some believe. There are real world consequences to people’s actions in cyber space. People should protect themselves by ensuring operating systems are always up to date, they use anti-virus and they don’t click on links or attachments in suspicious emails.
______
______
Harms of cybercrime:
Cyber-security researchers have identified a total of at least 57 different ways in which cyber-attacks can have a negative impact on individuals, businesses and even nations, ranging from threats to life, causing depression, regulatory fines or disrupting daily activities. The researchers, from Kent’s School of Computing and the Department of Computer Science at the University of Oxford, set out to define and codify the different ways in which the various cyber-incidents being witnessed today can have negative outcomes.
They also considered how these outcomes, or harms, can spread as time passes. The hope is that this will help to improve the understanding of the multiple harms which cyber-attacks can have, for the public, government, and other academic disciplines.
Overall the researchers identified five key themes under which the impact—referred to in the article as a cyber-harm—from a cyber-attack can be classified:
- Physical/Digital
- Economic
- Psychological
- Reputational
- Social/societal
Each category contains specific outcomes that underline the serious impact cyber-attacks can have. For example, under the Physical/Digital category there is the loss of life or damage to infrastructure, while the Economic category lists impacts such as a fall in stock price, regulatory fines or reduced profits as a possibility.
In the Psychological theme, impacts such as individuals being left depressed, embarrassed, shamed or confused are listed, while Reputational impacts can include a loss of key staff, damaged relationships with customers and intense media scrutiny. Finally, on a Social/Societal level, there is a risk of disruption to daily life such as an impact on key services, a negative perception of technology or a drop in internal morale in organisations affected by a high-level incident.
The researchers point to high-profile attacks against Sony, JP Morgan and online dating website Ashley Madison, as examples where a wide variety of negative outcomes were experienced, from reputational loss, causing shame and embarrassment for individuals or financial damage. They say these incidents underline why a taxonomy of impacts and harms is so important for businesses. Many successful cyber-attacks have been traced to exploits of well-known vulnerabilities that had not been dealt with appropriately because of a lack of action by firms who did not appreciate the ways in which they could be affected by a cyber-attack.
Additional harms are:
The loss of intellectual property and sensitive data
Cost of countermeasures and insurance
The loss of trade and competitiveness
Distortion of trade
Job loss
Erosion of customer loyalty
Impaired security for your business—or governments and states
Increased potential for future attacks
_____
Attacks on American businesses and organizations increased by 176 percent in 2014—that’s 138 successful attacks each week. These attacks are also taking more time to resolve as well, with the worldwide average to detect an attack at 170 days, the longest average time at 259 days and the average time to resolve an incident at 45 days. Virtually every industry deals with the impact of cybercrime, with the highest annual costs in the energy & utilities and defense industries. Cybercrime threatens the critical infrastructure of businesses and government around the globe, and can harm civilians in myriad ways. It is estimated hundreds of billions of dollars have been lost from the global economy due to cybercrime, and unfortunately there is no sign of it slowing down.
_____
Although freedom of speech is protected by law in most democratic societies, that does not include all types of speech. In fact, spoken or written “true threat” speech/text is criminalized because of “intent to harm or intimidate”, that also applies for online or any type of network related threats in written text or speech. Internet medium has been widely used for issuing threats personally or by certain terrorist group etc to create an atmosphere of fear and unrest. Another form of cybercrime in the form of bullying and stalking is also becoming widespread and notorious. People bullying their bosses, teachers, classmates, and co-workers have become very common, also the cases of dejected lovers stalking people is at rising which has become a serious issue of threat for our society. Though the government is coming up with laws to curb these cases there is also a need for moral counselling.
_____
Emotional impact of cybercrime:
The first study to examine the emotional impact of cybercrime shows that victims’ strongest reactions are feeling angry (58 per cent), annoyed (51 per cent) and cheated (40 per cent), and in many cases, they blame themselves for being attacked. Only 3 per cent don’t think it will happen to them, and nearly 80 per cent do not expect cyber criminals to be brought to justice resulting in an ironic reluctance to take action and a sense of helplessness. Despite emotional burden, the universal threat and incidents of cybercrime, people still aren’t changing their behaviour – with only half (51 per cent) of adults saying they would change their behaviour if they became a victim. Even fewer than half (44 per cent) reported the crime to the police.
_____
Charities affected by cybercrime in 2019:
Charities of all sizes were affected by cybercrime in 2019. Charities can often find themselves in the cross-hairs of cyber-criminals looking for easy targets, with almost a quarter reporting at least one attack during a twelve-month period, according to Cyber Security Breaches Survey 2019. Despite these figures, 44% of charities are not protecting themselves from cyber-attacks as many charity leaders don’t see the risks.
As it turned out, smaller charities got off relatively lightly despite many of them having comparatively unsophisticated cyber security. Of larger, high-income charities, over 50% reported being on the receiving end of a cyber-attack during the year. Many of these attacks were so-called “phishing attacks “, as well as ransomware attacks and other digital attacks which involved viruses and other forms of malware.
_____
Cybercrime is causing Life-Threatening Problems at Hospitals:
For most of us, we take it for granted that there’s a hospital near us we can go to if a medical emergency strike. Whether it’s a broken bone, heart attack symptoms, or something else, we know we can get treatment to avoid more serious consequences (in most cases). But what if your local hospital was shut down because a ransomware attack disabled their computers and equipment? That’s exactly what happened recently in Wyoming.
Campbell County Health reported a systemwide crippling of their computers that affected its flagship hospital and nearly 20 clinics located in the city of Gillette. For eight hours, the hospital’s emergency department was forced to transfer patients even though the next nearest hospital was located 70 miles away. The health care system stopped admitting new patients, labs were shuttered and some surgeries were postponed. It took 17 days to restore normal order.
Redirecting patients to the next nearest hospital sounds routine, but when you have to travel 70 additional miles to get to the hospital, that’s a pretty big deal. Studies have found that delaying treatment for serious conditions such as heart attacks and strokes by more than an hour significantly reduces the patients’ chances of survival.
_
WannaCry cancels Surgeries and Appointments across the U.K.’s National Health Service:
In 2017, the U.K. Comptroller and Auditor General released a report analyzing the impact of the WannaCry attack on the NHS. The report (among other findings) noted that the attack:
- caused disruption in at least 34% of the NHS trusts (organizational units) in England
- resulted in approximately 19,000 appointments that were cancelled, and
- caused patients in five areas to travel further to accident and emergency departments
Keeping in mind that minutes count when it comes to getting treatment for serious conditions and accidents, it’s not far-fetched to guess that these healthcare disruptions may have led to avoidable fatalities.
_
Vanderbilt Study finds Cyber Attacks increase Heart Attack Fatality Rate:
A recent study by Vanderbilt looked at how heart attack victims fared at hospitals impacted by a data breach vs. hospitals who hadn’t been impacted by a data breach. The researchers analyzed data from a total of 3,025 different hospitals across the US. This study looked more at long term impacts rather than immediate and direct impacts from the attack. But the results are pretty interesting: Hospital time-to-electrocardiogram increased as much as 2.7 minutes and 30-day acute myocardial infarction mortality increased as much as 0.36 per-centage points during the three-year window following a breach. In other words, in addition to direct problems caused while the attack is ongoing, there are lasting impacts that cause increased fatality rates for 3 years after the attack.
_____
Cyber criminals now targeting political manipulation:
Cyber-attacks against the U.S. Democratic Party and the leak of stolen information reflect a trend toward criminals employing overt campaigns to destabilize organizations and countries. 2016 marked a change in the motives of cyber criminals with a sharp increase in the number of attacks aimed at political manipulation. This was among the key findings of the Symantec Internet Security Threat Report (ISTR), Volume 22, that was released.
_______
Global Price Tag of consumer cybercrime:
The 2013 Norton-Symantec Report showed self-reported experiences of more than 13,000 adults across 24 countries:
Figure above shows Global Price Tag of consumer cybercrime: type of crime wise:
Norton-Symantec experts have also analyzed the incidence of cybercrime in different countries around the world. As expected, it concludes that cybercrime has no boundaries, its action is globally distributed, although substantial differences are related to the local law framework and to the real effort of the authorities. The difference in the impact of cybercrime is also influenced by many other factors, including the penetration level of technology, perceived corruption, and the adoption of defense mechanisms. The study revealed that the annual number of victims has been estimated at 378 Million. The countries where the greatest percent of the population are victims are Russia (85%), China (77%), and South Africa (73%). The greatest cost of consumer cybercrime are reported in the USA ($38 billion), Europe ($13 billion) and China ($37 billion.)
Figure above shows Global Price Tag of consumer cybercrime-region wise:
The 2013 Norton Report states that the lack of efficient authentication mechanisms and defense mechanisms is the primary cause of incidents for mobile users. Almost half don’t use basic precautions and a third were victims of illegal activities last year. What’s very concerning is that, given the awareness level of users regarding cyber threats, only a small portion of mobile users (26%) have installed security software and 57% aren’t aware of existence of security solutions for mobile environments. These numbers explain why mobile technology is so attractive for cybercrime. In the majority of cases, the systems are totally exposed to cyber threats due to bad habits and risky behavior.
_____
Financial services have the highest cost of cybercrime according to Accenture and the Ponemon Institute, 2017.
____
Global Cybercrime Cost:
In August of 2016, Cybersecurity Ventures predicted that cybercrime will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015. This represents the greatest transfer of economic wealth in history, risks the incentives for innovation and investment, and will be more profitable than the global trade of all major illegal drugs combined. The cybercrime prediction stands, and over the past three years it has been corroborated by hundreds of major media outlets, academia, senior government officials, associations, industry experts, the largest technology and cybersecurity companies, and cybercrime fighters globally.
According to Ninth Annual Cost of Cybercrime Study 2019 the total value at risk from cybercrime is US$5.2 trillion over the next five years as seen in the figure below:
Cybercrime costs include damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, post-attack disruption to the normal course of business, forensic investigation, restoration and deletion of hacked data and systems, and reputational harm.
A report (sponsored by McAfee), published in 2014, estimated that the annual damage to the global economy was $445 billion. Approximately $1.5 billion was lost in 2012 to online credit and debit card fraud in the US. In 2018, a study by Center for Strategic and International Studies (CSIS), in partnership with McAfee, concludes that close to $600 billion, nearly one percent of global GDP, is lost to cybercrime each year.
Cybercrime is fuelling the market for cybersecurity products and services, which is expected to grow from $75 billion in 2015 to $175 billion by 2020. The cyber-insurance market is also getting a boost from cybercrime – and projected to grow from $2.5 billion in 2015 to $7.5 billion by 2020.
_
Estimates of the cost of cybercrime show significant variation, from tens of billions to a trillion dollars or more. This reflects the absence of data and differing methodologies. In 2014, taking into account the full range of costs, CSIS estimated that cybercrime cost the world between $345 billion and $445 billion. As a percentage of global GDP, cybercrime cost the global economy 0.62% of GDP in 2014. Using the same methods, CSIS now believe the range is now between $445 billion and $600 billion. Another effort at a global estimate suggests that as a percentage of global GDP, cybercrime cost the global economy 0.8% in 2016 by accounting for underreporting of losses by companies and governments.
Table below shows Regional Distribution of Cybercrime 2017:
| Region
(World Bank) |
Region
GDP (USD, trillions) |
Cybercrime
Cost (USD, billions) |
Cybercrime Loss (% GDP) |
| North America | 20.2 | 140 to 175 | 0.69 to 0.87% |
| Europe and Central Asia | 20.3 | 160 to 180 | 0.79 to 0.89% |
| East Asia & the Pacific | 22.5 | 120 to 200 | 0.53 to 0.89% |
| South Asia | 2.9 | 7 to 15 | 0.24 to 0.52% |
| Latin America and the Caribbean | 5.3 | 15 to 30 | 0.28 to 0.57% |
| Sub-Saharan Africa | 1.5 | 1 to 3 | 0.07 to 0.20% |
| MENA | 3.1 | 2 to 5 | 0.06 to 0.16% |
| World | $75.8 | $445 to $608 | 0.59 to 0.80% |
The cost of cybercrime is unevenly distributed among all the countries of the world. CSIS found variations by region, income levels and level of cybersecurity maturity. Unsurprisingly, the richer the country, the greater its loss to cybercrime is likely to be. The relationship of the developing world to cybercrime is complex, as the mobile connections that have brought the internet to millions are easily exploitable, but the value that can be extracted from these connections remains relatively low, and weak defenses in wealthier countries mean that is where criminals focus their attention. The countries with the greatest losses (as a percentage of national income) are in the mid-tier nations—those that are digitized but not yet fully capable in cybersecurity.
_________
Cyber-attacks became more profitable than the drug trade:
Information security professionals, no matter how big the enterprise they work for, are currently overwhelmingly outgunned by cybercrime. The threat of these criminal enterprises is large and growing and if left unchecked will have a disastrous impact on our economy in the near term. McKinsey & Company estimates that cyberattacks will slow the pace of technology and business innovation over the next few years and cost the economy as much as $3 trillion annually. Data breaches have already taken a heavy toll and costs are on the rise. An IBM-sponsored survey conducted by the Ponemon Institute found that the average cost to the company of a corporate data breach is now $5.9 million. Of this, the cost of lost business from a breach averages $3.2 million. However, this average can be misleading because some of the more widely publicized breaches in recent years have cost the affected companies billions of dollars in revenue and shareholder value.
Considering its relatively low entry price point and the relative reduce risk of physical harm and prosecution, cybercrime has surpassed drug trafficking as the biggest illegal revenue generating industry in the world. It already generates more illegal revenue than crude oil theft, human trafficking and small arms dealing combined.
Cyber criminals run highly organized and collaborative enterprises that operate with troubling and destructive efficiency. Juniper Networks conducted a study that found that global cybercrime takes in larger profits than the illegal drug trade. “The cyber black market has evolved from a varied landscape of discrete, ad hoc individuals into a network of highly organized groups, often connected with traditional crime groups (e.g., drug cartels, mafias, terrorist cells) and nation-states,” the report said. And even when the goals of the attackers are not monetary gain, the costs can be enormous. Though not a penny of its cash was stolen, the attack on Sony cost the entertainment company billions of dollars through the release of data. Types of data stolen can include financial data, personal health information (PHI) and associated insurance information.
What’s more, cyber attackers have adopted the practice of gaining strength in numbers. There is a network of collaboration these criminals easily tap into to help them with their schemes. With these hackers constantly working together to do damage to businesses, it only makes sense for businesses to start working together on a large scale.
_____
_____
Cyber-security:
Cybersecurity consists of technologies, processes and controls designed to protect systems, networks, programs, devices and data from cyberattacks. Effective cyber security reduces the risk of cyberattacks and protects against the unauthorised exploitation of systems, networks and technologies. Robust cyber security addresses people, processes and technology. We are living in a world where the information is maintained in as ‘0’s and ‘1’s. Privacy and security of data is a primary concern of most of the organizations. The capability to detect, investigate, analyze, and to respond to cyber threats and attacks is an indispensable component of cybersecurity. Cyber security is essential because cyber threats are existential. The United States government spends the largest amount of money every year on cyber security. The United States has a yearly budget of 28 billion dollars. Canada has the 2nd highest annual budget at 1 billion dollars. Australia has the third highest budget with only 70 million dollars.
Cybersecurity deals with the security of the cyberspace from cybercriminals. The cyberspace constitutes all those things (hardware, software, and data/information) that are connected to the Internet/network. It is important to implement the cybersecurity effectively to protect the Internet system and the trust of people on this system from various cyberattacks. A flaw in cybersecurity and an uncovered cyberspace will provide a chance to cyber-attackers to disrupt the Internet system. The three basic fundamental principles of cybersecurity are confidentiality, integrity, and availability. The three basic fundamental principles are also known as the CIA triad. The elements of the triad are considered as the most crucial components of cybersecurity. The cyberattacks on the information and data on the Internet can affect these three fundamental principles of cybersecurity. So, there is a great need to setup cybersecurity to preserve these fundamental principles. Cybersecurity that does not constitute these three fundamental principles is considered to be vulnerable to cyberattacks.
_
There are three elements of cyber security confidentiality, integrity, and availability.
_
Confidentiality:
In the present day, every person may have confidential information like login credentials (username and password), SSN, credit card information, and a soft copy of personal documents and work files which may be stored on the computer system or server or it may be on any device connected to the Internet which needs protection from cyberattacks. Access to confidential information must be restricted to an organization of authorized users only. The measure is to be taken according to the importance of data. The higher the importance of data, the higher the risk. So, serious measures are to be taken to protect the confidential information from cyberattacks to narrow down or eliminate the risk level. There are various methods which can be used to protect the confidentiality of information from the cyberattacks: data encryption, biometric verification, using strong user id and password, and user awareness.
Integrity:
Integrity means protecting the information and data on the Internet from alteration by cybercriminals. Integrity provides the consistency and accuracy of information on the network. The integrity of the information and data on the cyberspace can be preserved by taking appropriate steps like file permissions, user access controls, and digital signature. The bigger attacks are always the main attraction of security professionals. But security professionals cannot underestimate the small cybercrimes, as the number of small integrity attacks on information can make a huge impact on the infrastructure of an organization, state, or country. The information on the Internet might include cryptographic checksums to ensure the integrity. Backup must be maintained to recover from any tampering in information and data on the Internet due to cyberattacks or any natural calamities (earthquakes and tsunami).
Availability:
Availability is a security policy which ensures that any individual, employee of an organization (public or private), with authorized access can use information and data on the Internet according to the specified access level by its organization. Information which cannot be used by any authorized user is like waste in a dustbin. Server systems and computer systems must have sufficient capacity to satisfy user requests for access of information on the Internet. Availability of information can be disrupted by cyberattacks, natural calamities, and environmental factors.
Here are some cybercrimes that are classified according to the cybersecurity fundamental principles as shown in table below.
| Security goals | Objective | Recent incidents of cybercrimes in 2016-17 |
| Confidentiality | Limits the data access to authorized users only | (1) Confidential information of users of nine password manager apps like Dashlane, My Passwords, Password manager, etc. was found to be leaked. Methods used by attackers were data residue attacks and clipboard sniffing |
| (2) 85 million user accounts have been stolen from Dailymotion on 20 October 2016 | ||
| Integrity | Assures the accuracy of data | (1) Cyberattack on the Ukraine Kiev’s power grid caused the power outage on December 17 near midnight in the northern part |
| (2) Two weeks before the Trump’s presidency in America, a cyber-attacker hacked the radio stations to play “F∗∗k Donald Trump” across the country | ||
| Availability | Makes sure that authorized users always access the network and its resources | (1) Cyberattack affected 900,000 customers of Deutsche Telekom by knocking a million routers offline in November 2016 |
| (2) DDoS attacks on five major Russian banks disrupted the services of the bank to their customers for two days in November 2016 | ||
| (3) The WannaCry attack locked 90,000 computers in 99 countries and was ready to release them for a ransom of $300–$500 bitcoins |
_
Figure below shows Classification of cyberattacks on the basis of fundamental principles of cybersecurity.
_
Enormous economic and social benefits can be leveraged from modern information communications technologies. This fact has been repeatedly acknowledged by States in their commitments to a shared vision of an open, secure, accessible, and peaceful ICT environment. Yet, despite these benefits and commitments, the world has a serious ICT problem. The source of the problem is not just the technologies themselves, which are prone to vulnerabilities and flaws. Rather, human behaviour is a large part of the problem. Indeed, both State and non-State actors are using cyberspace and related ICT tools, techniques, and capabilities for a range of malicious purposes. The aggregate effect of these “cyber insecurities” is undermining trust in the technologies and related products and services. Moreover, it is undermining trust between governments, with important implications for international peace and security.
Such insecurities or uncertainties stem from the way different actors exploit ICT vulnerabilities, and the capacity of the targets to minimize the consequences and ensure business continuity. Consequences can be localized or, depending on the severity and the actors involved, escalate to the international level. A digital or cybersecurity threat begins when a specific actor learns about a vulnerability in an ICT, gains access to the technology, and then determines how to exploit the confidentiality, integrity, accessibility of the activities or the digital environment in which they are carried out or on which they directly or indirectly rely, generating immediate or indirect effects as seen in the figure below:
Figure above shows Cyber insecurities and their effects
_
Cybercrime is possible because computers and networks are not properly secured. Only by understanding how computer security works—and how it sometimes does not—can one predict where and how network attacks and intrusions will occur, track the actions of cybercriminals who break into systems, build evidence based on those break-ins, and help the victims of cybercrime protect themselves from future attacks. The first step in preventing cybercrime is to secure computer systems and networks against attacks. No system can be completely secure, but the goal of security is to present a barrier significant enough to repel most—if not all—attackers. Generally, the elements or issues that must be addressed to create a secure environment are the same for any type of system. But the specifics of how to implement a security policy and how to make individual security changes vary from one operating system to the next, and different technologies such as broadband, mainframe systems, and wireless networks present their own unique challenges. When planning security, one must take into consideration not only the method by which Internet access is brought to a system, but also the software programs used to interact with Internet-based resources. Web browsers are notoriously vulnerable to numerous attacks. However, with a bit of effort to keep the software up-to-date and configure settings for the best security, most common attacks can be avoided.
_
Cyber security is important because government, military, corporate, financial, and medical organizations collect, process, and store unprecedented amounts of data on computers and other devices. A significant portion of that data can be sensitive information, whether that be intellectual property, financial data, personal information, or other types of data for which unauthorized access or exposure could have negative consequences. Organizations transmit sensitive data across networks and to other devices in the course of doing businesses, and cyber security describes the discipline dedicated to protecting that information and the systems used to process or store it. As the volume and sophistication of cyberattacks grow, companies and organizations, especially those that are tasked with safeguarding information relating to national security, health, or financial records, need to take steps to protect their sensitive business and personnel information. Cyberattacks and digital spying are the top threat to national security, eclipsing even terrorism.
_
Various elements of cyber security:
For a strong cyber security system certain element are needed. The elements are as following:
- Application security: Applications play an essential role in business ventures; that is why every firm needs to focus on web application security. Web application security is important in order to protect customers, their information and interests. Application security helps in thwarting any attempts to violate the authorization limits set by the security policies of the computer system or networks.
- Information security: Information includes business records, personal data, customer’s data, intellectual property etc; hence, it is important for a corporation to have strong cyber security for information to prevent its leakage. Information security involves safeguarding sensitive information from illegitimate access, usage, or any other kind of damage. This also ensures that the important data does not get lost when any issue like natural disasters, malfunction of system, theft or other potentially damaging situation arises.
- Network Security: Network security consists of protecting the usability and reliability of network and data. A network penetration test is conducted to assess the vulnerabilities in a system and network. It refers to broad range security policies for thwarting and monitoring unauthorized access, misuse, damage to a computer system and other network systems. Network security extends coverage to diverse computer networks, surrounding private and public communication systems among corporations and organizations.
- Disaster Recovery/ Business continuity planning: Business continuity planning (BCP), also known as disaster recovery, is about being prepared for any kind of interference or cyber threat by identifying threats to the systems on time and analyzing how it may affect the operations and methods to counter that threat.
- Operational security (OPSEC): Operations security is used to protect organization functions. It identifies important information and assets to track down threats and vulnerabilities that exist in the functional method.
- End-user education: It is important for an organization to train their employees about cyber security because human error is one of the major causes of data breaches. Every employee should be aware of the common cyber threats and should have the knowledge to deal with them. Human error is the leading cause of data breaches, so you need to equip staff with the knowledge to deal with the threats they face. Training courses will show staff how security threats affect them and help them apply best-practice advice to real-world situations. Training will allow management to accustom themselves with system users and threats to it and user training will help in eliminating resistance to change and advancements and lead to user scrutiny on a closer level.
- Leadership commitment: It is important to have leadership commitment in organization and corporations in order to have a strong cyber security program. Without having the leadership in the team it is difficult to develop, implement and maintain the cyber security processes.
_
The legal, technical and institutional challenges posed by the issue of cybersecurity are global and far reaching, and can only be addressed through a coherent strategy taking into account the role of different stakeholders and existing initiatives, within a framework of international cooperation. In this regard, the World Summit on the Information Society (WSIS) recognized the real and significant risks posed by inadequate cybersecurity and the proliferation of cybercrime. At WSIS, world leaders and governments designated ITU to facilitate the implementation of WSIS Action Line C5, dedicated to building confidence and security in the use of ICTs. In this regard, the ITU Secretary-General launched the Global Cybersecurity Agenda (GCA) on 17 May 2007, alongside partners from governments, industry, regional and international organizations, academic and research institutions. The GCA is a global framework for dialogue and international cooperation to coordinate the international response to the growing challenges to cybersecurity and to enhance confidence and security in the information society. It builds on existing work, initiatives and partnerships with the objective of proposing global strategies to address today’s challenges related to building confidence and security in the use of ICTs. Within ITU, the GCA complements existing ITU work programs by facilitating the implementation of the three ITU Sectors’ cybersecurity activities, within a framework of international cooperation. The Global Cybersecurity Agenda has seven main strategic goals, built on five work areas: 1) Legal measures; 2) Technical and procedural measures; 3) Organizational structures; 4) Capacity building; and 5) International cooperation.
_
Security Methods:
Following are the security methods from keeping data and system secure from virus and cybercrime:
- Anti-virus:
Do not install multiple anti-virus program at same time. Installing multiple anti-virus at a time may cause your computer to run very slow or it may crash. Install only one anti-virus at a time and keep it updated. Make sure that your installed anti-virus program allows you to install new updates. Many tools are pre-installed on a new computer system needs paid registrations and at certain point these tools will stop working or stop getting new updates. There is need to ensure that the anti-virus software gets automatically updated itself regularly. Everyday new viruses are written and get spread through different ways. Never disable your anti-virus if you are installing any cracked software or game. When anti-virus is enabled it will delete some files of that software and that software will stop running. Disabling anti-virus may cause to crash of system or due to some virus your hard disk may get corrupt.
- Firewall:
Firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted internal network and untrusted external network, such as the Internet. A firewall is first program in a computer system and most important program, because firewall sees incoming data from internet. Firewall decides which data can enter into system and which data can leave the system. Firewall defends against untrusted connections from internet and from local networks.
- Keep Your Software And Operating System Updated:
Even if you have a good security installed on your computer, it will not protect computer if it is not updated. By updating operating system time to time it can give very good security from viruses and hackers and updated OS and software can eliminate bugs. Make sure that auto update is on. Try to avoid use of cracked operating system.
- Terminate Online Session Completely:
Closing the browser window or typing in a new website address without logging out may give others a chance of gaining access to your account information. Always terminate your online session by clicking on the “Log out or Sign Out” button. Avoid using the option of “remember” your username and password information.
- Two factor authentication:
Two factor authentication is a method of mitigating unauthorized access to a system or sensitive information. The idea is that the user “needs to know something” like their username or password and has “to have something” like a card, dongle, cellphone, or app. Two factor authentication improves security and reduces the impact of phishing and other social engineering attacks as an attacker needs credentials and the two factor authentication method to gain access.
- Virtual Keyboard:
A virtual keyboard is a computer keyboard that a user operates by typing on or within a wireless- or optical detectable surface or area rather than by depressing physical keys. Such a system can enable the user of a small handheld device, such as a cellular telephone or a PDA (personal digital assistant) to have full keyboard capability. In one technology, the keyboard is projected optically on a flat surface and, as the user touches the image of a key, the optical device detects the stroke and sends it to the computer. In another technology, the keyboard is projected on an area and selected keys are transmitted as wireless signals using the shortrange Bluetooth technology. Theoretically, with either approach, the keyboard could even be projected in space and the user could type by moving fingers through the air. The term virtual keyboard is sometimes used to mean a soft keyboard, which appears on a display screen as an image map. In some cases, a software-based keyboard can be customized. Depending on the host system and specific software, the user (who may be someone unable to use a regular keyboard) can use a touch screen or a mouse to select the keys. The Virtual Keyboard is designed to protect your password from malicious “Spyware” and “Trojan Programs”. Use of Virtual keyboard will reduce the risk of password theft.
