Dr Rajiv Desai
An Educational Blog
INTELLIGENCE AGAINST TERRORISM
INTELLIGENCE AGAINST TERRORISM:
I thank everybody for visiting my website. This is the 100th article on my website. For this important occasion, I have chosen a topic that is the talk of the town. Everybody worldwide is concerned about rise of terrorism and this article is a small step to eradicate terrorism using our intelligence.
_______
_______
Prologue:
In February 2001, CIA director George Tenet publicly testified to Congress that “the threat from terrorism is real, it is immediate, and it is evolving.” Furthermore, “Osama bin Laden and his global network of lieutenants and associates remain the most immediate and serious threat.” Nevertheless, the Intelligence Community gave no specific warning of the September 11, 2001 attacks. Although all observers grant that terrorist groups are very difficult targets and that undetected movements of small numbers of their members in an open society cannot realistically be prevented, serious questions remain. Look at the scenario around Pathankot terrorist attack at the intervening night of January 1 and 2, 2016 in which seven security personnel and six terrorists belonging to Jaish-e-Mohammed group were killed at Pathankot Indian air force base. Two events struck me. First, on the intervening night of December 31 and January 1, Gurdaspur SP (superintendent of police) was kidnapped along with his friend and cook by the same Pakistani terrorists who later attacked the Pathankot airbase. The terrorists released SP and cook but slit the throat of SP’s friend before dumping them on the road and speeding away. There was 24 hour gap between abduction and terrorist attack but nobody predicted or anticipated it. What kind of policing is this? Gurdaspur is 40 km away from Pathankot. The Indian National Investigation Agency has not found any link between SP and the terrorists who attacked Pathankot air base. Indian media and analysts were discussing whether SP is innocent or connived with terrorist. I thought otherwise. I watched SP’s TV interview and found that he is not intelligent. I also found that his superiors are also not intelligent. They all had 24 hours to catch terrorists to prevent terror attack. The issue is not of SP’s connivance with terrorist. The issue is that so many top police officers are so unintelligent. Second, one terrorist was talking to his mother on phone before attack. Mother told him to eat well. What kind of mother is this? I expect mother to scold son for attempting to kill innocent people. Are our police and intelligence officers not intelligent to thwart terrorist attacks? Do family members of terrorists slyly support terrorism? Good intelligence is the best weapon against terrorism and intelligence gaps hurt efforts to prevent more terror. In his article “Old Allies and New Friends: Intelligence-Sharing in the War on Terror”, Derek Reveron states “the war on terror requires high levels of intelligence to identify a threat relative to the amount of force required to neutralize it” as opposed to the Cold War where the opposite was true. As a result, intelligence is the cornerstone of effective counterterrorism operations in the post 9/11 world. We need to be more intelligent to defeat terrorism, so I am writing this article ‘Intelligence against terrorism’ as 100th article on my website.
________
Introduction to intelligence against terrorism:
_
Please read my article on ‘Terrorism’ posted on June 1st, 2013 on my website at https://drrajivdesaimd.com/?p=4463 where-in I showed that best way to end terrorism is better policing, better intelligence, infiltrating terror cells and better politics. I have also defined terrorism as “premeditated, intentional, threat of violence and/or act of violence against non-combatants, in order to achieve political/ religious/ economic/ social/ ideological goals, through spread of fear & publicity, by non-state and/or state actors, coercing government and/or civilian population to change its policies & ways”. Left-wing terrorism (sometimes called Marxist–Leninist terrorism or revolutionary/left-wing terrorism) is terrorism meant to overthrow capitalist systems and replace them with socialist societies. Right-wing terrorism is terrorism motivated by a variety of far right ideologies and beliefs, including anti-communism, neo-fascism, neo-Nazism, racism, xenophobia and opposition to immigration. In this article I have focussed on intelligence against radical Islamic terrorism.
_
Terrorists can seek to act upon political processes and public perceptions in two subtly different modes. The first is where violence is directed toward a symbol of the social and cultural order to which the perpetrator is opposed. In these symbolic crimes, exemplified by the 9/11 attack on the Pentagon as a building that is both a connotative and denotative signifier of U.S. military power. The salience of the act is derived from the drama of violence performed against an iconic representation of some facet of a cultural or social order. The second mode is where the impact of the incident is contingent to a greater degree upon the logic illuminated by the signal crime concept. Terrorist attacks that signal risk and threat tend to be located in routine public settings where mass civilian casualties are likely to occur. They exert political and perceptual influence by signalling the risks and threats that can be manufactured in everyday life situations by a determined minority and in doing so induce changes in how citizens think, feel, or act in relation to their security. Recent examples of where this signalling logic has been enacted through terrorist attacks are the Bali nightclub bombings and the bombings on the public transport systems in Madrid and London. Some instances of terrorist violence, such as the 9/11 attack on the World Trade Center embody both a symbolic and a signalling logic. For the most part though, the accent tends toward one or the other of these two communicative modes. Differentiating between the symbolic and signal modes by which terrorist violence acts upon political processes and public perceptions provides insight into the subtly different ways that locally situated terrorisms can affect a democratic social order. But for both modes, the potency and power of violence depends upon inducing a sense of uncertainty about security in the public mind and political process. Terrorism seeks to manufacture uncertainty to induce a reaction that destabilizes a social order to render it more precarious in some manner. That it sometimes achieves this is perhaps evidenced by the aftermath of the Madrid train bombings where commentators have suggested that the al-Qaeda sponsored attack altered the outcome of the subsequent democratic elections.
_
Before the 1960s, terrorism was seen largely as a threat to law and order inside a society. Preventing and controlling it and investigating acts of terrorism were considered as part of the normal law enforcement responsibilities of the police. It had the leadership role in counter-terrorism, whether it be in respect of intelligence collection; or investigation and crisis management after the commission of an act of terrorism. The intelligence collection cells of the Police such as the Special Branch (SB) and the Criminal Investigation Department (CID), as they were called in countries such as India, which followed the British model of police administration, had the major responsibility for the collection of the intelligence required for the prevention and investigation of acts of terrorism. The role of the armed forces and the national intelligence agencies was confined to providing back-up support to the police. This view of terrorism as a threat to law and order, controllable by the police, started changing from the 1960s due to various reasons. As a result, terrorism came to be viewed, initially, as a para-military threat to the internal security of a nation beyond the limited competence of its police and its intelligence cells and, subsequently as a threat to national security as a whole, internal as well as external. It was felt that the enhanced threat called for large financial and human resources and sophisticated skills in intelligence collection and analysis. It also called for counter-intelligence as applied to non-State actors and for counter-terrorism methods which involved a greater use of military means for dealing with the menace.
_
At no time in the history of mankind has intelligence played as crucial a role as it does today. The immediate response to the painful shock of 11 September was the introduction and enforcement of tough security measures—from the intense scrutiny of all foreign visitors and physical searches of airports, to the erection of fences and concrete roadblocks around historic monuments, government offices, and military installations. Subsequent administrative shakeups were accompanied by military actions in Afghanistan and later, the invasion of Iraq. Few would doubt that the United States’ initial reaction was an indispensable and justifiable act of self-defense. But do these measures reduce the danger of terrorism and protect against further brutal assaults on the country? Do these demonstrations of superior military might strike at the causes and roots of terrorism? Can military action result in democratic change and strengthen the rule of law? A myriad of problems have to be grappled with and resolved before we feel confident that we can effectively address the difficult threat that terrorism poses. Today, the most immediate problem is the need to readdress the effectiveness of our intelligence services, and ensure their readiness to protect the free world from mortal surprises in an age of nuclear proliferation and international terrorism. Napoleon is said to have noted that, “one spy in the right place is worth twenty thousand men in the field,” and this adage is more true today than it was two hundred years ago. Despite the technological prowess, signal and imagery collection capabilities of the United States, there is no substitute for human penetration, and the latter has been woefully neglected over the past decade. Spies do not spring up by a wave of the hand inside an adversary’s backyard. They need to be carefully selected, meticulously vetted, trained, patiently nurtured, and prepared for risky assignments. They are of course, not the end in and of themselves, but should instead form a key part of a larger strengthened system of intelligence. We need to employ far more forceful tactics, with special operations featured as the preferred method of handling concerns. Intelligence collection, analysis, interpretation, dissemination should serve as a prelude to vigorous intervention into international events fraught with dangers of new terrorist attacks. Time-tested covert actions to influence political, economic, or military conditions abroad should become the core of the intelligence community’s response to radical Islamic extremists wherever they may be. These actions include subversion, sabotage, operational deception, disinformation, and massive sophisticated propaganda efforts to confuse and manipulate the targeted contingents. No country nurturing or harbouring terrorists should be exempted from special operations going beyond diplomatic demarches and economic sanctions. Toward this end, human penetration—the recruitment of agents within or the infiltration of agents into the vital structures of institutions, groupings and cells of potential adversaries—must be at the center of all intelligence efforts.
_
In an important speech nearly a decade ago, Gen. Michael Hayden, a retired four-star Air Force general and former director of both the Central Intelligence Agency and the National Security Agency, described the challenges the United States faced then and the critical importance of intelligence in winning the war on terrorism. We’re now in an age in which our primary adversary is easy to kill, he’s just very hard to find. So you can understand why so much emphasis in the last five years has been placed on intelligence. Moreover, the moment of an enemy’s attack may be just that, a moment, a split second, the time it takes for an airliner to crash or a bomb to detonate. There can be little or no time to defeat him on the battlefield he’s chosen. This rings even truer today. In the age of ISIS-directed, -enabled, and -inspired attacks against the world, the enemy is harder to find than ever before. We have limited opportunities to detect and disrupt him. Our future success depends on our ability to adapt. It is not enough to maintain the status quo and hope for better results. Terrorists have evolved since September 11; our domestic national security efforts must also evolve. One key is the expanded use of HUMINT, which will help local law enforcement agencies combat those who seek to harm Americans.
_
Modern 21st century intelligence services principally concern themselves with information technology, study communication, Facebook and the rest. They make conclusions but that human factor, the collection of information from people, is neglected. This is the problem of the 21st century, we have a strictly bureaucratized intelligence service, but on the other hand there is an overwhelming amount of information. Thirdly, the processing and selection of information is limited. What is known by the public about the activities of intelligence services is a drop in the ocean, a secrecy which is intended to prevent potential terrorists from gaining the knowledge to outsmart intelligence. Most often, the public and media don’t have the right information because of the complications of intelligence operations and criminal prosecutions and so on, the information will never be accessible at this time, perhaps in ten years, but not now. There is a veil of secrecy, and if you uncover your methodology you are vulnerable. We see that terrorists never attack twice in the same way because they know that the national intelligence services adapt to it. One of the changes in terrorism has been the targeting of ordinary people, whereas previously terrorists mostly targeted public figures. Thirty or forty years ago it was unthinkable that the victims would be civilians in an airport or on the street. The victims were principally military people, diplomats, and government buildings. Hostage-takers on planes tried not to kill passengers but swap them. But the 9/11 attack on the twin towers changed everything.
__
Humiliation as a cause of Terrorism:
Many people reject the search for ‘root causes’ for terrorism, because they fear that such endeavours amount to nothing but the condoning of terrorism. Many equate understanding with condoning, and describing with prescribing, and believe that we excuse terrorism when we conceptualize perpetrators as ‘human beings’ rather than ‘mad monsters’
Against background of profound and diffuse non-recognition and humiliation, it is not surprising that people from these marginalized and demeaned communities would be drawn to narrative interpretations of the world that would address and explain their humiliation and offer a way out, however pathological, however much such interpretations may involve substituting for their experience of humiliation an imaginary vision of the world that can seem to restore each person’s sense of recognition and value, channel the rage resulting from the long legacy of collective humiliation into purifying violence, and bring into imaginary being the “perfect” society that once existed until being destroyed and defiled by “unbelievers,” by those who might prevent the vision from being realized by denying or opposing it. When terrorists engage in mass murder, they seek to reverse the dehumanization that was done to them by dehumanizing their imagined oppressors while seeking to bring about the redemption of an imaginary world in which they will become healed, become recognized, become finally included and loved as they anticipated they would be from their earliest days. A psychological connection between terrorism and humiliation is clear. It is not hard to imagine humiliated young people believing that such powerful acts are the only way to avenge themselves, their families, or their people, regain control of their lives, and express the rage that comes from humiliating experiences.
__
Terrorism and internet:
The Internet is an electronic media that has been used to foster terror related activities by assisting with the self-radicalization process of individuals. This medium allows information to be easily distributed to those seeking conversion to a particular ideology. The activities include promotion of terror manifestos and ideology, attracting recruitment, psychological warfare, deceptions, communication and networking, fundraising, and attacks on the networks of security authorities. The Internet allows a person or group to appear to be larger or more important or threatening than they really are. The determining factor in whether terrorists turn to the internet or not is whether it promotes their goals. There are five goals of a terrorist organization, as defined by Ernest Evans, a research associate at the Brookings Institute. They are:
1. To publicize its cause on a regional and international level.
2. To harass and intimidate authorities to force them to make concessions.
3. To polarize society in order to bring down the regime.
4. To aggravate relations between states or nations.
5. To free political prisoners and secure monetary ransoms to finance their cause.
The internet is well-suited to publicity of any kind, and terrorists have used this aspect of it already to promote their goals. The other goals identified by Evans could also be achieved using the internet. For example, terrorists can harass and intimidate authorities using the internet in addition to or instead of traditional means. Technology and the Internet are being invoked in fearful terms because it is easier to point the finger there than unpack the multifold and complicated reasons behind these acts—the growth of hateful ideologies, racial and ethnic tensions, the ease of buying semi-automatic weapons, the long-term effects of an on-going war waged by drones, and twisted minds that embrace violence. Terrorists make extensive use of the World Wide Web to train, to finance and to distribute information. The Internet is a facilitator ‘par excellence’. We want a vigorous defence against any and all attempts by terrorists to threaten our way of life through the exploitation of the openness of the Internet and our enthusiastic embrace of all it has to offer. Accordingly, the Internet has become the theatre of operations in counterterrorism efforts.
_
Terrorist Attack Cycle:
The approach to analysing terrorist attacks begins with the premise that attacks do not just appear in a vacuum. While there are a wide variety of motives behind terrorist attacks, all terrorist actors follow the same five-step attack planning cycle: target selection, planning, deployment, escape and exploitation. Focusing on the attack cycle causes analysts to examine how the attack was conducted rather than just focus on who was responsible for the attack. By focusing on the mechanics of the attack an analyst can then begin to identify vulnerabilities in the attack planning cycle, points throughout the attack cycle where attackers can be detected and attacks thwarted before they can be launched. One of the other benefits of focusing on the “how,” rather than the “who,” is that it permits authorities to identify attackers as they are in the process of planning their attacks regardless of their identity. Terrorism is a tactic used by a wide variety of actors not only jihadist but also neo-Nazis, anarchists and others. When looking at the methodology of an attack, actors become vulnerable to detection if they are conducting steps along the terrorism planning cycle, such as conducting pre-operational surveillance or assembling improvised explosive devices. Looking at how an attack was conducted can also help an analyst determine the capabilities of a specific individual or group, what political actors might be supplying them and assess the capabilities of that terrorist actor in future attacks. An actor who is conducting unsophisticated attacks against soft targets will not be able to rapidly develop the capability to conduct sophisticated attacks against a hardened target without significant practical experience or outside training. Therefore rapid leaps in a terrorist actor’s operational capability are firm indicators that the actor has received external training. Conversely, analysts can also draw some firm conclusions from actors that possess the means to conduct large sophisticated attacks but that choose instead to execute smaller limited operations. The actors who engage in terrorism and the states that sponsor terrorism will change as the international environment changes, but terrorism will remain a fact of modern life. Understanding how attacks are carried out provides individuals and companies the ability to take common-sense measures to protect themselves and their employees from attacks.
________
________
Threat of Radical Islamic Terrorism:
The present problem of terrorism is based on an ideology and an ideology cannot be countered or killed through legal action or by mere condemnation. We have to develop a counter-ideology to overcome it. The violence begins from the mind. It must, therefore, be uprooted from the mind itself. This goes directly to the root cause of terrorism. Therefore, in order to eliminate this root cause we need to initiate our efforts by beginning from the right starting point. And this starting point is the re-engineering of minds of individuals by taking them away from the culture of violence and bringing them closer to the culture of peace. Terrorism will persist in one form or another until the ideology of violence is countered with another ideology based on peace. The ideology behind present-day terrorism is that, Islam being a political system, it is the duty of all Muslims to establish Islamic rule in the world. This thinking was not prevalent during the time of the Prophet Muhammad. It is a later innovation which was developed in the last few centuries by a handful of people. Having become widespread in the Muslim world today, it is leading to present-day violence. A large number of Muslims, and especially many easily influenced youth, have become obsessed with this ideology and are trying to establish the political rule of Islam, thinking it to be their ticket to paradise. Having failed to achieve this objective of establishing Islamic rule by the peaceful method, they have started resorting to suicide bombing, the idea being that if we cannot eliminate non-Islamic rule, then let us at least de-stabilize it and pave the way for Islamic rule. They believe that the West keep Muslims in poverty and imposes upon them a western culture deeply offensive to traditional Islam.
___
Radicalism versus extremism:
A key distinction is made between “radicalism” and “extremism”. Radicalism is seen as comprising two main elements reflecting thought/attitude and action/behavior, respectively: (1) advocating sweeping political change, based on a conviction that the status quo is unacceptable while at the same time a fundamentally different alternative appears to be available to the radical; (2) the means advocated to bring about the system-transforming radical solution for government and society can be non-violent and democratic (through persuasion and reform) or violent and non-democratic (through coercion and revolution). Crucially, radicalism is not violent or anti-democratic per se. It may be thought of as worrisome or undesirable, but it is not necessarily a threat. Extremists, by contrast, are never democrats. Their state of mind tolerates no diversity. They are also positively in favour of the use of force to obtain and maintain political power. The latter factor in particular makes extremism considerably more worrisome than “mere” radicalism. Radicalism does not necessarily lead to extremism. Behaviors or expressions can (inadvertently) communicate the intention or capability to commit a terrorist attack. Such pre-attack “indicators” can be used to improve police services’ ability to detect and interdict terrorist plots before they materialize.
_
The figure below shows distinction between radicalism and extremism vis-à-vis conceptual framework of pre-attack activities:
___
I quote from my article on terrorism. I do not believe that ‘religion has nothing to do with terrorism and terrorists have no religion’. Had there been no Islam, there would be no 9/11. Has there been no Sikhism, there would be no khalistan movement. Has there been no Christianity, there would be no IRA. Fundamentalism is often a form of nationalism in religious disguise. Religion is used by terrorists to kill innocents as religion provides them moral legitimacy and a cover up. In addition to spiritual reward of transcendence, religion may also offer benefits in the afterlife that can hardly be matched in this world. The change desired by radical Islamic terrorists is so badly needed that failure to achieve change is seen as a worse outcome than the deaths of civilians. This is often where the inter-relationship between terrorism and religion occurs. When a political struggle is integrated into the framework of a religious struggle, such as over the control of an ancestral homeland or holy site such as Jerusalem, failing in the political goal becomes equated with spiritual failure, which, for the highly committed, is worse than their own death or the deaths of innocent civilians. The terrible combination of nationalism, politics and religion has deadly consequences for the people.
__
ISIS displayed its ability to strike at the heart of Europe during attacks in Paris in November 2015 and Brussels in January 2016, while those trained by al-Qaeda carried out the January 2015 raid on the Charlie Hebdo offices (also in Paris). The potency of these groups is enhanced by their on-going ability to inspire small cells of radicalized supporters living in the West to carry out attacks on their behalf. The vast majority of plots in the West emanate from such supporters, who have claimed affiliation with a terrorist group without ever having travelled to popular safe havens such as Iraq, Pakistan, Somalia, Syria, or Yemen. It appears as though Mohamed Lahouaiej Bouhlel, the terrorist who killed 84 people with a 19-ton truck in Nice recently, was one such individual.
___
The Evolution from al Qaeda to ISIS:
In the decade before the September 11 attack, our intelligence consisted mostly of federal entities directing their efforts at nation-states and, to a far lesser degree, at al Qaeda. After the attack, we focused far more attention on al Qaeda and its leader, Osama bin Laden. Domestically, the FBI and large local law enforcement agencies began to expand their intelligence capabilities. Within a few years, the federal government added a new cabinet-level agency, the Department of Homeland Security (DHS). It received several billion dollars annually to distribute as grants to state and local entities to prevent, prepare for, respond to, and recover from terrorist attacks. The FBI and DHS began investing in preventive resources for states and localities, expanding the Joint Terrorism Task Forces (JTTF) and creating state and local fusion centers. The goals were better intelligence sharing among state, local, and federal law enforcement agencies, and more robust intelligence operations within larger, more sophisticated local agencies. As we changed, the terrorists also changed. Our foreign operations disrupted al Qaeda and killed much of its leadership, including bin Laden. In its place, ISIS emerged, filling the vacuum left by the American withdrawal from Iraq. Experts estimate that ISIS has between 40,000 and 200,000 adherents in over 20 countries and assets in excess of $2 billion. It has exploited the refugee crisis to slip terrorists into the West, who then execute ISIS-directed or -enabled terrorist attacks such as we saw in Paris and Brussels. Part of the difficulty in fighting ISIS comes from its use of modern technology. It uses a sophisticated social media program to recruit and influence Western Muslims to engage in “lone wolf” attacks, as in San Bernardino. The program has been effective; over six thousand Europeans and several hundred Americans are believed to have gone to the Middle East to train with and fight for ISIS. But use of encryption technology in ISIS-directed and -enabled attacks poses an even thornier problem, which was highlighted by the recent legal battle between the FBI and Apple over San Bernardino terrorist Syed Rizwan Farook’s iPhone.
___
Amateur terror attacks may mark a new chapter in Europe:
For several years, Islamic State (IS = ISIS) and al-Qaeda have exhorted followers via videos or messages to carry out such attacks using whatever comes to hand. In September 2014, Abu Mohammed al-Adnani, an ISIS spokesman who Western intelligence agencies have dubbed the group’s “attacks minister”, issued chilling instructions that some have since apparently followed. “If you cannot (detonate) a bomb or (fire) a bullet, arrange to meet alone with a French or an American infidel and bash his skull in with a rock, slaughter him with a knife, run him over with your car, throw him off a cliff, strangle him, or inject him with poison,” he said. Adnani said there was no need to “consult anyone” as all unbelievers were fair game: “It is immaterial if the infidel is a combatant or a civilian … They are both enemies. The blood of both is permitted.” The four attacks in two weeks claimed by the Islamic State — two in Germany and two in France including the slaying of the priest— have been terrifyingly different. The assailants’ weapons: a truck, an axe, a knife and a bomb. Their victims: revellers enjoying Bastille Day fireworks, commuters on a Bavarian train, bystanders at a music festival and the priest. The locations: from small towns to the major coastal city of Nice. The randomness of the attacks is making it even more difficult for security services to do their jobs because the potential targets are virtually limitless, as are the means and the profiles of perpetrators. “It’s a mass diffusion of the phenomenon, and it’s quite worrying that we’re seeing the attacks go in that direction,” said Raffaello Pantucci, a terrorism expert at London’s Royal United Services Institute. The new pattern is spreading fear in Europe, particularly in enclaves far from capitals like Paris and Berlin that once seemed the most likely targets.
_________
_________
Why Europe in general and France in specific face more terror threat?
France is an attractive target for radicalised Muslims because it is a bastion of the values they despise most. The French emphasis on secularism has outraged jihadists with the ban on the Islamic face veil causing particular anger. The country is also an epicentre of free speech where criticism of religion, including satire, is (rightly) welcomed. For most of us, this land of liberty is a resplendent symbol of civilisation and freedom. For the jihadists, it is a hated symbol of decadence. Inside the banlieues (banlieue means the outlying residential area of a city) where a modern generation of young Muslims often feels alienated from their host country, criminality and radicalisation abound, especially when militant Salafism is being preached in prisons and on the internet. It is no surprise that the country has sent as many as 1,800 recruits to fight with IS in Syria. In addition, France has taken an assertive stance against overseas Islamist extremism, sending troops to Mali, Afghanistan and Syria. Thus the great Republic is seen as a barrier to the warped fantasies of a Caliphate. The jihadist threat requires concerted action. The appalling attack in Nice, which killed 85 civilians, offers another horrifying reminder of the threat from Islamist violence. It is another terrorist assault on France that has already witnessed the killing of Jewish students and teachers in Toulouse, the Charlie Hebdo shootings and last November’s massacre in Paris. France is estimated to have 2,000 citizens involved in Syrian and Iraq jihadi networks and a further 3,800 individuals known to domestic intelligence services as “radicalised”, all watched over by just 3,200 intelligence officers. “The services are overwhelmed,” said Jean-Charles Brisard, head of the Paris-based Centre for the Analysis of Terrorism, “when you consider it takes 25 officers to provide round-the-clock surveillance on one individual, you can see the difficulty.” France’s terrorism woes stem in no small part from the intense marginalization of its massive Muslim population. Combine that with an overburdened French security apparatus that can’t seem to keep pace with the scale of potential threats—Islamic or otherwise—and the extent of French vulnerability quickly comes into focus. Solutions to such deep social and institutional failures, however, aren’t so easy to come by.
