Dr Rajiv Desai
An Educational Blog
DIGITAL TRANSACTION
Digital transaction:
___
____
Prologue:
History of banking dates back to 2000 B.C. Archaeologists believe that depositing and lending have always been human way of business and economy during renowned Roman, Chinese, and Indian empires. In fact, if we really think about it, there can actually be no trusted way of keeping earned money safe to be used when required other than a trusted group that also provides interest on such deposits. From that time banks and their ways have evolved tremendously. Computing revolution has been the biggest step forward here. For what was confined to signatures and psychical presence, has now been replaced by plastic money and virtual presence. John Shepherd-Barron, the Scotsman is credited with inventing the world’s first automated cash machine. Shepherd-Barron said once that he came up with the idea of the cash machines after being locked out of his bank. Plastic bank cards had not been invented yet, so Shepherd-Barron’s machine used special checks that were matched with a personal identification number. The first automated teller machine (ATM) was installed at a bank in London in 1967. The history of economic development has been characterised by periods of massive transformation brought about by technological innovation. Steam power led to industrialisation and rapid urbanisation, electricity enabled the assembly line and mass production of consumer goods, the automobile encouraged mass mobility and the development of suburban living, and the internet and World Wide Web have revolutionised access to communications and knowledge. Digital money is a technology that moves economic transactions, payments, remittances and transfers from the physical into the digital world. Many people today are using a mix of cash and online methods of payment. People are increasingly paying their bills through banks and using credit/debit cards and other online transactions. The old adage that “criminals go where the money is” finds aptness today as criminals go where digital transaction occurs. Security is essential for any payment transaction that takes place over internet/private network. My website was hacked repeatedly for 2 days on 5th and 6th February 2017 discarding my previous article “Are ordinary people bad?” posted on 22/12/2016. If this can happen to an educational website where no monetary gain is achievable, what about digital transaction? So security of digital payment has to be of paramount importance and gets priority over other aspects of digital transactions. This article is delayed due hacking of my website and consequent measures to upgrade security.
_____
Abbreviations and synonyms:
ATM = automated teller machine
POS = point of sale device
Aadhaar = A 12-digit unique number which UIDAI issue for all residents in India.
CSC = card security code = CVV = card verification value
NFC = Near Field Communication
BLE = Bluetooth Low Energy
AEPS = aadhaar enabled payment system
USSD = Unstructured Supplementary Service Data
UPI = Unified Payment Interface
NCPI = national payment corporation of India
UIDAI = Unique Identification Authority of India
PIN = personal identification number
OTP = one-time password is a password that is generated for only one login session
EMV = Europay, MasterCard, and Visa [EMV card is chip card]
SET = Secure Electronic Transaction
RSA = Rivest, Shamir and Adleman [asymmetric cryptographic algorithm]
ECC = Elliptic curve cryptography
PAN = personal area network
DES = Data Encryption Standard
AES = Advanced Encryption Standard
HTTPS = HyperText Transfer Protocol Secure
TLS = Transport Layer Security
SSL = secure socket layer
IVR = interactive voice response
RFID = Radio-Frequency Identification
HCE = Host card emulation
$ = US dollar = dollar
PSP = Payment service provider
P2P = peer to peer [peer-to-peer (P2P) network is created when two or more PCs are connected and share resources without going through a separate server computer]
____
Nomenclature used in this article:
Merchant: The term “Merchant” means any person who offers a Consumer goods and service and accepts orders directly from Consumers.
Consumer: The term “Consumer” means a customer, including a licensee, subscriber, or buyer, of any goods and service acting primarily in a personal, family, or household capacity – other than for purposes of resale.
Transaction: The term “Transaction” refers to any agreement for provision of a goods and service between a Merchant and Consumer.
Payer: Payer is a person or organization that gives someone money that is due for goods and services received or to be received or a debt incurred. Consumer is a payer.
Payee: Payee is the party in an exchange who receives payment. A payee is paid in cash, check (cheque), digital transaction or other transfer medium by a payer, with the payer receiving goods and services in return. Merchant is a payee.
Electronic: Electronic means relating to technology having electrical, digital, analog, magnetic, wireless, optical, electromagnetic, or similar capabilities.
______
Note:
Please read my articles ‘Computer and Internet’ at https://drrajivdesaimd.com/2010/01/23/the-computer-and-internet/ and ‘Smartphone’ at https://drrajivdesaimd.com/2015/02/09/smartphone/ to understand digital transaction better.
_____
_____
Basics of digital and analog:
Traditionally, digital means the use of numbers and the term comes from digit, or finger. Digit is a single character in a numbering system. In decimal system, digits are 0 through 9. In binary system, digits are 0 and 1. Computers are digital machines because at their most basic level they can distinguish between just two values, 0 and 1, or off and on. Today, digital is synonymous with computer. Digital information can assume only one of two possible values: one/zero, on/off. There is no simple way to represent all the values in between, such as 0.25. All data that a computer processes must be encoded digitally, as a series of zeroes and ones. The opposite of digital is analog. A typical analog device is a clock in which the hands move continuously around the dial. Such a clock is capable of indicating every possible time of day. In contrast, a digital clock is capable of representing only a finite number of times (every tenth of a second, for example). Analog information is made up of a continuum of values within a given range.
_
Digital describes electronic technology that generates, stores, and processes data in terms of two states: positive and non-positive. Positive is expressed or represented by the number 1 and non-positive by the number 0. Thus, data transmitted or stored with digital technology is expressed as a string of 0’s and 1’s. Each of these state digits is referred to as a bit (and a string of bits that a computer can address individually as a group is a byte). Prior to digital technology, electronic transmission was limited to analog technology, which conveys data as electronic signals of varying frequency or amplitude that are added to carrier waves of a given frequency. Broadcast and phone transmission has conventionally used analog technology.
_
If you have an analog watch, it tells the time with hands that sweep around a dial: the position of the hands is a measurement of the time. How much the hands move is directly related to what time it is. So if the hour hand sweeps across two segments of the dial, it’s showing that twice as much time has elapsed compared to if it had moved only one segment. That sounds incredibly obvious, but it’s much more subtle than it first seems. The point is that the hand’s movements over the dial are a way of representing passing time. It’s not the same thing as time itself: it’s a representation or an analogy of time. That’s really what the term analog means. Until computers started to dominate science and technology in the early decades of the 20th century, virtually every measuring instrument was analog. If you wanted to measure an electric current, you did it with a moving-coil meter that had a little pointer moving over a dial. The more the pointer moved up the dial, the higher the current in your circuit. The pointer was an analogy of the current. All kinds of other measuring devices worked in a similar way, from weighing machines and speedometers to sound-level meters and seismographs (earthquake-plotting machines). Digital is entirely different where every information (variable) is converted into numbers (digits) and displays or stores the numbers instead. Cell phones transmit and receive calls by converting the sounds of a person’s voice into numbers and then sending the numbers from one place to another in the form of radio waves. Used this way, digital technology has many advantages. It’s easier to store information in digital form and it generally takes up less room. You’ll need several shelves to store hundreds of analog LP records, but with an MP3 player you can put the same amount of music in your pocket! Electronic book (e-book) readers are similar: typically, they can store a couple of thousand books—around 50 shelves worth—in a space smaller than a single paperback! Digital information is generally more secure: cell phone conversations are encrypted before transmission—something easy to do when information is in numeric form to begin with. You can also edit and play about with digital information very easily. Anyone can edit a photo (in digital form) in a computer graphics program, which works by manipulating the numbers that represent the image rather than the image itself. It’s easy to convert analog information into digital: you do it every time you make a digital photo, record sound on your computer, or speak over a cell phone. The process is called analog-to-digital conversion (ADC). A modem is used to convert the digital information in your computer to analog signals for your phone line and to convert analog phone signals to digital information for your computer. Remember, most physical quantities are analog, thus a conversion is needed.
_
In general, humans experience the world analogically. Vision, for example, is an analog experience because we perceive infinitely smooth gradations of shapes and colors. Most analog events, however, can be simulated digitally. Photographs in newspapers, for instance, consist of an array of dots that are either black or white. From afar, the viewer does not see the dots (the digital form), but only lines and shading, which appear to be continuous. Although digital representations are approximations of analog events, they are useful because they are relatively easy to store and manipulate electronically. In analog technology, a wave is recorded or used in its original form. So, for example, in an analog tape recorder, a signal is taken straight from the microphone and laid onto tape. The wave from the microphone is an analog wave, and therefore the wave on the tape is analog as well. That wave on the tape can be read, amplified and sent to a speaker to produce the sound. In digital technology, the analog wave is sampled at some interval, and then turned into numbers that are stored in the digital device. On a CD, the sampling rate is 44,000 samples per second. So on a CD, there are 44,000 numbers stored per second of music. To hear the music, the numbers are turned into a voltage wave that approximates the original wave. The trick is in converting from analog to digital, and back again. This is the principle behind compact discs (CDs). The music itself exists in an analog form, as waves in the air, but these sounds are then translated into a digital form that is encoded onto the disk. When you play a compact disc, the CD player reads the digital data, translates it back into its original analog form, and sends it to the amplifier and eventually the speakers. When information, music, voice and video are turned into binary digital form, they can be electronically manipulated, preserved and regenerated perfectly at high speed. The millionth copy of a computer file is exactly the same as the original.
_
The above discussion presupposes that in order to carry out digital transaction, you ought to have computer/laptop or smartphone with internet connection. But you can carry out digital transaction without internet connection and even without phone provided you have intermediary that connect you to your bank. I want to emphasize that internet and digital are not synonymous. Non-internet digital transactions involve SMS, MMS, USSD, payment Processing IVR and AEPS through 2G mobile phones. For example, you may have 2G cell phone without any internet connectivity. You can still perform digital transaction through USSD code whereby your GSM telecom service provider can act as intermediary between you and your bank. You can even perform digital transaction without any phone provided your bank agent has micro-ATM which connects your ID (e.g. Aadhaar card in India) to your bank account. All these are digital transactions although you have neither internet connection nor phone. All ATM and POS transactions are digital transactions on private networks independent of internet although they may still use internet protocols. Internet means connecting a computer to any other computer anywhere in the world via dedicated routers and servers, digitally (data in the form of 0 and1). Internet is always digital but digital data can be transferred without using internet, for example using 2G cell phones with cellular networks and using ATM/POS with private interbank networks.
_________
_________
Money, cash and currency:
_
What is money?
Throughout history there have been many different manifestations of money, both physical and electronic. Economists identify money through the roles that it serves in society. In particular, something may be considered money from the perspective of economic theory to the extent that it serves as a medium of exchange with which to make payments; a store of value with which to transfer ‘purchasing power’ (the ability to buy goods and services) from today to some future date; and a unit of account with which to measure the value of any particular item for sale.
_
Money is any clearly identifiable object of value that is generally accepted as payment for goods and services and repayment of debts within a market or which is legal tender within a country. The money can’t be in two places at once, can’t be double spent. In modern times the broader concept of “money” includes other forms of money such as bank accounts. Money as a means of exchange has been evolving way back. It is as old as man. We started from trade by barter and moved to coins and cowries and to paper money. In economics we are told that money is a store of value but the truth about it is that money stores value at the point of exchange, at the point of conversion of goods into money but as days go by the value is lost due to depreciation and devaluation. So, a lot of things affect money as we know it. Today, the present state of money is called fiat money. The thing about fiat money is that though it is a store of value, it fails to maintain that storage of value over a period of time. Every fiat money is subject to socio-political events, any negative socio-political events in a country affects value of stored money. Socio-political happenings affect the value of money; body language of the leaders of the country affects the money. So when a leader or top echelon of an administration makes a careless statement, it can affect the value of money. This aggregates into a substantial form over a period of time. This simply means that money in its present form does not provide a safe haven to store wealth, assets. Also, any money that does not have finite amount, that can be printed like fiat money cannot have a strong value, it does not provide a relative stability in storage of value.
_
Legal tender:
Legal tender is a medium of payment recognized by a legal system to be valid for meeting a financial obligation. Paper currency and coins are common forms of legal tender in many countries. Legal tender is variously defined in different jurisdictions. Formally, it is anything which when offered in payment extinguishes the debt. Thus, personal cheques, credit cards, and similar non-cash methods of payment are not usually legal tender. The law does not relieve the debt obligation until payment is tendered. Coins and banknotes are usually defined as legal tender.
_
Different measures of money supply:
Different measures of money supply include M0, M1, M2, M3 and M4. Not all of them are widely used and the exact classifications depend on the country. M0 and M1, also called narrow money, normally include coins and notes in circulation and other money equivalents that are easily convertible into cash. M2 includes M1 plus short-term time deposits in banks and 24-hour money market funds. M3 includes M2 plus longer-term time deposits and money market funds with more than 24-hour maturity. M4 includes M3 plus other deposits. The exact definitions of these measures depend on the country. The term broad money is used to describe M2, M3 or M4, depending on the local practice.
_
Cash is king in India:
Cash is money in the physical form of currency, such as banknotes and coins. The Indian payment business has been a high cash-intensive economy. To peak in the current scenario, the value of notes and coins in circulation in the economy as a percentage of GDP is ~12.2%, which is higher than countries like Russia (11.9%), Brazil (4.1%) and Mexico (5.7%). Another metric to compare cash intensity is to look at global monetary aggregates. M0 (amount of money held in bills and coins) relative to M2 (amount held in demand deposit and savings accounts) is a good indicator. For India, M0 as a percentage of M2 is over 50%, which is higher than other developing countries like Mexico (9%), South Africa (9%), or China (5%). Even in cash-intensive Egypt, M0 is 24% of M2. In addition, globally India had highest share of cash transactions among developed as well as developing countries; evident from the fact that nearly 87% of the value of all transactions in India in 2012, took place in cash. A few reasons for such high dependence on cash are factors including lack of means to use non-cash payments, existence of the black economy and lack of awareness, especially in rural India.
_____
_____
Transfer of money:
Money is believed to be first used in 600AD in China, and money transfers started about 150 years ago — around the time the telegraph was invented. Western Union completed the first transcontinental telegraph line in 1861. In 1879, WU left the telephone business. That inevitably led to money transfer becoming their primary business. In the past, transferring money was pricey, and it required lots of time and effort. One gave the money to a bank or a telegraph office, and the clerk would then send a note to the recipient, informing him to pay a specified amount. Finally, the bank or the telegraph office would send the money to adjust the imbalance in the other agency. Now, the process is similar — you go to a financial institution, and tell them to send the money to another place. The difference now is that over time, the transfer method has evolved to purely electronic, and it’s not as expensive. The main benefits of the electronic procedure are time-efficiency—completed for minutes, and safety—due to the money being tracked via an identification number. In recent years, many international money transfer companies have gone online, which has simplified the process and made it extremely popular–thus lowering the fees. You can now transfer money either through banks, or through money transfer company. Banks are always a solid solution for making payments abroad. While being trustworthy, banks tend to also have cluttered interdependent procedures, often resulting in slower service.
______
Cheque:
A cheque (or check in American English) is a document that orders a bank to pay a specific amount of money from a person’s account to the person in whose name the cheque has been issued. The person writing the cheque, the drawer, has a transaction banking account where their money is held. The drawer writes the various details including the monetary amount, date, and a payee on the cheque, and signs it, ordering their bank, known as the drawee, to pay that person or company the amount of money stated. A cheque is a negotiable instrument instructing a financial institution to pay a specific amount of a specific currency from a specified transactional account held in the drawer’s name with that institution. Both the drawer and payee may be natural persons or legal entities. Cheques are order instruments, and are not in general payable simply to the bearer as bearer instruments are, but must be paid to the payee. In some countries, such as the US, the payee may endorse the cheque, allowing them to specify a third party to whom it should be paid. Cheques have been a tempting target for criminals to steal money or goods from the drawer, payee or the banks. A number of measures have been introduced to combat fraud over the years. These range from things like writing a cheque so it is difficult to alter after it is drawn, to mechanisms like crossing a cheque so that it can only be paid into another bank’s account providing some traceability. However, the inherent security weaknesses of cheques as a payment method, such as having only the signature as the main authentication method and not knowing if funds will be received until the clearing cycle to complete, have made them vulnerable to a number of different types of fraud.
_
Cheque usage has been declining for some years, both for point of sale transactions (for which credit cards and debit cards are increasingly preferred) and for third party payments (for example, bill payments), where the decline has been accelerated by the emergence of telephone banking and online banking. Being paper-based, cheques are costly for banks to process in comparison to electronic payments, so banks in many countries now discourage the use of cheques, either by charging for cheques or by making the alternatives more attractive to customers. Cheques are also more costly for the issuer and receiver of a cheque. In particular the handling of money transfer requires more effort and is time consuming. The cheque has to be handed over in person or sent through mail. Experts have been looking for alternatives to the cheque. However, scrapping cheques would have had serious ramifications, not only for the elderly and most vulnerable in society, but also for small businesses and charities that rely on this payment method.
____
Money or postal order:
A cheque sold by a post office or bank for payment to the third party by a customer is referred to as a money order or postal order. These are paid for in advance when the order is drawn and are guaranteed by the institution that issues them and can only be paid to the named third party. This was a common way to send low value payments to third parties, avoiding the risks associated with sending cash via the mail, prior to the advent of electronic payment methods.
_____
The unbanked and the underbanked:
The word unbanked is an umbrella term used to describe diverse groups of individuals who do not use banks or credit unions for their financial transactions. They have neither a checking nor savings account. Some consumers are unbanked for a variety of reasons. These include: a poor credit history or outstanding issue from a prior banking relationship, a lack of understanding about banking system, a negative prior experience with a bank, language barriers, a lack of appropriate identification needed to open a bank account, or living paycheck to paycheck due to limited and unstable income. Underbanked consumers have either a checking or savings account, but also rely on alternative financial services. These households use non-bank money orders or non-bank check-cashing services, payday loan institutions, rent-to-own agreements or pawn shops on a regular basis. The most common groups of unbanked persons include low-income individuals and families, those who are less-educated, households headed by women, young adults and immigrants.
_
More than 2 billion adults worldwide, in both developed and developing countries, lack adequate access to banking services. Of this group, the majority isn’t excluded by choice; rather cost, distance, need, and other variables make it challenging or impossible to access banking services. Historically, banks and financial institutions haven’t seen this population as a lucrative group, because they tend to be low-income, drift in and out of the banking system, and don’t adopt high-value products, like credit. However, these populations are now becoming easier to access and, as a result, more attractive to financial institutions, because if products are scaled appropriately, they could represent a massive revenue stream. In response, financial institutions, mobile network operators (MNOs), and card networks are using digital technology like mobile phones and payment cards to access these populations in the hopes of building new streams of revenue in an increasingly competitive banking system. By leveraging phones and cards to build out financial ecosystems, hand financial access to broad swaths of people without it, and expand the range of services available to large populations, these firms have the opportunity to profit immensely. In a new report from BI Intelligence, let us take a close look at who the un- and underbanked are, the way financial institutions are using mobile phones and payment cards to access these populations, and whether there’s a profit opportunity for these stakeholders.
Here are some key takeaways from the report.
- The un- and underbanked provide an important new opportunity for payments companies that can leverage digital technology. Previously, these individuals were not seen as valuable clients because they are typically low income and, therefore, nonlucrative. But with digital technology available that can scale quickly, payments companies can gain significant market share and revenue.
- Mobile phones are a key way of bringing the unbanked into the financial system through services like mobile money. And among the underbanked in developed countries, mobile provides account access in areas underserved by brick-and-mortar branches.
- Multiple players are teaming up to build payment card and point-of-sale (POS) infrastructure in developing countries in order to provide citizens without mobile phones secure, simple access to the banking system. In developed countries, prepaid cards are functioning as checking accounts for the un- and underbanked.
- For financial institutions, a small investment in the un- and underbanked can turn into a major revenue stream. Over time, these populations can build up larger balances or provide banks and card networks with interchange or interest-based fee revenue. In the next several years, digital technology will help make these populations a key competitive market.
_________
Digital money:
Since the world’s first gold coins were produced over 2500 years ago in Lydia, western Turkey, money has played a major role in stimulating commerce and economies. Money has traditionally been considered as medium of exchange and measure of value, allowing economic transactions to be conducted between strangers over time and distance. It has given rise to organised companies and public institutions and has been instrumental in helping communities to become more productive and to improve their standard of living. For a long time, money was embodied in precious metals such as gold and silver. With the introduction of banknotes in seventh century China, money started to decouple from physical objects with intrinsic value. Today’s electronic money can be moved from our employer, to our bank account, to our favourite retail outlets without ever physically materialising. It is this virtual money that now dominates what economists call the money supply. Given the intangible character of money, it is unsurprising that major advances in information technologies have led to radical changes in the way we deal with money and payments. In the 1960s, 1970s, and 1980s, computerisation encouraged financial innovations such as credit cards and ATMs. The impact of these innovations is profound, with Moody’s, for example, estimating credit cards added $1.1trn to private consumption and GDP from 2003 to 2008. In the 1990s, the wide adoption of the internet and World Wide Web led to online banking, online shopping and e-commerce in general. The relationship between information technology and money is now closer than ever, with lending, card issuance, deposits, payments and cash management increasingly conducted using digital media. Trends are clear: there is less and less cash in circulation in economies around the world, and a larger and larger percentage of payments are not in cash. Bills and coins now account for only seven percent of the USA’s total economic transactions, and an average of seven percent in the EuroZone. In Sweden, the first European country to introduce bank notes in 1661, only three percent of its economy is represented by bills and notes. Digital money is a collection of technologies and services that will profoundly affect every society and economy in the world. The transition to digital money involves the transformation of cash, cheques, credit and debit cards from physical to digital objects that we will carry in smart mobile devices. It also encompasses the whole global payment infrastructure, including the management of personal identities and personal financial data. Digital money will likely not eliminate cash, any more than the computerised office eliminated paper. In both cases, the digital and the physical will co-exist. But there are continuing problems with cash that digital money helps resolve. Notes and coins are unhygienic in the ways in which they transfer germs, and inefficient in the cost of storing, guarding and moving. Cash-based economies have great challenges in tax collection. Improving the flow of money can provide major economic and social benefits because it reduces time lost in making transactions, queuing for tickets etc, or waiting for receipts or confirmation of payments. It was not so long ago that time was continually lost in waiting for a cheque to be written, paid-in and cleared. Digital money has the potential to remove this ‘friction’ in transactions, improving and lubricating the flow of economic and social activities. This also has the potential to ‘dis-intermediate’ financial systems, because the use of digital money no longer makes it necessary to rely on intermediate services. International travellers, for example, have typically relied on foreign exchanges to change money into local currency, often paying much higher exchange rates than interbank spot rates. Foreign exchange companies have profited by running wide spreads between buying and selling foreign currencies. This traditional form of money exchange is rapidly disappearing as travellers are able to use ATMs linking them to their home bank accounts. The prospect of digital money is likely to improve access and flow still further.
_
The ways we make payments are changing dramatically. Skidata, the Austrian company founded in 1977, was one of the first to develop mobile payment systems, originally providing electronic ticket access to turnstiles at ski resorts. In the late 1980s it was the first to provide hands-free ticketing. The diffusion of the technology has accelerated and the business has since grown to provide mobile contact-less access and transaction services in a wide range of areas such as sports and events, tourism and car parking. Consumers are readily embracing payments on smart phones. Major merchants accept mobile payments on the internet and at point-of-sale. Numerous transit and transportation systems use mobile payment. Innovations in ‘digital wallets’ run on smartphones include just about all the various items carried around in purses and wallets today that facilitate payments. The volumes of payment transactions are likely to go up by a few orders of magnitude over the next decades. In contrast to the billions of people disengaged from the banking system, the six billion mobile phone users worldwide bring unprecedented levels of connectivity. Banks and financial service companies are increasingly adopting mobile technologies to allow digital money transactions for millions for the first time. Indeed the impact of digital money will have a particularly profound effect on the world’s poorest, which is why organisations such as the World Bank and Bill and Melinda Gates Foundation are taking a strong interest in its implications and possibilities. Cash is especially disadvantageous for the poorest, who do not have the security of bank safes for their savings and are hampered by the inconvenience of transactions needing to be face-to-face rather than conducted electronically. The poor have no choice but to use cash. The emergence of digital money, which by receiving and making payments at such an increased scale lubricates the flow of innovation and economic development for all, including the poorest, presents both major opportunities and threats for citizens, corporations and governments.
______
Electronic money (Digital cash):
Electronic money is nothing more that the replacement of physical cash in the shape of coins and banknotes with an electronic equivalent. Digital cash is traditional bank money held on computers. Digital cash is a system that allows a person to pay for goods and services by transmitting a number from one computer to another. Like the serial numbers on real dollar bills, the digital cash numbers are unique. Each one is issued by a bank and represents a specified sum of real money. One of the key features of digital cash is that, like real cash, it is anonymous and reusable. Digital cash is also known as e-currency, e-money, electronic cash, electronic currency, digital money, digital currency and cyber currency, refers to a system in which a person can securely pay for goods and services electronically without necessarily involving a bank to mediate the transaction. Because the definition of electronic money is so broad as to include any sort of electronic device to store monetary value, the methods of electronic money are only limited to the existing technology. At present there are two main storage methods for electronic money, by software and by cards. The method of software money is a payment system where money is stored in a computer hard drive by means of a proprietary software program. The program creates an electronic wallet that is charged with money from a bank account, and then the user can purchase goods and services by sending the information via this electronic method. The transaction is encrypted and the identity of the user is kept hidden from the merchant. The most viable and promising electronic money system is that of storing monetary value in secure cards with microchips, known as smart cards.
_
From this definition it is obvious that electronic money is very much like physical money for all practical purposes. It is anonymous; it is given value by a financial institution; and it must be subject to be used to pay for goods and services in any sort of transaction. The new Electronic Money Institutions European Directive states that: ‘electronic money’ shall mean monetary value as represented by a claim on the issuer which is:
(i) stored on an electronic device
(ii) issued on receipt of funds of an amount not less in value than the monetary value issued
(iii) accepted as means of payment by undertakings other than the issuer
This definition is wide ranging, and attempts to be technology neutral.
_
Tatsuaki Okamoto and Kazuo Ohta list six properties of an ideal digital cash system:
- Independence. The security of the digital cash is not dependent on any physical location. The cash can be transferred through computer networks.
- Security. The digital cash can’t be copied and reused.
- Privacy (untraceability). The privacy of the user is protected; no one can trace the relationship between the user and his purchases.
- Off-line Payment. When a user pays for a purchase with electronic cash, the protocol between the user and the merchant is executed off-line. That is, the shop does not need to be linked to a host to process the user’s payment.
- Transferability. The digital cash can be transferred to other users.
- Divisibility. A piece of digital cash in a given amount can be subdivided into smaller pieces of cash in smaller amounts.
_
Since digital cash is merely an electronic representation of funds, it is possible to easily duplicate and spend a certain amount of money more than once. Therefore, digital cash schemes have been structured so that it is not possible to spend the same money more than once without getting caught immediately or within a short period of time. Another approach is to have the digital cash stored in a secure device, which prevents the user from double spending. Electronic money also encompasses payment systems that are analogous to traditional credit cards and checks. Here, cryptography protects conventional transaction data such as an account number and amount; a digital signature can replace a handwritten signature or a credit-card authorization, and public-key encryption can provide confidentiality. There are a variety of systems for this type of electronic money, ranging from those that are strict analogs of conventional paper transactions with a typical value of several dollars or more, to those (not digital cash per se) that offer a form of “micropayments” where the transaction value may be a few pennies or less. The main difference is that for extremely low-value transactions even the limited overhead of public-key encryption and digital signatures is too much, not to mention the cost of “clearing” the transaction with bank. As a result, “batching” of transactions is required, with the public-key operations done only occasionally.
_
Basic Model of Digital Cash transaction:
A Digital Cash transaction usually involves three types of users:
- a Payer or consumer
- a Payee, such as a merchant
- a financial network like a Bank with whom both Payer and Payee have accounts.
And usually involves three transactions:
- Withdrawal, the Payer transfer some money (token) from his/her bank account to his/her wallet
- Payment, the Payer transfer the money (token) to the Payee’s wallet or account.
- Deposit, the Payee receives money (token) to his/her account for selling goods and services; salary and debt repayment are also considered as deposits.
_____
The benefits of digital cash:
Electronic money has brought lots of new opportunities and possibilities. Using digital money is very easy and convenient. With electronic money, people can send mass payments to freelancers, remote workers, and others. It can also be used to pay for utilities, cell phone services, and internet access, transfer money to others, pay for goods and services online and offline, trade and much more. Electronic transactions are carried out almost instantly, while problems such as lines, change, and other are done away with. Digital cash saves not only time but money as well. All transfers within one payment system are available at a little to no cost. By using electronic money you stay anonymous and you are the only person who has access to your personal data. Electronic payment systems allow for anonymous payments. All account information is known only to the owner of that account, everyone else sees just a wallet number. In order to withdraw money or replenish your account balance, you don’t have to go anywhere, sign service agreements, present documents, and copies. Deposits and withdrawals come into effect immediately, all this can be done from home. With digital money, you have access to your account from anywhere and at any time. You’ll need only internet access to control your funds and perform operations. The number of services that accept electronic money is constantly growing.
_
_
Disadvantages of digital cash:
Although there are many benefits to digital cash, there are also many significant disadvantages. These include fraud, failure of technology, possible tracking of individuals and loss of human interaction. Fraud over digital cash has been a pressing issue in recent years. Hacking into bank accounts and illegal retrieval of banking records has led to a widespread invasion of privacy and has promoted identity theft. There is also a pressing issue regarding the technology involved in digital cash. Power failures, loss of records and undependable software often cause a major setback in promoting the technology. Privacy questions have also been raised; there is a fear that the use of debit cards and the like will lead to the creation by the banking industry of a global tracking system. Some people are working on anonymous e-cash to try to address this issue.
_________
Cash versus digital cash:
________
________
The difference between digital currency, virtual currency and cryptocurrency:
Digital currency can be defined as an Internet-based form of currency or medium of exchange distinct from physical (such as banknotes and coins) that exhibits properties similar to physical currencies, but allows for instantaneous transactions and borderless transfer-of-ownership. Both virtual currency and cryptocurrency are types of digital currencies but converse is not true. Although digital currency provides a host of features like ease-of-use, anonymity, efficiency there are potential issues with its use like tax evasion, money laundering, and instability in exchange rates and so on. Digital currencies are exactly what they sound like: currencies stored and transferred electronically. Any money based in 1’s and 0’s meets this definition; dollars stored in a bank account are supposed to be a representation of dollars actually held somewhere, whereas physical bitcoins are a representation of their digital counterparts. From the perspective of economic theory, whether a digital currency may be considered to be money depends on the extent to which it acts as a store of value, a medium of exchange and a unit of account. How far an asset serves these roles can differ, both from person to person and over time. And meeting these economic definitions does not necessarily imply that an asset will be regarded as money for legal or regulatory purposes.
Types of digital currencies:
- Virtual currency:
A virtual currency has been defined in 2012 by the European Central Bank as “a type of unregulated, digital money, which is issued and usually controlled by its developers, and used and accepted among the members of a specific virtual community”. The US Department of Treasury in 2013 defined it more tersely as “a medium of exchange that operates like a currency in some environments, but does not have all the attributes of real currency”. The key attribute a virtual currency does not have according to these definitions, is the status as legal tender. Virtual currencies were developed because of trust issues with financial institutions and digital transactions. Though they aren’t even considered to be “money” by everyone, virtual currencies are independent of traditional banks and could eventually pose competition for them.
_
- Cryptocurrency:
A cryptocurrency is a type of digital token that relies on cryptography for chaining together digital signatures of token transfers, peer-to-peer networking and decentralization. A cryptocurrency is a digital asset designed to work as a medium of exchange using cryptography to secure the transactions and to control the creation of additional units of the currency. Cryptocurrencies are a subset of alternative currencies, or specifically of digital currencies. Bitcoin became the first decentralized cryptocurrency in 2009. Since then, numerous cryptocurrencies have been created.
_
Bitcoin vs. digital cash:
_
_
Digital transaction of Bitcoin vs. digital cash:
_
- Digital cash:
Most of the traditional money supply is bank money held on computers. This is also considered digital currency. One could argue that our increasingly cashless society means that all currencies are becoming digital (sometimes referred to as “electronic money”), but they are not presented to us as such.
_____
The synopsis of various currencies vis-à-vis digital transaction is depicted in the figure below:
_________
_________
Payment system:
Money and payment systems are intrinsically linked. In order for an asset to function as a medium of exchange, there needs to be a secure way of transferring that asset — a payment system. And for any system other than the exchange of physical banknotes or coins, a means of recording the values stored is also needed — a ledger. The word “payment system” is a system that enables payment to be effected between a payer and a beneficiary, involving clearing(wherein the payment service provider acts as a counterparty between the buyer and seller by calculating the obligations between them and guaranteeing its settlement), payment (act of paying or transacting) or settlement service (the final act of changing the records of ownership of the asset transacted, either after netting all the cross obligations or on gross terms) or all of them. Modern payment systems are computerised and most money exists only as digital records on commercial banks’ accounts. Historically, payments have been viewed as utility products, fundamentally transactional and tactical in nature, undifferentiated and volume-driven. A payment was often perceived as merely the final step in a transaction, with limited opportunity to provide value-added services or solutions. However, this competitive landscape is getting redefined by the advent of non-traditional payment providers, evolution of new solutions, changing customer expectations and changing global demographics. A shift in global trade flows and the currency market’s role remains crucial in formulating the roadmap for invention and adoption of differentiated payment services. A vast geographical and demographic stretch lies beyond the formal payment system in emerging countries. This unbanked and under banked market has a huge revenue generation potential for financial institutions.
_
A payment system is any system used to settle financial transactions through the transfer of monetary value, and includes the institutions, instruments, people, rules, procedures, standards, and technologies that make such an exchange possible. A common type of payment system is the operational network that links bank accounts and provides for monetary exchange using bank deposits. What makes a payment system a system is the use of cash-substitutes; traditional payment systems are negotiable instruments such as drafts (e.g., checks) and documentary credits such as letters of credit. With the advent of computers and electronic communications a large number of alternative electronic payment systems have emerged. These include debit cards, credit cards, electronic funds transfers, direct credits, direct debits, internet banking and e-commerce payment systems. Some payment systems include credit mechanisms, but that is essentially a different aspect of payment. Payment systems are used in lieu of tendering cash in domestic and international transactions and consist of a major service provided by banks and other financial institutions.
_
Payment systems may be physical or electronic and each has its own procedures and protocols. Standardization has allowed some of these systems and networks to grow to a global scale, but there are still many country- and product-specific systems. Examples of payment systems that have become globally available are credit card and automated teller machine networks. Specific forms of payment systems are also used to settle financial transactions for products in the equity markets, bond markets, currency markets, futures markets, derivatives markets, options markets and to transfer funds between financial institutions both domestically using clearing and real-time gross settlement (RTGS) systems and internationally using the SWIFT network.
_
How to define digital payments?
Payments are made using payment instruments. Cash, for example, is a payment instrument. So too are checks. However, digital payments are not one instrument but rather an umbrella term applied to a range of different instruments used in different ways. Since there is no one standard definition of a digital or e-payment, you should settle on a clear and implementable definition at the start of any measurement exercise. The subject matter is complex, but there are two key dimensions of categorization that are most important:
- The nature of the payment instrument: through which means—paper or digital—are the instructions carried.
- The payer-payee interface: whether the payer, payee, or both use an electronic medium in a payment transaction.
_
Electronic (digital) payment:
The term electronic (digital) payment can refer narrowly to a payment for buying and selling goods and services offered through the Internet/private network, or broadly to any type of electronic funds transfer. It is transfers of value which is initiated and/or received using electronic devices and channels to transmit the instructions. Note that digitizing is often applied to processes other than payments: hence a government could digitize its accounting system, but still make payments by paper (check or cash).
_
Who is acquirer Bank?
The bank which has acquired the transaction or the bank whose device has been used or the bank of the payee/ merchant.
Who is issuer Bank?
Issuer is the bank in which the user, customer or payer hold his/ her account.
_____
Broad definition of digital transaction:
Digital transaction is defined as sale or purchase of goods and services, whether between businesses, households, individuals, governments, and other public or private organisations, conducted over computer-mediated networks. Out of order, payment and delivery of goods and services, at least one must be conducted digitally over internet/private network to be classified as digital transaction. The relationship between information technology and money is now closer than ever, with lending, card issuance, deposits, payments and cash management increasingly conducted using digital media.
_
Narrow definition of digital transaction as proposed in India:
Digital transaction is defined as transaction in which the customer authorizes the transfer of money through electronic means, and the funds flow directly from one account to another. These accounts could be held in banks, or with entities/ providers. These transfers could be done through means of cards (debit / credit), mobile wallets, mobile apps, net banking, Electronic Clearing Service (ECS), National Electronic Fund Transfer (NEFT), Immediate Payment Service (IMPS), pre-paid instruments or other similar means.
_
Digital transaction involve digital device to transfer fund:
_
Electronic payments systems can be divided broadly into two major categories:
- Cash-like systems that transfer money using electronic tokens that represent value with no intermediary instruments, instructions or services – such as a pre-paid e-wallet or electronic purse.
- Account-based systems that are used to transfer a numerical value that represents money, from one account to another. Account-based instruments such as cheques, money orders and credit cards are not money –but instead provide evidence of the intention and ability to pay via an account-based system
_
The various factors that have led the financial institutions to make use of electronic payments are:
- Decreasing technology cost:
The technology used in the networks is decreasing day by day, which is evident from the fact that computers are now dirt-cheap and Internet is becoming free almost everywhere in the world.
- Reduced operational and processing cost:
Due to reduced technology cost the processing cost of various commerce activities becomes very less. A very simple reason to prove this is the fact that in electronic transactions we save both paper and time.
- Increasing online commerce:
_
There are also many problems with the traditional payment systems that are leading to its fade out.
Some of them are enumerated below:
- Lack of Convenience:
Traditional payment systems require the consumer to either send paper cheques by snail-mail or require him/her to physically come over and sign papers before performing a transaction. This may lead to annoying circumstances sometimes.
- Lack of Security:
This is because the consumer has to send all confidential data on a paper, which is not encrypted, that too by post where it may be read by anyone.
- Lack of Coverage:
When we talk in terms of current businesses, they span many countries or states. These business houses need faster transactions everywhere. This is not possible without the bank having branch near all of the companies’ offices. This statement is self-explanatory.
- Lack of support for micro-transactions:
_
The problems in implementing electronic payment systems are:
- Preventing double-spending: copying the “money” and spending it several times. This is especially hard to do with anonymous money.
- Making sure that neither the customer nor the merchant can make an unauthorized transaction.
- Preserving customer’s confidentiality without allowing customer’s fraud.
___
There are several payment methods supporting electronic payments over the internet/private network:
- Electronic payment cards (credit, debit, and charge)
- Virtual credit cards
- E-wallets (or e-purses)
- Smart cards
- Electronic cash (several variations)
- Wireless payments
- Stored-value card payments
- Loyalty cards
- Person-to-person payment methods
- Payments made electronically at kiosks
_
Various technological methods of digital transactions:
1. Electronic Tokens:
An electronic token is a digital analog of various forms of payment backed by a bank or financial institution. There are two types of tokens:
a) Pre-paid tokens – These are exchanged between buyer and seller, their users pre-pay for tokens that serve as currency. Transactions are settled with the exchange of these tokens. Example include digital wallet.
b) Post Paid Tokens – are used with fund transfer instructions between the buyer and seller. Examples include credit/debit cards.
2. Electronic or Digital Cash:
This combines computerized convenience with security and privacy that improve upon paper cash. Digital cash can be transferred from payer’s account to payee’s account. Example includes net banking.
3. Electronic Cheques:
The electronic cheques are modelled on paper checks, except that they are initiated electronically. They use digital signatures for signing and endorsing and require the use of digital certificates to authenticate the payer, the payer’s bank and bank account. They are delivered either by direct transmission using telephone lines or by public networks such as the Internet.
____
Overview of modes of digital transactions in India:
Remember, different countries have different modes of digital transactions.
_
Following are common modes of digital transactions:
- Automated Teller Machine (ATM): ATM is a combined computer terminal, with cash vault and record-keeping system in one unit, permitting customers to enter the bank’s book keeping system with a plastic card containing a Personal Identification Number (PIN). It can also be accessed by punching a special code number into the computer terminal linked to the bank’s computerized records. It is cash dispensing machines, deposits, funds transfer between two or more accounts and bill payments.
- Electronic Purses/Wallets: E-wallets that store card numbers and cash. This is a virtual wallet that can store credit card, debit card and other information.
- Electronic Funds Transfer at Point of Sale (EFT/POS): EFT/POS is an online system that involves the use of plastic cards in terminal on merchants’ premises and enables customers to transfer funds instantaneously from their bank accounts to merchant accounts when making purchases.
- Credit Cards: This is a plastic card for payment for the goods or items delivered.
- Debit Cards: These were a new form of value transfer, where the card holder after keying of a PIN, uses a terminal and network to authorize the transfer of value from their account to that of a merchant.
- Smart Cards: A smart card is a plastic card with a computer chip inserted into it and that store and transacts data between users.
- Mobile: A mobile payment is an electronic payment made through a mobile device (e.g., a cell phone or a PDA). This uses a mobile device to initiate and confirm electronic payment.
- Telephone Banking: Telephone banking or telebanking is a form of virtual banking that deliver financial services through telecommunication devices.
- Personal Computer Banking (Home Banking): This term is used for a variety of related methods whereby a payer uses an electronic device in the home or workplace to initiate payment to a payee.
- Online/Internet Payments: This is the means by which customers transact business with a bank through the use of the Internet network. Customers can access their bank accounts and make transfers through a website provided by the bank and complying with some rigorous security checks.
- Electronic Cheque: Electronic cheques are used in the same way as paper cheque – the clearing between payer and payee is based on existing and well known banking settlement system.
- Digitized ‘E-Cash’ Systems: E-cash payment system takes the form of encoded messages and representing the encrypted equivalent of digitized money.
- Digital P2P Payments: Bank-based P2P system allows users to send money from bank accounts and credit cards electronically. It employs e-mail services to notify recipients of an impending funds transfer.
_
Alternative payments:
Alternative payments refer to payment methods that are used as an alternative to credit card payments. Most alternative payment methods address a domestic economy or have been specifically developed for electronic commerce and the payment systems are generally supported and operated by local banks. Each alternative payment method has its own unique application and settlement process, language and currency support, and is subject to domestic rules and regulations. The most common alternative payment methods are debit cards, charge cards, prepaid cards, direct debit, bank transfers, phone and mobile payments, checks, money orders and cash payments.
_
Micropayment using digital cash transaction:
Internet transactions often involve micro payments, such as the sale of a cell phone ring tone for 50 cents. Credit card companies charge a fee for each transaction, so using a credit card to make these small purchases may cost more than the product itself. An electronic cash transaction does not need to use a credit card network, so the customer can avoid paying the credit card fee. A micropayment is a financial transaction involving a very small sum of money and usually one that occurs online. A number of micropayment systems were proposed and developed in the mid-to-late 1990s, all of which were ultimately unsuccessful. A second generation of micropayment systems emerged in the 2010s. There are a number of different definitions of what constitutes a micropayment. PayPal defines a micropayment as a transaction of less than £5 while Visa defines it as a transaction under 20 Australian dollars. While micropayments were originally envisioned to involve very small sums of money, practical systems to allow transactions of less than 1 USD have seen little success. One problem that has prevented the emergence of micropayment systems is a need to keep costs for individual transactions low, which is impractical when transacting such small sums even if the transaction fee is just a few cents.
_
Comparison of payment systems:
Comparison of payment systems (also known as comparison of payment processing services, comparison of payment processors, or comparison of merchant services) is a list displaying comparative information and fee rates on various payment systems (also payment processing services, payment processor, or merchant services) for consumer use. Information such as these are compared and shown: seller’s/merchant’s fees, buyer’s fees, banking transfer fees, clearing-house fees, interchange fees, chargeback/return fees, currency conversion fees, monthly fees, usage, verification time, deposit time, technology support, customer-service quality, etc. Consumer can choose any type of digital payment system depending on transaction fees, time taken for transaction, convenience, privacy and security.
_
Default payments:
The recent growth of digital commerce is transforming consumer payments like never before. In particular, consumer behaviour dynamic called “default payments”—a payment made with credit card, debit card, and bank account details that have been stored for on-going and future transactions—is taking root in unexpected ways. Although it only accounts for 8% of retail sales today, e-commerce is growing at a faster clip than other channels, and is expected to reach $0.5 trillion by 2018. A study confirmed that default payments are already the dominant mode of payment in digital transactions, used extensively in online shopping, with mobile apps, and with mobile wallets at the physical point-of-sale (PoS) terminal. Mobile diary participants made 84%of their digital payments using default payment options.
_
Hidden payments:
Payments processed through non-bank systems are ‘hidden payments’ estimated to have reached 24-40 billion dollars in 2014. This would make them around 10% of non-cash payments, at the upper end of this range. ‘Hidden payments’ include those made through closed loop cards, mobile apps, digital wallets, mobile money and virtual currencies. The growing level of ‘hidden payments’ is a disintermediation threat for banks and those within the financial services industry. There are also wider implications for regulators and consumers around some elements of these payment methods. This includes dispute resolution, consumer protection, information security, privacy, fraud and anti-money laundering provisions.
_____
_____
The figure below shows traditional and digital payment system:
____
____
Payment gateway:
A payment gateway is a merchant service provided by an e-commerce application service provider that authorizes credit card or direct payments processing for e-businesses and online retailers. The payment gateway may be provided by a bank to its customers, but can be provided by a specialised financial service provider as a separate service. A payment gateway facilitates a payment transaction by the transfer of information between a payment portal (such as a website, mobile phone or interactive voice response service) and the front end processor of acquiring bank.
_
Payment service provider (PSP):
A payment service provider offers shops online services for accepting electronic payments by a variety of payment methods including credit card, bank-based payments such as direct debit, bank transfer, and real-time bank transfer based on online banking. Typically, they use a software as a service model and form a single payment gateway for their clients (merchants) to multiple payment methods. Typically, a PSP can connect to multiple acquiring banks, card, and payment networks. In many cases, the PSP will fully manage these technical connections, relationships with the external network, and bank accounts. This makes the merchant less dependent on financial institutions and free from the task of establishing these connections directly, especially when operating internationally. Furthermore, by negotiating bulk deals they can often offer cheaper fees. Furthermore, a full-service PSP can offer risk management services for card and bank based payments, transaction payment matching, reporting, fund remittance and fraud protection in addition to multi-currency functionality and services. Some PSPs provide services to process other next generation methods (payment systems) including cash payments, wallets, prepaid cards or vouchers, and even paper or e-check processing. A PSP is thus a much broader term than a payment gateway which is how the payment card industry refers to them. PSP fees are typically levied in one of two ways: as a percentage of each transaction or a fixed cost per transaction.
__
An Internet Merchant Account (IMA) allows merchants to accept debit/credit card payments directly to their business bank account, online. Due to the stringent criteria required for an Internet Merchant Account (IMA), many smaller businesses opt for a payment processing company instead. Using a Payment Gateway, provided by a Payment Service Provider (PSP) offers an alternative for businesses whose card-based-turnover is too low or who fail to meet the criteria for an Internet Merchant Account (IMA). AT Integrated ecommerce platform includes and automates all technical aspects of accepting online payments. It can accept online payments using a combination of online payment processors at the same time
_
Online payment process:
Online payment refers to money that is exchanged electronically. Typically, this involves use of computer networks, the internet and digital stored value systems. When you collect a payment over the internet, you are accepting an online payment. Online payment usually is the transaction that results in transfer of monetary funds from the customer bank or credit card account to your bank account. The online payment can be done from a credit card, checking account or other clearing house like PayPal for example. Merchants accepting online payments need to comply with a list of security requirements. The online payment specific security is designed to decrease the chance of the billing and personal information being stolen. The transfer needs to occur over secure encrypted connection. In the cases of recurring billing where customer data is stored, the merchant needs to enforce a longer list of security features and protocols that are usually referred to as PCI (Peripheral Component Interconnect) compliance requirements. Recurring billing systems that employ online payment procedures need to be periodically scanned for security vulnerabilities. To accept an online payment the merchant needs to have access to an Online Payment Gateway. The online payment gateway is a service provider that is integrated with the credit card and transfers the online payment information between the merchant and the payment processor. An e-commerce online payment system facilitates the acceptance of electronic payment for online transactions. Also known as a sample of Electronic Data Interchange (EDI), e-commerce online payment systems have become increasingly popular due to the widespread use of the internet-based shopping and banking.