- Backup most important data:
Backup of all the important files whether personal or professional should be created. Getting used to back up your files regularly is the first step towards security of your personal computer. For data that’s crucial, like medical information, or irreplaceable, like family photos, it’s important to keep copies. These backups should ideally be duplicated as well, with one stored locally on an external hard drive only periodically connected to your primary computer, and one remote, such as in a cloud storage system.
- Cryptography:
Cryptography is the science of encrypting and decrypting information. Encryption is like sending a postal mail to another party with a lock code on the envelope which is known only to the sender and the recipient. A number of cryptographic methods have been developed and some of them are still not cracked. Network Encryption is a security protocol implemented at the network level which encrypts data so network access is limited to authorized computers. Proxies is a security strategy which connects users to a remote location so that their data and information is encrypted. Proxies can allow users the ability to manipulate their shared information so a potential hacker would acquire wrong or misleading data.
If you can, encrypt the data that’s stored on your smartphone and computer. If a hacker copies your files, all he’ll get is gibberish, rather than, for instance, your address book and financial records. This often involves installing software or changing system settings. Some manufacturers do this without users even knowing, which helps improve everyone’s security.
A popular Internet security protocol that uses public key encryption is the Secure Sockets Layer (SSL). SSL is commonly used by browsers and Internet servers when transmitting confidential data. When implementing SSL protocols, a browser will indicate the URL with “https” instead of “http,” and, depending on the browser, a padlock icon appears either to the left of the URL or at the bottom of the page.
Cybersecurity Tips for Encryption:
- Any sensitive information that could be accessed by hackers or cyber criminals should be encrypted.
- Wireless devices are easier for cyber criminals to compromise than wired hardware. Because so much information is now transmitted over wireless networks, encryption becomes more important.
- Users should keep their private keys confidential and protected with passwords.
- Technology advances are leading to increased use of authentication based on biometrics, such as fingerprint, retina and face scans, as well as voice identification.
- Password management:
Almost half of the population uses ‘password’, ‘123456’ or ‘qwerty’ as their password. You should implement a password management policy that provides guidance to ensure staff create strong passwords and keep them secure. Ensure that your password is a mixture of words and special characters. Don’t have the same passwords for various social media accounts. Have multiple passwords for different accounts and try to use password manager in order to remember them. Remembering all passwords especially when using different passwords for different accounts is very difficult, so a password manager handles it for you to increase your security. A password manager stores your account details in an encrypted vault, allowing you to use a unique password on every website.
Encrypting a password is typically used to protect it from eavesdropping. Passwords remain the primary means for online authentication and must be protected when stored on a server. Encryption is an option, but it has an inherent weakness in this application because the server authenticating the password must have the key to decrypt it. An attacker who steals a file of encrypted passwords might also steal the key. Hashing is a better option. Encryption is a two-way function; what is encrypted can be decrypted with the proper key. Hashing, however, is a one-way function that scrambles plain text to produce a unique message digest. With a properly designed algorithm, there is no way to reverse the hashing process to reveal the original password. An attacker who steals a file of hashed passwords must then guess the password. Password should be hashed to protect against attackers who gain read-only access to the database where a server stores whatever it needs to verify passwords.
- Implement email security solutions and phishing simulations:
Considering the rise in business email compromise, phishing, and other email-related concerns, the modern virtual mailbox represents a significant area of cyber security vulnerability. Unlike physical messages sent by a physical mail carrier, emails can contain a variety of threats from attachments containing malware (often Microsoft Office files such as Excel spreadsheets and Word documents) to embedded links that direct users to malicious websites.
Many businesses tend to rely on the anti-spam filters that come with bundled with their email platform or antivirus programs to protect their business’s communications. However, there are additional third-party email solutions that you can use such as anti-phishing platforms and email signing certificates.
Anti-phishing platforms can automatically identify and even quarantine potentially dangerous emails so users can’t engage with them. Some anti phishing solutions even provide an educational component to help users understand why emails are being quarantined (such as a sender’s name not matching their email address or signature, embedded links directing users to dangerous websites, etc.). Email signing certificates allow users to digitally sign and encrypt emails containing sensitive or confidential information to avoid man-in-the-middle (MitM) attacks and eavesdropping. By signing your emails, it allows your recipients to authenticate that you are you and mitigates email tampering.
While putting these protections in place is exceedingly important, you still need to take it a step further and conduct periodic phishing simulations. This will allow you to test the cyber security awareness of your employees to assess how well they can apply the lessons from your training in real-life scenarios. Seeing whether employees are approaching email more judiciously or are opening every messages will help you recognize which employees are your biggest risks as well as identify new areas to address with cyber security and phishing awareness training.
- Monitor traffic and access to increase visibility:
This concept summarized the importance of IT threat monitoring. This function involves continuous monitoring of the traffic, access, and denial logs on your network and other IT infrastructure components such as servers and workstations. It can involve the use of security information and event management (SIEM) tools and intrusion detection/intrusion prevention systems (IDS/IPS) but also can include the services of a cyber security operations center (CSOC). A CSOC team can provide 24/7/365 monitoring of systems and logs to ensure that threats are identified and addressed to mitigate damage. This can be particularly helpful in monitoring traffic to identify distributed denial of service (DDoS) attacks, which can result in a slow network, iffy connectivity, or even website downtime.
- Regularly assess and test your systems:
Vulnerability assessments, risk assessments, and penetration tests are three methods of IT security which are related but having separate functions:
A vulnerability assessment helps to identify, assess, and prioritize any vulnerability in cyber security that may exist in your existing system.
A risk assessment, on the other hand, is useful for evaluating potential risks for specific tasks or events (if you did “A,” then X could happen as a result).
Lastly, penetration tests are your IT security team’s way of testing to see how your defenses can be breached or compromised.
The goal with these tools is to help you understand the strengths and weaknesses of your cyber security posture. This knowledge is just as valuable as knowing the strengths and weaknesses of your enemy — in this case, hackers or insider threats. This approach supports the ancient wisdom of Chinese military strategist Sun Tzu in (a translation of) his military treatise “The Art of War”:
Sun Tzu:
“If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.”
These tools are invaluable in terms of identifying network vulnerabilities, out-of-date software that need patching or updates, gaps in your existing cyber security defenses, and other cyber security vulnerability concerns.
- Cyber Liability Insurance – legal protection that can protect a business or organization from liability during a data breach. Cyber liability insurance has become important with the increasing number of social security and credit card numbers stolen.
__
CISO:
Cybersecurity risk management is generally set by leadership, often including an organization’s board of directors in the planning processes. Best-in-class organizations will also have a Chief Information Security Officer (CISO) who is directly responsible for establishing and maintaining the enterprise vision, strategy and program to ensure information assets and customer data is adequately protected.
Common cyber defense activities that a CISO will own include:
- Administering security procedures, training and testing
- Maintaining secure device configurations, up-to-date software, and vulnerability patches
- Deployment of intrusion detection systems and penetration testing
- Configuration of secure networks that can manage and protect business networks
- Deployment of data protection and loss prevention programs and monitoring
- Restriction of access to least required privilege
- Encryption of data where necessary
- Proper configuration of cloud services
- Implementation of vulnerability management with internal and third-party scans
- Recruitment and retention of cybersecurity professionals
When an organization does not have the scale to support a CISO or other cybersecurity professional, board members with experience in cybersecurity risk are extremely valuable.
_____
Computer protection (countermeasures):
In cyber security a countermeasure is an action, device, procedure, or technique that reduces a threat, a vulnerability, or an attack by eliminating or preventing it, by minimizing the harm it can cause, or by discovering and reporting it so that corrective action can be taken.
Some common countermeasures are listed below:
- Security by design
Security by design, or alternately secure by design, means that the software has been designed from the ground up to be secure. In this case, security is considered as a main feature.
Some of the techniques in this approach include:
-The principle of least privilege, where each part of the system has only the privileges that are needed for its function. That way even if an attacker gains access to that part, they have only limited access to the whole system.
-Automated theorem proving to prove the correctness of crucial software subsystems.
-Code reviews and unit testing, approaches to make modules more secure where formal correctness proofs are not possible.
-Defense in depth, where the design is such that more than one subsystem needs to be violated to compromise the integrity of the system and the information it holds.
-Default secure settings, and design to “fail secure” rather than “fail insecure” (see fail-safe for the equivalent in safety engineering). Ideally, a secure system should require a deliberate, conscious, knowledgeable and free decision on the part of legitimate authorities in order to make it insecure.
-Audit trails tracking system activity, so that when a security breach occurs, the mechanism and extent of the breach can be determined. Storing audit trails remotely, where they can only be appended to, can keep intruders from covering their tracks.
-Full disclosure of all vulnerabilities, to ensure that the “window of vulnerability” is kept as short as possible when bugs are discovered.
- Security architecture
The Open Security Architecture organization defines IT security architecture as “the design artifacts that describe how the security controls (security countermeasures) are positioned, and how they relate to the overall information technology architecture. These controls serve the purpose to maintain the system’s quality attributes: confidentiality, integrity, availability, accountability and assurance services”.
Techopedia defines security architecture as “a unified security design that addresses the necessities and potential risks involved in a certain scenario or environment. It also specifies when and where to apply security controls. The design process is generally reproducible.”
The key attributes of security architecture are:
-the relationship of different components and how they depend on each other.
-the determination of controls based on risk assessment, good practice, finances, and legal matters.
-the standardization of controls.
- Security measures
A state of computer “security” is the conceptual ideal, attained by the use of the three processes: threat prevention, detection, and response. These processes are based on various policies and system components, which include the following:
-User account access controls and cryptography can protect systems files and data, respectively.
-Firewalls are by far the most common prevention systems from a network security perspective as they can (if properly configured) shield access to internal network services, and block certain kinds of attacks through packet filtering. Firewalls can be both hardware- or software-based.
-Intrusion Detection System (IDS) products are designed to detect network attacks in-progress and assist in post-attack forensics, while audit trails and logs serve a similar function for individual systems.
-“Response” is necessarily defined by the assessed security requirements of an individual system and may cover the range from simple upgrade of protections to notification of legal authorities, counter-attacks, and the like. In some special cases, a complete destruction of the compromised system is favored, as it may happen that not all the compromised resources are detected.
Today, computer security comprises mainly “preventive” measures, like firewalls or an exit procedure. Some organizations are turning to big data platforms, such as Apache Hadoop, to extend data accessibility and machine learning to detect advanced persistent threats. Relatively few organisations maintain computer systems with effective detection systems, and fewer still have organized response mechanisms in place.
- Vulnerability management
Vulnerability management is the cycle of identifying, and remediating or mitigating vulnerabilities, especially in software and firmware. Vulnerability management is integral to computer security and network security. Vulnerabilities can be discovered with a vulnerability scanner, which analyzes a computer system in search of known vulnerabilities, such as open ports, insecure software configuration, and susceptibility to malware. Beyond vulnerability scanning, many organizations contract outside security auditors to run regular penetration tests against their systems to identify vulnerabilities. In some sectors, this is a contractual requirement.
- Reducing vulnerabilities
Two factor authentication is a method for mitigating unauthorized access to a system or sensitive information.
Enoculation, derived from inoculation theory, seeks to prevent social engineering and other fraudulent tricks or traps by instilling a resistance to persuasion attempts through exposure to similar or related attempts.
It is possible to reduce an attacker’s chances by keeping systems up to date with security patches and updates, using a security scanner or/and hiring competent people responsible for security.
- Hardware protection mechanisms
While hardware may be a source of insecurity, such as with microchip vulnerabilities maliciously introduced during the manufacturing process, hardware-based or assisted computer security also offers an alternative to software-only computer security. Using devices and methods such as dongles, trusted platform modules, intrusion-aware cases, drive locks, disabling USB ports, and mobile-enabled access may be considered more secure due to the physical access (or sophisticated backdoor access) required in order to be compromised.
- Secure operating systems
One use of the term “computer security” refers to technology that is used to implement secure operating systems. In the 1980s the United States Department of Defense (DoD) used the “Orange Book” standards, but the current international standard ISO/IEC 15408, “Common Criteria” defines a number of progressively more stringent Evaluation Assurance Levels. Many common operating systems meet the EAL4 standard of being “Methodically Designed, Tested and Reviewed”, but the formal verification required for the highest levels means that they are uncommon. An example of an EAL6 (“Semiformally Verified Design and Tested”) system is Integrity-178B, which is used in the Airbus A380 and several military jets.
- Secure coding
In software engineering, secure coding aims to guard against the accidental introduction of security vulnerabilities. It is also possible to create software designed from the ground up to be secure. Such systems are “secure by design”. Beyond this, formal verification aims to prove the correctness of the algorithms underlying a system; important for cryptographic protocols for example.
- Capabilities and access control lists
Within computer systems, two of many security models capable of enforcing privilege separation are access control lists (ACLs) and capability-based security. Using ACLs to confine programs has been proven to be insecure in many situations, such as if the host computer can be tricked into indirectly allowing restricted file access, an issue known as the confused deputy problem. It has also been shown that the promise of ACLs of giving access to an object to only one person can never be guaranteed in practice. Both of these problems are resolved by capabilities. This does not mean practical flaws exist in all ACL-based systems, but only that the designers of certain utilities must take responsibility to ensure that they do not introduce flaws.
Capabilities have been mostly restricted to research operating systems, while commercial OSs still use ACLs. Capabilities can, however, also be implemented at the language level, leading to a style of programming that is essentially a refinement of standard object-oriented design. An open source project in the area is the E language.
- End user security training
The end-user is widely recognized as the weakest link in the security chain and it is estimated that more than 90% of security incidents and breaches involve some kind of human error. Among the most commonly recorded forms of errors and misjudgement are poor password management, the inability to recognize misleading URLs and to identify fake websites and dangerous email attachments. A common mistake that users make is saving their user-ID/password in their browsers to make it easier to login to banking sites. This is a gift to attackers who have obtained access to a machine by some means. The risk may be mitigated by the use of two-factor authentication.
Many ISPs are strongly placed to play a valuable role in educating their customers as to the nature of the threats they face, and the techniques and tactics they can use to mitigate these.
- Digital hygiene
Related to end-user training, digital hygiene or cyber hygiene is a fundamental principle relating to information security and, as the analogy with personal hygiene shows, is the equivalent of establishing simple routine measures to minimise the risks from cyber threats. The assumption is that good cyber hygiene practices can give networked users another layer of protection, reducing the risk that one vulnerable node will be used to either mount attacks or compromise another node or network, especially from common cyberattacks.
As opposed to a purely technology-based defense against threats, cyber hygiene mostly regards routine measures that are technically simple to implement and mostly dependent on discipline or education. It can be thought of as an abstract list of tips or measures that have been demonstrated as having a positive effect on personal and/or collective digital security. As such, these measures can be performed by laypeople, not just security experts.
- Response to breaches
Responding forcefully to attempted security breaches (in the manner that one would for attempted physical security breaches) is often very difficult for a variety of reasons:
-Identifying attackers is difficult, as they are often in a different jurisdiction to the systems they attempt to breach, and operate through proxies, temporary anonymous dial-up accounts, wireless connections, and other anonymizing procedures which make back tracing difficult and are often located in yet another jurisdiction. If they successfully breach security, they are often able to delete logs to cover their tracks.
-The sheer number of attempted attacks is so large that organisations cannot spend time pursuing each attacker (a typical home user with a permanent (e.g., cable modem) connection will be attacked at least several times per day, so more attractive targets could be presumed to see many more). Note however, that most of the sheer bulk of these attacks are made by automated vulnerability scanners and computer worms.
-Law enforcement officers are often unfamiliar with information technology, and so lack the skills and interest in pursuing attackers. There are also budgetary constraints. In addition, the identification of attackers across a network may require logs from various points in the network and in many countries, the release of these records to law enforcement (with the exception of being voluntarily surrendered by a network administrator or a system administrator) requires a search warrant and, depending on the circumstances, the legal proceedings required can be drawn out to the point where the records are either regularly destroyed, or the information is no longer relevant.
____
VPN: Use Cyber Criminals’ own weapons against them:
Despite the rising number of attacks and the growing risk you will be hacked, attacked or have your data stolen there are things you can do to prevent it. One such tool is called VPN, virtual private network. The virtual private network is how cyber criminals are able to hide from law enforcement as it prevents their computer connections from being detected, monitored or tracked.
The technology itself dates back to the very start of the Internet itself and was originally intended as a security feature for government and big businesses. The VPN uses what is called a tunneling protocol to create secured connections that are undetectable and untraceable and then enhances that protection with data encryption. What its creators did not realize is that while they accomplished their goals the end result produced many unintended consequences. One of those is that VPN works just as well to protect a criminal as it does to protect an innocent.
The good news is that using VPN does a lot to enhance the security of today’s Internet users. It can be used to protect single devices or an entire network. It can be used to protect your family or business from outside attack, or to connect a remote device to a home network with safety. The best part is through its encryption, the technology that scrambles your data into unreadable gibberish, because it makes attacking a VPN user so difficult and time consuming, black hats are more likely to search for easier prey than waste their valuable time on you. Originally VPNs were only available to governments, big business or those with considerable cyber skills. Today top rated VPN services are available on a commercial basis.
Bottom line, cybercrime is here to stay and the only thing you can do about is be prepared. That means using antivirus, antimalware, Internet best practices and a VPN. You’ve probably already got the first three, why wait for something bad to happen, get VPN today.
______
Defense in Depth:
Defense in Depth (DiD) is an approach to cybersecurity in which a series of defensive mechanisms are layered in order to protect valuable data and information. If one mechanism fails, another steps up immediately to thwart an attack. Organisations can better prepare and protect themselves by creating layers of security, sometimes referred to as ‘Defense in Depth’. The intent is to not rely on a single solution or approach to security, but instead reduce the potential effectiveness of an attack by attempting to disrupt a threat actor at different stages during an attack. Threat actors carefully plan out their attacks, often studying the victim and their environment. When successful, they will reuse the techniques again and sometimes make them available on the black market. Approaches such as ‘Defense in Depth’ are meant to reduce the effectiveness of these attacks and make them less appealing to use.
Figure above sets out a summary of a typical cyberattack structure called the ‘Kill Chain’, overlaid with controls at each point. The Kill Chain describes the phases of a successful cyberattack, from ‘Reconnaissance’ to ‘Action on Objectives’. The overlaid controls provide a representation of how security can be layered in ‘Defense in Depth’ throughout IT systems to deter, detect and disrupt the attacker from accomplishing its goals. To mitigate threats, controls should be implemented strategically at each stage of the Kill Chain – so even if one control fails to stop the attacker, the next control can successfully mitigate an attack.
_____
How Microsoft helps reduce Cybercrime:
Microsoft says that the first step towards fighting cybercrime is to use secure, reliable and honest Information Technology spanning from firmware to operating system to the cloud. While it is true that a well-protected computer would reduce chances of it getting hacked, it is also true that many computers come with pre-installed malware. That is why Microsoft used the word “honest”. You may not believe that many computers have pirated software installed on them, and in a way that they give false positives so that users believe the software is genuine. There are not many methods to detect the fake software (except for manual forensic methods) and these software are often bundled with malware that sends your information to the cyber criminals who created the fake software. The Cybercrime page of Microsoft says that in a sample they tested, almost 90% of computers using pirated operating system or pirated software had the malware preinstalled. That means new Windows PCs were already infected and designed to send your personal information to the cyber criminals.
Microsoft has a huge cybercrime research cell which works in two ways:
1.Fight the malware that are utilized by criminals via spambots etc.
2.Gather information that helps them make better software for their cloud etc. platforms.
Microsoft has tapped the thousands of spambots originating from cybercriminals and led them to an artificial sink or honey pots, so that computers across the world, especially in East Asia-Pacific region are safe. According to their study, most of the infected computers are found in countries situated in East Asia and outside Europe. However, they, sitting at Redmond, are running an analysis all the while to counter whatever type of malware they can detect, and stop them from spreading any further to contain the damage.
There are some explosive findings of Microsoft India’s Truthlabs report:
- About 65 percent of the samples had more than one category of malware.
- Auto-Dialer Trojans, which can cause huge financial losses, were found in 100 percent of the samples.
- 90 percent of the samples in the form of DVDs gave false positive results in Anti-Piracy Checktests, thereby cheating users to believe the installed product to be a genuine one.
In the words of Keshav Dhakad, Regional Director of Intellectual Property & Digital Crimes Unit (DCU), Asia, Legal & Corporate Affairs, Microsoft,
“With fighting malware and cybercrime, we also want cybercriminals to know that Microsoft platforms will always remain hostile to their nefarious activities, and we will continue to invest ininnovative technology and tools to enable us to fight newer threats to protect our customers. That’s where we’ve been successful in creating a secure, trusted and reliable environment-be it on-premise or on the cloud”.
_____
Cybersecurity Solutions require a Multi-pronged Approach:
There isn’t a “one-size-fits-all” solution to cybersecurity. However, in general, solutions should include both sophisticated technology and more “human” components such as employee training and prioritization in the boardroom.
Real-time Intelligence:
Real-time intelligence is a powerful tool for preventing and containing cyberattacks. The longer it takes to identify a hack, the more costly its consequences. A 2013 study by the Ponemon Institute revealed that IT executives believe that less than 10 minutes of advance notification of a security breach is sufficient time to disable the threat. With just 60 seconds’ notification of a compromise, resulting costs could be reduced by 40%.
According to James Hatch, director of cyber services at BAE Systems, “Detecting [a cyberattack] early is key…It could be the difference between losing 10% of your [computers] and 50%.” Unfortunately, in reality, on average it takes companies more than seven months to discover a malicious attack.
Complementary Actions:
Companies can take several smaller, tactical steps to protect themselves. These include:
- Enacting a multi-layered defense strategy. Ensure that it covers your entire enterprise, all endpoints, mobile devices, applications, and data. Where possible, utilize encryption and two- or three-factor authentication for network and data access.
- Performing a third-party vendor assessment or creating service-level agreements with third parties: Implement a “least privilege” policy regarding who and what others can access. Make it a habit to review the use of credentials with third parties. You could even take it a step further with a service level agreement (SLA), which contractually obligates that third parties comply with your company’s security policies. Your SLA should give your company the right to audit the third party’s compliance.
- Continuously backing-up data. This can help to safeguard against ransomware, which freezes computer files until the victim meets the monetary demands. Backing up data can prove critical if your computers or servers get locked because you wouldn’t need to pay for access to your data.
- Patching frequently. A software patch is a code update in existing software. They are often temporary fixes between full releases of software. A patch may fix a software bug, address new security vulnerability, address software stability issues, or install new drivers.
- Whitelisting software applications. Application whitelisting would prevent computers from installing non-approved software. This allows administrators to have much more control.
Anti-hacker Insurance:
An emerging trend is anti-hacker insurance, or cyber-insurance. Its scope varies across providers, but typically protects against security breaches and losses. Insurers typically limit their capacity to between $5 million and $100 million per client. As of October 2016, only 29% of US business had purchased cyber-insurance. However, the overall cyber-insurance market is estimated to be $20 billion by 2025, up from $3.25 billion today. Insurers are bullish, estimating that premiums will triple over the next few years. For an organization to determine how much cyber insurance it needs, it should measure its cyber risk. It must understand how their assets are impacted by a cyberattack and how to prioritize them.
Bug Bounty Programs:
Another new idea in the industry is something called a bug bounty program, where an organization pays outsiders (“friendly hackers”) to notify it of security flaws. Companies ranging from Google and Dropbox to AT&T and LinkedIn have already adopted this practice.
______
______
Mobile security:
The amount of malware installed on Android platforms has increased by 400 percent. Part of the problem is the fact that individuals are much more relaxed when it comes to their smartphones than their computers. While 72 percent of users have free antivirus software on their laptop computer, only 50 percent have any kind of protection on their phone. Bear in mind, this is dangerous because mobile devices are now handheld personal assistants. They’re used to track everything from work-related information to family and friends to health information to finances. They’re a one-size-fits-all gadget and if any phones are the victim of cybercrime then all of that data becomes accessible to the hacker.
_
Attacks via smartphones:
One of the most common attack vectors to smartphones are related to unsafe browsing (phishing, spear phishing, malware). More than 60% of fraud online is accomplished through mobile platforms, according to RSA, and 80% of mobile fraud is achieved through mobile apps instead of mobile web browsers. As most people use their phones to manage financial operations or handle sensitive data outside the security of their home network, this becomes a prominent threat. The fact that users typically hold all their information on their phone, and that smartphones are now used for two-factor authentication – one of the most widely used cybersecurity tools – increases the security risk if the device is lost or stolen.
_
Increased use of Mobile Technologies by Customers:
Due to a growing number of online targets, hacking has become easier than ever. In consumer banking, usage of mobile devices and apps have exploded. According to a 2014 Bain & Company study, mobile is the most-used banking channel in 13 of 22 countries and comprises 30% of all interactions globally. In addition, consumers have adopted mobile payment systems. For banks competing with fintech startups, customer convenience will remain important. They may have to weigh the potential fraud losses with losses from a more inconvenient user experience. Some institutions are utilizing advanced authentication to confront these added security risks, allowing customers to access their accounts via voice and facial recognition.
_
Mobile security solutions:
- Mobile antivirus:
–Scanners for Android, but iOS’s isolation model prevents implementing on iOS devices
–Effective at detecting known threats, but provide little protection against unknown threats; expect traditional scanners to be replaced by cloud enabled, reputation-based protection
–Addresses threats in malware threat category and subset of malware based attacks in resource abuse, data loss and data integrity categories
- Secure browser:
–Secure browser apps for iOS and Android checks visited URLs against blacklist or reputation database and blocks malicious pages
–User must use the third-party secure Web browser to do all surfing
–Secure browsers address Web-based attacks and social engineering attacks; can also potentially block malware downloaded through browser
- Mobile device management (MDM)
–Enables admins to remotely manage iOS and Android devices
–Admins can set security policies such as password strength, VPN settings, screen lock duration; can also disable specific device functions, wipe missing devices and use the device’s GPS to locate missing device
–Doesn’t specifically protect against any one threat category, but helps reduce risk of attack from many categories
- Enterprise Sandbox
–Aims to provide secure environment where enterprise resources such as email, calendar, contacts, corporate websites and sensitive documents can be accessed
–Essentially divides device’s contents into two zones: secure zone for the enterprise data, and insecure zone for the employee’s personal and private data.
–Focused on preventing malicious and unintentional data loss; though doesn’t block other attack categories explicitly, does limit impact of other attacks
- Data loss prevention (DLP)
–Scan publicly accessible storage areas of device for sensitive materials
–Due to iOS’s isolation system, iOS-based DLP tools only inspect calendar and contact lists
–On Android, could scan external flash storage, email and SMS inboxes, as well as calendar and contact lists
–Due to isolation models, unable to scan data of other apps
_
Google android vs. Apple iOS
Apple’s iOS operating system has long been considered the more secure of the two operating systems. Apple’s operating system is a closed system. Apple doesn’t release its source code to app developers, and the owners of iPhones and iPads can’t modify the code on their phones themselves. This makes it more difficult for hackers to find vulnerabilities on iOS-powered devices. Android devices are the opposite, relying on an open-source code, meaning that the owners of these devices can tinker with their phone’s and tablet’s operating systems. Too much tinkering, and owners might create a weakness in their devices’ security. Then there are manufacturers themselves. If a phone maker puts out a new device with a modification to the Android operating system and there’s a vulnerability in that code, hackers will find it. Android is more often targeted by hackers, too, because the operating system powers so many mobile devices today. The global popularity of the Android operating system makes it a more attractive target for cybercriminals. Android devices, therefore, are more at risk of the malware and viruses that these criminals unleash.
While iOS may be considered more secure, it’s not impossible for cybercriminals to hit iPhones or iPads. The owners of both Android and iOS devices need to be aware of possible malware and viruses, and be careful when downloading apps from third-party app stores. It’s safest to download apps from trusted sources, such as Google Play and the Apple App Store, which vet the apps they sell.
