Dr Rajiv Desai
An Educational Blog
INTERNET OF THINGS (IoT)
INTERNET OF THINGS (IoT):
_______
_______
Prologue:
The phrase “Internet of Things” was coined by Kevin Ashton an expert on digital innovation in 1999 as the title of a corporate presentation he made at his place of employment, Proctor & Gamble. During his time there, Kevin Ashton came up with the idea of putting a RFID (Radio Frequency Identification) tag on each lipstick and having them communicate with a radio receiver on the shelf to track sales & inventory, and signal when restocking was needed. He theorized that such data collection can be used to solve lots of problems in the real world. The Internet is continuously changing and evolving. The main communication form of present Internet is human to human. The Internet of Things (IoT) can be considered as evolution of Internet that realizes machine-to-machine (M2M) learning. The first version of Internet was about data created by people, while the next version is about data created by things. Most of us think about being connected in terms of computers, tablets and smartphones. IoT describes a world where just about anything can be connected and communicate in an intelligent fashion. The IoT embeds some intelligence in Internet connected objects to communicate, exchange information, take decisions, invoke actions and provide amazing services. Billions of connected devices are part of the Internet of Things. They use built-in hardware and software to send and receive data via various communication protocols. They might use our smartphones as their gateway to the Internet, connect to some other piece of hardware in our homes that’s acting as a hub or connect directly through our home Internet service. They often send data to cloud-computing servers where it’s then aggregated and analysed. We can usually access the results via apps or browsers on our mobile devices or home computers. Merging virtual world with physical things gives anyone with a mobile device and appropriate authorization, the power to monitor or control anything. IoT heralds a vision of the future Internet where connecting physical things from refrigerators to washing machines to cars to banknotes through a network, will let them take an active part in the Internet, exchanging information about themselves and their surroundings. This will give immediate access to information about the physical world and the objects in it—leading to innovative services and increase in efficiency & productivity. IoT has become a leading theme in conferences, books, academic and professional journals, university courses, research summer schools, research programs of companies, universities, applied research organizations and government-funded research programs, as well as reports on global future developments and industry analysis. This article is targeted towards students who are interested in understanding and contributing to the on-going merger of the physical world of things and the Internet.
_______
Note:
Please read my articles ‘The Computer and Internet’ and ‘Smartphone’ in this website before reading this article as computer, internet and smartphone are intimately linked to ‘Internet of Things’, and without understanding basic concepts of internet, one cannot understand IoT. Is Uber an IoT application? Most people would say it is not; it’s just a pair of smartphone apps connecting a passenger and driver. But imagine for a moment the consumer end of the Uber app as it is today, and on the other end, a driverless car. You would immediately see that as IoT.
_______
Abbreviations and synonyms:
RFID = Radio Frequency Identification
M2M = Machine-to-Machine communication
CPS = Cyber-Physical System
IoE = Internet of Everything
BLE = Bluetooth Low Energy
NFC = Near Field Communication
WoT = Web of Things
IIoT = Industrial Internet of Things
WSN = Wireless Sensor Networks
API = Application Program Interface
QR code = Quick Response Code
_______
Here are a few examples of how the Internet of Things could transform our daily lives:
1. You just walked out the door without your keys in your pocket. “Beep Beep”. Your smart-door delays locking the door for 30 seconds because you just left without your keys, giving you the chance to duck back inside if need be.
2. You’ve got a history of heart disease. So much so that your GP recommends that you get an unobtrusive, internal heart monitor implanted into your arm. It constantly monitors your heart rhythm and detects even the smallest arrhythmias. Any alarming changes and it sends a text message to your phone: “This is your heart. Please proceed to a hospital immediately.”
3. You are fast asleep in your home and fire broke out. The smoke sets off your smoke alarm but you’re not hearing the alarm. Then your smoke alarm sends out a message to the motion detectors throughout your house. They notice the alarm is going off, but there is no movement in the house. They send a message back to the smoke detector, which sends a signal to the local fire brigade, and they come home to extinguish fire.