_
For nations already on maximum high alert, it is also severely testing security services, and putting more and more pressure on police. Being constantly on full alert is impossible. A single human on highest alert on a permanent basis will either self-destruct from adrenaline exhaustion or will decline into a haze. The same can be said for a police or security force. Its ability to endure a constant crisis posture is as limited as for a single person – because the force consists of people. One problem, experts say, is that detecting the attackers is not like sniffing out traditional terrorist cells. In Germany, for instance, two attacks were committed by asylum seekers — an axe-wielding Afghan teenager and a 27-year-old Syrian suicide bomber — who had pledged allegiance to the Islamic State. Both men appeared to provide pre-attack videos to the group before their assaults. But German authorities, at least for now, believe they were otherwise unconnected to the group, and officials are still probing the extent to which they radicalized on their own. As the terrorism threat mounts, meanwhile, police have become so overburdened that some in Germany are already discussing whether to call out the army to deal with counterterrorism operations. Police in Germany insist they are at their breaking point. “There can’t be any illusion when it comes to our capacities, especially when several cities are hit at the same time,” said Rainer Wendt, federal chairman of the German Police Union. “We need at least 20,000 additional police officers, but even that won’t do.” The problem, he said, is that the recent attackers were not part of sophisticated terrorist cells. “If ISIS did have structures in Germany, we would be able to monitor them,” he said. Wendt added that German police “long ago reached our limits” regarding the surveillance of terrorism suspects. “My estimate is that there are about 400,000 to 500,000 migrants in our country who are unregistered or have assumed a false identity,” Wendt said. He noted, for instance, that the Afghan attacker who on July 18 used an axe and a knife to injure five people, four of them on a Bavarian commuter train, looked older than 17, the age claimed on his documents.
_
It is also clear that IS is taking advantage of the migrant crisis in Europe. And that poses a formidable challenge for Europe. There is a “fundamental conflict” between European Union incentives and drives to promote openness and free movement of people and goods with privacy, which is in some ways in conflict with the responsibilities that each country has as a nation-state to protect the borders and securities of their nations and peoples. Europe’s open border policy allowing weapons and terrorists to flow freely into France – with at least two of the night attackers coming in from Belgium – means that there are now real fears that it is almost impossible for the intelligence services to keep track of the jihadi threat. In my view, if people want to defeat terrorism, they will have to sacrifice some freedom and some privacy. Remember, terrorists are using freedom and privacy to attack us. Sometimes individual rights need to be balanced against the need to protect collective security. For example, the right of freedom of movement can be subject to restrictions to protect national security if the restriction in question is the least intrusive means of effectively protecting national security. The global campaign against IS should be stepped up with increasing intensity. Intelligence must be co-ordinated to ensure that those who are on the radar of the authorities are intercepted and their plots foiled. Above all, France should learn some valuable lessons from their Israeli counterparts. For decades, the Jewish state has had to face a protracted threat from terrorism. Israel has used human intelligence to penetrate Muslim communities, using informers where necessary. In addition, her major public events have been properly protected with roads blocked off and city centres given multiple layers of security. Israelis cannot afford to be complacent about terrorism, and neither can Europeans.
_
Counterview is that jihadist threat not as big as you think:
The vast majority of the estimated 85,000 to 106,000 militants fighting with militant jihadist groups around the world are fighting for purely local reasons, for instance, trying to install Sharia law in northern Nigeria or trying to impose Taliban rule on Pakistan and Afghanistan, while only a small number of these militants are focused on attacking the West.
_______
_______
Combating Terrorism through Intelligence:
_
What is intelligence?
I have defined intelligence in my article ‘The Intelligence” posted on January 23, 2010 as ability to receive, understand, process, memorize, comprehend, rationalize, learn, think and judge various sensory inputs from environment in a given circumstance and come out with best possible solution to the problem posed by environment and/or perform better in environment. Here we are taking of intelligence in the perspective of security and national interest. Intelligence is a district type of activity aimed at increasing one’s knowledge of an opponent as well as data gathered by such activity, by penetrating opponent’s security system. “Intelligence” (derived from intellection, Lat.. Intellectio), means “knowledge capacity”, “understand”, “good understanding”, which was the meaning of “understanding”, “secret relationship”, “secret information”, and the phrase “service d’ intelligence” (intelligence service). To these meanings of intelligence we can add information processed: cognitively with a specific meaning for a beneficiary or can be defined as “a communication, news, news that make someone aware of a situation; clarification on a person or thing; all material of information and documentation, sources; each of the new elements in relation to the prior knowledge of the meaning of a symbol or group of symbols”. For a military it can mean knowledge of the enemy and can distinguish between to defeat and to lose because information means knowledge and knowledge is power. Analysts see it as a package of information pending for clarification, and policymakers consider they should be informed so that they can meet the needs, stated or understood. Walter Laqueur states in the book A world of secrets: The Uses and Limits of Intelligence that “the term intelligence refers to a body that collects information, and on the other hand, to the information that was processed and ready for use by consumer”. Intelligence gathers under the same umbrella the informational component of national security, internal and external policies, as well as certain aspects of international security in the case of global cross-entities (states, organisations). According to Melanie M.H. Gutjahr, intelligence is the process by which certain types of information considered important to national security are required, collected, analysed and presented to the factors of decision. Intelligence is the first line of defence against terrorism. It may guide activities for law enforcement, concentrates under cover actions and determines the scope of military operations. Thus the globalisation of war against terrorism strengthens warning capabilities by joining agencies of information in a multinational network of by various means-political, economic and military. The US has created a global coalition to combat terrorism.
_
Intelligence cycle:
The Intelligence Cycle is the process of developing raw information into finished intelligence for policymakers to use in decision making and action. The process of tasking, collecting, processing, analyzing, and disseminating intelligence is called the intelligence cycle. The intelligence cycle drives the day-to-day activities of the Intelligence Community. It starts with the needs of those who are often referred to within the Intelligence Community as intelligence “consumers”—that is, policymakers and other decision makers who need intelligence information in conducting their duties and responsibilities. There are five steps which constitute the Intelligence Cycle.
1. Planning and Direction:
This is management of the entire effort, from identifying the need for data to delivering an intelligence product to a consumer. It is the beginning and the end of the cycle–the beginning because it involves drawing up specific collection requirements and the end because finished intelligence, which supports policy decisions, generates new requirements. The whole process depends on guidance from public officials. Policymakers and other major departments and agencies of government–initiate requests for intelligence.
2. Collection:
It is the gathering of the raw information needed to produce finished intelligence. There are many sources of information including open sources such as foreign broadcasts, newspapers, periodicals, and books. Open source reporting is integral to intelligence agency’s analytical capabilities. There are also secret sources of information. Intelligence operations officers collect such information from agents abroad and from defectors who provide information obtainable in no other way. Finally, technical collection–electronics and satellite photography–plays an indispensable role in modern intelligence, such as monitoring arms control agreements and providing direct support to military forces.
3. Processing:
It involves converting the vast amount of information collected to a form usable by analysts through decryption, language translations, and data reduction.
4. All Source Analysis and Production:
It is the conversion of basic information into finished intelligence. It includes integrating, evaluating, and analyzing all available data–which is often fragmentary and even contradictory–and preparing intelligence products. Analysts, who are subject-matter specialists, consider the information’s reliability, validity, and relevance. They integrate data into a coherent whole, put the evaluated information in context, and produce finished intelligence that includes assessments of events and judgments about the implications of the information for the nation.
5. Dissemination:
The last step, which logically feeds into the first, is the distribution of the finished intelligence to the consumers, the same policymakers whose needs initiated the intelligence requirements. The policymakers, the recipients of finished intelligence, then make decisions based on the information, and these decisions may lead to the levying of more requirements, thus triggering the Intelligence Cycle.
_
Intelligence is information that is analysed and converted into a product to support a particular customer. Intelligence is both a process and a product and has played an important role in diplomacy and warfare throughout history. In the information age, intelligence has taken on an even greater importance. But in the popular media, the role, means, and purpose of intelligence is very often misrepresented at best. Only a tiny fraction of intelligence officers perform clandestine intelligence gathering. They don’t assassinate people, carry weapons or even wear trench coats. The vast majority of the intelligence community carries out its mundane tasks at a computer terminal and, while intelligence alone cannot stop the next terrorist attack, it is the critical first step in identifying and possibly preventing one. The work of intelligence against terrorism in the 21st century will be an arduous task, which will require a close look at new social and technological developments, an objective analysis of the new trends and threats, as well as much vision. Intelligence is essential in countering terrorism, in diminishing its tactical effects and strategic importance.
_
It should be remarked that intelligence in the field of counter-terrorism is different, and in many aspects a more arduous task, than the classical intelligence, military and political, against enemy or rival states. The lives of many people are in continuous danger, often in real time during the work of the intelligence agencies; the rules of the game are cruel, for the personnel involved and for the terrorists themselves; the moral and ethical problems involved more intricate. But as in the case of military and political intelligence too, countries and security agencies have faced strategic surprises, the most prominent being the sarin gas attack in Tokyo in March 1995.
_
The Elements of Intelligence:
The term “elements of intelligence” refers to dividing intelligence according to the types of activity involved. These are collection, analysis, covert action, and counterintelligence. Collection refers to the gathering of raw data through espionage, technical means, open sources, or in any other manner. After collecting information, some analyses of information are necessary in order to decide whether it is useful. Covert action is different than the other elements of intelligence. Covert actions seek to influence political events directly. In terms of intensity, covert action can range from persuasion or propaganda to paramilitary action. Counter intelligence seeks to protect a society against any harm that might be inflicted by hostile intelligence services. Counter intelligence involves denying certain information to adversaries. While the need for collection and analysis is generally understood and accepted, there is less acceptance of covert action as an appropriate intelligence function and less understanding of the critical importance of counterintelligence.
_
Counter-intelligence:
In the past, counter-intelligence in its traditional sense was defined as the specialised task of pre-empting efforts at intelligence collection, subversion and sabotage by other States , whether friends or foes. Now, counter-intelligence has acquired a new non-State dimension, which calls for a capability to frustrate the attempts of terrorist organisations, indigenous or foreign, to recruit and train new volunteers and acquire modern skills and equipment for use against the State.
_
Counter-terrorism:
Counter-terrorism (also spelled counterterrorism) (also called anti-terrorism) incorporates the practice, military tactics, techniques, and strategy that government, military, law enforcement, business, and intelligence agencies use to combat or prevent terrorism. The counter-terrorism page primarily deals with special police or military organizations that carry out arrest or direct combat with terrorists. Most counter-terrorism strategies involve an increase in standard police and domestic intelligence. The central activities are traditional: interception of communications, and the tracing of persons. New technology has, however, expanded the range of military and law enforcement operations. Domestic intelligence is often directed at specific groups, defined on the basis of origin or religion, which is a source of political controversy. Mass surveillance of an entire population raises objections on civil liberties grounds. Home-grown terrorists, especially lone wolves are often harder to detect because of their citizenship or legal alien status and ability to stay under the radar. To select the effective action when terrorism appears to be more of an isolated event, the appropriate government organizations need to understand the source, motivation, methods of preparation, and tactics of terrorist groups. Good intelligence is at the heart of such preparation, as well as political and social understanding of any grievances that might be solved. Ideally, one gets information from inside the group, a very difficult challenge for HUMINT because operational terrorist cells are often small, with all members known to one another, perhaps even related. Counterintelligence is a great challenge with the security of cell-based systems, since the ideal, but nearly impossible, goal is to obtain a clandestine source within the cell. Financial tracking can play a role, as can communications intercept, but both of these approaches need to be balanced against legitimate expectations of privacy. Most studies of counterterrorism ignore the vital role of intelligence, focus only on its most controversial aspects, or fail to recognize how counterterrorism intelligence differs from traditional intelligence issues. Many of the common criticisms of the CIA and other agencies misunderstand counterterrorism intelligence and what is realistic for gaining information on terrorist groups. In particular, the important role of signals intelligence, liaison relationships, document exploitation, and interrogation are overlooked. In addition, intelligence analysis and the relationship with the policymaker differ fundamentally for counterterrorism.
_
Counter-terrorism intelligence is of three categories:
1. Strategic: This is about the organisational set-up of the terrorists, their office-bearers, aims, modus operandi, source of funds, weapons and explosives at their disposal, contacts with external elements, including foreign intelligence agencies etc.
2. Tactical: This relates to their specific plans of action. This is also called preventive intelligence, which would enable the State to frustrate their plans.
3. Psychological: This covers details of the psychological warfare (psywar) propaganda of the terrorists against the State, which need to be countered, and data relating to the terrorists, which would enable the State to mount its own psywar against them. As examples of such data, one could cite indicators of discontent against the leadership in terrorist organisations, the use of coercive methods by them for the recruitment of volunteers, misuse of children for terrorist operations etc.
_______
Cost of intelligence:
In the wake of the tragic shootings in Paris, French police and intelligence agencies are being asked to explain why known militants—including one who had visited an al-Qaeda affiliate in Yemen several years ago—were not subject to intense surveillance before they launched terrorist attack at the offices of a French satirical weekly. The answer is fairly simple, if less than satisfying: it costs a lot of money to do so. A perhaps somewhat high estimate is that the full-scale surveillance of an individual for a year costs some $8 million. The costs of watching even 125 people in that way would add up to $1 billion—a sum that is one-third of the entire FBI counterterrorism budget. French police believe that, among prisoners alone, 200 would “merit attention” and 95 would be “dangerous” once released. Nor is malpractice evident in the fact that the surveillance of some terrorist suspects is relaxed over time. Very often, would-be terrorists lose their enthusiasm for the enterprise. As terrorism specialist John Horgan has pointed out, walking away from terrorism is a common phenomenon. It is not that they necessarily abandon their radical views, but that they abandon violence as a means of expressing them. Policing agencies must therefore pick and choose carefully. At any one time there could easily be thousands of plausible candidates for scrutiny, and many of them may well seem to be more threatening those who actually committed terrorist mayhem in Paris. Under the influence of what might be called “the 9/11 Commission Syndrome,” in which all terrorism leads are supposed to be followed up on, government agencies chase more than 5,000 “threats” in the United States every day. The vast majority of this activity leads, of course, to nothing, and the massive enterprise is often called “ghost-chasing” in the FBI, an agency that may have pursued well over 10 million leads since 2001. The enterprise leads to only a very small number of productive investigations—there are only 100 or so arrests on terrorism charges in the United States each year, and most of these are of would-be terrorists who are either trivial or at most aspirational. However, in addition, there will be a considerable number—thousands or even tens of thousands—who are deemed suspicious enough to watch. At that point, budgetary considerations must necessarily come into play. Investigators can afford to give only a few the full surveillance treatment. When something like the French tragedy happens, policing and intelligence agencies are urged to work even harder to ferret out potential terrorists in our midst—in other words, to heap even more hay onto the haystack. That is certainly an understandable reaction, but it almost never comes associated with even the barest elements of a rounded analysis. On average, one or two people have perished per year since 2001 at the hands of Islamic terrorists in the United States and in France, less than that in Canada and Australia, a bit more in the United Kingdom. Under present circumstances, then, the likelihood a citizen in those countries will be killed by a terrorist is one in millions. Whatever the fears of French police have been, terrorism in their country, looked at rather coldly, has not resulted in many deaths. The question then becomes, as risk analyst Howard Kunreuther put it shortly after 9/11, “How much should we be willing to pay for a small reduction in probabilities that are already extremely low?” In seeking to answer that key question, it should be kept in mind that terrorism often exacts considerable political, economic, emotional, and psychic damage that may not be inflicted by other hazards, natural and unnatural. Moreover, it is worth considering that terrorism in the developed world might suddenly increase in frequency and intensity. However, this would be a sharp reversal of current patterns, and the terrorist surge would have to be massive to change the basic calculus. As with crime, perfect safety is impossible, a rather obvious point that is nonetheless often neglected. Funds directed at a hazard that kills few might sometimes be more productively directed at one that kills many. Terrorism’s very high cost combined with its very low probability make stopping terrorists as difficult as finding a needle in a haystack.
____
U.S. spends over $16 billion annually on counter-terrorism:
The Washington Post published details of the nation’s top-secret intelligence budget, based on documents provided by former intelligence contractor Edward Snowden. The documents show that, for the 2013 fiscal year that ends Sept. 30, the intelligence community requested a total of $52.6 billion, with $16.6 billion (31.6%) of that designated for counter-terrorism efforts. In fiscal year 2012, the United States spent $17.25 billion on counter-terrorism. Since the terrorist attacks on Sept. 11, 2001, the United States has spent more than $500 billion on intelligence, according to The Post. Can any developing nation spend so much money on counter terrorism? The 2013 budget request was about twice the size of the estimated 2001 budget (in constant dollars), the paper said. In terms of money spent, monitoring and disrupting violent extremists and suspected terrorist groups is the intelligence community’s second-biggest mission objective, after warning U.S. leaders about economic instability, societal unrest and other critical events around the world (which takes about $20 billion). Other priorities include preventing the spread of weapons of mass destruction, protecting U.S. computer networks and defending against foreign espionage.
________
Priorities within the intelligence services in the fight against terror:
The intelligence services continue to collect more information in the attempt to discover and discourage terrorists. A huge amount of information, however, does not necessarily make it easier to predict acts of terrorism as the processing of information is time-consuming. The intelligence services should therefore prioritise the processing of information higher than they do today.
There are three levels where intelligence agencies work:
1. Strategic level
The top level where the intelligence services advice and inform the politicians in order for them to make decisions on strategy, including overall priorities and allocation of resources.
2. Operational level
The medium level where the intelligence services advice and inform the ministries in order for them to establish targets and framework, as well as allocate resources for the executive branch.
3. Tactical level
The lowest level where the intelligence services supply government agencies with information about possible terrorists and their plausible targets. This makes it possible to solve specific tasks to prevent or counter terrorism.
Intelligence should be divided into categories of plausible acts of terrorism that the authorities should prevent immediately and with tough means, and other issues that can be resolved with more gentle and long-term efforts. The intelligence services should prioritise tactical analysis to prevent imminent acts of terrorism and generally prevent terrorism from happening.
_______
Focus on intention and not capability:
U.S. intelligence knew in November of 1941 that the Japanese fleet was moving about the western Pacific. I mean, they were watching the fleet. They couldn’t quite figure out the intentions until December 7. In Europe, in November of 1944, American intelligence and British intelligence knew the Germans were massing forces in and around the Ardennes. They didn’t know why until the Battle of the Bulge. In 1990, we were aware Saddam Hussein was making unusual movements of armoured forces in his country, in various places. We didn’t know why until he invaded Kuwait. You know, how many times does that have to happen before you realize that intelligence on intentions is very difficult to ascertain. Understand the duties of intelligence agencies. Of course, we have to know about people’s capabilities. We have to know about their capacity to injure us. But more importantly, we would like to know their intentions. Most intelligence focuses on capabilities, but the capabilities required by a terrorist are readily available and transportable. You cannot track capabilities because virtually anyone could be capable of an attack. The Middle East is awash with explosives. And some of the explosives can be made in Europe, from fairly common material by those who know how to do it. And such people are readily available and can’t be identified as bomb-makers just by looking at them. The intelligence challenge is to identify those with the intent to carry out terror attacks and ability to access the material. Identifying both is critical. And the problem of intelligence is that it must assume that anyone might be a terrorist. Intelligence of this sort is a process of discarding. You begin with the assumption that you have no idea what you are looking for, and over time you find the basis for dismissing some, then more and then focusing on a few. This sounds reasonable, until you consider that the process requires you to examine virtually everyone. If everyone is suspect – and they should be – then everyone is subject to examination and no one has the right to privacy. The problem is that terrorism, by its nature, gives out limited signals. It can be carried out by very few people. It requires little money and limited communication. So how do you find the terrorists? To the extent they can be found, it requires a massive intrusion into society. Since there is no exchange of millions of dollars, you must inspect transactions of $500. Since there is no massive flow of product, you must subject all cars to inspection. Obviously, there is one common denominator in this group of radical Islamic terrorists. They are Muslims and for the most part – but not exclusively – from a region ranging from North Africa to the Middle East to Afghanistan. That is a common denominator but actually not a very useful one. If they were more numerous they would be easier to catch. One of the strategies of terrorism is to keep the number of terrorists extremely small. If they expand and communicate with others, they will be detected. So given the number of Muslims in Europe, the exclusion of innocent Muslims from the profile you are looking for still leaves a number that dwarfs police security intelligence and the army as well. Racial profiling doesn’t work because terrorists aren’t stupid. So what would work given the resources available? The most important measure would be the penetration of the command structure of terrorist organizations with spies. Some would sneer at this, saying it is old fashioned and that technical means of intelligence from satellites to telephone intercepts are superior. However, the electronic search for the infinitesimal will identify some terrorists, but not the most dangerous. They understand that every credit card transaction is being fed into the system, and every car rental and every phone call is being tracked. Even if this isn’t true, they must assume it. Human intelligence is required to win the trust of the members, carry out terrorist (but not suicide) attacks and become one of them. Human penetration of IS by reliable sources with access to all levels of the organization is stunningly difficult and likely to fail as well. But if it works, it is the one way the enemy might lower its guard. Security cannot defeat terrorists. It mainly can determine timing. Electronic intelligence will capture some of the less capable terrorists. Human intelligence requires people from the region prepared to undertake staggering risks, and doing it flawlessly.
_______
Effective intelligence gathering systems are necessary to law enforcement in the fight against terrorism. The greatest weakness of modern liberal nations in their defense against terrorism is their reluctance or inability to see subversion as a problem until it is too late. It is commonplace to assert that the ability of an open society to deal with terrorism depends on its intelligence capacity. With the developing threat of terrorism in the world, counter-terrorism assistance programs as well as close intelligence and law enforcement relationships have been instigated with many nations in order to prevent terrorist incidents or resolve them in a manner that will deny the terrorists political and financial benefits from their actions. A well-developed intelligence capability may provide authorities with information concerning upcoming terrorist operations, permitting them to take steps to avert the incident or at least to minimize the damage, as well as aid in the apprehension of suspected terrorists and their prosecution. Activities that can be undertaken by intelligence organizations include the surveillance of suspected terrorists, the infiltration of terrorist movements, the development of informant networks, the design and implementation of contingency systems to respond to terrorist threats, the collection storage and analysis of information as well as direct counter terrorist warfare. Since terrorist operations are covert, efforts to obtain this information must also be largely covert. There is almost no debate as to the need to place a high priority on intelligence collection against terrorist threats. Because lives are at stake, the timely acquisition of tactical intelligence on planned or suspected terrorist attacks is vital if adequate counter measures are to be effective. Intelligence is comprises of a wide range of activities. There are various methods of collecting information, and there are different techniques for analyzing the information that has been collected. Some of these may be similar to the methods the social sciences use, while others, such as decoding of encrypted messages, are peculiar to the intelligence world. Some of the activities may also be similar to law enforcement work, such as investigating and trailing suspected foreign intelligence agents to learn about their activities. Using encryption to protect communication is another intelligence activity. There are also some ways to deceive adversaries such as “double agent” operations and transmitting of fake messages. Given these wide-ranging parameters, two broad categories of intelligence collection are used, human intelligence and technical intelligence. Technical Intelligence (TECHINT) and Human Intelligence (HUMINT) are the two main intelligence collection methods that can be used to combat terrorism. Human intelligence refers to the gathering of information by human sources, rather than through modern technical apparatus. Recent advances in technical intelligence have proven their use in gathering information and in many ways TECHNIT has grown to supersede the use of human intelligence efforts. However, important question remain regarding the effectiveness of solely relying on TECHNIT in the face of growing terror threats. Is technical intelligence enough in and of itself to provide law enforcement with the necessary and trustworthy information to combat domestic threats, or are human intelligence types of collection techniques necessary to support this intelligence? Although advances in TECHINT capabilities have reduced the need for HUMINT, the fact remains that HUMINT is the oldest, cheapest and most reliable method for gathering information. There have been numerous occurrences of intelligence failure in cases where only one method of intelligence gathering was used.