_______
_______
Cloud security:
There is a clear and obvious trend for the greater adoption of cloud computing. More and more businesses are deploying IT services and applications in this way as they seek simpler management, utility-based payments and less reliance on traditional datacentres and admin teams. It would be rare to find an organisation that hasn’t adopted PaaS, IaaS or SaaS for some of their hosting or business applications.
Similarly, the threat from cybercrime is at least as omnipresent and is also clearly growing all the time; driven by an increasingly versatile adversary, complete reliance on IT systems to run the business and a growing technical complexity of platforms, applications, interactions and devices. The reasons for this growth are simple, in the same way cloud computing gives greater flexibility and functionality options to companies, it can offer the same flexibility to cyber criminals, and the pay-as-you-play usage model means that they can also benefit from utility billing (and might not have to pay at all).
For companies, the challenge is a side-effect of the nature of cloud itself – in moving away from physical servers that you control, see, touch and manage directly to a cloud platform that can be anywhere, is virtual and isn’t under your direct control, you simplify the management and purchasing processes, but expose new vulnerabilities that derive from this more “arms-length” way of providing access to data and delivering IT capability.
- Criminals using cloud as a business platform
In the same way businesses look to leverage the cloud to host applications, run shop fronts or applications backends, deliver web sites, store and share files etc… organised cyber criminals will do likewise. The ability to run a global business (legitimate or not) and deliver services, applications, manage databases, deliver content, run discussion boards and helpdesks are all business activities that form part of the international ecosystem that makes up the criminal community. Much of this is of course underground (whether on the dark web or not) but the same ability businesses have to be global in reach and flexible in resourcing are available to those who might attack them also.
- Criminals using cloud to mount attacks like DoS
One thing that cybercrime has made extensive use of is the highly scalable “on demand” nature of cloud platforms. If you have a distributed denial of service attack to mount, one way is to harness millions of vulnerable, exploited computers into a botnet and use that to mount an attack. Another is to operate from a cloud platform that allows you to rapidly and temporarily ramp up your processing power and network bandwidth, mount the attack to take systems down temporarily and then scale it all back. Of course, there is a question as to how the cybercriminal pays for this service. Utility-based computing allows users to pay for what they need/use, to uncapped levels and be billed accordingly.
The advantage the cybercriminal has, compared to a “normal” cloud user, is that they can leverage this with no intention of paying whatsoever, either through the use of a credit card that has itself been the result of cybercrime, or by piggybacking their IT demands on top of those of a legitimate cloud customer business (who will only know this has happened when they get their service charges at the end of the month).
In fact, theft of IT resources in this way could be used to handle any peak of computing activity, crunching through a key space or password database to decrypt credentials or keys, mining bitcoins, sending large volumes of spam or phishing emails… anything where the computing power or network bandwidth costs are the limiting factor suddenly becomes possible when you don’t have to actually pick up the tab.
- Cloud as a platform for employee misuse
Cloud platforms provide ease-of-use, flexibility, global access and cheap IT resources to both companies and cyber criminals. They also of course provide a wealth of facilities and services to end users, people themselves. If a user wants a handy contact management system, or a place to store files that they can work on in the workplace or at home, or a translation service for text, or a social network/messaging app to communicate with business partners – the cloud is out there. It is probably free, it is probably flexible and it is probably available now, rather than at some future point in time when your IT department can deliver it.
However, it also exposes sensitive corporate data, maybe even personal data, outside the organisation’s control on an external application provider’s server or in their database.
It most likely allows access to the data from home systems that could be shared, might be missing anti-virus software or patches applied (and might already be compromised). For the employee, they have just found a neat way to solve a business problem, they won’t have read the T&Cs and almost certainly won’t be aware of the risks.
In short it is a bit of a security nightmare – so much so that it has a suitably dark name: “Shadow IT”. Shadow IT usage by employees might not be “cyber-crime”, but it still lets you lose a lot of data.
Additionally, if you are looking to steal or extract data maliciously the cloud helps as well. You can copy a file to a file upload service and bypass corporate email gateways with their filters on file sizes, types, content and detailed logging of message senders and recipients. If stealing customer lists, intellectual property, source code or other valuable data is your game, cloud storage makes it easy.
- Business cloud platforms are a cybercrime target
As businesses adopt the cloud, its widely known that common cloud platforms hold increasing amounts of valuable business data. Hence for an attacker it is not about finding a company to target, it is about finding a place on the cloud that isn’t as secure as it could be, taking the information that they find there and then worrying about whose information it is.
It is wrong to say the cloud is “less secure” than a businesses own IT infrastructure. In fact, a well-run, enterprise class cloud platform could easily be more resilient, robust and secure than the less well-run networks of the smaller businesses that use it as a platform. But the aggregation of data and common access methods will always make the cloud a target.
- Forensics in the cloud
The last thing to consider is the difference between on-premise and cloud when it comes to incident response and forensics. Here you have both pros and cons.
In a cloud environment there isn’t a physical server you can isolate and take to a lab and directly examine. It is nowhere to be found, so a breach might be harder to investigate given just the log and activity data and the current state of the configuration are available (both of which might have been modified/compromised by the attacker).
On the upside, you might be able to spin up an identical replacement (or a patched version thereof) and continue providing services without interruption, thus allowing you to take a server off-line more easily to examine it and diagnose the breach. This means you don’t have to suffer from letting service levels drop and upsetting customers.
In a nutshell, a physical server is easier to directly examine, investigate and diagnose; a cloud server is easier to replace.
_______
_______
First, second, and third-party strategies to combat cybercrime:
Convicting offenders is only one example of what Neal Kumar Katyal (2001) calls first-party strategies to combat cybercrime: those targeted at offenders. Katyal points out that many other strategies exist to raise perpetration costs, including those based on social norms and Internet architecture. Moreover, second-party strategies focusing on victim precaution can also reduce opportunities for crime; this includes not only awareness-raising or stimulating use of firewalls, but also changing our perceptions of victimhood when networks (rather than people) are being attacked. Finally, third party strategies engage third parties, such as Internet Service Providers, financial service providers, software and hardware manufacturers, and other possible capable guardians as an opportunity-reducing strategy.
Katyal’s notion of first-, second-, and third-party strategies provides a useful conceptual tool for discussing and devising a broad, comprehensive array of opportunity reducing measures. Particularly the use of digital architecture as a regulatory tool to combat cybercrime deserves more attention from governments than it does (Katyal, 2003), although there are also challenges and downsides to technical solutions that need to be factored into the equation (see, e.g., Reidenberg, 2003; Starr, 2004; Koops, 2008).
_____
_____
Cybersecurity as preventive measure:
The gargantuan task of knowing how to prevent cybercrime often comes down to nullifying cyber security threats and figuring out how to prevent cyberattacks. However, hackers’ continuously-changing tactics, a growing number of actors, and rapidly expanding technologies make it challenging for cyber security experts and businesses alike to stay a minimum of one step ahead of cybercriminals. Furthermore, there is no one singular method of 100% cybercrime prevention — understanding how to prevent cybercrime is about bringing together an effective combination of technologies, best practices, and procedures to craft the solution that is best for your business.
Cybercrime prevention is not a one-size-fits-all approach. Organizations of different sizes have different needs, threats, risk tolerances, vulnerabilities, and capabilities.
NIST, also known as the U.S. Commerce Department’s National Institute of Standards and Technology, is the go-to resource for cyber security professionals. Recently NIST released version 1.1 of its popular Cybersecurity Framework document, which outlines ways to improve cyber security for critical infrastructure. The goal of the document is to provide “a prioritized, flexible, repeatable, performance-based, and cost-effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks.” Ideally, the framework should be used to complement your organization’s existing cyber security program and risk management processes, not replace them, and outlines five concurrent and continuous “functions”— Identify, Protect, Detect, Respond, and Recover — to address cyber security risks as seen in the figure below:
_
Preventing cyberattacks would save organizations a lot of money and trouble, however, this may not be a practical approach. IBM contends that attacks are a matter of “when” not “if.” The numbers bear out this perspective. Cybersecurity incidents doubled in 2017 and more than 2.9 billion records were leaked from publicly disclosed incidents. Given the prevalence, if not inevitability of cyberattacks, organizations need to address response as much as prevention. IT analyst IDC notes that “as businesses adopt new technologies, their protection strategies must change to keep pace. These strategies must include stronger and more varied security mechanisms, but they must also include ways to recover quickly should a breach or an incident occur.” Organizations are adopting an approach of cyber resilience to gain this position of preventive security and rapid recovery. Cyber resilience encompasses data protection, disaster recovery and business continuity and resiliency practices. It combines them with advanced technologies to assess risks, protect applications and data, and recover rapidly during and after a cyberattack. IBM, aligning with the IDC view, has identified a five-point, cyber resilience lifecycle:
- Identify risks and vulnerabilities – Dynamic analysis (DAST), static analysis (SAST) and open source testing can help pinpoint business-critical applications and associated risks. Potential business impact of disruption is assessed against business continuity and disaster recovery readiness.
- Protect applications and data – The goal is to safeguard applications and data before they are leveraged. Air gapping — physically separating data as a fail-safe — is an effective way to secure back-up data from infection, particularly against malware that can rapidly traverse and infect connected systems.
- Detect data corruption and configuration anomalies – Organizations are looking to automated testing capabilities to detect changes in data and system configuration files, without disrupting business systems.
- Respond to changes in configuration and data – Unauthorized changes in configurations and data need to be rapidly addressed. Dashboard technologies can provide real-time visibility into open vulnerabilities and enable rapid, if not preventive, response.
- Recover access to critical applications and data – Should an attack be sustained, mission-critical applications and data (from air-gapped backup) must be restored rapidly. Automation and orchestration technologies use pre-determined workflows to restore an entire business process, application, database or discrete system with the click of a button.
_____
_____
Artificial intelligence (AI) against cyberattack:
The tech companies deploying AI to secure online networks are finding it increasingly useful in reducing — if not eliminating — the risks. Microsoft, which began using AI for digital security in 2012, blocked more than 1 billion malware messages using AI cyberdefense in 2017. While ransomware increased more than 350 percent between 2016 and 2017, Microsoft’s Office 365 has reached a 99.9 percent accuracy rate in detecting these attacks. Today, most of Microsoft’s fellow tech giants — including Salesforce, Amazon, Google, Facebook and Netflix — are also using AI to defend against online attacks, as are others throughout the tech industry.
At Microsoft, the company’s Cyber Defense Operations Center watches over its global cloud estate 24/7, and it has combined the expertise of its security personnel with advanced AI to detect and respond to threats in real time. Microsoft calls them cyber storm chasers — a nod, says Dispensa, to actual weather chasers, who, like cybersecurity researchers, predict threats to reduce their societal and economic impact. AI and machine learning require massive amounts of data to be effective, and Microsoft is rare in the breadth of information it has access to. From Windows to Hotmail to Office 365, its advanced AI systems sift through all of these signals and combine them, making it easy for researchers to spot potential threats and shut them down immediately. The cyber storm chasers also connect this rich data set with news and intelligence reports from across the industry to further identify potential risks. Threats uncovered each day show up immediately in their antivirus signatures, email protection and directly in their identity system where a user has become inadvertently compromised. Even with all that data, AI systems and a dedicated team of cyber storm chasers, Microsoft software missed a security flaw that WannaCry hackers took advantage of in their ransomware attack. The National Security Agency discovered the flaw, and Microsoft immediately sent updates to correct the error. The flaw still left many systems vulnerable, but since then, Microsoft has further invested in its security efforts.
Cisco’s Security Business Group employs machine learning to study traffic patterns and user behavior, and draws conclusions about normal and non-normal behavior. For example, if you forget your password nine times and suddenly remember it on the 10th try, it would raise an alarm. Using AI and machine learning, Cisco’s security-research team, Talos, has been able to reduce the time to detection (TTD) rate for cyberattacks. Cisco’s median TTD of 4.6 hours from November 2016 to October 2017 was well below the median of 39 hours in 2016. Though it doesn’t currently track year-over-year growth, Talos prevented 7.2 trillion attacks last year.
IBM — one of the world’s largest tech companies, with 380,000 employees — began training and implementing its supercomputer, Watson, for use in cybersecurity in 2016. Its behavioral biometrics technology uses machine learning to track mouse movements in real time and combines the information with learned behavior patterns and fraud patterns to distinguish real users from threat actors. IBM also employs Watson to read thousands of security blogs and articles published each year to stay on top of trends. Watson has been able to find threats 60 times faster than manual investigations, and decreases complex analysis time from one hour to less than one minute.
The boom of the Internet of things (IoT) means that there are ever more data points to track and more points of entry into systems. The use of machine learning and artificial intelligence (AI) can help address this problem, and at the same time mitigate the skills gap. These technologies can gather and analyze data, trace threats, search for vulnerabilities, respond to breaches, and thus reduce the IT team’s workload.
Some of the advantages that AI technology can bring to organizations are:
Prevention. With AI, systems can be developed to search for security flaws and deploy solutions in real time.
Detection. AI can help cybersecurity analysts to detect and analyze high risks incidents, and to investigate threats.
Response. Machine learning and artificial intelligence can segregate networks to isolate assets or to redirect attackers away from vulnerabilities or valuable data.
There’s much a human can read and process but AI can make correlations and provide all of the details associated with a particular threat actor, campaign or motivation for an attack. Helping organizations recover from an attack is just as critical as preventing them. People don’t always have the decision-making capability to deal with cyberattacks, but AI can advise solutions. AI and machine learning are still far from perfect, although when they come to a conclusion, these technologies have gone above and beyond anything a human could possibly do to make that same determination.
______
AI technology to prevent and detect cyber-frauds:
AI has gained a new wave of popularity recently due to the variety of reasons. One of them is, obviously, the adoption of new standards in security. The industry in whole moves to embrace promising technologies, and many bank institutions are already heading in that direction. As Narrative Science report says, 32% of respondents among banks confirmed using AI technologies such as predictive analytics, recommendation engines, voice recognition and response. Again, one of the most important uses of artificial intelligence in banking sphere concerns fraud detection. Banks are beginning to utilize AI to fight against cybercrime and address complex issues in real time. Over the last ten years, AI has significantly improved the monitoring process: now it’s is capable of learning in a fast-paced environment and respond to fraudsters’ techniques as they appear. Let’s take bank accounts. When an account activity is being monitored, some user patterns can be distinguished. This way, if there’s a sign of any abnormal activity, it’s being flagged for review. So, when a customer is trying to make a purchase using a debit or credit card, the detection mechanism can analyze transactions within 0.3 seconds, detecting fraud or approving non-fraudulent transactions without interruption to purchases. Such systems are trained to recognize potential fraud through supervised training, when the variety of random samples is manually classified as genuine or fraudulent. Subsequently, the algorithm learns from these manual classifications to determine the legitimacy of future activities on its own. Within several years, the strategic use of AI and machine learning will become an integral part of banking organizations’ security principles. AI can save banks considerable money by eliminating complex fraud cases and protecting their brand. Within several years, the strategic use of AI and machine learning will become an integral part of banking organizations’ security principles. AI can save banks considerable money by eliminating complex fraud cases and protecting their brand.
______
Implementing Blockchain Technology for Cyber Security:
Although originally invented for the cryptocurrencies (bitcoins), Blockchain technology can be very useful for tightening cybersecurity. Blockchain could reduce banks infrastructure costs by US$ 15-20 billion per annum by 2022. Owing to their distributed nature, blockchains provide no ‘hackable’ entrance or a central point of failure and, thereby, provide more security when compared with various present database-driven transactional structures.
Blockchain technology applications in Cybersecurity are as follows:
- Resolving the “lack of trust” problem between counterparties at the basic level
- Eliminates human intervention from the Authentication process
- Ensures decentralized storage
- Cryptographic security that protects that storage from unauthorized modification
- Has the potential to improve everything from improving data integrity and digital identities to enabling safer IoT devices to prevent DDoS attacks
- Provides traceability of all transactions
- Synchronized, consensus-based third-party validation on every recorded transaction
_____
Deception technology:
‘Deception technology’ is a rapidly advancing defence strategy which is finding favour with enterprises, both small and large, that are seeking innovative ways to outwit old foes. The term refers to the use of traps and decoys which resemble your genuine network and systems, including bogus files and simulated SCADA, IoT, and network infrastructure devices. These decoys can run real operating systems and applications to match that of production assets; the object of the exercise being to fool hackers and cyber-criminals into thinking they’ve discovered an unsecured entry point into your enterprise. Even the lightest engagement triggers an alert and enables your security team to begin monitoring and recording their behaviour, safely within the deception sandbox. Meanwhile, your team is acquiring valuable intelligence about what adversaries are looking for and how they’re going about it. That’s information you can use to inform your security strategy and strengthen your defences against future incursions. Early versions of honeypot deception technology was renowned for being difficult to manage and deploy. Machine learning has made deception technology extremely simple to deploy and operate. Additionally, only minimal time investment is needed to for ongoing management due to the accuracy and fidelity of the alerts. It is not uncommon to hear of overall operational time saving gains due to automated analysis, incident response, and time typically spent triaging an incident. Research suggests the global market for the technology is growing at more than 15 per cent a year and will be worth $US2.09 billion by 2021.
______
______
Cybercrime reporting, investigation, intelligence and forensic:
Sometimes cybercrime and hacking can be obvious, but often times a criminal’s methods are more subtle. How do you know?
- Computer
- Unexpected software installs on your computer
- Your mouse moves by itself and actually shows purpose
- Your antimalware software, task manager, or registry editor is disabled
- Standard programs or files won’t open or function properly
- Files you haven’t touched have been deleted or moved
- Your passwords have been changed without your consent
- Money is missing from your bank account or you get bill or calls about purchases you haven’t made
- Cell Phone
- Your battery is dying faster than usual and takes longer to charge
- Your phone is constantly warm when not charging or playing games
- Strange noises or echoing occurs during phone calls
- Your data usage skyrockets
_
Cybercrime can be particularly difficult to investigate and prosecute because it often crosses legal jurisdictions and even international boundaries. Additionally, an offender may disband one online criminal operation – only to start up a new activity with a new approach – before an incident even comes to the attention of the authorities. The good news is that federal, state and local law enforcement authorities are becoming more sophisticated about cybercrime and are devoting more resources to responding to these threats. Furthermore, over the past several years, many new anti-cybercrime statutes have been passed that empower federal, state and local authorities to investigate and prosecute these crimes. However, law enforcement needs your help to stop the nefarious behavior of cybercriminals and bring them to justice. If you believe your computer, website or email account has been illegally hacked, it’s important to alert the proper authorities as soon as possible. Failing to take action can allow the guilty party to continue preying on other unsuspecting victims. Hacking reports help authorities to not only track down the culprit but also to devise ways to improve security measures and prevent future hacking.
-Note any unusual activity on your website or with your various online accounts. Make a detailed list of the questionable behavior, documenting all pertinent details.
-Contact your Internet service provider or website hosting service. Alerting them of the suspected hacking can help them take action against any security breaches, preventing others from being hacked in a similar fashion.
-Report the suspected hacking activities to your local police. The local authorities will be able to use your report to determine if it fits into a pattern, with the information possibly helping track down the responsible parties.
– It’s important to learn the difference between a technical glitch or bug and a genuine hacking attempt. Just because your site isn’t working properly doesn’t necessarily mean it’s been hacked.
-Noticing programs on your computer you don’t remember installing could be one indication your computer has been illegally hacked. Unknown programs requesting firewall access may also be a sign that harmful programs have been placed on your computer.
-Scanning your computer and finding viruses, spyware and Trojans may be another possible indication of hacking. Many free virus scans exist to help you diagnose potential threats.
-After compromising your online accounts, hackers will often change your passwords. Contact your service provider immediately if you’re unable to log-in with existing passwords.
-Check your outgoing mail periodically to make certain your account hasn’t been compromised and used to send spam without your knowledge. If you detect spam, change your password immediately. Likewise, if you receive spam from a friend’s account, be sure and let him know so he can change his password.
_
Report cybercrimes online in India:
National Cyber Crime Reporting Portal (www.cybercrime.gov.in) is a citizen-centric initiative that will enable citizens to report cybercrimes online through the portal. All the cybercrime related complaints will be accessed by the concerned law enforcement agencies in the states and UTs for taking action as per law. This portal was launched on pilot basis on August 30, 2019 and it enables filing of all cybercrimes with specific focus on crimes against women, children, particularly child pornography, child sex abuse material, online content pertaining to rapes and gang rapes. So far, more than 700 police districts and more than 3,900 police stations have been connected with this portal, said the statement. After its successful completion, this portal can improve the capacity of the law enforcement agencies to investigate the cases and will improve success in prosecution and also focuses on specific crimes like financial crime and social media related crimes like stalking and cyber bullying.
_
Collect and Keep Evidence:
Even though you may not be asked to provide evidence when you first report the cybercrime, it is very important to keep any evidence you may have related to your complaint. Keep items in a safe location in the event you are requested to provide them for investigative or prosecutive evidence. Evidence may include, but is not limited to, the following:
-Canceled checks
-Certified or other mail receipts
-Chatroom or newsgroup text
-Credit card receipts
-Envelopes (if you received items via FedEx, UPS or U.S. Mail)
-Facsimiles
-Log files, if available, with date, time and time zone
-Social media messages
-Money order receipts
-Pamphlets or brochures
-Phone bills
-Printed or preferably electronic copies of emails (if printed, include full email header information)
-Printed or preferably electronic copies of web pages
-Wire receipts
____
Diffusion of cybercrime:
The broad diffusion of cybercriminal activities is an issue in computer crimes detection and prosecution. According to Jean-Loup Richet (Associate Professor at the Sorbonne Business School), technical expertise and accessibility no longer act as barriers to entry into cybercrime. Indeed, hacking is much less complex than it was a few years ago, as hacking communities have greatly diffused their knowledge through the Internet. Blogs and communities have hugely contributed to information sharing: beginners could benefit from older hackers’ knowledge and advice. Furthermore, hacking is cheaper than ever: before the cloud computing era, in order to spam or scam one needed a dedicated server, skills in server management, network configuration, and maintenance, knowledge of Internet service provider standards, etc. By comparison, a mail software-as-a-service is a scalable, inexpensive, bulk, and transactional e-mail-sending service for marketing purposes and could be easily set up for spam. Jean-Loup Richet explains that cloud computing could be helpful for a cybercriminal as a way to leverage his attack – brute-forcing a password, improve the reach of a botnet, or facilitating a spamming campaign.
_____
Cybercrime often goes unpunished:
For cyber criminals, the idiom “crime doesn’t pay” is laughable. Internet crime is worse than ever, and the reasons are clear: It’s highly lucrative and far less risky than, say, an old-fashioned bank heist. Until we take the necessary steps to increase the risk and lower the value of cybercrimes, we won’t be able to stop them.
To fully appreciate the risks and rewards of cybercrimes versus traditional crimes, consider the following statistics from the FBI: In 2010, bank robbers pulled off 5,628 heists and ran off with $43 million. (These numbers held steady in the first and second quarters of 2011.) The average robbery netted $7,643.
Further, the loot was recovered in 22 percent of cases. Often, the thieves wielded guns, so when caught, they faced long mandatory jail times. Injuries, death, and hostage situations occurred, though they constitute the minority of cases. Overall, physical bank robberies are high risk. Except in rare cases, you won’t strike it rich as a criminal, and you have a strong chance of getting caught and sentenced to jail.
Let’s compare that to Internet crime statistics. Per an FBI 2011 report, 300,000 people were victimized over the Internet to the tune of $1.1 billion. Although that averages out to only $3,666 per victim, the typical Internet hacker commits thousands to hundreds of thousands of these crimes and almost never gets caught. Those who get nabbed are unlikely to spend any time in jail, and when they do, they’ll probably serve, at most, a few years in a low-security facility.
In contrast, identity thieves almost never get caught. For instance, from 2003 to 2006, the FBI was able to arrest between only 1,200 and 1,600 identity thieves, and about a third of those cases resulted in convictions, much less jail time. To put this in further perspective, these crimes affected 8.3 million victims, nearly 4 percent of the entire U.S. adult population. This means that one identity thief was convicted for every 20,750 victims.
The conviction rate in 2010 was even worse. According to FBI’s 2010 Internet Crime Report, from 303,809 complaints, 1,420 prepared criminal cases resulted in a mere six convictions. That’s one jailed cybercriminal for every 50,635 victims, and these are just the cases significant enough to be reported to the FBI.
So rob a bank and face a one-in-four or one-in-five chance of doing hard time. Steal someone’s identity and your odds of being caught are almost infinitesimal. Until we make the Internet secure, cyber criminals will continue to pull off high-value, low-risk offenses.
_____
Limitations of police:
The cyber police have been able to solve just about 14% of the total 2,518 cybercrime cases registered in 2019 in Mumbai. This is a 6% drop from the year before, though cyber offences increased by over 83%, from 1,375 cases in 2018 to 2,518 in 2018. Mumbai Police say their major concern is that a rising number of people are falling victim to credit and debit card, and e-wallet frauds. A plague of ignorance and misplaced priorities in government and law enforcement, from neighborhood cops all the way up to international bodies, is allowing cyber-crime to run rampant. American statistics show only three in 1,000 cyber-crimes are actually prosecuted – the actual ratio could be closer to three in 100,000 as the FBI tends to underestimate the extent of cyber-crime. Police and agents are either told not to pursue online fraudsters or not given the training and resources to do so. We continue to blame users for not avoiding clicking on every phishing link. When a breach becomes public the response all too often is to blame the victim company. We are focusing on defending systems over identifying, pursuing, and bringing to justice the person behind the cyber-crime.
Police says people are regularly gunned down on the streets. So where exactly should they put their resources? To fight cybercrime? Or to fight crimes where people die? It’s all a matter of balancing. When you balance the damage done by cybercrime and compare it to a loss of life, it’s pretty obvious what’s more important.
National police forces and legal systems are finding it extremely difficult to keep up with the rapid growth of online crime. They have limited resources and expertise to investigate online criminal activity. The victims, police, prosecutors, and judges rarely uncover the full scope of the crimes that often take place across international boundaries. Action against the criminals is too slow, the arrests are few and far between, and too often the penalties are very light, especially compared with those attached to real-world crimes. Because of the low prioritization for prosecuting cybercriminals and the delays in launching effective cybercrime penalties, we are thereby sending the wrong message to the criminals and that’s why online crime is growing so fast. Right now would-be online criminals can see that the likelihood of their getting caught and punished is vanishingly small, yet the profits are great.
Police must balance both fiscal constraints and resource limitations. They simply cannot, organizationally, respond to every type of threat. If we are to keep up with the cybercriminals, the key is cooperation. The good news is that the computer security industry is quite unique in the way direct competitors help each other. We have to allocate more time and money to finding and snaring internet crooks, hauling them into court, and shutting down this criminality. In other words, proactively catching criminals will have long-term benefits, and that rather than focusing too hard on stopping staff clicking on phishing links, we should also go after the fraudsters sending the links in the first place.
One key problem is that police officers, at the city to state level, lack the basic skills to pursue online crimes, and instead hand cases off to overworked and undermanned specialized cybercrime units. As a result, in many cases, cybercrime falls through the cracks, considered too big for your neighborhood plod and not significant enough to catch the attention of elite federal or national cyber-crime investigation teams. One solution would be to expand the skill set of rank-and-file officers to include basic IT and data security techniques. Tech-savvy persons with professional degrees in IT or computer science should be recruited for the cyber police station as opposed to non-specialists. We need to rebalance resource investment in this area, we need to build cyber investigation-capable law enforcement. There is also the matter of international cooperation, and in that area authorities need to be a bit more creative.
For example, even though an online criminal may be shielded from extradition by operating out of somewhere like Russia, they almost inevitably expose themselves to arrest when they opt to spend their ill-gotten gains in Malta, Israel, and high-end destinations. To that end, building diplomatic ties and getting cooperation from law enforcement in other countries will be critical.
_____
Types of Cyber Crime Investigators:
Depending on your particular investigation needs, you may look for help from one of a variety of investigators:
- Computer forensics investigator: If you require evidence of activity on your computer, a computer forensics investigator can legally and accurately recover digital data. They also have the ability to resurface hidden or deleted data and emails.