The typical online payment process has the following stages:
- Customer submits the payment information to the merchant. For example customer completes the payment form on the merchant website and submits the information.
- The merchant submits the payment information to the online payment gateway.
- The online payment gateway submits the payment to the payment processor.
- The payment processor authorizes the payment and responds to the payment gateway
- The payment gateway responds back to the merchant
- The merchant responds back to the customer showing if the online payment was successful or not and taking the appropriate action.
_______
_______
The figure below shows key barriers for adoption of digital transactions in India:
Barriers to adoption of digital transaction differ from country to country.
_____
_____
Pros and Cons of digital payment and digital transactions:
Digital payments have several advantages, which were never available through the traditional modes of payment. Some of the most important are:
– Privacy
– Integrity
– Compatibility
– Good transaction efficiency
– Acceptability
– Convenience
– Mobility
– Low financial risk
– Anonymity
- Perhaps the greatest advantage of e-payments is the convenience. Individuals can pay their bills and make purchases at unconventional locations 24 hours a day, 7 days a week, 365 days a year. There is no waiting for a merchant or business to open. Vacationers and others away from home need not worry that they forgot to drop off the payment for the utilities or mail the check for their credit card bill. They can simply pull up their account online and pay their bills on the road.
- This leads to the second best benefit of e-payments- they save time. Once the initial set-up of the payment system for each account is completed, an individual can pay his bills in a flash. In a research study Marketwatch.com found that the average American, who writes checks and mails them for payment, spends over 24 hours during the course of a year paying bills. E-payments have reduced the amount of time spent on bill management or payment by about 60%. This has given busy individuals more time to spend doing those things they enjoy.
- The cost of e-payments is yet another benefit. For the majority of merchants, vendors, and businesses, there is no fee or charge to pay online. For others, the fee is nominal. While there are no additional charges for making a cash payment, trips to the store typically cost money, and checks also need postage. Compared to the cost of postage, check writing fees and trips to the post office, individuals paying their bills online can save hundreds of dollars per year. In this day and age, reducing expenses is quite important for many individuals.
- Despite the belief of many to the contrary, e-payments are secure. They may even be more secure than the old fashion way of mailing in a check. According to most sources, most instances of identity theft occur by stealing mail out of a person’s mailbox or from discarded trash, not over the Internet. Encryption technology allows an individual’s personal financial data to be scrambled before it is sent electronically. It also lowers the risk of human error by reducing the number of people touching the payment once it leaves the payer.
- Transparency and tax coverage: Transparency can be brought to system by digital transactions. For example, 20 million fake ration cards were weeded out and 42000 million leaks were plugged on digitization of Public Distribution System in India. Similar advantages can be tapped out by digitizing payments on other Government projects like infrastructure. Only 3 percent of over 1.3 billion people in India are estimated to pay income tax. This percentage can be significantly improved if tax authorities have information on people with informal income sources other than salaries.
- Increased Sales: As Internet banking and shopping become widespread, the number of people making cash payments is decreasing. In a 2014 survey, Bankrate established that more than 75 percent of those surveyed carry less than $50 a day, meaning electronic alternatives are increasingly becoming the preferred payment option. As such, e-payment enables businesses to make sales to the customers who choose to pay electronically and gain a competitive advantage over those that only accept traditional methods.
___
On the flip side, with so many benefits to using e-payments, it’s important to remember that there are negative aspects too. Some of the biggest downsides of e-payments are the lack of authentication, repudiation of charges and credit card fraud. There is no way to authenticate or verify that the individual entering the information online is who they say they are. There is no request for picture identification or even a signature. Therefore, an unauthorized user may carry out transactions in your name before you have time to alert authorities the information has been taken. Because no identifying information is provided at the time of the online payment, an individual may have an extremely hard time disputing a charge later. Further, given the benefits of convenience and speed that come along with e-payments, this creates the perfect opportunity for fraudulent credit card transactions. One of the other disadvantages of e-payments is that most sites require you to open an online account with them. You need to register with the institution in order to be authorized to perform money transactions with them. While the overall payment process is efficient, the initial registration to a given site can be time-consuming. It also involves a username and a password, which implies the need of password protection, to maintain an e-payment account at each organization. If a person has more than one or two accounts, e-payments can become extremely cumbersome. At times, there occur millions and millions of requests at a time which gets difficult to handle. In case of hardware failures of the online transaction processing systems, visitors of website get in trouble and their online transactions get effected. Electricity problem is another issue, i.e. if there is shortage in electric supply additional backup facilities like generators and related hardware is a must. The fundamental of operation of online transaction systems is atomicity. Atomicity ensures that if any step fails in the process of transaction, the entire transaction must fails, due to which the same steps have to be repeated again and again while filling forms which causes dissatisfaction among buyers.
_____
Electronic Payment System Disadvantages:
- Internet Connection:
Not everyone enjoys the luxury of having a stable and fast Internet connection at home. Aside from having a personal computer or laptop, having stable Internet access at home is a basic prerequisite to performing electronic banking. Of course, people can always use a public computer with Internet access; however, the security of public computers is always a concern.
- Computer Know-How:
Conducting a successful electronic banking transaction, like paying bills online, requires basic computer skills and knowing your way around the Internet. Being computer-literate is not common to everyone—especially seniors who might not have grown up using computers—and this is a major disadvantage to electronic banking.
- Loss of Human Touch:
Some people still value talking and interacting with bank tellers, managers and other bank clients. Electronic banking takes the majority of these “human interactions” away, leaving the banking experience as a very hands-off, impersonal process.
- Password Threats:
In case of e-banking or online financial transactions, you need to be a registered user with the respective website. Though most transactions involve the use of one-time passwords thus ensuring safety to a considerable extent, some parts of a transaction, or your personal details and bank account information is accessible through your credentials for the online portal. This gives rise to the need of password protection when handling financial accounts online. Also, if you are transacting with multiple financial institutions or have accounts with multiple banks, the risk of privacy breach is multiplied. For some, maintaining multiple accounts online feels tedious.
- Limitations on Amount and Time:
For withdrawal or fund transfer, certain banks may impose limits on the amount or the number of daily transactions, whereby an amount exceeding a certain figure cannot be withdrawn at once, or only a certain number of transactions are allowed per day. While this is taken as a safety measure, some may find it inconvenient. The access to money may be delayed in case of electronic modes as against having physical access to money. In case of taking electronic payments, the payment terms may need to be longer. When different electronic payment services do not cooperate with one another, e-currency exchange services may need to be opted for.
- Security Concerns:
One of the biggest disadvantages of doing electronic banking is the question of security. With the prevalence of keyloggers, phishing emails, trojans and other online threats, it is natural for people to be concerned with the security of their identity, funds and electronic banking transactions. Using antivirus and similar programs is not full-proof. People worry that their bank accounts can be hacked and accessed without their knowledge or that the funds they transfer may not reach the intended recipients. When transacting online, your personal or account information and credit card number is exposed over the Internet. This leads to the risk of your account being hacked. Hackers may use your identity for fraudulent activities or make huge fund transfers from your account, which could mean financial losses for you.
- False Identity:
There are no means to verify if the person entering information online is the same person he claims to be. This is because unlike physical transactions, the individual is not present in person, and one’s identity is not verified using a photograph or a physical signature. Mostly, electronic cash transactions are based on cryptographic systems. Information being transferred is encoded by means of numeric keys when the transaction details travel across the web. Though electronic payments carry less risk of forgery, the keys are vulnerable to attack.
- Anonymity and Privacy Concerns:
All the transaction and user details are recorded by the payment systems you are using, and stored in their database. This leads to lack of anonymity. Cases of identity theft have raised privacy concerns in electronic payments. If credit card details are not sent over a secure server, if online transactions are not carried out over a secure Internet connection, if virus protection software or firewalls are not in place, or if data encryption techniques are not used, there is a serious risk of privacy breach. In the absence of proper security measures, sensitive information may be exposed to hackers, leading to illegitimate use of your identity or money.
- Additional Cost and Effort:
One of the downsides to accepting electronic transactions is that you’ll have to pay fees for these services. Depending on how you process your transactions, you might be charged various processing fees, which can cut into your profits. Talk with your bank or whoever sets up your electronic transactions to learn if you will have a gateway fee, processing fees and transaction fees, and what they will be. Some systems require setup fees, while some others enforce a certain number of transactions every month. Electronic payment systems need Internet access, which may invite additional costs. Setting up the account, accessing the Internet, familiarizing oneself with the interface and operating it efficiently, involves additional effort, and may be cumbersome for some.
- Loss of Payment Cards:
Electronic payments involve the use of payment cards (credit and debit cards, ATM cards, identity cards, etc.) And this involves the risk of their theft or loss. In case a lost smart card falls in the wrong hands or if it is stolen, your identity is at the risk of theft and the money in the account that the card is linked to, may be spent by fraudulent users. There are measures to inform the bank about the loss of your card and get it blocked. But the time between losing the card and blocking it, is critical. Unauthorized users may carry out transactions in your name during that period.
________
Electronic billing:
Electronic billing or electronic bill payment and presentment, is when a company, organization, or group sends its bills over the internet, and customers pay the bills electronically. Billers, bankers, aggregators and consolidators can play various roles in the overall process. Once roles are defined, it is easier to identify which model is most appropriate for the client’s strategy. Billers may also implement more than one model in order to best serve their clients. Because the industry is continuously changing and redefining, the options and opportunities will continue to expand. Due to the multiple benefits offered by the electronic billing system many people prefer to take this mode nowadays. The electronic billing system is also widely accepted by various government organizations for the benefit of people at large. The electronic billing system can be used to transact with a particular service provider or in general with all the service providers utilized by the user.
Advantages of electronic billing:
1) The first advantage is that it offers a paperless mode of transaction which is also environmentally friendly and clutter free for both the receiver and sender of the electronic billing.
2) The online billing services are one of the least expensive forms of billing when compared to the traditional billing.
3) The electronic billing system is absolutely hassle free as one can protect the bill with the help of password and can be opened only by the recipient.
4) The electronic billing services are both customer friendly and also beneficial for the bill generators as there is focus on the process rather than on the mode of bill dispatch.
5) The electronic billing also provides a great advantage of saving time and effort that are normally lost in a traditional billing system. Besides there is no loss of bill when making use of the electronic mode of billing.
Disadvantages of electronic billing:
1) Most of the online billings systems are outsourced. As a result of the outsource billing there is a fee involved when making use of this system of billing.
2) With online billing system there is always fear of safety and security to the personal information due to the increased spywares and malwares being rampant on the internet.
3) When the electronic payment system is opted the customer account gets instantly debited for the funds that need to be paid while in a traditional billing system the customer gets sometime between the billing receipt and actual payment.
4) There is likelihood of many disputes that may arise due to the downtime of internet on the website that support electronic billing system. This can lead to many users being dissatisfied with the entire system and reduction in its use.
_______
E-commerce:
E-commerce is a transaction of buying or selling online. Electronic commerce draws on technologies such as mobile commerce, electronic funds transfer, supply chain management, Internet marketing, online transaction processing, electronic data interchange (EDI), inventory management systems, and automated data collection systems. Modern electronic commerce typically uses the World Wide Web for at least one part of the transaction’s life cycle although it may also use other technologies such as e-mail. Along with the e-commerce and its unique charm that has appeared gradually, virtual enterprise, virtual bank, network marketing, online shopping, payment and advertising, such this new vocabulary which is unheard-of and now has become as familiar to people. This reflects that the e-commerce has huge impact on the economy and society from the other side. E-Commerce has become an important tool for small and large businesses worldwide, not only to sell to customers, but also to engage them. In 2012, ecommerce sales topped $1 trillion for the first time in history. Mobile devices are playing an increasing role in the mix of E-Commerce, this is also commonly called mobile commerce, or m-commerce. In 2014, one estimate saw purchases made on mobile devices making up 25% of the market by 2017. The e-commerce market continues to grow. Online sales accounted for more than a third of total U.S. retail sales growth in 2015, according to data from the U.S. Commerce Department. Web sales totalled $341.7 billion in 2015, a 14.6% increase over 2014. E-commerce conducted using mobile devices and social media is on the rise as well: Internet Retailer reported that mobile accounted for 30% of all U.S. e-commerce activities in 2015. And according to Invesp, 5% of all online spending was via social commerce in 2015, with Facebook, Pinterest and Twitter providing the most referrals.
_
E-Commerce or Electronics Commerce is a methodology of modern business which addresses the need of business organizations, vendors and customers to reduce cost and improve the quality of goods and services while increasing the speed of delivery. E-commerce refers to paperless exchange of business information using following ways.
_
E-Commerce business models can generally categorized in following categories.
- Business – to – Business (B2B)
- Business – to – Consumer (B2C)
- Consumer – to – Consumer (C2C)
- Consumer – to – Business (C2B)
- Business – to – Government (B2G)
- Government – to – Business (G2B)
- Government – to – Citizen (G2C)
_
Advantages of e-commerce:
- Enhances convenience: Customers can make orders for goods at their own convenience and from the comfort of their homes without having to travel to the business premise. Orders are also delivered to them at their most ideal locations. It’s the best shopping option for people who are always busy.
- Allows for product and price comparison: Again, when making purchases, customers want to get the best deals. This business model allows for product and price comparison by consumers so that the best products are bought at the fairest prices. They can also enjoy extra benefits like discounts, coupons, items on sale and also get the best deals.
- Easy fund-raising for start-ups ventures: So many people have the desire to venture into business but lack sufficient funds to set up shop. Leasing a physical store can be quite expensive. E-commerce makes it easier for start-ups to do business and grow.
- Efficient: Resources are used efficiently since most of the business services are automated. Business owners sometimes spend a lot of resources meeting business needs and this eats into profits. E-commerce thrives on efficiency.
- Customer reach: It’s easier to reach many customers on the internet. Using social media links and good search engine optimization strategies, an online business can increase brand awareness and grow its customer base.
- Prompt payments: Payments are fast since online stores use electronic or mobile transactions payment methods. The mobile wallet system for merchant accounts drive up sales and increase revenue generation.
- Ability to sell different products: The flexibility of conducting business over the internet makes it possible for entrepreneurs to display and sell several products and also cater to a wider demographic.
_
Disadvantages of e-commerce:
- Poor quality products: You don’t physically see and inspect whatever you are paying for before it’s delivered. Customers, therefore, run the risk of falling victim to false marketing and buying poor quality products from the virtual shop.
- Impulsive purchases: Online stores display a large number of products and due to the convenience of shopping, customers can find themselves making bad financial decisions through impulsive purchases.
- Internet scammers: The internet is a good thing but some people have decided to use it for all the wrong reasons. Scammers have made this type of business model unattractive for some consumers.
- Lack of after sales support: As a result of lack of physical premises, customers find it hard to access after sales support. It can take up to several days before any help is accorded to a customer in need.
- Fast changing business environment: Technology evolves so fast. Some entrepreneurs find it hard to keep up and lose a lot of business in the process. This may make business growth unattainable.
- Loss of personal touch: Business is all about relationships. This business model erodes the personal touch between a customer and the business owner. Cultivating loyalty can thus be a problem since there are many such businesses that provide different options.
- Delivery of goods can get delayed: It takes time before the goods ordered for are delivered. Sometimes the delivery delays and this inconveniences the customer. This is different from physical business premises where customers walk out with the products bought.
_
Digital marketing:
Digital marketing is an umbrella term for the marketing of products or services using digital technologies, mainly on the Internet, but also including mobile phones, display advertising, and any other digital medium. Digital marketing such as search engine optimization (SEO), search engine marketing (SEM), content marketing, influencer marketing, content automation, campaign marketing, and e-commerce marketing, social media marketing, social media optimization, e-mail direct marketing, display advertising, e–books, optical disks and games, are becoming more and more common in our advancing technology. In fact, this extends to non-Internet channels that provide digital media, such as mobile phones (SMS and MMS), callback and on-hold mobile ring tones. The whole idea of digital marketing can be a very important aspect in the overall communication between the consumer and the organisation. This is due to digital marketing being able to reach vast numbers of potential consumers at one time. Another advantage of digital marketing is that consumers are exposed to the brand and the product that is being advertised directly. To clarify the advertisement is easy to access as well it can be accessed any time any place. However, with digital marketing there are some setbacks to this type of strategy. One major setback that is identified is that Digital marketing is highly dependent on the internet. This can be considered as a setback because the internet may not be accessible in certain areas or consumers may have poor internet connection.
_
Digital Transaction Management (DTM):
Digital Transaction Management (DTM) is a category of cloud services designed to digitally manage document-based transactions. DTM removes the friction inherent in transactions that involve people, documents, and data to create faster, easier, more convenient, and secure processes. DTM goes beyond content and document management to include e-signatures, authentication and nonrepudiation; document transfer and certification; secure archiving that goes beyond records management; and a variety of meta-processes around managing electronic transactions and the documents associated with them.
_________
_________
ATM, POS and payment cards:
____
ATM:
A cash machine, also known as an automated teller machine or automatic teller machine is an electronic telecommunications device that enables the customers of a financial institution to perform financial transactions, particularly cash withdrawal, without the need for a human cashier, clerk or bank teller. According to the ATM Industry Association (ATMIA), there are now close to 3 million cash machines installed worldwide. There are about 201,861 ATMs in India, according to RBI data. On most modern cash machines, the customer is identified by inserting a plastic ATM card with a magnetic stripe or a plastic smart card with a chip that contains a unique card number and some security information such as an expiration date or CVV (card verification value). Authentication is provided by the customer entering a personal identification number (PIN). Using a cash machine, customers can access their bank deposit or credit accounts in order to make a variety of transactions such as cash withdrawals, check balances, or credit mobile phones. If the currency being withdrawn from the cash machine is different from that in which the bank account is denominated the money will be converted at an official exchange rate. Thus, cash machines often provide the best possible exchange rates for foreign travellers, and are widely used for this purpose.
__
Hardware:
A cash machine is typically made up of the following devices:
- CPU (to control the user interface and transaction devices)
- Magnetic or chip card reader (to identify the customer): A card reader is a data input device that reads data from a card-shaped storage medium. Modern card readers are electronic devices that can read plastic cards embedded with either a barcode, magnetic strip, computer chip or another storage medium.
- PIN pad EEP4 (similar in layout to a touch tone or calculator keypad), manufactured as part of a secure enclosure
- Secure cryptoprocessor, generally within a secure enclosure
- Display (used by the customer for performing the transaction)
- Function key buttons (usually close to the display) or a touchscreen (used to select the various aspects of the transaction)
- Record printer (to provide the customer with a record of the transaction)
- Vault (to store the parts of the machinery requiring restricted access)
- Housing (for aesthetics and to attach signage to)
- Sensors and indicators
_
Software:
Today, the vast majority of cash machines worldwide use a Microsoft Windows operating system, primarily Windows XP Professional or Windows XP Embedded. A small number of deployments may still be running older versions of the Windows OS, such as Windows NT, Windows CE, or Windows 2000.
_
An ATM is simply a data terminal with two input and four output devices. Like any other data terminal, the ATM has to connect to, and communicate through, a host processor. The host processor is analogous to an Internet service provider (ISP) in that it is the gateway through which all the various ATM networks become available to the cardholder (the person wanting the cash). Most host processors can support either leased-line or dial-up machines. Leased-line machines connect directly to the host processor through a four-wire, point-to-point, dedicated telephone line. Dial-up ATMs connect to the host processor through a normal phone line using a modem and a toll-free number, or through an Internet service provider using a local access number dialled by modem. Nowadays wireless is the standard in ATM connectivity. We are seeing more and more that wireless is being used for all types of ATM locations; including hotels, c-stores, and retail. Many of the problems that prevented independent ATM deployers (IADs) from adopting wireless technology have now been fully addressed. ATMs predate the Internet, and have used all forms of private networks, including dialup, X.25, frame relay and other private IP networks. They could also include private wireless or encrypted communication over public mobile networks. ATMs have adopted the hardware architecture of a personal computer, such as USB connections for peripherals, Ethernet and IP communications, and use personal computer operating systems. Needless to say all ATMs connect to some server. This is called the Host Server. These Host Servers may be of your own bank or another bank. The ATM is connected to a collection of massive interbank networks. The two largest interbank networks are Cirrus and Pulse, although there are many others. An ATM can only provide access to bank accounts that are enrolled in the interbank networks it has access to; these are usually listed on the side of the machine. These interbank networks use phone lines, internet access and central computers to distribute information among one another and facilitate financial transactions. When a cardholder wants to do an ATM transaction, he or she provides the necessary information by means of the card reader and keypad. The ATM forwards this information to the host processor, which routes the transaction request to the cardholder’s bank or the institution that issued the card. If the cardholder is requesting cash, the host processor causes an electronic funds transfer to take place from the customer’s bank account to the host processor’s account. Once the funds are transferred to the host processor’s bank account, the processor sends an approval code to the ATM authorizing the machine to dispense the cash.
_
Card fraud at ATM:
In an attempt to prevent criminals from shoulder surfing the customer’s personal identification number (PIN), some banks draw privacy areas on the floor. For a low-tech form of fraud, the easiest is to simply steal a customer’s card along with its PIN. A later variant of this approach is to trap the card inside of the cash machine’s card reader with a device often referred to as a Lebanese loop. When the customer gets frustrated by not getting the card back and walks away from the machine, the criminal is able to remove the card and withdraw cash from the customer’s account, using the card and its PIN. This type of fraud has spread globally. Although somewhat replaced in terms of volume by skimming incidents, a re-emergence of card trapping has been noticed in regions such as Europe, where EMV chip and PIN cards have increased in circulation. Another simple form of fraud involves attempting to get the customer’s bank to issue a new card and its PIN and stealing them from their mail. By contrast, a newer high-tech method of operating, sometimes called card skimming or card cloning, involves the installation of a magnetic card reader over the real cash machine’s card slot and the use of a wireless surveillance camera or a modified digital camera or a false PIN keypad to observe the user’s PIN. Card data is then cloned into a duplicate card and the criminal attempts a standard cash withdrawal. The availability of low-cost commodity wireless cameras, keypads, card readers, and card writers has made it a relatively simple form of fraud, with comparatively low risk to the fraudsters.
____
Micro-ATM:
_
A micro ATM is nothing but a modified card swipe/point of sale machine through which a customer/agent can remotely connect to a bank’s core banking system. Micro ATMs are portable terminals that can verify bank customer identity. In order to reach people in rural remote areas, banks assign a banking correspondent who will sign up customers in far flung areas, verify their identity, and deposit or disburse cash. The banking correspondent carries a micro ATM, which is similar to the small machine you use in retail stores to swipe your debit or credit cards to purchase goods. Micro ATMs come with cellular data connectivity to send data for verification and disbursement to the bank, where the details are verified on the server side. These handheld machines accept debit cards or smart cards to initiate the process, and some models have fingerprint sensors to verify the identity of the customer. Once the identity is confirmed and the transaction approved by the bank servers, the banking correspondent hands over the cash to the customer. In India, this machine comes with a fingerprint scanner attached to it, through which Aadhaar verification can be done (vide infra). They are used to disburse cash in remote locations where bank branches cannot reach.
_
Advantages of micro-ATM:
- Bankers say that the cost of deployment of a micro ATM is much lesser than that of an ordinary ATM.
- ATMs need at least 80-100 transactions a day to be viable due to their high cost. A micro ATM costs less than Rupees 20,000 to maintain.
- It is portable
- Micro ATMs have connectivity through GSM; hence it can travel from village to village
Disadvantages of micro-ATM:
- A micro ATM cannot provide ‘anytime’ money.
- If the bank correspondent is unavailable, the account holder will not be able to undertake any financial transaction.
______
POS:
POS (point of sale) or Swipe Machine as it is popularly known is a technological instrument provided to a Merchant Establishment to carry out the sale of goods and services to customers in a cashless environment. All the customer has to do is swipe his/her Debit, Credit or Prepaid Card. POS machine is also known as Electronic Data Capture (EDC) machine used to facilitate debit/credit card payments. An EDC machine is a payment terminal provided by the bank on which the merchant can swipe or dip cards to receive payments. To make a payment, payment terminals, touch screens, and a variety of other hardware and software options are available. A point-of-sale (POS) terminal is a computerized replacement for a cash register. Much more complex than the cash registers of even just a few years ago, the POS system can include the ability to record and track customer orders, process credit and debit cards, connect to other systems in a network, and manage inventory. Generally, a POS terminal has as its core a personal computer, which is provided with application-specific programs and I/O devices for the particular environment in which it will serve. Increasingly, POS terminals are also Web-enabled, which makes remote training and operation possible, as well as inventory tracking across geographically-dispersed locations. The point of sale is often referred to as the point of service because it is not just a point of sale but also a point of return or customer order. Additionally, current POS terminal software may include additional features to cater for different functionality, such as inventory management, CRM, financials, or warehousing.
_
Types of POS:
_
Mobile Point of Sale Apps:
Many mobile payment apps available on the market present a simple and sleek way to accept payments. By simply downloading an app, anyone can turn their phone or tablet into a cash register. To turn these mobile payment apps into fully fledged “mobile point-of-sale solutions” for small and medium retailers, the peripheral devices of traditional point-of-sale systems need to be added to the feature set. With the latest mobile technologies, these peripheral can be effectively emulated virtually, thereby turning tablet-based mobile payment solutions into comprehensive mobile point-of-sale and mobile marketing solutions. For example, a merchant can scan a barcodes (to sum up individual items or redeem voucher codes) directly through a tablet or smartphone-based camera, replace receipt printers with SMS and email receipts, process item returns, incorporate customer loyalty programs and import their products to store inventory levels. This new, backpack-sized revolution puts the power of point-of-sale into the hands of every business owner. These tablet and smartphone-based point-of-sale systems deliver technology once reserved for large and established retailers, and make it available to businesses of all shapes and sizes.
_
JavaPOS:
JavaPOS (short for Java for Point of Sale Devices), is a standard for interfacing point of sale (POS) software, written in Java, with the specialized hardware peripherals typically used to create a point-of-sale system. The advantages are reduced POS terminal costs, platform independence, and reduced administrative costs. JavaPOS was based on a Windows POS device driver standard known as OPOS. JavaPOS and OPOS have since been folded into a common UnifiedPOS standard.
_
Cloud-Based Point of Sale:
Cloud-based point of sale (POS) systems provide numerous advantages over more traditional hardwired POS systems, one of which is a significant reduction in costs, especially to small business owners. Cloud-based point of sale software is the latest trend in POS software and is increasing in popularity every day. The system itself can be directly accessed from the Web and is usually compatible with most point of sale hardware, including printers, cash register drawers, etc. Also, cloud-based point of sale systems offer convenience and cost significantly less since vendors can easily access their customer data from virtually anywhere there’s a WiFi connection. Some of the key benefits of a cloud-based point of sale system are immediate centralization of information (very important for chain retailers), less expensive startup costs, and the ability to access key data from virtually anywhere an Internet connection exists.
_____
Shopkeepers prefer POS over e-wallets in India:
Shopkeepers have stopped using e-wallet because e-wallet does not allow him to transfer more than Rs 25,000 from his e-wallet to his bank account. Rest of the money he had amassed will remain in his e-wallet. With POS, the money goes directly to their bank account. They can pay vendors through their bank account using online payments or through cheques.
______
Payment cards:
A payment card is a device that enables its owner (the cardholder) to make a payment by electronic funds transfer. The most common types of payment cards are credit cards and debit cards. Payment cards are usually embossed plastic cards, 85.60 × 53.98 mm in size, which comply with the ISO/IEC 7810 ID-1 standard. They usually also have an embossed card number conforming with the ISO/IEC 7812 numbering standard. Most commonly, a payment card is electronically linked to an account or accounts belonging to the cardholder. These accounts may be deposit accounts or loan or credit accounts, and the card is a means of authenticating the cardholder. However, stored-value cards are cards that store money on the card itself. A card-based transaction typically travels from a transaction acquiring device, such as a point-of-sale (POS) terminal or an automated teller machine (ATM), through a series of networks, to a card issuing system for authorization against the card holder’s account. The transaction data contains information derived from the card (e.g., the account number), the terminal (e.g., the merchant number), the transaction (e.g., the amount), together with other data which may be generated dynamically or added by intervening systems. The card issuing system will either authorize or decline the transaction and generate a response message which must be delivered back to the terminal within a predefined time period. A number of International Organization for Standardization standards, ISO/IEC 7810, ISO/IEC 7811, ISO/IEC 7812, ISO/IEC 7813, ISO 8583, and ISO/IEC 4909 define the physical properties of payment cards, including size, flexibility, location of the magnetic stripe, magnetic characteristics, chip characteristics and data formats. They also provide the standards for financial cards, including the allocation of card number ranges to different card issuing institutions.
___
Visa and MasterCard operate under what is called a four-party system.
The four entities are:
- The Cardholder: The individual in possession of a payment card.
- The Issuer: The bank or organisation that issues the card to the cardholder.
- The Acquirer: The bank which receives payment from the issuer on behalf of the merchant.
- The Merchant: The entity with goods and services to sell that receives payment instructions and details from the cardholder – to be settled by their acquirer (via the scheme network) with the issuer.
___
‘Card present’ payment transactions need PIN while ‘card not present’ payment transactions need CVV. ‘Card present’ payment transaction is done at ATM or POS while ‘card not present’ payment transaction is done at web payment system and depositing money in third party digital wallet.
___
Credit Card:
Credit card numbers are not randomly assigned, each digit in the number sequence has a meaning.
_
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services, based on the cardholder’s promise to the card issuer to pay them for the amounts so paid plus other agreed charges. The card issuer (usually a bank) creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. A credit card is different from a charge card, where it requires the balance to be repaid in full each month. In contrast, credit cards allow the consumers a continuing balance of debt, subject to interest being charged. A credit card differs from a charge card also in that a credit card typically involves a third-party entity that pays the seller and is reimbursed by the buyer, whereas a charge card simply defers payment by the buyer until a later date. A credit card also differs from a cash card, which can be used like currency by the owner of the card. The main benefit to the cardholder is convenience. Compared to debit cards and checks, a credit card allows small short-term loans to be quickly made to a cardholder who need not calculate a balance remaining before every transaction, provided the total charges do not exceed the maximum credit line for the card. When a cardholder swipes his or her credit card at a payment terminal, a process is set in place to confirm that the cardholder is authorized to use the card and that the cardholder has sufficient funds to make a purchase. The details of the credit card are encrypted at the point-of-sale terminal, and are sent to a gateway provider for routing to the credit card issuer. When the card issuer receives the encrypted request, it verifies that the account has sufficient funds. If sufficient funds are available, the credit card company will provide a credit card authorization key to the business operating the terminal.
_
Payment using credit card is one of most common mode of electronic payment. Credit card is small plastic card with a unique number attached with an account. It has also a magnetic strip embedded in it which is used to read credit card via card readers. When a customer purchases a product via credit card, credit card issuer bank pays on behalf of the customer and customer has a certain time period after which he/she can pay the credit card bill. It is usually credit card monthly payment cycle.
_
Credit card benefits:
- Purchase Protection: With these policies, qualifying purchases can be covered against damage or theft. In fact, some cards have specific policies to cover mobile phone purchases.
- Extended Warranty: Extended product warranty programs are commonly available from many card issuers that cover qualifying purchases for an additional extra year when the manufacturer’s warranty is 36 months or less.
- Price Protection: Some credit cards offer policies that provide for a refund if you find a lower price after making a purchase.
- Return Guarantee: If a store will not accept your return within 90 days, some credit cards offer a return guarantee policy.
_____
Debit Card:
Debit card, like credit card is a small plastic card with a unique number mapped with the bank account number. It is required to have a bank account before getting a debit card from the bank. The major difference between debit card and credit card is that in case of payment through debit card, amount gets deducted from card’s bank account immediately and there should be sufficient balance in bank account for the transaction to get completed. Whereas in case of credit card there is no such compulsion. Unlike credit and charge cards, payments using a debit card are immediately transferred from the cardholder’s designated bank account, instead of them paying the money back at a later date. Debit cards usually also allow for instant withdrawal of cash, acting as the ATM card for withdrawing cash. Merchants may also offer cashback facilities to customers, where a customer can withdraw cash along with their purchase. Debit cards free customer to carry cash, cheques and even merchants accepts debit card more readily. Having restriction on amount being in bank account also helps customer to keep a check on his/her spending. Some cards may bear a stored value with which a payment is made, while most relay a message to the cardholder’s bank to withdraw funds from a payer’s designated bank account. In some cases, the primary account number is assigned exclusively for use on the Internet and there is no physical card. In many countries, the use of debit cards has become so widespread that their volume has overtaken or entirely replaced cheques and, in some instances, cash transactions. The development of debit cards, unlike credit cards and charge cards, has generally been country specific resulting in a number of different systems around the world, which were often incompatible. Since the mid-2000s, a number of initiatives have allowed debit cards issued in one country to be used in other countries and allowed their use for internet and phone purchases.
_
_
There are currently three ways that debit card transactions are processed: EFT-POS (also known as online debit or PIN debit), offline debit (also known as signature debit) and the Electronic Purse Card System. One physical card can include the functions of all three types, so that it can be used in a number of different circumstances.
_
- Online debit card system:
Online debit cards require electronic authorization of every transaction and the debits are reflected in the user’s account immediately. The transaction may be additionally secured with the personal identification number (PIN) authentication system; some online cards require such authentication for every transaction, essentially becoming enhanced automatic teller machine (ATM) cards. Overall, the online debit card is generally viewed as superior to the offline debit card because of its more secure authentication system and live status, which alleviates problems with processing lag on transactions that may only issue online debit cards. Some on-line debit systems are using the normal authentication processes of Internet banking to provide real-time on-line debit transactions.
- Offline debit card system:
Offline debit cards have the logos of major credit cards (for example, Visa or MasterCard) and are used at the point of sale like a credit card (with payer’s signature). This type of debit card may be subject to a daily limit, and/or a maximum limit equal to the current/checking account balance from which it draws funds. Transactions conducted with offline debit cards require 2–3 days to be reflected on users’ account balances.
- Electronic purse card system:
Smart-card-based electronic purse systems (in which value is stored on the card chip, not in an externally recorded account, so that machines accepting the card need no network connectivity) are in use throughout Europe since the mid-1990s, most notably in Germany (Geldkarte), Austria (Quick Wertkarte), the Netherlands (Chipknip), Belgium (Proton), Switzerland (CASH) and France (Moneo, which is usually carried by a debit card). In Austria and Germany, almost all current bank cards now include electronic purses, whereas the electronic purse has been recently phased out in the Netherlands.
____
Debit card cashback:
Debit card cashback is a service offered to retail customers whereby an amount is added to the total purchase price of a transaction paid by debit card and the customer receives that amount in cash along with the purchase. For example, a customer purchasing $18.99 worth of goods at a supermarket might ask for twenty dollars cashback. They would pay a total of $38.99 ($18.99 + $20.00) with their debit card and receive $20 in cash along with their goods. This benefits the store as it reduces the amount of cash banking the store has to do. Many customers find it a useful way to obtain cash as it avoids them having to use a cash machine, which may incur additional fees.
____
Charge card:
With charge cards, the cardholder is required to pay the full balance shown on the statement, which is usually issued monthly, by the payment due date. It is a form of short-term loan to cover the cardholder’s purchases, from the date of the purchase and the payment due date, which may typically be up to 55 days. Interest is usually not charged on charge cards and there is usually no limit on the total amount that may be charged. If payment is not made in full, this may result in a late payment fee, the possible restriction of future transactions, and perhaps the cancellation of the card.
_
Pre-paid cards:
Pre-paid cards are pre-loaded from your bank account, safe to use, limited amount of transaction and can be recharged like mobile recharge. A “prepaid credit card” is not a true credit card, since no credit is offered by the card issuer: the cardholder spends money which has been “stored” via a prior deposit by the cardholder or someone else, such as a parent or employer. However, it carries a credit-card brand (such as Discover, Visa, MasterCard, American Express, or JCB) and can be used in similar ways just as though it were a credit card. Unlike debit cards, prepaid credit cards generally do not require a PIN. An exception is prepaid credit cards with an EMV chip. These cards do require a PIN if the payment is processed via Chip and PIN technology. Prepaid debit cards, also called reloadable debit cards, appeal to a variety of users. The primary market for prepaid cards has traditionally been unbanked people, that is, people who do not use banks or credit unions for their financial transactions, possibly because of poor credit ratings. The advantages of prepaid debit cards include being safer than carrying cash, worldwide functionality due to Visa and MasterCard merchant acceptance, not having to worry about paying a credit card bill or going into debt, the opportunity for anyone over the age of 18 to apply and be accepted without regard to credit quality and the option to directly deposit paychecks and government benefits onto the card for free.
_
Stored-value card:
With a stored-value card, a monetary value is stored on the card, and not in an externally recorded account. This differs from prepaid cards where money is on deposit with the issuer similar to a debit card. One major difference between stored value cards and prepaid debit cards is that prepaid debit cards are usually issued in the name of individual account holders, while stored-value cards are usually anonymous. The term stored-value card means that the funds and/or data are physically stored on the card. With prepaid cards the data is maintained on computers controlled by the card issuer. The value stored on the card can be accessed using a magnetic stripe embedded in the card, on which the card number is encoded; using radio-frequency identification (RFID); or by entering a code number, printed on the card, into a telephone or other numeric keypad.
_
Fleet card:
A fleet card is used as a payment card, most commonly for gasoline, diesel and other fuels at gas stations. Fleet cards can also be used to pay for vehicle maintenance and expenses, at the discretion of the fleet owner or manager. The use of a fleet card reduces the need to carry cash, thus increasing the security for fleet drivers. The elimination of cash also helps to prevent fraudulent transactions at the fleet owner’s or manager’s expense. Fleet cards provide convenient and comprehensive reporting, enabling fleet owners/managers to receive real time reports and set purchase controls with their cards, helping to keep them informed of all business related expenses.
_
ATM card:
An ATM card is any payment card issued by a financial institution that enables a customer to access an automated teller machine (ATM) in order to perform transactions such as deposits, cash withdrawals, obtaining account information, etc. Most payment cards, such as debit and credit cards can also function as ATM cards, although ATM-only cards are also available. Charge and proprietary cards cannot be used as ATM cards. The use of a credit card to withdraw cash at an ATM is treated differently to a POS transaction, usually attracting interest charges from the date of the cash withdrawal. Interbank networks allow the use of ATM cards at ATMs of private operators and financial institutions other than those of the institution that issued the cards. ATM cards can also be used on improvised ATMs such as “mini ATMs”, merchants’ card terminals that deliver ATM features without any cash drawer. These terminals can also be used as cashless scrip ATMs by cashing the receipts they issue at the merchant’s point of sale.
______
Card security code:
card security code (CSC; also called card verification data [CVD], card verification number, card verification value [CVV], card verification value code, card verification code [CVC], verification code [V-code or V code], card code verification, or signature panel code (SPC)) is a term for a security feature for “card not present” payment card transactions instituted to reduce the incidence of credit card fraud. It is the three-digit number printed in the signature space on the back of most credit/debit cards, such as Visa, Mastercard, and Discover cards. The CSC/CVV is in addition to the bank card number which is embossed or printed on the card. The CSC is used as a security feature, in situations where a PIN cannot be used. The PIN is not printed or embedded on the card but is manually entered by the cardholder during a point-of-sale (card present) transactions. Contactless card and chip cards may electronically generate their own code, such as iCVV or Dynamic CVV. French digital payment security company Oberthur Technologies has introduced a dynamic CVV (card verification value) in place of the usual static CVV. The CVV is the familiar three-digit security code on the back of the card. The dynamic CVV, which uses a random number generator to update the CVV, attempts to reduce card fraud by changing the CVV every hour or even more frequently. Since “card-not-present” transactions make up 65% of all card fraud, this can be a useful security addition since a compromised CVV now only has a limited lifespan. Virtual terminals and payment gateways do not store the CVV code, therefore employees and customer service representatives with access to these web-based payment interfaces who otherwise have access to complete card numbers, expiration dates, and other information still lack the CVV code.
_____
Magnetic vs. chip card:
Magnetic card:
A magnetic stripe card is a type of card capable of storing data by modifying the magnetism of tiny iron-based magnetic particles on a band of magnetic material on the card. The magnetic stripe, sometimes called swipe card or magstripe, is read by swiping past a magnetic reading head. Magnetic stripe cards are commonly used in credit/debit cards, identity cards, and transportation tickets. They may also contain an RFID tag, a transponder device and/or a microchip mostly used for business premises access control or electronic payment.
_
In most magnetic stripe cards, the magnetic stripe is contained in a plastic-like film. The magnetic stripe is located 0.223 inches (5.66 mm) from the edge of the card, and is 0.375 inches (9.52 mm) wide. The magnetic stripe contains three tracks, each 0.110 inches (2.79 mm) wide. Tracks one and three are typically recorded at 210 bits per inch (8.27 bits per mm), while track two typically has a recording density of 75 bits per inch (2.95 bits per mm). Each track can either contain 7-bit alphanumeric characters, or 5-bit numeric characters. Track 1 standards were created by the airlines industry (IATA). Track 2 standards were created by the banking industry (ABA). Track 3 standards were created by the Thrift-Savings industry. Magstripes following these specifications can typically be read by most point-of-sale hardware, which are simply general-purpose computers that can be programmed to perform specific tasks. Magnetic stripe cloning can be detected by the implementation of magnetic card reader heads and firmware that can read a signature of magnetic noise permanently embedded in all magnetic stripes during the card production process. This signature can be used in conjunction with common two factor authentication schemes utilized in ATM, debit/retail point-of-sale and prepaid card applications.
_
Magnetic Stripe card is an “insecure” card compared with a chip card with secure and encryption protocols to access/read/update information stored on that card. Chip Cards have an embedded chip in the plastic in 2 variants, Contact or Contactless (chip+antenna) chip cards. Contact Chip Cards require to be “inserted” in a chip card reader and now it is a regular option today for issuer banks globally because most of the POS global population have been upgraded to have this reader. Contactless Chip Cards can be read “from far away” without inserting card, in fact it can be read “tapping” a POS terminal with a contactless chip card reader or can be read from a “max” distance depending on the kind of chip an ISO standard supported by that card. This is where mobile payments technology is finding its own space in the Payments Industry.
_
Chip card:
_
Chip-enabled cards are bank cards that are embedded with a micro-computer chip in addition to magnetic strip. Chip cards are also known as EMV cards. EMV stands for Europay, MasterCard, and Visa, the three companies that originally created the standard. The standard is now managed by EMVCo, a consortium with control split equally among Visa, MasterCard, JCB, American Express, China UnionPay, and Discover. EMV is a technical standard for smart payment cards and for payment terminals and automated teller machines that can accept them. EMV cards are smart cards (also called chip cards or IC cards) that store their data on integrated circuits in addition to magnetic stripes (for backward compatibility). These include cards that must be physically inserted (or “dipped”) into a reader and contactless cards that can be read over a short distance using radio-frequency identification (RFID) technology. Payment cards that comply with the EMV standard are often called Chip and PIN or Chip and Signature cards, depending on the authentication methods employed by the card issuer. There are standards based on ISO/IEC 7816 for contact cards, and standards based on ISO/IEC 14443 for contactless cards (MasterCard Contactless, PayWave, ExpressPay).
_
The magnetic strip only has one-way communication, meaning that the terminal can only read the information. EMV has two-way communication, so the terminal can actually write back to the chip with transaction information (which is why the transaction takes longer). The first thing is the existence of the chip itself makes the card extremely hard to counterfeit. With traditional magnetic stripe cards, it’s pretty simple for criminals to skim your card and use the data to make their own at home—the equipment required only costs about $100. But manufacturing a card with a working EMV chip is a much harder feat. This is partly due to the second layer of protection: how the chip actually works. The chip works like a very tiny computer. Unlike a magnetic strip, which holds a static amount of data about the card and account, the chip is “smart” enough to produce a unique code each time it’s used. It works like this: when you go to use your chip credit card at a store, you’ll dip the card into the bottom of a point-of-sale unit, kind of like what you do at an ATM. When that happens, the chip starts a “dialogue” with the POS unit. At the end of that dialogue, the card creates an application cryptogram: a dynamic number. Each time a card is inserted into a reader and the correct PIN is entered, the chip uses electricity from the terminal to generate a dynamic authorization code. Each transaction will produce a unique string of numbers that is sent to the financial institution to verify that the card being used is the same one that was issued for that account (and, in some cases, to verify that enough funds are available for the transaction). Since it’s different for each transaction, it makes it basically impossible to skim the data on the card. After that, either a pin code or a signature is required to add an extra layer of identification, which is up to the card issuer. There are two major benefits to moving to chip card-based credit card payment systems: improved security (with associated fraud reduction), and the possibility for finer control of “offline” credit-card transaction approvals. One of the original goals of EMV was to provide for multiple applications on a card: for a credit and debit card application or an e-purse.
_
EMV chip card transactions improve security against fraud compared to magnetic stripe card transactions that rely on the holder’s signature and visual inspection of the card to check for features such as hologram. The use of a PIN and cryptographic algorithms such as Triple DES, RSA and SHA provide authentication of the card to the processing terminal and the card issuer’s host system. The processing time is comparable to online transactions, in which communications delay accounts for the majority of the time, while cryptographic operations at the terminal take comparatively little time. The supposed increased protection from fraud has allowed banks and credit card issuers to push through a “liability shift”, such that merchants are now liable (as of 1 January 2005 in the EU region and 1 October 2015 in the US) for any fraud that results from transactions on systems that are not EMV-capable. RBI has given a mandate that all magnetic stripe-based cards should be removed out of circulation and be replaced by chip-based cards by end of September 30, 2017 in India. Although not the only possible method, the majority of implementations of EMV cards and terminals confirm the identity of the cardholder by requiring the entry of a personal identification number (PIN) rather than signing a paper receipt. Whether or not PIN authentication takes place depends upon the capabilities of the terminal and programming of the card.
_
Chip and PIN versus chip and signature:
Chip and PIN is one of the two verification methods that EMV enabled cards can employ. Rather than physically signing a receipt for identification purposes, the user just enters a personal identification number (PIN), typically of 4 – 6 digits in length. This number must correspond to the information stored on the chip. Chip and PIN technology makes it much harder for fraudsters to replicate the card, so if someone steals a card, they can’t make fraudulent purchases unless they know the four-digit PIN. Chip and Signature, on the other hand, differentiates itself from Chip and PIN by verifying a consumers identity with a signature. As of 2015, chip and signature cards are more common in the USA, Mexico, the Philippines and some European countries (such as Germany and Austria), whereas Chip and PIN cards are more common in other European countries (e.g., the UK, Ireland, France, Finland and the Netherlands) as well as in India,Canada, Australia and New Zealand.
_
Can you still use your chip card at merchants that don’t have a chip-enabled terminal yet?
Yes. In addition to the embedded chip that provides an added layer of security at chip-enabled terminals, your card will also continue to have the traditional magnetic strip, enabling you to use it at merchants who do not yet have a chip-enabled terminal.
_
Disadvantages of chip cards:
The plastic card in which the chip is embedded is fairly flexible. The larger the chip, the higher the probability that normal use could damage it. Cards are often carried in wallets or pockets, a harsh environment for a chip. However, for large banking systems, failure-management costs can be more than offset by fraud reduction. If the account holder’s computer hosts malware, the smart card security model may be broken. Malware can override the communication (both input via keyboard and output via application screen) between the user and the application. Man-in-the-browser malware (e.g., the Trojan Silentbanker) could modify a transaction, unnoticed by the user. Smart cards have also been the targets of security attacks. These attacks range from physical invasion of the card’s electronics, to non-invasive attacks that exploit weaknesses in the card’s software or hardware. The usual goal is to expose private encryption keys and then read and manipulate secure data such as funds. Once an attacker develops a non-invasive attack for a particular smart card model, he is typically able to perform the attack on other cards of that model in seconds, often using equipment that can be disguised as a normal smart card reader.
_
Smart card:
A smart card is a plastic card that contains an embedded computer chip–either a memory or microprocessor type–that stores and transacts data. This data is usually associated with either value, information, or both and is stored and processed within the card’s chip. The card data is transacted via a reader that is part of a computing system. Systems that are enhanced with smart cards are in use today throughout several key applications, including healthcare, banking, entertainment, and transportation. All applications can benefit from the added features and security that smart cards provide. Smart cards in banking applications are known as chip cards.