4. You’re walking down the supermarket aisle, and you get to the milk fridge. Your shopping trolley vibrates, and the screen mounted on the trolley handles displays a message: “There is no milk in your fridge. Would you like to purchase some?” The fridge has sent a message to your phone. Your phone knows that you’re in the supermarket and has told your trolley. Your trolley knows you’re next to the milk fridge and has told you that you’re out of milk. So, you buy milk. Then you simply wheel your trolley out through the smart gates, instantly scanning all the products in your trolley and charging your credit card. You receive an email with the itemized receipt.
5. You fall hard from your bike. You’ve hit your head, you’re unconscious and you’re away from home. The accelerometer in your helmet has detected that you’ve hit your head. Your helmet ‘calls out’ to see if your bike is nearby (it is) and if it’s moving (it’s not). Your bike sounds an emergency alarm for five seconds. If it’s not deactivated, your bike sends your exact location to an ambulance, and any other emergency contacts you’ve pre-listed. Your bike alarm continues to sound, attracting the attention of passers-by. It also sends out a signal to the road sign 1km down the road warning motorists to slow down.
________
________
Introduction to internet of things:
Nowadays the main communication form on the Internet is human-human. But it is foreseeable that any object will have a unique way of identification and can be addressed so that every object can be connected. The Internet will become the Internet of Things. The communicate forms will expand from human-human to human-human, human-thing and thing-thing (also called M2M). What IoT means is that everyday objects, ones that we interact with regularly, will be capable of ‘talking’ to each other. Humans will fall more and more out of the loop. Machines will be talking to machines, objects talking to objects. This will bring a new ubiquitous computing and communication era and change people’s life extremely. The Internet of Things (IoT) is a dynamic global information network consisting of Internet-connected objects, such as Radio frequency identifications, sensors, actuators, as well as other instruments and smart appliances that are becoming an integral component of the future Internet. Over the last decade, we have seen a large number of the IoT solutions developed by start-ups, small and medium enterprises, large corporations, academic research institutes (such as universities), and private and public research organizations making their way into the market. The Internet of Things (IoT) envisages a future in which digital and physical things or objects (e.g., refrigerators, TVs, cars) can be connected by means of suitable information and communication technologies, to enable a range of applications and services. The IoT characteristics include an ultra-large-scale network of things, device and network level heterogeneity, and large numbers of events generated spontaneously by these things.
_
Many of us have dreamed of smart homes where our appliances do our bidding automatically. The alarm sounds and the coffee pot starts brewing the moment you want to start your day. Lights come on as you walk through the house. Some unseen computing device responds to your voice commands to read your schedule and messages to you while you get ready, then turns on the TV news. Your car drives you to work via the least congested route, freeing you up to get caught up on your reading or prep for your morning meeting while in transit. We’ve read and seen such things in science fiction for decades, but they’re now either already possible or on the brink of coming into being. And this new tech is forming the basis of what people are calling the Internet of Things. According to a recent survey and study done by Pew Research Internet Project, a large majority of the technology experts and engaged Internet users who responded — 83 percent — agreed with the notion that the Internet/Cloud of Things and embedded & wearable computing will have widespread and beneficial effects by 2025.
_
Everyday objects are becoming increasingly connected to the Internet. Whether it’s a smart phone that allows you to check your home security, or an app that lets you start your car or close your garage door from anywhere in the world; these technologies are becoming part of what is known as the Internet of Things (IoT). An observable trend is the rapid deployment and consumer use of IoT devices, which can communicate with one another and share information without user input or activity. This trend is evident in the now billions of IoT devices in use by individuals and organizations in public and private sectors.