- Cell Phones forensics investigator: A cellular forensic investigator will understand the different types of phones and will use this information to recover data, text messages, photographs, GPS, and other information.
- Computer security investigator: If your computer has been attacked by a criminal or compromised by an employee or family member, a computer security investigator can uncover the source of the attack and exactly what has been done to your computer. Through this investigation, you can discover whether your computer was used to perpetuate a crime and find out how to prevent future attacks.
- Computer crime investigator: A computer crime investigator can make sure that, if your system is used in a crime, the blame doesn’t fall on you. They can find out exactly what kind of crime was committed and can gather evidence to be used in court.
____
Digital Forensics and Cyber Forensics:
Digital forensics is a branch of forensic science which deals with recovery and investigation of digital or electronic data. This data can be from a computer system, mobile device, cloud service, and so on. Its various sub branches include computer forensics, network forensics, forensic data analysis, and mobile device forensics.
Cyber or computer forensics is the application of forensic science to collect, process, and interpret digital evidence to help in a criminal investigation and presenting digital evidence in a court of law. It is the branch of forensic science in which evidence is found in a computer or any other digital device and with increasing cybercrime, cyber forensics has now become crucial for public safety, national security, and law enforcement.
Cyber forensic techniques include:
- Cross-driven analysis that correlates data from multiple hard drives.
- Live analysis, which obtains data acquisitions before a PC is shut down.
- Deleted file recovery.
- Detecting data theft using Stochastic Forensics.
- Concealing a file, message, image, or video within another file using Steganography.
_
Computer forensic investigations go through five major standard digital forensic phases:
- Policy and Procedure Development
Law enforcement and government agencies are hiring experienced cyber security experts to draw proper guidelines, policies, and procedures to be followed during computer forensic investigation because data can be delicate and highly sensitive.
- Evidence Assessment
Evidence assessment is a critical part of digital forensics as it provides a clear understanding of the case details and includes examining hard drives, email accounts, social networking sites, and other digital archives for digital evidence linking someone to the crime. The investigators should also preserve the acquired evidence properly.
- Evidence Acquisition
During evidence acquisition, computer forensic investigators are subjected to follow the policies dedicated to preserving the integrity of potential evidence. This step should be completed carefully and legally as the documented evidence are crucial in the proceedings of a court case.
- Evidence Examination
The analysis of digital evidence provides details like the date, time, and location where the data were created and downloaded. It also helps the investigators to find the connection between uploading of files from storage devices to a public network.
- Reporting
Lastly, investigators need to report the whole process of investigation and evidences acquired and examined to the authorities. This is needed to ensure that all the guidelines, policies, and procedures have been followed throughout; it also ensures the authenticity and integrity of the data retrieved for the evidential reasons.
______
Computer anti-forensic tools:
Anti-forensics can be a computer investigator’s worst nightmare. Programmers design anti-forensic tools to make it hard or impossible to retrieve information during an investigation. Essentially, anti-forensics refers to any technique, gadget or software designed to hamper a computer investigation. Some criminals have found ways to make it even more difficult for investigators to find information on their systems. They use programs and applications known as anti-forensics. Detectives have to be aware of these programs and how to disable them if they want to access the information in computer systems.
There are dozens of ways people can hide information. Some programs can fool computers by changing the information in files’ headers. A file header is normally invisible to humans, but it’s extremely important — it tells the computer what kind of file the header is attached to. If you were to rename an mp3 file so that it had a .gif extension, the computer would still know the file was really an mp3 because of the information in the header. Some programs let you change the information in the header so that the computer thinks it’s a different kind of file. Detectives looking for a specific file format could skip over important evidence because it looked like it wasn’t relevant.
Other programs can divide files up into small sections and hide each section at the end of other files. Files often have unused space called slack space. With the right program, you can hide files by taking advantage of this slack space. It’s very challenging to retrieve and reassemble the hidden information.
It’s also possible to hide one file inside another. Executable files — files that computers recognize as programs — are particularly problematic. Programs called packers can insert executable files into other kinds of files, while tools called binders can bind multiple executable files together.
Encryption is another way to hide data. When you encrypt data, you use a complex set of rules called an algorithm to make the data unreadable. For example, the algorithm might change a text file into a seemingly meaningless collection of numbers and symbols. A person wanting to read the data would need the encryption’s key, which reverses the encryption process so that the numbers and symbols would become text. Without the key, detectives have to use computer programs designed to crack the encryption algorithm. The more sophisticated the algorithm, the longer it will take to decrypt it without a key.
Other anti-forensic tools can change the metadata attached to files. Metadata includes information like when a file was created or last altered. Normally you can’t change this information, but there are programs that can let a person alter the metadata attached to files. Imagine examining a file’s metadata and discovering that it says the file won’t exist for another three years and was last accessed a century ago. If the metadata is compromised, it makes it more difficult to present the evidence as reliable.
Some computer applications will erase data if an unauthorized user tries to access the system. Some programmers have examined how computer forensics programs work and have tried to create applications that either block or attack the programs themselves. If computer forensics specialists come up against such a criminal, they have to use caution and ingenuity to retrieve data.
A few people use anti-forensics to demonstrate how vulnerable and unreliable computer data can be. If you can’t be sure when a file was created, when it was last accessed or even if it ever existed, how can you justify using computer evidence in a court of law? While that may be a valid question, many countries do accept computer evidence in court, though the standards of evidence vary from one country to another.
_
Computer Forensics Tools:
The computer is a reliable witness that cannot lie. Digital evidence contains an unfiltered account of a suspect’s activity, recorded in his or her direct words and actions. But, some people say that using digital information as evidence is a bad idea. If it’s easy to change computer data, how can it be used as reliable evidence?
To identify all the hidden details that are left after or during an incident, the computer forensics is used. The purpose of computer forensics techniques is to search, preserve and analyze information on computer systems to find potential evidence for a trial. Computers are getting more powerful day by day, so the field of computer forensics must rapidly evolve. We have many computer forensic tools that are used to apply forensic techniques to the computer. Programmers have created many computer forensics applications. For many police departments, the choice of tools depends on department budgets and available expertise.
Here are a few computer forensics programs and devices that make computer investigations possible:
-Disk imaging software records the structure and contents of a hard drive. With such software, it’s possible to not only copy the information in a drive, but also preserve the way files are organized and their relationship to one another.
-Software or hardware write tools copy and reconstruct hard drives bit by bit. Both the software and hardware tools avoid changing any information. Some tools require investigators to remove hard drives from the suspect’s computer first before making a copy.
-Hashing tools compare original hard disks to copies. The tools analyze data and assign it a unique number. If the hash numbers on an original and a copy match, the copy is a perfect replica of the original.
-Investigators use file recovery programs to search for and restore deleted data. These programs locate data that the computer has marked for deletion but has not yet overwritten. Sometimes this results in an incomplete file, which can be more difficult to analyze.
-There are several programs designed to preserve the information in a computer’s random access memory (RAM). Unlike information on a hard drive, the data in RAM ceases to exist once someone shuts off the computer. Without the right software, this information could be lost easily.
-Analysis software sifts through all the information on a hard drive, looking for specific content. Because modern computers can hold gigabytes of information, it’s very difficult and time consuming to search computer files manually. For example, some analysis programs search and evaluate Internet cookies, which can help tell investigators about the suspect’s Internet activities. Other programs let investigators search for specific content that may be on the suspect’s computer system.
-Encryption decoding software and password cracking software are useful for accessing protected data.
Some Digital forensic tools are as follows:
Kali Linux:
Kali Linux is an open-source software that is maintained and funded by Offensive Security. It is a specially designed program for digital forensics and penetration testing.
Ophcrack:
This tool is mainly used for cracking the hashes, which are generated by the same files of windows. It offers a secure GUI system and allows you to runs on multiple platforms.
EnCase:
This software allows an investigator to image and examine data from hard disks and removable disks.
SafeBack:
SafeBack is mainly using for imaging the hard disks of Intel-based computer systems and restoring these images to some other hard disks.
Data dumper:
This is a command-line computer forensic tool. It is freely available for the UNIX Operating system, which can make exact copies of disks suitable for digital forensic analysis.
Md5sum:
A tool to check helps you to check data is copied to another storage successfully or not.
These tools are only useful as long as investigators follow the right procedures. Otherwise, a good defense lawyer could suggest that any evidence gathered in the computer investigation isn’t reliable. Of course, a few anti-forensics experts argue that no computer evidence is completely reliable.
Whether courts continue to accept computer evidence as reliable remains to be seen. Anti-forensics experts argue that it’s only a matter of time before someone proves in a court of law that manipulating computer data without being detected is both possible and plausible. If that’s the case, courts may have a hard time justifying the inclusion of computer evidence in a trial or investigation.
_____
Cybercrime Investigation:
A computer can be a source of evidence. Even where a computer is not directly used for criminal purposes, it may contain records of value to criminal investigators in the form of a logfile. In most countries Internet Service Providers are required, by law, to keep their logfiles for a predetermined amount of time. For example; a European wide Data Retention Directive (applicable to all EU member states) states that all e-mail traffic should be retained for a minimum of 12 months. There are many ways for cybercrime to take place, and investigations tend to start with an IP Address trace, however, that is not necessarily a factual basis upon which detectives can solve a case.
If the case is internet based, finding the internet protocol (IP) addresses is your first step in the investigation. An IP address consists of numbers and letter, and that series is attached to any data moving through the internet. In order to retrieve an IP address from some Internet Service Providers (ISP) you will need to subpoena, warrant, or court order the company for information.
What an IP address contains:
- who owns and operates the network address,
- associated domain name/ computer name,
- geolocation,
- email addresses, and
- local service provider identifier.
Judd Robbins, a computer scientist and leading expert in computer forensics, lists the following steps investigators should follow to retrieve computer evidence:
- Secure the computer system to ensure that the equipment and data are safe. This means the detectives must make sure that no unauthorized individual can access the computers or storage devices involved in the search. If the computer system connects to the Internet, detectives must sever the connection.
- Find every file on the computer system, including files that are encrypted, protected by passwords, hidden or deleted, but not yet overwritten. Investigators should make a copy of all the files on the system. This includes files on the computer’s hard drive or in other storage devices. Since accessing a file can alter it, it’s important that investigators only work from copies of files while searching for evidence. The original system should remain preserved and intact.
- Recover as much deleted information as possible using applications that can detect and retrieve deleted data.
- Reveal the contents of all hidden files with programs designed to detect the presence of hidden data.
- Decrypt and access protected files.
- Analyze special areas of the computer’s disks, including parts that are normally inaccessible. (In computer terms, unused space on a computer’s drive is called unallocated space. That space could contain files or parts of files that are relevant to the case.)
- Document every step of the procedure. It’s important for detectives to provide proof that their investigations preserved all the information on the computer system without changing or damaging it. Years can pass between an investigation and a trial, and without proper documentation, evidence may not be admissible. Robbins says that the documentation should include not only all the files and data recovered from the system, but also a report on the system’s physical layout and whether any files had encryption or were otherwise hidden.
- Be prepared to testify in court as an expert witness in computer forensics. Even when an investigation is complete, the detectives’ job may not be done. They may still need to provide testimony in court [source: Robbins].
All of these steps are important, but the first step is critical. If investigators can’t prove that they secured the computer system, the evidence they find may not be admissible. It’s also a big job. In the early days of computing, the system might have included a PC and a few floppy disks. Today, it could include multiple computers, disks, thumb drives, external drives, peripherals and Web servers.
______
Challenges for law-enforcement agencies:
Recent developments in ICTs have not only resulted in new cybercrimes and new criminal methods, but also new methods of investigating cybercrime. Advances in ICTs have greatly expanded the abilities of law-enforcement agencies. Conversely, offenders may use new tools to prevent identification and hamper investigation.
Law-enforcement agencies can now use the increasing power of computer systems and complex forensic software to speed up investigations and automate search procedures. It can prove difficult to automate investigation processes. While a keyword-based search for illegal content can be carried out easily, the identification of illegal pictures is more problematic. Hash-value based approaches are only successful if pictures have been rated previously, the hash value is stored in a database and the picture that was analysed has not been modified.
Forensic software is able to search automatically for child-pornography images by comparing the files on the hard disk of suspects with information about known images. For example, in late 2007, authorities found a number of pictures of the sexual abuse of children. In order to prevent identification, the offender had digitally modified the part of the pictures showing his face before publishing the pictures over the Internet. Computer forensic experts were able to unpick the modifications and reconstruct the suspect’s face. Although the successful investigation clearly demonstrates the potential of computer forensics, this case is no proof of a breakthrough in child-pornography investigation. If the offender had simply covered his face with a white spot, identification would have been impossible.
General challenges are enumerated below:
- Reliance on ICTs
- Technology is evolving rapidly
- Number of users
- Availability of devices and access
- Availability of information
- Missing mechanisms of control
- International dimensions
- Independence of location and presence at the crime site
- Automation
- Anonymity
- Encryption technology
- Speed of data exchange processes
- Speed of development
- Failure of traditional investigation instruments
- Irrelevance of geographic distance (no borders)
- Investigative Costs, Resources, Equipment, Training
- “Real Time” Investigations
- Jurisdiction
- Legal Issues
The investigation and prosecution of cybercrime presents a number of challenges for law-enforcement agencies. It is vital not only to educate the people involved in the fight against cybercrime, but also to draft adequate and effective legislation. Here I have very briefly reviewed key challenges to promoting cybersecurity. Detailed discussion is beyond the scope of this article.
______
Digital evidence:
There is no single definition of electronic or digital evidence. The United Kingdom (UK) Police and Criminal Evidence Code defines digital evidence as “all information contained in a computer”. A broader approach defines digital evidence as any data stored or transmitted using computer technology that supports the theory of how an offence occurred.
Digital evidence plays an important role in various phases of cybercrime investigations. It is in general possible to divide between two major phases: the investigation phase (identification of relevant evidence, collection and preservation of evidence, analysis of computer technology and digital evidence) and the presentation and use of evidence in court proceedings.
Challenges for digital evidence:
In the early days of computer technology, the ability of law enforcement to carry out investigations involving digital data was limited by a lack of computer forensic equipment and expertise. The growing importance of digital evidence has spawned an increasing number of computer forensic laboratories. Yet, while the logistical aspects of the issue can be solved fairly easily, a number of challenges remain.
- Need for scientific research and training
Digital evidence is a relatively new category of evidence and the field is developing fast. And despite the very limited time-frame available for basic scientific research, the procedures for searching, seizing and analysing digital evidence now already need to be based on scientifically reliable principles and procedures. Despite intensive research already undertaken there are various areas that require the attention of scientists. It is therefore important that scientific research in controversial areas such the reliability of evidence in general or the quantification of potential rates of error should continue. The impact of the constant evolution is not restricted to the need for ongoing scientific research. Given that developments might raise new challenges for forensic examination, it is necessary to be constantly training experts.
- Need for binding legal standards
Although computer and network technologies are used globally and the challenges related to the admissibility of digital evidence in court are – despite the different legal systems – similar, binding legal standards dealing with digital evidence have not been widely implemented. Only some countries have so far started to update their relevant legislation to enable courts to deal directly with digital evidence. As with regard to substantive criminal law and procedural instruments in the fight against cybercrime, here too there is a lack of global harmonization of legal standards, in the area of digital evidence.
- Quantitative aspects
The low costs compared to the storage of physical documents are giving rise to an increasing number of digital documents. Despite the availability of tools to automate search processes, identifying the relevant digital evidence on a storage device that can carry millions of documents is a logistical challenge for investigators.
- Reliance on expert statements
Analysing and evaluating digital evidence requires special skills and technical understanding which is not necessarily covered in the education received by judges, prosecutors and lawyers. They therefore rely increasingly on the support of experts in the recovery of digital evidence. While this situation is not significantly different from other sophisticated investigation techniques, such as DNA sequencing, it prompts the need for necessary debate on the consequences for such dependence. To avoid a negative influence, courts are encouraged to question the reliability of evidence and require qualification of the associated uncertainty.
- Fragile nature of digital evidence
Digital data are highly fragile and can so easily be deleted or modified that experts consider it alarming. Like other categories of evidence, digital data present some degree of uncertainty. To avoid a negative impact on reliability, the collection of digital evidence is often subject to certain technical requirements. The shutdown of a computer system will, for example, result in a loss of all memory stored in the RAM system memory unless special technical measures to prevent this process are applied. In cases where data are stored in a temporary memory, the technique of collecting the evidence can be different from the process of collecting traditional digital evidence. Such a sophisticated approach can be necessary, for example, if the suspect is using encryption technology and the investigators want to examine whether information stored in the RAM memory can help them to access encrypted information.
Modifications can be made both intentionally by the offender or accidentally by the investigators. A loss or modification of data can in the worst scenario lead to wrongful conviction.
As a consequence of its fragility, one of the most fundamental principles of computer forensics is the need to maintain the integrity of digital evidence. Integrity can in this context be defined as the property whereby digital data have not been altered in an unauthorized manner since the time they were created, transmitted or stored by an authorized source. Protecting integrity is necessary to ensure reliability and accuracy. Handling evidence of this kind requires standards and procedures in order to maintain an effective quality system. This includes general aspects such as case records, the use of widely accepted technology and procedures, and operation by qualified experts only, as well as the application of specific methods such as checksum, hash algorithm and digital signatures. The required methods are costly and cannot completely exclude the risks of alteration.
- Limited amount of data recorded
For many Internet users, it is surprising how much information about their activities is stored. The average user might not be aware that when accessing the Internet or carrying out specific actions like using a search engine he/she is leaving traces. These can be a valuable source of digital evidence in cybercrime investigation. Nonetheless, not all digital information generated during the use of computer technology is stored. Many actions and much information such as clicks and keystrokes are not retained unless special surveillance software is installed.
- Layer of abstraction
Even if a suspect’s activities create digital evidence, this evidence is separated in time from the events it records and is therefore more of a historic record than a live observation. In addition, the evidence is not necessarily personalized. If, for example, a suspect is using a public Internet café to access child pornography, the traces do not necessarily contain identity-related information that allows identification. Unless the suspect at the same time downloads his e-mails or uses services that require a registration, in which case a link is created. But as this is not necessarily the case, experts point out that this leads to a layer of abstraction that can introduce errors.
- Requirements related to infrastructure
The design of courtrooms has followed similar principles for decades and in some countries even centuries. Leaving aside aspects of security (e.g. installed metal detectors and x-ray machines) and comfort (e.g. air conditioning), it is possible to use a courtroom designed and equipped a hundred years ago for criminal proceedings. The need to deal with digital evidence raises challenges, in terms of the layer of abstraction and the fact that digital evidence cannot be presented without tools like printers or screens, has implications for the design of courtrooms. Screens need to be installed to ensure that the judges, prosecutor, defence lawyers, the accused and of course the jury are able to follow the presentation of evidence. Installing and maintaining such equipment generates significant cost for judicial systems.
- Changing technical environment
As pointed out above, technology is constantly changing. This calls for constant review of procedures and equipment as well as related training in order to ensure the suitability and effectiveness of investigations. With ever new versions of operating systems or software products, the way data relevant for investigations is stored can change. Similar developments take place with regard to the hardware. In the past, data were stored on floppy disks. Today, investigators will find that relevant information might be stored on MP3-players or in watches that include a USB-storage device. The challenges are not limited to keeping up with the latest trends in computer technology. Forensic experts also need to maintain equipment to deal with discontinued technology, such as floppy disks. In addition to changes in hardware, discontinued software needs to be accessible: files from discontinued software tools can often not be opened without using the original software.
It is also necessary to carefully study fundamental changes in user behaviour. The availability of broadband access and remote storage servers has, for example, influenced the way information is stored. While in the past investigators were able to focus on the suspect’s premises when searching for digital evidence, today they need to take into consideration that files might physically be stored abroad and accessed remotely by the suspect when necessary. The increasing use of cloud storage presents new challenges for investigators.
______
Cyber intelligence:
As cybercrime has proliferated, a professional ecosystem has evolved to support individuals and groups seeking to profit from cybercriminal activities. The ecosystem has become quite specialized, including malware developers, botnet operators, professional cybercrime groups, groups specializing in the sale of stolen content, and so forth. A few of the leading cybersecurity companies have the skills, resources and visibility to follow the activities of these individuals and group. A wide variety of information is available from these sources which can be used for defensive purposes, including technical indicators such as hashes of infected files or malicious IPs/URLs, as well as strategic information profiling the goals, techniques and campaigns of the profiled groups. Some of it is freely published, but consistent, on-going access typically requires subscribing to an adversary intelligence subscription service. Cyber Intelligence can be defined as the tracking, analyzing, and countering of digital security threats. The cyber intelligence community provides security against digital threats such ad viruses, hackers, and terrorists that aim to steal sensitive information over the Internet.
Cyber counter-intelligence:
If someone is going to attack your company, the best defense is a good offense. This is why, instead of acting preventively or reactively, this kind of company prefers to change things up, and catch the cybercriminal as they take their first steps. Cyber counter-intelligence also includes measures to identify, penetrate, or neutralize foreign operations that use cyber means as the primary tradecraft methodology, as well as foreign intelligence service collection efforts that use traditional methods to gauge cyber capabilities and intentions. It is generally accepted that conventional cyber security generally has failed. As such, Cyber Counter-intelligence (CCI) is fast gaining traction as a practicable approach to secure and advance our own interests effectively.
_____
Cybercriminal Profiling:
Forensic psychologists often employ deductive or inductive profiling in dealing with crimes committed in the physical world, applying these techniques to ascertain characteristics of criminals. Deductive profiling techniques involve the use of data, including crime scene evidence, forensic evidence, offender characteristics and victimology. In deductive profiling, the available information is processed by applying personal experiences, with the profiler assuming one or more facts of a case as self-evident about an offender or crime. Then, by following hunches and experience, arrive at conclusions. The ‘truth’ of facts or conclusions arrived at using deductive profiling depends upon the truth (i.e., contingent truth). Also, in the deductive profiling method, the conclusions are true if the hypothesis and the premises are true and valid. On the other hand, inductive criminal profiles are created by studying statistical data, including study of the demographic characteristics and behavioral patterns shared by criminals. Inductive profiling is also theory-driven and based on the available cases of crime. Inductive profiling relies on information collected through interviews with offenders, and this forms the foundation for investigators’ profiles. Again, the inductive profile technique involves hypothesis (formalized operational definitions) for testing, and coding of data to allow for statistical analysis.
Applicability of these techniques has been possible in crimes committed in the physical world. However, applicability of these techniques to deal with crimes committed in the digital world is still debatable. In the digital world, forensic psychologists have knowledge about the law, criminology and psychology. This can be used to better understand technological aspects relating to crime, in order to develop cyber-criminal profiles. As such, they are required to take an interdisciplinary approach when dealing with cybercrimes. Unfortunately, highlighted issues of tractability, geography, law and anonymity makes it difficult for forensic psychologists to collect information about criminals and cyber-crimes (Tompsett, Marshall, and Semmens, 2005). Again, most cyber-crimes go either unnoticed or unreported, and hence go unpunished. Importantly, it is possible to draw some parallels between non-cyber-crimes and cybercrimes. It is also possible to develop a profile from the existing techniques that can be used for law enforcement.
Profiling Techniques:
From the perspective of deductive profiling methods, cyber-criminal profile should be developed in a four-step process.
The four-step approach is:
- Victimology
- Motive identification.
- Identifying offender characteristics.
- Forensically analyzing digital evidence
The first step is victimology. Today, criminals victimize both organizations and individuals. This step involves understanding the aspects of organizations and individuals that attract cyber-criminals. Victimology helps security specialists understand an offender’s motive behind the crime. Victimology includes the following:
-Crimes committed for monitory purposes (e.g. hacking a company data base to steal information that can be sold to third parties)
-Crimes committed due to emotional reasons (e.g. cyber-stalking)
-Crimes driven by sexual impulses (e.g. paedophiles)
-Politically motivated crimes (e.g. cyber-terrorists)
-Crimes those are less dangerous in nature such as sharing copyrighted movies, software by individuals (Source: Shinder, 2010)
The second step is motive identification – what is the reason for the crime?
Victimology and motive leads to the third step – identifying offender characteristics. Several topologies and ways to classify cyber-criminals based on offender motives have been introduced (Rogers, 2006). However, changes in criminal behavior with the evolving technological environment necessitate modification of existing schemes. Other studies have suggested that crime can be addictive, and in the cyber world, criminals become addicted to the internet and computers (Nykodym et al, 2008). It is also argued this addiction, aided by various opportunities including the access and availability of the internet and computers, and fueled by criminal motives, could facilitate the making of a cyber-criminal. This understanding may be used in analyzing the modus operandi of cyber-criminal.
Modus operandi reflects criminal character (Lickiewicz, 2011). For instance, a cyber-criminal may destroy information by using a virus that is attached to an e-mail, while another may hack into a computer system by attacking the server with a view to stealing information. This suggests that one’s technical expertise helps him or her to understand the behavior of a cyber-criminal. A cyber-criminal may be required to have a level of technical efficacy successfully penetrate a sophisticated and secure network (Kirwan and Power, 2013). On the other hand, ‘script kiddie’ may use an already developed program to attack a computer system. It is worth noting that human elements, such as social engineering skills, possessed by some professional cyber-criminals should not be disregarded. This is because cyber-criminals with average technical skills can participate in a crime by employing simple techniques of subtle psychological manipulations and friendly persuasion. Kirwan and Power (2013) affirm that technical skills and other skills, including social skills and motives, determine the modus operandi of a cyber-offender.
Step four of the deductive cyber-profiling technique involves forensically analyzing digital evidence. Digital forensics are important, because it is the means through which a cyber-criminal profiler can trace the offender in the event there is no physical evidence (Kwan, Ray and Stephens, 2008). In the view of Lickiewicz (2011), not all criminals are traceable, as one of three cyber-criminals manages to remove or modify the audit trail by wiping their traceable digital footprints.
The four-step approach suggested is an iterative process. New information regarding the offender, motive, victim and forensic evidence could be revealed while in an investigation proceeds.
As for inductive profiling methods, they can be applied alongside the deductive techniques described above, to help deal with cyber-crimes. For example, statistical analysis data studying demographic characteristics and behavioral patterns shared by criminals, and breaches in cyber-security, could be employed to identify criminal attack trends such as motive for attack, type of victims who are likely to be targeted, and most common modes of attack used by cyber-criminals. This may help to identify serial offenders, and other cases with similar modus operandi.
Nykodym et al. (2005) point out that “the idea that an individual committing crime in cyberspace can fit a certain outline (a profile) may seem farfetched, but evidence suggests that certain distinguishing characteristics do regularly exist in cyber criminals”. Therefore, the possibility of using the tools and techniques discussed above might be worth testing in a practical scenario. Considering the exponential increase in the cyber-crimes that has been taking place lately, collaboration between practitioners and academic is needed. Such endeavours may help the law enforcement to “collect legally valid evidences from cyber- crimes so that appropriate actions can be taken against cyber criminals (Kwan et al. 2008).
In a nutshell,
Cyber-criminal profiling is a tool which could bring more offenders to justice.
______
______
The role of cybercrime law:
Cybercrime law identifies standards of acceptable behaviour for information and communication technology (ICT) users; establishes socio-legal sanctions for cybercrime; protects ICT users, in general, and mitigates and/or prevents harm to people, data, systems, services, and infrastructure, in particular; protects human rights; enables the investigation and prosecution of crimes committed online (outside of traditional real-world settings); and facilitates cooperation between countries on cybercrime matters (UNODC, 2013, p. 52). Cybercrime law provides rules of conduct and standards of behaviour for the use of the Internet, computers, and related digital technologies, and the actions of the public, government, and private organizations; rules of evidence and criminal procedure, and other criminal justice matters in cyberspace; and regulation to reduce risk and/or mitigate the harm done to individuals, organizations, and infrastructure should a cybercrime occur.
Accordingly, cybercrime law includes substantive, procedural and preventive law.