_
Contactless smart cards:
Contactless smart cards have antenna connected to the main chip. Contactless smart card communicates with and is powered by the reader through RF induction technology (at data rates of 106–848 kbit/s). These cards require only proximity to an antenna to communicate. Like smart cards with contacts, contactless cards do not have an internal power source. Instead, they use an inductor to capture some of the incident radio-frequency interrogation signal, rectify it, and use it to power the card’s electronics. Contactless transactions allow a cardholder to simply tap his or her card against a terminal when prompted. As opposed to other wireless transactions that run on earlier implementations of RFID (radio frequency identification) technology, EMV transactions rely on NFC (near field communication), a newer subset that allows for greater security by insisting on a “handshake,” or active permission, from both the terminal and the initiating device (i.e. a card or even a smartphone).
_
Hybrids:
Hybrid cards implement contactless and contact interfaces on a single card with dedicated modules/storage and processing. Dual-interface cards implement contactless and contact interfaces on a single card with some shared storage and processing. An example is Porto’s multi-application transport card, called Andante, which uses a chip with both contact and contactless (ISO/IEC 14443 Type B) interfaces.
_
USB smart card interface:
The CCID (Chip Card Interface Device) is a USB protocol that allows a smartcard to be connected to a Computer, using a standard USB interface. This allows the smartcard to be used as a security token for authentication and data encryption such as Bitlocker. CCID devices typically look like a standard USB dongle and may contain a SIM card inside the USB dongle.
_______
_______
Internet Banking:
Internet Banking refers to the banking services provided by the banks over the internet. Some of these services include paying of bills, funds transfer, viewing account statement, etc. Net banking does not involve any sort of physical card. It is used by customers who have accounts enabled with Internet banking. Instead of entering card details on the purchaser’s site, in this system the payment gateway allows one to specify which bank they wish to pay from. Then the user is redirected to the bank’s website, where one can authenticate oneself and then approve the payment. Typically there will also be some form of two-factor authentication. It is typically seen as being safer than using credit cards, with the result that nearly all merchant accounts in India offer it as an option. A very similar system, known as iDEAL, is popular in the Netherlands. Online banking account is easy to open and operate. The online services offered might differ from bank to bank, and from country to country. To know about the various services, always go through the welcome kit that you get at the time of opening the account. You also get the password to access your online account, which you are supposed to keep with great care for security reasons. Banks also deliver their latest products and services over the internet. Internet banking is performed through a computer system or similar devices that can connect to the banking site via the internet. Nowadays, you can also use internet banking on your mobile phones using a Wi-Fi or 3G connection through bank apps. With the ease of availability of cyber cafes in the cities, it has become quite popular. Banking is now no more limited in going and visiting the bank in person for various purposes like depositing and withdrawing money, requesting for account statement, stop a payment, etc. You can do all these tasks and many more using the online services offered by the banks. You can also keep a track of your account transactions and balance all the time. Now getting passbooks updated to know the total account balance is a matter of past.
_
Benefits of Internet Banking:
- Safe and Effective
- Low Processing Charges
- Highly Dependable
- Rapid Settlement
Disadvantages of Internet Banking:
- Highly Technical – One of the major drawbacks of Internet banking is that this is a highly technical method of funds transfer which is not easy to operate for everyone. An individual with little knowledge of computer or the Internet might not be able to operate an Internet banking account easily.
- The Risk involved with Online Payments –it is quite possible that your information might get passed on to a hacker if you’re using an unsecured browser or using public Wi-Fi network.
____
Electronic fund transfer:
An electronic funds transfer (EFT) is a transaction that takes place over a computerized network, either among accounts at the same bank or to different accounts at separate financial institutions. Electronic Funds Transfer (EFT) is a system of transferring money from one bank account directly to another without any paper money changing hands. One of the most widely-used EFT programs is Direct Deposit, in which payroll is deposited straight into an employee’s bank account, although EFT refers to any transfer of funds initiated through an electronic terminal, including credit/debit card, ATM, net banking, Fedwire and point-of-sale (POS) transactions. It is used for both credit transfers, such as payroll payments, and for debit transfers, such as mortgage payments. Some financial institutions and merchants issue cards with cash value stored electronically on the card itself. Examples include prepaid phone cards, mass transit passes, general purpose reloadable cards, and some gift cards. These “stored-value” cards, as well as transactions using them, may not be called EFT although they transfer funds electronically.
_
There are three main electronic methods of transferring money in the US: ACH transfers, wire transfers, and electronic transfers via third-party systems.
_
- ACH Transfers:
The most popular method of transferring money would be ACH. ACH stands for Automated Clearing House, which is an electronic network used by financial institutions to process transactions in batches. ACH is a computer-based clearing and settlement facility established to process the exchange of electronic transactions between participating depository institution. The ACH system comprises direct deposit, direct debit and electronic checks (e-checks). The typical ACH transfer takes a couple days to process and to clear the receiving financial institution. This is because it requires setup and confirmation by the receiving party. Examples of ACH transfers include payroll direct deposit, automatic loan payment withdrawals, online bill pay, distribution of Social Security benefits, and person-to-person payments. Because most ACH transfers are automated, they are rather inexpensive for credit unions & members. ACH payments can be setup as reoccurring or one-time transactions.
_
ACH vs. Plastic
ACH payments offer several advantages over credit and debit card payments.
First, ACH processing accounts are less expensive to establish, operate and maintain. ACH transactions demand lower rates than PayPal and plastic.
Second, ACH transactions are the best option for recurring payments and subscriptions.
Finally, offering customers the option to pay directly from their bank accounts serves a larger percentage of the market.
_
- Wire Transfers:
Wire transfer, bank transfer or credit transfer is a method of electronic funds transfer from one person or entity to another. A wire transfer can be made from one bank account to another bank account or through a transfer of cash at a cash office. When a wire transfer is made from one bank account to another, both account holders are verified. Additionally, the amount of money in each account is verified, so there are no charge backs associated with wire transfers. In general, a wire transfer is fast and secure. Since it is handled individually by the banks, and does not go through a clearing-house first, a wire transfer can take place almost in real time. Unlike the batch-processing nature of ACH transfers, wire transfers are designed for individual transactions. The biggest benefit of wire transfers is speed or availability of funds. You can send money to a person located across the country or halfway around the world typically within the same day. Wire transfers involve more interaction between the institution that sends and the institution that receives the money. Due to the fund availability and speed of the transaction, wire transfer fees are typically more expensive than ACH transfers. Incoming wire fees may be charged by the receiving institution as well. Different wire transfer systems and operators provide a variety of options relative to the immediacy and finality of settlement and the cost, value, and volume of transactions. Central bank wire transfer systems, such as the Federal Reserve’s FedWire system in the United States are more likely to be real time gross settlement (RTGS) systems. RTGS systems provide the quickest availability of funds because they provide immediate “real-time” and final “irrevocable” settlement by posting the gross (complete) entry against electronic accounts of the wire transfer system operator. Other systems such as CHIPS (Clearing House Interbank Payments System) provide net settlement on a periodic basis. Various modes of EFT in India include NEFT (National Electronic Funds Transfer), RTGS and IMPS (immediate payment system).
_
- Electronic Transfers via third party:
Other portals to send money electronically include e-commerce entities like PayPal & Dwolla. These companies allow users to send and receive money, possibly without fees associated with ACH and wire transfers. However, consumers may not use them because of the time and effort to set up accounts. PayPal, the most common system, doesn’t impose a fee when a customer sends money to another PayPal user through a linked banking system.
_
In summary all forms of EFT’s are acceptable. Depending on price and fund availability, the cheapest option to send money would be ACH transfer, especially if it is a reoccurring payment. Wire transfers would be better if the transaction is urgent, and PayPal services would be wise if you and the recipient have user accounts.
_
There are a few advantages of an electronic funds transfer (EFT), including less “float” time, meaning the time it takes for a paper check to clear various banks. It is less labour intensive on the banking side, and it ensures that consumers receive funds sooner. EFT also renders mailing payments obsolete. A disadvantage of electronic funds transfer (EFT) is that the process cannot be reversed if a sender should enter an incorrect account number. Other disadvantages associated with EFT include the potential for hacking of personal banking details and periodic technical difficulties.
_____
_____
Mobile digital transaction:
Mobile payment:
Mobile payment (also referred to as mobile money transfer) generally refers to payment services operated under financial regulation and performed from or via a mobile device. Instead of paying with cash, cheque, or credit cards, a consumer can use a mobile phone to pay for a wide range of services and goods. Although the concept of using non-coin-based currency systems has a long history, it is only recently that the technology to support such systems has become widely available. Essentially, mobile money payment system allows users make payments with their mobile phones. It is a savings and transfer system that turns mobile phones into a savings account platform, allowing the owner save money in it and from which withdrawals or transfers could be made. Under the payment system, customers could do their normal basic financial transactions on a daily basis by making payments for goods and services or by engaging in person-to-person transfer directly on their mobile phones. For instance, the system also allows for payment to be made through a mobile phone after purchases have been made at a grocery store. The shop owner in turn, receives instant payment electronically. Through the system, users can also pay utility bills, school fees, hotel bookings, and house rents, among other transactions, using a mobile phone device. One important thing about mobile money is the fact that it thrives on agency network, thereby taking traditional banking and its cumbersome processes in the cities to the streets in sub-urban areas where accredited mobile money agents also operate.
_
Types of mobile payments:
There are various types of mobile options. Commerce payment options are where customers open an internet browser, add items to the cart, order, receive their goods and services and are provided with a receipt. With payments, customers use contactless/mobile technologies, where payment information is stored on their device and they enter a PIN to complete a transaction. Finally, mobile wallets are looking to replace your current wallet by storing all your payment information. There are other types of options available within these types of mobile payments. For example, with mobile apps, payments will occur on a consumer’s device in order to purchase goods from a specific retailer, such as the Starbucks mobile app, and data is stored on the device. Mobile POS takes places on a merchant’s device, but data is not stored. Online payment services occur on a consumer’s device, such as PayPal, for purchasing goods. Mobile P2P transfers, such as Venmo, also occur on a consumer’s device for bank transfers. Don’t think that mobile payments will be limited to your smartphone or tablet. Bluetooth Low Energy (BLE) takes place on either the consumer or merchant’s device where data is stored in a mobile payment account. Examples include PayPal’s beacon and iBeacon. Finally, Near Field Communication (NFC) occurs on a consumer’s device; data is stored on the mobile device and is used to purchase goods. Examples include Apple Pay, Android Pay and Samsung Pay. In most cases, startups would begin with a text message service, then mobile apps and finally contactless payment systems. Merchants are using BLE and NFC that connect mobile devices with either beacons or NFC tags. With BLE, the transmission is continuous and can be used in large areas so that customers can receive notifications and coupons. NFC must be activated by the customer and is better suited for one-on-one interactions.
__
There are many models for mobile payments:
- Mobile wallets
- Card-based payments
- Carrier billing (Premium SMS or direct carrier billing)
- Contactless payments NFC (Near Field Communication)
- Direct transfers between payer and payee bank accounts in near real-time (bank-led model, intra/inter-bank transfers/payments that are both bank and mobile operator agnostic)
Additionally there is a new emerging model from Haiti: direct carrier/bank co-operation. Financial institutions and credit card companies as well as Internet companies such as Google and a number of mobile communication companies, such as mobile network operators and major telecommunications infrastructure such as w-HA from Orange and handset multinationals such as Ericsson and BlackBerry have implemented mobile payment solutions.
______
Mobile wallet (e-wallet, digital wallet):
As the name suggests, the mobile wallet represents a payment tool that permits you to transfer money and receive payments securely from your mobile phone. Because it can be used from remote locations, it encrypts the data and features memory and password protection, there’s no doubt that the mobile wallet is considerably safer than carrying a real wallet around. While there’s still a lot of work to be done, the technology is very promising and experts even state that the mobile wallet will be able to keep IDs, documents and transit passes in the near future. The biggest benefit of the mobile wallet is that the charges used for processing a payment are significantly lower compared to traditional transaction fees. Furthermore, the digital payment method helps reduce the complexity of redeeming loyalty points at POS stations. Lastly, they permit you to unlock a prepaid credit card for payments made at a particular location automatically.
_
“Wallet“ in the conventional sense of the term, refers to a purse or folding case for safely holding money or personal information such as identity card. Digital or Electronic Wallet (e-wallet) refers to an electronic, internet based payment system which stores financial value as well as personal identity related information. Such electronic payment systems enable a customer to pay online for the goods and services, including transferring funds to others, by using an integrated hardware and software system. Hardware can be a mobile or computer. Communication between the buyer and the seller may happen over the internet or blue tooth or on mobile network. Thus, e-wallet is nothing but an online money account which does not require the use of a physical card for undertaking transactions/remittances. Unlike savings bank accounts, they, at present, do not offer any interest for keeping money in it, but rewards the holders through cash-backs for making purchases through it. Unlike credit cards, e-wallets are pre-loaded money. Hence, it resembles more to a debit card.
_
In India, e-wallet comes under the legally recognized term – “Pre-paid Payment Instruments”. Pre-paid Payment Instruments (PPIs) are defined in the RBI Guidelines issued under the Payment and Settlements Systems Act, 2005 as payment instruments that facilitate purchase of goods and services, including funds transfer, against the value stored on such instruments. The value stored on such instruments represents the value paid for by the holders by cash, by debit to a bank account, or by credit card. The pre-paid instruments can be issued as smart cards, magnetic stripe cards, internet accounts, internet wallets, mobile accounts, mobile wallets, paper vouchers and any such instrument which can be used to access the pre-paid amount. Unlike other pre-paid payment instruments, e-wallet is only an internet based online account, sans the existence of a physical card. Mobile wallet is an e-wallet where the mobile phone gets doubled up as an electronic wallet.
_
Digital (mobile) wallet is issued by banks, third parties, telecom service providers, handset providers, payment networks and internet giants as seen in the figure below:
_
Mobile phone is your bank by incorporating digital wallet:
Phrases like e-wallet, digital wallet and mobile money have entered popular lexicon in the wake of demonetisation of high currency notes in India. It is being proclaimed that ‘mobile phone is your bank’. Various banks are advertising the launch of e-wallets and related mobile apps. However, if you carefully examine these offerings, it would emerge that most of them are trying to partly replace or complement physical systems. For instance, e-wallet being offered by any bank is essentially a digital bank account through which one could pay bills to service providers and make banking and financial transactions. One can do so through an Internet-enabled smartphone, a laptop or a desktop computer. All such transactions are subject to loaded costs fixed by the respective bank or service provider, in addition to hidden costs like broadband charges. And if one has more than one bank account or is holding multiple cards (debit, credit and cash cards), then one has to maintain that many digital accounts. In this sense, e-wallet products of banks are actually digital services bouquets – designed to replace paper cheques and cash payments – and not a replacement of the leather wallet you are so used to carry in your pockets.
_
An ideal digital wallet should have everything we have in a typical leather wallet – credit and debit cards, coupons, receipts of payments, cash, besides personalised items like pictures of your loved ones. And of course, such a wallet should enable its owner to make a transaction anytime with ease, comfort and confidence using a card of choice and preferred mode of payment (credit or debit). Actually, the first patent covering the concept of a ‘digital wallet’ filed in the US in 1994 – and issued in 1996 – had covered all this. This was much before smartphones had appeared. Subsequently, over two dozen related technologies were patented. The inventor who patented the concept was Sam Pitroda, who had invented the digital diary in the 1970s. Just as digital diaries replaced paper diaries (and eventually became Personal Digital Assistant), Pitroda envisaged a digital wallet to replace the leather wallet – with a back-end platform of a service provider, a bank and a telecom carrier. Such a wallet was to work both ‘over-the-air’, meaning the Internet, and over NFC or ‘near field communication’ technologies. In a book on his invention released in 2010, Pitroda had argued that true mobile money services could be delivered only by aggregating services of various banks and merchants across a common service provider-based delivery network and infrastructure.
____
Types of e-wallets permitted in India:
As per the Reserve Bank of India, there are three kinds of e-wallets in India: closed, semi-closed and open.
- Closed e-wallets:
These are wallets issued by an entity for facilitating the purchase of goods and services from it. These instruments do not permit cash withdrawal or redemption. As these instruments do not facilitate payments and settlement for third party services, issue and operation of such wallets are not classified as payment systems. Hence, RBI approval is not required for issuing them. E.g. Cab services, e-commerce and mobile companies create e-wallets for making payments towards purchase of products from them /for usage of their services. They provide cash backs for payments made through this channel. This is one way of ensuring loyalty of their customers.
- Semi-Closed e-wallets:
These are wallets which can be used for purchase of goods and services, including financial services at a group of clearly identified merchant locations/ establishments which have a specific contract with the issuer to accept them. These wallets do not permit cash withdrawal or redemption by the holder. E.g. AirTel Money, which is used for making payments for a range of services like money transfer from Airtel Money to another bank account or any other Airtel Money Wallet or paying select utility bills.
- Open e-wallets:
These are wallets which can be used for purchase of goods and services, including financial services like funds transfer at any card accepting merchant locations [point of sale (POS) terminals] and also permit cash withdrawal at ATMs / Banking Correspondents (BCs). E.g. M-Pesa is an open wallet used in Kenya.
___
Operational Mechanism of digital wallet:
Under mobile or electronic wallet, the individual pre-loads cash in the e-wallet and use it to make payments or transfers. Loading of money is done either electronically using a computer / mobile by debiting from a credit card or bank account or physically by handing over cash at a local merchant (point of sale [POS]) or at the ATM counters. An internet connection and a mobile /computer are required. With the technology in place, mobile based operations through e-wallets have become a mode for financial inclusion. There are charges for use of mobile / e-wallet, which include registration fees and cash loading charges (above a limit) towards payment companies / service providers. These charges are at times higher than those for internet banking. However, the main advantage with the e-wallet is that while shopping online, the customer stands to benefit from the concessions/ offers from the payment companies in the form of cash-backs etc.
_
A digital wallet has both a software and information component. The software provides security and encryption for the personal information and for the actual transaction. Typically, digital wallets are stored on the client side and are easily self-maintained and fully compatible with most e-commerce Web sites. A server-side digital wallet, also known as a thin wallet, is one that an organization creates for and about you and maintains on its servers. Server-side digital wallets are gaining popularity among major retailers due to the security, efficiency, and added utility it provides to the end-user, which increases their satisfaction of their overall purchase. The information component is basically a database of user-input information. This information consists of your shipping address, billing address, payment methods (including credit card numbers, expiry dates, and security numbers), and other information.
_
The key point to take from digital wallets is that they’re composed of both digital wallet devices and digital wallet systems. There are dedicated digital wallet devices such as the biometric wallet by Dunhill, where it’s a physical device holding someone’s cash and cards along with a Bluetooth mobile connection. Presently there are further explorations for smartphones with NFC digital wallet capabilities, such as the Samsung Galaxy series and the Google Nexus smartphones utilizing Google’s Android operating system and the Apple Inc. iPhone 6 and iPhone 6 Plus utilizing Apple Pay. Digital wallet systems enable the widespread use of digital wallet transactions among various retail vendors in the form of mobile payments systems and digital wallet applications. The M-PESA mobile payments system and microfinancing service has widespread use in Kenya and Tanzania, while the MasterCard PayPass application has been adopted by a number of vendors in the U.S. and worldwide.
____
Potential applications of digital wallet:
_____
Benefits of mobile wallets:
Use of debit cards requires access to designated point of sales and ATM counters. However, in case of e-wallets, money moves along with the holder and he can access it from an instrument held in his hand – his mobile or computer, giving a lot of flexibility for the account holder. Further e-wallets avoid the dangers associated with card thefts. For those who stay far away from the brick and mortar ATM / bank branches, as in the case of rural areas, money is still accessible to them at the click of a button. In case of any requirement for physical cash, they just need to go to the nearby banking correspondent or a local merchant who can double up like an ATM machine. Thus, e-wallet comes handy for those who do not have a bank account, net banking or credit card, especially those who may otherwise be in-eligible for receiving them. At present, services are not generally designed to handle big payments. The use of e-wallets substantially reduces the cost of doing banking transactions. Through e-wallets small and micro payments covering a large number of people can be cost effectively carried out. Effecting such transactions through the normal/traditional route would be burdensome for the banks, requiring more people to be employed at their counters. Using plastic (i.e., Debit/Credit card) costs much more than mobile wallet today, owing to monopoly and other costs of transaction. Mobile wallets are free today and provide additional incentive for traders to sell at lower prices (1–2 % saved). The use of e-wallet has been very successful in Kenya through M-Pesa transactions, where millions of people are estimated to be using this service to transfer small amounts of money to other people and merchants via their mobiles. In Kenya, this has been facilitated by the support of large number of agents and business correspondents. Use of e-wallets particularly facilitates e-commerce as customers are not required to fill out order forms at each site when they purchase an item as the information has already been stored and is automatically updated and entered in the order fields across merchant sites. Use of e-wallets helps in moving away from a cash based economy. In the process, all the transactions get accounted in the economy, which has the effect of reducing the size of the parallel economy.
_____
Impediments to mobile wallet use:
- The major impediment to more mainstream use of digital wallets is that there is no one application accepted everywhere. Of course, smartphone users can easily download several different digital wallet apps in order to have one that works with every merchant that accepts one, but that is confusing and awkward and defeats the purpose of a virtual wallet.
- Mobile access concerns:
Another impediment to more universal digital wallet adoption is that high-quality mobile coverage is far from comprehensive. Even Verizon’s 4G network only provides coverage to about 75 percent of the country. Customers shopping in areas with poor service will be out of luck at checkout time if they are relying on a digital wallet.
- Not many People understand or use Digital Wallets:
Analytics firm ComScore surveyed more than one million consumers about their knowledge of digital wallets. While a majority had heard of PayPal, barely half had heard of any other apps like Level Up, Square, V.Me, or Google Wallet. A strikingly small 12 percent had ever used any of the applications at all. Of those who had used the technology, PayPal was the runaway favorite, while second-place Google Wallet had been used by only 8 percent of the survey subjects.
- A study found that the number one concern preventing more digital wallet usage was fear of being hacked. A whopping 93 percent said that digital wallets would be safer if they had to be unlocked with a passcode, even though that feature is available on every digital wallet application currently on the market. The study revealed a high level of uncertainty about how the applications worked and how secure they were.
_
India faces two issues vis-à-vis mobile transactions with/without wallet:
- A prepaid cell phone is one that allows users to pay in advance for their service without the commitment and penalties of a long term contract. When the customer purchases a prepaid cell phone, he/she sets up an account that is directly connected to that specific phone. The customer is able to add money to the account via online payments, over the phone, or cash. The disadvantage is that they are deactivated when customer’s account runs dry. So you cannot perform digital transaction till you activate phone.
- Mobile services are turned off repeatedly in India due to some agitation, unrest, terrorism etc.
_
Risks involved with a Digital Wallet:
Data transmission across mobile networks is the least secure method, and transactions using a digital wallet will be subject to the risks inherent in any mobile transaction. There is also the risk of having your phone lost or stolen, jeopardizing your personal and financial information. Perhaps one of the biggest risks with a digital wallet is the personal liability in the event of fraud. Most consumers who use debit or credit cards to pay for purchases have a level of protection from their bank or credit card company. Most do not hold cardholders liable for fraudulent purchases on their credit cards. This fraud insurance does not currently exist for consumers using digital wallets.
_
Digital Wallets may be safer than Plastic:
There is a physical level of protection inherent in digital wallets that is lacking in credit and debit cards. This is because digital wallets are locked up with a pin code and smart phones can be locked with a pin code as well, providing a level of security that is lacking when someone steals a person’s credit cards or online identities. In addition, all of a consumer’s credit card and banking details are heavily encrypted by digital wallet applications. Credit card fraud costs banks and credit companies over $8 billion a year. If fraud goes down as consumers adopt digital wallets, banks may get behind the technology and promote it as a safe alternative, which would lead to wider acceptance of the technology. There are more than 135 billion credit and debit card transactions globally each year. Digital wallet applications hope to take a bite from that market and grab a significant share of those transactions. As more consumers understand and demand the convenience, more merchants will upgrade their technology to accept digital payments, which may ultimately — and ironically — provide more security and protection for consumers.
___
QR code payments:
QR Codes can be of two main categories:
- The QR Code is presented on the mobile device of the person paying and scanned by a POS or another mobile device of the payee
- The QR Code is presented by the payee, in a static or one time generated fashion and it’s scanned by the person executing the payment
Mobile self-checkout allows for one to scan a QR code or barcode of a product inside a brick-and-mortar establishment in order to purchase the product on the spot. This theoretically eliminates reduces the incidence of long checkout lines, even at self-checkout kiosks.
___
What are Contactless Payments and how do they work?
To understand how contactless payments work, let’s take a hypothetical example. You have an iPhone, which allows you to take advantage of Apple Pay. You input your credit card information onto your phone, which stores it for later use. Later on, you’re shopping at a store that has mobile payment readers at the register. Rather than reach for your wallet, you take out your phone and hold it a few centimeters away from the point-of-sale (POS) terminal. This device then automatically reads the payment information stored on the smart chip embedded in your card and then processes the transaction. Each chip connects to an antenna, and POS terminals emit a high frequency radio wave that facilitates communication between the reader and the phone. When the mobile device is in range, a wireless communication protocol links the terminal and the phone, which exchange information and conduct a secure transaction. All of this occurs in fractions of a second.
_
NFC:
Near-field communication (NFC) is a set of communication protocols that enable two electronic devices, one of which is usually a portable device such as a smartphone, to establish communication by bringing them within 4 cm (1.6 in) of each other. Simply put, it’s a method of wireless data transfer that detects and then enables technology in close proximity to communicate without the need for an internet connection. It’s easy, fast and works automatically. The tech involved is deceptively simple. Evolved from radio frequency identification (RFID) tech, an NFC chip operates as one part of a wireless link. Once it’s activated by another chip, small amounts of data between the two devices can be transferred when held a few centimeters from each other. No pairing code is necessary to link up and because it uses chips that run on very low amounts of power (or passively, using even less), it’s much more power-efficient than other wireless communication types. At its core, NFC works to identify us by our enabled cards and devices (and by extension, our bank accounts and other personal info.) NFC devices are used in contactless payment systems, similar to those used in credit cards and electronic ticket smartcards and allow mobile payment to replace/supplement these systems. A more recent and admittedly more enticing use case for NFC is with your smartphone, which can digitize your entire wallet. Virtually every mobile OS maker has their own apps that offer unique NFC functionality. Android users have the widest variety to choose from. First off, US users can nab Google Wallet, which accesses your funds for contactless payments. Samsung Pay, which operates similarly is for Samsung phone users in US and Korea. The market potential for NFC payment technology is enormous, as merchants have actually been inadvertently rallying behind this type of contactless payment tech. As more U.S. merchants adopt the EMV security standard as of October 1, 2015, they must order new EMV-compliant terminals from major providers such as Verifone and Ingenico. More often than not, these devices accept NFC payments through mobile wallets. In short, EMV will help make NFC technology universal because NFC offers a clear preferred mobile acceptance technology. And this transition is well underway. Verifone said in its Q3 2015 earnings call that NFC terminal penetration had likely reached 100% among top-tier merchants. Most transactions do not require authentication, but some require authentication using PIN, before transaction is completed. The payment could be deducted from a pre-paid account or charged to a mobile or bank account directly. Mobile payment method via NFC faces significant challenges for wide and fast adoption, due to lack of supporting infrastructure, complex ecosystem of stakeholders, and standards.
_
Host card emulation (HCE) is the software architecture that provides exact virtual representation of various electronic identity (access, transit and banking) cards using only software. Prior to the HCE architecture, NFC transactions were mainly carried out using secure elements. HCE enables mobile applications running on supported operating systems to offer payment card and access card solutions independently of third parties while leveraging cryptographic processes traditionally used by hardware-based secure elements without the need for a physical secure element. This technology enables the merchants to offer payment cards solutions more easily through mobile closed-loop contactless payment solutions, offers real-time distribution of payment cards and, more tactically, allows for an easy deployment scenario that does not require changes to the software inside payment terminals.
_
Bluetooth Payment Technology:
Bluetooth is a bit of a wild card in the payments industry. Mobile payments technology focuses quite a bit on NFC, and with good reason. But Bluetooth could be the true transformer in this area. All the major mobile platform developers, such as Apple, Google, Microsoft, and BlackBerry have supported Bluetooth for the last several years, but they shifted focus to NFC in the payments world as they released their mobile wallets (Apple Pay, Android Pay, etc.). Bluetooth, however, could change the game. Mobile payments such as Apple Pay have been slow to catch on in certain areas, but Bluetooth likely would not have such problems, especially because it has some inherent advantages. For starters, Bluetooth has a much longer range than NFC, as it can reach up to 50 meters compared to NFC’s need to have the two devices centimeters away from each other. This longer range could reduce friction during the checkout process even more than NFC technology already does. On top of this, Bluetooth creates a truly hands-free experience because shoppers would not even need to take out their phones to tap them to a reader. Furthermore, Bluetooth payment processing is almost always faster than NFC, even if it’s by fractions of a second. And finally, NFC is limited to one-to-one interaction, as in one mobile device and one payments reader. But Bluetooth can facilitate multiple transactions at once from a single payments terminal, which would further speed up the checkout process.
_
_
RFID Payment:
Using RFID wristbands as the digital wallet solution, one can gain a complete control as well as the transparency with real-time data reporting and actionable insight. It keeps digital record of everything while minimizing cash handling and speed up your transactions.
__
Cloud-based mobile payments:
Google, PayPal, GlobalPay and GoPago use a cloud-based approach to in-store mobile payment. The cloud based approach places the mobile payment provider in the middle of the transaction, which involves two separate steps. First, a cloud-linked payment method is selected and payment is authorized via NFC or an alternative method. During this step, the payment provider automatically covers the cost of the purchase with issuer linked funds. Second, in a separate transaction, the payment provider charges the purchaser’s selected, cloud-linked account in a card-not-present environment to recoup its losses on the first transaction.
_
Audio signal-based payments:
The audio channel of the mobile phone is another wireless interface that is used to make payments. Several companies have created technology to use the acoustic features of cell phones to support mobile payments and other applications that are not chip-based. The technologies Near sound data transfer (NSDT), Data Over Voice and NFC 2.0 produce audio signatures that the microphone of the cell phone can pick up to enable electronic transactions.
_
Direct carrier/bank co-operation:
In the T-Cash model, the mobile phone and the phone carrier is the front-end interface to the consumers. The consumer can purchase goods, transfer money to a peer, cash out, and cash in. A ‘mini wallet’ account can be opened as simply as entering *700# on the mobile phone, presumably by depositing money at a participating local merchant and the mobile phone number. Presumably, other transactions are similarly accomplished by entering special codes and the phone number of the other party on the consumer’s mobile phone.
_
Bank transfer systems:
Swish is the name of a system established in Sweden. It was established by major banks in 2012 and has been very successful with half the population as users in 2016. The main usage is payment between private people, but is also used by sports clubs for snack sales etc. In 2017 it will be extended to internet shopping. The smartphone app is the front-end. The phone number is used as user number when doing transactions. The connection between the phone number and the actual bank account number is registered in the internet bank. Users with a simple phone or without the app can receive money if the phone number is registered in the internet bank. Like many other mobile payment system, it has the problem that users have to do an effort to register and get the app, before being able to use the system. It managed to reach a critical mass and more reluctant people are now also using it.
___
UPI:
Unified Payments Interface (UPI) is a system that powers multiple bank accounts (of participating banks), several banking services features like fund transfer (P2P), and merchant payments in a single mobile application. UPI was launched by National Payments Corporation of India with Reserve Bank of India’s (RBI) vision of migrating towards a ‘less-cash’ and more digital society. UPI has built on the Immediate Payment Service (IMPS) platform. UPI can be used for multiple common banking tasks. UPI is a payment system that allows money transfer between any two bank accounts by using a smartphone. UPI allows a customer to pay directly from a bank account to different merchants, both online and offline, without the hassle of typing credit card details, IFSC code, or net banking/wallet passwords. UPI works only on smartphones, and needs internet connection. UPI apps can be downloaded from the android Play Store. UPI apps are based on Immediate Payment Service technology and don’t require the user to fill details like full name, bank name, branch and IFSC code. All you need is just the Virtual Payment Address (VPA) to transfer fund. It is similar to having an email address.
Requirements to use the UPI based apps:
- You need to have an active bank account.
- Your mobile number should be registered for Phone Banking, all transaction related messages and one time password.
- You need to have a smartphone with 3G or 4G network connections.
__
Mobile payment through credit/debit card:
A simple mobile web payment system includes a credit/debit card payment flow allowing a consumer to enter their card details to make purchases. In addition, if the payment vendor can automatically and securely identify customers then card details can be recalled for future purchases turning credit card payments into simple single click-to-buy giving higher conversion rates for additional purchases.
__
Mobile payment through Carrier billing:
Direct operator billing, also known as mobile content billing, WAP billing, and carrier billing, requires integration with the mobile network operator. The consumer uses the mobile billing option during checkout at an e-commerce site—such as an online gaming site—to make a payment. After two-factor authentication involving a PIN and One-Time-Password (often abbreviated as OTP), the consumer’s mobile account is charged for the purchase. It is a true alternative payment method that does not require the use of credit/debit cards or pre-registration at an online payment solution such as PayPal, thus bypassing banks and credit card companies altogether. This type of mobile payment method, which is extremely prevalent and popular in Asia, provides the following benefits:
- Mobile network operators already have a billing relationship with consumers, the payment will be added to their bill.
- Provides instantaneous payment
- Protects payment details and consumer identity
- Better conversion rates
- Reduced customer support costs for merchants
- Alternative monetization option in countries where credit card usage is low
- Security – Two-factor authentication and a risk management engine prevents fraud.
- Convenience – No pre-registration and no new mobile software is required.
______
______
In the paragraphs above, I discussed digital transaction via smartphone and internet connection using various modes: net banking via bank apps, payment transaction using credit/debit cards, digital wallet, UPI, carrier billing, NFC etc. Now I discuss mobile digital transaction without smartphones and without internet connections:
___
Digital mobile transactions without Internet:
India has around 220 million smartphone users and they get good internet connectivity in cities but there is a huge amount those people who live in rural areas and use 2G cell phones having no internet connections. There should be an option for them to perform digital transaction too. Their option includes SMS/ USSD/ IVR/ AEPS based transactional payments. USSD-based mobile banking through GSM network is a solution for those users who don’t use smartphones. In fact this service can prove to be useful for those who have smartphones too when they go out of the range of internet connectivity or their data pack gets finished but their accounts should not be linked for internet banking. Once your account is linked to net banking, USSD won’t work.
__
Premium SMS / Premium MMS:
In the predominant model for SMS payments, the consumer sends a payment request via an SMS text message to a short code and a premium charge is applied to their phone bill or their online wallet. The merchant involved is informed of the payment success and can then release the paid for goods. Since a trusted physical delivery address has typically not been given, these goods are most frequently digital with the merchant replying using a Multimedia Messaging Service to deliver the purchased music, ringtones, wallpapers etc. A Multimedia Messaging Service can also deliver barcodes which can then be scanned for confirmation of payment by a merchant. This is used as an electronic ticket for access to cinemas and events or to collect hard goods. Transactional payments by SMS have been popular in Asia and Europe and are now accompanied by other mobile payment methods, such as mobile web payments (WAP), mobile payment client (Java ME, Android…) and Direct Mobile Billing.
_
Remote Payment by SMS and Credit Card Tokenization:
Even as the volume of Premium SMS transactions have flattened, many cloud-based payment systems continue to use SMS for presentment, authorization, and authentication, while the payment itself is processed through existing payment networks such as credit and debit card networks. These solutions combine the ubiquity of the SMS channel, with the security and reliability of existing payment infrastructure. Since SMS lacks end-to-end encryption, such solutions employ higher-level security strategies known as ‘tokenization’ and ‘target removal’ whereby payment occurs without transmitting any sensitive account details, username, password, or PIN. To date, point-of-sales mobile payment solutions have not relied on SMS-based authentication as a payment mechanism, but remote payments such as bill payments, seat upgrades on flights, and membership or subscription renewals are commonplace. In comparison to premium short code programs which often exist in isolation, relationship marketing and payment systems are often integrated with CRM, ERP, marketing-automation platforms, and reservation systems. Many of the problems inherent with premium SMS have been addressed by solution providers. Remembering keywords is not required since sessions are initiated by the enterprise to establish a transaction specific context. Reply messages are linked to the proper session and authenticated either synchronously through a very short expiry period (every reply is assumed to be to the last message sent) or by tracking session according to varying reply addresses and/or reply options.
_____
USSD:
USSD stands for Unstructured Supplementary Service Data and has been developed by National Unified USSD Platform (NUUP) in India. It is an interface between the telecom operator and your bank. Alike your regular phone calls and SMS, USSD utilizes the GSM network to transfer the information and has the ability to work with a 2G cell phone, a feature phone and a smartphone. USSD-based mobile banking will not work in CDMA network. Every code that you enter over your phones keypad that contains asterisk (*) or hash (#) characters is an MMI code. MMI stands for Man-Machine-Interface. MMI code for USSD is *99# Even though most of these MMI codes look pretty similar, they fall into different groups with completely different actions. Some are just used locally on the device, some are sent to the SIM, others are sent to the network. USSD is similar to Short Messaging Service (SMS), but, unlike SMS, USSD transactions occur during the session only. With SMS, message scan be sent to a mobile phone and stored for several days if the phone is not activated or within range. The Wireless Application Protocol (WAP) supports USSD. USSD is defined in the GSM standard documents GSM 02.90 and GSM 03.90. It is important to remember that NUUP uses IMPS platform for fund transfer, which is an immediate transfer service, so once a transaction is initiated it cannot be stopped or cancelled. This is unlike an online transaction done via a laptop or mobile where it can be cancelled after initiation.
_____
Aadhaar-enabled payment system (AEPS):
_
Aadhaar Enabled Payment System is a way to get money from the bank account in India. This system of getting money neither requires your signature nor Debit card. You don’t even need to visit a bank branch for getting money through the Aadhaar Enabled Payment System. Rather, it uses Aadhaar data for the authentication. Like UPI and USSD, this is another initiative by the NPCI. The AEPS system leverages Aadhaar online authentication and enables Aadhaar Enabled Bank Accounts (AEBA) to be operated in anytime-anywhere banking mode through Micro ATMs. This system is controlled by the National Payments Corporation of India (NPCI).
_
AEPS will allow inter-operability among different systems adopted by different banks in a safe and secured manner.
- AEPS enables bank customers to access their Aadhaar-linked bank accounts through the Aadhaar authentication.
- Customers can find out their account balance, deposit cash, withdraw money and transfer funds to other Aadhaar-linked bank accounts through the help of business correspondents of any bank.
- The only inputs required from a customer for a transaction are the Aadhaar number and fingerprint captured during the enrolment.
- AEPS will allow inter-operability among different systems adopted by different banks in a safe and secured manner.
- AEPS is aimed at empowering the marginalised and excluded segments to conduct financial transactions through micro ATMs deployed by banks in villages.
_
Benefits of Aadhaar Enabled Payment System:
- You can perform financial and non-financial transaction through the banking correspondent.
- A banking correspondent of any bank can do the specified transaction of any bank.
- There is no need of signature or debit card.
- It is fast and secure. No one can forge your fingerprint.
- Banking correspondent can reach to the distant rural place with the micro-ATM.
_
It surprising that only through the Aadhaar number you can access your bank account. But it is possible because the Aadhaar is linked to your bank account. This linking leads you to your bank account. The fingerprint is authenticated by the UIDAI. In response to a transaction, UIDAI tells to the bank about the authenticity of the user. Once, UIDAI authenticates, the bank gives green signal to the transaction. Thus, in the Aadhaar Enabled Payment System six institutions are involved.
- You, the bank customer
- Banking correspondent – The facilitator of AEPS
- The bank of BC – The bank to which banking correspondent is attached
- Your Bank – the bank with which you held the bank account
- NPCI – It does switching, clearing and settlement of transactions
- UIDAI – For finger-print authentication
_
Aadhaar payment app is set to revolutionize digital transactions in India:
Indian Government is all set to roll out Aadhaar Payment app which enable people to transact anywhere in India with single finger print scan. Currently the system is said to be deployed in small set of villages for pilot and roll out is expected to happen any time in future. All the merchants who will accept payments are required to download this app and link it with finger print scanner. Whenever a user intends to pay will have to give a finger print authorization and it will auto debit money from the bank account linked to his aadhaar. Point of sale machines are the only means to do digital transactions by using debit and credit card, but companies like Visa and master who issue them are charging money to the end user between 0.5 – 2.5% depending on transaction type. And government is not able to encourage people because of charges levied. With the launch of this app these charges will be zero and the moment of digital India will be much closer to the reality.
____
Payment Processing IVR:
Interactive voice response (IVR) is a technology that allows a computer to interact with humans through the use of voice and DTMF tones input via keypad. With the IVR technology, different business and organizations can provide a secure mechanism for processing payment using digital transaction. The main benefit of Payment processing IVR is you neither need a specific device such as Smartphone nor internet connection for processing payment. Interactive voice response (IVR) is a payment solution that allows callers to interact with an automated telephone-payment system to make ACH, Debit and Credit Card payments 24/7. IVR payment gateway can be accessed via a toll-free number or can be routed from your existing telephone system. Upon arrival at the IVR gateway, callers are presented with pre-recorded call flows and scripts, some of which are custom recorded and others pre-built for optimum usability, speed to market, and corporate-brand continuity. Capturing IVR payments is simplified via touch-tone prompts and account-data validation.
______
______
The figure below shows synopsis of digital transactions via mobile phones:
_______
_______
Digital transaction statistics:
As you can see in the figure below, major payment systems in the US in 2005 were cash, checks and credit/debit cards based on number of transactions.
_
India is becoming a digital country:
Although there are over 25 million credit cards and close to 700 million debit cards in India, most people only use the latter to withdraw cash from ATMs. And even if they have credit cards, shop owners and vendors often do not have the connectivity or power to charge them—leaving card-swiping machines to collect dust. Rural India, meanwhile, remains almost entirely run by cash. For every 1 million Indians, there are 693 Point of Sale (POS)—credit and debit card processing— machines in comparison to the 4000 machines for every 1 million people in China and Russia. Moreover, well over half of all POS systems in India are confined to major cities. That impacts both consumers and vendors. Low-value transactions in India—a pack of cigarettes and roadside meals usually cost less than $5, making credit and debit cards an inefficient and expensive payment mode. In this plastic-averse climate, digital wallet mobile apps like Paytm and Mobikwik—which allow online and offline payments using money deposited from a bank account—are more likely to become the country’s most viable alternative to cash. Paytm, which is backed by Chinese behemoth Alibaba, reported a 300 percent hike in downloads following demonetisation announcement in November 2016 and in December 2016 digital wallet transactions have outnumbered those of both credit and debit cards.
_
_
The figure below shows credit/debit card penetration in various countries in 2013:
There are more than 135 billion credit and debit card transactions globally each year.
_
Mobile payment statistics:
Mobile payment is being adopted all over the world in different ways. The worldwide mobile payment revenue in 2015 was 450 billion U.S. dollars and is expected to surpass 1 trillion U.S. dollars in 2019. The mobileQR code and barcode redemption market is estimated to cross $50 billion globally by 2017, according to Mind Commerce. The mobile money market is expected to grow to $721 billion by 2017 according to Gartner estimates. It’s no wonder that everyone from big players like PayPal, Google, ISIS to startups such as ZooZ, Clutch,Corduro and CloudZync are all rushing to grab a share of this market. In developing countries mobile payment solutions have been deployed as a means of extending financial services to the community known as the “unbanked” or “underbanked,” which is estimated to be as much as 50% of the world’s adult population, according to Financial Access’ 2009 Report “Half the World is Unbanked”. These payment networks are often used for micropayments. Digital wallet is being used more and more in Asian countries as well. One in five consumers in Asia are now using digital wallet representing twofold increase from two years ago. A recent survey by MasterCard’s mobile shopping survey shows on 8500 adults aged 18–64 across 14 markets showed, 45% users in China, 36.7% users in India and 23.3% users in Singapore are the biggest adopters of digital wallet. The survey was conducted on between October and December 2015. Also analysis showed (48.5%) consumers in these regions made purchase using smartphones. Indian consumers are leading the way with 76.4% using a smartphone to make purchase which is a drastic increase of 29.3% from previous year. This has made companies like Reliance and Amazon India to come out with its own digital wallet. Flipkart has already introduced its own digital wallet.
_
Digital transactions to reach $8 trillion by 2020:
New data from Juniper Research has found that the digital commerce market is set to increase from $4.9 trillion in 2015 to just over $8 trillion by 2020. Juniper’s latest research, Digital Commerce: Key Trends, Sectors & Forecasts 2016–2020, forecasts that the digital commerce market will see significant growth in transaction values as a result of the contributions from three major commerce segments. Juniper said that the digital commerce market will see strong contributions from three key sectors — digital banking, remote digital goods and remote physical goods.
__________
__________
Technology and security of digital transaction:
_
Information technology and internet banking:
Information in its most restricted technical sense is a message (utterance or expression) or collection of messages that consists of an ordered sequence of symbols, or it is the meaning that can be interpreted from such a message or collection of messages. Information can be recorded or transmitted. It can be recorded as signs, or conveyed as signals by waves. Information is any kind of event that affects the state of a dynamic system. The concept has numerous other meanings in different contexts. Moreover, the concept of information is closely related to notions of constraint, communication, control, data, form, instruction, knowledge, meaning, mental stimulus, pattern, perception, representation, and especially entropy. In fact, information can be defined as processed data. Communication is the activity of conveying meaningful information. Communication requires a sender, a message, and an intended recipient, although the receiver need not be present or aware of the sender’s intent to communicate at the time of communication; thus communication can occur across vast distances in time and space. Communication requires that the communicating parties share an area of communicative commonality. The communication process is complete once the receiver has understood the message of the sender. Information technology (IT) is the use of computers and software to manage information. In some companies, this is referred to as Management Information Services (or MIS) or simply as Information Services (or IS). The information technology department of a large company such as bank would be responsible for storing information, protecting information, processing the information, transmitting the information as necessary, and later retrieving information as necessary. Information and communications technology or information and communication technology, usually abbreviated as ICT, is often used as an extended synonym for information technology (IT), but is usually a more general term that stresses the role of unified communications and the integration of telecommunications (telephone lines and wireless signals), computers, middleware as well as necessary software, storage- and audio-visual systems, which enable users to create, access, store, transmit, and manipulate information. In other words, ICT consists of IT as well as telecommunication, broadcast media, all types of audio and video processing and transmission and network based control and monitoring functions.
______
India does not have adequate infrastructure to facilitate digital payments:
Though the scarcity of currency (due to demonetisation) encouraged many people to shift to internet banking or use of prepaid, credit and debit cards and e-wallets, the experience was often frustrating as transactions were often inordinately slow or even failed as networks sagged when the overloaded IT infrastructure often crashed under the heavy traffic. Such mishaps have only served to worsen people’s anxieties and erode their confidence in the security of digital transactions. This is not surprising considering that India’s ranking in the cyber world is way down the ranks. In fact the global Networked Readiness Index 2016 of the World Economic Forum, which indicates a country’s success in harnessing information technology, shows India’s rank has now dropped as low as 91, which is even lower than that of Sri Lanka, Vietnam and Bhutan, as other countries have moved ahead faster on the digital front; and India’s ranking on the average internet connection speed and download speed at a very low 105 and 96. This is primarily due to the high price of spectrum which adds to delivery costs and reduces funds for telecom infrastructure. Indian Banks, which have been aggressively pushing digital transactions, have asked Indian government to nudge telecom service providers to ensure smoother connectivity to enable a more efficacious transition to a cashless economy. Senior bank officials have informed the government that patchy connectivity is currently a hindrance as they strive to onboard people to e-platforms. Efficient telephony data is a prerequisite for digital transactions such as payment using unified Payment Interface (UPI), m-wallets or mobile banking. Customer experience, particularly for first time users who are migrating from cash to digital transactions, will be significantly affected if the connectivity is weak. Data connectivity is essential for digital banking to succeed. Indian telecom companies have to ensure that data connectivity is there all the time, everywhere and that it is stable. Indian Banks do not have the required infrastructure to open so many more bank accounts after demonetisation, offer digital platforms, assist customers in using net banking, and conduct awareness campaigns. Banks have to increase capacities of their servers for rising digital transactions. Then there are other serious issues like the lack of adequate data protection and privacy laws that can jeopardise user safety. Similarly the state’s ability to protect citizens from cybercrime is also rather limited which also puts a big question mark on the security financial transactions. All this clearly shows that the country has still a long way to go before it can hope to spruce up IT infrastructure and provide adequate security and privacy to facilitate a fast shift towards digital payments and a cashless economy. Most recent numbers show that mobile connectivity is yet to be provided to 56,117 villages out of 250,000 villages. Though the government has launched the Digital India program in 2015 to boost connectivity and reduce the digital gap between the rural and urban sector it will take huge resources and strenuous efforts to finish the task. But until that happens it would be futile to think of any sudden shift to a cashless economy.