_____
HUMINT:
Human intelligence (HUMINT) refers specifically to the “collection of information for intelligence purposes from humans, and related documents”. Human intelligence (frequently abbreviated HUMINT) is intelligence gathered by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as signals intelligence (SIGINT), imagery intelligence (IMINT) and measurement and signature intelligence (MASINT). NATO defines HUMINT as “a category of intelligence derived from information collected and provided by human sources.” Typical HUMINT activities consist of interrogations and conversations with persons having access to information. Sources may be neutral, friendly, or hostile, and may or may not be witting of their involvement in the collection of information. “Witting” is a term of intelligence art that indicates that one is not only aware of a fact or piece of information, but also aware of its connection to intelligence activities. The manner in which HUMINT operations are conducted is dictated by both official protocol and the nature of the source of the information. Within the context of the U.S. military, most HUMINT activity does not involve clandestine activities. Both counter intelligence and HUMINT do include clandestine HUMINT and clandestine HUMINT operational techniques. HUMINT can provide several kinds of information. It can provide observations during travel or other events from travellers, refugees, escaped friendly POWs, etc. It can provide data on things about which the subject has specific knowledge, which can be another human subject, or, in the case of defectors and spies, sensitive information to which they had access. Finally, it can provide information on interpersonal relationships and networks of interest. HUMINT is both a source of positive intelligence, but also of information of strong counterintelligence value. Interviews should balance any known information requirements of both intelligence collection guidance and of counterintelligence requirements. Human intelligence has some limitations compared to technical sources. The identification and recruitment of potential agents takes a long time. Also, communication and control are always problematic issues. It is very hard for the controller to make sure that the agent doesn’t lie or fabricate evidence.
_
Human intelligence today has emerged as a prime tool in effectively curbing the menace of terrorism. The power of human information was on acute display during the Cold War when the very tool of human intelligence acted as a deterrent. A similar analogy can be drawn in the present times when human intelligence can be effectively used to monitor terrorism activities. A marked feature of terrorist groups is the existence of “sleeper cells”. These sleeper cells remain dormant with its members going on about their daily lives until they are activated. Once they are activated they carry out the orders given by their bosses and execute terrorist activities. This is the reason why we see normal people with simple lives executing gruesome attacks. Indoctrinated in the school of violence they wait to execute their plans. And no amount of technology can detect these sleeper cells and their movement. And it is at this juncture where human intelligence becomes important. A successful example of the power of human intelligence in India has been the ‘mukhbir” scheme in Mumbai. After 1993 attacks in and around the city where vested interests sitting in the foreign decks remote controlled attacks in the city, the Mumbai police department was at a loss. They decided to give impetus to the “mukhbir” scheme where informants were placed in every area and their movements and information was regulated on the local police station level. A decentralised strong informant system worked wonders for the police. Between 1993 and 2005 Mumbai didn’t see any major terrorism attacks and the success was largely attributed to the human intelligence network. Effective schemes like protection of the mukhbirs and security to their families ensured that the system worked on a robust strong and effective framework. The informants had complete knowledge and control on the information that flowed in the ground level. For example if arms were transported in the Mumbai docks, if RDX was being moved or if any sleeper cell was being activated, these informants would immediately inform the police and the impending terrorist strikes would be averted. However after 2005 this robust network began to crack and by 2007 it almost ceased to exist. And tragically after that Mumbai has become a victim of one terrorist strike after another. While a direct analogy between human intelligence and terrorist strikes cannot be drawn, yet it can be said with a certain absolute certainty that such robust human intelligence network indeed acts as a deterrent to the impending terrorist strikes. An average citizen, working as an information vigilante would be a powerful deterrent to the terrorist who would not be able to decide whom to belief. Thus human intelligence indeed is a powerful medium to combat terrorism but yet it cannot refute the effectiveness of technical intelligence in today’s world. As the war of terrorism moves from the street to the information highway of the internet, technical intelligence plays a crucial role in counter-terrorism.
_
Intelligence officers work secretly in order to be able to garner information from different sources. They must have a plausible reason for being in the country. This may include a clearly visible source of financial support, which can be used as a pretext for meeting people with access to information. Sometimes an intelligence officer is disguised as a diplomat or some other kind of governmental official. This is called as official cover. Nonofficial cover refers to any other types of disguise that could explain why the officer is in the host country, such as businessman, journalist, tourist, etc…However, official cover has several drawbacks. Most important among these is that the host countries’ counter intelligence service may be able to determine fairly precisely which “diplomats” are intelligence officers and which are not. Also, nonofficial cover has too much difficulty. One method is to persuade a private organization to allow an intelligence officer to pose as a member of its staff. There are various collection techniques and different collection sources for HUMINT. Like intelligence officers, intelligence sources also can be classified. Some groups of people volunteer to assist the intelligence agency, whereas recruited sources are generally considered more reliable, since the intelligence officer has had a chance to study their character and motivation before attempting to recruit them. Sources to be recruited are chosen according to their ability to access to the desired information. On the other hand, volunteer people can be used by host countries intelligence service to pass false or misleading information. In addition to classifying sources, we can also distinguish among the reason for why they provide information. Sources may be motivated by ideological, ethnic, and religious loyalties that are stronger than their ties to the countries of which they are citizens. They may be disillusioned by the actions or ideologies of their own countries. They may be greedy. They may be somewhat unbalanced people who wish to bring some excitement into their lives. They may desire to avenge what they see as ill treatment by their government. They may be subject to black mail. The relative importance of these motives depends on the characteristics of the societies involved and on the tactics of the opposing intelligence services.
_______
Importance of Human Intelligence in War against terrorism:
One of the major reasons of the failures in the Global War on Terrorism is the human intelligence failure. Without credible information we cannot win this war. Knowledge of the enemy cannot be gained by reasoning from other analogous cases or by any deductive calculation. Knowledge of the enemy can only be achieved by entering his area and deploying spies in the enemy area. Knowledge of the enemy’s dispositions can only be obtained from other men. Modern technology like satellites, GPS, surveillance drones have their limitations which cannot be 100% accurate as compare to the human intelligence which is based on primary source. Encryption makes traditional counterterrorist intelligence collection methods more difficult, requiring renewed investment in human intelligence (HUMINT) collection. The uncovering of recent terror plots, including the arrests in Europe and the detection of letter bombs targeting synagogues in the US can be credited to human intelligence. More recently, humint’s importance was highlighted by the fact that many terror plots in France have been foiled thanks to it, according to a member of France’s main counter-terrorism force. The modern day terrorist is adept at counter-surveillance skills, and the efforts made into training terrorists to cover their tracks have paid rich dividends. It is important to note here that while terrorists may be ingenious in their usage of modern tools, they are essentially low-level technicians, with only a minority engaging in communication systems which can be traced and monitored. The difficulties faced by law enforcement agencies in relying on modern intelligence gathering methods was admitted by US Defense Secretary Robert Gates in 2009 when he stated that it was years since he received useful intelligence on the whereabouts of bin Laden. This is traceable to bin Laden’s judicious use of modern communication technology, relying more on human couriers. It is reported that bin Laden stopped using his satellite phone as early as 1998 when he realized that his conversations about the African embassy bombings were being monitored. In uncovering recent plots, intelligence was garnered through interrogations of captured suspects. But intelligence services have also infiltrated or bought up members of terrorist groups. The infiltration of terrorist cells has helped counter-terrorism officials to gain good intelligence on the activities and membership of a group, and they have also been used in the execution of terrorist leaders. For example, the Israeli security agencies used a local contact to replace Hamas bomb-maker Yahya Ayyash’s phone with an explosive device which killed him in 1996. One of the problems with using human intelligence sources is the difficulty in infiltrating a terrorist organization due to obvious fears of detection and murder of the asset. In one instance, Egyptian security forces blackmailed their assets in an attempt to assassinate Aymaan al-Zawahiri, the leader of the Egyptian Islamic Jihad. The plan backfired with Zawahiri surviving and executing his betrayers. Gaining assets in jihadist groups is particularly difficult owing to their allegiance to a larger community based on faith rather than a solitary-cause movement. For example, the member of a pan-Islamic jihadist group owes allegiance to the Ummah (Islamic community) beyond the group. Under these circumstances getting him/her to betray the cause becomes even more difficult. The fear of being double-crossed by an asset also plays on the minds of his/her handler. A member of a terrorist group used as an asset by intelligence agencies can cause significant damage because of his/her ability to play both sides. This was most effectively demonstrated in the case of Humam Khalil Abu Mulal al-Balawi, a Jordanian doctor, who was recruited by the CIA to infiltrate al Qaeda in Pakistan. Balawi scheduled a meeting with his CIA handlers in an American base in Afghanistan, and when he arrived he blew himself up, killing seven Americans. Significantly, the attack killed senior veterans of the CIA, and has been described as a serious blow to the agency’s efforts in the region. The setbacks faced in using human intelligence tools should not come in the way of expediting their recruitment for intelligence gathering. Human intelligence should not be limited to intelligence and counter-terrorism agencies, but adopted at the grassroots levels of policing. Cooperative community policing being adopted worldwide is indicative of this trend. A key element to bolstering the intelligence apparatus should be developing cooperation between the different security wings. Human intelligence should be shared quickly and followed up with equal speed, as this could be the game changer in a ticking time bomb situation. The example of the Nigerian bomber’s father, who tried to warn the authorities about his son before he attempted to bomb a plane bound for the United States, is a case in point.
_________
TECHINT:
Technical Intelligence Collection (TECHINT) refers to a group of techniques using advanced technology, rather than human agents, to collect information. These include: Photographic or Imaginary Intelligence (PHOTOINT); Signal Intelligence (SIGNINT); Communication Intelligence (COMINT); Electronic Intelligence (ELINT); Telemetry Intelligence (TELINT); Measurement and Signature Intelligence (MASINT); and Intelligence Collection from Computers and Internet (HACKINT). Collection platforms can range from the mundane to the exotic. For a modern, technologically advanced intelligence community, the decision about which platforms to use and in what combinations is principally a product of two assessments: Which platforms can best collect the desired intelligence? Second, what are the relative costs and risks involved in using particular platforms? Colossal amount of information can be fished out from across the world using TECHINT using decrypting techniques, traffic analysis, computer exploitation techniques, cable and phone tapping, remotely piloted aircrafts, satellite pictures etc. Technical intelligence does not stop at the weapons or the technical finesse of the enemies. It must also seek out the source of those weapons and also the production capabilities of that source and how the money has been routed. Thus technical intelligence effectively encompasses the “white collar” division as well. It has been often found that “Hawala money”, participatory notes has been used to promote terrorist activities in India. The security establishment must make concerted efforts to address these sources of money and how it has been utilized in terms of procuring weapons. Such economic intelligence converged with the technical finesse can strength the security establishment to a large extent. Today modern warfare is not limited merely to guns and bombs; it has transgressed into domains like biological weapons and chemical weapons. In such a scenario it becomes all the more important to have an idea about the strength of the enemies. For example in the event of an anthrax attack, mere guns and bombs would not be able to mitigate the effects. Scientific research coupled with remedial measures is the key in the event of such an attack. And to have such a mechanism we must have a fair idea of the weapons the enemies possess beforehand. Thus technical intelligence not only acts as a deterrent but also as an effective tool of mitigating the threats posed by terrorism.
_
Thus seen in totality human intelligence and technical intelligence are important building blocks towards building an effective tool to combat terrorism. And this can be achieved when there is a perfect synthesis between the two. Both HUMINT and TECHINT are crucial disciplines of intelligence system of any nation. However with unprecedented advancement of technology, TECHINT has superseded HUMINT in terms of usage and is now more widely used method of collecting intelligence. There are certain drawbacks of HUMINT, which has resulted in decrease in reliance over this discipline of intelligence. HUMINT involves identification, screening and recruitment of agents which is a time consuming process. Also a human is considered to be more vulnerable and impressionable which may lead to compromise and a resultant fabrication of information. Besides, there is a huge risk to life involved because of high susceptibility of the informant or agent to the counterintelligence units. There are many aspects in which TECHINT has a clear advantage over HUMINT. TECHINT is solely reliant on advanced technological equipment with minimum human interference which makes it easier and less risky to derive information. A high degree of covertness can be maintained while carrying out a TECHINT operation without any risk of getting misleading or fabricated information. Also, the process of information collection is less time consuming while a high level of accuracy can be maintained. Nevertheless, technology also has its own limitations, as it is extremely expensive to develop and can be countered using certain measures by the terrorists. For e.g. an underground hiding of terrorists cannot be easily gauged and detected by satellite pictures or remotely piloted aircrafts. Considering the above viewpoints it is critical that a synergy be maintained between HUMINT and TECHINT. The intelligence derived from any of the techniques should be substantiated or complemented by the other technique. The intelligence community should not disregard HUMINT as its capability of providing first-hand information cannot possibly be substituted by any other means and cannot become out-dated. Relying solely on a single form of intelligence might result in intelligence failure, the cost of which is generally paid by the innocent citizens. An example of a debacle caused by relying only one form of intelligence is the Pearl Harbour bombing, in which the US did not have any HUMINT contribution. The US has paid a high price in 2001 when relied mostly for electronics and computerized intelligence, rather than human intelligence. We need to recruit specialists in foreign languages to all national security and intelligence agencies that belong to the ministry of interior or defence. France should rely more on human, rather than computerized intelligence and needs to recruit more specialists for its security and intelligence agencies to tackle terrorism. Hence both HUMINT and TECHINT have their own importance and place in the intelligence system and both should be used utilised complementarily in order to foil the attempts of terrorist groups in creating a menace around the globe.
_________
The figure below shows classification of intelligence against terrorism:
__________
__________
Mass Surveillance will not stop Terrorism:
In response to the terrorist attacks in Paris, the U.K. government is redoubling its efforts to engage in mass surveillance.
Then Prime Minister David Cameron wanted to reintroduce, the Communications Data Bill—which would compel telecom companies to keep records of all Internet, email, and cellphone activity. He also wants to ban encrypted communications services. Cameron seems to believe terrorist attacks can be prevented by mass surveillance. Brothers Said and Cherif Kouachi and Amedy Coulibaly, who murdered 17 people, were known to the French security services and considered a serious threat. France has blanket electronic surveillance. It didn’t avert what happened. Police, intelligence, and security systems are imperfect. They process vast amounts of imperfect intelligence data and do not have the resources to monitor all known suspects 24/7. The French authorities lost track of these extremists long enough for them to carry out their murderous acts. You cannot fix any of this by treating the entire population as suspects and then engaging in suspicionless, blanket collection and processing of personal data. Mass data collectors can dig deeply into anyone’s digital persona but don’t have the resources to do so with everyone. Surveillance of the entire population, the vast majority of whom are innocent, leads to the diversion of limited intelligence resources in pursuit of huge numbers of false leads. Terrorists are comparatively rare, so finding one is a needle-in-a-haystack problem. You don’t make it easier by throwing more needleless hay on the stack. It is statistically impossible for total population surveillance to be an effective tool for catching terrorists. Even if your magic terrorist-catching machine has a false positive rate of 1 in 1,000—and no security technology comes anywhere near this—every time you asked it for suspects in the U.K. it would flag 60,000 innocent people. Law enforcement and security services need to be able to move with the times, using modern digital technologies intelligently and through targeted data preservation—not a mass surveillance regime—to engage in court-supervised technological surveillance of individuals whom they have reasonable cause to suspect. That is not, however, the same as building an infrastructure of mass surveillance. Mass surveillance makes the job of the security services more difficult and the rest of us less secure.
_________
_________
Intelligence sharing:
Intelligence sharing is the ability to exchange intelligence, information, data, or knowledge among federal, state and local, intelligence & law enforcement agencies to facilitate the use of actionable intelligence to a broader range of decision-making. The main problem lies in the inability of intelligence services of different European countries to coordinate their actions. For instance, it turns out that situation, when a criminal who committed the attack in one country had already been considered suspicious by the security forces of a neighboring state, occurs quite regularly. So why don’t employees of intelligence agencies share information with their colleagues to prevent terrorist attacks and ensure security? After each new terrorist attack, there are calls to improve coordination between the intelligence agencies of various EU countries so that they could closely work together, share available data and prevent terrorist attacks in the future. Back in January 2015, after the attack on the editorial office of Charlie Hebdo, it was promised that the exchange of intelligence information within the EU would be intensified. The recent attacks, however, show that little has changed in this regard in practice. European intelligence agencies still treat each other with suspicion and follow the old principle — “intelligence has no friends, only competitors.” Thus, French intelligence officers are reluctant to share data with the Germans, Spaniards — with the Brits, and all together they are afraid to give out valuable information to the new members of the EU — in order to prevent its leakage to Moscow. Another issue here is the principle of state sovereignty. The problem lies in the very concept of the state and its functions. The most important duty of a sovereign state is to ensure the security of citizens. It is impossible to imagine a situation in which German police will track someone on the territory of Belgium. Why then do we need the Belgian State? European intelligence agencies not only don’t want to negotiate with each other, but often just can’t do it as different countries have different systems of transliteration of Arabic names. The problem is also complicated by the fact that intelligence services usually have very few people who speak Arabic. Unfortunately, there is also still a bunch of other difficulties which hamper efficient coordination and share of available data between intelligence agencies. In every country, there are usually dozens of intelligence agencies which compete with each other, have their own databases and their own networks of agents. The failure of such system is clearly visible on the example of the US. After the 9/11 attacks it turned out that two of the terrorists were registered in the lists of the CIA, but the latter didn’t even bother to transfer the information about them to the FBI. It is easy to imagine the scale of the chaos in the countries where not two or three, but dozens of special services are involved in intelligence and counterintelligence activities.
_
Intelligence sharing and the fight against terrorism in the EU: lessons learned from Europol: 2016 report:
Ex-post investigations of major terrorist attacks in Europe have highlighted the contradiction between the seemingly free movement of terrorists across Europe and the lack of EU-wide intelligence sharing. The recent terrorist attacks in Belgium and France have once again highlighted the contradiction between the seemingly free movement of terrorists across Europe and the lack of EU-wide intelligence sharing. Due to their earlier criminal activities, most perpetrators of the attacks in both Paris and Brussels were known to the various security agencies in several EU member states. For instance, the Abdeslam brothers had run a café in Brussels that was notorious for drug peddling. In early 2015, Belgian police questioned them about a failed attempt to travel to Syria, but they were not detained. Soon after, Dutch police stopped them during a routine traffic check, fined them €70 for carrying a small quantity of hashish and then released them because they were not listed in their national information system. Allegedly neither the French security agencies nor the EU coordinating agency, Europol, were informed of either of these incidents prior to the Paris terrorist attacks in November 2015. Similar stories of information non-sharing have emerged in the aftermath of other major terrorist attacks in Europe since the Madrid bombings in 2004. In response, EU policymakers have repeatedly promised to improve intelligence sharing across Europe, and some have even floated the idea that Europol should be turned into a centralised EU criminal intelligence hub, akin to the US Federal Bureau of Investigation (FBI). Although there is a clear need for borderless intelligence sharing as a response to borderless terrorism, Europol is highly unlikely to become a genuine intelligence agency in the foreseeable future. It is one thing for Europe’s politicians to make public promises to improve the fight against terrorism via better intelligence sharing across Europe, and quite another thing for them to persuade the relevant national agencies, over which politicians usually exercise less than perfect control, to comply.
_____
After terror attacks, push for better, more centralized intelligence agencies in Europe:
There has been a familiar refrain, criticizing intelligence and security agencies in Europe after recent terrorist attacks. After the bombings in Paris and Brussels, the Nice truck attack and attack on a parish church in northern France, observers have wondered why intelligence agencies weren’t able to better coordinate and ultimately act to prevent the tragedies before they happened. It is imperative that government intervene in this area to better coordinate our intelligence, to develop the territorial intelligence and better national intelligence. In broad terms, the push to improve intelligence agencies has generally followed three lines of thought: 1) Better centralize intelligence gathering 2) Increase the sharing of information and 2) Upgrade the state’s ability to conduct surveillance and wiretapping. But the sharing of information only works if there is information to share. On that front, Belgium has had some success in reforming and strengthening its security laws. For example, until just a few months ago, house searches could not be done between the hours of 9 p.m. and 5 a.m. Law enforcement also now have expanded powers to wiretap suspects.
__
Intelligence agency versus investigation agency:
Intelligence agencies provide the most sensitive protective security shield for a country. They mostly operate in shadows, develop sources and penetrate the enemy to prise out information that could be vital for the very survival of a country. They have many successes, and the best among them have their share of failures. Sadly, the successes never get reported, to protect sources and ongoing operations, but their failures are always projected in the media to their detriment. Investigation, on the other hand is a process that takes place after an event, and therefore mostly a post mortem of the incident. If the investigation has been professionally done, and the case vigorously prosecuted, the case ends in conviction, bringing laurels to the agency. But is this the only true picture? Are Intelligence agencies always at a disadvantage vis-à-vis Investigation agencies? Do Investigating agencies produce intelligence that can be used in operations prior to an event? Do Intelligence and Investigating agencies work closely, sharing vital information? Do Intelligence agencies across the world always share information that is vital for each other’s country?
_
Sharing information vs. protecting the source:
Why do intelligence and investigative agencies differ?
Prior to 26/11, Headley visited India several times, the last in July, 2008. Sometimes he flew into India from Pakistan, and sometimes from other international ports. But each time he returned to Pakistan from India. This, as it now appears, was to brief the Lashkar and ISI handlers, of his trips to Mumbai, and the various targets that had been identified for the assault. It is now known that the Americans had warned their Indian counterparts of a likely seaborne attack on Mumbai and that Taj Mahal Hotel, and places frequented by foreigners, and especially Americans, were potential targets. The U.S. warnings in September, 2008, caused Indian anti-terror officials to meet with management of the Taj, and beef up security. It is also reported that as late as on 18 November, 2008, the Americans advised their Indian counterparts about a suspicious vessel related to a potential maritime threat to Mumbai. Of course they did not identify the source of the information. It is also not clear whether this information was passed on the basis of inputs from Headley, his wives, or other sources or even a combination of these sources. There are two scenarios. Headley may have been working with the Americans, or they may have been tailing and following his correspondence with his handlers in Pakistan through telephone and email interceptions. In either case, it would be unfair to expect the Americans to share Headley’s details with us. Had they done so after Outalha’s (his ex-wife) warnings, it is possible that Headley would have been intercepted either during his April or July, 2008 visits to India. The publicity that such an action would have generated would have killed Headley’s utility as a source for the Americans, with or without his knowledge. Would the Americans protect their source, in their strategic interest, or try and save lives that were likely to perish in the Lashkar’s attacks on India? Can we find fault with the Americans for not exposing their operations, which are vital for their country?
_
Do Intelligence and Investigation agencies share vital information pertaining to national security?
An instance that comes to mind is the 9/11 assault on the twin towers of New York by the al-Qaeda. One of the finest accounts of this tragic incident is Lawrence Wright’s ‘The Looming Tower: Al-Qaeda and the Road to 9/11’. Wright has, after extensive and thorough research, established that there was failure in sharing crucial information due to entrenched agency cultures of the CIA and the FBI. According to Wright’s account, had the CIA shared with the FBI vital information regarding whereabouts of several persons they were tailing, who finally participated in the 9/11 attacks, the tragedies may well have been prevented. And the FBI and the CIA are both agencies that are pledged to protect the United States of America and its people. The non-sharing of information was a mistake, or due to other professional reasons is something that the Americans would have analysed and dealt with appropriately but such incidents do happen all the time. Intelligence agencies would like to get the maximum out of their operations. They fear that sharing inputs prematurely would jeopardise their operations. They intrinsically dislike Investigation agencies which are open, and are accountable to the courts, leading to publicity. Getting entangled in courts is something that the Intelligence sleuths shudder at. The power of arrest and interrogation under law is vested only with Investigating agencies. They can further go for extensive searches and unearth much more, and more quickly, than Intelligence agencies, and can be more effective. Intelligence agencies have to conduct their operations secretly, and this imposes severe restrictions on their capabilities. Probably there is need to share certain type of information at some level, in the national interest which is certainly above the interest of any one agency, in order to prevent such deadly attacks on the nation. Who is to decide the level, the type or class of information to be shared, and the exact time that such information needs to be shared, will have to be separately worked out.