Substantive cybercrime law includes laws that prohibit specific types of cybercrime and punishes non-compliance with these laws. Cybercrime includes traditional, real-world (offline) crimes (e.g., fraud, forgery, organized crime, money-laundering, and theft) perpetrated in cyberspace that are ‘hybrid’ or ‘cyber-enabled’ crimes, as well as ‘new’ or ‘cyber-dependent’ crimes that have been made possible with the advent of the Internet and Internet-enabled digital technologies (Wall, 2007; Maras 2014; Maras, 2016). For these reasons, many countries have developed laws that are specifically designed to deal with cybercrime. For example, Germany, Japan, and China, have amended the relevant provisions of their criminal code to combat cybercrime. Countries have also used existing laws that were designed for real-world (offline) crime to target certain cybercrimes and cybercriminals. As another example, in Iraq, the existing civil code (Iraqi Civil Code No. 40 of 1951) and penal code (Iraqi Penal Code No. 111 of 1969) are used to prosecute real-world crimes (e.g., fraud, blackmail, identity theft) perpetrated via the Internet and digital technology. Some countries, instead of developing new special laws against cybercrime, amended their national legislation or codes, adding specific paragraphs to address cybercrime. With this practice, an interesting consequence for consideration has been that some countries decided to criminalize separately the illegal use of information and communication technology to commit any crime. Thus, if the perpetrator used illegal access in order to commit forgery or fraud, such behaviour would constitute two crimes at the same time.
Procedural law demarcates the processes and procedures to be followed to apply substantive law and the rules to enable the enforcement of substantive law. An important part of procedural law is criminal procedure, which includes comprehensive rules and guidelines on the manner in which suspected, accused, and convicted persons are to be handled and processed by the criminal justice system and its agents. Ultimately, procedural cybercrime law includes provisions on jurisdiction and investigative powers, rules of evidence and criminal procedure that relate to data collection, wiretapping, search and seizure, data preservation and data retention. Cybercrime presents certain unique challenges regarding procedure, especially with respect to jurisdiction, investigations, and digital evidence.
Preventive law focuses on regulation and risk mitigation. In the context of cybercrime, preventive legislation seeks to either prevent cybercrime or, at the very least, mitigate the damage resulting from the commission of a cybercrime (UNODC, 2013, 55). Data protection laws (e.g., the EU General Data Protection Regulation of 2016, and the African Union Convention on Cyber Security and Personal Data Protection of 2014) and cybersecurity laws (e.g., The Law of Ukraine on the Basic Principles of Ensuring the Cyber Security of Ukraine of 2017) are designed to lessen the material harms from criminal breaches of private data should a cybercrime occur, and/or minimize private vulnerability to cybercrime. Other laws enable criminal justice agents to identify, investigate, and prosecute cybercrime by ensuring the necessary tools, measures, and processes are in place to facilitate these actions (e.g., telecommunications and electronic communications service providers’ infrastructure is such that it enables wiretapping and data preservation). In the United States, the Communications Assistance for Law Enforcement Act (CALEA) of 1994 (codified at 47 U.S.C. § 1001-1010) required telecommunications service providers and equipment manufacturers to ensure that their services and products enable government agencies with lawful authorization (i.e., with the appropriate legal order) to access communications.
With escalations in reports of serious cybercrime, one would expect to see a corresponding increase in conviction rates (Broadhurst, Grabosky, Alazab, Chon, 2014; Kaspersky Lab, 2015; Ponemon Institute, 2015). However, this has not been the case with many investigations and prosecutions failing to get off the ground (Frolova, 2011; Onyshikiv & Bondarev, 2012; Zavrsnik, 2010). The chief causes of this outcome may be attributed to trans-jurisdictional barriers, subterfuge, and the inability of key stakeholders in criminal justice systems to grasp fundamental aspects of technology aided crime. In the same way that science influences the utility of forensic inquiry, the capacity of investigators, prosecutors, judges and jurors to understand illicit use of technology also directly impacts conviction rates (Dubord, 2008; Leibolt, 2010). The ease with which cybercrime crosses national borders, irreconcilable differences between national legal frameworks, and deceptions employed by cyber criminals impedes attribution, and prevents crime fighters from interrogating suspects and apprehending offenders. Cybercrime offending can be technically complex and legally intricate. Rapid advancements in the functionality of information communication technologies (ICTs) and innate disparities between systems of law globally are stark challenges for first responders, investigating authorities, forensic interrogators, prosecuting agencies, and administrators of criminal justice.
_____
Cyber Law Experts:
Cyber Law has become a multidisciplinary approach and hence specialization in handling cyber-crimes is required. Cyber law experts handle:
- Patent and Patent Infringements or other Business Cyber crimes
- Cyber Security for Identity thefts and Credit Cards and other financial transactions
- General Cyber Law
- Online Payment Frauds
- Copyright Infringement of software, music and video.
Cyber Law Implementation Professionals:
Many agencies play a role in cyber law implementation, which include the e-Governance agencies, law and enforcement agencies, cybercrime research cells and cyber forensic labs. Each of these would have a different category of professionals.
_____
_____
International dimensions of cybercrime:
Cybercrime often has an international dimension. E-mails with illegal content often pass through a number of countries during the transfer from sender to recipient, or illegal content is stored outside the country. Within cybercrime investigations, close cooperation between the countries involved is very important. The existing mutual legal assistance agreements are based on formal, complex and often time-consuming procedures, and in addition often do not cover computer-specific investigations. Setting up procedures for quick response to incidents, as well as requests for international cooperation, is therefore vital.
A number of countries base their mutual legal assistance regime on the principle of “dual criminality”. Investigations on a global level are generally limited to those crimes that are criminalized in all participating countries. Although there are a number of offences – such as the distribution of child pornography – that can be prosecuted in most jurisdictions, regional differences play an important role. One example is other types of illegal content, such as hate speech. The criminalization of illegal content differs in various countries. Material that can lawfully be distributed in one country can easily be illegal in another country.
The computer technology currently in use is basically the same around the world. Apart from language issues and power adapters, there is very little difference between the computer systems and cell phones sold in Asia and those sold in Europe. An analogous situation arises in relation to the Internet. Due to standardization, the network protocols used in countries on the African continent are the same as those used in the United States. Standardization enables users around the world to access the same services over the Internet.
The question is what effect the harmonization of global technical standards has on the development of the national criminal law. In terms of illegal content, Internet users can access information from around the world, enabling them to access information available legally abroad that could be illegal in their own country.
Theoretically, developments arising from technical standardization go far beyond the globalization of technology and services and could lead to the harmonization of national laws. However, as shown by the negotiations over the First Protocol to the Council of Europe Convention on Cybercrime (the “Convention on Cybercrime”), the principles of national law change much more slowly than technical developments.
Although the Internet may not recognize border controls, there are means to restrict access to certain information. The access provider can generally block certain websites and the service provider that stores a website can prevent access to information for those users on the basis of IP-addresses linked to a certain country (“IP-targeting”). Both measures can be circumvented, but are nevertheless instruments that can be used to retain territorial differences in a global network. The OpenNet Initiative reports that this kind of censorship is practised by about two dozen countries.
_____
International effort to curb cybercrime:
The Convention on Cybercrime, also known as the Budapest Convention on Cybercrime or the Budapest Convention, is the first international treaty seeking to address Internet and computer crime (cybercrime) by harmonizing national laws, improving investigative techniques, and increasing cooperation among nations. It was drawn up by the Council of Europe in Strasbourg, France, with the active participation of the Council of Europe’s observer states Canada, Japan, Philippines, South Africa and the United States. The Convention and its Explanatory Report was adopted by the Committee of Ministers of the Council of Europe at its 109th Session on 8 November 2001. It was opened for signature in Budapest, on 23 November 2001 and it entered into force on 1 July 2004. As of September 2019, 64 states have ratified the convention, while a further four states had signed the convention but not ratified it.
Since it entered into force, important countries like Brazil and India have declined to adopt the Convention on the grounds that they did not participate in its drafting. Russia opposes the Convention, stating that adoption would violate Russian sovereignty, and has usually refused to cooperate in law enforcement investigations relating to cybercrime. It is the first multilateral legally binding instrument to regulate cybercrime. Since 2018, India has been reconsidering its stand on the Convention after a surge in cybercrime, though concerns about sharing data with foreign agencies remain.
_
In 2011, Russia, China, Tajikistan and Uzbekistan submitted a draft of the International Code of Conduct for Information Security before the 66th UN General Assembly Meeting (United Nations General Assembly, 2011). The Code seeks observance of human rights and freedoms within the information space (Brown, 2015). Respect for the sovereignty, territorial integrity and political independence of all nation-states is also addressed, and the code pushes for the development of transparent multilateral and democratic international Internet governance arrangements (Kshetri, 2013). In 2015, Secretary of State John Kerry affirmed the view of the US during remarks made to an audience in South Korea. He stated that “basic rules of international law apply in cyberspace” and “countries should work together to deter and respond effectively to online threats” (U.S. Department of State, 2015). He also promoted the Budapest Convention as “the best…legal framework for working across borders to define what cybercrime is and how breaches of the law should be prevented and prosecuted” (U.S. Department of State, 2015).
However, without a universal cybercrime convention, cross-jurisdictional conflict of criminal laws raises the unavoidable dilemma of “what law should be applied to determine the legal effect of a person’s conduct when he does an act in one state which produces harmful effects in another” (Stimson, 1936). Cybercrime cases that demand cooperative mechanisms that are not provided for within existing legal instruments create significant difficulties for police and prosecuting agencies (Bermay & Godlove, 2012; Gercke, 2012; International Telecommunications Union, 2012). The following multilateral and bilateral instruments are only able to deliver solutions within certain contexts:
- Budapest Convention;
- United Nations Convention against Transnational Organized Crime (2000) and its three protocols;
- European Convention on Mutual Assistance in Criminal Matters (1959);
- Inter-American Convention on Mutual Assistance in Criminal Matters (1992);
- Stanford Draft International Convention to Enhance Protection from Cyber Crime and Terrorism (1999);
- Draft African Union Convention on the Establishment of a Credible Legal Framework for Cyber Security in Africa (2011); and
- Commonwealth Model Law on Computer and Computer Related Crime (2002).
On the global level, the United Nations Office on Drugs and Crime (UNODC) is the leading organisation, with a set of international instruments to fight cybercrime. Since cybercrime often involves an organised approach, the UNODC’s Convention against Transnational Organised Crime could be used in the fight against cybercrime. Additionally, Interpol facilitates a global network of 190 national police organisations, which plays a key role in the cross-border investigation of cybercrime.
CYBERPOL: The International Cyber Policing Organization Public Utility was established in Belgium by Royal Decree WL22/16.595 together with 136 Countries on the 22 July 2015. The first International Cyber Policing Summit took place on the 17 and 18 November 2015 attended by 110 officials and 8 ambassadors at the Palais Des Congres te Brussels. CYBERPOL predicted Cyber Crime will cost the global economy $1.2 Trillion by the end of 2019.
______
______
Cybercrime awareness:
The Norton Cyber Security Insights Report 2016 sets out to understand how consumers are personally impacted by cybercrime and puts a human face on the headlines dominating the news. This online survey of 20,907 consumers in 21 markets was commissioned by Norton to give a global view of online crime and the toll it takes on consumers.
Here are a few facts and figures from the 2016 Norton Cyber Security Insights Report that will change the way you think about cyber security.
- Forty percent of Millennials report having experienced cybercrime in the past year.
- Nearly three in 10 people cannot detect a phishing attack.
- Another 13 percent have to guess between a real message and a phishing email, meaning four in 10 are vulnerable.
- Eighty – six percent of people said they may have experienced a phishing incident.
- 7 in 10 consumers wish they could make their home Wi-Fi network more secure.
- Yet only 27 percent believe it is likely their home Wi-Fi network could be compromised.
_
Creating awareness on cybercrime:
A strong coordination and transparency on issues related to cybercrimes and security should be encouraged between Government, Netizen, and his primary groups and various stakeholders that he deals with. A normal individual who uses internet (Netizen) is connected with various stakeholders for various transactions and dealings on day to day basis. These stakeholders can be Schools / colleges that he belongs to; family members who use internet at home; Media that he follows; heads of the various govt. and private organizations that he comes across / depends on; banking sectors, retailer outlets and various shopping centers where netizen deals with money transactions; various website owners; Internet service providers; Fellow Internet users etc.
The Government can take initiative of creating awareness among netizens and stakeholders at various levels, with multiple approaches, like
- Inform and educate all the stakeholders on cybercrimes and security measures as they deal with general public on a larger scale through internet.
- Informing, educating and altering the netizens through those stakeholders that he deals with by using Internet for various transactions. For instance, the bank can take the responsibility to alert the customer through personal counselling or by providing information whenever required.
- Encouraging cross-flow of knowledge and information between media, cyber cells, ethical hackers and education sectors to reach the netizen in easiest and appropriate way.
- On the whole, the surveillance of the Government should be vigilant on all the stakeholders, and the netizens to make sure that — the required and updated information and awareness is happening; the rules, regulations and being followed within the crux of cyber laws and provisions; and the netizens is acting safe and secure with proper measures.
_
Learned Helplessness:
Symantec survey shows that less than 1 in 10 people (9%) claim that they feel ‘very’ safe online. Also, only half (51%) of adults asked, would change the way they behave online if they became a victim (Symantec, 2010). People might accept a situation, even if it feels unpleasant just because they cannot understand it or do not know enough about it. Following this point, one might argue that persons may accept cyber-attacks because of a sense of ‘learned helplessness’.
Due to a sense of learned helplessness and a lack of knowledge about online attacks and ways to resolve an incident, users may simply accept the possibility of being victims. Indirectly, a key question therefore becomes, whether they also accept the reality of impacts and hope that the severity is low. The anonymous nature of cybercrime, can lead to an acceptance that one (e.g., an individual, industry, government) will become a victim of cybercrime at some point. Moreover, the sense of learned helplessness can potentially also result in a low uptake of protective security behaviors.
Users are called upon to make many security-related decisions every day which can cause anxiety. These behaviors include: (a) not opening an email from a sender they do not recognize; (b) not accessing unknown attachments; (c) only downloading and running programs from trustworthy sources; (d) the use of anti-virus software and security software (e.g., firewall); and (e) creating regular backups. Some of these decisions can also cause the user feelings of anxiety due to a lack of knowledge about the possible implications of making incorrect decisions.
Members of the public have often reported a lack of knowledge about a number of key areas within the cybersecurity domain. A few examples are lack of knowledge about how to use security packages, how to secure their technology devices, and the threats online. Even when these individuals are aware of the threats, they may report that they do not understand them (Gross, Canetti and Vashdi, 2017). These low levels of public understanding of cyber-threats and security practices could lead to a lack of public engagement with security issues and a general loss of confidence in cyber and/or technology. This also has been seen in the domain of information privacy in the context of new forms of technology, where some users now consider privacy as ‘the boring bit’ (Williams, Nurse & Creese, 2017). These issues characterize the broad social impacts.
_____
_____
Cybercrime prevention:
One of the simplest ways you can participate in eradicating cybercrime is by learning how to protect yourself online and not be an easy target for cybercriminals. By learning how to protect your identity and information online, you become less vulnerable to the crime. Although online shopping and online banking have become everyday life for many people, always be aware of the trustworthiness of the website. Avoid using public computers for anything that requires credit card payment, and make sure the website you use to make online purchases or do anything with your banking is a fully legitimate and safe business. Keep your computer up-to-date with the latest security software, choose strong passwords and steer clear of suspicious emails or “special offers” that ask for your personal information often in the form of contests, sales or fake banks.
_
_
Some of the FBI’s recommendations:
Set strong passwords; use multi-factor authentication; use anti-virus software; back up important data; install patches and updates; do not click on links from untrusted sources; avoid using public Wi-Fi for sensitive activities; use privacy settings on social media sites; if you are a victim of a cybercrime, contact the local police and Internet Crime Complaint Center, also known as IC3 and submit a complaint; if your banking and/or personal information has been hacked, contact credit reporting agencies and alert your banks.
_
Here are steps you can take to avoid becoming a victim of cybercrime.
- Education – Hackers aren’t the only ones who can gain power from information. By educating yourself about the types of scams that exist on the Internet and how to avert them, you are putting yourself one step ahead of the cybercriminals. Since phishing is prevalent, read up on the latest phishing scams and learn how to recognize a phishing attempt. Remember, phishing is when hackers attempt to lure you into revealing personal information by pretending to be a legitimate organization or person. These scams often play off major new stories, so keep informed on the latest news-related scams.
- Use a firewall – Firewalls monitor traffic between your computer or network and the Internet and serve as a great first line of defense when it comes to keeping intruders out. Make sure to use the firewall that comes with your security software. And if you have a home wireless network, enable the firewall that comes with your router.
- Click with caution – When you’re checking your email or chatting over instant messenger (IM), be careful not to click on any links in messages from people you don’t know. The link could take you to a fake website that asks for your private information, such as user names and passwords, or it could download malware onto your computer. Even if the message is from someone you know, be cautious. Some viruses replicate and spread through email, so look for information that indicates that the message is legitimate.
- Practice safe surfing – When navigating the web, you need to take precautions to avoid phony websites that ask for your personal information and pages that contain malware. Use a search engine to help you navigate to the correct web address since it will correct misspellings. That way, you won’t wind up on a fake page at a commonly misspelled address. (Creating a phony site at an address similar to the real site is called “typosquatting,” and it is a fairly common scam.)
- Practice safe shopping – In addition to practicing safe surfing, you also need to be careful where you shop online. Be cautious when shopping at a site that you’ve never visited before and do a little investigation before you enter your payment information.
And when you’re on a payment page, look for the lock symbol in your browser, indicating that the site uses encryption, or scrambling, to keep your information safe. Click on the icon to make sure that the security certificate pertains to the site you are on.
You also want to look at the address bar to see if the site starts with “https://” instead of “http://” because this is another way to see if the site uses encryption.
When it comes time to pay, use a credit card instead of a debit card. If the site turns out to be fraudulent your credit card issuer may reimburse you for the charges, but with a debit card your money is gone.
Evaluate the site’s security and privacy policies in regards to your personal data.
Do not provide photocopies of both the sides of the credit card to anyone. The card verification value (CVV) which is required for online transactions is printed on the reverse of the card. Anyone can use the card for online purchases if the information is available with them. CVV must be kept secret.
- Use comprehensive security software and keep your system updated – Because hackers have a wide variety of ways to access your system and information, you need comprehensive security software that can protect you from all angles. Security Software can help protect you from malware, phishing, spyware, and other common and emerging threats.
Just make sure that you keep your security software up to date by selecting the automatic update function on your security control panel. And don’t forget to perform regular scans.
You also want to update your operating system (OS) and browser with the latest security patches. If you are a Microsoft Windows user, you can enable automatic updates to keep your OS safe.
- Secure your wireless network – Hackers can access data while it’s in transit on an unsecured wireless network. You can keep the hackers out by enabling the firewall on your router and changing the router’s administrator password. Cybercriminals often know the default passwords and they can use them to hack into your network.
You may also want to set up your router so it only allows access to people with passwords that are encrypted. Check your owner’s manual for instructions on setting up encryption.
Know the ins and out of public Wi-Fi networks: Accessing personal information on unprotected public Wi-Fi is like broadcasting your entire screen on TV – everything you do on a website or through an app, could potentially be exposed. Avoid anything that involves sharing your personal information (paying a bill online, logging in to social media accounts, paying for anything with a credit card, etc.). If you must access the information over public Wi-Fi, consider using a Virtual Private Network (VPN) to secure your connection and help keep your information private.
- Use strong passwords – Although it may be easier for you to remember short passwords that reference your birthday, middle name, or pet’s name, these kinds of passwords also make it easy for hackers. Strong passwords can go a long way in helping secure your information, so choose a password that is at least 10 characters long and consists of a combination of letters, numbers and special characters. Also consider changing your password periodically to reduce the likelihood of it being compromised.
- Two-factor authentication – Anywhere you can use this, take advantage of making your account more secure. It is an extra layer of security which requires you to enter a unique code, sent to your phone, every time you log into your account.
- Use common sense – Despite the warnings, cybercrime is increasing, fueled by common mistakes people make such as responding to spam and downloading attachments from people they don’t know. So, use common sense whenever you’re on the Internet. Never post personal information online or share sensitive information such as your social security number and credit card number. Exercise caution when clicking on any links or downloading any programs.
- Be suspicious – Even if you consider yourself cyber savvy, you still need to keep your guard up for any new tricks and be proactive about your safety. Backup your data regularly in case anything goes wrong, and monitor your accounts and credit reports to make sure that a hacker has not stolen your information or identity.
Although protecting yourself does take some effort, remember that there are a lot of resources and tools to help you. And by adopting a few precautions and best practices, you can help keep cybercrime from growing.
- Never reveal personally – identifiable information online. A lot of creeps use the Internet to take advantage of other people, especially kids and teens. Never reveal any personally-identifiable information online, whether it’s on your profile page or in a blog, chatroom, instant messenger chat or email.
- Always use a screen name instead of your real name.
- Never give out your address, telephone number, hangout spots or links to other websites or pages where this information is available.
- Be careful about sending pictures to people you do not know very well.
- Never tell people personal or private information about your friends or family.
- Never assume you’re completely anonymous online. Even if you don’t put personal information online, there are different ways that people can still figure out who you are and where you live.
- Never arrange meetings with strangers.
Just because you’ve seen a person’s picture and read his or her profile, does not mean you know them. Many people online lie about who they are and what their intentions are. Just because someone seems nice online, does not mean they really are. They could be trying to hurt you. Never arrange a meeting with a stranger you’ve met online. Even meeting a stranger in a crowded place could be dangerous as he could follow you home. If you wish to meet an online friend in person, talk to your parents and arrange a time and place where your friend can meet your parents first, just in case. If you are worried about your parents meeting one of your online friends, you probably shouldn’t be friends with them in the first place.
- Online Banking Tips
- Never use unprotected PCs at cyber cafes for internet banking.
- Never keep your pin and cards together.
- Never leave the PC unattended when using internet banking in a public place.
- Register for Mobile SMS , Email Transaction Alerts.
- Never reply to emails asking for your password or pin.
- Visit banks website by typing the URL in the address bar.
- Log off and close your browser when you have finished using internet banking.
- Memorize your PIN. Never carry your PIN.
- Report lost or stolen card immediately.
- If You have any of the following symptoms, your computer may be infected
- Does your computer suddenly take longer to start up?
- Do program sizes keep changing?
- Do you keep running out of disk space?
- Do you keep getting 32 bit error messages?
- Your computer won’t boot up.
- File names are strange or keep changing.
- You can’t access your hard drive without booting from a floppy startup disk.
- Your computers CMOS settings keep changing – and you have a new CMOS battery.
- Your computer is sending out emails that you didn’t write.
- Strange unexplained things are happening with your computer; e.g. the CD ROM opens and closes when no one is using the computer.
- Monitor your children’s Internet activity by checking all of the sites visited.
- Use a VPN
VPN services are becoming more popular every year, and it’s completely natural to use one if you plan on keeping third party companies (especially your ISP) from spying on your online activities. Another reason to use a VPN may be to log into your secure network from a remote place, including when you use untrustworthy internet connections on the road while travelling, or when you are merely away from home.
- Get insured
The market for cyber security insurance has boomed in the last couple of years, and it’s now something that companies of all sizes need to think about. Cyber security insurance isn’t only about protecting against financial risk. If your company is hit by a data breach, there’s a lot of damage to contain, and you may need help with that from the kind of experts and damage-limitation specialists your insurer could provide.
- Think about backup and recovery
A company is hit by ransomware every 40 seconds, but the irony is that no firm needs to pay a ransom if their backups and disaster recovery efforts are on point. Yes, such a cyberattack will cause annoyance and disruption, but if a backup is there, there’s no need to pay hackers any money. This probably strikes you as an extremely basic point. However, it’s clear that plenty of companies drop the ball. Otherwise, there wouldn’t be a statistic saying that nearly half of affected US companies end up paying ransoms to hackers! This indicates that an awful lot of companies don’t manage to get business continuity right, however obvious the need for it may seem. This is not only about ransomware – reliable backups back all kinds of hacks and breaches easier to recover from.
- Always Monitor Your Accounts
Cybercrime prevention techniques aren’t always perfect, but you can limit the damage by monitoring your accounts. Even when you protect yourself, the sites you use may still experience a breach. Keep an eye on your credit card and bank statements and check your credit report. If you do spot strange activity, contact your bank or credit card company immediately. They can put a hold on your account to prevent any further charges and may even refund unauthorized charges.
_____
_____
Here are some of the areas that future cyber criminals would focus on:
Data protection and privacy: The parameter of data protection already serves as a great challenge with respect to online services. The future of data aggregation, globalized sensor proliferation, and personalization would require the augmented services to adopt common legal frameworks to ensure security and privacy. Countries might exercise sovereignty rights for setting their specific rules with respect to when data should be stored and processed by different authorities for reliable and legitimate purposes. Cyber criminals might have found a new resource in the form of Aadhaar, which is linked to vital information sources such as bank accounts and mobile numbers of every Indian. It is important for authorities to be on their toes in safeguarding the same from future unknown hacking techniques.
Identity and reputation: For businesses, industries, governments, and citizens; identity and reputation are going to be everything. As such, damage due to a potential cybercrime could be significant and difficult to restore or repair. Identity theft and espionage would be a lucrative focus for cybercriminals to either launch attacks using stolen data or through direct extortion from individuals and businesses.
Cryptocurrency mining: Cryptocurrencies can be mined using computational power, and profits can be earned as arbitrage between value of coins mined and the cost of infrastructure and power. Cybercriminals can exploit private and government infrastructure by deploying malware for mining cryptocurrencies in an unauthorised manner. From one compromised server in a data center, a hacker can easily mine $2,000 a month. This would cause loss of business, hardware damage and increased costs for the victims.
Cyber-jacking: Instead of physically hijacking a plane, cyber criminals can hack into the management systems of aircrafts and hijack or crash a plane.
Human malware: Hackers can target pacemakers, cardioverter-defibrillators, insulin pumps, and other such devices. Researchers have demonstrated that it is possible for hackers to break into your implant and cause collateral damage.
Quantum computing: High-speed computers with tremendous computing power are being developed to assist artificial intelligence applications, robotics and machine learning. The computing power of these machines can easily break the current encryption technologies and cause havoc if they get into the hands of a cybercriminal.
Industrial espionage: Cyberattacks in the future will be geared towards industries of prime importance such as power, energy, oil and nuclear power. Such attacks can disrupt the critical infrastructure of a country, especially if done through a state-sponsored platform.
______
______
Final comments:
For the security of the nation and its economy, opposing the growing phenomenon of cybercrime is a crucial issue. Events of cybercrime are becoming increasingly widespread, and their impact on the world economy is becoming alarming. As stated in the UNODC report, the majority of cyber-attacks are of a transnational nature; this means that it is difficult to fight them just locally. There is a need to come up with a global response through a shared set of rules and common technological development road maps. The implementation of cyber security policies is a prerogative of each State, but it is important to incentivize International cooperation as well as public and private partnerships regarding this phenomenon.
The difficulty in facing this type of crime is in the discrepancy between the tools and the knowledge available to cyber criminals and the tools and knowledge available to those who have to defend themselves or are tasked with opposing this phenomenon. The tools to conduct a cyberattack are becoming more powerful and easier to locate and use, as well as being relatively cheap. The skills necessary to conduct a cyber-attack are diminishing. With little effort, a criminal can equip himself with the necessary tools and information to carry out this task, and the development of the dark web further simplifies things. The fight against cybercrime requires strong legislative actions, mechanisms for law enforcement, adequate instruments, collaboration, but most importantly knowledge.