_____
Bank systems creak under weight of digital transactions in UK:
Billions must be spent to underpin services and battle online challengers. Pressure is mounting on the archaic technology systems that underpin some of the largest banks as they roll out online and mobile services to compete in the digital age. Behind the banks’ new mobile apps and faster digital payment services is, in many cases, decades-old technology. The growth of channels offering instant banking access is creating a surge in transactions that threatens to overload the core IT systems serving them. “We believe it is more pressing than ever that banks address the challenges with their back office systems,” says David Parker, UK head of retail banking at Accenture. “In general these systems are old, complex and they were created long before digitisation existed.” Many of the banks’ core systems were originally built for slower branch-based banking and overnight batch-processing of payments. Experts say some banks even run off pre-decimal systems. “In one case the core system converts customer account data in and out of pre-decimal pounds, shilling and pence,” one former banker said. Most of the large UK banks still use overnight batch-processing — working through millions of payment transactions every night that were made through the day — rather than real-time systems. But these old systems are prone to failure. RBS experienced a severe systems upgrade failure in 2012 which left many thousands of customers without access to their accounts. The bank is now spending about £1.3bn per year improving its technology platform and core IT processes. A number of other banks are making significant changes, and some have successfully overhauled entire systems, albeit at a high cost. Santander UK, for example, integrated Abbey after its takeover of the bank in 2004 on to its Parthenon core banking system. Juan Olaizola, the bank’s chief operating officer, says the key to success in digital is “balancing the investment between front and back ends”. “Though the emphasis tends to be on the apps and the customer-related experience, it is only the back-end services that provide frictionless customer experiences, as we see in success stories such as Amazon or Uber. “Banks are still far from providing this type of customer-centric services,” he says. He notes that the “massive growth” in smartphones means the bank has to respond at a “speed that we don’t control . . . a speed previously unknown to banks”. System upgrades often cost more than banks originally expected and have even scuppered some merger and acquisition deals, such as Santander’s purchase of branches from RBS. Some lenders in the UK are reducing their branch network in tandem with launching enhanced mobile and internet services. Lloyds Banking Group, for example, has announced plans to close 200 branches, amounting to 6 per cent of its network. However, a number are revamping their existing branches with digital improvements. Nationwide, for example, recently committed to invest £300m in its branches. This will involve new formats such as “Nationwide Now”, comprising digitally enabled features and branch locations in order to better connect people to its staff.
________
Security of digital transaction:
Money is inexorably linked to the issues of secure identity and trust in payment systems. Secure transactions have to prevent attempts to steal identities for criminal purposes, and placate the fears of consumers about the consequences of losing their phones. There needs to be trust in the system that strangers will honour transactions. Transactions security, precluding errors and preventing crime, requires confidence in the identity of individuals, as access to the global digital economy is built on the assurance that people are who they say they are. The transition to universal digital money, therefore, has to be accompanied by a similar transition to universal digital identity management and systems that people trust to guarantee privacy. These are hard problems, requiring considerable innovation amongst large technology and financial service companies to provide robust technical systems, and in governments, especially in emerging economies around the world where a significant portion of residents remain barely connected to their administrative and financial systems. The key challenge to be resolved lies in the ability to manage and store personal information, while guaranteeing privacy in the maintenance of records and ensuring the continuing openness of access for consumers.
_
Security is an essential part of any transaction that takes place over the internet. Customer will lose his/her faith in e-business if its security is compromised. Following are the essential requirements for safe e-payments/transactions −
- Integrity: prevention against unauthorized data modification
- Nonrepudiation: prevention against any one party from reneging on an agreement after the fact
- Authenticity: authentication of data source
- Confidentiality: protection against unauthorized data disclosure
- Privacy: provision of data control and disclosure
- Availability: prevention against data delays or removal
- Encryption – Information should be encrypted and decrypted only by authorized user.
- Auditability – Data should be recorded in such a way that it can be audited for integrity requirements.
_
Cyber security as per Cisco:
A digital economy requires a secure digital network that enables business innovation, generates insights and creates customer experiences. From retail banking to digital payments, companies that seize the digital opportunity need security everywhere—from the network to the endpoint and from the cloud to every corner of their operations—to limit the risk of sensitive data compromise. Cisco Systems, Inc. (known as Cisco) is an American multinational technology conglomerate that develops, manufactures, and sells networking hardware, telecommunications equipment, and other high-technology services and products. Cisco is the largest networking company in the world. According to Cisco study, the potential risk of loss from cyber threats can be staggering for customers—upwards of $575 billion globally. Digitalisation provides organisations with opportunities to grow and innovate but it also brings a new world of risks. At Cisco, they have nearly 200,000 networks that they protect every single day, which extrapolates to hundreds of thousands of customers in businesses, governments, universities and other organisations with tens of millions of users. Cisco blocks about 20 billion malware, spyware, virus, and other attacks per day. To secure digital economy and succeed in the digital world, industries, government and educational institutions must embed cyber security purely into the fabric of their organisation. It has to be a fundamental part of every organisation’s purpose and strategy. As per a Cisco report, there are more than 1 million unfulfilled cyber security jobs worldwide.
______
Online bank robberies:
Operation High Roller was a series of fraud in the banking system in different parts of the world that used cyber-collection agents in order to collect PC and smart-phone information to electronically raid bank accounts. It was dissected in 2012 by McAfee and Guardian Analytics. A total of roughly $78 million was siphoned out of bank accounts due to this attack. The attackers were operating from servers in Russia, Albania and China to carry out electronic fund transfers. The McAfee and Guardian Analytics report describes the technical details and the impact of a series of cyber-attacks. The old adage that “criminals go where the money is” today means that “bank robbers go online”. It should come as no surprise that large organized crime groups are targeting online banking sites. Still, the attacks drew much attention, for three reasons.
1) Highly automated: The attackers reduced manual intervention to a minimum, relying mostly on automation. The attacks were also fast and easily missed by the user.
2) Sophisticated: The banks’ protection measures, such as two-factor authentication and fraud detection, were circumvented. Users did not notice this right away because the fraudulent transactions were hidden by malware (inserting javascript code into pages).
3) Targeted: Only PCs from users with corresponding high balances were targeted (e.g. around 5000 PCs in the Netherlands).
The cyber-attacks had three phases. First, targets were identified using online reconnaissance and (spear) phishing. Victims with access to high balance accounts (hence the name “High Rollers”) were singled out. Secondly, malware (SpyEye, Zeus and Ice 9) was loaded onto the victim’s PC – tailor customised for the victim’s online banking websites. The malware was triggered when the victim started an online banking session. SpyEye, Zeus and Ice 9 are common types of malware toolkits, tailored for this attack. Later, automated fraudulent transactions were carried out in the name of the user and hidden from them behind warning and waiting messages. The malware transfers sums from savings accounts to checking accounts, then to mules abroad who take the cash and send it onwards using person-to-person money transfer (such as Western Union).
_
Online frauds:
A lot of ATMs in India use the old operating system known as Windows XP, according to research done by Kaspersky Labs. This makes them easy targets for hackers and cyber criminals. As most of these ATM machines are not updated with the latest operating system they have a high possibility of being compromised from inside or outside,” said Altaf Halde, Managing Director (South Asia), Kaspersky Lab. Recently, some leading Indian banks were hit by a malware which compromised data and accounts. Millions of customers were affected, and the country’s largest public sector bank, the State Bank of India blocked 600,000 debits cards of its customers after the incident. Other banks which reported the cyber-attack included YES Bank, HDFC Bank, ICICI Bank and Axis Bank. 3.2 million Bank accounts were compromised in India during October-November 2016. Halde said ‘point of sales’ machines like the ones used to swipe credit cards also use the old operating system, hence hackers could target these devices internally or externally. E-wallets have not been compromised yet, but they can be hit by android malware, which can infect the system and keep track of your activities. Sadly, most people in India are not aware of the latest cyber threats. It’s also important that the government keeps itself updated and a step ahead to fight cyber-crime. FireEye said India’s existing cyber security infrastructure is inadequate to deter the new generation of malware launched by hackers acting individually or backed by other governments. So what’s holding back a stronger electronic protection system in India? “The key roadblock to stronger cyber security is cost-conscious organisations that do not allocate the resources required to provide effective security and reduce risks,” said Vipul Kumra, Systems Engineering Leader for India at FireEye. This could explain the increase in online attacks post demonetisation. According to reports in the Indian media, there were 80,000 actual breaches between December 9 and 12. Security officials said there were 200,000 threats per day till November 28. This increased to 600,000 daily threats in December, most of which were neutralised. “One of the interesting implications of demonetisation which is yet to be examined is the rise of immature digital payment providers. Many of these start-ups do not place the same emphasis on security that you expect from traditional financial institutions,” said Kumra of FireEye. Online fraud globally was $10.7 billion in 2016 and $25.6 billion will be global online fraudulent transactions by 2020
_
Internet users lost about $476 on an average to cyber-attacks: study by security software firm Kaspersky Lab 2017:
With the variety and sophistication of online financial threats against consumers growing, losses from online fraud, identity theft and hacking are now running at billions a year. With many cases going unreported, the true economic cost is likely to be significantly higher. The research reveals how costly these attacks are for Internet users, and how lucrative they’ve become for cybercriminals. On average, Internet users lose $ 476 per attack and one-in-ten people surveyed said they lost more than $ 5,000. A large majority of respondents said they conduct financial operations online (81 per cent) and just under half (44 per cent) store financial data on their connected devices. As more users go online to manage their finances, more cybercriminals are looking for opportunities to cash in, making it important for users to have robust Internet security in place to protect themselves and their money. However, only 60 per cent respondents said they protect all their devices. Interestingly, almost half (45 per cent) respondents said that they assume they will be reimbursed by banks for financial cybercrime without any problem, but as the survey shows, over half (52 per cent) of people affected have not had all their stolen money returned. Cybercriminals are continually looking for new ways to exploit and defraud consumers and that’s why it’s important for Internet users to be on their guard at all times.
____
Cyber security threats:
Cyber security threats are constantly evolving. Viruses infecting personal desktops were the first generation. The second generation can be traced back to 2001, when hackers took down the Microsoft and EBay websites by targeting their domain name server with a denial of service (DoS) attack, giving rise to “botnets.” In computing, a denial-of-service attack (DoS attack) is a cyber-attack where the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. BOTs are the more intelligent versions of yesterday’s remote-access Trojan. There is a definitive architecture to bots, bot nets, and their damage. Most bots use one or more attacks to break into remote machines. Once coded, the bot is used to compromise multiple machines and make a bot network (or botnet). The botnet is used by the attacker (or sold or rented) to accomplish some sort of malicious activity. DoS attacks are very common, but bots can also steal user passwords, send spam or phishing e-mails, sniff traffic and steal identities. The third generation began in 2007, with the release of Red October, a state-sponsored cyber-espionage campaign that stole data from classified computers, mobile devices, and network equipment. Perhaps the most famous of these attacks is Stuxnet. Malware is also evolving to become more platform-focused. Now, with the advent of smart devices, malware is penetrating pervasively and focusing on all security dimensions, that is, access, data theft, and destruction.
_
Electronic payment process initiates at customers’ end and finishes at merchants’ end using banking application to authenticate and pay. The medium of payment can be anything from card to online banking. Anything loose between these ends can potentially lead to exploitation. For users’ end, things like careful two-factor authentication, strong pass words, antivirus and secure computers are the usual tips. Of course, security is an ongoing process where banks and ecommerce websites play a critical role in customer awareness. On Organization’s end, it needs to opt for multiple layer security, to get total application security. Use of a web application scanner, can scan all your apps and inform about possible vulnerabilities and malwares. For a deeper and proactive approach, manual penetration testing needs to be done. Once found, these weak points can be fixed and patched. Web applications are riddled with vulnerabilities and it’s not always a plausible solution to fix them all at once. One needs to prioritize the vulnerabilities that need foremost attention, based on their level of sensitivity, and work towards fixing them. A Web Application Firewall (WAF) can be used for blocking attacks. While a traditional WAF cannot achieve this, a managed WAF is more than capable of protecting your applications against such threats. A WAF not only protects your vulnerable apps, but also provides protection against DoS and DDoS attacks. It can differentiate between automated and human requests, and hence protect against BOTs. It is not just about technical view of the risk, but from a business point of view too, strong security facilitates advanced services and higher value transactions to be moved to the internet cost effectively. Hence security is no longer just about mitigating risks but a fundamental foundation to cost effective business transactions and digital payments.
______
Measures for digital transaction security include measures to protect client computer, communication channels and servers.
1.Client computer protection:
– Privacy — Cookie blockers; Anonymizer
– Digital certificate
– Browser protection
– Antivirus software
– Computer forensics expert
2. Communication channel protection:
a) Encryption
–Public-key encryption (asymmetric) vs. Private-key encryption (symmetric)
–Encryption standard: Data Encryption Standard (DES), Advanced Encryption Standard (AES)
b) Protocol
–Secure Sockets Layer (SSL)
–Secure HyperText Transfer Protocol (S-HTTP)
c) Digital signature
3. Server protection:
a) Access control and authentication
— Digital signature from user
–Username and password
–Access control list
b) Firewalls
International Computer Security Association’s classification:
- Packet filter firewall: checks IP address of incoming packet and rejects anything that does not match the list of trusted addresses (prone to IP spoofing)
- Application level proxy server: examines the application used for each individual IP packet (e.g., HTTP, FTP) to verify its authenticity.
- Stateful packet inspection: examines all parts of the IP packet to determine whether or not to accept or reject the requested communication.
______
Collective responsibility:
Companies, customers, and the government should collectively participate to mitigate cyber-attacks and minimise its damages.
- First, all companies that offer platforms or services enabling digital payments should increase awareness among their customers of the risks, and educate them on ways to secure themselves. They must employ behaviour analytics and pattern analysis at their fraud prevention departments to predict suspicious behaviour. They must be proactive in looking out for any fake applications or websites that masquerade their service. They must monitor discussion boards, social media platforms, and forums that discuss hacking and fraud tactics, and implement measures to thwart such tactics.
- Second, the government should check if the current policies regulating these platforms are adequate and update them regularly. People must be educated on the risks involved, strict policies must be enforced, and companies accountable for not meeting security standards must be held. Benefits that come from overlooking security precautions must be minimised, and public-private partnerships on live information sharing about cyber-attacks and fraud should be strengthened.
- Third, customers should educate themselves about the risks involved and take precautions. They must minimise vulnerability with two-factor authentication and change their password frequently. They must check the authenticity of applications by looking for the number of downloads and read reviews by other users — the higher the number of downloads and reviews, the higher the chances that the application is legitimate. Customers must also check for other application releases from that developer. For instance, they must check the Website’s authenticity by searching for the proper spelling of the Web address, check if the Website is secure by looking out for a green padlock symbol on the left side of the Web address, and keep Web browsers updated so they can recognise illegitimate sites easily.
_____
_____
Digital Authentication:
The term authentication refers to an electronic process that allows for the electronic identification of a natural or legal person. Additionally, authentication may also confirm the origin and integrity of data in electronic form, such as the issuance of a digital certificate to attest to the authenticity of a website. The overall purpose of authentication is to reduce the potential for fraud, especially in the event of an individual purposely misrepresenting their identity or through the unauthorized use of another person’s credentials. The terms digital authentication or electronic authentication (e-authentication) synonymously refer to the process where the confidence in user identities is established and presented electronically to an information system. The digital authentication process presents a technical challenge due to the necessity of authenticating individual people or entities remotely over a network. Its level of security depends on the applied type of authentication, the authentication factors used, as well as the process of authentication applied.
_
Authentication in an Electronic Banking Environment:
Financial institutions engaging in any form of Internet banking should have effective and reliable methods to authenticate customers. An effective authentication system is necessary for compliance with requirements to safeguard customer information, to prevent money laundering and terrorist financing, to reduce fraud, to inhibit identity theft, and to promote the legal enforceability of their electronic agreements and transactions. The risks of doing business with unauthorized or incorrectly identified persons in an Internet banking environment can result in financial loss and reputation damage through fraud, disclosure of customer information, corruption of data, or unenforceable agreements. There are a variety of technologies and methodologies financial institutions can use to authenticate customers. These methods include the use of customer passwords, personal identification numbers (PINs), digital certificates using a public key infrastructure (PKI), physical devices such as smart cards, one-time passwords (OTPs), USB plug-ins or other types of “tokens”, transaction profile scripts, biometric identification, and others. The level of risk protection afforded by each of these techniques varies. The selection and use of authentication technologies and methods should depend upon the results of the financial institution’s risk assessment process.
_
Existing authentication methodologies involve three basic “factors”:
- Something the user knows (e.g., password, PIN);
- Something the user has (e.g., ATM card, smart card); and
- Something the user is (e.g., biometric characteristic, such as a fingerprint).
_
- A password is an example of “something you know”. To establish a level of trust it must be something that ONLY the user knows. Passwords that often get shared or written down can be intercepted (e.g. over the network, or by key loggers) or weak passwords can be cracked. Dependent on the level of risk identified, this form of authentication on its own may no longer be sufficient. More innovative use of the “something you know” factor, such as selection of password/PIN characters from a drop-down list or image selection may help to address part of the problem, such as key logging, but still rely on the same basic principle.
- The “something you have” factor requires the user to be in possession of something. This “something” is usually referred to as a token. A token is typically, but not necessarily, a hardware device that has been issued to the user for the purposes of authentication. There are various forms of token. The important attributes are that the token can be authenticated by the system and uniquely associated with the user. The process of authenticating a token should use some form of “strong authentication” that is less easily compromised than a simple password, i.e. using some form of cryptographic process.
- The “something you are” factor refers to some form of biometric authentication, based on a measurement of some personal characteristics (which may or may not be physical). It is important here to understand the difference between the use of biometrics for authentication and identification, which may impose different requirements on the process (biometric identification can spot a known person in a crowd, whereas biometric authentication validates a claimed identity). Multiple forms of biometric authentication are available, all of which may enhance the level of confidence in the authentication process. At present the applicability of biometric authentication to the on-line community may be limited, with it being better suited to a more closed community. Not all biometric authentication methods require dedicated or expensive hardware; however all do require some initial measurement to be taken during registration.
Whilst biometrics will have a part to play in some situations, in most cases where the desire is to increase the level of trust in the authentication process over passwords, the use of a token is often the most appropriate choice. It is important to consider that “something you have” also has its own inherent weakness – it can be stolen. It is therefore on its own not more secure that “something you know”, but should be combined with “something you know” to form a “two-factor” authentication system, in which a compromise of either one of the factors on its own would not be sufficient for an attacker to gain access.
_
Ways to authenticate:
Authentication is used to verify that the information comes from a trusted source. Basically, if information is “authentic,” you know who created it and you know that it has not been altered in any way since that person created it. These two processes, encryption and authentication, work hand-in-hand to create a secure environment.
There are several ways to authenticate a person or information on a computer:
- Password:
The use of a user name and password provides the most common form of authentication. You enter your name and password when prompted by the computer. It checks the pair against a secure file to confirm. If either the name or the password does not match, then you are not allowed further access.
_
- Pass cards:
These cards can range from a simple card with a magnetic strip, similar to a credit card, to sophisticated smart cards that have an embedded computer chip.
_
- Digital signature:
Digital signature is basically a way to ensure that an electronic document is authentic. Digital signatures are unique digital keys used to authorize and check transactions and positively identify the initiator. The Digital Signature Standard (DSS) is based on a type of public-key encryption method that uses the Digital Signature Algorithm (DSA). DSS is the format for digital signatures that has been endorsed by the U.S. government. The DSA algorithm consists of a private key, known only by the originator of the document (the signer), and a public key. If anything at all is changed in the document after the digital signature is attached to it, it changes the value that the digital signature compares to, rendering the signature invalid. Digital signature can leverage (strong) authentication to achieve better security, data integrity and non-repudiation for digital transactions.
_
_
Digital Signatures as part of E-Signature Security:
People often assume that digital signatures and electronic signatures are the same; however, they are actually two different things. An e-signature is a legal concept, while a digital signature is a security technology. If an e-signed document is modified or tampered with in any way, the digital signature technology will detect it and indicate that the document has been altered. Digital signatures are therefore the foundation of any reliable electronic signature and a core requirement for a trustworthy solution. This is a unique and significant advantage over the paper world, where it is not always possible to detect whether changes have been made to a document.
_
Mobile signature:
A mobile signature is a digital signature generated either on a mobile phone or on a SIM card on a mobile phone.
According to the EU directives for electronic signatures the mobile signature can have the same level of protection as the hand written signature if all components in the signature creation chain are appropriately certified. The most successful mobile signature solutions can be found in Turkey, LIthuania, Estonia and Finland with millions of users. Technically the mobile signature is created by a security module when a request for it reaches the device (SIM card,) and after introducing the request to the user with a few explanation prompts, the device asks for a secret code that only the correct user should know. Usually this is in form of a PIN. If the access control secret was entered correctly, the device is approved with access to secret data containing for example RSA private key, which is then used to do the signature or other operations that the request wanted. The PKI system associates the public key counterpart of the secret key held at the secure device with a set of attributes contained in a structure is called digital certificate. The choice of the registration procedure details during the definition of the attributes included in this digital certificate can be used to produce different levels of identity assurance. Anything from anonymous but specific to high-standard real-word identity. By doing a signature, the secure device owner can claim that identity.
Thus, the mobile signature is a unique feature for:
- Proving your real-world identity to third parties without face-to-face communications
- Making a legally-binding commitment by sending a confirmed message to another party
- Solve security problems of the online world with identity confirmation (an anonymous but specific identity is often equally good as a high-standards identity)
_
- Digital certificate:
Authentication is the digital process of verifying that people or entities are whom or what they claim to be. Digital certificate are in effect virtual fingerprints, or retinal scans that authenticate the identity of a person in a concrete, verifiable way. A typical digital certificate is a data file or information, digitally signed and sealed by the encrypted using RSA encryption techniques, that can be verified by anyone and includes:
- The name of holder and other identification information, such as e-mail address
- A public key, which can be used to verify the digital signature of a message sender previously signed with the unique private key.
- The name of issuer, or Certificate Authority.
- The certificate’s validity period.
To create a digital certificate for an individual, the identity of the person, device, or entity that requested a certificate must be confirmed through combination of:
- Personal Presence.
- Identification document.
Digital certificates may be distributed online, which includes:
- Certificate accompanying signature.
- Directory service.
Digital signatures are mainly applied for the verification of authenticity, integrity and non-repudiation. A digital certificate is a certificate issued by a certificate authority to verify the identity of the certificate holder. It actually uses a digital signature to attach a public key with a particular individual or an entity. The decision to revoke a certificate is the responsibility of the issuing company.
_
- Tokenization:
Tokenization describes the substitution of sensitive data with non-sensitive equivalents, the tokens. Tokenization refers to the process of replacing sensitive information with a unique symbol or token generated randomly. The replacement ensures that the data cannot be transmitted to a third party via any means and cannot be stored in an unsecure format. The general concept behind a token-based authentication system is simple. Allow users to enter their username and password in order to obtain a token which allows them to fetch a specific resource – without using their username and password. Once their token has been obtained, the user can offer the token – which offers access to a specific resource for a time period – to the remote site. In other words: add one level of authentication — instead of having to authenticate with username and password for each protected resource, the user authenticates that way once (within a session of limited duration), obtains a time-limited token in return, and uses that token for further authentication during the session. Advantages are many — e.g., the user could pass the token, once they’ve obtained it, on to some other automated system which they’re willing to trust for a limited time and a limited set of resources, but would not be willing to trust with their username and password (i.e., with every resource they’re allowed to access, forevermore or at least until they change their password). Security tokens are used to prove one’s identity electronically (as in the case of a customer trying to access their bank account). The token is used in addition to or in place of a password to prove that the customer is who they claim to be. The token acts like an electronic key to access something. Some may store cryptographic keys, such as a digital signature, or biometric data, such as fingerprint details. Some may also store passwords. Some designs feature tamper resistant packaging, while others may include small keypads to allow entry of a PIN or a simple button to start a generating routine with some display capability to show a generated key number. Special designs include a USB connector, RFID functions or Bluetooth wireless interface to enable transfer of a generated key number sequence to a client system. Security remains the paramount concern for digital transactions, and MasterCard is pursuing tokenization as a way to make digital and even card-on-file transactions safer. While contactless and in-app payments are growing, payments made via a browser will continue to account for the largest share of digital payments. The most noteworthy advantage of tokenization is that it protects the cardholder at many points during a transaction and particularly, post-authorization when there’s a risk of recurring transactions. In addition, it features a cryptogram that helps the provider decide whether to allow a de-tokenization attempt and reveal card data. Perhaps this is the reason why 22 of the world’s greatest banks are pushing for the adoption of this type of payment in the US. With regard to mobile payments, this means concretely replacing the debit or credit card numbers (primary account number) against a token. This token has the same format as the underlying card (i.e. 16 digits for credit cards and the respective analog card information for debit cards) but is linked to a specific device (smartphone, tablet, wearable). It has a separate expiration date. The token service provider ensures the mapping between PAN and token, as well as the integrity of the token. A significant advantage of network tokenization consists in the fact that the payment infrastructure doesn’t require merchant and/or acquirer adjustments and all existing interfaces continue to be active. The payments occur via the same communication channels as before, the sole difference being that instead of credit card data, only token details are transmitted. Furthermore, tokenization technology increases mobile payment security. This is so because of increased data transmission security and decreased merchant responsibility. Sensitive payment data no longer require storage with the merchant and will no longer be transferred during the transaction. Instead, the exchanged data are coupled to a device, a merchant or even a transaction before expiring completely in case a data contamination has taken place. The card owner’s data are therefore significantly more secure.
_
- Biometrics:
Recently, more sophisticated forms of authentication have begun to show up on home and office computer systems. Most of these new systems use some form of biometrics for authentication. Biometrics uses biological information to verify identity. Biometric authentication methods include:
- Fingerprint scan
- Retina scan
- Face scan
- Voice identification
_
_
Fingerprint sensors:
A fingerprint sensor is an electronic device used to capture a digital image of the fingerprint pattern. The captured image is called a live scan. This live scan is digitally processed to create a biometric template (a collection of extracted features) which is stored and used for matching. Many technologies have been used including optical, capacitive, RF, thermal, piezoresistive, ultrasonic, piezoelectric, MEMS.
_
Biometrics vs. passwords/PIN:
Unfortunately, both passwords and PINs are too easily compromised, they’re complex and they’re cumbersome. A large part of the problem is that passwords and PINs depend on authenticating information that’s readily accessible to anyone—things like birth dates, hometowns and pets’ names are all part of an individual’s digital “lifeprint” that they leave on social media pages, public records and other unsecured websites. Another glaring problem with passwords is that they are static—according to a 2015 study by TeleSign, 21 percent of people use passwords that are over 10 years old. An overwhelming 73 percent of online accounts are guarded by duplicated passwords, making it that much easier for hackers to take down multiple accounts by cracking just one password. Passwords and PINs were fine when you had to remember one or two of them, but in today’s world, there are simply too many accounts that require them, and too many rules to follow to make them actually secure. The same rules that make passwords secure also make them almost impossible to remember, which is likely why the most popular passwords continue to be ‘12345678’ and ‘password.’ Biometrics rely on something you are, rather than something you know. A well-implemented biometric solution (one that relies on a complex data set, is fully encrypted, and, we would argue, is stored on a device) provides a convenient authentication solution that doesn’t sacrifice security. Biometrics are probabilistic in nature; as opposed to a password entry that is either right or wrong, the algorithms that power biometric systems calculate the probability that the fingerprint, face or voice being presented is a match with the fingerprint, face or voice that it has on record for the user. Also unlike passwords, biometrics can be affected by environmental conditions—if you’re in a crowded area, for example, you may not achieve optimum success with voice-recognition, or if you’re in a dark room, facial recognition may be affected by shadows. In 2002 a Japanese cryptographer demonstrated how fingerprint recognition devices can be fooled 4 out of 5 times using a combination of low cunning, cheap kitchen supplies and a digital camera. Taking latent fingerprints from a glass, which were enhanced with a super-glue fumes in the form of cyanoacrylate adhesive and photographed. An image tool were then used to improve the contrast and then printed onto a transparency sheet. The sheet were then used to expose a UV sensitive printed-circuit board and etched. The copper imprints were then used for a plastic finger mould and gelatine found in Gummy bears a fake finger could be made. Eleven commercially available fingerprint biometric systems took the fake finger as the real thing. Noted cryptographer Bruce Schneier said “The results are enough to scrap the systems completely, and to send the various fingerprint biometric companies packing,” I disagree. The process of making fake finger prints is far difficult than finding password through phishing, guessing etc. If you’re a fraudster, you first would need to steal the phone, unlock the device, impersonate someone’s biometrics, defeat the anti-replay technology and do so in a way that didn’t trigger any flags in the risk engines of the financial institutions. And you’d have to do all that before the consumer realizes they don’t have their phone. The adoption of biometrics has been very rewarding—those with the right technology embraced the solutions almost immediately. Fingerprint-based solutions tend to dominate the adoption, largely due to the convenience and familiarity to the end-user. With authentication systems in particular, balancing security with convenience is a tough line to walk. For knowledge-based systems, added security means more frequent password changes, tougher security questions, or additional steps in the authentication process. But myriad security questions or forgotten passwords can frustrate customers or, at worst, cause them to abandon their activity altogether. Biometrics solves the “security versus convenience” question by providing a highly secure method of authentication using unique identifiers that customers always have with them. For banks biometrics will be essential in the years ahead.
__
According to a test by the National Physical Laboratory’s Centre for Mathematics and Scientific Computing in the UK, the failure to enrol rate of the fingerprint biometric system is 1%. This means some people might not even be able to enrol in a biometric system using their fingerprints. Glitches such as this cast a doubt on whether biometrics are as reliable as their sales and marketing pitches make them out to be. To many, 1% seems like a small number and not worth worrying about. However, let’s imagine that there are 100 million people wanting to use a biometric system to safeguard their digital wallets. If the failure to enrol rate is 1%, 1 million people would not be able to even use the system – that’s pretty significant.
__
Authentication methods that depend on more than one factor are more difficult to compromise than single-factor methods. Accordingly, properly designed and implemented multifactor authentication methods are more reliable and stronger fraud deterrents. For example, the use of a logon ID/password is single-factor authentication (i.e., something the user knows); whereas, an ATM transaction requires multifactor authentication: something the user possesses (i.e., the card) combined with something the user knows (i.e., PIN). A multifactor authentication methodology may also include “out–of–band”5 controls for risk mitigation. The success of a particular authentication method depends on more than the technology. It also depends on appropriate policies, procedures, and controls. An effective authentication method should have customer acceptance, reliable performance, scalability to accommodate growth, and interoperability with existing systems and future plans.
_
Types of authentication:
The most frequent types of authentication available in use for authenticating online users differ in the level of security provided by combining factors from the one or more of the three categories of factors for authentication:
- Single-factor authentication:
As the weakest level of authentication, only a single component from one of the three categories of factors is used to authenticate an individual’s identity. The use of only one factor does not offer much protection from misuse or malicious intrusion. This type of authentication is not recommended for financial or personally relevant transactions that warrant a higher level of security.
Personal identification number:
A personal identification number (PIN, pronounced “pin”; often redundantly PIN number) is a numeric password used to authenticate a user to a system. PINs may be used with banking systems to authenticate the identity of the cardholder, but are also used in other, non-financial systems. Usually, both a private PIN and public user identifier is required to authenticate a user to the system. In these situations, typically the user is required to provide a non-confidential user identifier or token (the user ID) and a confidential PIN to gain access to the system. Upon receiving the user ID and PIN, the system looks up the PIN based upon the user ID and compares the looked-up PIN with the received PIN. The user is granted access only when the number entered matches with the number stored in the system. Hence, despite the name, a PIN does not personally identify the user. The PIN is not printed or embedded on the card but is manually entered by the cardholder during automated teller machine (ATM) and point of sale (POS) transactions (such as those that comply with EMV), and in card not present transactions, such as over the Internet or for phone banking. Card not present transaction may need CVV number rather than PIN. PINs may also be used in contexts other than ATM or POS transactions, such as door access, Internet transactions, or to log in to a restricted website. In such cases, the PIN may simply be a password, and not necessarily associated with a specific card.
Mobile phone passcodes:
A mobile phone may be PIN protected. If enabled, the PIN (also called a passcode) for GSM mobile phones can be between four and eight digits and is recorded in the SIM card. If such a PIN is entered incorrectly three times, the SIM card is blocked until a personal unblocking code (PUC or PUK), provided by the service operator is entered. If the PUC is entered incorrectly ten times, the SIM card is permanently blocked, requiring a new SIM card from the mobile carrier service.
_
- Two-Factor authentication (2FA):
Two-factor authentication (2FA) is an information security process in which two means of identification are combined to increase the probability that an entity, commonly a computer user, is the valid holder of that identity. 2FA requires the use of two reliable authentication factors:
- Something the user knows, e.g. a password or a PIN
- Something the user owns, e.g. a mobile phone, a hardware token or a smart card
In many 2FA solutions, possession of the second factor, “something that the user owns”, is demonstrated by knowledge of a one-time password (OTP). This OTP is either generated by the second factor in the possession of the user, e.g. a mobile phone, or by a trusted server that is then delivered to the second factor. This delivery can include SMS text messages. When elements representing two factors are required for authentication, the term two-factor authentication is applied — e.g. a bankcard (something the user has) and a PIN (something the user knows). Business networks may require users to provide a password (knowledge factor) and a pseudorandom number from a security token (ownership factor). Access to a very-high-security system might require a mantrap screening of height, weight, facial, and fingerprint checks (several inherence factor elements) plus a PIN and a day code (knowledge factor elements), but this is still a two-factor authentication. 2FA reduces the possibility of an authentication credential being stolen and hacked. Passwords are static codes that are prone to theft, e.g. through a phishing, keylogging, or replay attacks. By utilising OTPs, a 2FA solution can avoid many of the weaknesses associated with static password solutions. To hack an account protected by two factor authentication, the hackers must gain access to the physical feature that is being sent the information (e.g. a mobile phone). CNET states that the second way a hacker can gain access through 2FA is by gaining “access to the cookies or tokens placed on the device by the authentication mechanism. This can happen in several ways, including a phishing attack, malware, or credit card-reader skimming.”
_
One-time password:
A one-time password (OTP) is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid a number of shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two factor authentication by ensuring that the one-time password requires access to something a person has (such as a small keyring fob device with the OTP calculator built into it, or a smartcard or specific cellphone) as well as something a person knows (such as a PIN). The most important advantage that is addressed by OTPs is that, in contrast to static passwords, they are not vulnerable to replay attacks. This means that a potential intruder who manages to record an OTP that was already used to log in to a service or to conduct a transaction will not be able to abuse it, since it will no longer be valid. A second major advantage is that a user who uses the same (or similar) password for multiple systems, is not made vulnerable on all of them, if the password for one of these is gained by an attacker. A number of OTP systems also aim to ensure that a session cannot easily be intercepted or impersonated without knowledge of unpredictable data created during the previous session, thus reducing the attack surface further. OTPs have been discussed as a possible replacement for, as well as enhancer to, traditional passwords. On the downside, OTPs are difficult for human beings to memorize. Therefore, they require additional technology to work. OTP generation algorithms typically make use of pseudorandomness or randomness, making prediction of successor OTPs by an attacker difficult, and also hash functions, which can be used to derive a value but are hard to reverse and therefore difficult for an attacker to obtain the data that was used for the hash. This is necessary because otherwise it would be easy to predict future OTPs by observing previous ones. Concrete OTP algorithms vary greatly in their details.
_
Is SMS a reliable method for OTP delivery?
There is occasionally an issue with reliability of OTP delivery with SMS text message-based 2FA solutions. Mobile network operators (MNOs) cannot guarantee SMS text message delivery within an acceptable timeframe for 100 percent of all SMS messages delivered. There are times when the mobile network is overloaded, e.g. peak times at events and natural disasters, and other times when network coverage is either poor or non-existent, e.g. an IT engineer in a data centre that may be underground or protected from radio. Late delivery of an OTP contained in an SMS text message can be problematic for a time-critical login that can mean no access to critical enterprise resources.
_
Advances in mobile two-factor authentication:
Advances in research of two-factor authentication for mobile devices consider different methods in which a second factor can be implemented while not posing a hindrance to the user. With the continued use and improvements in the accuracy of mobile hardware such as GPS, microphone, and gyro/accelerometer, the ability to use them as a second factor of authentication is becoming more trustworthy. For example, by recording the ambient noise of the user’s location from a mobile device and comparing it with the recording of the ambient noise from the computer in the same room on which the user is trying to authenticate, one is able to have an effective second factor of authentication. This also reduces the amount of time and effort needed to complete the process.
_
Transaction authentication number:
A transaction authentication number (TAN) is used by some online banking services as a form of single use one-time passwords to authorize financial transactions. TANs are a second layer of security above and beyond the traditional single-password authentication. TANs provide additional security because they act as a form of two-factor authentication. Should the physical document or token containing the TANs be stolen, it will be of little use without the password; conversely, if the login data are obtained, no transactions can be performed without a valid TAN.
_
- Multi-factor authentication:
Instead of using two factors as used in 2FA, multiple authentication factors are used to enhance security of a transaction in comparison to the 2FA authentication process. Multi-factor authentication (MFA) is a method of computer access control in which a user is only granted access after successfully presenting several separate pieces of evidence to an authentication mechanism – typically at least two of the following categories: knowledge (something they know), possession (something they have), and inherence (something they are).
_
- Strong authentication:
Strong authentication is often confused with two-factor authentication or more generally multi-factor authentication. However, strong authentication is not necessarily multi-factor authentication. The European Central Bank (ECB) has defined strong authentication as “a procedure based on two or more of the three authentication factors”. The factors that are used must be mutually independent and at least one factor must be “non-reusable and non-replicable”, except in the case of an inherence factor and must also be incapable of being stolen off the Internet. In the European, as well as in the US-American understanding, strong authentication is very similar to multi-factor authentication or 2FA, but exceeding those with more rigorous requirements.
___
___
___
___
Mutual authentication:
Mutual authentication or two-way authentication refers to two parties authenticating each other at the same time, being a default mode of authentication in some protocols (IKE, SSH) and optional in others (TLS). Better institution-to-customer authentication would prevent attackers from successfully impersonating financial institutions to steal customers’ account credentials; and better customer-to-institution authentication would prevent attackers from successfully impersonating customers to financial institutions in order to perpetrate fraud. Most Mutual authentication is machine-to-machine, leaving it up to chance whether or not users will notice (or care) when the remote authentication fails (e.g. a red address bar browser padlock, or a wrong domain name). Non-technical mutual-authentication also exists to mitigate this problem, requiring the user to complete a challenge, effectively forcing them to notice, and blocking them from authenticating with a false endpoint.
_
Google Authenticator:
Google Authenticator is an application that implements two-step verification services using the Time-based One-time Password Algorithm (TOTP) and HMAC-based One-time Password Algorithm (HOTP), for authenticating users of mobile applications by Google. The service implements algorithms specified in RFC 6238 and RFC 4226. Authenticator provides a six- to eight-digit one-time password which users must provide in addition to their username and password to log in to Google services or other sites. The Authenticator can also generate codes for third-party applications, such as password managers or file hosting services. Previous versions of the software were open-sourced but subsequent releases are proprietary.
How to use Goggle Authenticator app:
Typically, a user installs the Authenticator app on a smartphone. To log in to a site or service that uses two-factor authentication, the user provides user name and password to the site and runs the Authenticator app. The app displays an additional six-digit one-time password and transmits it to the site, which asks the user what that password is. The user enters it, thus authenticating the user’s identity. For this to work, a set-up operation has to be performed ahead of time: the site provides a shared secret key to the user over a secure channel, to be stored in the Authenticator app. This secret key will be used for all future logins to the site. With this kind of two-factor authentication, mere knowledge of username and password is not sufficient to break into a user’s account. The attacker also needs knowledge of the shared secret key or physical access to the device running the Authenticator app. An alternative route of attack is a man-in-the-middle attack: if the computer used for the login process is compromised by a trojan, then username, password and one-time password can be captured by the trojan, which can then initiate its own login session to the site or monitor and modify the communication between user and site.
______
Authorization:
The process of authorization is distinct from that of authentication. Whereas authentication is the process of verifying that “you are who you say you are”, authorization is the process of verifying that “you are permitted to do what you are trying to do”. Authorization thus presupposes authentication. For example, a client showing proper identification credentials to a bank teller is asking to be authenticated that he really is the one whose identification he is showing. A client whose authentication request is approved becomes authorized to access the accounts of that account holder, but no others. However note that if a stranger tries to access someone else’s account with his own identification credentials, the stranger’s identification credentials will still be successfully authenticated because they are genuine and not counterfeit; however, the stranger will not be successfully authorized to access the account, as the stranger’s identification credentials had not been previously set to be eligible to access the account, even if valid (i.e. authentic). Similarly when someone tries to log on a computer, they are usually first requested to identify themselves with a login name and support that with a password. Afterwards, this combination is checked against an existing login-password validity record to check if the combination is authentic. If so, the user becomes authenticated (i.e. the identification he supplied in step 1 is valid, or authentic). Finally, a set of pre-defined permissions and restrictions for that particular login name is assigned to this user, which completes the final step, authorization. Even though authorization cannot occur without authentication, the former term is sometimes used to mean the combination of both.
_
______
______
Following are the drawbacks of online payment systems regarding security:
- Unauthorized transactions or stealing money.
- Hacking of personal data and use it for identity theft.
- Attacking on data and make it corrupts.
- Take advantage of the convenience and speed of the electronic system to mask illegitimate or illegal transactions – i.e., money laundering.
- Take advantage of the efficiency of the electronic system to facilitate funding of illegal.
_
Security tries to accomplish the following tasks:
- Authentication which identifies buyer and also makes sure that person is who he/she claims to be. Used methods are i.e. digital signature, finger prints, password or smartcards etc.
- Data integrity which means, that there must be a way to verify that data is not changed during the transactions.
- Confidentially must be preserved, so information concerning the tarns action are need to know basis.
- Non repudiation, which means that person who did the payments is not able afterwards deny doing so.
Among other considerations, it needs to consider the following important issues:
- Electronic Identification Strategy: It requires cryptographic security techniques to ensure transaction authentication and choose between secret key cryptography (SKC), MACing (Message Authentication Code) or public key cryptography (PKC) digital signatures.
- Level of Security: The determination of a security level will have impact on the type of electronic identification means given to clients. The choice is between logical securities in software-based authentication, or physical security if a security device is introduced into the picture.
- Client Authentication Strategy: With the PKC digital signatures, this issue is rooted in the PKI security model, and the role of certification authorities (CA). Where with SKC, the foremost options are the manual delivery of
cryptographic keys or implied security model suggests the client enrolment.
- Confidentiality Requirements: Even if the critical aspect of E-commerce security is transaction authentication, confidentiality requirements are a significant design issue. This confidentiality requirements issue is independent from the selection of a security model. Obviously, when the confidentiality mechanisms are considered, the selection of SKC or PKC does matter.
_______
_______
Technological Measures to ensure Security:
Major security measures are following:
- Encryption − It is a very effective and practical way to safeguard the data being transmitted over the network. Sender of the information encrypts the data using a secret code and specified receiver only can decrypt the data using the same or different secret code.
- Digital Signature, tokens and digital certificate [discussed vide supra].
- Security Certificates − Security certificate is unique digital id used to verify identity of an individual website or user.
_______
Cryptography:
Cryptography or cryptology is the practice and study of techniques for secure communication in the presence of third parties called adversaries. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure; theoretical advances, e.g., improvements in integer factorization algorithms, and faster computing technology require these solutions to be continually adapted.
_
Encryption:
_
Encryption is a modern form of cryptography that allows a user to hide information from others. Encryption is the process of taking all of the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. To encrypt a message, the message is passed to a method or an algorithm that transforms the message using a key (cryptographic key) into a meaningless script called cryptogram or ciphertext. The ciphertext can be sent to the intended recipient. The recipient must have a key to decrypt the ciphertext back to the original message. Computer encryption is based on the science of cryptography, which has been used as long as humans have wanted to keep information secret. Nearly every computing device we interact with on a daily basis utilizes some form of encryption technology. From smartphones (which can often have their data encrypted), to tablets, desktop, laptops, encryption is everywhere.
_
Encryption algorithms can be classified into two types, namely symmetric cryptography (private key cryptography) and asymmetric cryptography or public key cryptography. The two are similar in the sense that they both allow a user to encrypt data to hide it from others, and then decrypt it in order to access the original plaintext. They differ, however, in how they handle the steps between encryption and decryption. For example, if John and Robert both had keys to a box, with John having the public key and Robert having a matching private key, John could use his key to unlock the box and put things into it, but he wouldn’t be able to view items already in there, nor would he be able to retrieve anything. Robert, on the other hand, could open the box and view all items inside as well as removing them as he saw fit by using his matching private key. He could not, however, add things to the box without having an additional public key. In a digital sense, John can encrypt plaintext (with his public key), and send it to Robert, but only Robert (and his matching private key) could decrypt the ciphertext back into plaintext. The public key (in this scenario) is used for encrypting ciphertext, while the private key is used to decrypt it back into plaintext. Robert would only need the private key to decrypt John’s message, but he’d need access to an additional public key in order to encrypt a message and send it back to John. John on the other hand couldn’t decrypt the data with his public key, but he could use it to send Robert an encrypted message. Where Private Key – or symmetric – encryption differs from Public Key encryption is in the purpose of the keys themselves. There are still two keys needed to communicate, but each of these keys is now essentially the same. For example, John and Robert both possess keys to the aforementioned box, but in this scenario the keys do the same thing. Both of them are now able to add or remove things from the box. Speaking digitally, John can now encrypt a message as well as decrypting it with his key. Robert can do the same with his.
_
The goal of every encryption algorithm is to make it as difficult as possible to decrypt the generated ciphertext without using the key. If a really good encryption algorithm is used, there is no technique significantly better than methodically trying every possible key. For such an algorithm, the longer the key, the more difficult it is to decrypt a piece of ciphertext without possessing the key. Modern encryption technology uses more sophisticated algorithms as well as larger key sizes in order to better conceal encrypted data. The larger the key size, the more possible combinations that a brute force attack would have to run in order to successfully find decrypt the ciphertext. As key size continues to improve, the length of time it takes to crack an encryption using a brute force attack skyrockets. For example, while a 56-bit key and a 64-bit key look to be relatively close in value, the 64-bit key is actually 256 times harder to crack than the 56-bit key. Most modern encryptions use a minimum of a 128-bit key, with some using 256-bit keys or greater. 128-bit encryption primarily refers to the length of the encryption or decryption key. It is considered secure because it would take massive computation and virtually thousands of years to be cracked. For example, it would take 2128 different combinations to break the encryption key, which is out of reach for even the most powerful computers. 128-bit encryption is implemented in most network/Internet communications technologies such as in web browsers and websites.
_
Hash value:
A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value. A cryptographic hash function is a hash function which takes an input (or ‘message’) and returns a fixed-size alphanumeric string. The string is called the ‘hash value’, or ‘digital fingerprint’. Practical applications include message integrity checks, digital signatures, authentication, and various information security applications.
_
Digital signature via cryptography:
Public-key cryptography can also be used for implementing digital signature schemes. A digital signature is reminiscent of an ordinary signature; they both have the characteristic of being easy for a user to produce, but difficult for anyone else to forge. Digital signatures can also be permanently tied to the content of the message being signed; they cannot then be ‘moved’ from one document to another, for any attempt will be detectable. In digital signature schemes, there are two algorithms: one for signing, in which a secret key is used to process the message (or a hash of the message, or both), and one for verification, in which the matching public key is used with the message to check the validity of the signature. RSA and DSA are two of the most popular digital signature schemes. Digital signatures are central to the operation of public key infrastructures and many network security schemes (e.g., SSL/TLS, many VPNs, etc.).
_
Dual signature:
_
Data Encryption Standard (DES):
A well-known symmetric cryptography is DES (Data Encryption Standard) developed by IBM for the US government. Encryption standards have come a long way since DES was first adopted in 1977. In fact, a new DES technology, known as Triple DES (3DES) is quite popular, and it’s based on a modernized version of the original DES algorithm. While the original DES technology was rather limited with a key size of just 56 bits, the current 3DES key size of 168-bits make it significantly more difficult and time consuming to crack.