_
Sharing information and intelligence: Is that desirable?
There is a need to develop trust, respect and regard among officers of the Intelligence and Investigation agencies, with a healthy respect for each other’s strengths and problems, if they are to work in tandem. And is that desirable? The answer would be ‘yes’ to this question, on the basis of field experience. Rajiv Gandhi’s assassination could not be prevented. Investigation of the assassination was done by the special investigating team of the CBI. It was a blind case, and initially there were several suspects. However, diligent and scientific investigation soon established the manner in which the assassination was carried out by a human bomb, along with the nature of the improvised explosive device used. The role of the LTTE in the assassination was soon established. Tremendous efforts of the investigators were ably supplemented and complemented by Indian Intelligence agencies. The chase of the assassin squad became focussed when they started receiving real time inputs from clandestine wireless communication between the leader of the squad, Sivarasan, and his boss, Pottu Omman who was based in Jaffna, from the Intelligence agencies. This communication subsequently became the best part of the evidence marshalled by the special investigation team of the CBI against the LTTE in the court of law, as it had material to establish the preparations the LTTE made to target Rajiv Gandhi in Chennai, and its subsequent efforts to smuggle Sivarasan and his core team out of India. It was the best evidence of the conspiracy hatched by Prabhakaran, the LTTE chief, and his intelligence chief, Pottu Omman, to assassinate Rajiv Gandhi. India was able to get this vital evidence, thanks to their Intelligence agencies. Investigations were able to generate intelligence about the various moves of the assassin squad in and around Chennai, and later, Bangalore, where they were finally tracked down. But at one stage, the investigators came across a blank wall, as there were no leads forthcoming. There was constant pressure on the team to produce results, both in the media and in Parliament. They were trying to locate an LTTE cadre, a wireless operator going by the code name, Dixon. He was the person who had managed to link up with Sivarasan, who was confined in his hide-out in a remote part of Chennai due to aggressive publicity, and had enabled his being taken out of Chennai by the LTTE and its few supporters. Thanks to Intelligence agencies, investigators were able to procure a photograph of Dixon from their records, and the moment they published it, they started getting information from the public about Dixon’s location in Coimbatore. Very soon, Tamil Nadu police were able to locate the LTTE’s hideout, and then they were able to get further leads that eventually took them to Bangalore and Sivarasan’s lair in Konanakunte where they committed suicide. The close, successful collaboration of the Intelligence and Investigation agencies in this case is a case in point. Less than a year before the assassination of Rajiv Gandhi, on 19 June, 1990, in a violent, terrorist action using sophisticated grenades and AK-47 rifles, the LTTE massacred the EPRLF leader Padmanabha and 12 of his colleagues in the heart of Chennai. This was one of the unsolved cases that they looked at during the investigation of the Rajiv Gandhi case. After they made a breakthrough in the case, and made the first arrests on 11 June, 1991, Bhagyanathan, Nalini’s brother, told them that Sivarasan was involved in the Padmanabha killing also, and that his LTTE code name was Raghuvaran. The agencies were on the trail of Raghuvaran, who they knew as one-eyed and belonging to the LTTE’s intelligence group, in connection with the Padmanabha case. Even though Sivarasan @ Raghuvaran started visiting Chennai from September, 1990, while preparing for the Rajiv Gandhi assassination, and set up at least three hideouts in and around Chennai, he could not be located by the Intelligence agencies. Had the Padmanabha case been investigated on professional lines as was done in the Rajiv Gandhi case, with the Intelligence agencies supplementing the efforts of the Investigating agency, it should have been possible to establish the identity of the killers with a no-holds barred investigation involving arrests and searches. A successful investigation of the Padmanabha case would have stopped the LTTE in its tracks, and prevented the Rajiv Gandhi assassination. Unfortunately, when such assassinations take place, the Intelligence agencies come under severe pressure, both from the authorities and the media, and try to take cover. There are instances when the Intelligence and Investigating agencies then get into a competition to prove who is better and more effective, to the detriment of both, and the national interest. This is the time when they have to pool their limited resources, and strike at the adversary decisively. Synergy in professional dealings, invariably produce the best results. It has to be realized that professional investigation of sensitive cases impinging on national security is as vital as intelligence functions in securing the nation. This is the role of the newly established National Investigation Agency. But it is vital for overall success that the NIA and Intelligence agencies work in close collaboration with each other in order not to miss out on vital leads that may help prevent an incident, or solve a case.
_________
_________
Military intelligence in counter-terrorism:
First, there is a real danger in the phrase “military intelligence.” The fact is that particularly when we are dealing with asymmetric warfare terrorism and insurgency, military intelligence is not the approach any country should use to the problem of intelligence or any military should use in the approach to intelligence. We need what we call “fusion;” we need to understand that the military has to operate in a much broader context. They need to know what the civil authorities are doing. They need to work with law enforcement and police. To do this, you need to break down compartmentalization. You need to avoid the horrifying tendency to over-classify which seems to be one of the few universal human values. We need creation of common counterterrorism centers that force us to bring together all the elements of intelligence along with law enforcement. The breakdown of artificial bureaucratic barriers and classification is absolutely critical. If you have not done this, you have created the recipe for failure. If you have not practiced it in operation, you will probably fail the first time you encounter a truly serious challenge. When we talk about counterterrorism, it is not simply a military task, it is as much a problem of deterrence and response as it is active defense. The targeting intelligence design for a regular military operation is the perfect way to lose in counter terrorism or counter insurgency. You must have a fundamentally different level of targeting. You must focus on collateral damage, you must focus on civilian casualties, and you must focus on popular perceptions. And you must calibrate what you are doing in terms of whether you are winning rather than destroying the enemy. America failed to do this early in Iraq. It took us some years to adapt. America failed to do it in Afghanistan for nearly eight years and the price was almost immeasurably high in empowering the Taliban. One of the lessons Americans have consistently learned from Afghanistan is it was not the presence of foreign troops that the Afghans resented. It was two things: it was first civilian casualties, particularly from air strikes and artillery; and second, the failure to understand the technical victories that abandoned the people, that left them open to the Taliban, were dismal failures, because people saw no reason to regard the military as their protectors, as distinguished from the threat. We have seen similar results in other countries including Iraq. When you kill people, deprive them of their living, drive them out of their homes and blow them up, you have sent a very powerful message in strategic communication that in fact enhances terrorism or insurgency. Again, moving very quickly is a way of using extremely expensive toys. There are some countries which are rushing to acquire remotely controlled aircraft and combat vehicles. What they do not understand is, as is the case with many intelligence assets, if you do not have enough of the assets and enough of the people to use them properly, they actually blind you to establishing the military intelligence present with things like Special Forces on the ground. The person with the most toys does not win. The person with the best mix of military intelligence assets does. To conclude, fusion is everything. Begin by using military intelligence to support the police and paramilitary where this is possible, address the full range of tasks, understand the need for quick reaction civilian-military programs, focus on winning the population not tactical encounters or killing terrorists, and focus on key figures rather than the broad structure of terrorism so you can attempt to destroy the network, but above all understand the role of military intelligence. Like military operations, it is to shape the population’s rejection of terrorism and insurgency. It is not to conduct operations as if the people were part of the landscape and could somehow be ignored.
_
10,000 ISIS fighters killed in military airstrikes as counter-terrorism measure:
It’s been many months since the United States mobilized a coalition and launched a campaign of airstrikes against the Islamic State of Iraq and Syria. Despite the strikes hitting more than 6,200 targets, it has been difficult to measure the coalition’s success against ISIS. A senior U.S. official offered one measure of progress when he told a French radio network that airstrikes had killed 10,000 ISIS fighters since the campaign began. While that number seems substantial — given that estimates released by the CIA in the fall suggested ISIS had between 20,000 and 31,500 fighters — it might not be as significant as it initially appears. Even before airstrikes began, ISIS controlled major cities in Iraq and Syria, but the bombing campaign has yet to substantially slow its ability to launch new assaults and expand its territory. Just as troubling, analysts say, the death toll suggests ISIS is much bigger than Western intelligence first assumed. If 10,000 killed is accurate, then that means all the estimates of ISIS strength from the fall were wildly inaccurate. The issue is how many innocent civilians were killed in these airstrikes and whether local populations of ISIS occupied cities support airstrikes or support ISIS.
______
______
Artificial intelligence against terrorism:
Artificial intelligence (AI) applications in the field of counter-terrorism are among the fastest growing components of security programming for both government and corporate entities. One of the most important applications for artificial intelligence in the field of counterterrorism is the processing of collected data. You cannot wage a traditional war against terrorists, but a key to fighting terrorism is good intelligence. The only way to protect our citizens and apprehend terrorists before they execute their plans is to know what they are planning in advance. One of the chief obstacles in this battle is not only the acquisition of the necessary intelligence from the various types of surveillance that our government agencies employ but the ability to process all of this data and recognize patterns and relationships. Computer programs that have the ability to not only collect and sort millions of bits of random data, but to recognize how they relate to each other, are invaluable in the fight against terrorism because no human being has the ability to process the enormous amount of information that our intelligence agencies receive. Without the ability to process the information, the information is useless. Artificial intelligence is increasingly used in combination with physical surveillance. Instead of just having a person observing a bank of security monitors, an AI-enhanced CCTV system has the ability to identify potential problems itself and alert security personnel. These systems have been used in cities like Chicago and London for years. The ability to recognize aberrant or suspicious behavior or even facial recognition capabilities that some of these systems possess is extremely useful in fighting terrorism and capturing known terrorists and criminals. Even though AI-enhanced security systems like surveillance cameras have been used with some success, these systems often fail to exceed their human counterparts, as they can recognize red flags but lack “total picture” judgment. For example, a person standing a couple of feet from his or her suitcase for more than a few minutes at an airport could set off an alert with an AI-monitored camera system, whereas a human being looking at the same scenario would know that there is not yet a cause for concern. This can result in a “boy who cried wolf” scenario where too many false alarms cause alarms to be ignored. So, while artificial intelligence in all of its many forms is a very useful tool in the fight against terrorism, there is still no substitute yet for human beings. Computer programs are only as good as the information that they have received and, thus far, are only capable of recognizing patterns of events similar to those that have already taken place. They are not able to take the information that they have and extrapolate from that to predict events of a type that are not already programmed into their pattern-recognition algorithm, nor can they take information that they are programmed to recognize as a threat and then make a judgment, as humans can do. We have seen the results of becoming too reliant on technology in the aftermath of Sept. 11, when we realized too late that we had too few agents in the field who could infiltrate terrorist rings, and too few agents who were fluent in the necessary foreign languages. For years, the U.S. government had relied on technology at the expense of “boots on the ground” intelligence, going so far as to view experience living abroad as a negative for new recruits. Computerized surveillance systems were less costly in terms of both blood and treasure, and safer in terms of political fallout from captured agents. That technology was not enough, however, and we are still trying to catch up many years later. The field of artificial intelligence is advancing rapidly and will continue to have many applications in the fight against terror. At the present time, however, the advancements in these types of programs are not so great that we can depend on them to replace human beings who possess the ability to use logic, imagination and judgment.
________
________
Policing:
It is becoming clear that the police have an important role in preventing terrorism. They are in a good position to learn about and investigate local terrorist threats, and they can work to ensure that vulnerable targets in their jurisdictions are protected. Filling the first of these functions, investigation of terrorists, will require police to extend their normal community policing activities and improve their handling of information. Filling the second function, protecting vulnerable targets, will require greater adjustments. They will need to become more expert in crime prevention and security matters, and they will have to develop partnerships with businesses and a wide range of public and private agencies. However, these changes are consistent with current best practices in policing. In the aftermath of recent terrorist incidents, police executives and administrators are faced with two constraints: public fear and financial burdens. They are being forced to respond with creative and innovative methods in policing. There is a silent, but fundamental shift in police response to public safety; a replacement of the dominant police strategy, community policing with a new policing model emphasizing tactical methods, technology, and alternative service providers, such as private security personnel.
_
The Role of the Police in Counterterrorism: high policing and low policing:
Although few people would argue that the police should not be involved in counterterrorism, their precise role is unclear and indeed controversial. Some are concerned that expanding the police role in counterterrorism will change the character of policing in democratic states. In particular, that police will emphasize covert prevention of terrorism to the neglect of publicly visible policing of individual criminal victimization. Policing of this kind has been called “high policing”. High policing has two distinguishing features – its substantive focus and its methods. High policing targets what might be called macro-crimes, that is, crimes that are considered threats to society in general, such as drug trafficking and an illegal immigration, as opposed to micro-crimes that affect only individuals. In high policing, prevention is the key objective, utilizing the tactics of covert intelligence gathering, surveillance, and disruption. “Low-policing,” by contrast, emphasizes prevention through visible patrolling and deterrence through the application of criminal law. High policing differs sharply from the standard practices of normal or “low” policing because it is less transparent, less accountable, and less careful with respect to human rights. In general, high policing encourages a top-down command structure and changes the orientation of police from servicing to controlling the population. At the same time, other people argue that full-service or general-duties policing should play a large role in counterterrorism, indeed, that it has unique advantages in a war on terror that should be exploited. For example, general-duties policing provides unprecedented access to communities. Properly focused, it can obtain information about activities that are the precursors of terrorism. Furthermore, by being responsive to the mundane concerns of individuals, it raises the likelihood that the public will assist the police by providing information or accepting direction in the event of disasters. More particularly, routine policing can build bridges to communities that may shelter or give rise to terrorists. In short, the activities of low policing are not a distraction from counterterrorism but an essential “force multiplier.”
_
It is impossible to say with confidence whether the war on terrorism has changed the character of policing in developed democracies, in particular whether high policing has significantly impacted low policing. The evidence is fragmentary and impressionistic. It appears that specialized capabilities, especially for intelligence gathering and analysis, have been augmented in all countries. It is not at all clear how much traditional frontline policing in the form of uniformed patrol, response to calls-for-service, and criminal investigation has been. If we ranked the countries of along a continuum from transformative impact to no impact at all, the impression is that general policing has been affected most in Israel and least in the United States. Despite 9/11, American police seem still be to searching for their role in counterterrorism. After convening three executive roundtables, the IACP observed that they had “failed to identify a body of promising practice information that even began to approach what was needed…or, more important, to supply the field with hoped for response to post 9/11 change and conditions”. Among the other English-speaking democracies, Great Britain seems to have adapted its policing more to the requirements of counterterrorism due largely to the terrorism associated with the “troubles” in Northern Ireland during the last 35 years. Australia, Canada, and New Zealand, cluster toward the American end of and India tends more to the intermediate position. Countries in Western Europe range somewhere in the middle of this continuum.
_
The critical question is whether a shift to high policing, especially by general-duties police agencies, in Western democracies should be applauded or prevented. There are reasons why uniformed, general-duties police should take on a greater role in the prevention and control of terrorism, in addition to their inevitable role in responding to terrorist events and ameliorating their impacts. Local police can be enormously helpful in detecting terrorist-related activity, building bridges to informants in critical communities, and in coordinating security responses between public and private agencies. At the same time, acting as high police may come at a cost that policy makers and the public should be aware of. It may lead to a decline in crime-prevention services to the general public and undermine the investigation of ordinary crime, thereby separating itself from the population in general and reducing the possibility of obtaining useful information about terrorist activities. Taking stock of the advantages as well as the disadvantages of using general-duties police in counterterrorism, I think that they can contribute more by focusing and fine-tuning their standard operations than by creating specialized high policing capabilities. Customary activities by regular police represent a unique capacity for intelligence gathering while, at the same time, serving as the frontline for risk assessment and first-responding. But to do all this, the police will have to be cautious. There is no free lunch, and significant involvement by local police in high policing can come at a significant cost. This suggests that low policing and high policing should be conducted by separate personnel and perhaps by different levels of police. Such an approach would prevent high policing from overwhelming the low police functions that are crucial for the development of police legitimacy, thus serving the objectives of public safety against all threats, ordinary crime and disorder as well as terrorism.
_
Counterterrorism by police involves more than covert intelligence gathering and prevention. It can take ten distinct forms of activity: covert detection, disruption/dismantling of plots, risk analysis, target hardening, community mobilization, protection of persons and infrastructure, emergency assistance after attacks, order-maintenance during and after attacks, mitigation of damage, and criminal investigation of incidents. Whether general police agencies undertaken covert counterterrorism is a function of six factors: whether terrorism has occurred locally, governmental level at which policing is organized, size of police agencies, duration of exposure to terrorism, cultural tolerance of political dissent, and availability of new resources. Uninformed, general-duties police can contribute to covert counterterrorism in several ways: observation and contact during routine patrolling and law-enforcement, analysis of crime patterns indicative of terrorism preparation, forming partnerships with local businesses and communities of interest, using local knowledge to assess the validity of intelligence produced by specialized counterterrorism agencies, contributing local expertise in covert surveillance and penetration, and developing informers through leverage over local criminals. At the same time, there are distinct disadvantages to using general police in covert counterterrorism: drawing scarce resources from traditional activities of serving and protecting, diverting local police talent and expertise from normal duties, undermining the legitimacy of local police by associating them with covert operations, and changing the mind-set of policing from viewing the public as clients to be helped to suspects to be watched. On balance, police agencies with general responsibilities for order-maintenance and crime prevention can contribute more to counterterrorism by focusing on their standard operations than developing specialized, particularly covert, counterterrorism capabilities.
________
Policing methods:
Scholarly literature suggests there are various primary policing models that are relevant to law enforcement officers and the fight against terrorism.
_
1. Israeli Policing Model:
The first is the Israeli Model for Policing Terrorism, which emphasizes the role of local police agencies in collecting intelligence on terrorist networks, apprehending terror operatives, and protecting likely targets. For example, the Israeli Police work to prevent acts of terror by conducting patrols, raids, as well as working to increase public awareness. The positive benefit of this model is that the citizens of Israel, over time, have become more aware of their surroundings and possible terroristic threats. For example, Israeli citizens are educated by the police to be cautious and to report any item left unattended in a public setting that may possibly contain an explosive device. Such potential explosives include the pressure-cooker bombs that exploded near the finish line of the 2013 Boston Marathon. Allegedly, these bombs were concealed in two unattended black nylon padded knapsacks or duffel bags. Regrettably, as a result of the explosions, several people were killed and other bystanders and race participants were seriously injured. Perhaps this tragic event may have been prevented had public awareness been heightened by law enforcement to report unattended bags, as put forth in the Israeli Model. While the Israeli policing model has proven to be effective, there is scepticism about how this style of policing would be received by citizens in the United States. In Israel, this style of policing has led to on-going tension between the public and the Israeli police force. According to a 2014 RAND Corporation report, “Even with relatively low crime rates, the public in Israel perceives an increasing threat to personal security and concern over the quality of police service.” Perhaps the on-going tensions between the public in Israel and the Israeli police can be attributed to the fact that police are a national law enforcement force with national jurisdiction. This is unlike the United States, where law enforcement powers are based on federalism, which creates both federal and state law enforcement agencies. In Israel, there is only one national all-encompassing police agency with total jurisdiction, similar to a military force. This may add to the public perception that Israeli police are distanced from addressing local community concerns or needs, which is heightened by the fact that Israeli police are more focused on terrorism-related crimes than local crime and efforts to build positive community relationships. Additionally, some citizens may feel threatened or fearful when they observe or encounter police officers wearing paramilitary-style police uniforms. An appearance and demeanour that some citizens feel do not convey partnership or collaboration with the public. This is a reasonable concern as studies similar to the Milgram and Stanford Prison Experiment show that wearers of these kinds of uniforms may begin to act the way they perceive a wearer of such a uniform should act. This is known as deindividuation. In other words, it is believed that police officers wearing a paramilitary-style uniform on the job may be inclined to display unnecessary militaristic and aggressive behaviors in the performance of their duties.
_
2. Intelligence Led Policing:
Intelligence led policing, on the other hand, is a policing model that has more ties to community policing and community-oriented policing strategies, which have been used in the United States for the past three or four decades. Perhaps this is why in the United States the Intelligence Led Policing Model is emphasized in the fight against terrorism more so than the Israeli policing model. The intelligence-led policing model focuses more on working collaboratively with the public. In order for intelligence led policing to be successful in gathering actionable intelligence, officers on the street must work to build close relationships with community members as well as share that information with other agencies. For example, when looking at combating street crimes (such as burglary or robbery) one community may have three home robberies within a week. A neighboring community, county, or state might have five or six similar burglaries within the same period of time or shortly thereafter. Information obtained from local residents and crime scene investigators about those crimes needs to be shared within departments as well as with other local, state and federal agencies. The similarities pertaining to the various crime scenes are then analyzed using strategic and tactical analysis. Data that has been thoroughly analyzed via strategic and tactical analysis benefits police officers and investigators because it allows them to be more productive with their time. The reports furnished by analysts provide insight into where a crime, or a possible terrorist event, is more likely to occur or reoccur (i.e. geographically pertaining to location, as well as a potential time of day). These predictions are then shared within the law enforcement community and various federal agencies to apprehend or deter criminals and/or terrorists from targeting a specific location. According to the International Association of Chiefs of Police, “community policing is a necessary component of homeland security.” Local police must work hand-in-hand with citizens to gather information in order to generate useful intelligence. Understanding the need to have a close relationship with the local community enhances law enforcement’s ability to obtain needed intelligence to identify pre-incident terrorism indicators.
_
3. Community policing:
The particular advantages of community policing are that it provides local communities with a degree of collective influence over how they are policed and that in acting to address locally defined problems, local officers are well placed to generate trust and collect community intelligence. This connecting of trust and intelligence is important in that in traditional covert intelligence methodologies, the significance of trust could be glossed over on the basis that an informant exchanged their information for a financial or nonfinancial incentive. The rather different overt intelligence methodology being developed by police renders generating and sustaining social trust far more critical. Given the long history of difficult relations between many minority communities and the police, it is probable that only a comparatively thin form of trust can be cultivated by police. Thin trust is always fragile, and in the particular context of counterterrorist work, tensions can easily develop between national security imperatives and local demands that have to be sensitively managed. Despite any such equivocations, on balance, it is an approach that, when compared with the alternatives, is more coherent with the key values of the liberal democratic tradition. This is notable given that the violence enacted by those affiliating to radical Islamic terrorists is intended to destabilize the legitimacy of and ultimately undermine democratic processes. If this diagnosis is correct, then it would seem that democratic principles mediated through the institution of policing may provide a mechanism to effectively counter those who would seek to use violence to disrupt and destabilize democratic order.
________
Prevention of Terrorism: The Role of Local Police:
Local law enforcement, given its deep community ties and frontline role in thwarting terrorist planning, is ideally positioned to use HUMINT methods to detect terrorist activities. Local police are the best personnel who can prevent the terror attacks by deactivating the sleeper cells and terror groups if they go after the basic principles of policing including patrolling, information gathering, and surveillance of suspects of the area concerned. They are the appropriate persons in a good position to find out and investigate local terrorist threats, and they can work to neutralize the sleeper cells and ensure that vulnerable targets in their jurisdictions are protected. There is no substitute for the policeman who walks the streets. He is the gatherer of intelligence, the enforcer of the law, the preventer of the offence, the investigator of the crime and the standard-bearer of the authority of the State, all rolled into one. If he is not there, it means that all these functions are not performed. Patrolling is the central aspect of policing, and constant patrolling by police forces establishes an official presence that enhances security and builds confidence in the people. Police have to opt for compassionate patrols in daytime, which go covert at night and track specific suspects, terror groups or sleeper cells. Specifically in alert times, to deter terror attacks, in an area where the terror alert is there, police have to inundate that area with number of small patrol groups working together focusing on useful target. For detecting the early activities of terrorists, gathering intelligence through the human intelligence (HUMINT) sources of local police would be the primary and valuable with respect to any specified area or any sensitive area. Nothing can happen without the knowledge of the local police station. Local police station officers have an everyday presence in their area concerned to protect. They know the people in their area by their races, religions and professions and they have an idea about local leaders to members of assembly and parliament. They always have the opportunity to communicate regularly with the local residents and business people, street vendors, hawkers and are aware of minute and fragile changes in the locality under their jurisdiction. Undoubtedly, local police is the primary source to keep the terror groups off balance, and the population reassured by neutralizing the terror activities and attacks to create an accommodating milieu. But short of visibility and response are damaging the policing and police are becoming ineffective in preventing terror related attacks and sleeper cell activities. However, police force is not supposed to be hold culpable and responsible for their incompetence and ineffectiveness because their hands are cuffed due to political interference, intimidation and patronage, also, shortage of man power. At this crisis time it is necessary not only for the politicians not to interfere in police acts related to terror activities but also rapid expansion of police forces with a modern outlook.