Law enforcement agencies and companies have the difficult task of opposing and defending themselves from every type of known cyber-attack. While on the other hand, more and more often, criminals specialize in a specific type of attack and refine their techniques to reach high levels of efficiency, and develop new ones, often unknown to those who have to oppose this phenomenon. If we look at the evolution of phishing, we are no longer in the presence of fraudulent e-mails written incorrectly and easily identifiable, but instead we are witnessing an increase in spear phishing and targeted actions that are extremely difficult to recognize. The results, from a prosecutorial point of view, are unclear in this field; the problem is not due to a lack of pressing charges or from a lack of personnel, but it can be traced back to the nature of the phenomenon. As such, it is easier to work on prevention. What has emerged that this type of crime is very difficult to prosecute, and this currently constitutes the ideal situation for cyber criminals. They can continue to augment their capacities, their profits and their network, as well as provide fertile ground for illicit activity and be an example for others involved in organized crime or terrorism.
There are some elements that unfortunately don’t help in reducing the gap between the intensity of this phenomenon and the real capacity to defend ourselves from these attacks. Elements such as the speed with which cyber criminals reinvent themselves, their level of specialization and the quantity of resources they dedicate to their crimes will always be greater than the defensive efforts. Furthermore, the border between the types of various cyber attackers is diminishing day by day, and there is an increase in the relationship between cyber criminality and ordinary criminality, which is now using new technologies to expand the scope of their illicit activities by collaborating directly with cyber criminals or purchasing from them the tools and necessary resources to commit cybercrimes themselves.
Another factor that makes the fight against cybercrime more challenging is the difficulty in determining a singular type of victim. All web users (citizens, SMEs, large enterprises, States) are potential victims.
It is also useful to consider the psychological aspect of cybercrimes. The perceptions of danger in physical security and cyber security are completely different and influenced by personal experience. Physical theft is well understood, the virtual one a little less. In fact, none of us today would ever leave our front door open or a wallet unattended in a public place, but when it comes to cyber security, we are not able to see our weaknesses due to the tendency not to consider the virtual as real. Also, from a psychological point of view, the neutrality of the computer monitor destroys our ability to see the effects of our actions, both from the point of view of the criminal and that of the victim. The desensitization that occurs through the use of a PC prevents the cybercriminal from understanding the extent of the damage he is inflicting on the victim. The consequence of this is that the victim is downgraded to the status of just an IP address. The same process happens to the user, who lowers his/her guard on the web, loses inhibitions and underestimates the dangers of the web. This might lead him to click on a link received via e-mail or share personal information on social platforms. The ease with which we are inclined to communicate with unknown people via chat or webcam are examples of habits that we would probably never replicate as lightly in the real world. In addition, the physical distance between the cyber-criminal and the victim amplifies these aspects.
The human factor is a determining element in this type of crime, which frequently exploits human weaknesses for its own gains. Cyber criminals count on small human errors to convince a user to click on a link in a phishing e-mail that will lead to an infection of the PC, or push somebody into revealing personal information about themselves, counting on the habit of not checking the reliability of the person on the other side of the monitor. Cyber security is not a status to be acquired, but a mentality that needs to be adopted at 360 degrees in one’s private life and especially within one’s company or at one’s job. Only in this way can we achieve valid and long-lasting results. Even in the case of SMEs, the human element plays a fundamental role. Negligence in the workplace is one of the major causes, together with the system’s flaws and hacker attacks, of the loss of company data, which can lead to the loss of business and a loss of trust in the company by its clients, an enormous tragedy for an SME.
An SME might not think of itself as an appetizing target for a cyber-criminal, especially if they produce goods not related to ICT. In reality, it is the small and vulnerable companies which constitute an easy target, and the biggest problem is that they are not aware of that. A very common attitude of SMEs regarding cybercrime has emerged in that they prefer to pay for the damages following an attack as opposed to investing in prevention. We have to consider that it is not just the company victim of an on-line fraud attack that suffers, but indirectly the whole economic system, the market, and local institutions suffer as well.
Cybersecurity is a shared responsibility and requires the attention of a broad range of stakeholders. It requires an effective public/private partnership that incorporates businesses and institutions of all sizes along with national, state, local, tribal and territorial agencies to produce successful outcomes in identifying and addressing threats, vulnerabilities and overall risk in cyberspace. Individual consumers also have a role, and adding cybersecurity to schools as well as higher education curriculums will help raise awareness for all users. Teaching users how to better protect themselves is a necessary component to any strategy. Cyber space and cybercrime, its control, impact and all other aspects should be made part of school and college syllabi to make students aware of the field.
We continue to blame users for not avoiding clicking on every phishing link; and when a breach becomes public the response all too often is to blame the victim company. The entire world is focusing on defending systems rather than identifying, pursuing, and bringing to justice the person behind the cyber-crime. We need the new approach: catch the cybercriminal at any cost by whatever means available. The actual cybercriminals and the potential cybercriminals must realise that it is no longer low-risk crime and they will be caught and punished. Only then cyberattacks will be reduced. Cyber education, cyber hygiene, cyber vigilance and cyber security are not good enough, we need cyber arrests and cyber jail terms.
Remember; cybercriminals are one step ahead of cybersecurity by continuously-changing tactics, finding unknown vulnerabilities, delete logs to cover their tracks. and developing new modus operandi.
Remember; swift, certain and consistent punishment is the only way cybercrime will be curtailed.
______
______
Moral of the story:
_
- The computer technology and the network protocols currently in use are basically the same around the world. We are living in the world where most information is maintained in ‘0’s and ‘1’s. Confidentiality, integrity, and availability of data is a primary concern of everybody.
_
- There is no internationally accepted definition of cybercrime. Cybercrime is a term used to broadly describe criminal activity in which computers, hardware devices and computer networks are a tool, a target, or a place of criminal activity. The sine qua non of cybercrime is involvement at any stage of the virtual cyber medium. Cybercrime includes traditional, real-world (offline) crimes (e.g., fraud, forgery, organized crime, money-laundering, and theft) perpetrated in cyberspace i.e. ‘hybrid’ or ‘cyber-enabled’ crimes, as well as ‘new’ or ‘cyber-dependent’ crimes that have been made possible with the advent of the Internet and Internet-enabled digital technologies. Cybercrime really presents a continuum ranging from crime which is almost entirely technological in nature and crime which is really, at its core, entirely people-related. Just as concept of crime has undergone change with the growth of Information Technology, so the categories of criminals who engage in such crimes.
_
- A vulnerability is a weakness in design, implementation, operation or internal control of information & communication system. Vulnerability is a cybersecurity term that refers to a defect in a system that can leave it open to attack. Vulnerabilities are hunted and exploited by cybercriminals to carry out cybercrimes. Both technical and human vulnerabilities, which when identified, can be exploited by cybercriminals. Technical vulnerabilities include code errors, failure to install security patches for programs or systems used by the victim, failure to update antivirus and anti-malware, the incorrect configuration or failure of devices and corporate networks, or the use of repetitive passwords or passwords which are too simple. Human vulnerabilities include human error, poor password management, distraction, superficiality, greed, negligence, altruism, confidence, and curiosity. A resource (both physical and logical), called an asset, can have one or more vulnerabilities that can be exploited by a threat and cause harm. Threat actors could be individuals, ideological groups, organized criminals, nation-state actors, terrorists, disgruntled customer/ex-employee, insider, business partner, competitor, hacktivist, hobbyist etc.
_
- Cyber deviance refers to inappropriate or criminal behavior in a digital context and such behavior is not part of cyber citizenship, where individuals behave in an ethical and productive manner in online environments. The boundaries of acceptable and unacceptable cyber behavior are defined by government authorities, who develop laws around specific illegal online behaviors; and businesses, who detail inappropriate actions in their terms of service agreements. Cyber deviance overlaps with cybercrime. Youth who have lower levels of self-control and more frequent association with deviant peers are more likely to take part in cyber deviant activities. Parents and educators can exert considerable influence on adolescents’ behavior to reduce cyber deviance.
_
- Cyberattack is any attempt to expose, alter, disable, destroy, steal or gain unauthorized access to or make unauthorized use of an asset in computers and computer networks. Cybercrimes present the general form whereas cyberattacks present the specific form of attacks on cybersecurity. Cyberattacks are committed for a variety of reasons including financial fraud, information theft, activist causes, to deny service, disrupt critical infrastructure and vital services of government or an organization. The 5 most cyber-attacked industries are— healthcare, manufacturing, financial services, government, and transportation. Depending on context, cyberattacks can be part of cyberwarfare or cyberterrorism.
_
- Historically, societies have utilized a two-pronged strategy for maintaining the order they require to survive and prosper. They maintain internal order by articulating and enforcing a set of proscriptive rules (“criminal rules”) that prevent the members of a society from preying upon each other in ways that undermine order, e.g., by killing, robbing, committing arson, etc. Societies maintain external order by relying on military force (“war”) and, to an increasing extent, international agreements. Cybercrimes undermine society’s ability to maintain internal and external order by using computer & internet to launch virtual attacks from anywhere in the world. And cyberattacks may not fit neatly into the internal-external threat dichotomy.
_
- As the world has made a shift from the physical to the digital landscape, security threats have also changed from physical to cyber. Along with the changing world, the nature of crimes has also transformed and become virtual. Acts of stealing, extorting, blackmail, illegal trading, etc. have now become, hacking, ransomware, online blackmailing and dark web trading. Criminals are often the first to exploit emergent technologies and turn their complexity against their users. We have to be aware of the increasing amount of opportunities to commit crime facilitated, enabled or amplified by the Internet. The Internet deserves special attention in criminology as well as criminal law and policy, because of several characteristics: it is global, instantaneous, intrinsically transborder, digital, and enables automated information processing. For many people, being online is no longer the exception but the norm, often without the individual being aware. In 2020 we have about 4.5 billion internet users, about 200 billion IoT connected devices and more than 1.7 billion websites. And we are unable to control the flow of electrons and electromagnetic waves across physical borders. This creates the broadest attack surface for criminals to fraud from anywhere on anyone.
_
- Computers, computer networks & systems, and different information distribution or delivery technologies & systems are referred to as “cyberspace”. Cyberspace enables the creation, storage, modification, exchange and exploitation of information via interdependent and interconnected networks using information communication technologies. Cyberspace is a virtual world and Internet is just a part of it. This website exists in cyberspace and accessed by you through internet. Two of the key characteristics of cyberspace are the vast number of users and the borderless nature of the Internet, where an act in one continent permeates to other distant continents, sometimes within minutes. The characteristics of cyberspace have not only provided a whole new class of targets for crime, but also led to an increase in the number of cyber-savvy individuals with ready means to commit crimes that have widespread impact. Risks from cyber space are considered as among the greatest perceived risks in terms of impact and likelihood of occurrence.
_
- In contrast to traditional crime where criminals need to be physically present at the crime scene and can commit one offence at a time, criminals in cyberspace do not need to be close to the crime scene, they do not have to travel to the target country, and can attack a large number of victims globally with a minimum of effort and risk through hiding their identity. The information capabilities of the Internet change the nature of crime, as they provide cyber criminals with simple, cost effective and repeatable means of conducting rapid global-scale attacks, while remaining anonymous and/or unreachable for law enforcement. The WannaCry ransomware attack entrapped 200,000 victims from 150 countries within 24 hours.
_
- The unique characteristics of cybercrime include: low risk & low cost to perpetrator, high profit, anonymity, encryption, cryptocurrency, organizable, dark web, scalability, transnational, portability, transferability, accessibility, new opportunities, underground economy, criminal prosecution rare, less likely to be detected, less likely to be reported, no concrete regulatory measure, limited media coverage, lack of awareness among people, and dependence on cyberspace for everything by everybody. Cybercrime is highly complex, self-reinforcing, technologically advanced, geographically widespread, indiscriminate, relentless and unlikely to stop. It is just too easy and too rewarding, and the chances of being caught and punished are low. Encryption and anonymization on the internet are a new normal. It is becoming harder for law enforcement agencies to fight cybercriminals with new and advanced anonymization techniques. Anonymization is as effective as encryption because it allows any available data to be non-attributable to a user.
_
- The deep web is part of the World Wide Web whose contents are not indexed by standard web search-engines. Darknet is a hidden network built over internet and dark web refers to websites on a darknet. Darknet includes small, friend-to-friend peer-to-peer networks, as well as large, popular networks like Tor, Freenet, I2P, and Riffle operated by public organizations and individuals. Dark web is a segment of deep web where illegal activities occur on a daily basis. Dark web allows users to remain anonymous through encryption. This is attractive to anyone involved in illegal activity, such as child pornography, sex trafficking, illicit drugs, or counterfeit goods. But it also may be useful for anyone living in an authoritarian state wishing to communicate with the outside world, as well as providing a safe space for whistle-blowers. So while it’s not illegal to visit the dark web, it provides access to illegal activities.
_
- In the context of cybercrime, hacking means unauthorized access to another computer system. Hacking is the basic act of the criminals who later on tread on to the other computer related crimes and frauds. Most legal systems do not use the term hacking due to its ambiguity. A list of more specific hacking behaviors is criminalized instead. It’s important to learn the difference between a technical glitch or bug and a genuine hacking attempt. Just because your site isn’t working properly doesn’t necessarily mean it’s been hacked.
_
- Social engineering is a type of cybercrime that relies on human vulnerability, rather than vulnerabilities in software and operating systems. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information. Mistakes made by users are much less predictable, making them harder to identify and thwart than a malware-based intrusion. Social engineers manipulate human feelings, such as curiosity or fear, to carry out schemes and draw victims into their traps.
_
- Malware means malicious software. Malware is any software intentionally designed to cause damage to a computer, server, client, or computer network. There are various types of malware, including spyware, ransomware, viruses, worms, Trojan horses, adware, or any type of malicious code that infiltrates a computer.
_
- Cyber violence is a global phenomenon and disturbingly, it is on the rise, lending prima facie credence to the dystopian view that computer-mediated communication exacerbates bad behavior. Cyber violence is the use of computer systems to cause, facilitate, or threaten violence against individuals that results in, or is likely to result in, physical, sexual, psychological or economic harm or suffering and may include the exploitation of the individual’s circumstances, characteristics or vulnerabilities. Cyber violence is less prototypical than physical violence in where and how it takes place, in allowing perpetrators to deny their intent to harm more easily, and in enabling “normal” people to perpetrate widely-targeted harm. In practice, acts of cyberviolence may involve different types of harassment, violation of privacy, sexual abuse and sexual exploitation and bias offences against social groups or communities. Cyber violence may also involve direct threats or physical violence as well as different forms of cybercrime.
_
- Cyber violence is often targeted at women and girls and termed “cyber violence against women and girls” (CVAWG). CVAWG involves a range of conducts including unwanted sexual messages/advance, gender-based hate speech, threat of sexual violence, cyberstalking, cyberbullying, morphing, revenge porn and sextortion. Almost three quarters of women online have been exposed to some form of cyber violence. Many women and girls who were victims of cyber violence chose to minimize their online presence, that hurts digital inclusion, freedom of speech, and other human rights valued in democratic societies.
_
- “Child pornography” means any material that visually depicts a child engaged in real or simulated sexually explicit conduct or any depiction of a child’s sexual organs for primarily sexual purposes. Child pornography is, a) producing child pornography; b) offering or making available child pornography; c) distributing or transmitting child pornography; d) procuring child pornography for oneself or for another person; e) possessing child pornography; f) knowingly obtaining access, through information and communication technologies, to child pornography. The Internet has become a prime channel for the distribution of child pornography. Child pornography is illegal in most jurisdictions of the world.
_
- Identity theft occurs when someone steals your identity and pretends to be you to access resources such as credit cards, bank accounts and other benefits in your name. Two-thirds of victims had no idea how or when they had been hacked. Identity theft creates a sense of helpless.
_
- Intellectual property theft involves robbing people or companies of their ideas, inventions, and creative expressions—known as “intellectual property”—which can include everything from trade secrets and proprietary products to movies, music, and software. The theft of intellectual property accounts for at least a quarter of the cost of cybercrime and, when it involves military technology, creates risks to national security as well.
_
- Freedom of expression is a key driver behind the Internet’s success with portals that are used specifically for user-generated content. Opinions differ as to how far the principle of freedom of expression applies with regard to certain topics (hate speech, blasphemy, xenophobia) on internet as material that can lawfully be distributed in one country can easily be illegal in another country. Cross-jurisdictional conflict of criminal laws raises the unavoidable dilemma of what law should be applied to determine the legal effect of a person’s conduct when he does an act in one state which produces harmful effects in another.
_
- The email has spawned one of the greatest nuisances of our time, “spam”. Conservative estimates are that 100 million people receive at least one spam email. It is also estimated that somewhere between 50 percent and 70 percent of all email messages are spam. Spam is unsolicited e-mail from which the sender is attempting to gain an advantage (commercial or otherwise) and which the recipient neither asked for nor wanted. Spam wastes both the storage and network capacities of ISPs, as well as often simply being offensive. Yet, despite various attempts to legislate it out of existence, it remains unclear how advertisement spam can be eliminated without violating the freedom of expression in a liberal democratic society. Spam becomes cybercrime when it is used to spread computer viruses, trojan horses or other malicious software. Email spam is the most common method for cyber-criminals to spread malware. The objective may be identity theft, or worse (e.g., advance fee fraud). Most malwares are activated when you open an attachment or click a link contained in an email message. If your email client allows scripting, then it is possible to get a virus by simply opening a message. It’s best to limit what HTML is available in your email messages. The safest way to view email messages is in plain text.
_
- Cyberwarfare refers to the use of cyberattacks by one country to disrupt the vital computer systems of another, with the aim of creating damage, death and destruction. Cyberwarfare is the use of information technology to attack a nation, causing comparable harm to actual warfare. The cyber offensive operations can cripple whole economies, change political views, agitate conflicts within or among states, reduce their military efficiency, equalize the capacities of high-tech nations to that of low-tech nations, and use access to critical infrastructures to blackmail them.
_
- Cyber terrorism refers to unlawful attacks and threads of attacks against computers, networks and the information stored therein that are carried out to coerce a country’s government or citizens in furtherance of political or social objectives. Cyber-terrorism’s motive is to invoke fear to intimidate a society into changing behaviour for the purpose of an ideological goal. Cyberterrorism involves the idea that terrorists could cause massive loss of life, worldwide economic chaos and environmental damage by hacking into critical infrastructure systems. The cyber terrorism attacks and threats includes interfering and disrupting information and transportation systems, emergency services and government services, communication networks, infrastructure systems, banking and fiancé system.
_
- Similar to conventional crime, economic benefits, power, revenge, adventure, ideology and lust are the core driving forces of cybercrime. Additionally, boredom or the desire for “a little fun” are also motives for cybercrime.
_
- Cybercrime perpetrators are most commonly aged between 18 and 30 years old and mainly males, to some extent technical savvy, have a disregard for the law or a feeling of being above or beyond the law, have an active fantasy life, be a control freak or risk-taking, and have strong motivations.
_
- Growth of cyber criminals is occurring on two axes: first, the number of people who are technologically savvy enough to commit cybercrimes is growing exponentially; second, a derivative market in cybercrime appears to be growing as ‘enablers’ — ‘persons who use their technical expertise to create and then sell to others easy-to-use tools’ — make it possible for non-technologically savvy people to engage in cybercrime.
_
- The primary risk factor identified across multiple studies of cybercrime is low self-control, though it has greater explanatory power for less technical forms of cybercrime. Crime offers immediate, short-term benefits such as monetary gain, sexual pleasure, or excitement. When opportunities for law-breaking are presented to individuals with low self-control, it is likely that they are unable to resist the easy, immediate gratification that crime brings. Low self-control is typical in teenagers who, at their age, do not have the necessary brain structures in place to generate self-control; they do not have the emotional maturity that enables them to control their impulses, withstand peer pressure and calculate the risks of any dangerous decisions. Roughly 1 out of every 6 adolescents in the US and 1 out of every 4 in the UK disclosed that they had attempted some kind of Internet “hacking”. Majority of teenagers who hack and invade computer systems are doing it for fun rather than with the aim of causing harm.
On the other hand, people who show signs of low self-control are more susceptible to malware attacks. In other words, both perpetrator and victims of cybercrime show signs of low self-control.
_
- The image of a lone hacker behind a computer is no longer accurate. A vast majority of data breaches are often a result of organized crime. Roughly 80% of all cyber-based crime is being committed by sophisticated gangs of criminals engaged in highly organized operations. Organized cybercrime is the most profitable type of crime. There seems a trend towards increasing diversification and specialisation of tasks, in which hackers, virus writers, and spammers focus on their own special expertise, while collaborating to commit a wider range of cybercrimes. A distinct ‘underground’ criminal subculture is emerging, in which cybercrime tools and knowledge are shared and traded, and task-specific expertise is rented and hired for one-off operations. Organised cybercrime means loose groups of individuals who come together to do one thing, do it really well – for a period of time – then disappear. There is no such thing as organized cybercrime Mafia till date. There is no multi-year, multi-generation, sophisticated Mafia groups in cybercrime till date.
_
- The combination of massive budgets, access to talent, and protection from law enforcement make nation states the most dangerous source of cybercrime. China, Russia and North Korea have been the largest source of cyberattacks in the world.
_
- Victims of cyber-fraud are more likely to be cooperative, greedy, gullible/uncritical, careless, susceptible to flattery, easily intimidated, risk takers, generous, hold respect for authority, and good citizens. Time spent on internet is highly correlated with victimisation. Impulse online shopping, downloading music and compulsive email use are all signs of a certain personality trait that make you a target for malware attacks. Other personality traits of victims of cybercrime include extraversion, agreeableness, conscientiousness, emotional stability, and openness to experience. Counterintuitively those who emphasize the importance of online security, generally contradict themselves through their actions, and as a result, are more likely to fall victim to cybercrime. The victims of cybercrime feel that nowhere will ever be safe and that they could always be confronted with the perpetrator once again. Besides the financial consequences, the victims can experience feelings of shame, guilt and grief. Victims are concerned that police are inadequately equipped to fight cybercrime.
_
- It’s not only big money corporations that are being attacked. Civil society groups, journalists, human right activists, whistle-blowers, and NGOs are the new targets of cyberattacks.
_
- The world will need to cyber protect 300 billion passwords globally by 2020. There are 111 billion lines of new software code being produced each year — which introduces a massive number of vulnerabilities that can be exploited. 20% of cybercrime victims globally use the same password across all online accounts and 58% shared at least one device or account password with others.
_
- On average roughly 900 phishing attempts are detected per financial institution, and more than 9,000 attempts detected per technology company per year. Google, Apple, Facebook, and Yahoo are all phishing targets. On average, 85,000 malicious IPs (IP addresses) are launched every day, bringing the average reputation score of all URLs worldwide to 65 percent.
_
- Cybercrime is an easy way to target people because it requires only a computer, an internet connection, and criminal intent. The evidence of how simple it is to commit cybercrimes is in the number of victims estimated to have been targeted in 2017: nearly one billion people! Everyone and every device connected to the internet is a potential target for cybercrimes. Cybercrime is one of the most serious threats worldwide as all the world’s economies use the same basic infrastructure, the same software, hardware, and standards – with billions of connected devices.
_
- The growing use of social media, now estimated to be more than three billion users worldwide, provides fertile ground for hackers looking to commit cybercrime. Hacking services, hacking tutorials and tools like exploits & botnet hire are available on social media. Over 1.3 billion social media users have had their data compromised within the last five years. Up to 1 in 5 businesses have been infected with malware originating from social media and 1 in 8 have experienced a security breach as a result of a social media-directed cyberattack. Social media has become a tool as well as a target of cybercrime.
_
- Banks are a lucrative target for cybercrime as cyber criminals go where the money is. The software used for detecting frauds in most cases is either outdated or very time consuming. Besides cybercriminals, one of the biggest threats, and often one of the hardest to detect, is that of malicious, careless and compromised bank employees. When insiders abuse their privileged access or are compromised by external attackers, the valuable data is easily exposed. Even though banks are a popular target for hackers, they are also among the most sophisticated enterprises in the world from a security perspective. What we don’t hear about are the numerous attempts to breach banking systems that are successfully prevented.
_
- Google’s Android and Apple’s iOS are operating systems used primarily in mobile technology, such as smartphones and tablets. Apple’s iOS is considered more secure than Google’s Android. Mobile devices have proliferated in recent years, and with them malware and phishing scams. Because of its open marketplace, the Android platform is home to a variety of malware in particular. In a recent survey, 72% of all apps for the android OS were regarded as suspicious, unwanted, or malicious, with Trojans making up the majority of threats. More than 60% of fraud online is accomplished through mobile platforms, and 80% of mobile fraud is achieved through mobile apps instead of mobile web browsers.
_
- Cybercrime is a phenomenon that affects all the countries of the world – especially the most industrialized and computerized. Developing countries lack the capacity to combat cybercrimes due to weak security measures and legal loopholes. It is therefore not surprising that victimization rates are higher in countries with lower levels of development although the value that can be extracted from cybercrime remains relatively low as compared to developed nations.
_
- Estimates of the cost of cybercrime show significant variation, from tens of billions to a trillion dollars or more. This reflects the absence of data and differing methodologies. About 0.8 % to 1 % of the world’s GDP is lost to cybercrime in 2019 by conservative estimate although it could be higher. The total global cost of all the data breaches in 2019 amounts to $2.1 trillion. Cybercrime damages are anticipated to cost 5 to 6 trillion $ per year by 2021 according to various estimates. Globally cybercrime is more profitable than the global trade of all major illicit drugs combined, and cybercrime generates more revenue than crude oil theft, human trafficking and small arms dealing combined.
_
- Cybercrime costs include damage and destruction of data, financial losses, time wastage, lost productivity, theft of intellectual property, theft of data (personal, financial and confidential), embezzlement, fraud, data breach liabilities, damage to brand, loss of client and public confidence, post-attack disruption to the normal course of business, forensic investigation, regulatory issues, restoration and deletion of hacked data and systems, and reputational harm. Also, victims suffer from depression. shame and embarrassment; and disruption to daily life occurs when key services are attacked. Even when the goals of the attackers are not monetary gain, the costs can be enormous. Though not a penny of its cash was stolen, the attack on Sony cost the entertainment company billions of dollars through the release of data.
_
- Although cyberspace allows individuals to engage in business activity as never before, it also expands the scale and scope of the associated risks. The computing power, connectivity, and speed can spread malwares, compromise systems, and compound errors in seconds, potentially affecting interconnected parties, increasing business costs to rectify such mishaps, and hitting a larger target than even envisaged. SMBs are vulnerable to the same threats as larger businesses, but often lack the resources to fully implement cyber security. Small businesses, in particular, bear the brunt of 43% of cyberattacks and this percentage will only increase. About 45% of all companies hit by ransomware pay the demanded amount.
_
- Cybercrime is fuelling the market for cybersecurity products and services, which is expected to grow from $75 billion in 2015 to $175 billion by 2020. The cyber-insurance market is also getting a boost from cybercrime and projected to grow from $2.5 billion in 2015 to $7.5 billion by 2020.
_
- Essential services such as water and electricity supply now rely on ICTs. Cars, traffic control, elevators, air conditioning and telephones also depend on the smooth functioning of ICTs. Attacks against information infrastructure and Internet services now have the potential to harm society in new and critical ways.
_
- Cybercrime is possible because computers and networks are not properly secured. Effective cybersecurity reduces the risk of cyberattacks and protects against the unauthorized exploitation of systems, networks and technologies. Robust cybersecurity addresses people, processes and technology. Cyber security is important because government, military, corporate, financial, and medical organizations collect, process, and store unprecedented amounts of data on computers and other devices, and unauthorized access or exposure could have negative consequences.
_
- Unlike the physical world, in cyberspace certain readily identifiable third parties – such as Internet service providers, telecommunication providers, and victims themselves – have exclusive or shared technical control over the infrastructure through which most cybercrime is carried out. These characteristics provide new opportunities for innovative policy approaches to control undesirable behavior; including the use of technical architecture as a regulatory mechanism, the use of novel authorization and surveillance regimes to prevent or deter undesirable activity, and the use of data and activity logging to enhance persistence and recoverability of evidence, amongst others.
_
- Virtual private network (VPN) uses what is called a tunnelling protocol to create secured connections that are undetectable and untraceable and then enhances that protection with data encryption. VPN does a lot to enhance the security of today’s Internet users and makes attacking a VPN user difficult and time consuming.