_
AES:
The Advanced Encryption Standard is a symmetric cipher based on the Rijandael block cipher that is currently the United States federal government standard. The AES is a popular encryption algorithm that supports 128-bit. AES was adopted worldwide as the heir apparent to the now deprecated DES standard of 1977 and although there are published examples of attacks that are faster than brute force, the powerful AES technology is still thought to be computationally infeasible in terms of cracking. In addition, AES offers solid performance on a wide variety of hardware and offers both high speed and low RAM requirements making it a top-notch choice for most applications. If you’re using a Mac, the popular encryption tool FileVault is one of many applications that uses AES.
_
RSA:
RSA was first described in 1977 by Ron Rivest, Adi Shamir and Leonard Adleman of the Massachusetts Institute of Technology. RSA is one of the first widely used asymmetric cryptosystems for data transmission. In the RSA cryptosystem the two numbers are keys, namely private and public keys. A private key must be kept secret, while a public key can be revealed to anyone. Obviously, the RSA cryptosystem is more complex and harder to manage than DES since it involves two keys. The algorithm was first described in 1977, and relies on a public key based on two large prime numbers and an auxiliary value in order to encrypt a message. Anyone can use the public key in order to encrypt a message but only someone with knowledge of the prime numbers can feasibly attempt to decode the message. RSA opened the doors to several cryptographic protocols such as digital signatures and cryptographic voting methods. It’s also the algorithm behind several open source technologies, such as PGP, which allows you to encrypt digital correspondence.
_
ECC:
Elliptic curve cryptography is among the most powerful and least understood forms of encryption used today. Proponents of the ECC approach cite the same level of security with faster operational times largely due to the same levels of security while utilizing smaller key sizes. The high performance standards are due to the overall efficiency of the elliptic curve, which makes them ideal for small embedded systems such as smart cards. The NSA is the biggest supporter of the technology, and it’s already being billed as the successor to the aforementioned RSA approach.
_
White-box cryptography:
Cryptography is increasingly deployed in applications that are executed on open devices (such as PCs, tablets or smartphones). The open nature of these systems makes the software extremely vulnerable to attacks, since the attacker has complete control over the execution platform and the software implementation itself. This means that an attacker can easily analyse the binary code of the application, and the corresponding memory pages during execution; the attacker can intercept system calls, tamper with the binary and its execution; and use any kind of attack tool such as IDA Pro, debuggers, emulators, etc. Such an attack context is denoted as the white-box attack context. The challenge that white-box cryptography aims to address is to implement a cryptographic algorithm in software in such a way that cryptographic assets remain secure even when subject to white-box attacks. Therefore, white-box cryptography (WBC) is an essential technology in any software protection strategy. This technology allows to perform cryptographic operations without revealing any portion of confidential information such as the cryptographic key. Without this, attackers could easily grab secret keys from the binary implementation, from memory, or intercept information that would lead to disclosure at execution time. WBC could be seen as a special purpose code generator that turns a given cipher into a robust representation; a representation where the operations on the secret key are combined with random data and code, in such a way that the random data cannot be distinguished from key information.
_
Quantum cryptography:
The prospect of quantum cryptography offers an even more radical possibility for dealing with concerns over security and privacy of data in digital transactions. Quantum keys are used for encryption of passwords. They are secure because any attempt to interfere with the data is detectable: if quantum data is accessed it changes, thereby hindering attempts to break security codes.
______
______
Security Protocols in Internet:
Following are the popular protocols used over the internet which ensures security of transactions made over the internet.
- Secure Socket Layer (SSL):
It is the most commonly used protocol and is widely used across the industry. It meets following security requirements
- Authentication
- Encryption
- Integrity
- Non-reputability
TLS means “Transport Layer Security”. TLS is the new name for SSL. Namely, SSL protocol got to version 3.0; TLS 1.0 is “SSL 3.1”. TLS versions currently defined include TLS 1.1 and 1.2. Each new version adds a few features and modifies some internal details. We sometimes say “SSL/TLS”.
____
“https://” is to be used for HTTP URLs with SSL, whereas “http:/” is to be used for HTTP URLs without SSL. When SSL is used to secure HTTP, it assures a Web user that he/she communicates with his/her intended Web server and then sends or receives messages securely. To do this, SSL uses the RSA cryptosystem. HTTPS means “HyperText Transfer Protocol Secure”,
____
Secure Hypertext Transfer Protocol (SHTTP):
SHTTP extends the HTTP internet protocol with public key encryption, authentication and digital signature over the internet. Secure HTTP supports multiple security mechanism providing security to end users. SHTTP works by negotiating encryption scheme types used between client and server.
_
What is a secure payment page?
A secure payment page means that the webpage where credit card numbers are entered is secured via Secure Sockets Layer (SSL) 128 bit encryption. You can check to see if your pay-page is secure by right-clicking anywhere on the payment page, selecting “properties” and choosing “details.” The details will list the encryption/security, and you’re looking to see if “SSL” is listed as the security type. Another way to check is to see if the URL of your pay-page starts with “HTTPS” – if so, you have a secure site!
_
- Secure Electronic Transaction (SET):
Secure Electronic Transaction (SET) was a communications protocol standard for securing credit card transactions over insecure networks, specifically, the Internet. SET was not itself a payment system, but rather a set of security protocols and formats that enabled users to employ the existing credit card payment infrastructure on an open network in a secure fashion. However, it failed to gain attraction in the market. VISA now promotes the 3-D Secure scheme.
_
3-D secure:
In 2001 – and after the failure of SET, Visa and MasterCard began the development of two independent schemes designed to improve the security of payment card-based e-commerce. The primary goal of both schemes was the authentication of the cardholder in order to reduce Internet-based CNP fraud. Visa introduced 3-D Secure – branded by Visa as the ‘Verified by Visa’ scheme – while MasterCard introduced the Secure Payment Application (SPA). Despite initial objections to 3-D Secure, MasterCard eventually abandoned the full-scale implementation of SPA, and adopted 3-D Secure under the brand name of ‘MasterCard SecureCode’. 3-D Secure has nothing in common with three-dimensional world. 3-D Secure adds another security layer to online payments. 3-D Secure is an XML-based protocol designed to be an additional security layer for online credit and debit card transactions. This authentication method is based on a three domain model (that’s why it’s called 3-D).
These three domains are:
- acquirer domain (the merchant and the bank which gets money)
- issuer domain (the bank which issued the card)
- interoperability domain (the service provided by the credit card company, Visa, MasterCard, etc.)
In a nutshell, if 3-D Secure is implemented then straight after entering customer’s card information, he or she is asked to enter a password which helps the card issuer to identify the card holder. In case of a transaction completed with 3-D Secure, it is the card issuing bank that assumes the risk, not the merchant. And most importantly, chargebacks are not permitted if the merchant complies with the acquirer’s legal requirements (3-D Secure has been activated for the card; the payer has been redirected by the merchant to a website where the card authentication takes place; the authentication process was successful). 3-D Secure definitely reduces the risk of fraudulent transactions and decreases the number of disputed transactions. It also boosts consumer confidence which can result in increased sales.
_
3D Secure 2.0
Secure payment for online credit card and debit card transactions must move with the times. As mobile devices have become highly popular around the world and cyber criminals more knowledgeable and therefore more dangerous, new methods of card and user authentication have become mandatory. The development of version 2.0 of the 3D Secure protocol for online payment authentication has been catalyzed by these changes, as well as the need to improve the user experience associated with 3D Secure. Since January 2015 , EMVCo, a company which is collectively owned by American Express, Discover, JCB, MasterCard, UnionPay and Visa, is responsible for the development of the EMV 3DS 2.0 Specification. In October 2016, EMVCo published the specs for 3D Secure 2.0.
______
What measures need to be taken to strengthen the existing security system?
Some of the positive initiatives with regard to digital payment systems are two-factor authentication in net banking/online transactions by using one-time password’s (OTPs), SSL/128 bit encryption used as minimum level of security, etc. However, we should consider other ATM security solutions, including advanced anti-skimming technology, silent alarm notifications and video surveillance, ATM lighting and remote video monitoring at all places, 24/7 surveillance and security systems strictly controlling access to all banking facilities, and so on.
______
Note:
The word ‘token’ is used in different context with different meaning. Hardware tokens are issued to the user for the purposes of authentication e.g. smart cards. Software tokens generated randomly replace sensitive information with a unique symbol or token. Payment token refers to digital cash (e-money) being transferred from one account/wallet to another account/wallet. Cryptocurrency is also a type of digital token.
______
______
Risks of digital payments:
There are three kinds of risks unique to e-payments. One, device related risk. If someone loses their mobile phone and there are no passwords protecting the phone or the app, money in an e-wallet could be compromised, or, leaving your accounts open when making payments from a public device. Two, risk from rights access. Connecting the e-wallets or other apps with social networks could pose a risk of data leakage or a consumer unknowingly sharing information that should have been kept private. Three, negligence in sharing passwords or OTP (one time passwords) with others especially when using these modes publicly. There are some other risks that are common to e-payments as well non-electronic payments — for example, giving away your account details to a third party. Provided the consumer takes basic precautions, the benefit of electronic payments far exceeds the inconvenience and transaction costs one would have incurred in other forms of payment, especially when the payment ticket sizes are small. Besides, downloading unverified apps and software can compromise security. Users should download apps with high ratings. Banking portals can get compromised as well. HTTPs was always thought to be safe. But hackers can get there also. Problems can arise at both the bank and user end. A hacker could get at any of the five stages— origin, transmission, transaction, settlement and reconciliation. To keep fraudsters at bay precautions like unique passwords, typing out links in address bars instead of clicking on links, avoid exchanging sensitive information (even your birthday) over e-mail, enable two factor authentication if available and so on. Users must differentiate the way they treat the phone. “Phone has become your bank.” While banking online, do not forget to logout from your online Banking account and close the browser page when you are done. You may like to clear your browser history, cookies and cache to ensure that no important data about your account is accidentally stored on the computer. In case you suspect that you have become a victim of any fraudulent activity, please inform your bank and report it to the nearest police station. Your bank will ensure that no further transactions take place on your account by temporarily freezing access to your account.
___
Types of frauds:
__
__
Phishing:
In the case of phishing, you may receive e-mails from dubious looking email IDs. On clicking on any links or attachments in the mail, you maybe paving the way for a breach in your Bank account’s security. These e-mails usually look legitimate so it is a good practice to check the sender’s credentials before performing any other action on the mail. These e-mails usually ask for your personal and financial account details, security codes, ID and passwords which are then misused. Fake websites using the name, logo and details of legitimate banks are also created and used to trick customers. Such mails might also install malware on your system. Hence, it is a good idea to carefully monitor your e-mails and refrain from giving out information to such websites. Keep in mind that your Bank will never ask for such details. The best thing to do would in such cases is to contact your Bank immediately to report about such mails for the greater good of public awareness.
_
Malware/spyware:
There are several computer programs which are installed on your local hard drive from the websites you visit. These programs are designed to take away your sensitive information when you use your financial information online (for example on ecommerce website or when you use your internet banking). These programs then send away the information to the criminals who circulate such information in the first place through software. Malware, such as key loggers, can get into computers that are not securely configured or without adequate anti-virus or anti-malware protection. It steals banking credentials based on key strokes or passwords stored at less secure locations, such as browser password cache or text files.
_
Man in the middle (MITM) attack:
This method generally involves luring a customer to a honeypot wireless or wired network for free Internet in public places. In a MITM attack, the hacker sees the information going to and from your computer. They intercept, and alter, the communication between you and the website.
_
Vishing:
Vishing is the same as Phishing, except that instead of luring customers via e-mail, the scammers use Voice over IP or a direct telephone call to gain access to your personal details. For example, you might get a call from someone claiming to be an employee of the Bank you have your account in. Citing reasons like unauthorized transactions or standard safety procedures, they might ask you to share your personal and financial details so that they can verify and secure your account. Once you share your details, they use it to gain access to your account. It is difficult to book people involved in vishing and bring them to justice as it is conducted by voice process. Such scams are often generated from across borders, so as to avoid law and enforcement. Message or calls that seem suspicious to you should not be entertained. You should refrain from entertaining any such calls and ensure that you do not share any kinds of details. Remember that your Bank will never make such a call to you.
_
SIM Cloning:
Once someone procures your internet banking login details via phishing, he could clone your mobile phone SIM card with the help of fraudulent documents. This allows him access to the OTP (One Time Passwords), a security feature required for completing a transaction which he then uses to execute fraudulent transactions through your account. Ensure that your registered mobile number is updated with your bank’s database and is an active connection so that transactions using a duplicate SIM card are not performed on your account. If your SIM card is deactivated, please call your mobile phone operator immediately and register your new number with your bank.
_
Skimming:
Some criminals will tamper with ATM or POS machines (usually in case of POS machines, the merchants are involved). When you swipe your card, the details of the card will be extracted by the tampered machine and will be used later. Skimming is where the crooks use a booby-trapped card reader, for example glued over the real card reader on an ATM, or cunningly squeezed into the card slot on a payment terminal, to read and record the magnetic stripe on your card. Even if you have a Chip and PIN card, the magstripe contains almost enough information for a crook to convince a website they have your card. For example, your name as it appears on the front of the card, the “long code”, usually 16 digits across the face of the card, and the expiry date are all there on the magstripe, ready to be copied surreptitiously and used on the web. The CVV acts as a very low-tech barrier to card-not-present fraud, because most websites also require you to type in the CVV, which is not stored on the magstripe and therefore can’t be skimmed.
Of course, there are numerous caveats here, including:
- The vendor mustn’t store your CVV after the transaction is complete. The security usefulness of the CVV depends on it never lying around where it could subsequently fall foul of cyber thieves.
- The payment processor mustn’t allow too many guesses at your CVV. With unlimited guesses and a three-digit code, even a crook working entirely by hand could try all the possibilities with a few hours
_
Cloning means some criminals will simply clone the data on the card on to a different card. This technique also involves tampering with the card swiping machines.
_
A few simple precautions will help, regardless of your card provider:
- Don’t let your card out of your sight. Crooks working out of sight, even for just a few seconds, can skim your card easily simply by running it through two readers. They can also snap a sneaky picture of the back of the card to record both your signature and the CVV.
- Try to use the Chip and PIN slot when paying in person. Most chip readers only require you to insert your card far enough to connect up to the chip. This leaves most of the magstripe sticking out, making skimming the card details harder.
- If in doubt, find another retailer or ATM. Most ATMs still require you to insert your whole card, and can therefore be fitted with glued-on magstripe skimmers. If you aren’t sure, why not get hold and give it a wiggle? Skimmers often don’t feel right, because they aren’t part of the original ATM.
- Stick to online retailers you trust. Check the address bar of the payment page, make sure you’re on an encrypted (HTTPS) site, and if you see any web certificate warnings, bail out immediately.
- Keep an eye on your statements. If your bank has a service to send you a message notifying you when transactions take place, consider turning it on.
____
Chargeback fraud:
Chargeback fraud, also known as friendly fraud, occurs when a consumer makes an online shopping purchase with their own credit card, and then requests a chargeback from the issuing bank after receiving the purchased goods and services. Once approved, the chargeback cancels the financial transaction, and the consumer receives a refund of the money they spent. When a chargeback occurs, the merchant is accountable, regardless of whatever measures they took to verify the transaction. A 2016 study by LexisNexis stated that chargeback fraud costs merchants $2.40 for every $1 lost. This is because of product-loss, banking fines, penalties and administrative costs.
____
Credit card fraud:
_
The figure below shows points of contacts for credit card frauds:
_
Credit card fraud is a wide-ranging term for theft and fraud committed using or involving a payment card, such as a credit card or debit card, as a fraudulent source of funds in a transaction. The purpose may be to obtain goods without paying, or to obtain unauthorized funds from an account. Credit card fraud is also an adjunct to identity theft. Although incidence of credit card fraud is limited to about 0.1% of all card transactions, this has resulted in huge financial losses as the fraudulent transactions have been large value transactions. In 1999, out of 12 billion transactions made annually, approximately 10 million—or one out of every 1200 transactions—turned out to be fraudulent. Also, 0.04% (4 out of every 10,000) of all monthly active accounts were fraudulent. Even with tremendous volume and value increase in credit card transactions since then, these proportions have stayed the same or have decreased due to sophisticated fraud detection and prevention systems. Today’s fraud detection systems are designed to prevent one twelfth of one percent of all transactions processed which still translates into billions of dollars in losses. Credit card fraud happens when consumers give their credit card number to unfamiliar individuals, when cards are lost or stolen, when mail is diverted from the intended recipient and taken by criminals, or when employees of a business copy the cards or card numbers of a cardholder.
Protect yourself:
- Record all your account numbers and company contact information and keep this list in a safe and secure place. Do not keep it in your wallet or purse.
- Keep copies of your vouchers and ATM receipts, so that you can check them against your billing statements. Notify your card issuer immediately if you suspect unauthorized use or fraudulent use of your card.
______
Point-of-sale malware:
Point-of-sale malware (POS malware) is a type of malicious software (malware) that is used by cybercriminals to target point of sale (POS) terminals with the intent to obtained credit card and debit card information by reading the device memory from the retail checkout point of sale system. POS malware is released by hackers to process and steal thousands of transaction payment data. The card information which is usually encrypted and sent to the payment authorization is not encrypted by POS malware but sent to the cybercriminal. Finding this malware can be difficult, and you may not even realize you’re infected. However, IT departments may be able to notice the warning signs first, as it will show up as codes when open processes fail and the scan process doesn’t work. The problem is that you can’t see the malware until it wants to be seen, which is usually never. It can spread to other areas of the system and other systems.
____
Key ways in which digital payments can be breached:
- Key Logger: Just like tap dancers are strongly aware of how and when their tap shoes strike the floor, a key logger is a software that records the key-strokes made by the user on the keyboard. Static passwords like 3D PINs or banking passwords, that are entered regularly, are vulnerable to cyber-fraud through a key logger, as it can record regularly typed in passwords without the user’s knowledge. Using a dynamic PIN is a smart solution to the breach caused by key loggers. It is also beneficial to use apps that have an in-app secure swipe instead of the ones that require the keying in of an OTP.
- Social Engineering: Those calls that seem to come from the bank might not really be from the bank itself. Credit and debit cards are used at many online merchants and marketplaces. Even if these online transaction use OTPs and CVVs, someone may call the cardholder and pretend to be a representative of the bank, acting as if an online transaction needs to be confirmed, and subsequently ask the cardholder to share the received OTP. When the OTP is disclosed by the cardholder, a fraudulent transaction can take place.
- OTP Pop-Ups: As One Time Passwords have a limited time validity (in minutes), they are believed to be secure. Although OTPs mostly appear as pop-up notifications on mobile phones, these pop-up messages are clearly visible, even if the mobile phone is locked. This means that the OTP can be easily accessed without the permission of the user, making the transaction open to being breached.
- OTP Accessibility: Although an OTP is essential, the medium through which it is delivered is of utmost importance. Most of the times, a One Time Password is sent as an SMS. The problem with this is that many apps can read SMS messages. This means that if an app is malicious it can misuse the OTP that has been received. Therefore, users should be aware of what privileges they give to the apps on their smartphone and also look at reviews and number of downloads of the apps they choose.
- EDC Machines: Even with a second-step PIN verification, swiping a card on an EDC machine is not as safe as it seems. EDC machines are susceptible to breach and a compromised machine can copy the details of the cards when swiped. Most debit and credit cards have a static PIN, and even these PINs can be stored in compromised EDC machines. A breach like this can give easy access to the personal data of cardholders to fraudulent groups. A dynamic PIN for physical credit or debit cards could be a strong safeguard against compromised EDC machines.
____
____
Mobile security:
700 million Android phones have spying firmware preinstalled:
The term “mobile phone security” is something of a joke these days, with the number of exploits, bugs, and breaches that are endlessly assaulting us and putting our personal information at risk. So, when security outfit Kryptowire sounded the alarm on Chinese company Adups for using its preinstalled apps to spy on Android users with Blu smartphones, it wasn’t exactly a shock. Now, however, the impact of Adups alleged spying is growing in magnitude, and it’s dragging other Android device manufacturers into the quagmire. Trustlook, another digital security firm, dug deeper on what devices utilize Adups and could be used by the Chinese company to scrape your private information, and the list is absolutely massive. Trustlook says that over 700 million Android smartphones have Adups firmware installed that puts the user at risk of having text messages, call histories, and device information collected without their knowledge or consent. Qualcomm’s Choudhary reveals how his company is helping push the cause of mobile payments by providing secure solutions. “Secure applications, user authentication and device attestation are three key pillars of mobile security,” said Choudhary, who is the senior director for program management at the San Diego-based silicon giant. Choudhary says that Aadhaar in India is ‘light years’ ahead of other solutions abroad, but when you talk about hardware based security, India is lacking which is indicative of the nascency of mobile transactions in the country. He drew parallels to what happened in the US and China and hoped India would follow the same path. A good example of this deficiency is the fact that mobile wallets like Paytm don’t harness Qualcomm’s secure execution environment but just rely on Android’s built-in secure layer which Choudhary described as a ‘secure tunnel in the cloud”. While this is a good enough solution, it is not the best as you can always have more security. As mobile payments become more prevalent in India they will be bigger targets for hacking, which is why it is imperative for mobile wallets to use this capability.
_
Making Secure Mobile Transactions by:
- Download Apps from trustworthy sources
- Check App reviews and ratings
- Protect your Mobile Devices with Passwords
- Send data over a Secure Internet Connection
- Check Mobile Websites for HTTPS
- Watch Statements and report suspicious activity
- Do not activate the “developer mode” on the device
- Do not activate the “Install applications from third-party sources” option
- When installing new apps, carefully study which rights they request
- If the requested rights do not correspond with the app’s intended functions (e.g., a game requests rights to send text messages), do not install the app
- Use protection software. Most of us do not install antivirus on our phones and even if we do, we use some free version which comes with ads or if they do not have ads, they do not provide full protection. Spend money and get proper antivirus from reputed company.
- Don’t root your phone. Rooting phone has become more of a style nowadays. Most of us don’t even know what to do after rooting a phone or even worse, we don’t even know what can be done with a rooted phone apart from removing system apps. Rooted phones are vulnerable and they can be easily attacked by hackers. Do not root your phone.
- Wipe data if phone gets stolen: In this age, losing your phone is like losing your wallet – you could lose a lot of money through your apps. While chasing the thief can be one way of getting it back, remotely wiping off the data on your phone can help prevent monetary and data loss. Both Android as well as Apple devices let you do this.
_______
For desktop/laptop, take following precautions:
- Install a proper antivirus. Keep your antivirus definitions updated.
- Regularly scan your computer for spyware, malware, adware and viruses.
- Make sure that the antivirus you are using has protection against keylogger scripts, phishing and spam.
- If you are using internet banking, make sure that that you are using incognito mode of your browser. All browser extensions are disabled in incognito mode and hence, if there are any extensions which are capable of stealing sensitive information, you will stay protected.
- If you know how to handle Linux, try to dual boot your computer and have Linux installed. Spyware, malware, virus, adware etc. do not work on Linux operating systems. They infect Windows based computers and Mac computers.
- When using ecommerce website, make sure that the url of the website reads HTTPS and not HTTP. HTTPS means an encryption protocol where in your sensitive data is sent over the internet using secure encryption that cannot be broken. 128-bit SSL encryption is the most popular encryption method but you can also get 256-bit encryption on several websites.
- Use on-screen keyboards to enter password and user ID for net banking or logging in to websites where financial data will be entered. On-screen keyboards are extremely effective in preventing data theft caused by key logger scripts that often get installed on computers.
- Avoid going to websites which are loaded with too many ads.
________
________
Things to do with your bank can keep your money safe while using digital transactions:
Get Alerts:
Every bank should send SMS and / or email notifications to account holders whenever you carry out a card transaction or internet banking.
Set Limits:
Once you set a limit, you cannot use your card for any amount above the set limit. Setting limits will ensure that even if your card is going into wrong hands, you can limit the losses because of the limits you have set.
Primary and secondary debit cards:
Choose the bank where you want to stash all your money. Call this the primary bank account. The card corresponding to this account will then become your primary debit card. The other bank will be the secondary bank account and hence, the corresponding card will be your secondary debit card. Put all your money in primary account. Keep your primary debit card at home. Do not carry it with you. Do not use it for any digital transaction. Do not use it for withdrawing money from ATMs. Transfer some money from primary to your secondary account. Make sure that you transfer only a small amount. Use the debit card of your secondary account everywhere. This way, even if your card information is stolen or you lose your card, you will lose only a small amount of money and not your entire money. This is a very effective strategy of keeping your money safe.
Security questions:
When you are applying for a bank account, you will be asked to input some details as security. These security questions usually ask things like your first pet’s name, your first math teacher, your grandfather’s name, your place of birth etc. These are very common questions. Never share such information on social media platforms. Avoid sharing your important details like date of birth, your email id, your phone number etc. on social media websites such as Facebook.
Go for Credit Cards:
In case of credit cards, if you think that a fraud transaction has taken place, you can immediately call the issuer bank of the card and ask to delay the payments. The bank will do so and may even immediately revert the payment. This happens because in case of credit cards, the liability stays with the banks. This will not happen in case of debit cards. Once a transaction goes through using a debit card, you will lose your money.
_____
Switch to chip-based cards (vide supra):
Only and only if the chip cannot be read due to any kind of technical glitch, the magnetic stripe should be used. This instruction has been given to all merchants who are using the POS terminal. In case a merchant doesn’t do that, you can politely ask the merchant to use the chip and not the stripe. If the merchant denies, politely refuse the transaction.
_______
When you go to ATMs to withdraw cash, remember and follow the things mentioned below in the table.
| Things to do | Explanation |
| Check the machine | Take your time and check the machine to see if any skimmers have been installed or not. |
| Check for cameras | Check properly if any additional cameras have been installed somewhere which are positioned in such a way that they can record the keys that you are pressing. The machine itself will have a camera on top but that is meant for recording your face and is directed at your face and not at the keypad. While at ATM, ensure no one is looking over your shoulders. |
| Tear the receipt | In case you are taking a receipt from the ATM, tear off the receipt properly into tiny pieces if you want to throw it away right there. It is possible for criminals to take the receipt and get your account number despite the fact that the whole account number or the card number is not printed but only the last four digits. It becomes easy for the criminals to find the other digits using algorithms if they get the last four digits. At least the algorithms don’t need to work with the last four digits. |
| Don’t display money | Once you withdraw money from ATM, count it while facing the machine and then simply put it in your pocket or purse and then turn around and leave the ATM. Never display the money to others. Never count the money when you get out of the ATM. You may be robbed or money may be snatched away from thieves if you keep dangling the money in front of them. |
| Avoid white label ATMs | White label ATMs are those ATMs which are not issued by any bank. They are issued by private organizations and they dispense money for all bank cards. The problem with these machines is that they are not monitored by banks and in case of disputes, neither the bank and nor the private company will take ownership and you will lose your money. They are mostly targeted by criminals for skimming. Avoid them as much as possible. Of late, banks started circulating notices that one should use ATM of their respective banks and avoid ATMs of other banks and white label ATMs. Follow this if you want to stay safe. |
________
________
Use VPN:
Using a Virtual Private Network (VPN) not just sidesteps geographical restrictions on online content but can also add a layer of security to your online communications. It is widely used as a tool to secure web browsing sessions by enterprise as well as individual users. You can add a VPN on your smartphone or your Wi-Fi network at home. For a smartphone, you will have to downloaded and install a VPN app. Most VPN apps charge a monthly subscription, while some like Opera VPN are completely free to use. Deploying a VPN in wireless router will transmit all online communication through an encrypted tunnel created by the VPN. VPNs are by far one of the most effective tools for you to enhance your online security and anonymity.
- Anonymity Guaranteed
A good VPN service makes you anonymous on the internet by masking your real IP and tunnelling your data through a network of servers. This is why when connected to a VPN, you will be able to browse the internet anonymously and securely like never before. It becomes next to impossible for anyone – be it hackers, advertisers, spying agencies, etc. – to track your online activities, which cannot be said for other alternatives out there. Unlike web proxies and programs that hide IPs, VPNs not only allow users to access both websites and web applications without compromising their anonymity in the process, but they also provide them a secure cover of encryption for their data.
- Security on Public Wi-Fi Networks
As accessible as public Wi-Fi networks are, they are equally dangerous at the same time. These networks tend to be breeding grounds for hackers, cybercriminals and government agencies that will leave no stone unturned to get their hands on your information. Fortunately, this will not be a problem if you use a VPN, as once connected, your browsing sessions will remain private at all times.
- Data Protection made simple
Reliable VPNs offer numerous protocols for users to choose from, like PPTP, TCP, IPSEC, IKeV2, SSTP and UDP, which positively affect speed and security. At the same time, they also offer military-grade encryption. It is important to note that the very same encryption standards are employed by government bodies and entities to protect their own data. What this essentially means is that you will never have to worry about losing your data and personal information whenever and from wherever you go online.
- VPNs protect any and all Devices
VPNs are compatible across all platforms and devices. It really does not matter what devices you own, or which devices are being utilized in an organization. Once a VPN is set in place, its features will be available across all devices connected to the protected VPN, which makes it a viable solution for people looking for a cost effective solution in regards to their online security.
The applications of using a VPN are limitless, and it’s equally useful to all those individuals and businesses that wish to use the internet freely without having to worry about losing their data in the process and/or becoming a target of cyber criminals. On the other hand, individuals and businesses can switch between IPs and also set up secure remote access points, as well, which solidifies their credibility as one of the best tools out there for security, internet freedom, streaming and improving productivity without breaking the bank in the process.
______
Set Up a Password Manager:
You can’t remember strong, unique passwords for each account you have, and the accounts you’ve forgotten about are especially likely to have a weak or repeated password. The nice thing about setting up a password manager, though, is that once you put in the time to get it up and running it will genuinely make your life easier beyond just improving your security. You won’t have to go through password resets all the time, risk being locked out of accounts after too many failed entry attempts, or need to stretch your brain with complicated password mnemonics. Everything will just be there behind one long and strong master password. Password managers also make it easier to change passwords down the line, so they really do have a long-term benefit. There are a number of good password managers to choose from (some are free!) and the easiest way to set them up is just to choose one and then add and change passwords gradually over time as you visit sites and services that involve a login. Within a few weeks of adding accounts through natural browsing you’ll have significantly improved your personal security posture. Password managers are certainly not perfect. They centralize all your data, and it’s always possible that the companies that provide them could be breached. It’s happened. But unless you’re willing to devote just as much or more time to an elaborate password management strategy of your own creation, managers are a reasonable way to bring your password situation under control. It’s not your fault that passwords are such a lousy security system, but as long as they’re around we should all deal with them in a safe way.
____
Digital vault:
In 2016 alone, 873 data breaches exposed more than 29.8 million records containing potentially sensitive information, according to the Identity Theft Resource Center. Clearly, stronger measures must be taken. While more people are turning to digital solutions to store important information, the threat of cyber security remains a concern for many businesses, governments and individuals. With the digital vault options now available, consumers need to be educated on what features are essential to ensuring their security.
The top features are:
- Password manager: Keeping passwords in a highly secure location might be the feature you access the most in your digital safe deposit box. Look for a password generator and the ability to link directly to the login screen to copy and paste the password in. Also, make sure you can access the password vault even when offline.
- Encrypted email: Your digital box should have an encrypted email so you can send and receive sensitive documents.
- Accessible: Your digital box should have an easy-to-use mobile app, allowing you to access your passwords, documents and to download and receive encrypted information from a number of devices.
- Digital inheritance: You should be able to designate several loved ones as beneficiaries who will have access to your digital files and documents in case of a life-changing event.
- Security: Zero Knowledge technology is a must. This means only you and those you authorize can access your box. Also, you want something known as double encryption. This assures you that even if there is a breach, the hacker cannot access documents or data.
______
Make your PIN:
Theoretically, there are 10,000 possible four-digit combinations the numbers 0 to 9 can be arranged into, and if everyone selected a number entirely at random that would offer a reasonable level of protection. People, however, seem to exhibit a staggering lack of imagination and select very predictable numbers. This is probably because people choose numbers that are easy to remember, but this unoriginality leaves them vulnerable. The vast majority of PIN numbers begin with 1 or 0. If yours starts with 1, you’ve reduced the possibilities from 10,000 to 1000. We all carry debit cards, credit cards and mobile phones, and most of these items require a four digit pin to unlock them. Shockingly, it appears that one in every 10 people uses the same pin 1234. The customer PIN is the primary security measure against fraud; forgery of the magnetic stripe on cards is trivial in comparison to PIN acquisition. A street criminal can easily steal a cash card, but unless he observes the customer enter the PIN at an ATM, he can only have three guesses to match against a possible 10,000 PINs and would rarely strike it lucky. Even when successful, his theft still cannot exceed the daily withdrawal limit of around $300. However, bank programmers have access to the computer systems tasked with the secure storage of PINs, which normally consist of a mainframe connected to a \Hardware Security Module” (HSM) which is tamper-resistant and has a restricted API such that it will only respond to with a YES/NO answer to a customer’s guess. A crude method of attack is for a corrupt bank programmer to write a program that tries all PINs for a particular account, and with average luck this would require about 5000 transactions to discover each PIN. A typical HSM can check maybe 60 trial PINs per second in addition to its normal load, thus a corrupt employee executing the program during a 30 minute lunch break could only make with about 25 PINs.
_______
Golden rules for passwords:
Passwords are ultimate keepers of diversity and security. Since Ancient Roman times until now, they are used for one to prove being worthy to get some privilege others do not possess, however strongly desire to obtain. A “magic word”, which one knows and others don’t, opens the door for an opportunity and diversifies an individual selecting them from an enormous crowd. We can say that password is the oldest and the most widely used pillar of authentication, which is extensively used in 21st century Internet. Its importance is even greater than before, because nowadays more and more people are communicating remotely without seeing or hearing each other, using remote means to gain access to automated systems. Therefore, they have to rely only on passwords to verify remote party and prove their own identity. Just getting to know other person’s password allows you to become that person in the eyes of others, do whatever you please in their name, obtain their privileges in automated systems. That’s why passwords are so critical to protect properly. However, most of the schemes used for authentication today have their own weaknesses — although some of them are quite theoretical, in rapidly changing world theoretical threats frequently become very practical. Here are some golden rules when it comes to using passwords and pins for digital transactions or online transactions. Follow them properly and you should be safe:
- If you are using Net Banking, make sure that you change the password frequently. When we say frequently, you should ideally change it once every three months. You can do that more frequently if you want to.
- Never keep the passwords digitally stored on your computer. Passwords for sensitive websites like net banking, ecommerce website etc. should be kept written in a diary or a copy. We literally mean the old fashioned, pen and paper. That cannot be hacked! 3. Never use passwords that are easy to guess. Use passwords that have combination of letters, digits and special characters. Such passwords are very difficult to guess and crack using password cracking software.
- If you are using a comparatively easy password and you are using a hint to remember it yourself, make sure that you are not making the hint too obvious for others to guess.
- In case of PINs, make sure that you are changing your ATM PIN once every 3 months.
- For OTP, make sure that the message sent by bank or the ecommerce website or mobile wallets cannot be read on locked screen. This will simply defeat the whole purpose of OTP.
- Never ever share your PIN or password with anyone.
- If you have used a password for your bank, never use it anywhere else. Many people actually keep using the same password everywhere. This is not a good idea. Especially, your internet banking password should be totally different from any other password you provide anywhere else.
- What you may not realise is that a simple phrase could offer increased security and be more challenging to guess than a single word, even if the latter uses symbols and the like. How about something like “itraveltolondon”? Connecting multiple words to form a phrase that is unique (avoid famous or well-known phrases) offers two advantages: it is harder to hack and it is also easier to remember, as it can have personal relevance.
- If you are tech savvy, make use of a proper password manager for storing all your passwords and then lock the password manager using a master password and memorize the master password. Never store the master password.
_____
Web fraud detection:
Organizations that accept payment cards over the Web — also referred to as “card not present (CNP)” transactions — or organizations that back those payments, will deploy Web fraud detection software or services to detect and help prevent fraud. Web fraud detection systems typically focus on new account origination, account takeover and payment fraud. With account takeover and new account origination fraud , detection, organizations attempt to root out unauthorized or fraudulent users posing as legitimate users. Payment fraud detection involves determining whether purchases are being or have been made with stolen payment cards. Some vendors also offer fraud intelligence services, authentication, malware detection (such as man-in-the-browser infections on computers and mobile devices) and secure clients, as well as managed services in which the vendor is primarily responsible for monitoring and taking action on instances of fraud. Web fraud detection system vendors generally provide either an on-premises software product or platform, or cloud-based software as a service (SaaS) that scans financial transactions made via the Web or by using mobile devices.
____
Advances in Biometrics:
What’s needed, cyber-security experts say, is to move away from passwords by introducing new online authentication methods that create minimal friction for consumers and keep consumer credentials in a secure location where hackers can’t get at them.The push to leave passwords in the rearview mirror is already under way. Thirty-six percent of companies surveyed by Lawless Research foresee doing away with password authentication within four years, and another 36% predict they will no longer rely on passwords within five to nine years. An early frontrunner to replace passwords is biometrics. The technology is the equivalent of electronic DNA, which makes it nearly foolproof for consumer authentication. Biometric technology identifies an individual by measuring such physical traits as voice, fingerprints, heart rate, and retinas, and then comparing them to the original biometric record stored in a secure location, such as a device used by the consumer and registered with the company with which he does business. Further increasing the appeal of biometrics is that the technology is becoming standard on smart phones, tablets, and personal computers. These devices include voice-recognition applications, fingerprint scanners, and cameras with high quality lenses that can be used for selfies. As the cost of biometric technology comes down, device manufacturers are making it standard, which brings it into the mainstream.
_____
How you are fooled by scamster:
Verified By Visa Activation:
You receive email:
Email Subject
Verified By Visa Activation
Apparent Sender:
Visa
Return Address:
Verified by Visa < [email protected]
Email Format: HTML
URL of Web Content:
http://www.defi-des-entreprises.asso.fr/ administrator/components/com_comprofiler/www. usa.visa.com/index.html
Location:
France
Scam number:
aa-3279
Comments:
- Email asks you to confirm/update/verify your account data at Visa by visiting the given link. You will be taken to a spoof website where your details will be captured for the phishers.
- Visa never send their users emails requesting personal details in this way.
- The REAL URL of the spoof website is hidden by a hyperlinked image in the body of the email. This is a technique used to get past spam filters that can only read normal text.
- The spoof website this email link is hosted on the personal computer of the phishers.
- The REAL URL of the spoof website looks nothing like the actual Visa URL.
___
An offensive strategy could transform cyber security:
At a Passcode event in Washington, Carnegie Mellon University cyber security expert David Brumley said digital defenders need to attack their own systems to discover the flaws. As cyber security firms prepare for another year that could be full of high-profile breaches, they’re looking for fresh ideas to keep criminal hackers out of computer networks. Many companies that are targeted with cyber-attacks, such as financial institutions, healthcare organizations, and government agencies, have begun to deploy so-called penetration testers, professional white hat hackers who simulate cyber-attacks on sensitive computer networks.
______
What happens when you Transfer Money to Wrong Bank Account or Digital Wallet?
There are three things that you can do in this case. The Reserve Bank of India has clearly indicated that the transfer of funds electronically depends entirely on the account number. Unfortunately, the beneficiary’s name has little relevance in the online transfer process. The trouble with wrong beneficiary names arises later. Now, you can be confronted with three different situations. In case you have punched in a wrong account number, which is nonexistent, your money will automatically come back to your account. Ask your bank to hasten the process. Another case arises if you have punched in the wrong account number (unintended), but the right beneficiary name (the one you wanted), you can reach your bank and prove to them that you have done it by mistake. The bank will then, on your behalf, reach the account holder and ask for the amount to be returned as there is strong evidence of erroneous transfer. However, the bank can only ask as a facilitator. The third case, wherein you have typed in the wrong account number, however, the name of the unintended account belongs to a person with the same name, you’ll have to prove to the bank that the transaction is wrong. In each of the above cases, the bank can’t take the money away from the person and give it to you – it can only act as a facilitator. The situation worsens when there are multiple combinations of different banks, different cities, branches, etc.
Tip:
Banks normally ask you to type the account number twice. So if you happen to commit a mistake in typing, the mismatch in the two numbers will not allow you to proceed further. There’s your first level of precaution. Then, if the IFSC code is correct, it will ensure that the intended bank and branch are at least coordinated. Also, if you want to transfer a large sum of money online, you can do a ‘test’ transfer of a small amount and check.
_
When you transfer to the wrong digital wallet:
If you have made an error in typing the wrong number, you might assume the problem can be resolved with a quick call to your company. But the process is not so straightforward. Just like banks, even wallets can’t help you in getting your money back. Once you have initiated the transaction, the case is between you and the person you’ve transferred it to. Unlike an online bank app, did you know Paytm will not compensate you if your money gets stolen on account of them being hacked? Wallets don’t have access to the amount you spend. So, once you’ve made the transaction, it’s between you and the receiver. Also, ensure that the wallets you use are PCI DSS compliant (Payment Card Industry Data Security Standard). That being said, it doesn’t mean that they can’t be hacked. Money in the wallet may be stolen, but not your card details.
_______
_______
No password authentication:
The idealistic way to keep a secret safe is not to use it: if you never use it, nobody will intercept it. However, this makes such secrets useless. Since secrets give you privileges, you want to obtain and exercise those privileges now and then. To do that you have to prove you know the secret. This process involves communicating the secret to other party, which eventually exposes whole or part of a secret. Exercising a secret involves at least 2 parties: a prover (you) and a verifier (an entity which eventually decides whether your secret is the real correct one and you deserve the privileges you claim). However, if you cannot communicate with verifier directly, you have to use one or more intermediate entities, in which case those entities know the secret as well. While communicating, you may be using thousands of intermediate links to deliver your data, so once you send a secret to verifier — it’s not a secret anymore.
Existing methods of authentication:
Existing methods provide some level of protection,- better or worse,- yet each of them has significant drawbacks. So far, most current systems and secure protocols have used only three types of cryptographic primitives: encryption, key agreement and digital signatures. More high level tasks, like authentication, are achieved by combining those primitives in some way in a protocol.Internet authentication started with pretty basic passwords: a user entered the password in the web-form, password was sent via HTTP to the server, server verified the password and lets the user in. That was in the early days of the small Internet. At that time attackers were limited by having very little experience on how Internet works. Even if some had basic networking knowledge, they did not have equipment, tools or software (which was very expensive at that time) to do the attacks. Also, the attacks themselves were pointless because of the little commercial value of the information which traversed the Internet at that time. Eventually growth of the Internet and availability of the knowledge, software and tools created a first network attacker: HTTP passwords were easily stolen by simplest passive network sniffers and protocol analyzers. Next step was to change passwords to some values which were useless for passive eavesdroppers: people started hashing the password. Since both server and user had the same password, they could produce identical hashes of those and compare them, with user sending the hash to server. It seemed that attackers couldn’t get the password, because reversing a hash function is computationally “almost impossible”. This solution saved the day… for just a little while!
Attackers used two ways to overcome this:
- First: many people make their passwords “easy-to-remember”, so they attackers hashed a big set of popular words and by knowing the hash, could easily “lookup” the original password if it happened to be from the produced “dictionary”: a dictionary attack was invented.
- Second: even if someone used complex password, attackers just used the hash directly to authenticate with the server with a “modified browser”. They did not enter the password in the form, but injected hash directly to HTTP stream: an active attack was invented.
It was clear now that HTTP traffic had to be encrypted. However, since communicating parties were located far away from each other a key agreement was used and was eventually broken by attackers: man-in-the-middle was proposed. The history continues: the more sophisticated schemes for protecting the transmission of passwords are proposed, the better and smarter attacks are designed to defeat them. Wouldn’t it be great to avoid transmitting the passwords at all?
_
Three factor authentication (3FA) for digital transaction as proposed by me:
As there are many threats and vulnerabilities with digital payment systems, we need a system that goes much further than regular security standards. This digital payment system should have more than two layers of security so that it is virtually impenetrable. The system should be planned in such a way that each layer both independently stands by itself and also smartly integrates with the overall security structure. This system should have multiple security checkpoints so that only the authorised user can successfully, yet easily, make payments through it. Keeping balance between security and convenience, I propose three factor authentication (3FA) to enhance security and at the same time reduce inconvenience and avoiding any password/PIN.
These three factors are:
- Biometric authentication (e.g. finger print)
- Device authentication (e.g. smartphone or laptop) or card authentication at ATM/POS
- OTP as SMS on cell phone/email
Whether you are performing digital transaction at ATM, POS, smartphones or laptops, these three factor authentication should become rule worldwide. Finger print authentication should be available on all computers, smartphones, ATMs and POS worldwide. At ATM/POS whenever your card is swiped after finger print authentication, OTP is sent to your mobile phone and only after entering OTP, your transaction is completed. No need to remember any password/PIN anywhere any time. More importantly 3FA will create worldwide database of fingerprints which will help catch criminals involved in all types of crimes as these criminals’ fingerprints are also registered for digital transactions. About 1% people might not be able to enrol in a biometric system using their fingerprints. They can use face scan or voice identification.
______
______
Economy and digital transaction:
_
GDP per capita and spread of digital transactions:
The figure above shows that greater the GDP per capita, higher is the digital technological adoption.
_
Electronic payments grow faster than GDP across all regions: 2015 report:
Non-cash payment volumes are expected to continue to grow strongly in 2014, according to the World Payments Report 2015 from Capgemini/Royal Bank of Scotland. Volumes are projected to grow at a rate of 8.9% to reach a record high of 389.7 billion transactions, spurred by economic recovery in mature markets, expansion in China and the adoption of digital technologies and immediate payment schemes. Emerging Asian countries are driving the growth in non-cash, particularly China which is expected to move into fourth place behind the US, Europe and Brazil in terms of non-cash payments. The rising penetration of mobile phones in smaller Chinese towns and cities is resulting in increased mobile payments — 4.5 billion in 2014, up 170%. Steps taken by the Chinese regulatory authorities to accelerate the deployment of point-of-sale equipment to merchants and to open the domestic card payments to competition have also increased non-cash payments. Despite the rise of challengers and new market entrants, the report feels that banks are perhaps better positioned than their rivals to offer holistic solutions. Banks are able to operate across various payment methods and channels to offer customer-centric innovations. This makes them a consolidated provider for consumers and businesses, as opposed to customers having separate relationships with multiple parties depending on the payment scenario. Banks are also strongly placed to develop innovative offerings based on existing infrastructure, such as immediate payments, to differentiate themselves from other PSPs.
_____
2016 United Nations Study maps Top 10 Ways governments and companies can create Digital Economies:
A new report from the United Nations-based Better Than Cash Alliance unveils ten tangible steps governments and companies can take to leave behind a cash-dominant economy and embrace digitization of payments. The Better Than Cash Alliance research studied 25 countries, including India, Nigeria, Tanzania, Ghana, Brazil, and Mexico, among others. What emerged were ten ‘accelerators’ or actions that regularly proved to make a strong impact in advancing the creation of economies where digital payments are widely available. This report also highlights the ever increasing importance of transitioning to digital payments. The data compiled in the report provides evidence of the benefits that digital payments bring to various nations as depicted in the figure below:
_
_
The analysis of the evidence has led to identifying 10 actions on how other countries can accelerate their initiatives to save money, raise tax revenue, and increase opportunities for their citizens to lead better lives.
The 10 accelerators are:
- Promote merchant acceptance infrastructure across micro, small, and medium enterprises to deepen usage among consumers and larger payers alike.
- Leverage existing networks or platforms to deliver digital payment products and services to extend digital payment services more quickly and in a way that lowers the cost.
- Establish a shared digital infrastructure for players to reduce barriers to entry and promote innovation, both in public and private institutions.
- Establish interoperability to reduce barriers that confine digital transaction to a single payment platform to increase adoption and payments acceptance.
- Develop a unique identification program that both public and private sector players can access to verify identities can drive digital payments and financial inclusion. Consumer protection frameworks are essential to ensure adequate privacy, security, and data control.
- Digitize routine use cases that individuals frequently use for transactions can increase comfort with digital payments and increase digital transaction volumes.
- Digitize government payments to advance a digital payments ecosystem by saving transaction costs and increasing civilian access to payments.
- Digitize government receipts to promote comfort with digital payments among individuals and businesses, and ultimately reduces leakages and boosts revenues. Collaboration with private sector is key.