________
_______
Challenges and obstacles faced by intelligence against terrorism:
_
Intelligence failure:
Intelligence failure means failure of intelligent agencies to prevent terror attack.
Were the events of Sept. 11 the result of an intelligence failure?
Of course it was an intelligence failure. By definition, when something bad happens to you, and you didn’t know about it, it’s an intelligence failure. Every terrorist attack is a failure of intelligence. Poor coordination and lack of intelligence sharing between CIA and FBI; and too much reliance on technical intelligence rather than human intelligence led to 9/11 attack.
Brussels attack is a ‘failure of intelligence’: Belgian terrorism expert:
A Brussels-based terrorism and security expert said that attacks in the Belgian city were the result of a “failure of intelligence”. Speaking from Belgium, Thomas Renard, a terrorism expert at the Egmont Institute, a Brussels-based think-tank, said there had clearly been a “major failure” in the country’s security services. He said the fault could be down to a multitude of factors including a breakdown in interagency communication and co-operation, security authorities underestimating the threat posed by people of interest or whether too much emphasis had been put into the hunt for the Paris attackers, including Salah Abdeslam.
_
Legal blind spots:
The head of French domestic intelligence warned two months ago that Islamic State was likely to use car bombs as it sought to carry out more atrocities in France. DGSI director-general Patrick Calvar also predicted further terrorist outrages could provoke violence between far-right groups and France’s Muslim population. In May’s parliamentary testimony, Mr Calvar, 60, said the security service’s ability to track terrorists was hampered by three legal “blind spots”. These were the ability of terrorists to use encrypted internet software; a legal ban on surveillance of suspects once they had been charged with offences; and the ability of terrorists to travel undetected into and around Europe.
_
New encryption technology is aiding terrorists:
As the barbaric attacks in Paris, San Bernardino, Brussels, and Orlando have demonstrated, we need to enhance our capabilities to detect and thwart terrorists as they plan attacks. With the proliferation of off-the-shelf encryption technologies and other operational security measures, terrorists are becoming harder to find by traditional technical collection methods such as wiretaps and signals intelligence (SIGINT). Meeting this threat means investing in human intelligence (HUMINT) capabilities at home—not just at the federal level, but also at the state and local levels. The Edward Snowden leaks have accelerated the sophistication of encryption technologies by “about seven years,” Director of National Intelligence James Clapper told reporters. And that is not a development to be celebrated, he added in remarks at a breakfast hosted by The Christian Science Monitor. “From our standpoint, it’s not a good thing.” New, commercially available encryption software “had and is having major, profound effects on our ability” to collect intelligence, “particularly against terrorists,” he warned. That’s in large part because the Islamic State is “the most sophisticated user by far of the Internet.” They privately purchase software that “to ensure end-to-end encryption” of their communications. “And so that is a major inhibitor to discerning plotting, principally by ISIS and others,” Mr. Clapper said. The seven year estimation comes from the National Security Agency, he said. It raises the issue of the tension between the need for security against cyber-attacks – which as recently as February Clapper cited as a greater threat than terrorism – and the opposition to law enforcement against so-called unbreakable encryption software that, they say, could hinder their search for terrorists. Mobile phones contain “a wealth of information of potential great value to law enforcement.” But much of that data is now encrypted. Terrorists increasingly conduct their activities using encryption technology. The first reported case of an authorized wiretap being stymied by encryption came in 2011, and the intelligence community reports that the increasing use of encryption technology by terrorists is undercutting intelligence efforts. With court orders, law enforcement agencies can obtain metadata (e.g. phone numbers, call lengths, and location data) even for encrypted communications. But the substance of those communications remains hidden. As a result, SIGINT and wiretaps will likely show diminishing returns. Congress may pass legislation requiring US technology companies to provide law enforcement agencies with “back doors” to their encryption software. If this happens, terrorists will simply use encryption technologies developed by foreign companies. Given that terrorists may work around such back doors with relative ease, and that the back doors come at the expense of privacy, the best answer may be to protect encryption and find other ways to empower law enforcement agencies to preempt and disrupt terrorist attacks. When we decide to take the easy way out and paint technology in black and white terms, it can lead to insane outcomes, such as requests for “golden keys“ — backdoors to circumvent encryption that would leave all of our information more vulnerable to hackers. Law enforcement in France proposed banning the privacy tool Tor and, during states of emergency, shared and public Wi-fi. That would mean, during a time of fear, it would be even harder for people to communicate with loved ones. Thankfully, French Prime Minister Manuel Valls called this what it was: a terrible plan.
__
Terrorism, civil liberties and security:
In looking at civil liberties, and their reconciliation with the security of the State, a paradox is presented: it is that acts of terror thrive in the freedom of democracies. The freedom of association, expression and movement enjoyed in a liberal democracy are conducive to the planning and execution of acts of gross violence, designed to destabilise or destroy State structures, and to advance particular ideological ends. Innumerable themes are illustrative of the difficult juxtaposition of civil liberties and national security, in which a delicate balance may be less in evidence than a fervour for erosion of civil liberties in response to perceived crises. Detention without charge for years for suspects and extensive privacy incursions for the ordinary citizen have been considered necessary by States involved in a war on an intangible enemy – terror. But as the enemy is intangible so too are the contours of the front-line. Accordingly states engaged in wars against terrorist groups risk becoming engaged in a permanent state of emergency on their own soil. And so it is that the threat of terrorism in turn can pose a threat to the fundamental rights and freedoms which characterise democracy, the civil liberties and human rights upon which democratic societies are based. The greatest success the terrorist can achieve is to persuade the democratic state to abandon its democratic values.
_
Observers point to several major challenges that the Intelligence Community will likely encounter in supporting the counter terrorist effort.
1. First is a renewed emphasis on human agents. Signals intelligence and imagery satellites have their uses in the counterterrorism mission, but intelligence to counter terrorism depends more on human intelligence (humint) such as spies and informers. Any renewed emphasis on human intelligence necessarily will involve a willingness to accept risks of complicated and dangerous missions, and likely ties to disreputable individuals who may be in positions to provide valuable information. Time and patience will be needed to train analysts in difficult skills and languages. Counterterrorism is highly dependent upon human intelligence (humint), the use of agents to acquire information (and, in certain circumstances, to carry out covert actions). Humint is one of the least expensive intelligence disciplines, but it can be the most difficult and is undoubtedly the most dangerous for practitioners. Mistakes can be fatal, embarrass the whole country, and undermine important policy goals.
2. Second, terrorist activities pose significant analytical challenges. In addition to acquiring analysts with esoteric language skills, intelligence agencies must develop expertise in many third world areas that had been of peripheral concern in years past. Much of the data available will be in open, unclassified sources that intelligence agencies have often neglected.
3. Third is the closer relationship between intelligence and law enforcement agencies. In counterterrorism efforts, intelligence agencies work alongside law enforcement agencies that have far different approaches to gathering evidence, developing leads, and maintaining retrievable databases. Policies and statutes are being modified to facilitate a closer relationship between the two sets of agencies, but closer cooperation has raised difficult questions about using intelligence agencies in the U.S. and about collecting information regarding U.S. persons. Countering terrorism requires close cooperation between law enforcement and intelligence agencies; some terrorists will need to be brought to justice in courts, but others are dealt with by military forces or covert actions. In recent years, important steps have been taken to encourage closer cooperation between the two communities, but some believe terrorist acts may have been facilitated by continuing poor information exchanges between intelligence and law enforcement agencies and by blurred lines of organizational responsibility.
4. Finally, military operations against terrorists will reinforce requirements for collecting and transmitting precise intelligence to military commanders or operators through secure communications systems in real time. The growing reliance of military operations on the availability of precise intelligence is well understood, but the availability of collection platforms such as reconnaissance aircraft, unmanned aerial vehicles, and reconnaissance satellites has been limited throughout much of the past decade. Such platforms are especially important for counterterrorist operations. Military operations to counter terrorism are dependent on the availability of precise, real-time intelligence to support bombing campaigns using precision guided munitions. The linkage between sensor and “shooters” will be crucial as will access to global geospatial databases.
_
There are other challenges in countries such as France, where police forces were reduced several years ago because of spending cuts and a desire to streamline a complex array of law enforcement agencies. Also, security services are largely focused on Paris — where the majority of the roughly 10,000 soldiers deployed in the country’s counterterrorism operation are based. Also a problem is that government agencies do not coordinate across jurisdictional lines.
_________
Lone wolf:
“Lone wolf” is a term popularized in the 1990s by white supremacists Tom Metzger and Alex Curtis, who called on like-minded people to commit uncoordinated acts of terror. Some of the deadliest of the predatory species have been white racists: Norway’s deadliest killer Anders Breivik, Austrian letter bomber Franz Fuchs, “London Nail Bomber” David Copeland, Charleston church shooter Dylann Roof, Oklahoma City bomber Timothy McVeigh. It’s likely, though, that their ideologies only ran skin deep, just as radical Islam does for the recent killers of Middle Eastern and North African extraction.
_
A lone wolf or lone-wolf terrorist is someone who prepares and commits violent acts alone, outside of any command structure and without material assistance from any group. However, he or she may be influenced or motivated by the ideology and beliefs of an external group, and may act in support of such a group. Attacks in Orlando, Nice, Munich and elsewhere have raised public awareness of lone attackers, most of whom are unaffiliated with an organized terrorist group. Leaderless resistance, by reducing the need for coordination and communications that could be intercepted and traced, affords a greater level of operational security. But many people fail to understand that attacks conducted under the leaderless resistance model are not completely spontaneous. Would-be terrorists still need to follow the steps of the terrorist attack cycle (vide supra), and there are places throughout that cycle where they are vulnerable to detection. The operational security benefits of operating alone come at a steep price. Grassroots attackers operating under that model generally possess far less sophisticated terrorist tradecraft than their professional counterparts who belong to organized groups and have received training. Because of this, grassroots attackers are even more vulnerable to detection as they run through the steps of the terrorist attack cycle than a professional terrorist cadre. Furthermore, if they are acting alone, they must conduct every step of the attack cycle themselves, rather than assign individual steps to different personnel to reduce vulnerability. The limits of working alone also mean that solo attacks — such as the July 18 axe attack in Wurzburg, Germany — tend to be smaller and less damaging than those conducted by professional terrorists. There are exceptions, of course, including the July 14 truck attack in Nice, France, or Anders Breivik’s 2011 deadly vehicle bomb and gun attack in Norway. But most solo attackers tend to be more like stray dogs than lone wolves. This is especially true when they make amateur mistakes, particularly in areas such as pre-operational surveillance and weapons acquisition. Poor tradecraft has led to a number of thwarted plots. It has led others to seek help acquiring weapons or explosives, luring them into government sting operations. But the government cannot be everywhere at once. The number of dedicated counterterrorism agents is limited. These agents also, naturally, tend to focus most of their efforts on preventing large-scale attacks by professional operatives. Judging from the lack of such attacks (at least in North America and Australia), they are doing a good job.
_
Framework for Lone Wolf Radicalization and Mobilization:
Figure above demonstrates how personal, social, and political grievances increase susceptibility to extremist ideology, influence an individual’s worldview, and ultimately justify violence as a tool for political change.
_
Amateur terror attacks may mark a new chapter in the ISIS war in Europe:
Following the latest attack — the brutal slaying on 26’th July 2016 of a small-town priest in France — the violence has felt almost like the start of the uprising that the Islamic State has been attempting to spark among its sympathizers in the West for years. The attackers have included mentally disturbed individuals inspired by the extremist group — which has in recent months increased its calls for “lone wolves” to act. But other assailants may have maintained at least indirect contact with the group. Adding to the chaos, there have been two additional highly violent attacks in Europe by assailants with no definable political motive at all, including an Iranian German teen who went on a shooting rampage in Munich.
_
Internet and lone wolf:
The internet is a game-changer. It provides a lot of opportunity for lone wolves to learn about terrorist tactics and targets and to become radicalized via reading ideological web pages and tweets and blogs. But it can also sometimes provide authorities with a way to learn about lone wolves because they like to talk via the internet. ISIS is one of the most technologically and media-savvy groups we have ever had in the history or terrorism. They perfected using the internet. Al-Qaida had used it, but ISIS took it to a whole different level. A lone wolf pledges allegiance and ISIS gets the global publicity. And then they can claim—as apparently they did—that an ISIS fighter or sympathizer perpetrated the attack. They are a step ahead of us in terms of the media battle. You also have to realize ISIS is suffering major losses on the ground in Iraq and Syria. We may see the day in the near future where they are actually defeated, but they will continue, as a decentralized global force, to use the internet and social media to get different individuals to commit violence in their name. A lot of lone wolves blog or send out messages before an attack. The problem, as we are seeing in Orlando, is: How do you separate those who may be espousing extremist views from those who will actually follow through?
_
Lone wolf profile:
Many lone wolves have personal issues, they may be mentally unstable, they may have had financial problems, and they can latch on to an ideology and use that to justify their actions. It is both a personal grievance and a self-identification with a cause. We saw this in Orlando in June. Omar Mateen was neither meaningfully connected to known extremists nor behaving like one. Based on what we know so far, neither was Nice attacker Mohamed Bouhel. Instead, analysis has focused on issues of identity, sexuality, mental health and a violent past (and, in Bouhel’s case, on further evidence of the connection between persistent criminal behaviour and a subsequent shift towards extremism). These factors may be useful in understanding which individuals already under investigation might take extreme and violent actions, but they are not unique behavioural indicators of use to intelligence agencies. In a practical sense, any attempt to overlay them on top of the existing counter-terrorism investigative approach would be unworkable. If our understanding of what a terrorist looks like is starting to shift, so too is the judgment intelligence agencies must make about whether links to known terrorists are an important factor in deciding whether an attack is likely to succeed, and how lethal it will be. This point has also historically been central to counter-terrorism strategy. Operational experience and statistics showed that an attack plot involving returned foreign fighters or instruction from terrorist groups overseas would be significantly deadlier than those that did not. While lone actors or self-starters were certainly a concern, they typically struggled to build explosive devices or get access to weaponry without contacting known terrorist or criminal entities. Unfortunately, isolated actors and their cheerleaders overseas have realised this too. As Nice, Orlando and potentially Wurzburg all demonstrate, these unconnected individuals or networks are instead focusing on softer and typically more local targets. And utilising an attack methodology that challenges intelligence agency notions of what behaviour makes an individual ‘look like a terrorist’. After all, possessing a knife or renting a truck is no obvious precursor to a terrorist attack. Yet both Nice and Orlando have proved deadlier than many previous attacks directed by terrorist networks overseas or carried out by returning foreign fighters. Their tragic impact will not have gone unnoticed by the rest of the would-be terrorist community. Terrorist attacks over the past two months have challenged many counter-terrorism pre-conceptions.
_
Differences between lone wolves and other terrorists:
Love wolves are innovative and dangerous. There is no group decision-making process, so they are basically free to act upon any scenario they think up. There is no constraint on the level of violence, because they are not concerned with alienating supporters. Some groups definitely have supporters. They are not concerned with a government crackdown after an event. They are difficult to identify and capture working alone. The lone wolves are basically growing in terms of numbers, and in terms of the devastation.
__
Counter-terrorism against lone wolf:
Lone wolf is a unique threat. Even though a number of them will express certain things on the internet, we have free speech. We live in an open democracy. With organized groups or cells, you have opportunities with communications, or someone may get arrested. If a lone wolf does keep to himself or herself, it becomes a problem.
Grassroots defenders:
The limits of dedicated counterterrorism forces highlight the importance of what we call grassroots defenders. Perhaps the most important grassroots defenders are police officers on patrol. Though the vast majority of police officers are not assigned primarily to investigate terrorism, they often encounter grassroots militants who make operational security errors or who are in the process of committing crimes in advance of an attack, such as document fraud, illegally obtaining weapons or illegally raising funds for an attack. Cops simply doing their jobs have thwarted a number of terrorist plots, and police officers need to be trained to spot indicators of pre-operational terrorist activity. But police are not the only grassroots defenders. Other people, such as neighbours, store clerks, landlords and motel managers, can also notice operational planning activities, including people conducting pre-operational surveillance, creating improvised explosive mixtures, and purchasing bomb-making components and firearms. Grassroots defenders are an indispensable tool in the struggle against grassroots terrorists of all ideological stripes.
Situational awareness:
In July 2011, an alert gun store clerk in Killeen, Texas, alerted police after a man who exhibited unusual behavior came into the store to buy smokeless gunpowder. Police officers found him and, after questioning, learned he was planning to detonate a pressure cooker bomb and conduct an armed assault at a restaurant popular with soldiers from nearby Fort Hood. The clerk’s situational awareness and decision to call the police likely saved many lives. Based on sheer numbers, terrorists operating under the leaderless resistance model are simply far more likely to be seen by an ordinary citizen than they are by a dedicated counterterrorism agent. So it is important for citizens to be educated about terrorist behavior and report it when they see it. It is unrealistic to expect the government to uncover and thwart every plot. There are too many potential actors and too many vulnerable targets. Individuals need to assume some responsibility for their own security and for the security of their communities. This does not mean living in fear and paranoia but rather just understanding that there is a threat and that the threat can be spotted by alert citizens. Ordinary people exercising common sense and good situational awareness can and have saved lives.
_
How to pick up lone wolf from their internet activities:
“The conscious belief system,” psychiatrists J. Reid Meloy and Jessica Yakeley wrote in a 2014 psychological analysis of lone wolf terrorists, “is upon closer examination often quite superficial: a cherry-picked cluster of prescriptive or proscriptive statements that provide a broad rationalization for the homicidal aggression.” It’s enough for a system to be simple and binary, pitting good against evil, for it to serve as a justification for extreme violence.” Such defensive maneuvers are often part of a pathological narcissism in which the good object is within and the bad objects are all without,” Meloy and Yakeley wrote. The narcissism is an obstacle to affiliating with an actual terrorist group, the psychiatrists pointed out — but it tends to strengthen the lone terrorists’ dependence on virtual communities, such as those formed on the internet. There, communication is free from the constant trauma of real-world interactions. That trauma is ever-present in lone wolf terrorists’ stories — rejection by a father, a non-existent or troubled sex life, professional or academic underachievement. On the internet, none of this matters. The radicalization of Orlando shooter Omar Mateen and Nice truck driver Mohamed Lahouaiej Bouhlel could have been tracked by their internet activities. The Wuerzburg attacker, who had arrived in Germany as an unaccompanied minor and who lived with a foster family in a German town, probably left a similar trail. The tracks these people left online are known as “weak signals” because they are hard for intelligence services to pick up. Yet there are techniques for doing that. A team from the Swedish Defense Research Agency documented one in a 2013 paper. It’s based on a number of behavioral markers that help determine whether a person is capable of radical violence. For example, potential lone wolf terrorists “leak” — they burn to tell outsiders what they want or even plan to do; they also display “fixation” — a preoccupation with a person or a cause — and “identification,” picking a “warrior” role model. The Web can be trawled for the linguistic attributes of these behaviors. For example, the Swedish researchers wrote, “leaked information of intent is likely to contain auxiliary verbs signalling intent (i.e., “…will …,” “…am going to …,” “…should …”) together with words expressing violent action, either overtly or, perhaps more likely, through euphemisms.” A web crawler program instructed to look for such markers in the social network posts of people who visit radical sites (or, presumably, watch certain YouTube videos) could come up with a short list of people to watch. The Swedish researchers recommend always using a human analyst to check over the results of such trawling: Having such a human-in-the-loop makes it possible to tolerate a higher number of false positives than would be acceptable in a fully automated system. Since there is a trade-off between false positives and false negatives, the increase of false positives should decrease the number of false negatives (i.e., classifying weak signals from potential terrorists as non-interesting). If this sounds somewhat cynical — a false positive leading to a person being watched without his knowledge as a potential terrorist, or perhaps interrogated because of a computer program’s suspicions — it is. Unlike racial profiling, it is at least color-blind. There is simply no other way to look preemptively for potential lone terrorists, just as, in pre-Web days, there was no way to prevent “Unabomber” Ted Kaczynski from mailing his first bomb. It’s up to society in every specific country to decide whether intelligence services should have the power to use methods such as those suggested by the Swedish researchers — and to act on the information collected by such methods. The latter is especially important: The internet is full of hotheads of every description, and their freedom of speech is constitutionally protected in Western countries, though in most of Europe, hate speech is illegal.
___________
Limitations in terror suspect surveillance:
To keep a target under continuous surveillance, according to one experienced FBI source who asked to remain anonymous, could require three eight-hour shifts or perhaps two 12-hour shifts, with four special agents each shift. Several cars would be needed, sometimes even airplanes. If only one car was used, the person might quickly realize he was being followed. If you are just sitting around in the street, somebody’s going to notice you. If it’s a real sensitive case, you just cannot be made. You would run five or six cars, maybe seven or eight. If you don’t want any chance of the target making you, the average is three shifts, four guys to a shift, two cars – that’s a minimum. Three shifts, so 12 agents. If it’s a really important case, you could easily double that. That minimum translates into 24 agents in three shifts of eight agents to keep watch on a single target. If you assume that at any given point there are 500 or 600 potentially violent extremists in the U.K. and that it takes 20 to 25 people to keep somebody under surveillance 24/7, inevitably given that resources are limited, you can only watch maybe 50 to 60 people at any given time 24/7. All the others, you have to opt for lesser forms of surveillance, so constantly you have to decide who is really dangerous, who is less dangerous and who is perhaps not even dangerous at all. And inevitably mistakes are being made. So only a fraction of terror suspects can be watched 24/7. Limitations in watching terror suspects mean it is virtually impossible to prevent ‘lone-wolf’ killings.
_
We can’t expect intelligence services to prevent every terrorist attack.
French journalists recently pointed out in Le Monde that citizens expect 100% security. Yet intelligence services make very clear that such levels of security are not materially possible. The British Secret Intelligence Service states on its website: “we are likely to see a more unpredictable picture in the future, potentially with more frequent, albeit less sophisticated attacks.” Similarly intelligence scholars have long agreed that “intelligence failures are inevitable.” In other words, citizens should not expect too much from their intelligence services. In continental Europe, the task of domestic security services, expected to monitor potentially dangerous individuals and provide national security, has been significantly complicated by the growth of “Jihadi tourism.” More than a thousand aspirant-terrorists have travelled from Europe to Syria in recent years. The risks posed by these individuals when they return home have been very clearly demonstrated by Mohamed Merah’s attacks in Toulouse and Montauban, Mehdi Nemnouche’s attack at the Jewish museum in Brussels, and more recently by at least one of the Kouachi brothers who received training in Yemen before staging the attack on Charlie Hedbo. When the terrorist intent is clear enough, intelligence services employ both electronic and physical surveillance. The latter type of surveillance is notoriously time consuming, expensive, and places high demands on domestic security services. According to security expert Roy Godson, clandestine surveillance around the clock “requires at least twenty-four people and twelve cars.” Multiply this by the number of individuals judged to be at risk in France and elsewhere in Europe and the necessary resources quickly become colossal. Despite these difficult conditions, French intelligence did manage to thwart at least a handful of major plots in the last couple of years. And the Belgian police recently rounded up a group described as Jihadi militants, “on the verge of carrying out attacks.” Commentators have discussed a host of improvements, some of which are already being implemented by governments. Experts have called for greater pan-European security cooperation to share resources and costs, and to compensate for the lack of border security checks that result from the free movement of goods and people among countries that have signed the Schengen agreement. This approach could be broadened and applied to transatlantic cooperation, which could, for example, lead to even more intelligence sharing between the US intelligence community and multiple European partners. The French government has committed to invest more resources in its intelligence and security services. Some experts have suggested that the French laws regulating surveillance should be amended to give more flexibility to the services. Others argue that the analytical capabilities of the French intelligence apparatus need to be improved to better connect the dots. However, augmenting and improving intelligence capabilities can only do so much. Even when the dots are connected, there remains the challenge of persuading decision-makers to act. More generally, security capabilities cannot be increased indefinitely. Critics will condemn the growth of an almighty “security state.” Given the myriad of challenges faced by intelligence professionals, common wisdom in the field of security points out that intelligence is ultimately a human endeavour and as such it is inherently imperfect. The resulting conclusion is a sobering invitation to revise our expectations and accept relative levels of insecurity while striving to improve the use of intelligence to counter terror.