_
- A lot of cybercrime victims don’t even know they have been hit, meaning that cybercrime and cybercriminals can go undetected for a long time. A common man who is a user of computer, internet and smart phone is unaware of the traps set by clever criminals and the ways to get rid of them. Cybercrime may be thriving because of our failure to increase awareness among individuals so they can protect themselves and avoid being victims. Most people just don’t know what to do or how to do it. 51 % people cannot differentiate between real email and fake email. Nearly 3 in 10 people cannot detect a phishing attack. Only half (51 per cent) of adults say that they would change their behavior if they became a victim. Even fewer than half (44 per cent) reported cybercrime to the police. The worldwide average to detect a cyberattack on businesses and organizations is 170 days and the average time to resolve an incident is 45 days. The longer it takes to identify a hack, the more costly its consequences.
_
- There is supposed to be a high ‘dark number’ of undetected, unreported, uninvestigated, or unresolved cybercrimes. Cybercrime surveys are so compromised and biased that no faith whatever can be placed in their findings. Many statistics are published of computer-security incidents, notably of viruses and other malware and phishing attempts by security companies with an interest of selling, e.g., anti-virus software, and should therefore be taken with a pinch of salt. About 75% of the countries view their systems of police statistics as insufficient for recording cybercrime as cybercrime incidents are very rarely reported. Police data is under-reported for various reasons: lack of awareness among the population, fear of negative publicity, reputational damage leading to competitor advantage, lack of incentive, invisibility and complexity of digital traces, perception that the police response will be ineffectual, no prospect of restitutionary damages and victims not realizing that they have been victimized. Businesses may fear that negative publicity could damage their reputation. If a company announces that hackers have accessed their server, customers may lose faith. The full costs and consequences could be greater than the losses caused by the hacking attack. Victims believe that law-enforcement agencies will not be able to identify offenders. Comparing the large number of cybercrimes with the few successful investigations, they may see little point in reporting offences. Action against cyber criminals is too slow, the arrests are few and far between, and too often the penalties are very light, especially compared with traditional real-world crimes. American statistics show only three in 1,000 cyber-crimes are actually prosecuted – the actual ratio could be closer to three in 100,000 as the FBI tends to underestimate the extent of cyber-crime. Since most cyber-offenders are not reported and prosecuted, they may go on to re-offend.
_
- Identifying attackers is difficult, as they are often in a different jurisdiction to the systems they attempt to breach, and operate through proxies, temporary anonymous dial-up accounts, wireless connections, and other anonymizing procedures which make back tracing difficult. If they successfully breach security, they are often able to delete logs to cover their tracks. Logs record every action as it happens. Logs tell you what an actor (user or entity) did. This is enough if you want to monitor who did what when. One of three cybercriminals manage to remove logs by wiping their traceable digital footprints. Law enforcement officers are often unfamiliar with information technology, and so lack the skills and interest in pursuing attackers. Tech-savvy persons with professional degrees in IT or computer science should be recruited for the cyber police station as opposed to non-specialists.
_
- Cyber-criminal profiling is a tool which could bring more offenders to justice.
_
- Digital evidence is any data stored or transmitted using computer technology that supports the premise of how cybercrime occurred. There are number of challenges that need to be overcome for using digital evidence in the court of law, the most important being fragility of digital evidence i.e. digital evidence can be easily deleted or modified.
_
- The purpose of computer forensics techniques is to search, preserve and analyse information on computer systems to find potential evidence for a trial. The computer is a reliable witness that cannot lie, but data in computer can be easily manipulated, then how can computer be used as reliable evidence? Therefore, secure the computer system to ensure that the equipment and data are safe. That means cybercrime investigator must ensure that no unauthorized individual can access the computers or storage devices involved in the search. If investigators can’t prove that they secured the computer system, the evidence they find may not be admissible in the court of law.
_
- Countries differ on definition of cybercrime, leave alone the types of crime and punishment. Cybercriminals exploit this situation by coming up with new tools and discovering new vulnerabilities to attack targets. As cybercrimes make geographical boundaries insignificant, combating cybercrime calls for international harmonization of laws and cross-border regulation, along with mandatory global prosecution procedures; however, such is not the case, nor is it feasible in the near future.
_
- Criminal programmers design anti-forensic tools to make it hard or impossible to retrieve information during cybercrime investigation. Essentially, anti-forensics refers to any technique, gadget or software designed to hamper cybercrime investigation. Investigators have to be aware of these programs and how to disable them if they want to access the information in computer systems.
_
- Many banks are using AI technologies such as predictive analytics, recommendation engines, and voice recognition and response to prevent and detect cyber-frauds. AI is often considered to be a dual-use technology – while more cybersecurity companies are implementing AI-driven algorithms to prevent threats, hackers are also taking the opportunity to become more effective. Hackers once spent considerable time poring over lines of code for a weak point they could penetrate, today AI tools can find vulnerabilities at a much faster speed. AI tools are also being used to create extremely sophisticated phishing campaigns. To enable AI-driven defense system to win battle against AI-based attacker will require a totally new set of capabilities which we don’t have today.
_
- Digital hygiene or cyber hygiene is a fundamental principle relating to cyber security and it means establishing simple routine measures to minimize the risks from cyber threats. People should protect themselves by ensuring that operating systems are always up to date, they use up to date quality anti-virus, they regularly backup important data, they don’t click on links or attachments in suspicious emails, they check their bank account frequently and be cautious when surfing by staying away from suspicious websites. If it sounds too good to be true, it usually is. It is estimated that more than 90% of security incidents and breaches involve some kind of human error. Almost 90% of computers using pirated operating system or pirated software had the malware preinstalled, so spend money and buy genuine operating system and software.