- Establish regulation that promotes innovation and responsible practices, by understanding the gaps and barriers of existing regulation, and engaging all stakeholders.
- Implement policies that incentivize and improve the convenience of digital payments to drive faster and more widespread access and adoption of digital payments.
Understanding these accelerators will help governments develop tailored approaches to best apply this knowledge in their appropriate markets. The report is accompanied with a toolkit to specifically help policymakers and important stakeholders to develop such programs.
__
The Cost-Benefit of Electronic Payment Systems: The Case of India: a 2011 report:
Inclusive growth and financial security report shows benefits of e-payments to Indian society, and estimates that automating all government payment flows could save the Indian government up to $22.4 billion annually, almost 10% of the total payment flows between the government and household (estimated to be $296 billion, or $250 per capita). These savings would cover the required investment within the first year. The report was done in partnership with the Bill & Melinda Gates Foundation.
Where would these savings come from? The report identifies 3 current payment inefficiencies:
- Leakages account for 75-80% of the total losses due to the diversion of benefits to unintended individuals. For example, beneficiary rolls were found to contain absentee workers and deceased people. Misrepresentation of man-hours in the public works programs also occurs frequently.
- Transaction costs account for 15-20% of total losses due to the higher cost of making payments manually compared to electronic processing. The use of cash or checks increases the transaction cost for both the government and the beneficiary: for the government in transferring information between government offices, and for the beneficiary in the long distances to access the payment. The report estimates that for every 1 USD the government pays to a National Rural Employee Guarantee Scheme (NREGS) worker, it spends about 6 to 7 cents of lost wages and travel costs for the worker to redeem the benefit.
- Administrative and overhead costs account for 5-10% of total losses due to the manual processes used for auditing and payment reconciliation. For example, welfare budget planning can be cumbersome when the data to inform this analysis are maintained in manual records, making data aggregation and analysis costly and complex. The report also identifies and quantifies additional indirect benefits of rolling out an electronic payment solution in India, such as increased tax collection and better monitoring of suspicious monetary flows.
__
According to VISA study, the cost of cash places a huge burden on the Indian economy equivalent to 1.7% of GDP. This high cost of cash stems from large volumes of cash flow in the Indian economy relative to its peers across the globe. For example, in India, in 2015, the number of digital transactions per capita was only 10, compared to 163 in Brazil, 420 in South Korea and 429 in Sweden. By accelerating growth of Digital Payments, India has the opportunity to reduce its cost of cash from 1.7% of GDP to 1.3% of GDP delivering savings of INR 70,000 crores (USD 10.4 billion) in the next five years. If India could sustain a reduced cost of cash of 1.3% of GDP until 2025, India could save up to an additional INR 4 lakh crores (USD 59.4 billion) by FY 2024–25. In summary, the total savings by 2025 could be INR 4.7 lakh crores (about USD 70 billion) with the appropriate policy initiatives in place and followed by effective execution.
_
Electronic transactions can save healthcare $9.4 billion annually in the U.S.:
The U.S. healthcare system has lots of established electronic network connectivity between caregivers and insurance companies, but adoption of various types of electronic transactions remains very uneven, says a new study from the Council for Affordable Quality Healthcare. Each year out of total spending of about $3.20 trillion, the U.S. healthcare system spends as much as 14% of that money, or up to $448 billion, on administration, says the Center for Medicare and Medicaid Services. Greater use of web-based digital healthcare portals and other forms of electronic networking, such as electronic data interchange, could save the U.S. healthcare system as much as $9.4 billion annually, says the Council for Affordable Quality Healthcare, a Washington, D.C., healthcare research organization.
_
McKinsey projected that globally, digital finance could lead to a US$3.7 trillion GDP boost by 2025, create 95 million new jobs across all sectors, bring 1.6 billion new people into the formal financial system, and save US$110 billion annually in payment leakages in emerging countries. Digital finance could boost India’s gross domestic product (GDP) by $700 billion by 2025 and create 21 million new jobs across sectors, the McKinsey report said. The Indian digital payments industry is estimated to reach a size of $500 billion by 2020 and will contribute around 15% to the country’s gross domestic product (GDP), a survey conducted by Google and Boston Consulting Group revealed.
_
Digitizing Tax Payments can have dramatic Benefits for Emerging Economies:
Every year, an estimated US$7.7 trillion worth of payments flow from people to governments worldwide. Not surprisingly, taxes make up a significant portion of these payments. In 2015, a global agreement for financing the Sustainable Development Goals recognized domestic resource mobilization as essential to inclusive growth. This makes regular tax revenue more vital than ever to the future of many low-income countries. Yet, the reality is that countries who need revenue the most are only just starting to take advantage of all the opportunities available to them. There is growing evidence that enabling people and businesses to pay taxes digitally can increase government revenue and produce a wide range of other benefits for society. In Tanzania, our recent study found that the digitization of value-added tax payments could increase the country’s annual revenue by almost $500 million per year. The Ugandan city of Kampala has already experienced such success, boosting revenue by 167 percent in a single year after automating its tax collection system. Along with increasing overall tax revenue, digitizing individual and corporate tax payments can lower transaction costs for both the government and taxpayers. It reduces instances of fraud and corruption, increases government transparency, and improves the overall efficiency of a country’s tax system. For example, when Tanzania digitized national park fees it increased tourism sector revenues by a full 40 percent. Digitizing tax payments can help move people and businesses out of the shadow economy that flourishes in cash-heavy economies. Within one year of digitizing income and property tax payments by the Tanzania Revenue Authority, 15 percent of the tax base was making payments via mobile money, including payers who had no previous history of paying taxes. However, according to a new study by Karandaaz, a think tank in Pakistan, only 16 percent of low- and lower-middle-income countries receive tax payments predominantly in digital form. With the benefits so clear, why is the shift to digital so slow? Because digitizing an economy cannot happen overnight. It requires visionary leadership, a systematic collaboration across multiple government agencies and institutions, an investment in infrastructure, and the incentivizing of behavior change among citizens and merchants alike. Some countries are leading the way, however, and their lessons learned can inform others beginning on their own path toward the digitization of tax payments. There is widespread evidence that shifting to digital tax payments will reap significant financial and social dividends for countries. Every country now has the opportunity to create an economy where digital payments work well for everyone and are widely used.
______
_______
Legal and regulatory aspects of digital transaction:
_
Regulatory framework:
It should not come as a surprise that the electronic money payment system already has generated legislative interest, despite of its relative youth. At least in the European Union this interest has even gone as far as to the passing of a European directive on the subject, but for the moment it has been ignored by some others. The main regulatory tool in the European Union is the Directive 2000/46/EC on electronic money institutions, also known as the EMI.
_
Uniform Electronic Transactions Act:
The Uniform Electronic Transactions Act (UETA) is one of the several United States Uniform Acts proposed by the National Conference of Commissioners on Uniform State Laws (NCCUSL). Forty-seven states, the District of Columbia, Puerto Rico, and the U.S. Virgin Islands have adopted the UETA. Its purpose is to harmonize state laws concerning retention of paper records (especially checks) and the validity of electronic signatures. UETA does not attempt to create a whole new system of legal rules for the electronic marketplace. The objective of UETA is to make sure that transactions in the electronic marketplace are as enforceable as transactions memorialized on paper and with manual signatures, but without changing any of the substantive rules of law that apply. This is a very limited objective—that an electronic record of a transaction is the equivalent of a paper record, and that an electronic signature will be given the same legal effect, whatever that might be, as a manual signature. The basic rules in UETA serve this single purpose. The basic rules are in Section 7 of UETA. The most fundamental rule in Section 7 provides that a “record or signature may not be denied legal effect or enforceability solely because it is in electronic form.” The second most fundamental rule says that “a contract may not be denied legal effect or enforceability solely because an electronic record was used in its formation.” The third most fundamental rule states that any law that requires a writing will be satisfied by an electronic record. And the fourth basic rule provides that any signature requirement in the law will be met if there is an electronic signature. Almost all of the other rules in UETA serve the fundamental principles set out in Section 7, and tend to answer basic legal questions about the use of electronic records and signatures. Thus, Section 15 determines when information is legally sent or delivered in electronic form. It establishes when electronic delivery occurs—when an electronic record capable of retention by the recipient is legally sent and received. The traditional and statutory rules that govern mail delivery of the paper memorializing a transaction can’t be applied to electronic transactions. Electronic rules have to be devised., and UETA provides the rule. Another rule that supports the general validity of electronic records and signatures in transactions is the rule on attribution in Section 9. Electronic transactions are mostly faceless transactions between strangers. UETA states that a signature is attributable to a person if it is an act of that person, and that act may be shown in any manner. If a security procedure is used, its efficacy in establishing the attribution may be shown. In the faceless environment of electronic transactions, the obvious difficulties of identification and attribution must be overcome. UETA, Section 9 gives guidance in that endeavour. UETA is procedural, not substantive. It does not require anybody to use electronic transactions or to rely upon electronic records and signatures. It does not prohibit paper records and manual signatures. Basic rules of law, like the general and statutory law of contracts, continue to apply as they have always applied.
____
India lacks laws to protect customers of digital transactions:
The lack of basic privacy and security laws pertaining to digital payments in India puts the onus on consumers. India lacks laws to protect consumers if they lose money during digital transactions. There is no dedicated legal framework that embodies digital payment transaction in India. Presently, digital ecosystem is governed by cosmetic changes that was done in RBI Act for the regulation of payment systems in India and regulate and supervise these systems. Digital wallet payment is still a contractual payment between the two clients and it can always be repudiated. For fintech companies in India like Paytm, Mobilwik etc, security compliance falls under Section 43 A of the IT Act. There is a minimal data protection law in IT Act. But ISPs (internet service providers) and telcos still do not comply with Section 43 A. So compliance is still lower in the fintech sector. There has been 350 per cent rise in cases in cyber-crimes under IT Act 2000 between 2011 to 2014. From a legal prism, it is mandatory to address indemnity and liability, data security and other contractual obligations among the parties. Strong tripartite agreements (between e-wallet firm, gateway and customers) have to be frame worked. The second challenge is to bring robust changes in IT Act 2000. India through enacted the information technology act way back in 2000, but due to lack of amendments now the IT Act proves to be ineffective with growing digital payment traction. Only cosmetic changes amendments were being made in 2008. Even National Cyber Policy -2013 that postulated some important points needs to be implemented.
_____
_____
Digital skills (E-skills) and digital literacy:
_
_
The term “e-Skills” is defined as covering three main Information and Communication Technologies (ICTs) categories:
- ICT practitioner skills are the capabilities required for researching, developing, designing, strategic planning, managing, producing, consulting, marketing, selling, integrating, installing, administering, maintaining, supporting and servicing ICT systems.
- ICT user skills are the capabilities required for the effective application of ICT systems and devices by the individual. ICT users apply systems as tools in support of their own work. User skills cover the use of common software tools and of specialised tools supporting business functions within industry. At the general level, they cover “digital literacy”.
- e-Business skills correspond to the capabilities needed to exploit opportunities provided by ICT, notably the internet; to ensure more efficient and effective performance of different types of organisations; to explore possibilities for new ways of conducting business/administrative and organisational processes; and/or to establish new businesses.
__
Essential Student Digital Skills:
Do you consider digital skills necessary? Everyone else does. Other than the creators of fantasy novels and sci-fi movies, no one would have predicted fifty years ago how our lifestyles today would revolve around hand-held devices and the digital world. Technology has become so integrated in everyday life that we can hardly remember what the world looked like before our multi-device, constant-connectivity fantasy future became today’s reality. It’s expected that technology will become even more intuitive and ingrained in our daily life, and this leads to one important conclusion: the better equipped we are to handle this technological shift, the better our adjustment to it. Some digital skills are no-brainers; for example, today’s 5- and 6-year-old children know how to type and surf the web, a skill that adults might require a bit of studying and effort to fully master. Digital skills are part and parcel of higher education, and an important part of life for university students. Learning these key aspects of the 21st-century technology that surrounds us can only benefit students in their pursuit of knowledge. Online banking is gradually becoming mainstream. People that used to be sceptical about the safety of online transactions are now more likely to purchase goods and services online, check their bank accounts and transfer money or pay bills. The convenience, security and sheer effectiveness of online banking requires basic awareness of how online banking apps and other software work. Being aware of basic online banking functions ensures your finance is handled effectively and securely.
_
Digital literacy:
Cornell University defines digital literacy as ‘the ability to find, evaluate, utilize, share, and create content using information technologies and the Internet’. By this definition, digital skills are any skills related to being digitally literate. Digital literacy is the knowledge, skills, and behaviors used in a broad range of digital devices such as smartphones, tablets, laptops and desktop PCs, all of which are seen as a network rather than computing devices. Digital literacy initially focused on digital skills and stand-alone computers, but the focus has shifted from stand-alone to network devices. Digital literacy is distinct from computer literacy. Computer literacy preceded digital literacy. Computer literacy refers to knowledge and skills in using traditional computers, such as desktop PCs and laptops. Computer literacy focuses on practical skills in using software application packages. Digital skills is a more contemporary term and are limited to practical abilities in using digital devices, such as laptops and smartphones. A digitally literate individual will possess a range of digital skills, knowledge of the basic principles of computing devices, and skills in using computer networks. The individual has the ability to engage in online communities and social networks while adhering to behavioral protocols. The individual is able to find, capture, and evaluate information. Digital literacy requires the individual to understand the societal issues raised by digital technologies and possess critical thinking skills. These skills can be possessed through digital experiences that pushes individuals to think in a variety of ways through a multitude of media platforms. The evolution of digital media has quickly integrated into literacy.
_
Difference between Digital Skills and Digital Literacies:
We often hear people talk about the importance of digital knowledge for 21st-century learners. Unfortunately, many focus on skills rather than literacies. Digital skills focus on what and how. Digital literacy focuses on why, when, who, and for whom. For example, teaching digital skills would include showing students how to download images from the Internet and insert them into PowerPoint slides or webpages. Digital literacy would focus on helping students choose appropriate images, recognize copyright licensing, and cite or get permissions, in addition to reminding students to use alternative text for images to support those with visual disabilities. Digital skills would focus on which tool to use (e.g., Twitter) and how to use it (e.g., how to tweet, retweet, use TweetDeck), while digital literacy would include in-depth questions: When would you use Twitter instead of a more private forum? Why would you use it for advocacy? Who puts themselves at risk when they do so?
__
School curriculum:
Every child should have the opportunity to learn. Every child should be expected to be ‘digitally literate’ by the end of compulsory education, in the same way that every child is expected to be able to read and write. Every child should have the opportunity to learn concepts and principles from Computing (including Computer Science and Information Technology) from the beginning of primary education onwards, and by age 14 should be able to choose to study towards a recognised qualification in these areas. Pupils should be exposed to, and should have the option to take further, topics such as: understanding of the internet and the design of web-based systems; the application of computers in society, business, the arts, science and engineering; computer programming, data organisation and the design of computers; and the underlying principles of computing.
__
Computer educations in schools to promote digital transactions:
Information and Communications Technology (ICT) is instrumental in conducting human affairs globally. Early access to ICT has greatly benefitted developed countries; enriching their teaching and learning processes. Computer related technologies have improved educational quality, and increased access to educational resources. In developing countries they have enhanced equality in education. In the globalised world, technology has become the in-thing as countries and/or organisations devise means of gaining a competitive edge over the others. In view of this, education systems in individual countries need to be tailor-made to suit this endeavour. Information and Communication Technology (ICT) has played a major role in linking business and individuals far apart in terms of geographical distance. Digital Transactions are being carried out in or outside offices, twenty-four hours a day. In pursuit of the objectives to ensure that the country advances its technology base, all nations should introduce computer education in the school curriculum. Computer education in all schools may be introduced as a compulsory subject in high schools.
_______
Manual dexterity:
Manual dexterity is the ability to make coordinated hand and finger movements to grasp and manipulate objects. Manual dexterity includes muscular, skeletal, and neurological functions to produce small, precise movements. Development of these skills occurs over time, primarily during childhood. Fine motor skill (or dexterity) is the coordination of small muscles, in movements—usually involving the synchronization of hands and fingers—with the eyes. The complex levels of manual dexterity that humans exhibit can be attributed to and demonstrated in tasks controlled by the nervous system. Fine motor skills aid in the growth of intelligence and develop continuously throughout the stages of human development. Fine motor skills can become impaired. Difficulties with manual dexterity may be affected by a variety of conditions. Some reasons for impairment could be injury, illness, stroke, senility, congenital deformities, cerebral palsy, and developmental disabilities. Problems with the brain, spinal cord, peripheral nerves, muscles, or joints can also have an effect on fine motor skills, and decrease control. People with poor manual dexterity have great difficulty in carrying out digital transactions due to incoordination of hands and finger with the eyes.
_
Digital natives and digital immigrants:
Marc Prensky invented and popularized the terms digital natives and digital immigrants. A digital native, according to Marc Prensky, is an individual born into the digital age. A digital immigrant refers to an individual who adopts technology later in life. These terms aid in understanding the issues of teaching digital literacy, however, simply being a digital native does not make one digitally literate. Statistics and popular representations of the elderly portray them as digital immigrants. For example, Canada in 2010 found that 29% of its citizens 75 years of age and older, and 60% of its citizens between the ages of 65-74 had browsed the internet in the past month. Conversely, internet activity reached almost 100% among its 15 through 24-year-old citizens. Eugene Loos identifies the most common assumptions about digital technologies and the elderly, all of which contribute to portray them as digital immigrants and to perpetuate digital ageism. Senior citizens may be regarded as a homogenous group, however, this group does not want or is not able to make use of digital information sources. Eugene Loos claims this is not a problem because as time passes, these generations will be succeeded by new generations that have no problem at all with digital technologies.
_
Elderly population have triple whammy:
- Their digital skill and literacy are poor as they are digital immigrants.
- Their manual dexterity is poor as they have poor muscle coordination, poor vision, tremors and brain atrophy.
- Their reduced memory would make remembering passwords very difficult.
Elderly population have to be provided alternative to digital transactions.
_______
_______
The figure below shows synopsis of ‘digital needs’ for digital transactions:
_______
_______
Digital divide and digital dividend:
What is the digital divide?
As used here, the term “digital divide” refers to the gap between individuals, households, businesses and geographic areas at different socio-economic levels with regard both to their opportunities to access information and communication technologies (ICTs) and to their use of the Internet for a wide variety of activities. The digital divide reflects various differences among and within countries.
_
In its annual World Development Report (WDR) the World Bank appeared to strike a balance between outlining the positive outcomes from a deepening digital economy in countries such as India, and the fact that automation of jobs was in some cases leading to inequalities in the labour market between high-skill and low-skill workers. The 2016 WDR issue titled “Digital Dividends,” noted that almost 1.063 billion Indians were offline even though India ranked among the top five nations in terms of the total number of Internet users, along with China, the U.S., Japan and Brazil. With 60 per cent of the world’s population still offline, institutional and regulatory barriers to efficiency are exacerbating the problem of low and unevenly distributed “digital dividends” from growing Internet penetration across countries, this World Bank study has found.
_
76% of Indians not on internet:
At a time when Indian government is aiming to convert India into a digital economy, a study said nearly a billion Indians do not have an internet connection. Though mobile data plans in India are among the cheapest in the world, yet 950 million people out of a population of 1.25 billion do not have access to the internet. Only 34.8% of the total population uses the internet in the country. In 2015, online payment accounted for 14% of the total transactions mainly due to e-commerce websites. 80% of the employment is mainly in unorganised sectors. India is a country of $1.8 trillion GDP and 20% of it, and 80% of the employment is mainly in unorganised sectors without bank accounts or any other mean of transaction apart from cash transactions. In fact, half the population of India do not own bank accounts making electronic payment an alien concept for many.
____
While digital technologies have been spreading, digital dividends have not. Why? For two reasons. First, nearly 60 percent of the world’s people are still offline and can’t participate in the digital economy in any meaningful way. Second, some of the perceived benefits of digital technologies are offset by emerging risks. Many advanced economies face increasingly polarized labor markets and rising inequality—in part because technology augments higher skills while replacing routine jobs, forcing many workers to compete for low-paying jobs. Public sector investments in digital technologies, in the absence of accountable institutions, amplify the voice of elites, which can result in policy capture and greater state control. And because the economics of the internet favor natural monopolies, the absence of a competitive business environment can result in more concentrated markets, benefiting incumbent firms. Not surprisingly, the better educated, well connected, and more capable have received most of the benefits—circumscribing the gains from the digital revolution. Digital technologies have spread rapidly in much of the world. Digital dividends—that is, the broader development benefits from using these technologies—have lagged behind. In many instances, digital technologies have boosted growth, expanded opportunities, and improved service delivery. Yet their aggregate impact has fallen short and is unevenly distributed. For digital technologies to benefit everyone everywhere requires closing the remaining digital divide, especially in internet access. But greater digital adoption will not be enough. To get the most out of the digital revolution, countries also need to work on the “analog complements”—by strengthening regulations that ensure competition among businesses, by adapting workers’ skills to the demands of the new economy, and by ensuring that institutions are accountable.
_____
The figure below shows synopsis of how digital dividends can be spread rapidly:
____
To maximize the digital dividends requires better understanding of how technology interacts with other factors that are important for development—the “analog complements.” Digital technologies can make routine, transaction-intensive tasks dramatically cheaper, faster, and more convenient. But most tasks also have an aspect that cannot be automated and that requires human judgment, intuition, and discretion. When technology is applied to automate tasks without matching improvements in the complements, it can fail to bring broad-based gains. The digital revolution can give rise to new business models that would benefit consumers, but not when incumbents control market entry. Technology can make workers more productive, but not when they lack the know-how to use it. Digital technologies can help monitor teacher attendance and improve learning outcomes, but not when the education system lacks accountability. What should countries do? Making the internet universally accessible and affordable should be a global priority. The internet, in a broad sense, has grown quickly, but it is by no means universal. For every person connected to high-speed broadband, five are not. Worldwide, some 4 billion people do not have any internet access, nearly 2 billion do not use a mobile phone, and almost half a billion live outside areas with a mobile signal. The unfinished task of connecting everyone to the internet—one of the targets in the recently approved Sustainable Development Goals (SDGs)—can be achieved through a judicious mix of market competition, public-private partnerships, and effective regulation of the internet and telecom sector. Access to the internet is critical, but not sufficient. The digital economy also requires a strong analog foundation, consisting of regulations that create a vibrant business climate and let firms leverage digital technologies to compete and innovate; skills that allow workers, entrepreneurs, and public servants to seize opportunities in the digital world; and accountable institutions that use the internet to empower citizens. The long-term development impact is by no means definitive, being continuously shaped by the evolution of technology (connectivity) and the country’s choice of economic, social, and governance arrangements (complements). Countries that are able to swiftly adjust to this evolving digital economy will reap the greatest digital dividends, while the rest are likely to fall behind. The triple complements—a favorable business climate, strong human capital, and good governance— will sound familiar—and they should because they are the foundation of economic development. But digital technologies add two important dimensions. First, they raise the opportunity cost of not undertaking the necessary reforms. They amplify the impact of good (and bad) policies, so any failure to reform means falling farther behind those who do reform. With digital technologies, the stakes have risen for developing countries, which have more to gain than high-income countries, but also more to lose. Second, while digital technologies are no shortcut to development, they can be an enabler and perhaps an accelerator by raising the quality of the complements. Online business registries ease market entry for new and innovative fi rms. Well-designed internet-based training helps workers upgrade their skills. New media platforms can increase citizen participation.
_
Over-performers and underperformers:
Though ICT has promoted development across various dimensions of society from connecting individuals to spreading across businesses, and governments, there exists a digital divide in its accessibility between the high income and low income countries, with high income countries typically showing greater penetration of digital technology as compared to less developed countries. While in high income countries such as Finland, Norway, Denmark, Netherlands and Sweden, over 90 per cent of the population is using the Internet, in lower income countries such as Afghanistan, Sub-Saharan African countries such as Central African Republic, Ethiopia, Tanzania, and Malawi, less than 10 per cent of the population uses it. Similarly, with regard to the extent of mobile penetration, Sub-Saharan Africa has the lowest mobile penetration of 73 per cent, compared to 98 per cent penetration in high income countries (World Development Report 2016). Given a high degree of correlation between the economic progress of a country and its access to ICT, there are countries which have over-performed relative to their economic peers in providing digital technology. One such country worth mentioning here is Costa Rica, which is the world’s top over-performer, known for its communication technology and also press freedom. Similarly, there are countries which have underperformed among their income peers on access to information and communication. For instance, Cuba, which has the lowest number of mobile phone subscriptions and lowest press freedom index, has been the most underperforming country on access to information and communication. Further, two of the world’s most populated countries — India and China — are also among the few underperformers on access to ICT. India, which has been appreciated globally for providing IT services, faces a huge digital divide, having a relatively low percentage of population with access to the Internet. In 2016, it had only about 34 people per 100 using the Internet. China on the other hand has a very weak press freedom index, resulting in its overall low performance on access to ICT. Apart from the digital divide existing between countries, there also exists a gap in adoption of digital technology across different demographic groups within the country. The World Development Report 2016 highlights such differences in accessibility to the Internet in Africa, where gaps arise out of differences in factors such as income, location, gender and age. For instance, greater access to the Internet is seen in the top 60 per cent of the population based on income distribution compared to the bottom 40 per cent. Further, women use less digital technology compared to men, and gaps are even greater between the youth (20 per cent) and the matured population (8 per cent).
_______
The figure below shows digital pathway to financial inclusions:
_______
Digital transaction for poor people:
Digital transactions can contribute significantly to achieving the goal of full financial inclusion, but there is much work left to be done. Mobile technologies make it possible to provide the very poor and the most remote clients with financial services at an appropriate price. So far, though, we do not have breakthroughs in asset-building financial services that match the rapid growth of payment services. To do that, we will need to go far beyond using mobile technologies for processing payments. Rather, we will need to use this technology to re-engineer financial services for the poorest so that we can provide more relevant services at lower costs – services that are informed by a much better understanding of clients’ cash flows, needs, aspiration, and preferences. M-PESA, a mobile payment system started in 2003 and provided in Kenya and other African countries by Safaricom, now reaches over 70% of Kenyan households.
_
_
Highlights from studies on M-PESA:
- 50% of M-PESA users are unbanked and 41% live in rural areas
- users primarily transfer money from urban areas to family members in rural areas
- average daily balance of median respondent was about $3.70
- almost 70% of the money going into an account leaves that account before any new money is put in
- in 88% of cases, the e-money is cleared out of the account on the same day it is received
- M-PESA played an important role in helping clients manage financial emergencies, such as hospital bills
- more than 75 financial institutions in Kenya now work with Safaricom to provide mobile banking to their customers
- customers have found banking services linked to M-PESA difficult to use, filled with processing delays, and errors.
- getting the banks’ software systems to interface with Safaricom’s in a way that ensures that payments are deposited quickly to the correct account has proved to be an ongoing challenge
_______
_______
Mixing payment with pleasure (social shopping):
Shoppers embrace the Internet for a variety of reasons — convenience, price, selection — and over the last few years, one of the major developments in the e-commerce arena is social shopping. Social shopping refers to the use of virtual social networks, peer reviews and other online social tools in the purchasing process. Today’s consumer is heavily influenced by the choices of his or her peers, which is further reflected in the way brands are using social media to capture attention. Social shopping is the combination of social media and e-commerce. In essence, it is taking all of the key aspects of the social web — friends, groups, voting, comments, discussions — and focusing them on the world’s favorite activity — shopping — to create social shopping. Social shopping beats old-fashioned web shopping because it brings all types of products into one place. No more skipping around from site to site searching for that hard-to-find item. Social shopping also has advantages even over going to an actual store to shop. With social shopping, you are one click away from comparing prices, and you can easily find out what other people are saying about that Fossil watch or that Alexis Bittar necklace. Best of all, it’s fun. If you like shopping, then you will love social shopping. With each emerging technology or social media channel, retailers are on a never-ending quest to turn viewers into consumers. This is shifting how we shop and interact with retail businesses. Facebook, Twitter and Pinterest all have their shopping tools to drive digital transactions. The bigger issue is that shopping and social media are arguably two of the most appealing aspects of the internet; do we really want to mix payment with pleasure? If retailers meet our demand, the answer is yes. Facebook has been a primary vehicle for brands in not only the promotion of products but also in online transactions. One of the reasons is that Facebook allows consumers to share and talk about the products and services they like, which influences the purchasing decisions of their virtual friends. According to a report from Sociable Labs, 62 percent of online shoppers have read product-related comments from their Facebook friends, 75 percent of them have clicked on the product link to visit the retailer’s site, and 53 percent of those who clicked go even further and buy the product. Twitter is another social media tool in which brands are using to engage customers and encourage purchases, and it’s evident from the numbers that Twitter users don’t mind being pursued by brands — according to a study by Social Media Quickstarter, 64 percent of Twitter users surveyed claimed to follow brands in order to receive exclusive product promotions and discounts.
_______
_______
Money Laundering in Digital Currencies:
Digital currencies allow account holders to electronically manipulate funds similarly to other types of funds transfer services. Digital currency account holders can move funds internationally in a manner that approximates money transfers or traditional wire transfers. The ability to conduct transactions in digital currencies is constantly available, making digital currencies more convenient than other methods of funds transfer, which may be limited by normal business hours and international time zones. Additionally, digital currency transactions can be conducted from any location or device with Internet access. Some issuers also accommodate mobile payments through web-enabled phones. Digital currencies are generally easy to use, and transactions conducted in these currencies are instantaneous and irreversible. Because most digital currencies are denominated into internationally recognized weights of precious metals, inconveniences traditionally associated with international financial transactions, such as calculating international exchange rates for another nation’s currency, are eliminated. A digital currency account can function as a merchant account, allowing a digital currency account holder to function as a front or shell company. Data Communications Equipment (DCEs) that are automated allow individuals to execute multiple currency-to-currency exchanges in a short period of time and can be exploited to provide an ideal layering mechanism for funds placed into a digital currency account. Anonymity is a heavily marketed characteristic of the digital currency industry. Because digital currency accounts are obtained online and are not subject to the customer identification procedures associated with obtaining a traditional bank account, they often can be opened and funded anonymously. Many digital currency web sites advertise “full anonymity” for transactions. Some issuers require identification, but because users open digital currency accounts online, documents are generally faxed or scanned to the issuer and can be easily altered or falsified. Anonymity continues during the digital currency account funding process, again without face-to-face interaction. Individuals can fund digital currency accounts by making cash deposits directly to an exchanger’s bank account. Many DCEs maintain bank accounts in several countries to facilitate cash deposits in various national currencies. Industrywide, exchangers also accept wire transfers, postal money orders, and a variety of other payment types, some of which may make it difficult to determine the source of funds. Illicit users further attempt to conceal their identities by continually opening new digital currency accounts, as often as after each transaction. Digital currency accounts can also be funded with varying degrees of anonymity by mail and over the Internet, using electronic money orders (EMOs), checks, and online banking transfers. Some issuers allow individuals to redeem digital currency account balances in actual precious metals; launderers looking to conduct business in precious metals could exploit digital currencies to acquire them without the paper trail created by the commodities market. Many exchangers will convert digital currency balances into anonymous prepaid (stored value) cards that can be used to withdraw funds by various methods, including at worldwide automated teller machines (ATMs). Digital currencies also may be withdrawn through worldwide wire transfers, mailing third-party checks to anyone whom the account holder designates, or a variety of other methods. Various technologies can increase the utility of digital currencies for money laundering by providing additional anonymity and networking abilities. Because digital currency transactions are conducted over the Internet, they can be traced back to individuals’ computers; however, anonymizing proxy servers and anonymity networks protect individuals’ identities by obscuring the unique IP (Internet Protocol) address as well as the individuals’ true locations. Furthermore, mobile payments conducted from anonymous prepaid cellular devices, such as web-enabled phones, may be impossible to trace to an individual. Such portable devices that provide Internet access enable transfers of digital currency; afterward, they can be destroyed, easily and inexpensively, to prevent forensic analysis. Digital currency account holders also may use public Internet terminals or even “hijacked” wireless Internet connections to access their digital currency accounts, causing transactions to appear to originate with the unsuspecting Internet subscriber. Users of digital currency may also use encrypted chat rooms to conceal communications between individuals, making law enforcement scrutiny more difficult. Because digital currency is increasingly misused to purchase drugs and other illicit materials that are sold online, the proceeds of that activity are essentially prelaundered. Payment in digital currencies makes it easier for traffickers to launder funds that no longer need to be placed into the traditional financial system. Payment can be immediately forwarded to an international digital currency account, perhaps in payment to the original source of supply, or further layered through multiple digital currency accounts and exchangers until reintegrated into the legitimate economy. Online illicit drug sales are now being conducted on bulletin boards, on blogs, and in encrypted chat rooms, and sellers are increasingly demanding payment in digital currencies. Some digital currency issuers offer liberal–or even no–limits on transactions, funding amounts, and total account balances, allowing drug traffickers to more easily launder large sums with fewer transactions. Digital currency issuers who impose no limits on total value, funding, and transactions are ideal for large-scale drug trafficking networks and money laundering operations; such financial services make it easier and safer to launder larger amounts of money using fewer transactions. Federal officials have acknowledged the need to close the regulatory loophole that exists in relation to digital currencies. Despite industry assertions that digital currencies are not subject to regulation, as well as the formation of several trade associations and consortiums attempting to demonstrate industry self-regulation, U.S. Government entities are exploring the application of consistent federal regulation over the digital currency industry–which promotes itself as unregulated and anonymous. Additionally, because the value of digital currency accounts changes with the market performance of the backing commodity, any profits earned (capital gains) during the withdrawal of digital currency accounts may not get reported to the IRS unless the digital currency account holder decides to declare the amount voluntarily.
________
________
Cashless society:
A cashless society describes an economic state whereby financial transactions are not conducted with money in the form of physical notes or coins and where value can be exchanged via the transfer of information between transacting parties. Cashless societies have existed, based on barter and other methods of exchange, and cashless transactions have also become possible using digital currencies such as Bitcoin. However here I focuses on the term “cashless society” in the sense of a move towards, and implications of, a society where cash is replaced by its digital equivalent – in other words, legal tender (money) exists, is recorded, and is exchanged only in electronic digital form. A new study out of Sweden says the tiny country is on course to become the world’s first “cashless society,” thanks in part to a mobile payment app called Swish. Researchers said there are about 80 billion Swedish crowns in regular circulation, down from 106 billion six years ago. And out of that amount, only somewhere between 40 and 60 percent is actually in regular circulation. … The use of cash is small, and it is decreasing rapidly. Swish has more than 3.5 million users (of Sweden’s total population of 9.5 million) and nearly 4.5 billion Swedish crowns were “Swished” in 2016. In Sweden, only 3 percent of transactions are made with cash.
_
There are certainly positive outcomes that can be obtained by going cashless. For example, banning sale transactions of cigarettes or sugary drinks or stopping cardholders from overeating, gambling, or whatever other vice is targeted, could lead to a decrease in these vices and their associated problems. A decrease in those problems could positively impact other areas, like, for example, our nation’s health-care system. A cashless society would probably also mean less street crime. Yet in return for these benefits, there is an incalculable cost to our humanity. We would lose our freedom to make decisions. It is easy to imagine a totalitarian regime using these tools to great harm. Given various government policies, it is also very easy to imagine even a liberal government can be tempted to use the confluence of these technologies. And once used, because they are very powerful, even liberal governments will be enticed into using them until there is pretty complete monitoring and control of every transaction. A cashless society would certainly give governments unprecedented access to information and power over citizens. Currently, we have little evidence to indicate that governments will refrain from using this power. On the contrary, the U.S. government is already using its snooping prowess and big-data manipulation in some frightening ways. While helpful to the global economy and to the fight against crime and terrorism, many concerns have been raised over “dangerous” unintended consequences. It would mean that negative interest rates can be fully enforced, and money could be controlled in great detail. For example, some kinds of money might be set to “expire” and be worthless if not spent in specific ways or by specific times, or to devalue gradually. It also makes individual savings, and information about individual incomes and transactions, accessible to any party able to access the records – either legitimately (police and tax related) or not (hackers and persons with access to the relevant data), and in this way, it facilitates population surveillance. It also means that groups, individuals and causes could be deprived of cash by the simple expedient of preventing their access to cashless transaction media.
___
The Sinister Side of Cash in the US:
Paper money fuels corruption, terrorism, tax evasion and illegal immigration. There is little debate among law-enforcement agencies that paper currency, especially large notes such as the U.S. $100 bill, facilitates crime: racketeering, extortion, money laundering, drug and human trafficking, the corruption of public officials, not to mention terrorism. There are substitutes for cash—cryptocurrencies, uncut diamonds, gold coins, prepaid cards—but for many kinds of criminal transactions, cash is still king. It delivers absolute anonymity, portability, liquidity and near-universal acceptance. It is no accident that whenever there is a big-time drug bust, the authorities typically find wads of cash. Cash is also deeply implicated in tax evasion, which costs the federal government some $500 billion a year in revenue. According to the Internal Revenue Service, a lot of the action is concentrated in small cash-intensive businesses, where it is difficult to verify sales and the self-reporting of income. By contrast, businesses that take payments mostly by check, bank card or electronic transfer know that it is much easier for tax authorities to catch them dissembling. Though the data are much thinner for state and local governments, they too surely lose big-time from tax evasion, perhaps as much as $200 billion a year. Obviously, scaling back cash is not going to change human nature, and there are other ways to dodge taxes and run illegal businesses. But there can be no doubt that flooding the underground economy with paper currency encourages illicit behavior. Cash also lies at the core of the illegal immigration problem in the U.S. If American employers couldn’t so easily pay illegal workers off the books in cash, the lure of jobs would abate, and the flow of illegal immigrants would shrink drastically. Needless to say, phasing out most cash would be a far more humane and sensible way of discouraging illegal immigration than constructing a giant wall.
_
Benefits of Cashless economy
- Convenience: A cashless system could be convenient for users who like to combine multiple functions onto one handheld device: It eliminates the need to carry cash or plastic. Digital payments can be made with a tap or wave of a smartphone, depending on the technology used. It would make it easier to loan or borrow money – as with digital payments, lending and borrowing can be reduced to a tap or wave of a smartphone.
- Security: The technology being used to usher in a cashless age has the potential to offer security benefits to its users: It’s very easy to shut down a digital wallet remotely if it falls into the wrong hands. Your biometric ID is yours and yours alone, and therefore very hard to copy.
- One benefit of digitized currencies is their relative cost effectiveness in comparison to cash, which is expensive to produce, maintain and handle. There would be fewer cash management requirements, adding to the cost savings. There is a tremendous amount of money spent by financial institutions today to secure, count, and manage physical money. These costs are mandated because a certain amount of physical cash must be kept on hand to for people to have their needs met.
- Reduced instances of tax avoidance because it is financial institutions based economy where transaction trails are left.
- It will curb generation of black money
- Will reduce real estate prices because of curbs on black money as most of black money is invested in Real estate prices which inflates the prices of Real estate markets
- It will pave way for universal availability of banking services to all as no physical infrastructure is needed other than digital.
- There will be greater efficiency in welfare programmes as money is wired directly into the accounts of recipients. Thus once money is transferred directly into a beneficiary’s bank account, the entire process becomes transparent. Payments can be easily traced and collected, and corruption will automatically drop, so people will no longer have to pay to collect what is rightfully theirs.
- There will be efficiency gains as transaction costs across the economy should also come down.
- Counterfeit notes have negative impact on economy, by going cashless, that can be avoided.
- Hygiene – Soiled, tobacco stained notes full of germs are a norm in India. There are many such incidents in our life where we knowingly or unknowingly give and take germs in the form of rupee notes. This could be avoided if we move towards cashless economy.
- Reduced costs of operating ATMs.
- Speed and satisfaction of operations for customers, no delays and queues, no interactions with bank staff required.
- A Moody’s report pegged the impact of electronic transactions to 0.8% increase in GDP for emerging markets and 0.3% increase for developed markets because of increased velocity of money. A McKinsey survey concluded that digitizing the US currency would increase the nation’s GDP by almost 0.5%. Cashless society force people to convert their savings into consumption and/or investment, thereby providing a boost to GDP and employment.
- It could reduce criminal activities.
- Because a cashless society would require every transaction to leave an electronic “fingerprint” of it somewhere, it would become easier to track illegal transactions and catch those conducting them.
_______
Disadvantages cashless society/economy:
- Privacy compromised:
Governments and their agencies love electronic transactions. Without cash, it’s much harder to hide money from the tax man. The police and government agencies like the NSA love the trackable records that cashless payments leave behind. Last year, France and Spain both enacted laws that limit cash transactions. In France it is now illegal to use cash for anything more than 1,000 euros (around $1,080). In Germany, economist Peter Bofinger supports a ban on cash, calling it an anachronism. “The markets for undeclared work and drugs could be dried out,” writes Germany’s Der Spiegel, “and central banks would find it easier to enforce their monetary policies.” When all our payment transactions are tracked, it creates a trove of data we have no control over. It’s easy to imagine a daring divorce lawyer or a government agent trying to gain access to our financial history to try to build a story about who we are. The rich may be better equipped to buy themselves privacy whether that’s setting up corporate entities for their transactions or making political donations through PACs. However, for the average person trying to use a traditional bank account to process a payment online, there’s no anonymity.
- It will marginalize elderly people and poor people who are used to paying for things in cash, and are deeply suspicious (with good reason) of electronic payment systems.
- It will encourage people to spend frivolously, since paying for things on one’s smart phone is fast and easy. This will likely contribute to debt problems, gambling problems, and all sorts of irresponsible behavior. A student interviewed at the University of Gothenberg admitted that if she had a 500 krona note, she would think twice about spending it; electronic payment brought little to no psychological hesitation.
- Holding physical currency (paper money or coin) doesn’t really cost the holder anything besides inflation. But digital currency in banks can get eroded very, very easily with fees, charges, and all the other games that banks like to play.
- Are banks really willing and capable of handling all the millions and millions of tiny transactions that would happen every day? It’s difficult to see how the average bank is going to be competent enough to handle all these transactions efficiently. They are going to charge everyone sooner or later.
- Digital currency would be vulnerable to disruption by fraud or terrorist attacks. A stolen £20 note carries no personal information, whereas breaches of digital accounts not only provide access to funds but also a host of personal details. Losing physical cash is annoying, but losing identity information could be devastating; whole accounts wiped and details used to open fraudulent bank accounts and to apply for credit. Sweden provides a good example of the crime problems faced in an almost cashless economy – in the past 10 years card fraud cases have doubled, and between 2000 and 2011 instances of digital monetary fraud increased six fold. Practically no digital server is incorruptible or immune to hacking, and it would be worryingly naive to think the reduction of physical financial crime would necessarily outweigh the dangers of digital crime. The risks associated with electronic payment instruments are far more diverse and severe. Losing your credit cards or being the victim of digital hackers can lead to a whole host of problems including denied payment, card theft, card skimming, identity theft, account takeover, fraudulent transactions and data breaches. According to the digital security company Gemalto, more than 1 billion personal records were compromised in 2014.
- The government and big business are working hand in hand to see that this dream becomes a reality. What is the real reason it is being pushed? It all comes down to power, control, and profits: that is, the government wants more power, and big business wants to make more money.
- The elderly and the non-digital savvy have to get support from family, friends and professionals to show them how to use contactless payment and what to do with their money when it’s not in a cash format.
- Poor and homeless are at great disadvantage:
For poorer people, cashless transactions just aren’t practical. There are many people who are unbanked and cannot receive lines of credit for a whole range of reasons. A ban on cash would particularly impact the unbanked community. The cost of cash is higher for poor and unbanked people than for other groups. Poor who lack access to formal financial institutions carry larger amounts in cash and pay the most fees in aggregate terms for cash access transactions.
A cashless society could be a nightmare for the homeless:
For people who are homeless, there are more fundamental problems about proof of status. Having no fixed abode renders getting credit facilities impossible, and managing a bank account incredibly difficult. It’s not like people who are homeless are going to start accepting Bitcoin from passing strangers. And while a lack of cash doesn’t make you homeless, it has the potential to keep you on the streets. As David Fisher of the charity St Mungo’s Broadway puts it: “If we’re heading for a cashless society, how do we ensure that people on the margins of society are able to live, work and have good relationships within that kind of society?” But charities such as St Mungo’s are doing a good job of securing the kind of documentation many of us take for granted. Passports, utility bills, national insurance numbers and payslips can all be hard to get hold of. “We work with our clients where we can to access mainstream banks and banking technology, including debit and credit cards,” says Fisher. “Without a permanent address it can be difficult to maintain a bank account and other everyday services like phone contracts.”
- Personal cash theft is a relatively minor problem for American consumers, who lose less than $500 million through such crimes, but pay close to $8 billion dollars in fees for ATM transactions outside of their account-holding bank’s network. This is an interesting contrast to the high costs that businesses bear from cash theft.
- If the technology quits, you can’t pay:
Many of the proposals for a cashless society involve digital payments from a phone. What happens if that phone runs out of its battery? A person suddenly loses all access to their money. They wouldn’t be able to pay for anything unless they could find the charger for their phone. In remote areas, that may not be feasible to implement. Also, network connectivity issues must be resolved before dreaming about a cashless society.
- New fees could be added to raise costs:
Handling paper cash has virtually no cost to it at all. Debit cards have a low processing fee, but credit cards have a certain percentage that must be paid on each transaction. That’s another way that rewards are funded: through the pockets of businesses. Retailers and service providers increase their costs to compensate for these fees. A cashless society would have a different type of processing infrastructure and that would undoubtedly have an associated cost.
- The government loses an important alternative to pay for its debts, namely by printing true-to-the-letter paper money. This is why Greece may have to leave the euro, since its inability or unwillingness to adopt more austerity measures, a precondition to secure more euro loans, will force it to print drachma bills to pay for its debts.
_______
Perils of cashless society:
- A fully cashless society would mean the end of privacy. There would be a digital trail of every action you take through your purchases and transfers. If you buy AIDS medication or a porn magazine or book a hotel room for a romantic alliance, this information can be accessed by the government — or any hacker with the requisite skills — and used against you.
- A fully cashless society could mean the end of dissent. The government can use any data it gathers against you. (Even if you commit no crime, there is much you may be embarrassed by.) What’s more, they could make any opponent a pauper with one keystroke, freezing your bank account while they investigate alleged misdeeds. Just the fact that they have this power could have a chilling effect on dissent. Those in government now may well salivate over this, but tables turn fast, and when they are in opposition, would they want their opponents to have such power over them?
- A fully cashless society endangers freedom. Cash is empowerment: ask the young wife who saves spare cash from her alcoholic husband; or the old mother who stuffs spare notes under her mattress for years because it gives her a sense of autonomy. Indeed, in a misogynist country like India, cashlessness would hit women the hardest.
- You do not need to be in possession of aggressively Libertarian views to recognize that a cashless society requires the relinquishing of freedom. A cashless society could be almost Orwellian with regard to the control a government would possess over its population. In Denmark a central bank is responsible for all current accounts, with any international bank branches drawing funds from this central bank rather than individual depositors. Whilst in stable, democratic nations it is hard to imagine a situation where this control is leveraged by the government to manipulate the population, such as limiting access to funds in the face of strikes; in corrupt and dictatorial regimes, ultimate governmental control over access to funds could be especially dangerous – whole currencies could be invalidated, payments declined, funds frozen. An electricity outage, either deliberate or unavoidable, could immobilize the funds of a whole population.
- Most importantly, there is the matter of privacy and the threat to our liberties posed by a cashless society. That’s a topic that proponents of a cashless society are loath to examine. Maybe I have a legitimate reason for not wanting an electronic record of all of my transactions. Maybe my reason is not legitimate. It doesn’t matter. I have the right to live my life free from government surveillance. That right is guaranteed under the Fourth Amendment in American constitution: The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated. “Papers, and effects” includes currency – and government has no right to force an accounting of those “effects” by eliminating a practical means of cash transactions. Even Indian constitution gives right to possess lawful movable property and cash is a type of movable property.