___
Fight terrorism with intelligence and not military:
Much emphasis in the fight against terrorism has been placed on military capabilities. We have come to expect that planes, tanks, helicopters, and heavily armed soldiers will be used to protect the world and defeat our enemies. But calling out the Army, Air Force, Navy, and Marines in full battle gear to combat terrorism on a day-to-day basis is rarely a successful strategy at home or abroad. There’s no question that many nations have the military might to crush an enemy on the battlefield – but in fighting terrorism, the primary challenge is finding the enemy on a battlefield that has no boundaries. If the job is done right, successful prevention of terrorism depends on gathering accurate information and stopping something from happening – often without public awareness. It is only the failure to prevent attacks that is felt, and along with it a profound sense that we are ultimately powerless to protect ourselves. The terrorists are, by definition, in the business of terrorizing us, and want to make us feel helpless and hopeless in the face of their attacks. They want us to believe attacks come randomly and without warning, so that we don’t even try to predict the unpredictable. They hope that by making us adopt defeatism as a philosophy, they can defeat us. In fact, there is plenty we have done and can do to combat terrorism. Recent terrorist events perpetrated by Al Qaeda and ISIS have similar patterns that can be identified by intelligence agencies working hand in glove with local police and security services around the world. One of these recent patterns is for ISIS to devolve more authority to local Islamic extremist groups to carry out attacks. In many cases, the police are already aware of the activities of local extremist groups with established records of advocating and carrying out violent acts, and often know the players involved because of their past participation in terrorist activity. Monitoring the activities of local extremists in individual countries – such as travel in and out of the country and involvement in criminal enterprises – can be carried out through physical surveillance and other methods of monitoring permissible under legal boundaries. This can give local police the upper hand. By doing this, law-enforcement agents will not be able to prevent every terrorist attack, but they will make terrorists’ job a lot harder by dismantling networks and fostering a hostile operating environment. We know from past experience that faced with this situation, terrorists will either cease conducting attacks in that location and restrategize, or move their operations completely. Solid police work is crucial not only in following up on leads after an attack has occurred, but in preventing future attacks. Efforts by police to identify operational patterns and the individuals in communities involved in terrorist activity will go a long way toward undermining terrorists’ ability to instil a sense of randomness and fear.
_________
_________
How to survive a terror attack:
Run and Hide – don’t play dead, says official UK security advice:
Counter-terror officials released tips on how to behave in an attack, urging people to “escape if you can” – rather than lying down – or to barricade themselves into a safe place with their phones on silent. In the event that escape routes are cut off, then officials advise finding cover from the gunfire behind “substantial brickwork or heavy reinforced walls” as “cover from view does not mean you are safe, bullets go through glass, brick, wood and metal”. They outline what to do in “response to a fast moving incident such as a firearms or weapons attack” and also advise businesses to develop procedures for what is called a “dynamic lockdown” to stop armed terrorists entering a site.
British counter-terror officials issued the following advice on how to behave in a gun or bomb attack:
RUN:
Escape if you can
1. Consider the safest options
2. Is there a safe route? Run, if not hide
3. Can you get there without exposing yourself to greater danger?
4. Insist others leave with you
5. Leave belongings behind
HIDE:
If you can’t run, hide
1. Find cover from gunfire
2. If you can see the attacker, they may be able to see you
3. Cover from view does not mean you are safe, bullets go through glass, brick, wood and metal
4. Find cover from gunfire e.g. substantial brickwork/heavy reinforced walls
5. Be aware of your exits
6. Try not to get trapped
7. Be quiet, silence your phone
8. Lock/barricade yourself in
9. Move away from the door
TELL:
Call police number: What do the police need to know?
1. Location: Where are the suspects?
2. Direction: Where did you last see the suspects?
3. Descriptions: Describe the attacker, numbers, features, clothing, weapons etc.
4. Further information: Casualties, type of injury, building information, entrances, exits, hostages etc.
5. Stop other people entering the building if it is safe to do so
_________
_________
Now let me go through some terror attacks to find out shortcomings in intelligence:
_
Bangladesh terror attack July 1, 2016:
The assailants took control of the popular Holey Artisan Bakery at 9:20 p.m. in capital Dhaka reportedly chanting “Allahu Akbar” (God is great) as they fired their weapons. They killed 22 people in a terror attack that has left the country reeling in shock. Police named the five gunmen who attacked the restaurant as Nibras Islam, Rohan Imtiaz, Meer Saameh Mubasheer, Khairul Islam and Shafiqul Islam; and said that they were known to police. It was revealed that three of the attackers came from a privileged background, educated with western curricula. Two gunmen Meer Sameh Mubashir and Rohan Imtiaz had gone missing long before the attack. The gunmen separated the Muslims from the non-Muslims. The Muslims were given food and water, while the non-Muslims were not. The attackers took many hostages, almost all foreigners. Reports indicate that the attackers were “unfailingly polite and solicitous” with the restaurant staff and other Bangladeshis. They took the staff into their confidence, complaining that foreigners, with their skimpy clothes and taste for alcohol, were impeding the spread of Islam. “Their lifestyle is encouraging local people to do the same thing,” a militant said. Eyewitness accounts suggest that the gunmen killed the victims using machetes and knives, rather than by firing, possibly to conserve ammunition. “Had we been certain that the terrorists were so lightly armed, we would probably have ordered the assault far earlier, and perhaps lives could have been saved. However, that was not a call which we could take casually, with so many lives at stake,” a Dhaka-based police officer told media. On 6 July 2016, a video was released by IS from Syria through SITE intelligence website, where three Bengali speakers warned the Bangladeshi Government saying “What you witnessed in Bangladesh…was a glimpse. This will repeat, repeat and repeat until you lose and we win and the sharia is established throughout the world. The jihad that is waged today is a jihad under the shade of the Caliphate.”
_
Shortcomings:
1. Police was present at the onset of attack but could not prevent it.
2. Needless hostage situation was allowed to develop.
3. Five terrorists have taken 3 dozen hostages and it takes time to divide Muslim and non-Muslims; in the same time hostages should have attacked terrorists.
4. Two terrorists Meer Sameh Mubashir and Rohan Imtiaz had gone missing long before the attack and their families have registered missing complaint. Police had suspected of them becoming militants. Their photographs should have been flashed on TV and newspapers as missing persons possibly radicalized. This could have dissuaded them to carry out attack or help their capture before attack.
________
26/11 attack:
The 2008 Mumbai attacks were a series of attacks that took place in November 2008, when 10 members of Lashkar-e-Taiba, an Islamic militant organisation based in Pakistan, carried out a series of 12 coordinated shooting and bombing attacks lasting four days across Mumbai. The attacks, which drew widespread global condemnation, began on Wednesday, 26 November and lasted until Saturday, 29 November 2008, killing 164 people and wounding at least 308. Eight of the attacks occurred in South Mumbai: at Chhatrapati Shivaji Terminus, the Oberoi Trident, the Taj Mahal Palace & Tower, Leopold Cafe, Cama Hospital, the Nariman House Jewish community centre, the Metro Cinema, and in a lane behind the Times of India building and St. Xavier’s College. There was also an explosion at Mazagaon, in Mumbai’s port area, and in a taxi at Vile Parle. By the early morning of 28 November, all sites except for the Taj Hotel had been secured by Mumbai Police and security forces. On 29 November, India’s National Security Guards (NSG) conducted ‘Operation Black Tornado’ to flush out the remaining attackers; it resulted in the deaths of the last remaining attackers at the Taj Hotel and ending all fighting in the attacks. Two hotels, the Taj Mahal Palace & Tower and the Oberoi Trident, were among the four locations targeted. Six explosions were reported at the Taj hotel – one in the lobby, two in the elevators, three in the restaurant – and one at the Oberoi Trident.
_
Hostage situation at hotel Taj Mahal:
The terrorists entered Hotel Taj Mahal from the front/main gate entrance, firing indiscriminately on the Indian and foreign Hotel guests who were present. The two terrorists who had attacked the Café Leopold, also entered the Taj Hotel from the other gate and began firing indiscriminately around the swimming pool area. Fear and panic struck through the entire hotel. Now there were totally four terrorists inside the hotel. They started moving on various floors of the hotel, firing indiscriminately. Six explosions took place inside the hotel. The Wasabi restaurant on the first floor of the hotel was completely devastated. The terrorists continuously communicated receiving operational and motivational inputs from their co-conspirators/ LeT operatives. At the Taj Mahal, firefighters rescued 200 hostages from windows using ladders during the first night. CNN initially reported on the morning of 27 November 2008 that the hostage situation at the Taj had been resolved and quoted the police chief of Maharashtra stating that all hostages were freed; however, it was learned later that day that there were still two attackers holding hostages, including foreigners, in the Taj Mahal hotel. During Taj siege, 4 terrorists have taken dozens of hostages and were dividing Muslim and non-Muslims; and killing non-Muslims.
_
Death of top police officers:
At 9.45 p.m. on November 26, 2008, while having his dinner at his Dadar residence, ATS chief Hemant Karkare received a call about a terrorist attack at Chatrapati Shivaji Terminus (C.S.T.) station. He switched on the TV for news and left at once with his driver and bodyguards for C.S.T. There he donned a bullet-proof vest and helmet, and went to Platform No.1, but found it deserted. He was then informed that the terrorists had moved to the Cama Hospital next to the Azad Maidan police station. The operation was difficult as it was dark and the terrorists were well prepared and virtually on a fidayeen mission. The officers, with a few constables, went into Cama from the back. A couple of constables were left stationed at the back entrance of Cama, while the rest boarded a Qualis jeep. Senior Police Inspector Vijay Salaskar asked the driver of the Qualis to let him take over at the wheel. About that time, they heard on the wireless that the terrorists were hiding behind a red car. As they turned from the Crime Branch office towards Rang Bhavan looking for the red car, near the Corporation Bank ATM, they saw a terrorist running. Ashok Kamte, ACP of Mumbai East fired, the bullet hitting the terrorist on his arm, his AK-47 fell down. He was Kasab, the lone terrorist captured alive later. As they were thinking of getting down, a second terrorist, Ismail Khan appeared and fired a volley of bullets at them. All but one died. Hemant Karkare, Ashok Kamte, Salaskar and others died in fighting the Mumbai attacks, on 27 November 2008 in a narrow lane between St. Xavier’s College and Rang Bhavan, just a stone throw away from the Crime Branch office. The wounded Jadhav had no opportunity to render assistance. The two terrorists approached the vehicle, dumped the bodies of the three officers on the road and, leaving the constables for dead, proceeded to Metro Cinema. Upon arrival, they aimed three bursts of automatic fire at the police and press vehicles drawn up at that location, then drove off towards the government offices (Vidhan Bhawan) in South Mumbai. Here again they fired several times. While attempting to leave the area, one of the tires of the vehicle burst, so the terrorists departed to obtain another. At this point, Jadhav was able to contact headquarters. The bodies of the dead were recovered and taken to St George Hospital. In an investigation, Headline Today, an Indian news agency, found that a substandard bulletproof jacket had been issued to Mr. Karkare. Though, according to the post mortem report, the quality of the vest was not a factor in his death, concerns in the media about the quality of the vest continued because the vest itself was, according to Indian authorities, misplaced in the hospital.
__
A former director of India’s external intelligence agency has asserted that information gathered prior to the attack was sufficient to foil the plot beforehand. He is not alone. It is now known that the Research and Analysis Wing (RAW) intercepted several suspicious phone conversations between Lashkar operatives in advance. In mid-September, a seaborne operation was discussed that would target a hotel near the Gateway of India, which sits across from the Taj. Less than a week later, in another conversation, the operative identified hotels that were being considered; they included the Taj. Then, on November 19, a voice on a monitored satellite phone said, “We will reach Bombay between nine and eleven.” The point of origin was traced to Indian territorial waters, and the information was relayed to the Navy. A vessel was finally dispatched to the original location, by which time the source had moved on. (The attackers landed at Badhwar Park 8:30 P.M., just a half hour shy of the caller’s estimated time of arrival). Additionally, it emerged that the mobile phone numbers used by the attackers were known to the Indian Intelligence Bureau five days before they struck. A police operative had infiltrated a camp and provided SIM cards to be tracked. A note attached to the list recommended that they be carefully monitored. They weren’t. In fact, the enterprising operative was later arrested as a possible conspirator and held in custody for weeks during which the IB accused the police of exceeding their mandate. In this fractious climate, the broader constellation of dots was never connected. In a security conference of chief ministers following the attack, Prime Minister Manmohan Singh lamented rigid bureaucracy and stressed the “need to break down the barriers to information-sharing among the various intelligence agencies.” More important than gathering better intelligence, he said, was an efficient analysis of the intelligence available.
_
Shortcomings:
1. Americans had warned their Indian counterparts of a likely seaborne attack on Mumbai and that Taj Mahal Hotel, and places frequented by foreigners, and especially Americans, were potential targets. Yet attack could not be prevented or halted.
2. Intelligence agencies have intercepted several suspicious phone conversations revealing sea-borne attack on Mumbai. Yet intelligence input was not utilized.
3. Mobile phone numbers used by the attackers were known to the Indian Intelligence Bureau five days before they struck but yet attack occurred.
4. There was poor coordination between intelligence agencies and law enforcements.
5. Badhwar Park was the location of landing of the 10 terrorists from Pakistan via sea route on the evening of 26/11/2008. Many eye-witnesses saw them and one of them even talked to them, yet nobody suspected them of being terrorists.
6. Four terrorists have taken dozens of hostages in hotel Taj and were dividing them between Muslims and non-Muslims; the hostages were pleading with them to let them go; instead the hostages should have attacked terrorists.
7. How come top police officers and constables killed by two terrorists — were police not given proper weapons, proper bullet proof jackets and proper training? If armed police officers are to be slaughtered by terrorists, what about lay people?
_________
2016 Orlando nightclub shooting:
On June 12, 2016, Omar Mateen, a 29-year-old security guard, killed 49 people and wounded 53 others in a terrorist attack inside Pulse, a gay nightclub in Orlando, Florida, United States. He was shot and killed by Orlando police after a three-hour standoff. Pulse was hosting Latin Night and most of the victims were Hispanic. It was both the deadliest mass shooting by a single shooter and the deadliest incident of violence against LGBT people in U.S. history, as well as the deadliest terrorist attack in the U.S. since the September 11, 2001 attacks.
_
Hostage situation:
On June 11, 2016, Pulse, a gay nightclub in Orlando, Florida, was hosting Latin Night, a weekly Saturday night event drawing a primarily Hispanic crowd. About 320 people were inside the club, which was serving last call drinks at around 2:00 a.m. on June 12. After arriving at the club by van, Omar Mateen approached the building on foot, armed with a SIG Sauer MCX semi-automatic rifle and a 9mm Glock 17 semi-automatic pistol. At 2:02 a.m., a uniformed off-duty Orlando Police Department (OPD) officer working extra duty as a security guard engaged Mateen. Mateen bypassed him into the building, and began shooting patrons. Two additional officers also engaged Mateen, who then retreated farther into the nightclub and “began a ‘hostage situation'”. In the next 45 minutes, about 100 officers from the OPD and the Orange County Sheriff’s Office were dispatched to the scene.
_
FBI miss:
Mateen became a person of interest to the FBI in May 2013 and July 2014. The 2013 investigation was opened after he made comments to co-workers about being a member of Hezbollah and having family connections in al-Qaeda, and that he had ties to the Fort Hood shooter and the then-suspects of the Boston Marathon bombing. According to new documents released on July 18, Mateen said that he made these comments in response to “a lot of harassment” and frequent derogatory epithets made by St. Lucie County Sheriff’s deputies and his G4S co-workers, who taunted and made jokes about him being a possible Muslim extremist. The comments resulted in his employer G4S removing Mateen from his post and the county sheriff reporting him to the FBI. The documents also show him saying that he was “1000% American” and wrote that he was against any “anti-American” and “anti-humanity” terrorist organizations. The 2014 investigation was opened after he was linked to Moner Mohammad Abu Salha, an American radical who committed a suicide bombing in Syria. Mateen was interviewed three times in connection with the two investigations. Both cases were closed after finding nothing that warranted further investigation. After the shooting, Director Comey said the FBI will review its work and methods used in the two investigations. When asked if anything could have or should have been done differently in regard to Mateen, or the FBI’s intelligence and actions in relation to him, Comey replied, “So far, the honest answer is, ‘I don’t think so'”. A little over a month after the shooting, the FBI provided more details about its May 2013–March 2014 investigation into Mateen, which was closed after a veteran FBI agent assigned to the case and his supervisor concluded that “there was just nothing there” and removed his name from the Terrorist Watchlist. Mateen was interviewed twice during the investigation, and had provided a written statement in which he confessed that he had previously lied to FBI investigators. During the investigation, the FBI had tracked his daily routine using unmarked vehicles, closely examined his phone records, and used two informants to secretly record his face-to-face conversations. The FBI Director said that they could have taken more initiative in gaining access to his social media accounts in 2013, but noted that back then such checks were not yet “part of [their] investigative DNA”. However, it would not have mattered, as the analysis of Mateen’s computer after the shooting showed that his social media accounts, including Facebook, had no ties to any terrorist groups, and that he did not post any “radical statements” until the early morning of the shooting. The FBI in 2013 also did not have the probable cause needed to obtain a search warrant in order to secretly listen to his phone calls or probe into Mateen’s computer.
_
Gun sell to terrorist:
Mateen had purchased a Sig Sauer .223 caliber assault rifle at a firearms shop near his Florida home, St. Lucie Gun Sales, on June 4 and then a Glock 17 at the same store on June 5. Mateen had returned to the store a third time on June 9 to buy magazines for his weapons. The store is a federally licensed firearms dealer. Under law, the seller would have had to notify the Federal Bureau of Investigation of Mateen’s purchase so that his name could be checked against the National Instant Criminal Background Check System, or NICS. Mateen was actually listed on two federal watch lists: The Terrorist Identities Datamart Environment, which contains classified information, and the Terrorist Screening Database, which is the FBI’s central watchlist. The gun background check would have run Mateen’s name against that second database, but he had been removed from it in 2014. The sales were approved and early Sunday morning he used the weapons to fire round after round after round at defenceless people at the Pulse nightclub. Mateen left a third weapon, a revolver capable of firing only a mere six shots, in his van. Ed Henson, the owner of the St. Lucie Shooting Center and a former NYPD detective said that Mateen had multiple security licenses. He says handgun purchases require a three-day waiting period and a background check, while long gun purchases require only the background check. When Omar Mateen walked into a gun store to buy the weapons he used for the Orlando massacre, he had already undergone a more rigorous background check than the typical firearms customer. As the holder of a Class D security officer license from the state of Florida, he had submitted fingerprints and a photograph, passed criminal background and mental health screenings and submitted proof of 40 hours of professional training. As holder of a Class G gun permit, which allowed him to carry up to two concealed weapons, he underwent the same checks, as well as 28 hours of classroom and range training.
_
It appears the seeds of Mateen’s hatred were planted at home. His Afghan immigrant father, who founded a nonprofit group to support the Taliban, preached gays should be punished. In a video Seddique Mir Mateen expresses gratitude toward the Afghan Taliban, who stone homosexuals to death, calling them “our warrior brothers.” Other statements make it clear the elder Mateen could have passed anti-gay views onto his son. Mateen’s ex-wife, Sitora Yusufiy said Mateen was abusive and violent during their brief relationship. Mateen’s second wife Salman told the FBI she drove Mateen to the Pulse nightclub on a different occasion and she tried to talk him out of the attack. She also accompanied him at the time of gun purchase. Mateen exchanged text message with wife during Orlando attack.
_
Shortcomings:
1. FBI missed to read Mateen’s intent despite three interviews.
2. FBI should not have removed Mateen’s name from terror watch-list.
3. FBI should have interviewed Mateen’s ex-wife who said he was violent.
4. FBI should have investigated father of terrorist who is Afghan Taliban supporter.
5. Orlando police allowed hostage situation to develop. The police should not have waited 3 hours before entering night club.
6. The gun seller should have been alert and aware.
7. When anybody is interviewed by FBI/police several times as probable terror suspect, his photograph should be flashed on TV and newspaper as probable terror suspect which will deter him to indulge in terror activities and make other people of the town aware about him.
_______
2016 Nice attack:
On the evening of 14 July 2016, 84 people were killed and 303 injured when a 19-tonne cargo truck was deliberately driven into crowds celebrating Bastille Day on the Promenade des Anglais in Nice, France. The driver was Mohamed Lahouaiej-Bouhlel, a Tunisian resident of France. The attack ended following an exchange of gunfire during which police surrounded the truck and shot the driver, killing him. A 31-year-old delivery driver and Nice resident who was born in Tunisia Mohamed Lahouaiej Bouhlel drove a rented, refrigerated truck weighing about 19 tons into crowds along a roughly 2-kilometer stretch of Promenade des Anglais killing 84 people — including 10 children and adolescents — and injuring 202 others. The truck was rented on Monday and was supposed to have been returned Wednesday.
_
At approximately 22:10 CEST (20:10 UTC), 30 minutes before the incident, a 19-tonne white cargo truck was seen approaching the Promenade des Anglais, driven erratically. A witness described how the vehicle was repeatedly speeding up and slowing down. The fireworks were finishing when the truck slowly breached the vehicle barriers opposite the Lenval children’s hospital. Alexander Migues, a motorcyclist pursued the truck and attempted to pull open the driver’s side door, he clung on to the vehicle but was forced to let go after the driver directed a gun at him. Watching this, two nearby police officers opened fire on the truck. At this point, the driver sped up, drove northeast, and plunged into the crowds on the Promenade, swerving to hit pedestrians. Police tried to stop the truck with gunfire, as the driver continued for 2 kilometres killing and injuring pedestrians. Following an exchange of gunfire, the attacker was stopped near the Palais de la Méditerranée hotel. The driver fired repeatedly on three policemen, who returned fire and pursued him for hundreds of metres. According to eyewitness Éric Ciotti, an individual identified as M. Migues jumped onto the truck, distracting and drawing gunfire from the driver while the police surrounded the truck. The vehicle was raked with bullets and the driver killed.
_
Perpetrator Lahouaiej-Bouhlel was a young man completely uninvolved in religious issues and not a practising Muslim, who ate pork, drank alcohol, took drugs and had an unbridled sex life. Neighbours reported that Lahouaiej-Bouhlel rarely spoke to them and showed no interest in religion. Evidence from mobile phones and computer records suggested that Mohamed Lahouaiej-Bouhlel was not a recently radicalised “lone wolf”, as previously thought, but had several accomplices and had planned his attack for up to a year. It was increasingly evident that Bouhlel’s attack was premeditated and that he had logistical and planning support from the five others, with whom he had been in regular contact. He seems to have envisaged and developed his criminal plans several months before carrying them out. After the attack on the offices of the Charlie Hebdo magazine in January 2015, in which 12 people died, Bouhlel sent a text message to one suspect that read: “I am not Charlie. I’m happy they have brought some of Allah’s soldiers to finish the job”. Lahouaiej-Bouhlel had been in trouble with police between 2010 and 2016 for threatening behaviour, violence and petty theft. In March, a court in Nice convicted him of assaulting a motorist with an improvised weapon – a wooden pallet – during an altercation. He was given a six-month suspended prison sentence and ordered to contact police once a week, which he did. Lahouaiej-Bouhlel was “never flagged for signs of radicalisation”, officials say, and he was not on France’s “Fiche S” high-security watch list. The majority of attacks carried out in the country since January 2015 have been staged by men designated “Fiche S”, and also linked to IS.
_
Shortcomings:
1. Terrorist was in trouble with police between 2010 and 2016 for threatening behaviour, violence and petty theft, yet police could not determine that he was radicalized.
2. Police fired at truck at the onset of attack but failed to stop truck or kill driver. Were police not given proper weapons and proper training?
3. There should be large heavy physical barriers to prevent entry of any vehicle where large number of people has gathered.
___________
___________
Discussion:
____
How to win fight against radical Islamic terrorism:
_
How many Muslims support terrorism?