_
- Since we have early exposure to technology at an increasingly earlier age, efforts to help youth to develop self-control and make good choices when faced with offending opportunities must be made early in life. Developing and promoting programs that educate youth and children of the risks of engaging in cyber deviance and associating with deviant peers on-line may help to decrease youth participation in cybercrime offending. Helping children to understand what constitutes appropriate behaviors when using the Internet can be an important aspect of educating children to be responsible citizens in cyberspace. Cyberspace, cyber deviance and cybercrime, their control, impact and all other aspects should be made part of school and college syllabi to make students aware of the field.
_
- We continue to blame users for not avoiding clicking on every phishing link; and when a breach becomes public the response all too often is to blame the victim company. The entire world is focusing on defending systems rather than identifying, pursuing, and bringing to justice the person behind the cyber-crime. We need the new approach: catch the cybercriminal at any cost by whatever means available. The actual cybercriminals and the potential cybercriminals must realise that it is no longer low-risk crime and they will be caught and punished. Only then cyberattacks will be reduced. Cyber education, cyber hygiene, cyber vigilance and cyber security are not good enough, we need cyber arrests and cyber jail terms.
Remember; cybercriminals are one step ahead of cybersecurity by continuously changing tactics, finding unknown vulnerabilities, delete logs to cover their tracks. and developing new modus operandi.
Remember; swift, certain and consistent punishment is the only way cybercrime will be curtailed.
______
Dr. Rajiv Desai. MD.
February 18, 2020
______
Postscript:
If we cannot control exponential growth of cybercrime, we will have to revert to paper transaction instead of digital transaction just as many nations have reverted to paper ballots after experimenting with electronic voting,
_____



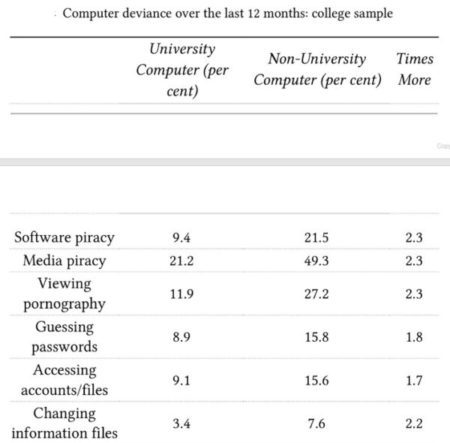
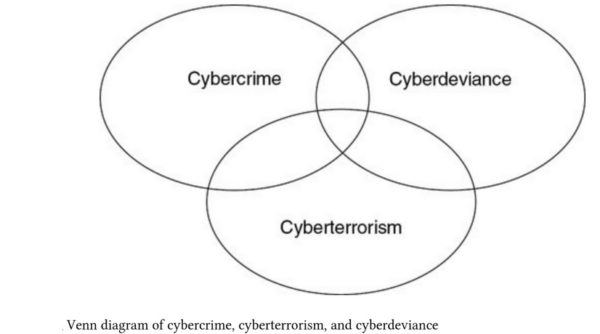
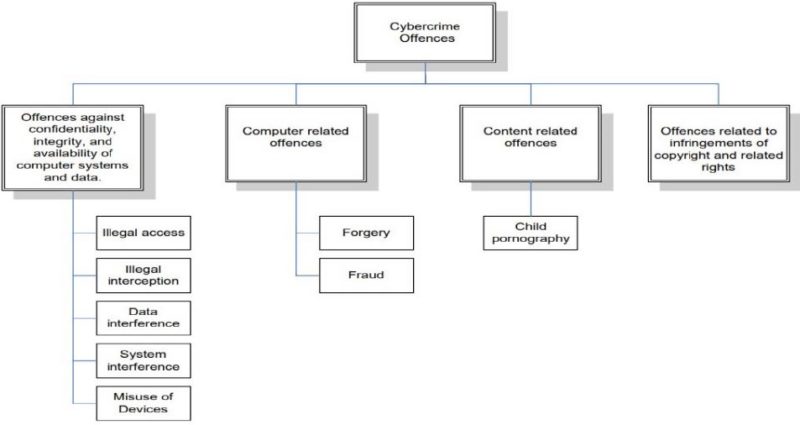

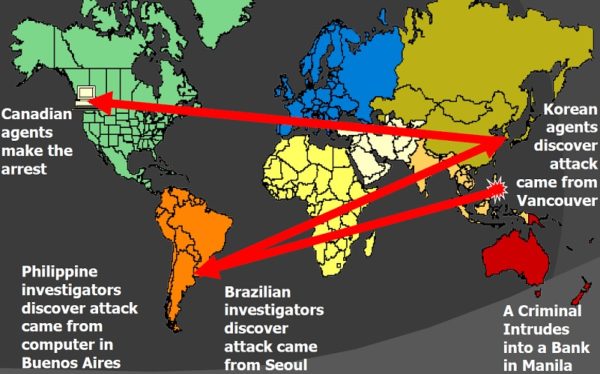
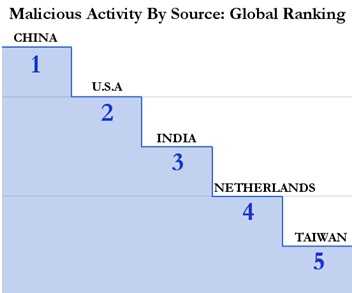

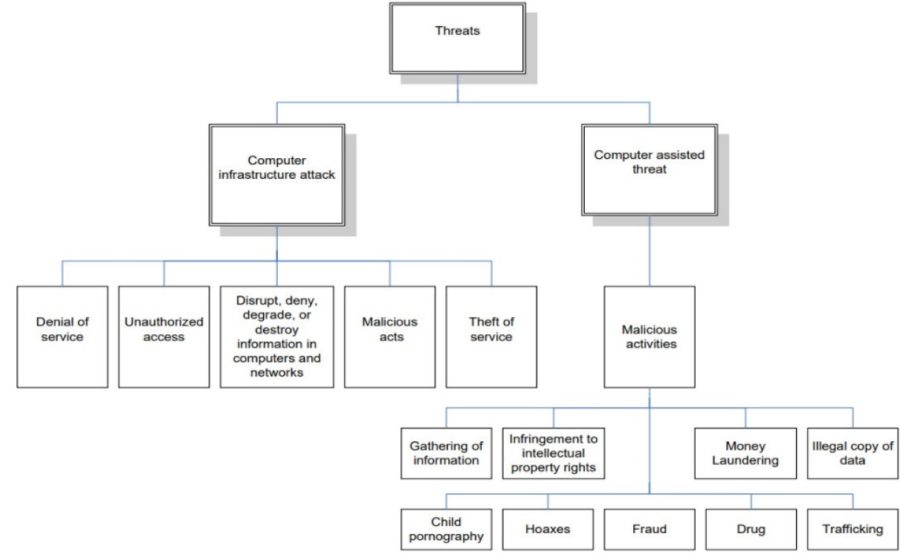
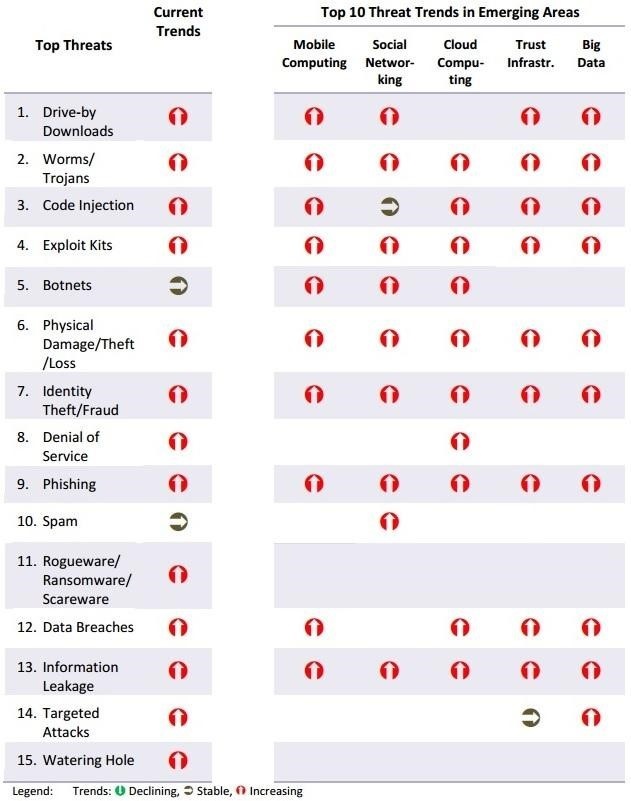
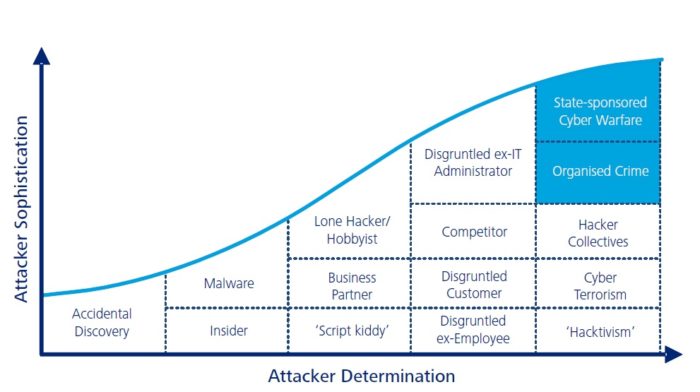
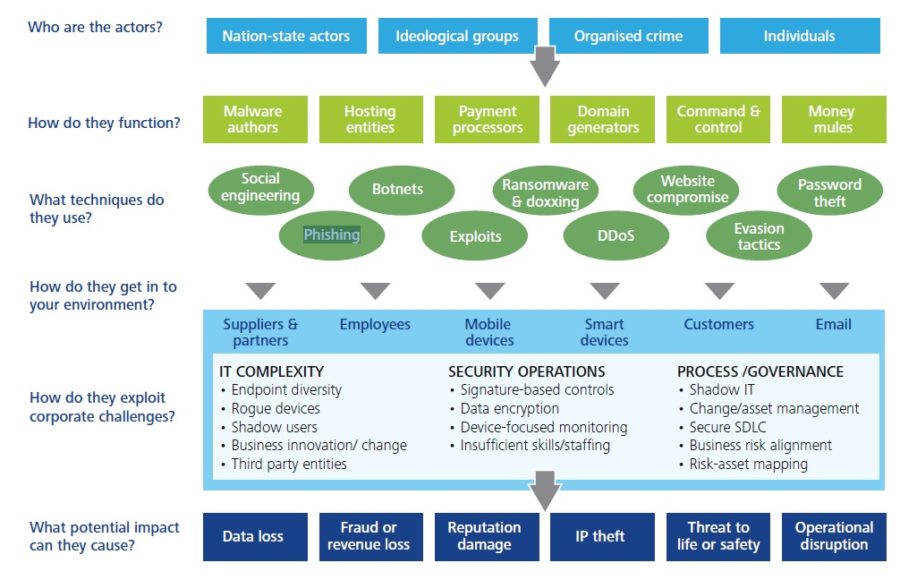
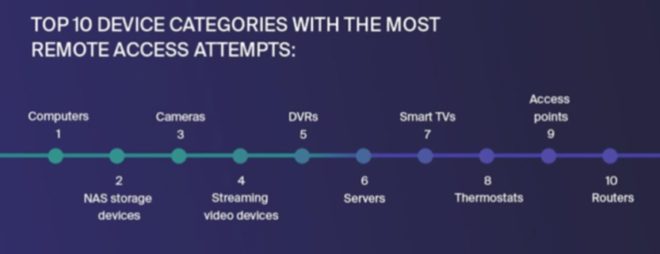

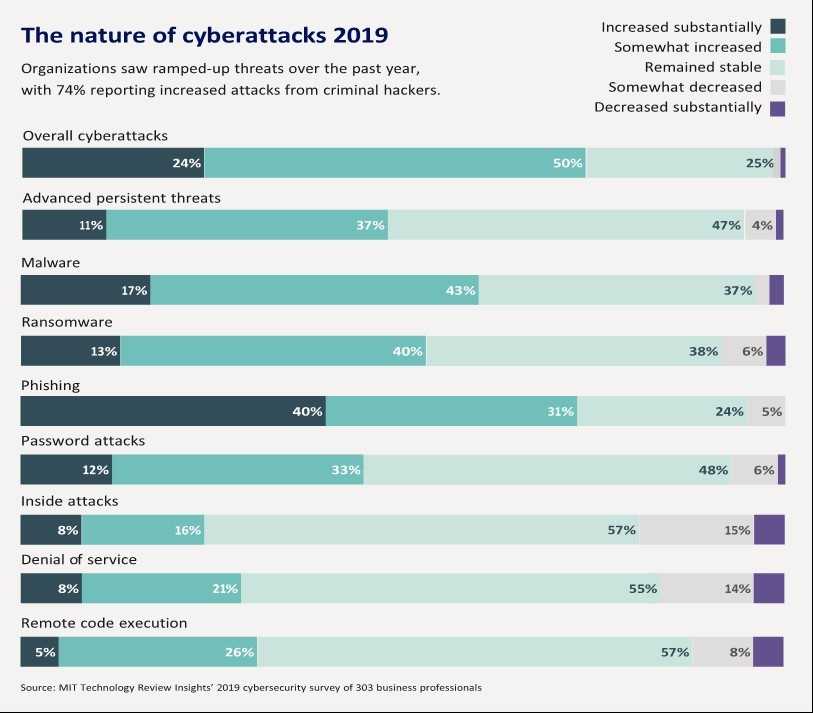

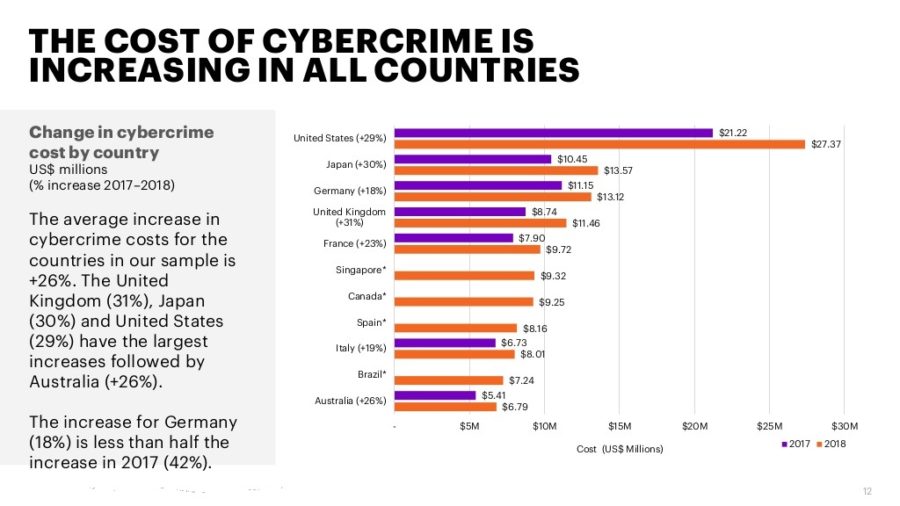
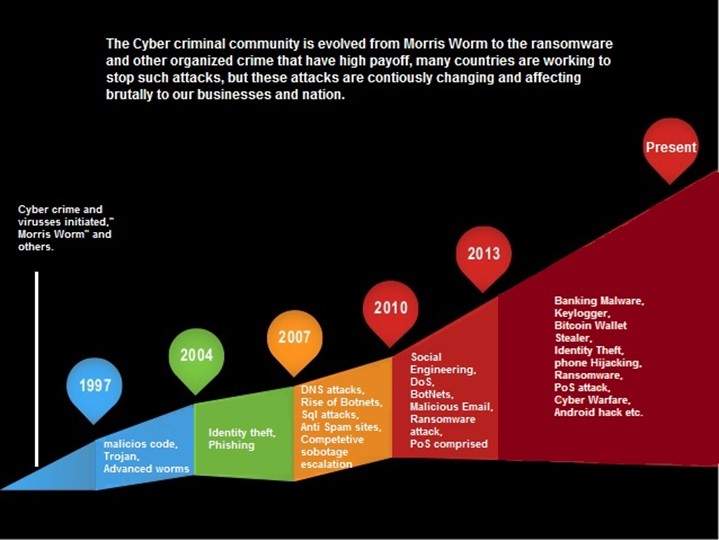
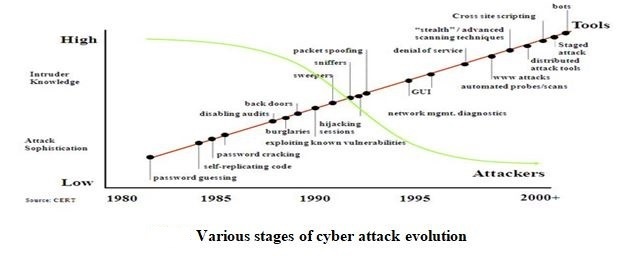
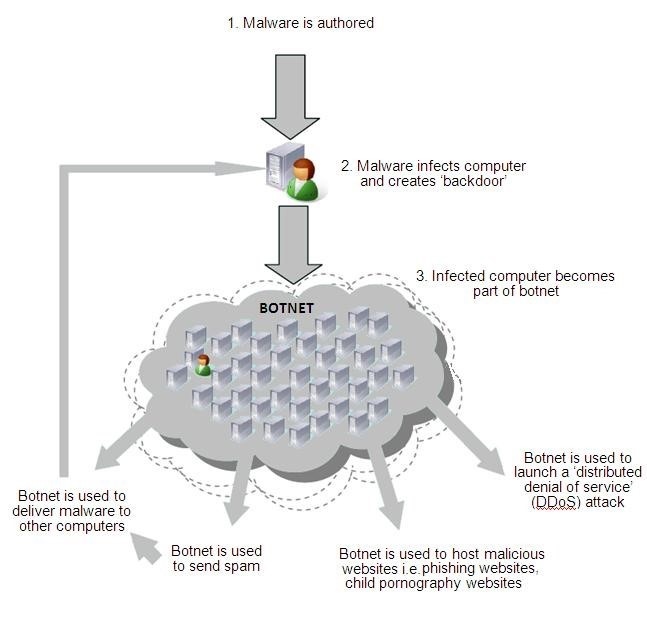
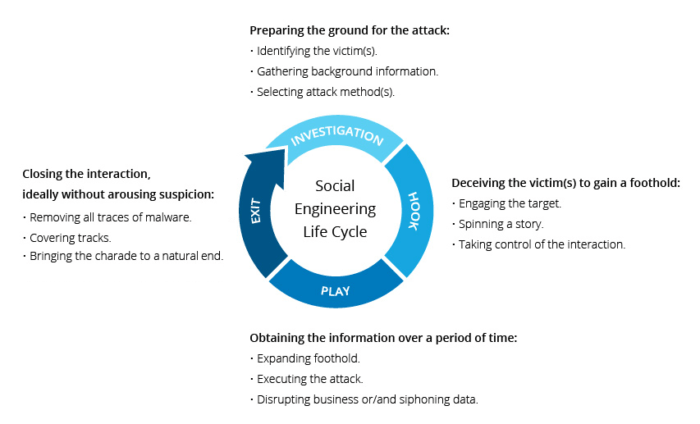
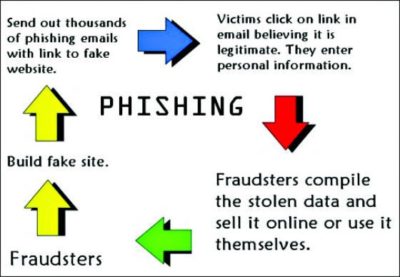

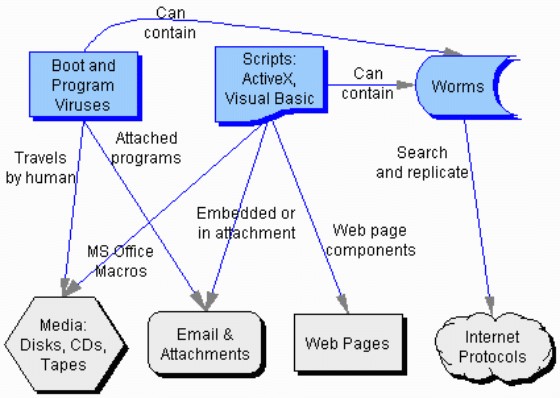

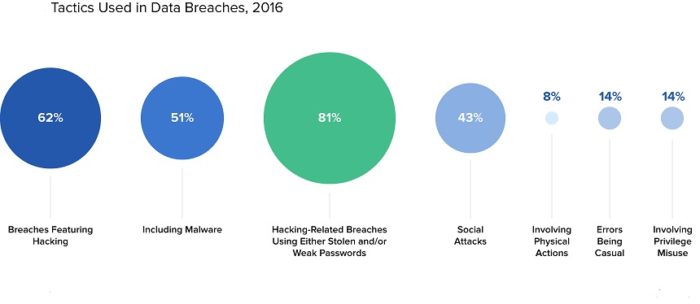
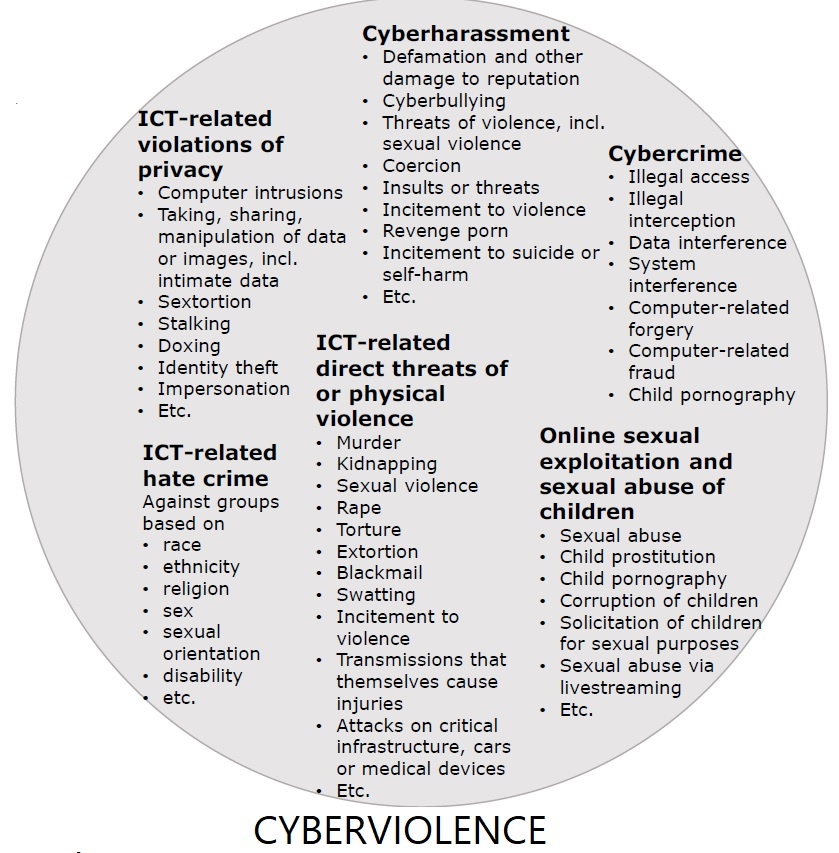

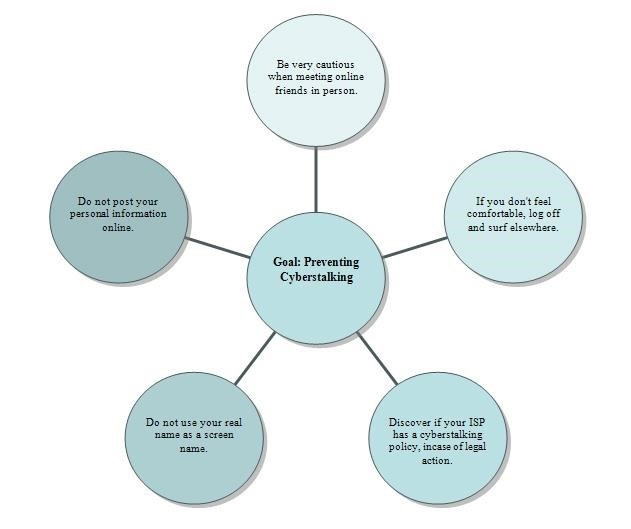
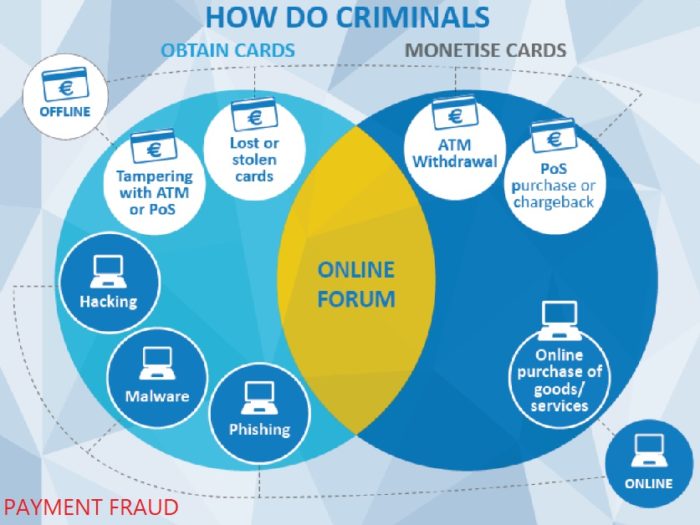
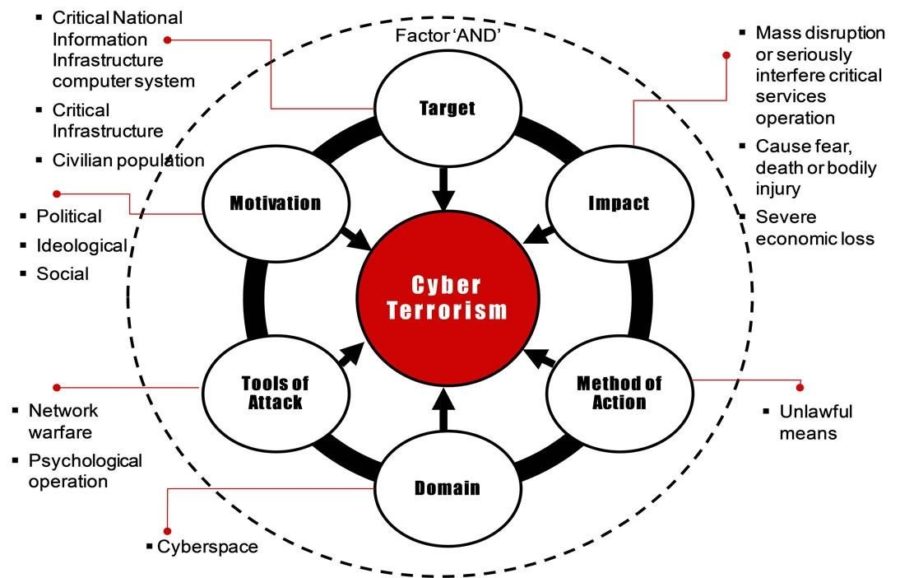
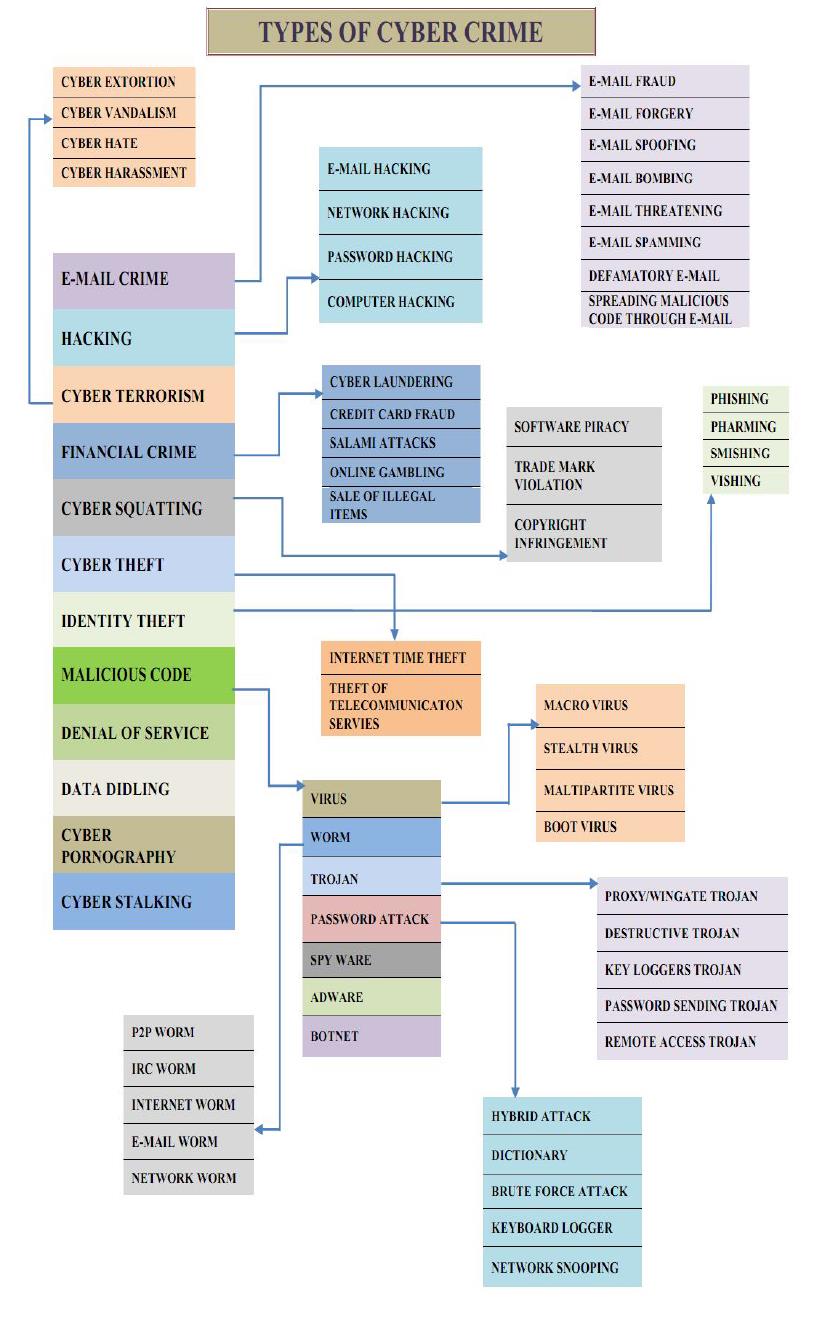
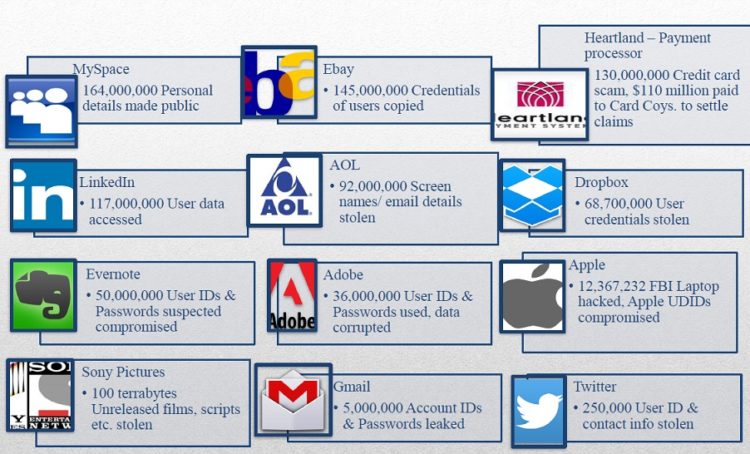
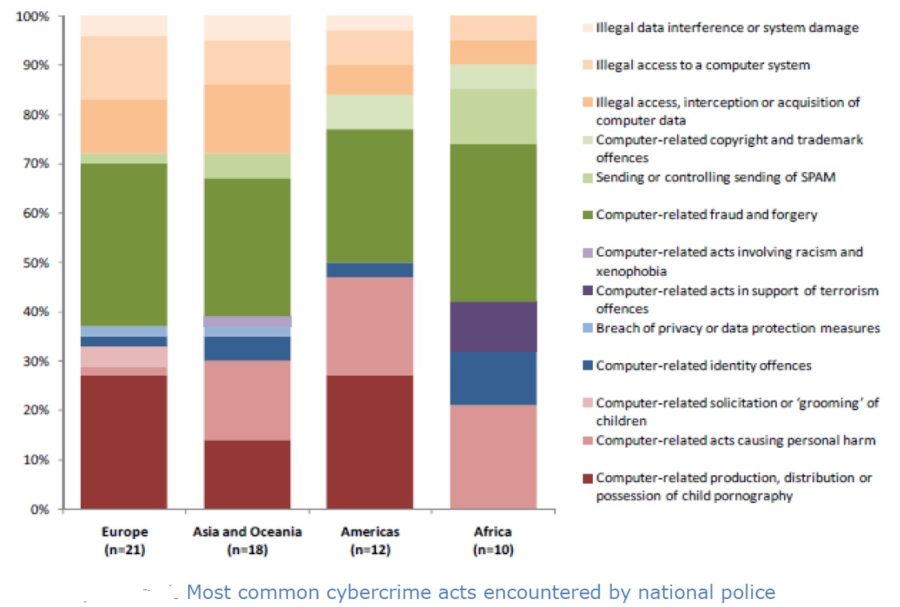
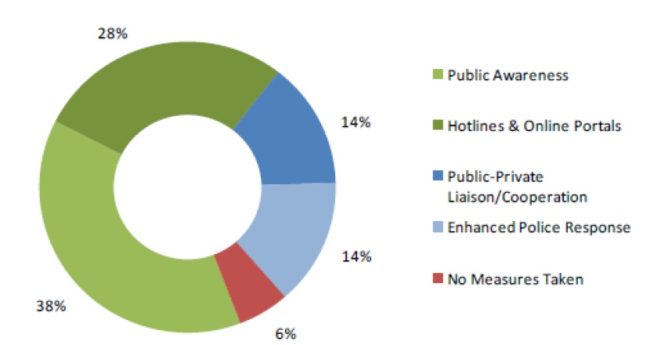
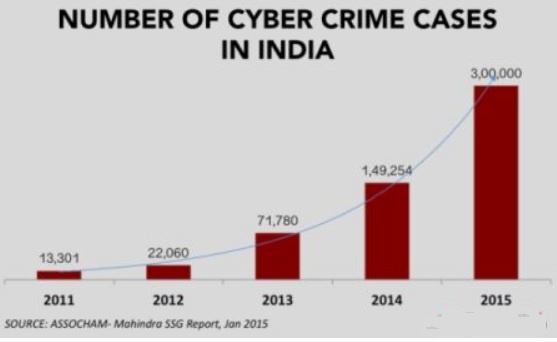

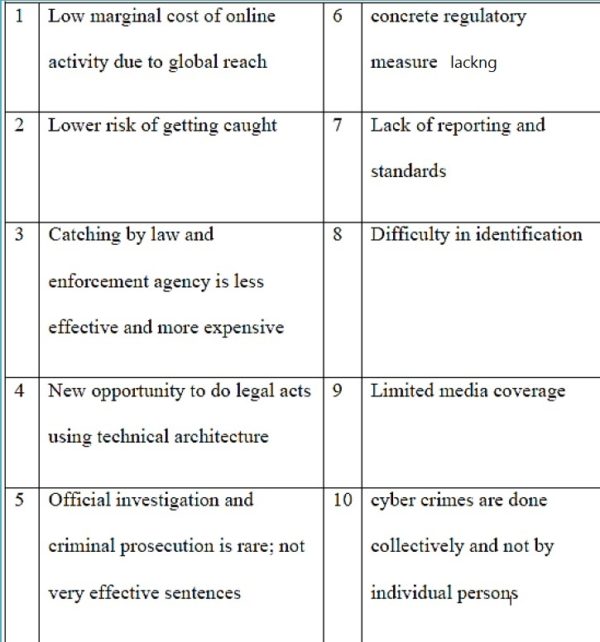
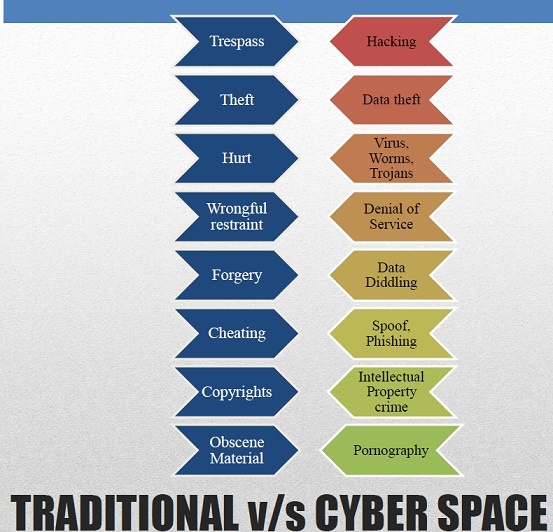



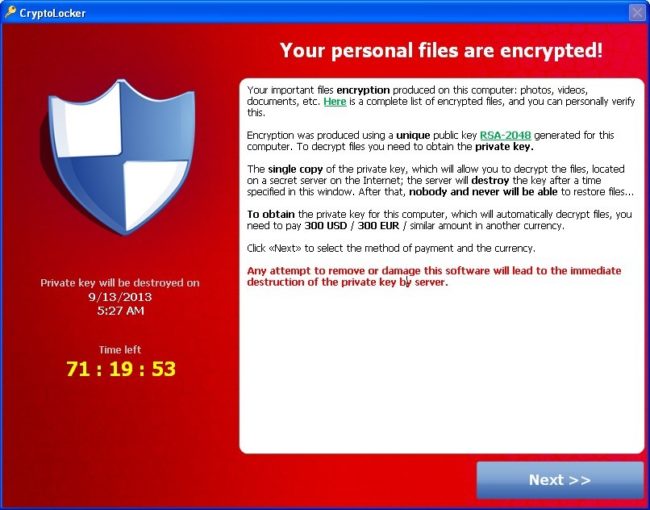
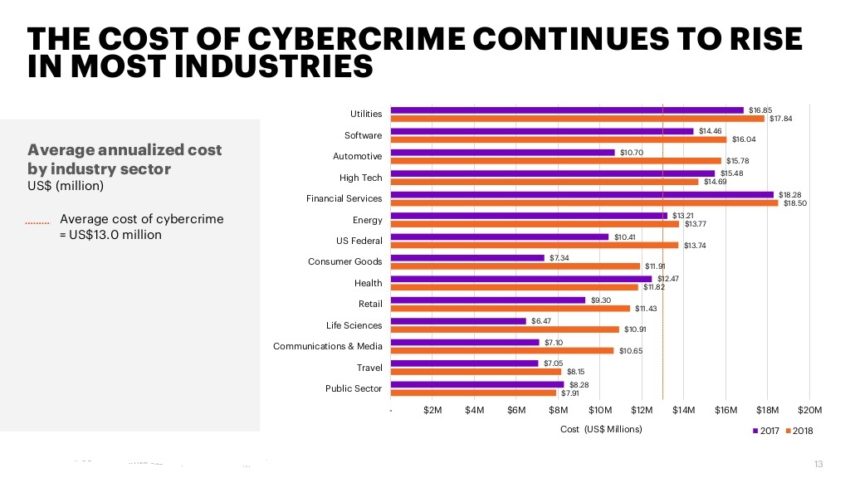
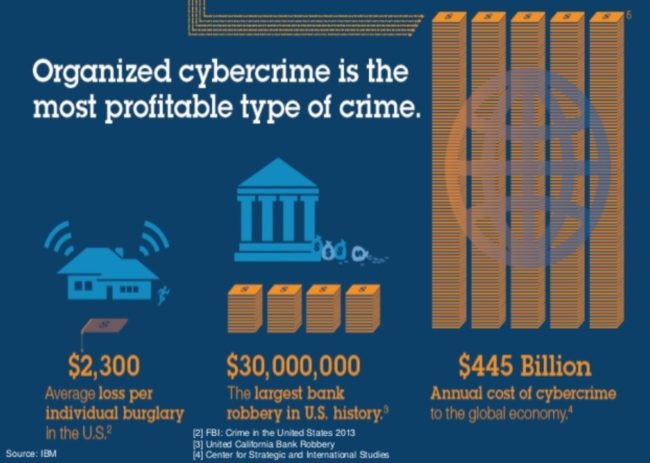
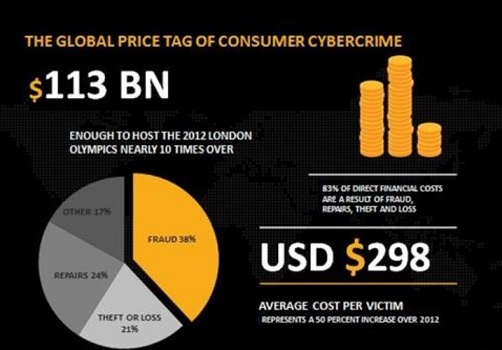
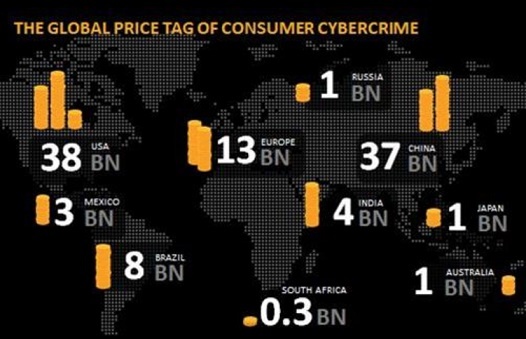
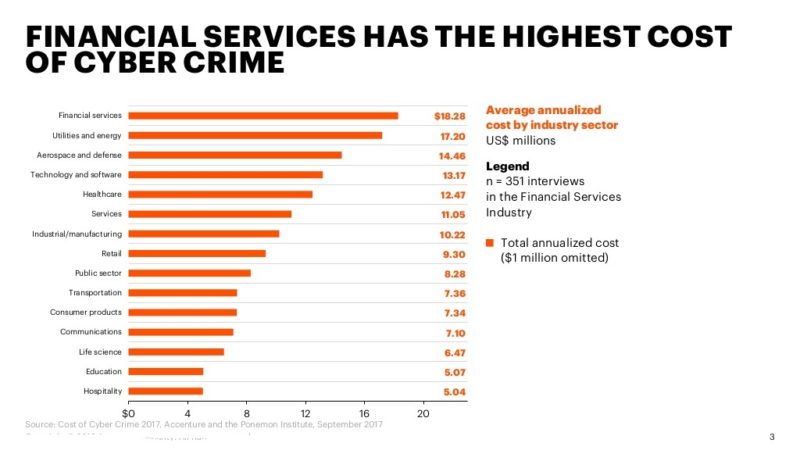
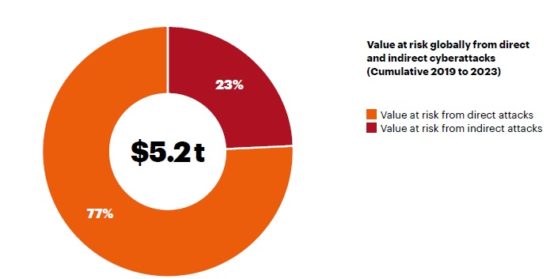
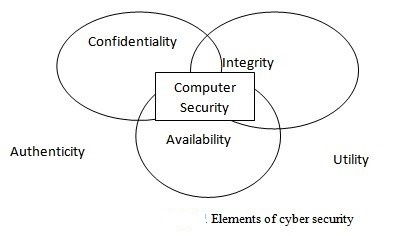
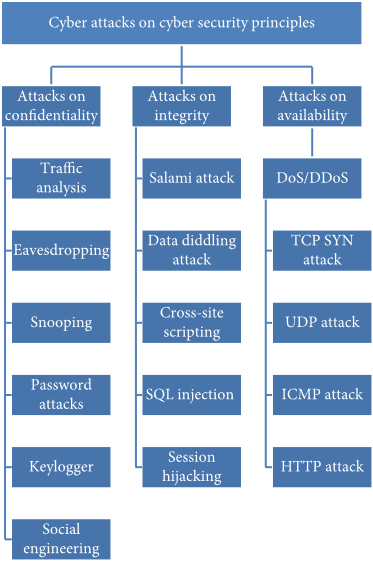
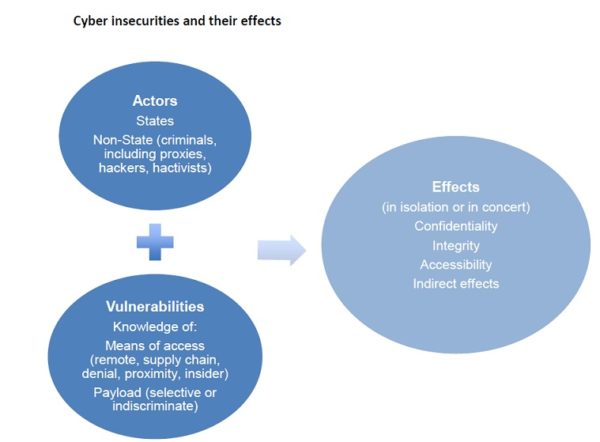
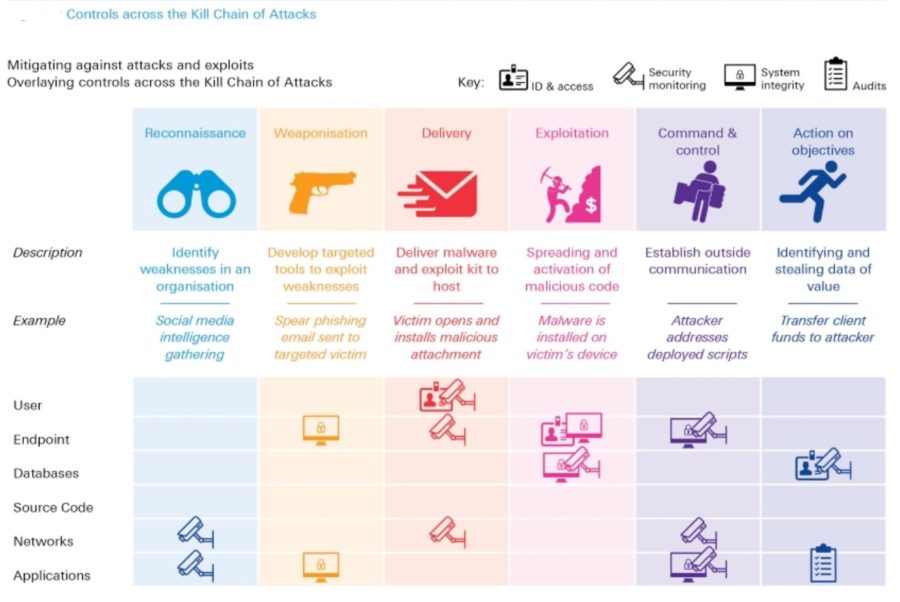

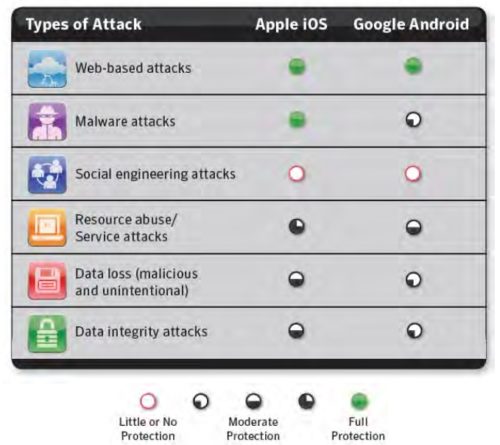
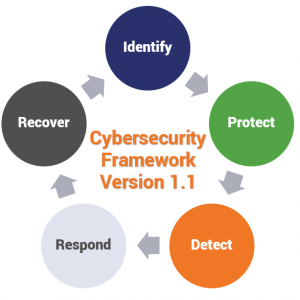


Thank you for the good writeup. It in fact was a amusement account it. Look advanced to more added agreeable from you! By the way, how can we communicate?
I have to thank you for the efforts you’ve put in penning this site. I really hope to see the same high-grade content by you in the future as well. In truth, your creative writing abilities has inspired me to get my own, personal website now 😉
I’m impressed by your effort as well as dedication. I am so grateful for your unlimited assistance and love.
Make every little thing much better with the Amazingness course.
Just want to say your article is as astonishing. The clarity in your post is just spectacular and i could assume you’re an expert on this subject. Well with your permission let me to grab your RSS feed to keep updated with forthcoming post. Thanks a million and please keep up the gratifying work.|
It’s nearly impossible to find educated people in this particular topic, but you seem like you know what you’re talking about! Thanks
I’m impressed, I must say. Actually hardly ever do I encounter a weblog that’s each educative and entertaining, and let me let you know, you’ve got hit the nail on the head. Your concept is outstanding; the issue is one thing that not sufficient persons are speaking intelligently about. I’m very joyful that I stumbled throughout this in my search for something regarding this.
Way cool! Some extremely valid points! I appreciate you penning this write-up and the rest of the website is really good.
You should take part in a contest for one of the finest sites on the internet. I’m going to highly recommend this web site!
Way cool! Some very valid points! I appreciate you writing this post and also the rest of the site is really good.
It’s nearly impossible to find experienced people for this subject, but you sound like you know what you’re talking about! Thanks
You made some good points there. I checked on the web for more information about the issue and found most people will go along with your views on this site.
I couldnít resist commenting. Perfectly written!
This is a topic that’s close to my heart… Best wishes! Where are your contact details though?
Thanks with regard to the informative in addition to useful post, obviously inside your blog everything is good.
You ought to take part in a contest for one of the most useful sites on the net. I most certainly will highly recommend this website!
Great web site you’ve got here.. Itís hard to find excellent writing like yours nowadays. I honestly appreciate individuals like you! Take care!!
Write more, thats all I have to say. Literally, it seems as though you relied on the
video to make your point. You obviously know what youre talking about,
why waste your intelligence on just posting videos to your weblog when you could
be giving us something enlightening to read?
Hi there friends, its enormous paragraph concerning teachingand completely defined, keep it up all the time.