- Large numbers of banknotes are hard to transport, conceal and use without detection. Cash seizure is a prominent law enforcement tool and one that can hit criminals hard. Indeed, if you are a serious criminal, you avoid using cash. You’d rather hide your money in an offshore bank account than store large numbers of banknotes. But the benefits of currency for national security aren’t limited to law enforcement. Cash has repeatedly demonstrated its importance in times of crisis. When natural disasters knock out an electrical grid for days or even weeks, cash is a saving grace for residents to obtain critical supplies. During the global financial crisis following the collapse of Lehman Brothers in 2008, cash became a safe haven for consumers looking to keep their assets intact. Indeed, the volume of cash in circulation increased dramatically in 2008. In one example, Australia’s Reserve Bank saw a 12 percent rise in demand for its currency in late 2008 thanks to an increase in precautionary holdings in response to financial sector uncertainty. Internationally, cash has become a key target in the fight against terrorism. When there is actionable intelligence on where terrorists keep their cash, the military can strike and destroy those locations and put a significant dent in the terror groups’ ability to operate. The United States military bombed a building that served as an Islamic State group “cash collection and distribution point” in Mosul, Iraq. By destroying a large amount of cash, described by authorities as tens of millions of dollars in banknotes, it put a severe dent into the Islamic State group’s ability to operate like a state. The U.S. pledged to continue targeting such stores of bills. Had the money been in a bank account somewhere, our government would be unable to reach it.
- In the digital economy there is no trust, only one-way control of global banks, of those who own and control digital networks, and those who can make money mysteriously through digital “tricks” — the owners of the global exchange. When I exchange Rs 100 even 100 times it remains Rs 100. In the digital world those who control the exchange, through digital and financial networks, make money at every step of the 100 exchanges. That is the how the digital economy has created the billionaire class of one per cent, which controls the economy of the 100 per cent.
_____
Most Transactions still involve Cash:
It’s virtually impossible for someone to easily transfer money to another at a low cost, unless both parties are physically present at the same place and same time. Not so, you may protest. We have Apple Pay, PayPal, Google Wallet, MasterCard, Visa, M-Pesa, bitcoin, and hundreds of alt-coins spawned by bitcoin, all of which claim that they will dethrone good old-fashioned cash. But not so fast. Despite all the hype around the supposedly new-fangled digital alternatives to money, these remain either expensive or inconvenient. Credit card companies charge retailers 2 to 3 percent of any transaction, which we’re all paying for in the form of higher prices, passed on by merchants. Direct withdrawals from bank accounts are cheaper but have traditionally taken a long time to clear, sometimes as long as a day. The drawbacks of these digital alternatives are evidenced by the resilience of cash. Eighty-five percent of all transactions globally (and 40 percent in the United States) are still carried out using cash, particularly transactions involving small amounts of money. It is a myth that an advanced society must necessarily be cashless. In Germany, a country which knows the perils of authoritarianism, more than 80% of transactions are in cash, as citizens safeguard their privacy and freedom. Even in the US, 40% of transactions are in cash. Note that Germany and the US actually have the banking and technological infrastructure to enable cashlessness. There are good reasons why that is the case. Cash is convenient. Cash is private. Cash is intuitive. Cash does not incur explicit transactions costs. Notes and coins have been around for thousands of years because of their many advantages. One outstanding characteristic of cash is that it is very fast. There is no waiting for the transaction to take place. Furthermore cash is a universal language. Illiterate people can use it, and the best currencies can be used anywhere in the world. Also cash does not require a highly developed infrastructure to support it. There is no need for telephone lines, internet connections, credit card reader machines, or other devices in an economy that depends on paper notes. This makes cash a very practical solution in poorer countries, where the bulk of the world’s population lives. A big advantage of cash is that the spender is able to spend only as much as he or she has. Contrast this with credit cards, where the user may spend far more than he or she has, and can even end up in debt. Some people expect that we will soon pay for everything from a microchip embedded in our hand or in an ID card, but there are many people who oppose such concentration of information in one source, and who prefer the anonymity of cash transactions. And yet cash is also cumbersome to carry and store. It can be stolen and forged, remains uninvested and usually loses purchasing power over time, and, most importantly, cannot be transferred easily across large distances. And so, there is a pressing need for a digital currency that works. In India, 600 million people have no bank account, and less than 20% of all Indians have a smartphone. Internet penetration is iffy, as is electricity. So cash will remain king for some time at least.
________
________
Cryptocurrency:
A cryptocurrency is a digital currency that is created and managed through the use of advanced encryption techniques known as cryptography. Cryptocurrency made the leap from being an academic concept to (virtual) reality with the creation of Bitcoin in 2009. While Bitcoin attracted a growing following in subsequent years, it captured significant investor and media attention in April 2013 when it peaked at a record $266 per bitcoin after surging 10-fold in the preceding two months. Bitcoin sported a market value of over $2 billion at its peak, but a 50% plunge shortly thereafter sparked a raging debate about the future of cryptocurrencies in general and Bitcoin in particular. I have already discussed difference between Bitcoin and digital cash (digital money/E-money) in earlier paragraphs. The following are 10 types of cryptocurrencies and how they work:
1) Ethereum
Ethereum is a decentralized computing platform that features smart contract functionality. It offers the Ethereum Virtual Machine (EVM), a decentralized virtual machine that executes peer-to-peer contracts using a cryptocurrency known as ether. The Ethereum platform allows multiple uses concerning smart contracts. With Ethereum, you can safely do business with a person you don’t know; because all terms are spelled out in a “smart contract” entrenched in the blockchain.
2) Ripple
Ripple is a real-time currency exchange, remittance network, and settlement system. It offers instant, certain, low-cost international payments. Also known as Ripple protocol or the Ripple Transaction Protocol (RTXP), it is built upon a decentralized open source Internet protocol and native currency referred to as XRP (ripples). Bases around public ledger, Ripple uses a consensus process to all exchange, remittance and payments in distributed process.
3) Litecoin
Litecoin is a peer-to-peer cryptocurrency released under the MIT/X11 license. The currency is Inspired by and technically almost identical to Bitcoin. Litecoin formation and transfer is based on an open source protocol.
4) Dash
Dash, formally called Darkcoin is a more secretive form of Bitcoin. It provides more privacy as it operates on a distributed mastercode network that makes dealings nearly untraceable. Launched in 2014, the currency has an increasing fan. Created and developed by Evan Duffield, this cryptocurrency according to Fernando Gutierrez from Dash.org, has X11 ASICs that presently mine Dash and CPU mining is not profitable anymore since a while ago.
5) Peercoin
Also known as PPCoin, Peercoin was created by software developers Scott Nadal and Sunny King. Lunched in 2012, it was the first digital currency to use a combination of proof-of-work and proof-of-stake. At first, the coins are mined using the proof-of-work hashing process. Over time, as the hashing difficulty increases, the users are rewarded coins using the proof-of-stake algorithm that requires minimal energy to generate blocks.
6) Dogecoin
Launched in 2013, Dogecoin is largely based on the Bitcoin protocol, but with some modifications. The currency uses the technology of scrypt as a proof-of-work scheme. Its block time is 60 seconds. There is no limit to the number of Dogecoin that can be produced. The digital currency deals with many coins that are lesser in value individually. Therefore, it has low entry barrier and good for carrying out smaller transactions.
7) Primecoin
Primecoin was developed by Sunny King. Its proof-of-work is built on prime numbers, and therefore, different from the common system of hashcash utilized by many cryptocurrencies built on the Bitcoin framework. The currency involves finding distinctive long chains of prime numbers and provides greater mining ease and security to the network.
8) Chinacoin
Chinacoin is a litecoin-based digital currency that uses the scrypt password-based key derivation function. At the moment, It’s generated in 60-second blocks with an about 88 coins per block.
9) Ven
Ven is a global digital currency that is designed to allow trade among members of Hub Culture. Launched in 2007, Ven is aimed at reducing the risk of inflation. The Ven value is determined on the financial markets from a basket of commodities, currencies and carbon futures.
10) Bitcoin
Bitcoin is a digital currency created by the mysterious Satoshi Nakamoto. Like other currencies, bitcoin can be used to buy items locally and electronically. As a new user, you can use Bitcoin without understanding all its technical details. Once you install a Bitcoin wallet on your mobile phone or computer, it will generate the first Bitcoin address and you can generate more whenever you need them. After creating bitcoins, you can use them for all types of real transactions.
____
The origin of Bitcoin:
Bitcoin is a cryptocurrency, a number associated with a Bitcoin address. In 2008, a programmer (or group of programmers) under the pseudonym Satoshi Nakamoto published a paper describing digital currencies. Then in 2009, it launched software that created the first Bitcoin network and cryptocurrency. Bitcoin was created to take power out of the hands of the government and central bankers, and put it back into the hands of the people. There are currently about 12 million Bitcoins in circulation, though when it was created, the programmer said there is a finite limit of 21 million Bitcoins out there. The value surged as high as $1000 each in December 2013. Now on 2nd February 2017, 1 Bitcoin = 992.27 US Dollar. Bitcoin uses peer-to-peer technology to operate with no central authority or banks; managing transactions and the issuing of bitcoins is carried out collectively by the network. Bitcoin is open-source; its design is public, nobody owns or controls Bitcoin and everyone can take part. Through many of its unique properties, Bitcoin allows exciting uses that could not be covered by any previous payment system.
_
Bitcoins are not printed like fiat money, but instead are “mined” using computing power in a distributed global network of volunteer software developers. At its core, Bitcoin is nothing more than a digital file that lists every transaction that has ever happened in the network in its version of a general ledger called the “block chain.” Bitcoin is the first example of a growing category of money known as cryptocurrency in which open-source software solves complex mathematical calculations to mine more Bitcoins. Anyone can process transactions using the computing power of specialized hardware. This process is called ‘mining’. These “miners” make the Bitcoin network function by validating transactions and thereby creating new Bitcoins. This occurs when the Bitcoin network collects all the transactions made during a set period of time (usually every 10 minutes) into a list called a “block.” Miners confirm these blocks of transactions and write them into the block chain by competing against each other to solve mathematical calculations. Every time a miner’s system finds a solution that validates a block of transactions, that miner is awarded 25 Bitcoins. Every four years, this reward is halved so that the total number of Bitcoins will never exceed 21 million. Bitcoin network shares a public ledger called the “block chain”. The ledger contains details of every transaction processed, thereby, allowing user’s computer to verify the validity of each transaction. The authenticity of each transaction is protected by digital signatures corresponding to the sending addresses, permitting all users to have full control over sending bitcoins from their own bitcoin addresses. Blockchain uses different types of cryptography, including ECDSA (Elliptic Curve Digital Signature Algorithm) and elliptic curve to authenticate transactions. For a new user not interested in the mining process, the most popular way to obtain Bitcoins is through a traditional exchange where fiat currency is converted into Bitcoins and then stored in a Bitcoin wallet. Wallets come in many forms, including desktop access, mobile access, and online web-based access. Each has its own risks as both desktop and mobile access are susceptible to hackers, a hard drive crash, or a lost mobile device. Online access uses third parties that may also be hacked, cheat its users, or go bankrupt. Bitcoins are listed on stock exchange. Presently, the largest exchanges are: (i) BTC China; (ii) Mt. Gox in Japan; (most widely used) (iii) BitBox in U.S.; (iv) Bitstamp in Slovenia; and (v) Bitcurex in Poland. At present, India does not have a centralised bitcoin exchange, but users can buy and sell coins through several websites. Around 23,000 Indian users have online bitcoin wallet where their digital currency is stored. Countries like Australia, United States, Canada etc. have legalized bitcoins operations within their territories. While countries like China, Japan etc. have adopted a restrictive approach. China has restricted only financial institutions from dealing directly in bitcoins without making it illegal.
______
Bitcoin Advantages:
- Freedom in Payment
- With Bitcoin it is very possible to be able to send and get money anywhere in the world at any given time.
- You don’t have to worry about crossing borders, rescheduling for bank holidays, or any other limitations one might think will occur when transferring money.
- You are in control of your money with Bitcoin. There is no central authority figure in the Bitcoin network.
- Control and Security
- Allowing users to be in control of their transactions help keep Bitcoin safe for the network.
- Merchants cannot charge extra fees on anything without being noticed. They must talk with the consumer before adding any charges.
- Payments in Bitcoin can be made and finalized without one’s personal information being tied to the transactions.
- Due to the fact that personal information is kept hidden from prying eyes, Bitcoin protects against identity theft.
- Bitcoin can be backed up and encrypted to ensure the safety of your money.
- Information is Transparent
- With the block chain, all finalized transactions are available for everyone to see, however personal information is hidden.
- Your public address is what is visible; however, your personal information is not tied to this.
- Anyone at any time can verify transactions in the Bitcoin block chain.
- Bitcoin protocol cannot be manipulated by any person, organization, or government. This is due to Bitcoin being cryptographically secure.
- Very Low Fees
- Currently there are either no fees, or very low fees within Bitcoin payments.
- With transactions, users might include fees in order to process the transactions faster. The higher the fee, the more priority it gets within the network and the quicker it gets processed.
- Digital Currency exchanges help merchant process transactions by converting bitcoins into fiat currency. These services generally have lower fees than credit cards and PayPal.
- Fewer Risks for Merchants
- Due to the fact that Bitcoin transactions cannot be reversed, do not carry with them personal information, and are secure, merchants are protected from potential losses that might occur from fraud.
- With Bitcoin, merchants are able to do business where crime rates and fraud rates may be high. This is because it is very hard to cheat or con anyone in Bitcoin due to the public ledger, otherwise known as the block chain.
- Speed: The decentralized nature of bitcoin means it bypasses banks and other financial institutions, which means payments and transfers can be completed quickly.
- Double-payment protection: Since each transaction is recorded via the public blockchain (transaction database), the “spending” of the same bitcoins more than once is next to impossible.
- Ease of participation: Without the need for credit cards and PINs, bitcoin users need only a computer or mobile device with an Internet connection in order to set up an account and begin transacting.
__
Bitcoin Disadvantages:
- Lack of Awareness & Understanding
- Fact is many people are still unaware of digital currencies and Bitcoin.
- People need to be educated about Bitcoin to be able to apply it to their lives.
- Networking is a must to spread the word on Bitcoin.
- Businesses are accepting bitcoins because of the advantages, but the list is relatively small compared to physical currencies.
- The workers need to be educated on Bitcoin so that they can help the customers. This will definitely take some time and effort. Otherwise, what is the benefit of such large companies accepting Bitcoin if their staffs don’t even know what digital currencies are?
- Risk and Volatility
- Bitcoin has volatility mainly due to the fact that there is a limited amount of coins and the demand for them increases by each passing day.
- However, it is expected that the volatility will decrease as more time goes on.
- As more businesses, medias, and trading centers begin to accept Bitcoin, its’ price will eventually settle down.
- Currently, Bitcoin’s price bounces everyday mainly due to current events that are related to digital currencies.
- Still Developing
- Bitcoin is still at its infancy stage with incomplete features that are in development.
- To make the digital currency more secure and accessible, new features, tools, and services are currently being developed.
- Bitcoin has some growth to do before it comes to its full and final potential.
- This is because Bitcoin is just starting out, and it needs to work out its problems just like how any currency in its beginning stage would need to.
- Illegal activity: As Silk Road revealed, the near-anonymity of bitcoin users makes it a particularly attractive destination for money laundering and the procurement of illicit goods, drugs and activities.
- Theft: Once a bitcoin wallet is “stolen” and emptied, monies contained in an account are—at least today—gone for good.
- Lack of centralized authority: A centralized clearinghouse guaranteeing the validity of a transaction offers the ability to roll back a monetary transaction. There is no such a capability with bitcoin.
- Lack of Security: There is no safety net or perfect way to protect your bitcoins from human error (passwords), technical glitches (hard drive failures, malware), or fiduciary fraud. According to an article in the UK edition of Wired, 18 of 40 web-based businesses offering to exchange bitcoins into other fiat currencies have gone out of business, with only six exchanges reimbursing their customers. The authors of the study estimate that the median lifespan of any bitcoin exchange is 381 days, with a 29.9% chance that a new exchange will close within a year of opening.
_______
_______
Blockchain:
_
The figure below shows how blocks are created in Bitcoin blockchain:
_
The blockchain is a distributed ledger book of all Bitcoin transactions. This means there’s no single database of records. The distributed nature of the blockchain also helps to secure it because the Bitcoin community collectively agree on all transactions; there’s no central authority that can block or reverse payments. Imagine it as a physical book where each page contains about ten minutes of Bitcoin transactions. After 10 minutes of transactions, the page is stamped with a special serial number (a hash), and glued permanently into the ledger book. Everyone can be assured that the transaction list in the ledger book is secure and complete because nobody can insert, modify or delete a transaction without tearing out the page. The serial number hash makes this process very difficult because it ensures all pages are mathematically ‘locked’ (or chained) together. If any content on a previous page is modified, the serial numbers will no longer align, and everyone would know that something hinky is going on. The only way to alter a transaction in the blockchain book is to tear out the page containing the transaction, plus all the following pages. Then alter the transaction on the original page, and then re-print every subsequent page, creating a new hash, and then gluing all of those pages back into the book. Bitcoin transactions are secure because it’s just too much work to modify them!
_
The term blockchain today usually describes a version of above mentioned distributed ledger structure and distributed consensus process of Bitcoin blockchain albeit without Bitcoin but with digital money (digital cash or E-money) and digital assets. Blockchain is a shared, immutable ledger for recording the history of transactions. It is unhackable distributed database of digital assets. This distributed ledger isn’t stored in one place; it’s distributed across several, hundreds or even thousands of computers around the world. And everyone in the network can have access to an up-to-date version of the ledger, so it’s very transparent. It fosters a new generation of transactional applications that establish trust, accountability and transparency. A blockchain is a data structure that makes it possible to create a digital ledger of transactions and share it among a distributed network of computers. It uses cryptography to allow each participant on the network to manipulate the ledger in a secure way without the need for a central authority.
_
Blockchain—a secure record of historical transactions, collected into blocks, chained in chronological order and distributed across a number of different servers to create reliable provenance. The key innovation of digital currencies is the ‘distributed ledger’ which allows a payment system to operate in an entirely decentralised way, without intermediaries such as banks. This innovation draws on advances from a range of disciplines including cryptography (secure communication), game theory (strategic decision-making) and peer-to-peer networking (networks of connections formed without central co-ordination). When payment systems were first computerised, the underlying processes were not significantly changed. Distributed ledger technology represents a fundamental change in how payment systems could work. And in principle, this decentralised approach is not limited to payments. For instance, the majority of financial assets such as shares or bonds already exist only as digital records, stored on centralised databases.
_
Assume an organization has 10 transactions per second. Each of those transactions receives its own digital signature. Using a tree structure, those signatures are combined and given a single digital fingerprint — a unique representation of those transactions at a specific time. That fingerprint is sent up the tree to the next layer of infrastructure, such as a service provider or telecom company. This process happens for every organization in the network until there is a single digital fingerprint that encompasses all the transactions as they existed during that particular second. Once validated, that fingerprint is stored in a blockchain that all the participants can see. A copy of that ledger is also sent back to each organization to store locally. Those signatures can be continuously verified against what is in the blockchain, giving companies a way to monitor the state and integrity of a particular asset or transaction. Anytime a change to data or an asset is proposed, a new, unique digital fingerprint is created. That fingerprint is sent to each client node for validation. If the fingerprints don’t match, or if the change to the data doesn’t fit with the network’s agreed-upon rules, the transaction may not be validated. This setup means the entire network, rather than a central authority, is responsible for ensuring the validity of each transaction.
_
There are two main ways to move funds currently digitally, through the correspondent banking systems or through the blockchain. The correspondent banking system is a way in which funds move through a chain of linked bank accounts to get from one bank account to another. This introduces many intermediaries in an international transaction since banks must regulate other financial institutions on their books. Domestically in the United States, companies and the government have created several ways to interact with the correspondent banking system. The funds typically move through a mix of three different systems, the Automated Clearing House (ACH), FedWire and CHIPS.
_
The figure below shows process of a typical blockchain transaction.
Digital records are lumped together into “blocks” then bound together cryptographically and chronologically into a “chain” using complex mathematical algorithms. This encryption process, known as “hashing” is carried out by lots of different computers. If they all agree on the answer, each block receives a unique digital signature. You don’t store details of the transaction, just the fact that it happened and the hash of the transaction. Once updated, the ledger cannot be altered or tampered with, only added to, and it is updated for everyone in the network at the same time.
What’s so clever about that?
- Well, the distributed nature of a blockchain database means that it’s harder for hackers to attack it – they would have to get access to every copy of the database simultaneously to be successful.
- It also keeps data secure and private because the hash cannot be converted back into the original data – it’s a one-way process. Blockchain data is subject to 256-bit encryption. So if the original document or transaction were subsequently altered, it would produce a different digital signature, alerting the network to the mismatch.
In theory then, the blockchain method makes fraud and error less likely and easier to spot.
_
The blockchain is basically a distributed database. Think of a giant, global spreadsheet that runs on millions and millions of computers. It’s distributed. It’s open source, so anyone can change the underlying code, and they can see what’s going on. It’s truly peer to peer; it doesn’t require powerful intermediaries to authenticate or to settle transactions. It uses state-of-the-art cryptography, so if we have a global, distributed database that can record the fact that we’ve done this transaction, what else could it record? Well, it could record any structured information, not just who paid whom but also who married whom or who owns what land or what light bought power from what power source. In the case of the Internet of Things, we’re going to need a blockchain-settlement system underneath. Banks won’t be able to settle trillions of real-time transactions between things. So this is an extraordinary thing. An immutable, unhackable distributed database of digital assets. This is a platform for truth and it’s a platform for trust. The implications are staggering, not just for the financial-services industry but also right across virtually every aspect of society. The blockchain is the biggest innovation in computer science—the idea of a distributed database where trust is established through mass collaboration and clever code rather than through a powerful institution that does the authentication and the settlement.
_
Getting rid of the middleman:
The blockchain architecture allows a distributed network of computers to reach consensus without the need for a central authority or middleman. A good example is in financial services, where trades are often verified by a central clearinghouse that maintains its own central ledger. Using that process, it can take days to settle a transaction, and the clearinghouse typically collects some kind of fee. Blockchain technology could eliminate that clearinghouse by giving each bank in the network its own copy of the ledger. A common network protocol and consensus mechanism would allow the participants to communicate with one another. Using this method, transactions could be approved automatically in seconds or minutes, significantly cutting costs and boosting efficiency.
_
Blockchain’s foundational elements include:
- Decentralization: Rather than one central authority controlling everything within an ecosystem, blockchain distributes control among all peers in the transaction chain, creating a shared infrastructure. Decentralization of trust has introduced possibilities to make processes such as cross-border payments, trading and settlement faster, more reliable and less costly.
- Digital signature: Blockchain enables an exchange of transactional value using unique digital signatures that rely on public keys (decryption code known to everyone on the network) and private keys (codes known only to the owner) to create proof of ownership. Anyone can verify the digital signature using public keys, but to make the digital signature one would need a private key. By using private keys between the signer and the recipient, data transactions can be maintained by only approved parties.
- Mining: A distributed consensus system rewards miners for confirmation and verification of transactions and stores them in blocks using strict cryptographic rules.
- Data integrity: The use of complex algorithms and consensus among users ensures that transaction data, once agreed upon, cannot be tampered with. Data stored on blockchain thus acts as a single version of truth for all parties involved, reducing the risk of fraud.
_
Efficiencies and Cost Reduction:
In addition to enabling trade, blockchain’s theft and tamper-resistant model can also be applied to non-monetary transactions. Because it eliminates errors and duplication, blockchain is ideal for transforming a host of digital processes.
Key benefits of blockchain include:
- Reduction of settlement time to mere seconds by removing intermediaries.
- Replacement of trusted third parties with access by all participants in the value chain to cloud-based assets that verify each party’s identity.
- Significant security enhancement in areas such as payments and credit card fraud through a decentralized public transaction record that stores details of every transaction and undergoes continuous verification by miners.
- Material cost reduction through the elimination of expensive proprietary infrastructure.
- Elimination of error handling through real time tracking of transactions with no double spending.
- Full automation of transactional processes, from payment through settlement.
- Removal of documentation bottlenecks caused by duplication.
- Risk reduction through data integrity ensured by chronological storing of data enforced with cryptography. This, in turn, reduces the compliance burden and cuts regulatory costs in areas such as know your customer (KYC) initiatives.
_
15% of banks worldwide expect to widely implement blockchain in 2017, which is a ledger of transactions updated in real time by various institutions, by next year, according to the report which surveyed 200 global banks. These banks, mostly medium to large-sized institutions, are focusing their blockchain technology on three areas: consumer lending, retail payments, and reference data, which refers to the real-time information sharing of transactions across business divisions and institutions. In four years, IBM says that 66% percent of banks expect to have blockchain in commercial production and at scale. The disruptive potential of blockchain is widely claimed to equal that of the early commercial Internet. A crucial difference, however, is that while the Internet enables the exchange of data, blockchain could enable the exchange of value; that is, it could enable users to carry out trade and commerce across the globe without the need for payment processors, custodians and settlement and reconciliation entities. Although blockchain is posited as an open system for transaction processing across the financial system, banks are looking inward, experimenting with the distributed ledger approach to create efficiencies and a single version of digital truth. Their goal is to automate processes, reduce data storage costs, minimize data duplication and enhance data security. Similar to the Internet and e-commerce, an open to all blockchain that disrupts the traditional financial market might only result from trial and error deployments within limited parameters, whether through internal trials or partnerships between incumbents and startups. However, to realize the full potential of blockchain across the financial system, the banking industry will need to come together and set standards that enable interoperability.
_
Blockchain’s challenges:
One obstacle to widespread enterprise adoption of blockchain technology is the need to get the network of participants, all of which have their own mix of back-office systems, to agree on a common network protocol and technology stack. The development of the technology also will bring its own regulatory hurdles and potential cybersecurity threats, experts say. Many questions around security and privacy still linger. In financial services, for example, it’s still unclear exactly how much information about a trade each participant needs to be able to see to verify a transaction while still keeping the contents of a particular trade private.
_
Use of Blockchain:
- Real-Time Payments
In order to pay out of one central counterparty, banks often need to maintain reserves with multiple counterparties at once. Blockchain enables banks to settle transactions point-to-point as a straight through process. This will create easier, cheaper, faster and better transactions for both the bank and the customer. Such technology removes intermediaries, simplifies counterparty connections and records data in a tamper-proof manner. It also promises faster speed, more transparency and efficiency for payments.
- Remittance
Utilizing blockchain will allow banks to settle point-to-point with payment service providers in different jurisdictions serving as a gateway to a ledger. This will significantly reduce lifting fees and allow for better exchange rates through a broader set of market makers and better deal algorithms. All of this will happen with a process reduced to a matter of seconds.
- Documentary Trade
Documentary trade today exists in a slow, manual process, often in person to verify the legitimacy of a client. It exists through paper-based administration. Blockchain creates an automated process without sacrificing transparency, which results in lower costs and higher efficiency. It digitizes an end-to-end process all while creating an improved paper trail.
- Asset Servicing
A key benefit of blockchain is that transactions are permanently replicated on a shared ledger. Used in asset servicing, firms will simplify a process that is currently supported across custodians, originators and investors. This will create a rapid settlement of cash flows while dramatically reducing accounting and auditing overhead.
- Securities Settlement
A key benefit of blockchain is that transactions are permanently replicated on a shared ledger. Used in asset servicing, firms will simplify a process that is currently supported across custodians, originators and investors. This will create a rapid settlement of cash flows while dramatically reducing accounting and auditing overhead.
- Commercial Lending
Commercial lending is hindered by each component of a loan existing in a company’s private ledger. Understanding transactions without overall transparency is challenging. Using blockchain technology, loans and all of their subcomponents can be held on one ledger where the full ownership and liabilities are transparent.
____
Financial and non-financial uses of blockchain are depicted in the figure below:
___
Why Banks are wary:
Financial institutions are hesitant about distributed ledger based on concerns about the technology’s scalability, privacy issues for sensitive information, and the governance and volatility of the bridge currency. Banks find blockchain hard to put into practice as unprecedented transparency of transactions sits uneasily with financiers.
_______
_______
Technological advancement and future of digital transactions:
_
______
Digital trends:
_
Cloud technology:
It’s a driving force even though 90% of all information is stored on-premise. You have heard of things like Salesforce’s app exchange, which allows over 2,000 apps to plug into each other. Although the usage of cloud services is an addition to and not a replacement of on-premises systems, cloud services continue to expand in numbers and sophistication. While enterprises are currently using disparate cloud offerings for various parts of their business operations, their desire to link these offerings to core legacy systems and data will grow. It has also been estimated that over 70% of organisations that are using or planning to use cloud services expect internal IT organisations to assume the role of cloud services broker. Citrix, a leading US company in mobile workspaces and cloud services, provides application-centric cloud orchestration solutions to businesses. This technology can manage both traditional enterprise and cloudnative application workloads by combining them into a single unified cloud management platform.
_
Mobile is upgrading:
When you have powerful phones, you can do a lot with them. We expect 30 million apps by end of 2020, as opposed to a couple million right now. In five years, we’ll do most of our business transactions on mobile apps with less than eight screens. That’s the new race.
_
Machine learning:
Software that gets smarter, like predictive business applications. For example, you book travel and a message says ‘People like you book this hotel.’ In the future, an application could ask you if you want all your content for your day’s meetings. People on the buy side of technology should be asking software providers when they will have predictive capabilities. Machine learning is a hot topic. The bottom line is humans and computers will work even closer together in the future. Anyone with a fully digital process will move faster than everyone else.
_
Cognitive analytics:
Cognitive analytics is a new approach to information discovery and decision-making. Inspired by the way the human brain processes information, draws conclusions, and codifies instincts and experiences into learning, it is able to bridge the gap between the intent of big data and the reality of practical decision-making. Machine learning systems, artificial intelligence, and natural language processing are now no longer experimental concepts but potential business disrupters that can drive insights to aid real-time decision making. IBM Watson is an artificially intelligent computer system that is able to process vast amounts of big data and answer questions posed in natural language from a human rather than a computer. The application of the cognitive analytics is relevant across various industries including health care, finance, retail, and the public sector.
_
Digital engagement:
Digital – encompassing mobile, social media, web, wearables and the Internet of Things – is everywhere. Through the seamless convergence of digital channels into a single enhanced user experience, businesses can create consistent, compelling and contextual platforms to engage customers across all its various touch points: online, in-store, as well as customer service personnel.
_
Wearables:
Wearables refer to devices that are either physically worn on the body – including watches, glasses, jewellery, and other accessories – or in the body that are ingested or implanted. Three modular components are responsible for the functionalities of the technology: sensors, displays, and computing architecture. Through these modular components, wearables enable the delivery of accurate and contextual information precisely at the point of decision-making to facilitate real-time decisions. Payments with smart watches will happen very soon – The Apple Watch is proving the buzz around the product is real, with approximately one million preorders so far and more expected to come before the official product launch. With the watch having NFC built in from the start, it is being viewed as a product that will force retailers to get up to speed with accepting payments via NFC in their stores.
_
Social activation:
Social activation refers to observations on how people feel, share, and evangelise to drive their messages across to their audience. With social media becoming a frequent online activity – 27% of total global web-time is attributed to social media – companies have begun to invest into social media monitoring. In addition, they have initiated social activation in the form of social-based customer service, communications, broadcast marketing, and crisis communications, as a mean to distribute mass messaging or to direct customers back to their websites and call centres. The business potential of social technology and social engagement is real: it enables companies to influence perception by converting customers into advocates for the purposes of marketing and sales enablement. In Hong Kong, businesses, especially e-commerce, use social media platforms such as Facebook and WeChat for various types of advertising purposes. Businesses can connect with customers through social media platform by linking their product catalogues to their e-commerce sites, monitoring how people engage with their businesses, and fostering relationships with them through social activation.
______
Pay digitally without internet connection using sound waves:
Sound waves are emerging as a potential game-changer for digital payments. The technology is making financial transactions possible between devices without the need for internet connectivity or communication tools such as NFC, widening the scope for digital payments. You can use a mobile app equipped with sound-based payments technology to make purchases at a store by placing your phone near the merchant’s device. The app has to be linked to your bank or credit card accounts or digital wallets. The transaction happens over sound waves. Bengaluru-based ToneTag and UltraCash have developed sound-based payments technology that function independently or can be integrated with the platforms of banks or digital wallets. An algorithm is used to encode data into sound waves which can be transmitted for making offline payments. It has to be integrated at both ends — the buyer’s mobile phone as well as the merchant’s phone or card readers. There is no need for any additional hardware. A transaction is initiated when a merchant’s device generates sound containing the encrypted payment data. This data is received by the microphone on the buyer’s phone. Sound is an analog signal, which means it is continuous. So, when the merchant initiates the payment by entering the bill amount on his device, the algorithm converts the numbers (digital) into analog format. During this conversion, the digital signal is massaged with encryption. An error-detecting code is used to detect any accidental changes to the raw data. The analog data is transmitted through the merchant’s device as a sound signal to the buyer’s phone. The buyer needs to place their phone near the merchant’s device to receive the bill. The buyer’s phone does the reverse of the above steps and decrypts the data, so the bill is readable. The buyer then makes the payment through a digital wallet or debit or credit card. It supports existing payment hardware such as smartphones, EDCs, PCs etc. which are found in most merchant outlets. The sound based payment technology is safeguarded with tokenization, HCE, multi-layer of encryption, Whitebox Cryptography as well as multi-factor authentication through PIN/Password or biometrics. It enables an extensive and comprehensive ecosystem. It is useful for businesses as it influences the way interactions take place in the sales funnel, between products and individuals, in business networking and interaction and in internal communication. In addition to merchant payments, sound based payment technology facilitates P2P money transfer between two mobile devices. The consumer initiates the payment and the merchant accepts, leading to data transfer using inaudible sound frequencies. This technology works through the app and a user doesn’t need a special hardware like an NFC tag to use it. The technology is fast, paired, encrypted, copy-protected, time-sensitive and inaudible.
________
The Next Wave of Money:
Artificial intelligence and robotics will play an increasing role in retrieving and exchanging money. Robotics is already expanding and placing food orders depending on pre-set preferences, at the same time making payments. Already much money is being invested in robotics and artificial intelligence, which can easily master one’s habits and make choices such as buying or selling. Robo-money will be wallets that increasingly manage themselves, automatically making investments or spending money on our behalf, given certain pre-conditions. Robo-advisory will also increase, which will reduce the cost of managing one’s money. But things are still evolving. How exactly the digital future will shape up remains to be seen, even as cyber security around money will have to increase. Needless to say, the next two decades will be challenging and exciting. While digital money will have its many glitches, it promises to also become all pervasive — and revolutionising.
______
______
I envision amalgamation of IoT, blockchain, artificial intelligence and robotics in future.
______
______
Take Quiz:
Please select the correct answer.
_
- Which of the following is not a function of Two-factor Authentication in digital transactions?
- A) Verify user identity
- B) Reduce the chance of identity theft
- C) Use as a transaction currency recognised by buyers and sellers
- D) For extra authentication
_
- Which of the following is the security measure to be taken during digital transactions?
- A) Provide personal or account information in email
- B) Carry out online transaction activities at public Internet access facilities
- C) Logout upon completion of online transaction
- D) Click on the hyperlinks in dubious emails
_____
Correct Answer C for both questions.
______
______
Moral of the story:
_
- The two ways of processing information are analog and digital. Digital describes electronic technology that generates, stores, and processes data in only two digits 0 and 1. Computers are digital machines because at their most basic level they can distinguish between just two values, 0 and 1, or off and on. Analog information is made up of a continuum of values within a given range. When information such as text, music, voice and video are turned into binary digital form, they can be electronically manipulated, preserved, secured and regenerated perfectly at high speed. Digital is not synonymous with electronic as prior to digital technology, electronic transmission was limited to analog technology, which conveys data as electronic signals of varying frequency or amplitude that are added to carrier waves of a given frequency as in conventional television broadcast and telephone transmission. When science becomes commerce, its purity declines. So digital transaction becomes electronic transaction, digital payment becomes electronic payment and digital money becomes electronic money.
_
- Money is store of value, medium of exchange and unit of account; performing function of payment for goods and services and repayment of debts; can’t be in two places at once, can’t be double spent. The money supply measures reflect the different degrees of liquidity—or spendability—that different types of money have. The narrowest measure is restricted to the most liquid forms of money; it consists of currency in the hands of the public which includes notes and coins of all denominations in circulation. Other measures of money supply include cheques, bank drafts, bank deposits, mutual funds, bonds etc. Cash is money in the physical form of currency, such as banknotes and coins.
__
- More than 2 billion adults worldwide in both developed and developing countries lack adequate access to banking services. Digital transaction has made these populations accessible to banking systems using mobile phones and payment cards as a means of extending financial services to their community and in the hopes of building new streams of revenue in an increasingly competitive banking system.
__
- Major advances in information technologies have led to radical changes in the way we deal with money and payments. Electronic money (digital cash or digital money) is an electronic equivalent of physical cash. Digital cash is traditional bank money held on computers (in software) and store-value payment cards. Digital currency includes digital cash, virtual currency and cryptocurrency (e.g. Bitcoin).
_
- It is generally accepted that in order to carry out digital transaction, you ought to have computer/laptop or smartphone with internet connection. But you can carry out digital transaction without internet connection and even without phone provided you have intermediary that connect you to your bank. I want to emphasize that internet and digital are not synonymous. Non-internet digital transactions involve SMS, MMS, USSD, payment processing IVR and AEPS through 2G mobile phones. For example, you may have 2G cell phone without any internet connectivity. You can still perform digital transaction through USSD code whereby your GSM telecom service provider can act as intermediary between you and your bank. You can even perform digital transaction without any phone provided bank agent has micro-ATM which connects your ID (e.g. Aadhaar card in India) to your bank account. All these are digital transactions although you have neither internet connection nor phone. All ATM and POS transactions are digital transactions on private networks independent of internet although they may still use internet protocols. Internet means connecting a computer to any other computer anywhere in the world via dedicated routers and servers digitally (data in the form of 0 and1). Internet is always digital but digital data can be transferred without using internet, for example using 2G cell phones with cellular networks and using ATM/POS with private interbank networks. Digital transaction is inapplicable for poor unbanked population in remote areas who have no bank account and no phone. However such population can purchase store-value payment cards and pay their bills digitally at POS and then it becomes digital transaction.
_
- Digital transaction is defined as sale or purchase of goods and services, whether between businesses, households, individuals, governments, and other public or private organisations, conducted over computer-mediated networks. Out of order, payment and delivery of goods and services, at least one must be conducted digitally over internet/private network to be classified as digital transaction. Electronic (digital) payment can refer to any type of electronic funds transfer initiated and/or received using digital devices and channels to transmit the instructions. Note that digitizing is often applied to processes other than payments: hence a government could digitize its accounting system, but still make payments by paper (cheque or cash).
_
- Bank notes and coins now account for only seven percent of the U.S. total economic transactions, and an average of seven percent in the Eurozone. There are more than 135 billion credit and debit card transactions globally each year. The worldwide mobile payment revenue in 2015 was 450 billion dollars and is expected to surpass 1 trillion dollars in 2019. Digital transactions will reach 8 trillion dollars by 2020 worldwide.
_
- E-Commerce or Electronics Commerce is a methodology of modern business which addresses the need of business organizations, vendors and customers to reduce cost and improve the quality of goods and services while increasing the speed of delivery. The e-commerce mediated through digital transactions has huge impact on the economy and society. Online sales accounted for more than a third of total U.S. retail sales growth in 2015.
_
- Greatest benefits of digital transactions are convenience, transparency and time saving as compared to traditional transaction. An average American, who writes checks and mails them for payment, spends over 24 hours during the course of a year paying bills. E-payments have reduced the amount of time spent on bill payment by about 60%. Biggest downsides of digital transactions are the lack of authentication, cyber-attacks, repudiation of charges, payment card fraud/loss, hardware/ software/ network /electricity failure and atomicity. Atomicity ensures that if any step fails in the process of transaction, the entire transaction must fails, due to which the same steps have to be repeated again and again while filling forms which causes dissatisfaction among buyers. Another disadvantage of digital transaction is that the process cannot be reversed if a sender should enter an incorrect account number. For developing nation like India, poor internet coverage/speed, lack of digital literacy/skill and habit of using cash cause additional impediments.
_
- ‘Card present’ digital (payment) transaction is done at ATM or POS while ‘card not present’ digital (payment) transaction is done at web payment system and depositing money in third party digital wallet. ‘Card present’ digital transactions need PIN/signature while ‘card not present’ digital transactions need CVV.
_
- Chip (EMV) cards ensures greater security than magnetic stripe cards because existence of the chip itself makes the card extremely hard to counterfeit and it is easy to skim/clone magnetic stripe card because magnetic stripe holds a static amount of data about the card while chip uses electricity from the terminal to generate a dynamic authorization code which is new every time chip card is used. Each transaction with chip card will produce a unique string of numbers that is sent to the financial institution to verify that the card being used is the same one that was issued for that account. Since it’s different for each transaction, it makes it basically impossible to skim the data on the chip card. Even if chip card is stolen, you still have PIN number which nobody knows. Chip cards can be used at merchants that don’t have a chip-enabled terminal yet as chip card continues to have the traditional magnetic strip. However, all merchants are supposed to use chip-enabled terminals. Merchants are liable in the US and the EU for any fraud that results from transactions on systems that are not chip-enabled.
_
- Electronic fund transfer (EFT) is transfer of money from one account into another account using a computerized network. Internet (net) banking is banking services provided by the banks over the internet to be used by customers who have bank accounts enabled with Internet banking and use web browser or bank apps on smartphone to carry out transactions. Net banking is one of the modes of EFT. Other modes of EFT include ATM, POS, ACH (in US), digital wallets, carrier billing, UPI & USSD (in India), payment Processing IVR, and using credit/debit card at web payment system.
_
- Digital transactions via mobile phones enable mobile money payment system through smartphones using internet/NFC/BLE or 2G cell phones without internet. Major drawbacks of mobile payment systems include mobile network access concerns, security issues, personal liability in the event of fraud, multiple apps/wallets as no one app/wallet is accepted everywhere, poor interoperability between different apps/wallets, and poor understanding of mobile payment systems by users. In India, mobile services are turned off repeatedly due to some agitation, unrest, terrorism etc. resulting in blocking digital transactions through mobiles.
_
- Social shopping is the combination of social media and e-commerce. Shopping and social media are arguably two of the most appealing aspects of the internet and social shopping is mixing digital transaction with pleasure.
_
- Out of many different modes of digital transactions, consumer can choose any type of digital payment system depending on transaction fees, time taken for transaction, convenience, privacy and security.
_
- For easy and efficient digital transactions, banks have to increase capacities of their servers and upgrade systems by improving its technology platform and core IT processes; and internet/ telecom/ mobile service providers have to enhance their infrastructure to ensure stable data connectivity all the time and everywhere.
_
- The old adage that “criminals go where the money is” finds aptness today as criminals go where digital transaction occurs. On average, Internet users lose $ 476 per attack and one-in-ten people lose more than $ 5,000. The potential risk of loss from cyber threats in digital transactions can be staggering for customers—upwards of $575 billion globally. Online fraud globally was $10.7 billion in 2016 and will be $25.6 billion by 2020. Measures for security of digital transactions include measures to protect client computer, communication channels and servers. Cybercriminals are continually looking for new ways to exploit and defraud consumers and that’s why it’s important for Internet users to be on their guard at all times. For users things like careful two-factor authentication, strong pass words, antivirus and secure computers are the usual tips.
_
- Authentication is the process of verifying that you are who you say you are. An effective authentication system is necessary in digital transactions for compliance with requirements to safeguard customer information, to prevent money loss, to prevent money laundering and terrorist financing, to prevent reputation damage, to reduce fraud, to prevent identity theft, and to promote legal enforceability of electronic agreements and transactions.
_
- A strong password is difficult to remember. The same rules that make passwords secure also make them almost impossible to remember. Also there are simply too many accounts that require passwords for example Facebook, email and bank accounts. Also better security means more frequent password changes. Forgotten passwords can frustrate customers or, at worst, cause them to abandon their activity altogether. Of course you may use digital vault or password manager online or offline by remembering only one very strong master password and keep all your passwords in it. Never store master password in case you are using password manger or digital vault. But you have to open digital vault or password manager every time you perform digital transaction to retrieve passwords. Biometrics solves the “security versus convenience” question by providing a highly secure method of authentication using unique identifiers that customers always have with them. Fingerprint-based solutions tend to dominate due to convenience and familiarity to the end-user.
_
- A secure payment page means that the page where credit/debit card numbers, CVV, usernames and passwords are entered is secured via Secure Sockets Layer (SSL) 128 bit encryption. A secure connection will have “HTTPS” in the address bar, along with a green lock icon. Secure payment page along with two-factor authentication using one-time passwords (OTPs) would definitely enhance security of digital transaction. Other measures to enhance security are digital signature and digital security token.
_
- Using a Virtual Private Network (VPN) adds a layer of security to your digital transaction by offering military-grade encryption so that it becomes next to impossible for anyone – be it hackers, advertisers, spying agencies, etc. – to track your online activities, which cannot be said for other alternatives out there. You do not have to worry about losing your data in the process and/or becoming a target of cyber criminals.
_
- I propose three factor authentication (3FA) to enhance security, and at the same time reduce inconvenience by avoiding use of any password/PIN.
These three factors are:
a) Biometric authentication (e.g. finger print)
b) Device authentication (e.g. smartphone or laptop) or card authentication at ATM/POS
c) OTP as SMS on cell phone/email
Whether you are performing digital transaction at ATM, POS, smartphones or laptops, these three factor authentication should become rule worldwide. Finger print authentication should be available on all computers, smartphones, ATMs and POS worldwide. At ATM/POS whenever your card is swiped after finger print authentication, OTP is sent to your mobile phone and only after entering OTP, your transaction is completed. No need to remember any password/PIN anywhere any time. More importantly 3FA will create worldwide database of fingerprints which will help catch criminals involved in all types of crimes as these criminals’ fingerprints are also registered for digital transactions. About 1% people might not be able to enrol in a biometric system using their fingerprints. They can use face scan or voice identification.
_
- Secure applications, user authentication and device attestation are three key pillars of mobile security and time has come to take a quantum leap from software based security to hardware based security.
_
- Keep in mind that your Bank will never ask for any details as your personal and financial account details, security codes, ID and passwords through emails or phone calls. If a bank needs to verify something, a notice will be sent to you where you will be asked to provide documents to bank.
_
- After completion of digital transaction, you must ‘logout’ from your online banking account, bank apps, digital wallets or any other apps used for transaction.
_
- Digital payments save money, raise tax revenue, and increase opportunities for their citizens to lead better lives. A report shows that automating all government payment flows could save the Indian government up to $22.4 billion annually. Another study showed that by accelerating growth of digital payments, India can reduce its cost of cash from 1.7% of GDP to 1.3% of GDP savings $10.4 billion in the next five years. Digitizing tax payments can increase government revenue and produce a wide range of benefits for society.
_
- Although greater the GDP per capita higher is the volume of digital payments, growth of digital payments is faster than GDP growth in developing nations due to economic recovery in these markets and adoption of digital technologies and immediate payment schemes. This faster growth of digital payment can boost GDP growth. Digital transactions cause 0.8% increase in GDP for emerging markets and 0.3% increase for developed markets because of increased velocity of money. Digital transactions also coerce people to convert their savings into consumption and/or investment, thereby providing a boost to GDP and employment. Another survey concluded that digitizing the US currency would increase the nation’s GDP by almost 0.5%. So increase in GDP growth increases digital transactions and vice versa increase in digital transactions increases GDP growth. Globally, digital finance could lead to a $3.7 trillion GDP boost by 2025, create 95 million new jobs across all sectors, bring 1.6 billion new people into the formal financial system, and save $110 billion annually in payment leakages in emerging countries.
_
- Although digital technologies have been spreading, digital dividends have not due to nearly 60 percent of the world’s population still offline and can’t participate in the digital economy in any meaningful way. For every person connected to high-speed broadband, five are not. Worldwide, some 4 billion people do not have any internet access, nearly 2 billion do not use a mobile phone, and almost half a billion live outside areas with a mobile signal. Additionally, some of the perceived benefits of digital technologies are offset by emerging risks. So better educated, well connected, and more capable have received most of the benefits—circumscribing the gains from the digital revolution.
_
- Technology can make people more productive, but not when they lack the know-how to use it. All nations should introduce ‘Computer Science and Information Technology’ education in the school curriculum to teach digital skills & digital literacy; and student should be well versed in digital transactions by the time they finish high school.
_
- Elderly population have triple whammy:
–Their digital skill and literacy are poor as they are digital immigrants.
–Their manual dexterity is poor as they have poor muscle coordination, poor vision, tremors and brain atrophy.
–Their reduced memory would make remembering passwords very difficult.
Elderly population have to be provided alternative to digital transactions. My proposed 3F authentication obviate need to remember password and all you have to do is to enter OTP; therefore will help elderly population to carry out secure digital transactions.