The Pew Research Center’s 2012 report:
A new Pew Research Center survey of Muslims around the globe finds that most adherents of the world’s second-largest religion are deeply committed to their faith and want its teachings to shape not only their personal lives but also their societies and politics. In all but a handful of the 39 countries surveyed, a majority of Muslims say that Islam is the one true faith leading to eternal life in heaven and that belief in God is necessary to be a moral person. Many also think that their religious leaders should have at least some influence over political matters. And many express a desire for sharia – traditional Islamic law – to be recognized as the official law of their country. The percentage of Muslims who say they want sharia to be “the official law of the land” varies widely around the world, from fewer than one-in-ten in Azerbaijan (8%) to near unanimity in Afghanistan (99%). But solid majorities in most of the countries surveyed across the Middle East and North Africa, sub-Saharan Africa, South Asia and Southeast Asia favor the establishment of sharia, including 71% of Muslims in Nigeria, 72% in Indonesia, 74% in Egypt and 89% in the Palestinian territories. At the same time, the survey finds that even in many countries where there is strong backing for sharia, most Muslims favor religious freedom for people of other faiths. In Pakistan, for example, three-quarters of Muslims say that non-Muslims are very free to practice their religion, and fully 96% of those who share this assessment say it is “a good thing.” Yet 84% of Pakistani Muslims favor enshrining sharia as official law. These seemingly divergent views are possible partly because most supporters of sharia in Pakistan – as in many other countries – think Islamic law should apply only to Muslims. Moreover, Muslims around the globe have differing understandings of what sharia means in practice. Few U.S. Muslims voice support for suicide bombing or other forms of violence against civilians in the name of Islam; 81% say such acts are never justified, while fewer than one-in-ten say violence against civilians either is often justified (1%) or is sometimes justified (7%) to defend Islam. Around the world, most Muslims also reject suicide bombing and other attacks against civilians. However, substantial minorities in several countries say such acts of violence are at least sometimes justified, including 26% of Muslims in Bangladesh, 29% in Egypt, 39% in Afghanistan and 40% in the Palestinian territories. These are among the key findings of a worldwide survey by the Pew Research Center’s Forum
on Religion & Public Life.
_
Other studies:
A recent poll says that 13% of Syrian refugees support Islamic State.
France:
A new, widely-covered poll shows that a full 16% of French people have positive attitudes toward ISIS. That includes 27% of French between the ages of 18-24. This is the ideology of young French Muslims from immigrant backgrounds…these are the same people who torch synagogues
Britain:
In 2006, a poll for the Sunday Telegraph found that 40% of British Muslims wanted sharia law in the United Kingdom, and that 20% backed the 7/7 bombers. Another poll from that year showed that 45% of British Muslims said that 9/11 was an American/Israeli conspiracy; that poll showed that one-quarter of British Muslims believed that the 7/7 bombings were justified.
Palestinian Areas:
A 2013 poll showed 40% of Palestinians supporting suicide bombings and attacks against civilians. 89% favoured sharia law. Currently, 89% of Palestinians support terror attacks on Israel.
Pakistan:
After the killing of Osama Bin Laden, the Gilani Foundation did a poll of Pakistanis and found that 51% of them grieved for the terrorist mastermind, with 44% of them stating that he was a martyr. In 2009, 26% of Pakistanis approved of attacks on US troops in Iraq. That number was 29% for troops in Afghanistan. Overall, 76% of Pakistanis wanted strict sharia law in every Islamic country.
Morocco:
A 2009 poll showed that 68% of Moroccans approved of terrorist attacks on US troops in Iraq; 61% backed attacks on American troops in Afghanistan as of 2006. 76% said they wanted strict sharia law in every Islamic country.
Jordan:
72% of Jordanians backed terror attacks against US troops in Iraq as of 2009. In 2010, the terrorist group Hezbollah had a 55% approval rating; Hamas had a 60% approval rating.
Indonesia:
In 2009, a poll demonstrated that 26% of Indonesians approved of attacks on US troops in Iraq; 22% backed attacks on American troops in Afghanistan. 65% said they agreed with Al Qaeda on pushing US troops out of the Middle East. 49% said they supported strict sharia law in every Islamic country. 70% of Indonesians blamed 9/11 on the United States, Israel, someone else, or didn’t know. Just 30% said Al Qaeda was responsible.
Egypt:
As of 2009, 87% of Egyptians said they agreed with the goals of Al Qaeda in forcing the US to withdraw forces from the Middle East. 65% said they wanted strict sharia law in every Islamic country. As of that same date, 69% of Egyptians said they had either positive or mixed feelings about Osama Bin Laden. In 2010, 95% of Egyptians said it was good that Islam is playing a major role in politics.
In a nutshell:
Tens of millions of Muslims all over the world sympathize with the goals or tactics of terrorist groups – or both. That support is stronger outside the West, but it is present even in the West. Islamist extremism is not a passing or fading phenomenon – it is shockingly consistent over time. And the West’s attempts to brush off the ideology of fanaticism have been an overwhelming failure.
_
Myth: Islam has nothing to do with terrorism.
Fact: We cannot ignore all data on terror: the imams who preach hate, the statistics that show fairly significant portions of Islamic nations support terrorism and the lists of registered terrorist groups, the vast majority of which are Islamic. The argument that Islam has nothing to do with terrorism relies on the theologians who insist that on some intellectual or spiritual level, their interpretation of Islam reflects peace. Certainly, that may well be their interpretation. But unfortunately, that is not the reality for all followers.
_____
The criminal known to security services has perpetrated a mass killing, the Tunisian Mohamed Lahouaiej-Bouhlel. Why did the French police allow a foreign national with a criminal record of violence to reside in France? Apart from utter incompetence, the explanation is that he was informer for the French authorities. Blackmailing Muslim criminals to inform on prospective terrorists is the principal activity of European counter-terrorism agencies. Every Muslim in Europe knows this. The terrorists, though, have succeeded in turning the police agents sent to spy on them and forcing them to commit suicide attacks to expiate their sins. This has become depressingly familiar; as Ryan Gallagher reported recently, perpetrators already known to the authorities committed ten of the highest-profile attacks between 2013 and 2015. The terrorists, in other words, are adding insult to injury. By deploying police informers as suicide attackers, terrorists assert their moral superiority and power over western governments. The message may be lost on the western public, whose security agencies and media do their best to obscure it, but it is well understood among the core constituencies of the terrorist groups: the superiority of Islam turns around the depraved criminals whom the western police send to spy on us, and persuades them to become martyrs for the cause of Islam. These attacks, in other words, are designed to impress the Muslim public as much as they are intended to horrify the western public. In so many words, the terrorists tell Muslims that western police agencies cannot protect them. If they cooperate with the police they will be found out and punished. The West fears the power of Islam: it reveals such fear by praising Islam as a religion of peace, by crushing dissent in the name of fighting supposed Islamophobia, and by offering concessions and apologies to Muslims. Ordinary Muslims live in fear of the terror networks, which have infiltrated their communities and proven their ability to turn the efforts of western security services against them. They are less likely to inform on prospective terrorists and more likely to aid them by inaction. The terrorists, in short, are winning the intelligence war, because they have shaped the environment in which intelligence is gathered and traded. But that is how intelligence wars always proceed: spies switch sides and tell their stories because they want to be with the winner. ISIS and al-Qaeda look like winners in the eyes of western Muslim populations after humiliating the security services of the West. As a result, western European Muslims fear the terrorists more than they fear the police. The West will remain vulnerable to mass terror attacks until the balance of fear shifts in the other direction. Destroying ISIS, al-Qaeda and other Muslim terror groups is not particularly difficult. Western intelligence doesn’t have to infiltrate terror groups, tap phones, mine social media postings and so forth (although these doubtless are worth doing). Muslim communities in the West will inform on the terrorists. They will tell police when someone has packed up and gone to Syria, and when he has returned. They will tell police who is talking about killing westerners, who has a suspicious amount of cash, who is listening to broadcasts from Salafist preachers. They will tell western security services everything they need to know, provided that western security services ask in the right way. The West does not have to be particularly clever. It simply needs to understand what kind of war is fighting. Most Muslims are peaceful people who disapprove of terrorism, but many are not. Opinion polls show a consistent minority of 20% to 40% approves of at least some form of terrorism. Support for ISIS generally is low, but much higher for Hezbollah, Hamas and other terrorist groups. By any reasonable count there are a few hundred million Muslims who in some way approve of terror, although very few of them would take part in terror attacks. But they are the sea in which the sharks can swim unobserved. They may not build bombs, but they will turn a blind eye to terrorists in their midst, especially if those terrorists are relations. They also fear retaliation from the terrorists if they inform. The way to win the war is to coerce these Muslims who passively support terror by action or inaction — coerce them so that they will inform on family members. The important reason why Sikh terrorism was eliminated in Punjab, India is because moderate Sikhs stopped supporting militant Sikhs and in fact moderate Sikhs came forward and gave vital information to police to catch the extremist. Nearly a decade long struggle came to a halt after the security forces adopted the policy of `tit for tat’. That meant the same extremist’s family who once targeted the family of security forces were targeted. In the conflict that began in Chechnya and has since metastasized into a loosely organized Islamic rebellion throughout the Caucasus region, Russian security services routinely arrest relatives. Most strikingly, whole extended families are rounded up in high-profile cases, and are often held until the militant either gives up or is killed. The Russian approach has been effective. Analysts estimate that a third of the participants in terrorist acts are related to another attacker. Mere verbal condemnation of religious terrorism by moderate believers is a lip-service. The way to end religious terrorism is to expose and corner extremist individuals by their family members and other moderate believers and also provide vital information about extremists to police by their family members and other moderate believers.
_
Look at Orlando attack where wife and father were knowing many things but did not inform police, look at Dhaka attack where family members have noticed changes in behaviour of their son, look at Nice attack where terrorist sent all his money to brother before attack, look at 26/11 attack where Headley’s wives knew his terror connections; and so on and so forth. It is inconceivable to think that close family members knew nothing about radicalization of terrorist. My ex-wife filed dowry complaint under IPC 498/A; and my parents and brother were arrested by police without any evidence merely because they were part of family. To eradicate dowry, we legislate such harsh laws, why not against terrorism? We have to legislate new terror laws by which a confirmed terrorists family members are arrested on the presumption of supporting terrorism. Although some of them may be innocent, they can get acquittal through courts. This will send a strong message to would-be terrorists that if you kill innocent people in suicide attacks, your family members may go to jail. This will send a strong message to family members of radicalised terror suspect that if they look the other way, there are in trouble.
__________
Fight ideology of terror:
People the world over are trying to find a solution to terrorism. The authorities are trying to crush the terror menace through legal action; western powers are trying to crush it through warfare; however, these methods are, apparently, proving ineffective. The present problem of terrorism is based on an ideology and an ideology cannot be countered or killed through legal action or by mere condemnation. We have to develop a counter-ideology to overcome it. Violence begins from the mind. It must, therefore, be uprooted from the mind itself. This goes directly to the root cause of terrorism. Therefore, in order to eliminate this root cause we need to initiate our efforts by beginning from the right starting point. And this starting point is the re-engineering of minds of individuals by taking them away from the culture of violence and bringing them closer to the culture of peace. In order to explain the importance of the above, let us state two parallel examples from history. One pertains to the American campaign against Communist Russia and the other refers to the American campaign against Saddam-led Iraq. Both Communist Russia and Iraq were declared enemies of the United States of America, but while the US was successful in curbing the menace of Communist Russia, the same America failed to cope with the menace of Saddam-led Iraq. The reason behind this difference was that America met the Russian challenge at an ideological level, while it opted for military action against Saddam’s Iraq. Terrorism will persist in one form or another until the ideology of violence is countered with another ideology based on peace.
_
These Danish Officers found solution to Terrorism:
Crime prevention officers in Aarhus, a small Danish town, are responsible for one of the most effective anti-terrorism operations the world has ever known. Instead of bombs, these officers take a very different approach, offering a chance for redemption to young men and women who previously went to Syria to train under the watch of ISIS militants. The results are shocking the entire continent. In 2012, Aarhus officers started receiving calls from concerned parents. Strangely enough, the callers all had the same complaint: their child had gone missing. Once the officers looked into the information provided, they learned all the missing persons were young men and women who lived in local Muslim communities. After a deeper investigation, officers learned the missing individuals had all travelled to Syria. They had been looking to join ISIS. At the time, European countries had passed harsh rules and resolutions against citizens who travelled to Syria with the intent of joining ISIS. France shut down mosques and the United Kingdom called Britons fighting alongside ISIS “enemies of the state.” Even Norway recently joined the gang, hinting it would revoke the citizenship of nationals involved with the militant group. Instead of following the trend, Danish officers from Aarhus took the exact opposite approach, making “it clear to citizens of Denmark who had travelled to Syria that they were welcome to come home, and that when they did, they would receive help with going back to school, finding an apartment, meeting with a psychiatrist or a mentor, or whatever they needed to fully integrate back into society”. The results were astounding. Instead of seeing more local young men and women fleeing to Syria to join militants, Aarhus helped about 330 young potential radicals denounce their terrorist ties. Instead of forcing people to stay by arresting them or stripping them of their rights, the Aarhus officers “fought the roots of radicalization.” But the program was not only effective at the beginning of the ISIS scare. Since the program was launched, “very few have left from Aarhus for Syria, even when traffic from the rest of Europe was spiking.” Arie Kruglanski, a social psychologist at the University of Maryland who studies violent extremism, says “there are strong correlations between humiliation and the search for an extremist ideology.” Militant groups like ISIS prey on young men and women who are the victims of racism, as well as political or religious discrimination. When they feel hopeless, Kruglanski claims, they are most at risk of joining these groups. With the Aarhus approach, however, these kids are taught they have a place to call home. “The original response was to fight [extremism] through military and policing efforts, and they didn’t fare too well,” Kruglanski says. Instead of stopping extremism, the established response “puts [people] as suspects and constrains them and promotes discrimination,” which, over time, exacerbates the problem, making it more likely to “inflame the sense there’s discrimination and motivate young people to act against society.” Musa Al-Gharbi, a Muslim sociologist who often writes for the American Conservative, recently wrote that Muslims in America are offered the short end of the stick when it comes to helping authorities find radicalized individuals in Islamic communities. “Often,” Al-Guarbi explained, “would-be jihadists give plenty of warning signs … [and] those who witness a loved one undergoing this kind of transformation frequently do attempt to challenge that person’s radical views.” But all too frequently, they “choose not to alert the authorities.” Why? Because the government fails to reward good behavior, and in many cases, it even instigates young Muslims’ participation in terrorist activities, putting them in jail for at least a decade and destroying their chance at a normal life once they are released. If law enforcement in America had the same approach as Aarhus officers, things could take a different shape, and those in American Islamic communities who are struggling to find help for their loved ones would have a place to seek help. What Aarhus officers were doing was “so unexpected that it created an opening for people to think differently about their ideology”. Instead of being treated harshly, they are treated with care. “That kind of shock opens people’s minds to [accept that] maybe they were wrong about their society that they perceived as their enemy. It opens a possible window into rethinking and re-evaluating,” Kruglanski says.
______
Liberal democracy and Islam:
I quote from my Christmas message of 2015 posted on my Facebook page.
Islam, speaking from the view-point of political philosophy, is the very antithesis of secular liberal democracy. Islam altogether repudiates the philosophy of popular sovereignty and rears its polity on the foundations of the sovereignty of God and the vicegerency of man. Muslims believe that God’s comprehensive revelation was made through Prophet Muhammad and recorded in the Holy Quran. This provides the primary foundation for all Islamic institutions. Scholars and theoreticians have long argued about the compatibility of Islam and democracy. Scholarly studies disagree about whether Muslim countries as a whole are less democratic than non-Muslim countries. For political scientists and statisticians, the compatibility between Islam and democracy remains controversial, and studies have reached opposite conclusions. When more data is considered, a nuanced relationship between Islam and democracy emerges. In all but the poorest countries, Islam is associated with fewer political rights. The Islamic world is not ready to absorb the basic values of modernism and democracy. Arab and Islamic leadership are patrimonial, coercive, and authoritarian. The basic principles such as sovereignty, legitimacy, political participation and pluralism, and those individual rights and freedoms inherent in democracy do not exist in a system where Islam is the ultimate source of law. From a political perspective, Islam seems to offer the worst prospects for liberal democracy. Of the forty-six sovereign states that make up the international Islamic Conference, only one, the Turkish Republic, can be described as a somewhat liberal democracy, and even there the path to freedom has been beset by obstacles. Of the remainder, some have never tried democracy; others have tried it and failed; a few, more recently, have experimented with the idea of sharing, though not of relinquishing, power. “Arab-Muslims have oil and West wants to grab that oil” is a myth perpetuated by sympathisers of Islamic radicals. There is no liberal democracy in the oil-rich Arab Middle East. Easy resource revenues eliminate a critical link of accountability between government and citizens, by reducing incentives to tax other productive activity and use the revenue to deliver social services effectively. The same revenues also generate staggering wealth that facilitates corruption and patronage networks. Together, they consolidate the power of entrenched elites and regime supporters, sharpening income inequality and stifling political reform. This is what has happened so far in Arab-Muslim world. It is the lack of liberal democracy in Middle East that prevents human development in Arab-Muslim world. In my view, we need liberal democracy in Islamic world. Saudi Arabia, Pakistan, Afghanistan, Jordan, Egypt, Syria, Iran, Iraq and other gulf states ought to become liberal democracy. It will allow oil revenues to reach all people equally and prevent Islamic fundamentalism, sectarian hatred, proxy wars and brutal dictatorship. It will promote education and development. Till that happens, ISIS menace will continue and if ISIS is destroyed, another fundamentalist group will emerge worse than ISIS. Remember, fundamentalist groups exist in every religion. There are Christian fundamentalist groups in western nations but they can’t do much due to liberal democracies in western world. There are Hindu fundamentalist groups in India but they can’t do much due to democracy, constitution and independent judiciary. Liberal democracy separates religion from the state. The moment God, religion and holy book becomes state, problems arise. Islamic nations are the only place in the world where religion becomes state. Islam is based on the belief that God has laid down an eternal law and it is up to us to submit to it: that is what the word Islam means: submission. For believing Muslims, legitimate authority comes from God alone, and the ruler derives his power not from the people, not from his ancestors, but from God and the holy law. The state is God’s state, ruling over God’s people, and the enemy, of course, is God’s enemy. When God makes the laws, the laws become as mysterious as God is. When we make the laws, and make them for our purposes, we can be certain what they mean. Islam must evolve to accommodate liberal democracy. When people derive satisfaction from a religion whose beliefs may inhibit their development, they may be quite willing to pay a price in terms of some alteration in traditional ways of doing things. It is time for Muslims to make a trade-off between religion and development. Liberal democracy is the best trade-off so that the sanctity of Islam is preserved, extremism is contained, people get education and Islamic nations become developed nations. All Islamic nations must become liberal democracies. Islam, oil wealth and liberal democracy ought to bind together for education and development of Muslims. This is the essence of Christmas Message of 2015. Essentially this Christmas message means the root cause of radical Islamic terrorism is lack of liberal democracy in Arab-Muslim world resulting in lack of separation of the religion and the state.
_________
_________
What is common between gun lobby of America and ISIS?
They latch on to few written statements.
ISIS latch on to few statements written in Holy Quran and misinterpret it to justify violence.
Gun lobby of America latch on to second amendment of American constitution and misinterpret it to justify gun violence.
End result is same. Innocent people die.
Now there is synergy between gun violence and terrorism.
Radicalised Islamic Americans are easily buying guns to perpetuate terrorist attacks.
Distinction between gun violence and terrorism is getting blurred.
___
Gun violence in America:
Gun lobby is an organized group which attempts to influence public policy and law with respect to firearms, especially as an advocate of ownership of and access to firearms by individual citizens. Gun control refers to laws or policies that regulate within a jurisdiction the manufacture, sale, transfer, possession, modification, or use of firearms by civilians. Proponents of gun control generally argue that widespread gun ownership increases the danger of gun violence. Opponents of gun control and advocates of gun rights argue that gun control does not reduce crime, violates individual liberties, and reduces the ability of citizens to defend themselves. In the year 2015 alone, more than 50,000 shootings amounted in 12,942 plus gun homicides. The data reveals that 36 Americans were killed by gun violence daily in 2015, and in poor and impoverished communities, 70% of those murders went unsolved (where nationally it was 36%). There were 372 mass shootings in the US in 2015, killing 475 people and wounding 1,870, according to the Mass Shooting Tracker, which catalogues such incidents. A mass shooting is defined as a single shooting incident which kills or injures four or more people, including the assailant. The number of gun murders per capita in the US in 2012 – the most recent year for comparable statistics – was nearly 30 times that in the UK, at 2.9 per 100,000 compared with just 0.1. Gun homicides are rare in several other European countries, including the Netherlands and Austria. This is because it is very difficult to procure rifles and shotguns in these nations. Every year more than10, 000 people die in America due to gun violence; much more than American casualties in Iraq & Afghanistan and many more than American casualties due to ISIS and Al Qaeda.
_
Why second amendment in the first place?
The American Revolution was a political upheaval that took place between 1765 and 1783 during which colonists in the Thirteen American Colonies rejected the British monarchy and aristocracy, overthrew the authority of Great Britain, and founded the United States of America. The American Revolutionary War (1775–1783), also known as the American War of Independence and the Revolutionary War in the United States, was the armed conflict between Great Britain and thirteen of its North American colonies, which had declared themselves the independent United States of America. Requested by several states during the Constitutional ratification debates, the widespread desire for such an amendment reflected the lingering resentment over the widespread efforts of the British to confiscate the colonists’ firearms at the outbreak of the Revolutionary War. Patrick Henry had rhetorically asked, shall we be stronger, “when we are totally disarmed, and when a British Guard shall be stationed in every house?”
As passed by the Congress and preserved in the National Archives, with the rest of the original hand-written copy of the Bill of Rights prepared by scribe William Lambert, the second amendment says:
A well-regulated Militia, being necessary to the security of a Free State, the right of the people to keep and bear Arms, shall not be infringed.
Patrick Henry believed that a citizenry trained in arms was the only sure guarantor of liberty while Alexander Hamilton wrote in Federalist No. 29 that “little more can be reasonably aimed at, with respect to the people at large, than to have them properly armed …”
The Second Amendment (1791) protects the right of individuals to keep and bear arms.
Although the Supreme Court has ruled that this right applies to individuals, not merely to collective militias, it has also held that the government may regulate or place some limits on the manufacture, ownership and sale of firearms or similar devices. The Supreme Court also suggested that the United States Constitution would not disallow regulations prohibiting criminals and the mentally ill from firearm possession.
_
My view on second amendment:
The second amendment was enacted to ensure the right of the people to keep and bear firearms for the security of a free state and the only sure guarantor of liberty against British colonial rule. It guarantees Americans the right to fight back – with firearms – against any tyrannical/colonial ruler/government. It has nothing to do with self-defense against criminals. The job of police is to maintain law and order, and not ordinary citizens. The tragic shootings in Baton Rouge and Dallas are yet another reminder that the second amendment, which grants Americans a constitutional right to be armed, is an extreme danger to police officers. It always was and it always will be. The right to bear arms means that police operate in an environment in which members of the public can purchase, store and practice with weaponry similar to that of police and military. Some of this weaponry can send pieces of armor-piercing lead through whatever bullet protection police officers may be wearing. This threat makes many police feel scared for their lives. Gun lobby allows easy procurement of guns resulting in gun violence in America which kills more than 10.000 innocent people every year. Nowadays radicalized individuals also buy the same guns to perpetuate terrorist violence. Orlando and San Bernardino showed the path of merger of gun violence and terrorism. Had there been tough gun control laws similar to European nations, gun violence could have been prevented and even terrorist attacks could have been prevented. I strongly recommend very tough gun control laws not only to prevent gun violence but also prevent terrorism and shooting of police officers.
__________
__________
Many terrorist are petty criminals:
I quote from my article on ‘Science of Crime’:
Spread of fear and publicity are the two things most terrorist master minds want and we must deny it. If bombs are planted in trains, all trains must run full. If bombs are planted on high court, all courts must run full house. By this way we can combat terrorism. Media must not give publicity to terrorists by showing terrorist acts 24 hours on television or talking to terrorists on phone and showing it “live”. Take the fear and the publicity out, and you will find terrorist becomes an ordinary criminal. Believe me, many terrorists were petty criminals before they became terrorists. Terrorism is new Avatar of criminals. Look at Kasab of 26/11. Look at Bouhlel of Nice attack. They were petty criminals who metamorphosed into terrorism after radicalization. Religion provided ground for enhancement of criminality and justification of violence. Who would have known them had they not become terrorists. Terrorism gave them unimaginable publicity. Back in 2012, at the beginning of the wave of terrorist violence that has now broken out over France, a 23-year-old petty criminal called Mohammed Merah killed seven people in Toulouse and the nearby town of Montauban. While police surrounded his small apartment, Merah spent his final hours editing together a 20-minute video clip of images of his killings. Shortly before dying in a firefight, Merah slipped through the police lines around his home and posted a USB key containing the clip to Al-Jazeera, the Qatar-based TV network. It was never broadcast. But the fact that Merah, as a final act, was still thinking about publicity, and using the mainstream media to obtain that publicity, is striking. Police knows most of petty criminals and it is time for police to know whether they have become radicalized.