_
- Cash transaction delivers speed, absolute anonymity, convenience, portability, liquidity and near-universal acceptance. Furthermore cash is a universal language. Illiterate people can use it, and the best currencies can be used anywhere in the world. Also cash does not require a highly developed infrastructure to support it. There is no need for telephone lines, internet connections, credit card reader machines, or other devices. However, cash can be stolen and forged, remains un-invested and usually loses purchasing power over time, and most importantly, cannot be transferred easily across large distances.
_
- India has the highest share of cash transactions among developed as well as developing countries; evident from the fact that nearly 87% of the value of all transactions in India in 2012, took place in cash. In 2015, the number of digital transactions per capita was only 10 in India, compared to 163 in Brazil, 420 in South Korea and 429 in Sweden. High dependence on cash is due to lack of means to use non-cash payments; existence of the black economy, black money and corruption; and lack of digital awareness in rural India. Also, India is a country of $1.8 trillion GDP and 20% of it, and 80% of the employment is mainly in unorganised sectors without bank accounts or any other mean of transaction apart from cash transactions. In fact, half the population of India do not own bank accounts making electronic payment an alien concept for many. Indian government says that there is 400-1000% increase in digital transactions after demonetisation on 8th November 2016. But this rise is transient and coerced.
_
- Cash facilitates crime, racketeering, extortion, money laundering, counterfeiting, drug and human trafficking, tax evasion, corruption of public officials, illegal immigration and terrorism. However digital transactions also promote money laundering, terrorism and cyber-crimes. Digital transactions are disadvantageous to poor, homeless, elderly and handicapped population. Digital transactions lead to over-reliance on technology; and if the technology infrastructure failed for whatever reason – design faults, material defects, sabotage, overloading, natural disasters or crises – it could have a disastrous effect on the economy and society. An electricity outage, either deliberate or unavoidable, could immobilize the funds of a whole population.
_
- Cashless society would certainly give government unprecedented access to information and power over citizens which compromise privacy and freedom of citizens, facilitates population surveillance and crush their dissent by freezing their funds. Even in developed nations cash transactions are common as citizens safeguard their privacy and freedom by keeping cash. Also cash has repeatedly demonstrated its importance in times of crisis, disasters and medical emergency.
_
- A cryptocurrency is a type of digital token that relies on cryptography for chaining together digital signatures of token transfers, peer-to-peer networking and decentralization. Bitcoin is a type of cryptocurrency. Bitcoin is nothing more than a digital file that lists every transaction that has ever happened in the network in its version of a general ledger called the “block chain.” Bitcoin is open-source; its design is public, nobody owns or controls Bitcoin and everyone can take part. Bitcoin was created to take power out of the hands of the government and central bankers, and put it back into the hands of the people. However the near-anonymity of Bitcoin users makes it a particularly attractive destination for money laundering and the procurement of illicit goods, drugs and activities. Bitcoins are susceptible to volatility, hackers, a hard drive crash, or a lost mobile device.
_
- There are two main ways to move funds currently digitally, through the correspondent banking systems or through the blockchain. The correspondent banking system is a way in which funds move through a chain of linked bank accounts to get from one bank account to another. This introduces many intermediaries in an international transaction since banks must regulate other financial institutions on their books. The term blockchain today usually describes a version of distributed ledger structure and distributed consensus process of Bitcoin blockchain albeit without Bitcoin but with digital cash and digital assets; where trust is established through mass collaboration and clever code rather than central authority/bank/institution. The entire network, rather than a central authority, is responsible for ensuring the validity of each transaction. This distributed ledger isn’t stored in one place; it’s distributed across several, hundreds or even thousands of computers around the world. And everyone in the network can have access to an up-to-date version of the ledger, so it’s very transparent. Transaction data, once agreed upon, cannot be tampered with, hence data stored on blockchain acts as a single version of truth. Using this method, digital transactions could be approved automatically in seconds or minutes, transparently and securely, significantly cutting costs and boosting efficiency. While the Internet enables the exchange of data, blockchain could enable the exchange of value; that is, it could enable users to carry out trade and commerce across the globe without the need for payment processors, custodians and settlement and reconciliation entities. Blockchain makes fraud and error very unlikely and easier to spot. There are concerns about technology’s scalability and privacy issues for sensitive information. 15% of banks worldwide are expected to widely implement blockchain in 2017.
_
- I envision amalgamation of Internet of Things, blockchain, artificial intelligence and robotics in future.
______
Dr. Rajiv Desai. MD.
February 13, 2017
______
Postscript:
I am neither engineer nor economist. So it took a while to understand digital transaction and its economic implications. I love cash because cash carries confidence that no electronics can replace. Behavioural economics suggests people are willing to forego future gains if they see clear but smaller immediate gains. A note in hand is worth two in the account.
______
______


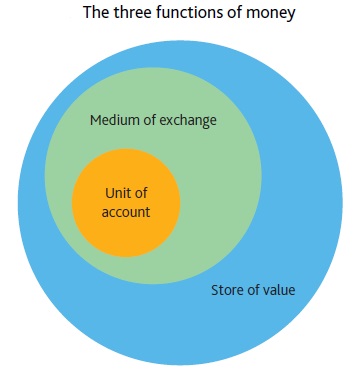

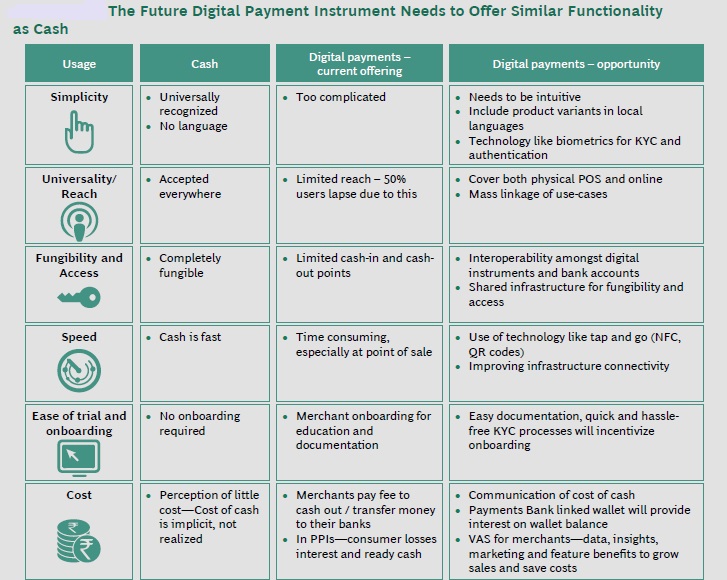
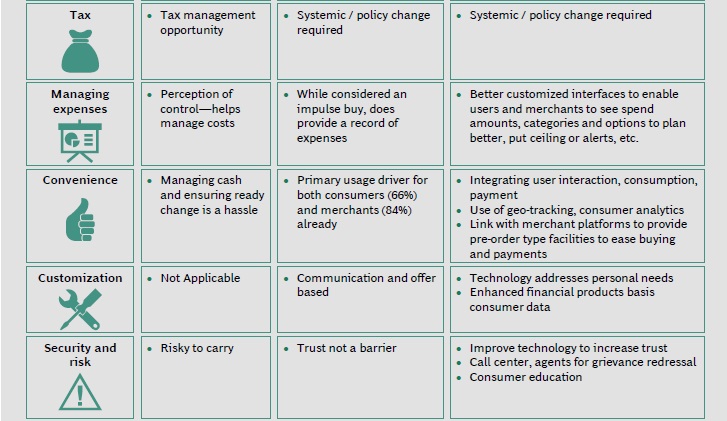
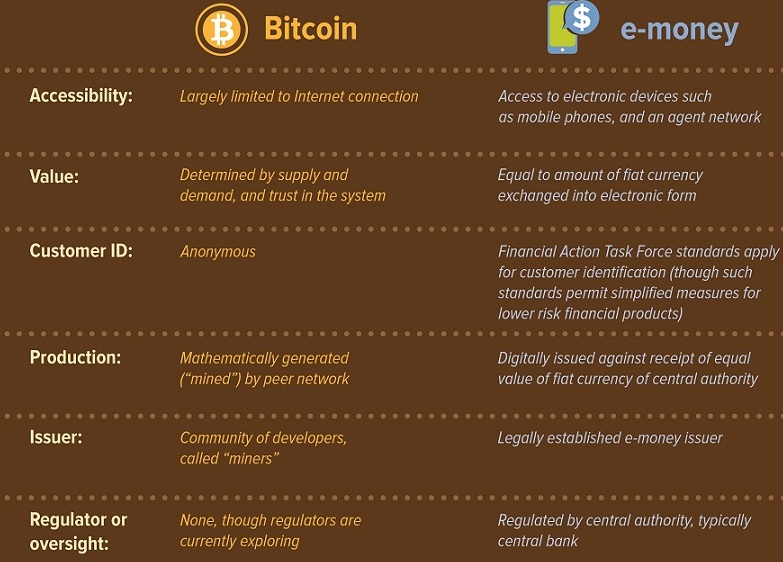
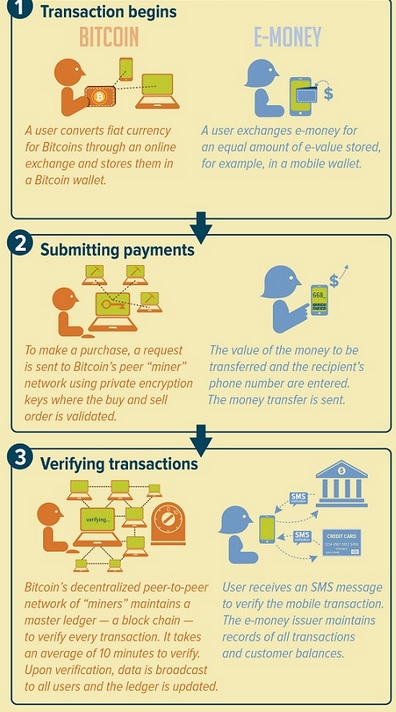
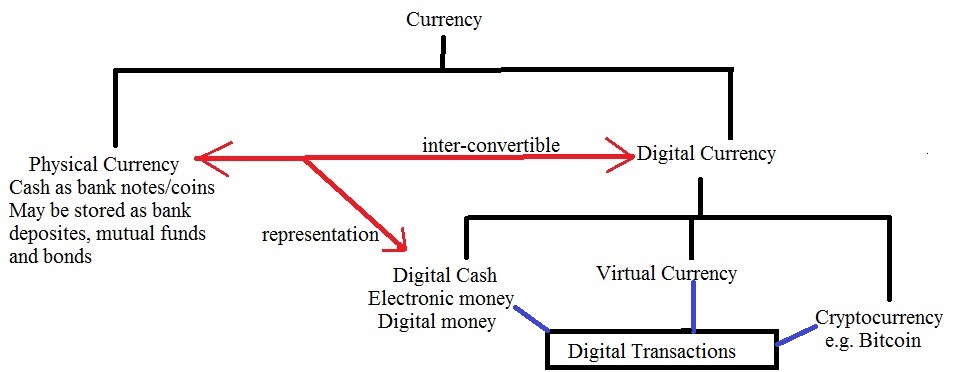
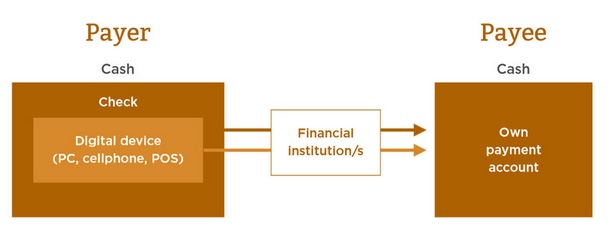

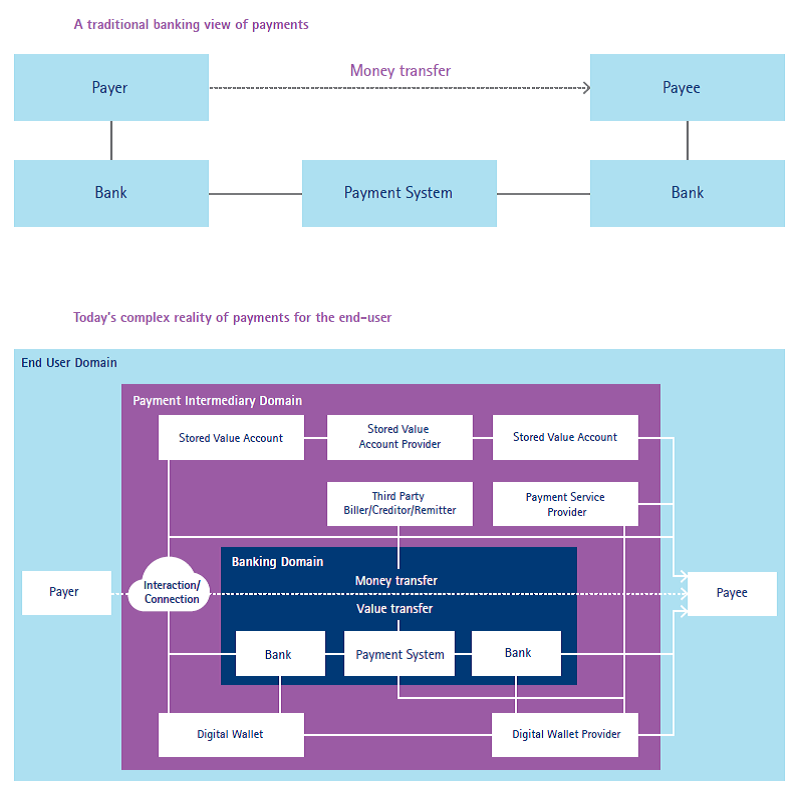
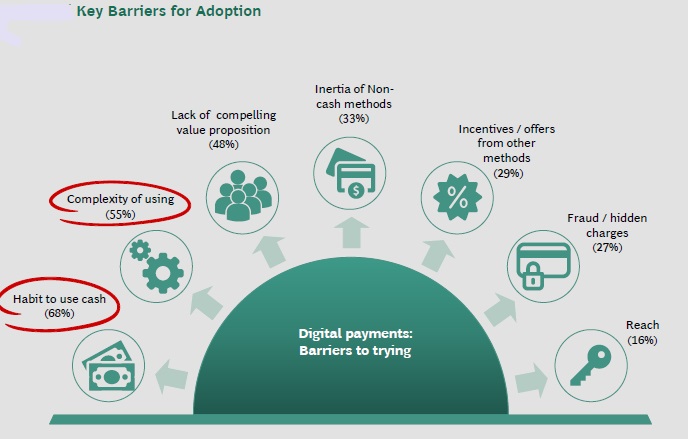
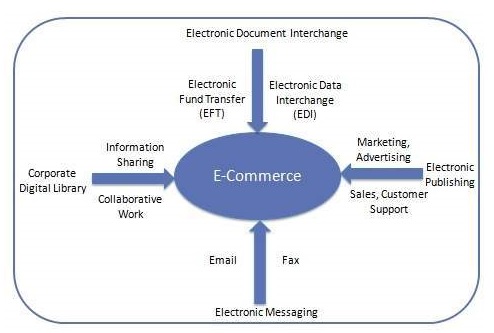


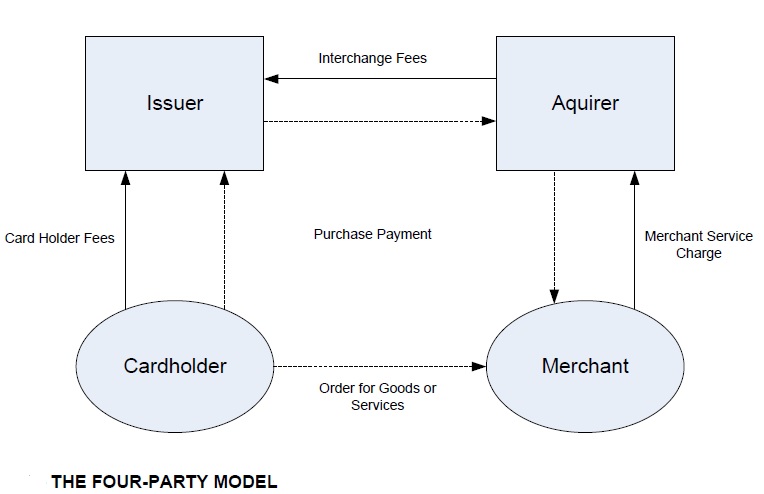
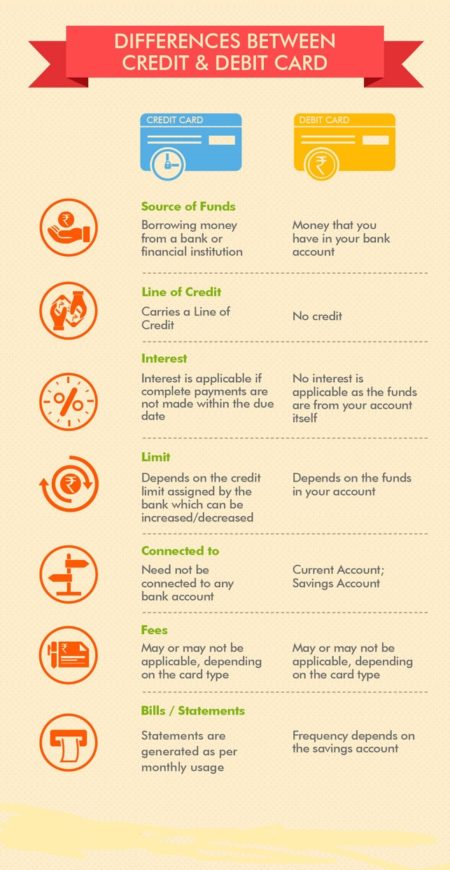

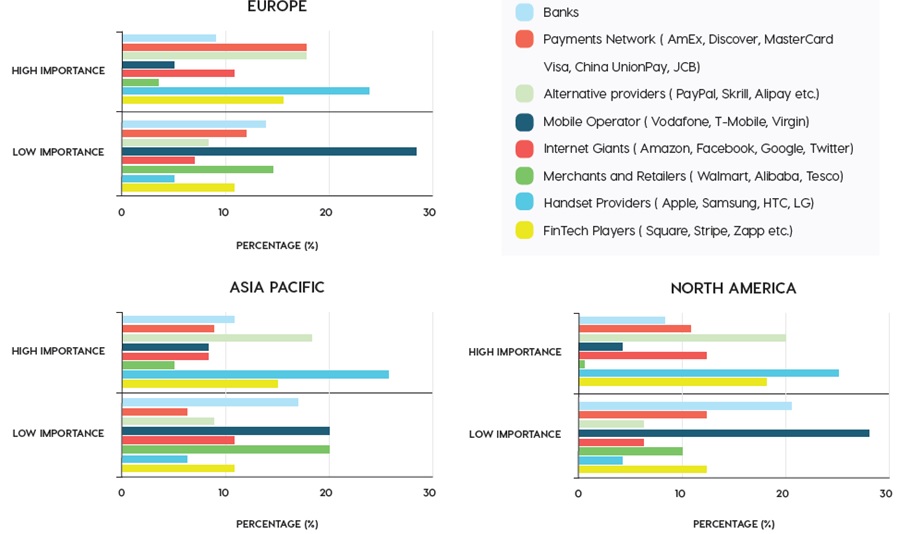
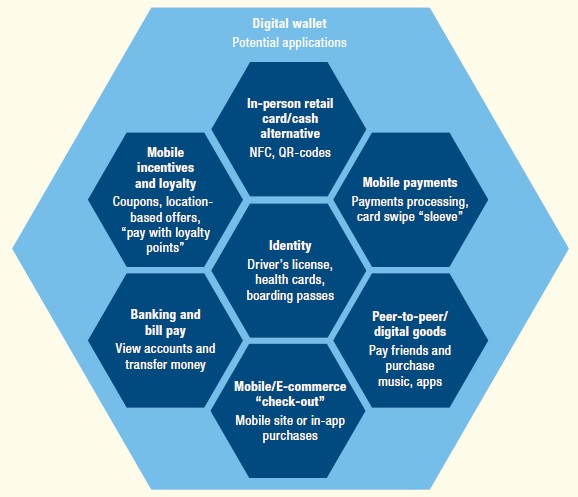
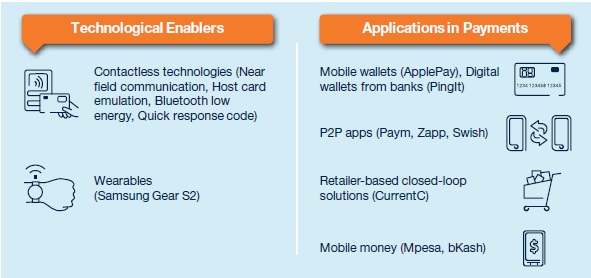

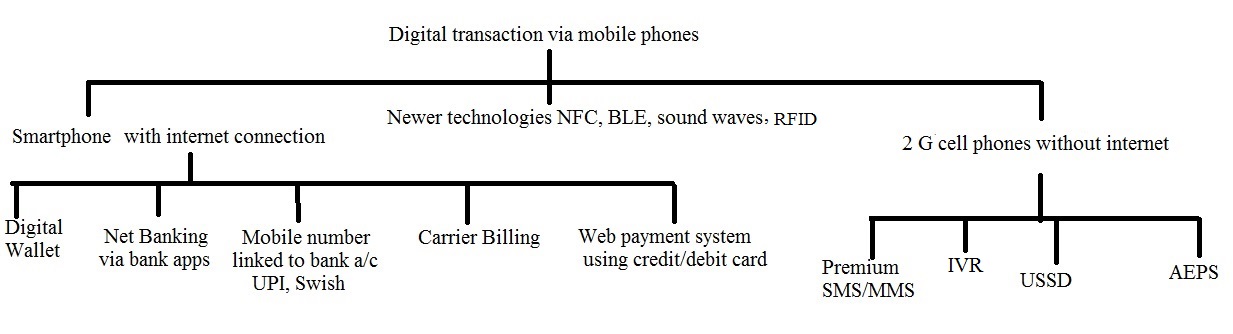
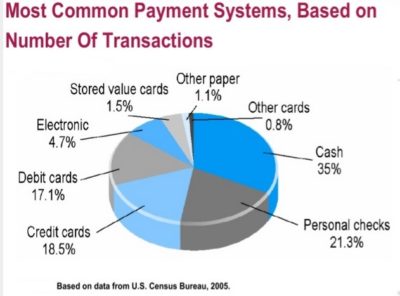
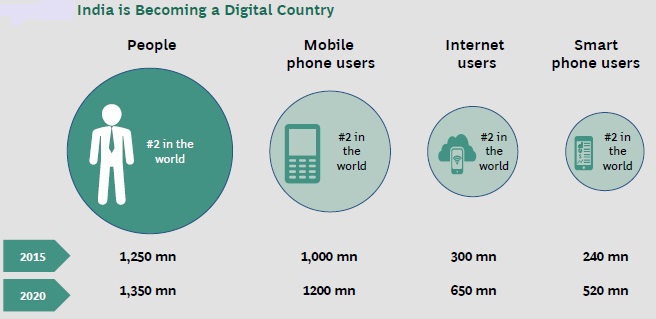
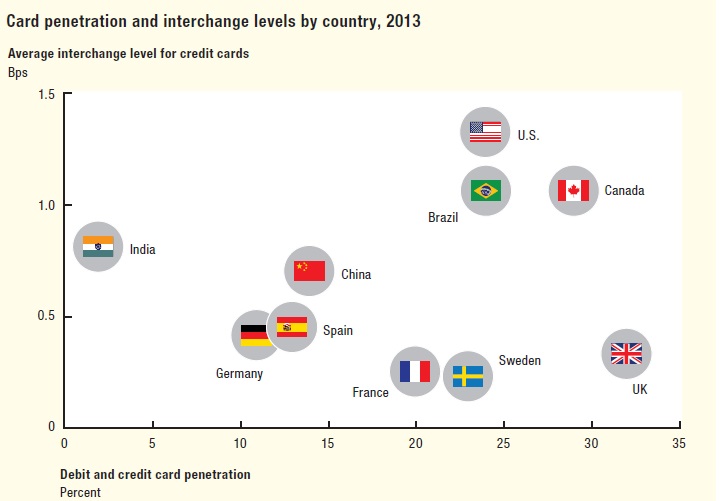

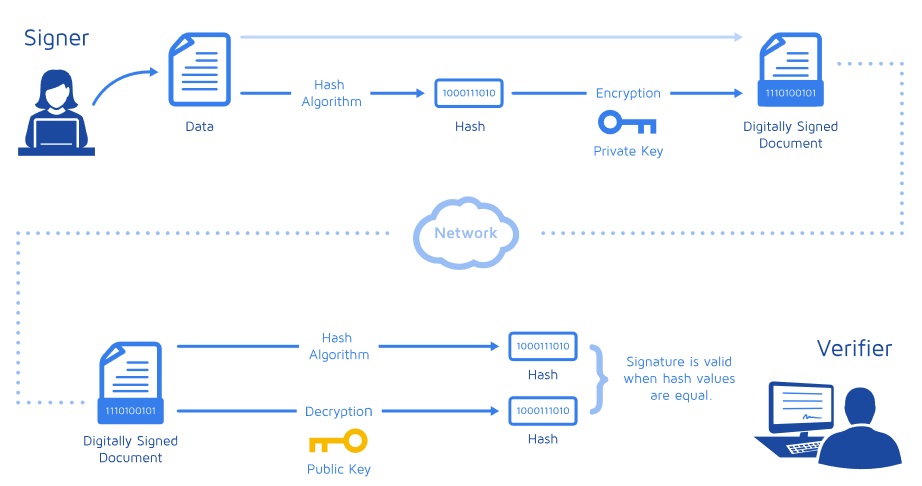
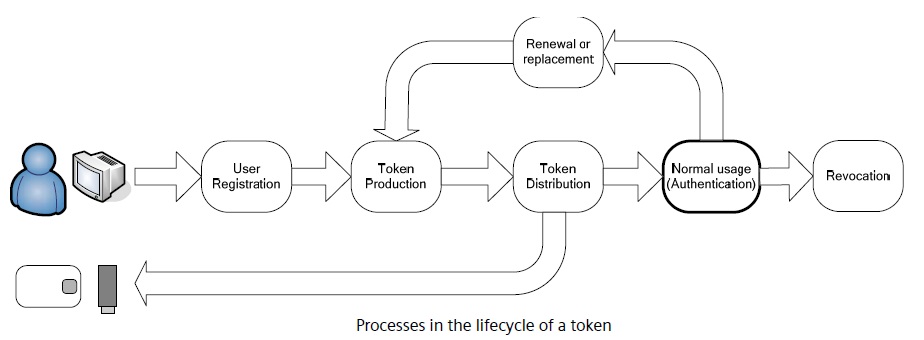


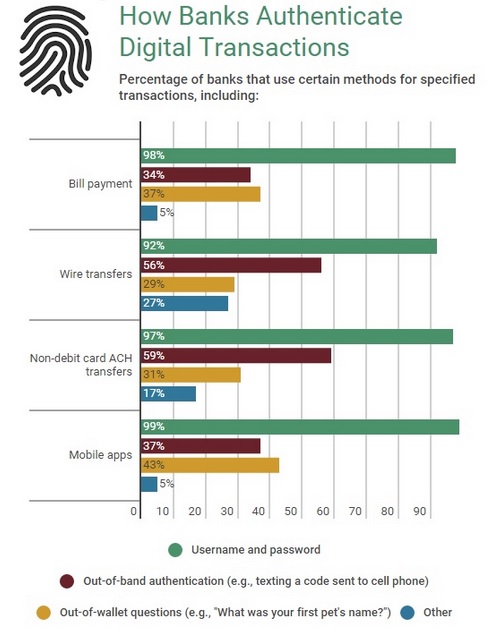
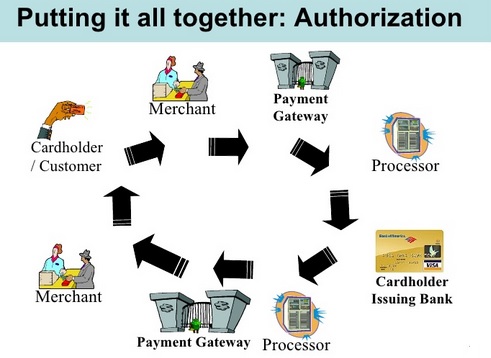
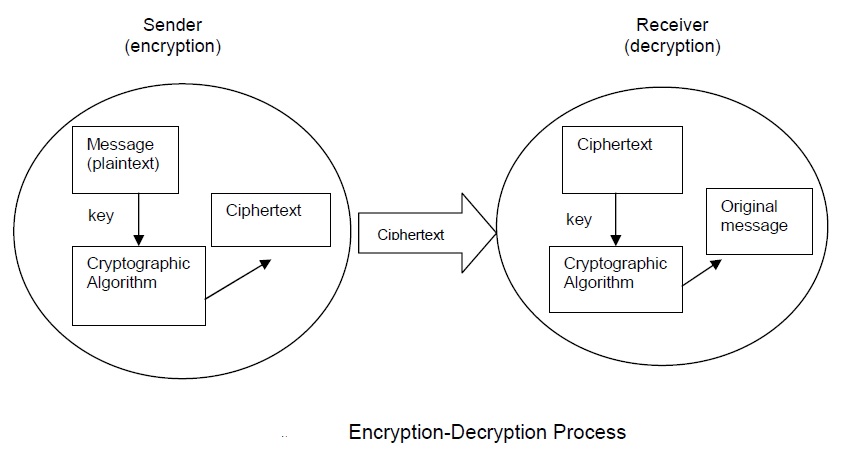
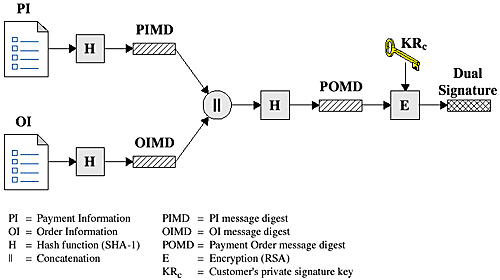
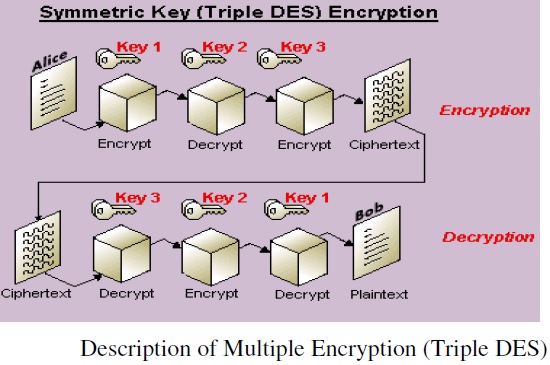

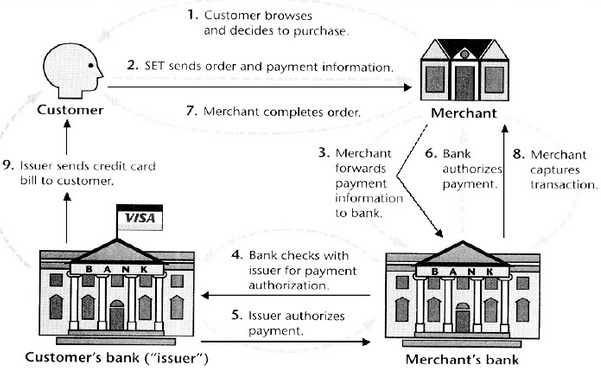

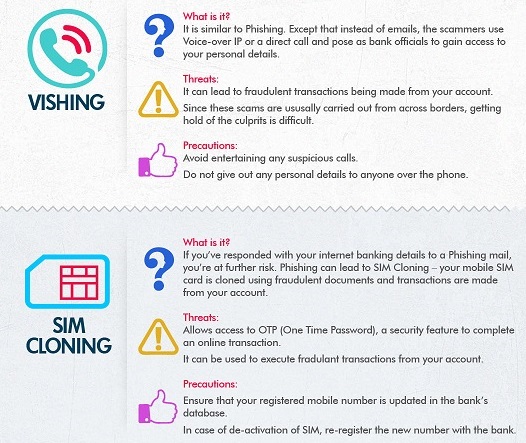
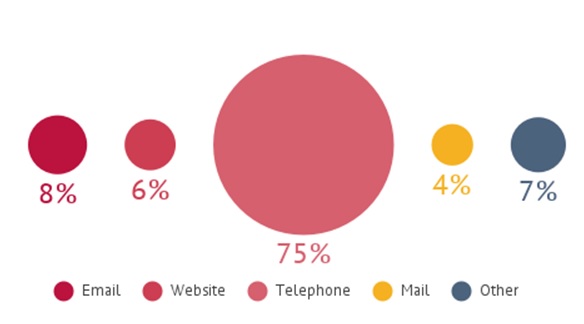
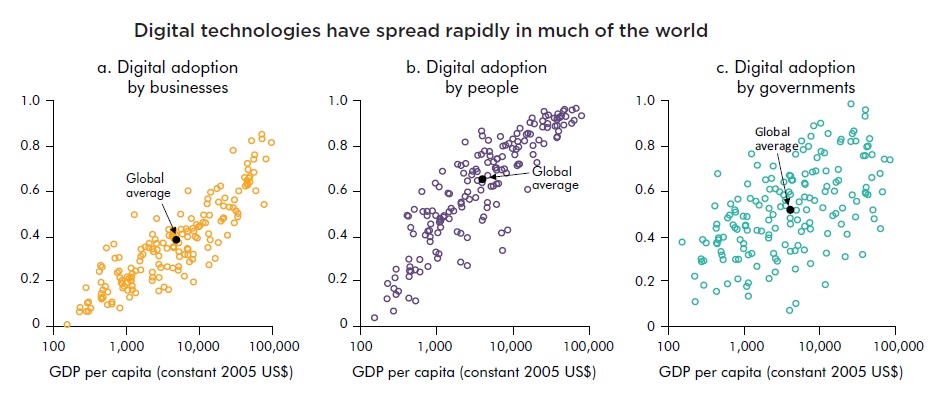
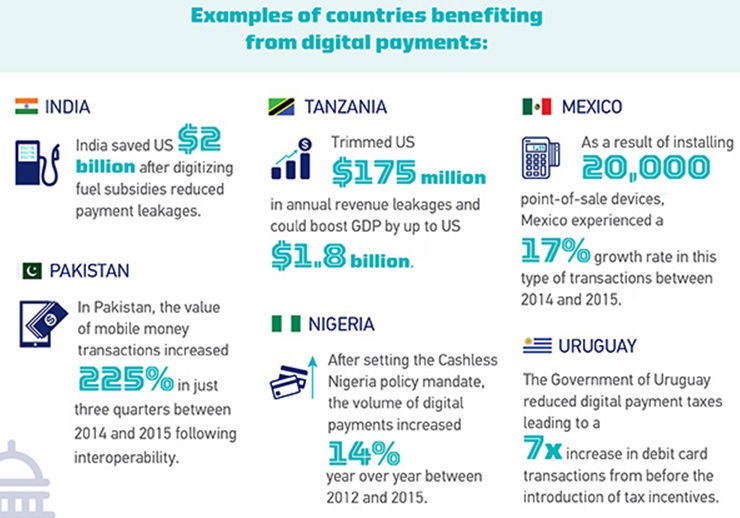
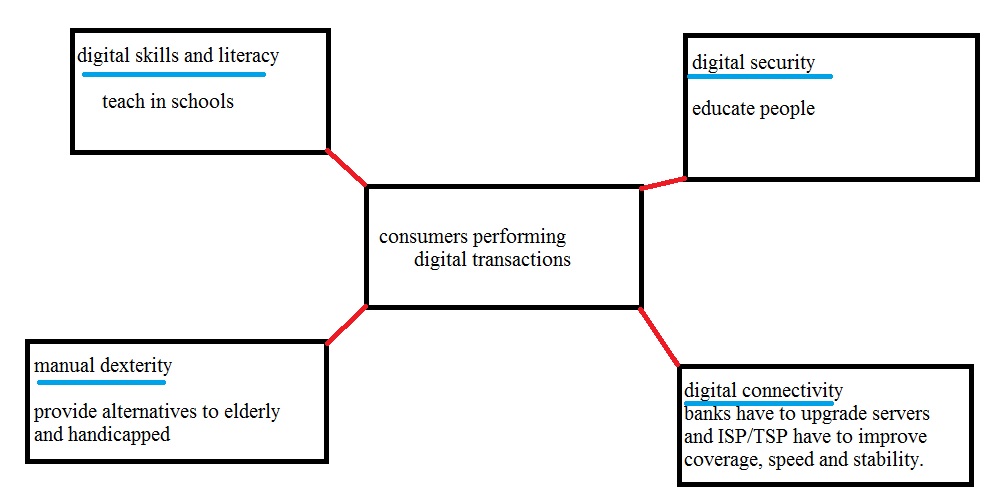
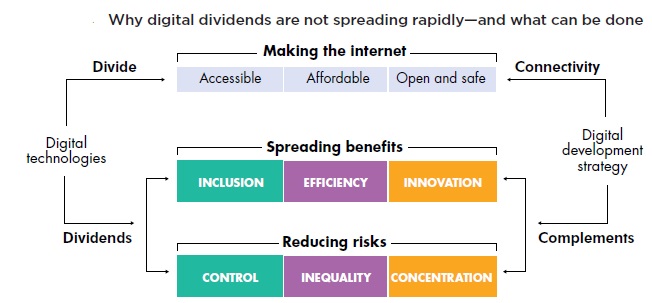
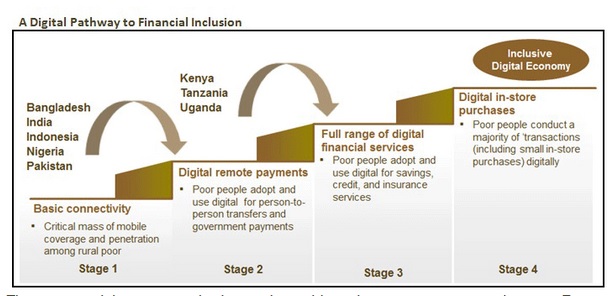
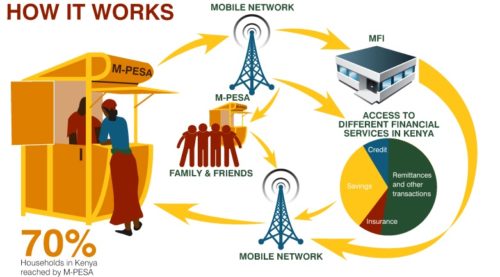
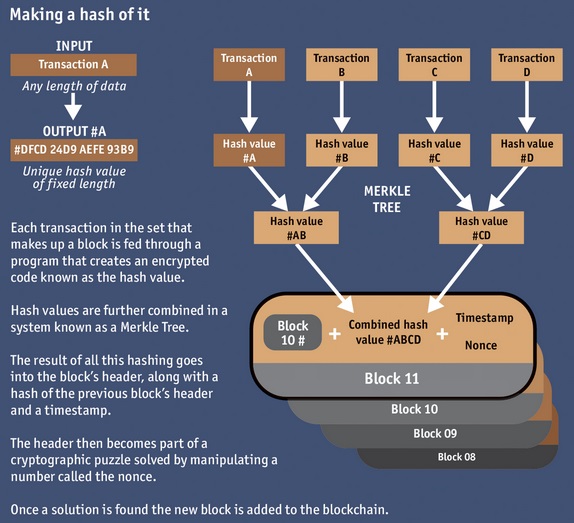
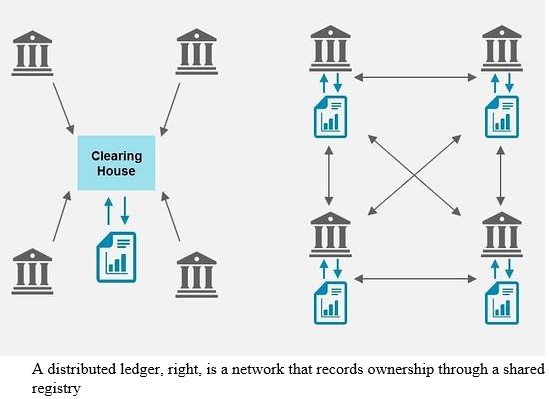
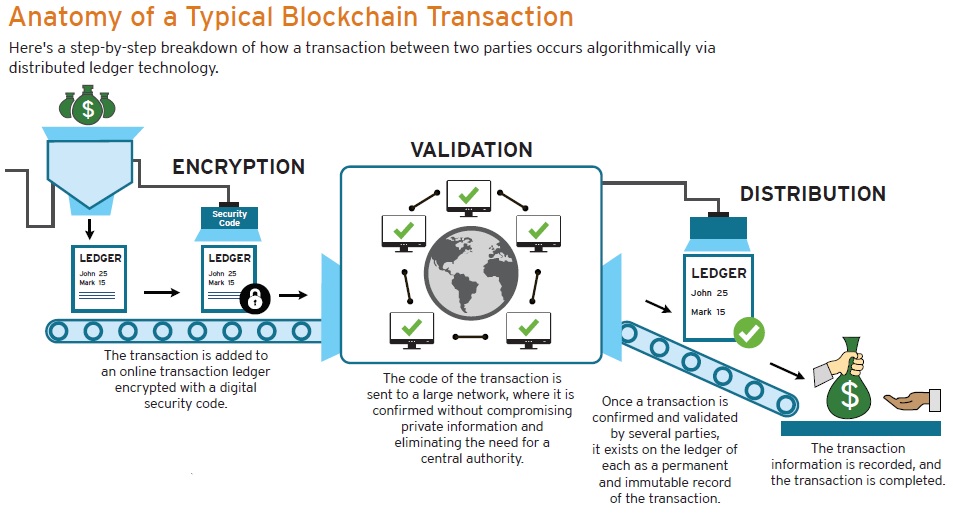
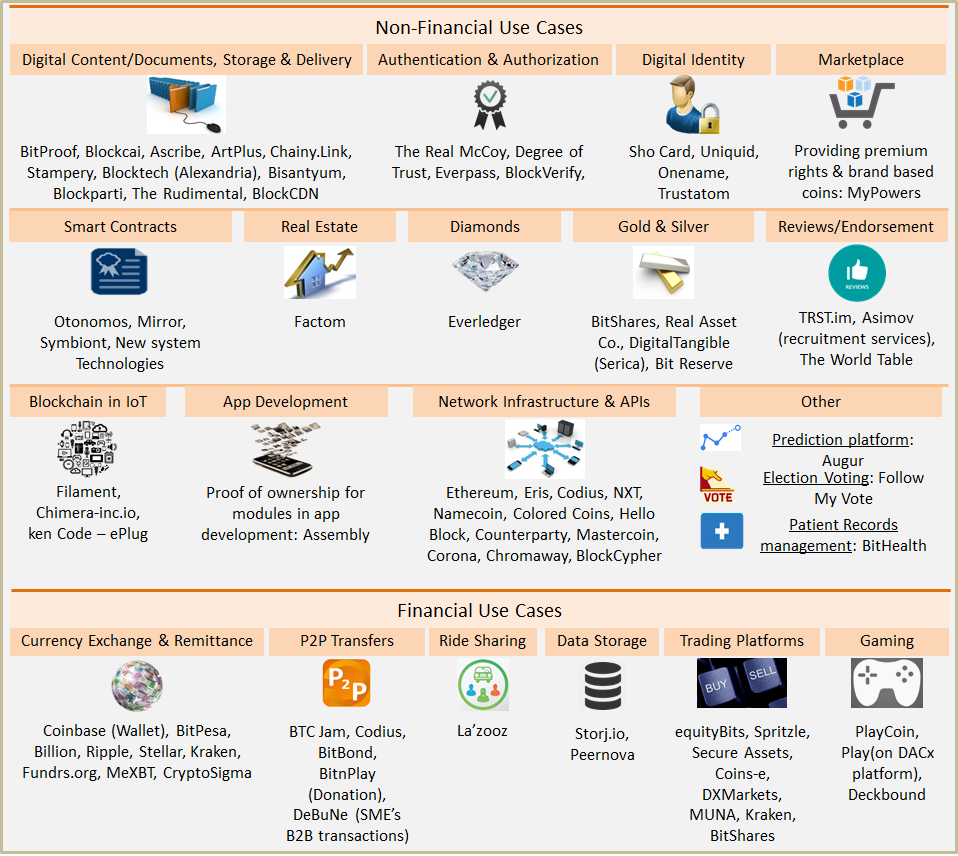

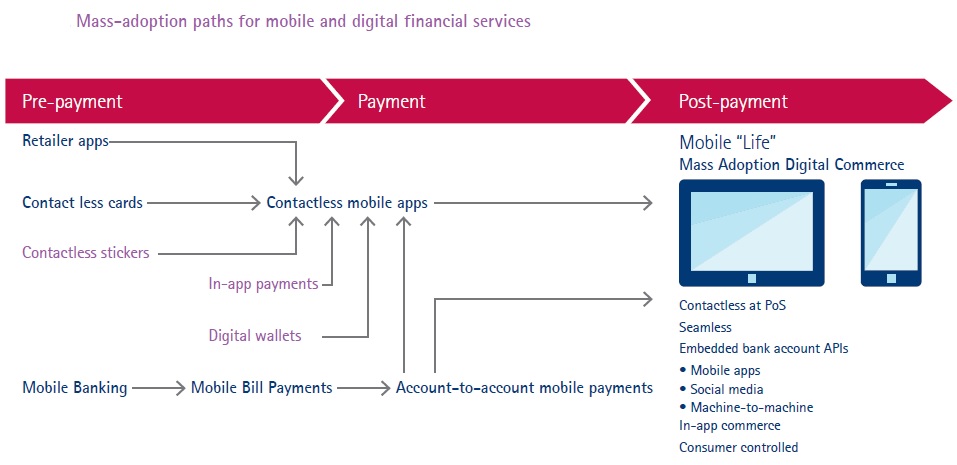
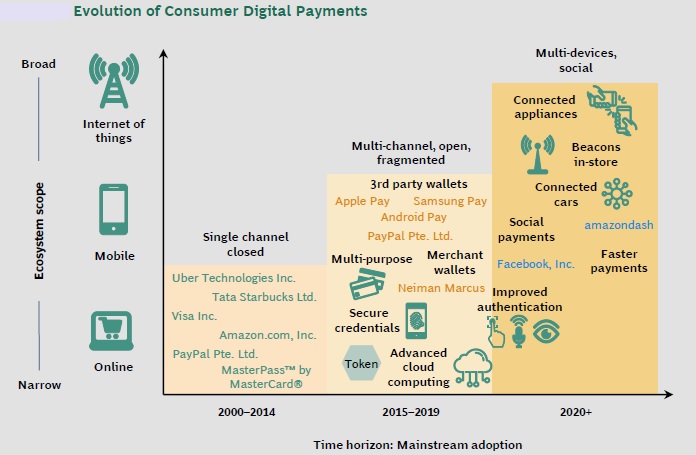
This design is spectacular! You definitely know how to keep a reader entertained. Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!) Excellent job. I really enjoyed what you had to say, and more than that, how you presented it. Too cool!
Excellent blog you have got here.. It’s hard to find high quality writing like yours these days. I truly appreciate individuals like you! Take care!!
It’s always nice to come across great content such as this. Keep up the good work.
Hello very cool site!! Guy .. Beautiful .. Wonderful .. I’ll bookmark your web site and take the feeds additionally?I’m satisfied to seek out numerous useful information here within the submit, we need develop extra strategies in this regard, thank you for sharing. . . . . .
I value the scalable features and accurate charts. This site is reliable.
Never disappoints, top quality.
Hello there, You have performed a great job. I will certainly digg it and individually recommend to my friends. I’m confident they will be benefited from this website.
very nice
Major thanks for the blog.Really looking forward to read more. Really Cool.
You’re so awesome! I do not suppose I’ve read something like that before. So good to find someone with genuine thoughts on this subject. Really.. thanks for starting this up. This site is something that’s needed on the internet, someone with a little originality.
Major thankies for the article.Thanks Again. Fantastic.
I have to express my gratitude for your generosity giving support to people that actually need guidance on this particular subject matter. Your real commitment to getting the message along appears to be especially useful and has frequently permitted employees much like me to arrive at their dreams. Your new informative guideline signifies a whole lot to me and extremely more to my office colleagues. Thanks a lot; from everyone of us.