_
One in five terrorist has criminal background:
_
What must a terrorist do differently than an ordinary criminal to carry out his crime successfully?
Consider the following example that compares a suicide bomber to a serial murderer.
Terrorist behaviour:
A suicide bomber must take several steps in order to carry out his task. He must obtain an explosive belt that can be concealed on his person; he must choose a target; he must figure out how to reach that target without being caught; and he must have a contingency plan should he be apprehended before he reaches his target or before he can detonate the bomb.
Criminal behaviour:
A serial murderer must take several steps in order to kill his victim. He must select a target and figure out the best way to approach that target and carry out the murder without being caught; he must decide on the method of killing; he must decide how to dispose of the body; and he must plan his escape route.
The common element in these two examples is the logical sequence of steps that both the terrorist and the criminal must take to see their missions through to successful conclusions.
________
________
Now let me discuss commonality of shortcomings in intelligence against various terror attacks:
_
1. Can police prevent terrorist attack?
Look at Orlando, Nice and Dhaka attack.
Police was present at the onset of these attacks but could not prevent massacre.
We the ordinary people have to do something.
Traditional protocol to survive a terror attack is to ‘Run and Hide’.
I suggest ‘Confront’.
Remember, there are few terrorists but there are dozens of people. Just attack them. Look at various terror attacks. Terrorists spend time in dividing people between Muslims and non-Muslims; and between natives and foreigners. Grab that time to attack them. Most terrorists are not hardened criminals but radicalised petty criminals, radicalised individuals and persons with various grievances. If dozens attack them, they can be overpowered despite being armed albeit with some casualty. Ordinary people may bear some casualty but better than all getting slaughtered. On one hand there is some chance of survival, on the other hand zero chance. So attack terrorists with whatever you have in hand.
_
2. No hostage situation.
Look at Dhaka, 26/11 and Orlando attack.
Terrorists have taken hostages and in order to save their lives, police/security forces delayed their response.
Terrorists are there to kill as many as possible. They take hostages to buy time to defend themselves, publish terror videos online and get instructions from their handlers.
No hostage situation to be allowed.
_
Let me briefly discuss two hostage situations:
A. Moscow theater hostage crisis 2002:
The Moscow theater hostage crisis was the seizure of a crowded Dubrovka Theater by 40 to 50 armed Chechens on 23 October 2002 that involved 850 hostages and ended with the death of at least 170 people. Russian security forces pumped an undisclosed chemical agent into the building’s ventilation system and raided it. All 40 of the attackers were killed and about 130 hostages died, including nine foreigners, due to adverse reactions to the gas. All but two of the hostages who died during the siege were killed by the toxic substance pumped into the theater to subdue the militants. The use of the gas was widely condemned as heavy-handed, but the American and British governments deemed Russia’s actions justifiable.
B. Sydney hostage crisis 2014:
The 2014 Sydney hostage crisis, commonly known as the Sydney siege, occurred on 15–16 December 2014 when a lone gunman, Man Haron Monis, held hostage ten customers and eight employees of a Lindt chocolate café located at Martin Place in Sydney. The Sydney siege led to a 16-hour standoff, after which a gunshot was heard from inside and police officers from the Tactical Operations Unit stormed the café. Hostage Tori Johnson was killed by Monis and hostage Katrina Dawson was killed by a police bullet ricochet in the subsequent raid. Monis was also killed. Three other hostages and a police officer were injured by police gunfire during the raid. Police have been criticised over their handling of the siege for not taking proactive action earlier and for the deaths of hostages at the end of the siege.
_
Let there be a national and international policy armed by laws that disallow any hostage taking by terror suspect. The moment police knows probable terrorist attack, kill or capture terrorist at the earliest (with full preparation) no matter whether they have taken hostages or not.
_
3. Publish photographs of probable terror suspects:
Look at Orlando and Dhaka attacks.
FBI has interviewed Mateen three times. Three attackers of Dhaka attack were missing from their home and their parents have filed missing complaint with police and police was suspecting them of getting radicalized. Why their photographs were not published on national TV/newspapers as probable terror suspects? At least it could have dissuaded them to carry out attack or prevented them from getting weapons. The Kerala police of India have launched a high-level investigation into reports suggesting that 20 youths from Kasaragod and Palakkad districts, who were found missing for more than a month, may have joined Islamic State. The parents received a series of messages from their children indicating that they had reached the Islamic State camp. The youths, all in their mid-twenties, are well-educated and come from well-to-do families. Why not make their photo public on national TV/newspapers as terror suspects? You may say that many terror suspects may be in fact innocent, so why defame innocents? Well, that is the price we have to pay to fight terrorism. Some privacy, some freedom and some reputation have to be sacrificed by everybody. You can’t have it both ways. You can’t find a needle in haystack. Right to life is greater than right to freedom, right to privacy and right to reputation. Both false positives and false negatives pose problems for counterterrorist efforts. In the case of false positives, a counterterrorism analyst searching for evidence of terrorist attack planning may obtain personal information on a number of individuals. All of these individuals surrender some privacy, and those who have not been involved in terrorist activity (the false positives) have had their privacy violated or their rights compromised despite the lack of such involvement. One might argue that the consequences of a false negative (a terrorist plan is not detected and many people die) are in some sense much larger than the consequences of a false positive (an innocent person loses privacy or is detained). For this reason, many decision makers assert that it is better to be safe than sorry. When government officials talk about security, they’re talking about protecting the general public from threats–foreign and domestic. Their goal isn’t to make money or exude trust among customers, but rather to stop the bad guys from doing bad things. It may sound Orwellian–punishing the good people to catch a few bad guys–but the government will argue that sacrificing some civil liberties is necessary to protect against the terrorist threat. In other words, there are situations where security trumps privacy.
_
4. Do general police have weapons to fight terrorist?
Look at 26/11 and Nice attack. Police have confronted attackers at onset of terror attack but could not kill terrorists. If terrorist have AK 47, semi-automatic or fully automatic rifles, then police should have better weapons.
_
The new heavily armed face of counter terror policing is revealed in U.K.
The latest face of anti-terror policing in London has been unveiled as a new batch of highly trained officers prepares to take to the streets. Equipped with SIG 516 semi-automatic carbines and Glock 9mm sidearms, the counter-terror police are capable of racing to the scene of any potential incident on BMW F800 motorcycles. Riding pillion the officers will be able to cut through the heavy London traffic on bikes which are capable of reaching top speeds of 120mph. Despite the fact they are carrying guns they are still police officers and the public can approach and talk to them, they are out on streets to reassure and help the public. The rest of the world should follow U.K. in arming police.
__________
__________
Big picture of intelligence against terrorism:
What is good and what is evil is debatable and people can be a combination of ‘good’ and ‘evil’ qualities. ‘Good’ means benevolence, altruism, selflessness and the ability to empathise with other people, to feel compassion for them, and to put their needs before your own. ‘Good’ can see beyond gender, race, religion, nationality and ethnicity. ‘Evil’ is opposite of ‘good’ meaning selfish, self-absorbed, narcissistic and the inability to empathise with others. Let me start with 9/11 attack. You need so many architects, engineers, contractors and workers to put their efforts over years to construct world trade centre twin tower at New York but it was destroyed in minutes by terrorist who flew airplanes into it. You need higher intelligence to construct but lower intelligence to destroy. Those 9/11 terrorists did not need lot of intelligence to destroy twin towers. People who constructed twin towers were far more intelligent than people who destroyed it. Both good people and evil people could be intelligent but comparably intelligence of good people is superior to intelligence of evil people. Remember this for ever. Terrorists and their masterminds are evil people with lower intelligence. We have to use our higher intelligence to capture them before they attack us. Sadly, many of the intelligence and law enforcement officers are not highly intelligent. Pathankot, Orlando and 26/11attack showed demonstration of poverty of intelligence by intelligence and law enforcement agencies. We need help from scientists, doctors, engineers, authors and analysts to get involved in intelligence against terrorism. Top intellectual cream of nation must be involved in solving terrorism menace.
__________
__________
The moral of the story:
_
1. The ideology behind present-day radical Islamic terrorism is that, Islam being a political system, it is the duty of all Muslims to establish Islamic rule in the world. Having failed to achieve this objective of establishing Islamic rule by the peaceful method, they have started resorting to violence, the idea being that if we cannot eliminate non-Islamic rule, then let us at least de-stabilize it and pave the way for Islamic rule. The change desired by radical Islamic terrorists is so badly needed that failure to achieve change is seen as a worse outcome than their own death or the deaths of innocent civilians. With a goal of creating a caliphate advocating Sharia law and religious intolerance in the name of God, the terrorists appeals to a sense of victimhood identity and martyrdom, and thereby justifies mass murder.
_
2. The root cause of radical Islamic terrorism is lack of liberal democracy in Arab-Muslim world resulting in lack of separation between the religion and the state. Nobody should overlook the fact that solid majority of Muslims worldwide want the Sharia ‘traditional Islamic law’ to be recognized as the official law of their country.
_
3. Many lone wolves have issues of identity, sexuality, mental health, financial problem, criminal behaviour and a violent past; so they latch on to ideology to justify their violent actions. They use novel terror methods which challenges intelligence agency notions and counter-terrorism preconceptions. Lone wolves are often harder to detect because of their citizenship or legal status and ability to stay under the radar. Random multiple lone-wolf phenomena has overwhelmed police and intelligence services in France and Germany.
_
4. The lone wolf terrorist depends on virtual communities on internet because there communication is free from the constant trauma of real-world interactions. Internet also provides a lot of opportunity for lone wolves to learn about terrorist tactics and targets and to become radicalized via reading ideological web pages and tweets and blogs. On the other hand, tracking their internet activities help us identify radicalised potential terrorists by web crawler program instructed to look for specific markers in the social network posts of people who visit radical sites.
_
5. Internet is being invoked in fearful terms by politicians because it is easier to point finger there than unpack reasons behind terrorist acts—the growth of hateful radical ideologies, racial and ethnic tensions, the ease of buying guns and explosive material, death of innocent civilians as collateral damage, and evil minds that embrace violence.
_
6. There are strong correlations between humiliation and the search for an extremist radical Islamic ideology. Militant groups like ISIS prey on young men and women who are the victims of discrimination based on race, religion, ethnicity and nationality. Orlando attacker Mateen and San Bernardino attacker Farook were repeatedly taunted for their religion by their co-workers.
__
7. Intelligence of a living organism is defined as ability to receive, understand, process, memorize, comprehend, rationalize, learn, think and judge various sensory inputs from environment in a given circumstance and come out with best possible solution to the problem posed by environment and/or perform better in environment. Intelligence in counter-terrorism means to collect, analyse and utilize information to prevent/halt/solve terrorism, catch terrorists alive/dead, uncover terrorist modus operandi and destroy terror infrastructure by penetrating terrorist’s intelligence and security system. In this article, both meanings of intelligence are used concurrently to defeat terrorism.
_
8. Good intelligence is the best weapon against terrorism and intelligence gaps hurt efforts to prevent more terror. While intelligence alone cannot stop the next terrorist attack, it is the critical first step in identifying and possibly preventing one. Intelligence is essential in countering terrorism, in diminishing its tactical effects and strategic importance.
_
9. Terrorism is carried out by very few people or even single individual, needs little money and limited communication. So intelligence focus should be on intent of suspects rather than their capability.
_
10. Intelligence against terrorism is successful only when law enforcement knows who the enemy is, and where and when he/she is most likely to strike next. Since terrorist operations are covert, efforts to obtain this information must also be largely covert.
_
11. Synergy between human intelligence and technical intelligence is a must to develop effective tool to combat terrorism. No matter advancements in technical intelligence, only human intelligence is capable of providing first-hand information which cannot possibly be substituted by any other means and cannot become out-dated. Robust human intelligence network acts as a deterrent to the impending terrorist strikes.
_
12. Intelligence sharing and coordination between intelligence agencies (CIA, IB etc.) and investigation agencies (FBI, police, CBI, NIA etc.) is a must for preventing terrorist attacks. Intelligence gathering can be done by both intelligence and investigation agencies but investigation agencies are accountable to courts. Countering terrorism requires close cooperation between law enforcement and intelligence agencies; some terrorists will need to be brought to justice in courts, but others are dealt with by military forces or covert actions.
_
13. In counter-terrorism, military intelligence must work in synergy with police, reduce civilian casualties and focus on winning hearts and minds of population rather than tactical victories.
_
14. Police agencies with general responsibilities for law & order maintenance and crime prevention can contribute more to counter-terrorism by focusing on their standard operations than developing specialized, particularly covert, counter-terrorism capabilities. Police has unique advantages in counter-terrorism by providing unprecedented access to communities resulting in obtaining information about activities that are the precursors of terrorism. Many lone wolf terrorists have had some interaction with local police due to their criminal behaviour before they became radicalized. In many cases, the police are already aware of the activities of local extremist groups with established records of advocating and carrying out violent acts, and often know the players involved because of their past participation in terrorist activity.
_
15. One in five terrorist has criminal background. Religion provides ground for enhancement of criminality and justification of violence. Terrorism gives them unimaginable publicity and that is why they leap from criminality to terrorism. Since police knows most of petty criminals in their area, it is time for police to know whether they have become radicalized.
_
16. Mass surveillance of entire population or entire Muslim population in a nation leads to diversion of limited intelligence resources in pursuit of huge numbers of false leads.
_
17. Only a fraction of terror suspects can be watched 24/7 because it takes 20 to 25 people to keep somebody under surveillance 24/7 and there are thousands of terror suspects; therefore it is virtually impossible to prevent ‘lone-wolf’ killings. On the other hand, walking away from terrorism is a common phenomenon. It is not that they necessarily abandon their radical views, but that they abandon violence as a means of expressing them. Out of thousands of plausible would-be terrorists, most don’t become terrorists. So spending enormous amount of resources on would-be terrorists is futile as most would never become terrorists.
_
18. European Union’s open door policy promotes openness and free movement of people and goods with privacy unthinkingly allows weapons and terrorists to flow freely in-between various European nations. In my view, if people want to defeat terrorism, they will have to sacrifice some freedom and some privacy occasionally. Remember, terrorists are using freedom and privacy to attack us. Sometimes individual rights need to be balanced against the need to protect collective security. Right to life is greater than right to freedom and right to privacy. On the other hand, we must not fall in the trap of abandoning democratic values, civil liberties and human rights upon which democratic societies are based as it would be the greatest success the terrorist can ever achieve.
_
19. It is inconceivable to think that close family members knew nothing about radicalization of an individual. If you want to eradicate radical Islamic terrorism, family members must come forward and help police catch potential terrorists. Failure to do so amount to veiled support to terrorism. In Russia, families are rounded up in high-profile terror cases and held until the militant either gives up or is killed. The Russian approach has been effective in curbing terrorism. Also, analysts estimate that a third of the participants in terrorist acts are related to another attacker. We have to legislate new terror laws by which a terrorist’s family members are arrested on the presumption of supporting terrorism. Although some of them may be innocent, they can get acquittal through courts. This will send a strong message to would-be terrorists that if you kill innocent people in suicide attacks, your family members may go to jail. This will send a strong message to family members of potential terrorist that if they look the other way, there are in trouble.
_
20. To say that Islam is a religion of peace, to crush dissent in the name of fighting Islamophobia, and to offer apologies to Muslims is not the solution of radical Islamic terrorism. The attempt to brush off radical Islamic ideology as work of few extremists is turning a blind eye to terrorism. Although most Muslims are peaceful people who disapprove of terrorism, a consistent minority of 20% to 40% approves of at least some form of terrorism (e.g. Palestinian and Kashmiri militants) although very few of them would actually take part in terror attack. The way to end radical Islamic terrorism is to expose and corner extremist individuals not only by their family members but also by moderate believers. Those family members and moderate believers who inform law enforcement about radicalized potential terrorists must be protected and rewarded by the government.
_
21. If any Muslim youth is missing from home; and parents and/or police suspect radicalization, publish their photo on national TV/newspapers as probable terror suspects. This will deter them to carry out terror attacks or prevent them from getting weapons. If they are indeed innocent, then return home and convince police about their innocence.
_
22. What is common between gun lobby of America and ISIS? They latch on to few written statements. ISIS latch on to few statements written in Holy Quran and misinterpret it to justify violence. Gun lobby of America latch on to second amendment of American constitution and misinterpret it to justify gun violence. The second amendment was enacted to ensure the right of the people to keep and bear firearms for the security of a free state and the only sure guarantor of liberty against British colonial rule. It guarantees Americans the right to fight back – with firearms – against any tyrannical/colonial ruler/government. It has nothing to do with self-defense against criminals. Lax gun laws not only allowed more than10,000 deaths every year in America due to gun violence but also allowed radicalized individuals to carry out terrorist attacks as in Orlando and San Bernardino; and also allowed shooting of police officers as in Baton Rouge and Dallas. I strongly recommend very tough gun control laws not only to prevent gun violence but also prevent terrorism and shooting of police officers.
_
23. Intelligence is ultimately a human endeavour thereby inherently imperfect, therefore intelligence failure is inevitable despite better resources, better methods and better coordination. As with crime, perfect safety is impossible from terrorism. It is unrealistic to expect government and intelligence agencies to uncover and thwart every plot. There are too many potential actors and too many vulnerable targets. Citizens need to assume some responsibility for their own security and for the security of their communities. Citizens ought to become educated about terrorist behavior and report it when they see it. Instead of ‘Run and Hide’ protocol for lay people in terror attack, we must adopt ‘Confront’ protocol.
_
24. Let there be national and international policy that supports attacking terrorists at the earliest (with full preparation) irrespective of whether they have taken hostages or not. No hostage situation in terrorism to be allowed or tolerated.
_
25. Equip general police with better weapons to fight terrorists.
_
26. Violence begins in mind and therefore should be uprooted from mind. Terrorism will persist in one form or another until the ideology of violence is countered with another ideology based on peace. That ideology of peace is to convince radicalized Muslim youth to come home and help them with going back to school/college, finding an apartment, finding a job, meeting with a psychiatrist or whatever they needed to fully integrate back into society. This will open their minds to accept that maybe they were wrong about their society that they perceived as their enemy.
_
27. Both good people and evil people could be intelligent but comparably intelligence of good people is superior to intelligence of evil people. You need higher intelligence to construct but lower intelligence to destroy. Terrorists by the very nature of their acts are people with lower intelligence. We have to use our higher intelligence to capture them before they attack us. Sadly, many of the intelligence and law enforcement officers are not highly intelligent.
_
28. Top intellectual cream of nation for example scientists, doctors, engineers, authors and analysts must be involved in intelligence against terrorism to solve terrorism menace.
_________
Dr. Rajiv Desai. MD.
August 8, 2016
________
Postscript:
This article is written not to demoralize police and intelligence agencies but to enhance their abilities and help them.
________



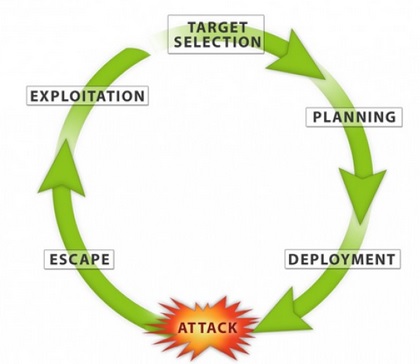
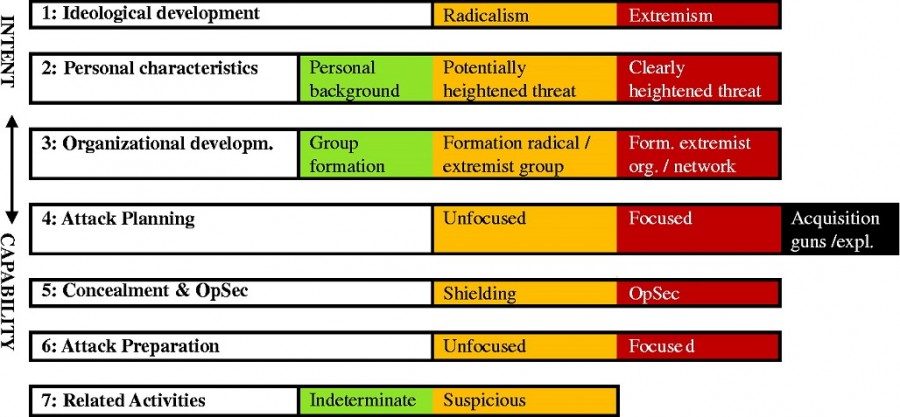
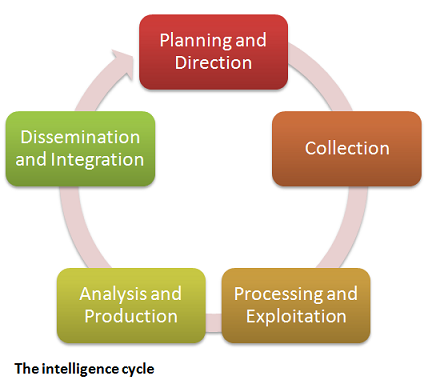
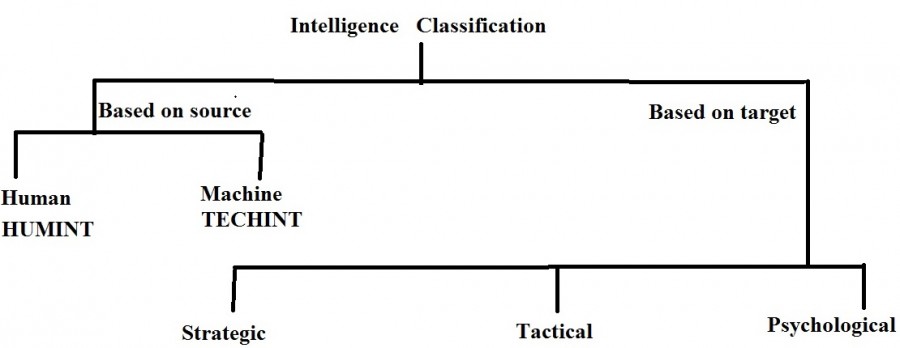
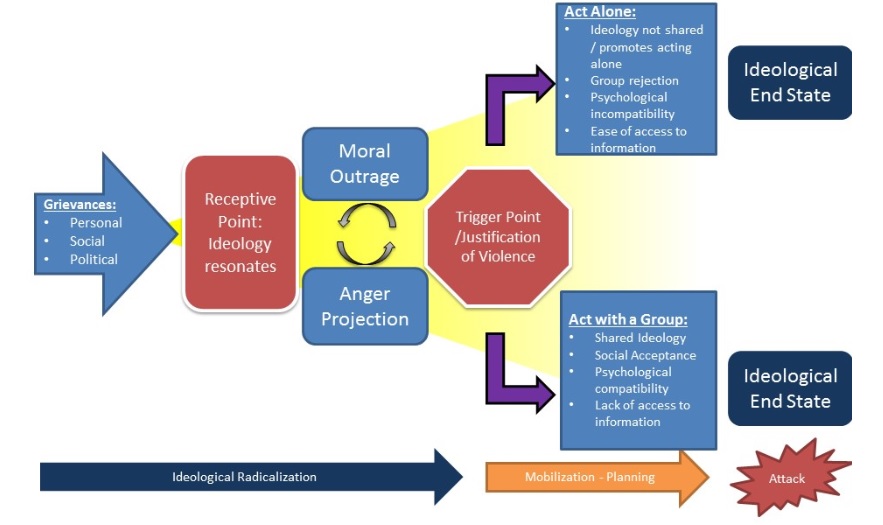

Nice post. I learn something new and challenging on blogs I stumbleupon every day. It’s always interesting to read articles from other authors and use something from other sites.
I like reading through an article that can make men and women think. Also, thanks for allowing for me to comment.
I want to to thank you for this good read!! I absolutely loved every bit of it. I have got you bookmarked to look at new things you post…
Having read this I believed it was really enlightening. I appreciate you finding the time and energy to put this content together. I once again find myself personally spending a lot of time both reading and leaving comments. But so what, it was still worth it!
I’m impressed, I have to admit. Rarely do I encounter a blog that’s both equally educative and engaging, and without a doubt, you have hit the nail on the head. The problem is something too few people are speaking intelligently about. I’m very happy I found this in my search for something regarding this.
I was able to find good advice from your blog articles.
I could not resist commenting. Exceptionally well written.