_
These IoT devices connect people, animals, plants, and objects to the Internet:
People have, and can, become part of the IoT through wearable devices and clothing, including, but certainly not limited to: Garmin Vivoactive, a wearable device that includes, among other features, a global positioning system to track exercise activities; Cityzen Sciences’ D-Shirt that tracks the heart-rate and temperature of a person, as well as the speed and intensity of an individual’s workout; Athos clothing which monitors heart-rate, breathing, and progress of workout and goals; Ralph Lauren’s Polo Tech Shirt designed to monitor the calories burned and the intensity of a workout, stress levels, and heart-rate, among other things; Misfit Shine, a wearable device that tracks adult exercise activities and sleep patterns; Exmovere’s ‘Exmobaby’ that tracks baby’s vital signs, mood, temperature, and movement; and Mimo’s Smart Nursery, which monitors babies’ positions, breathing, and sleeping patterns. Like humans, animals have been (and can be) connected to the IoT via sensors and wearable devices. For example, the Scout5000 enables the monitoring of pets by providing their owners with an activity pedometer, live streaming of pet activities, and the ability to engage in two-way remote communication with their pet. Similarly to animals, plants are also linked to the IoT via sensors. A case in point are Koubachi sensors that are designed to monitor plants by measuring conditions such as soil moisture and light, for optimal plant growth in individuals’ homes and gardens. In addition to people, animals, and plants, objects are IoT-enabled. These objects can be found in a variety of settings, including homes, work places, and education and healthcare centres. In the home, for example, IoT devices have afforded individuals the opportunity to remotely monitor and control energy use, household appliances, and the security of their homes. An example of an IoT technology used in homes is ‘Netatmo Welcome’. This technology uses cameras with facial recognition software to identify entrants to and/or those within a home. Those identified by the camera, both known and unknown, are sent to the owner’s smartphone. ‘Netatmo Welcome’ keeps a record of those who entered the home and the time and date that they entered. It further provides owners with access to the camera’s live streams and past events. Another area in which IoT devices are used is in healthcare. There are numerous IoT-enabled medical devices that are designed to remotely monitor patients’ vital signs, such as breathing, heart rate, blood pressure, and temperature, and internal functions, such as blood sugar levels. Some IoT medical devices are designed to alert physicians in a timely manner if the patient’s vital signs or internal functions are abnormal to prevent harm or even death of a patient.
_
The purpose of connecting people, animals, plants, and objects to the Internet is to enable their remote, real-time monitoring and the vast collection, storage, usage, and sharing of information about them in order to provide a service to the user. Ultimately, the automation capabilities of the IoT are designed to improve efficiency of actions and activities. IoT devices benefit the user by saving money and time, improving quality of life, and increasing convenience. For medical devices, these benefits can include lowered costs of care, improved quality of care, and improved outcomes for patients. These benefits and conveniences, however, come at a cost: namely to security and privacy. Overall, IoT devices were not built with security or consumer privacy in mind. Accordingly, measures are needed to ensure that these devices and the data they collect are protected from cyber-attacks and unauthorized access, monitoring, sharing, and use, to ensure that we can use IoT devices to our advantage and not to our detriment.
_
What is the Internet of Things?
Simply put, this is the concept of basically connecting any device with an on and off switch to the Internet (and/or to each other). This includes everything from cellphones, coffee makers, washing machines, headphones, lamps, wearable devices and almost anything else you can think of. This also applies to components of machines, for example a jet engine of an airplane or the drill of an oil rig. The analyst firm Gartner says that by 2020 there will be over 26 billion connected devices… That’s a lot of connections (some even estimate this number to be much higher, over 100 billion). The IoT is a giant network of connected “things” (which also includes people). The relationship will be between people-people, people-things, and things-things. The Internet of Things will connect everything with everyone in an integrated global network. People, machines, natural resources, production lines, logistics networks, consumption habits, recycling flows, and virtually every other aspect of economic and social life will be linked via sensors and software to the IoT platform, continually feeding Big Data to every node—businesses, homes, vehicles—moment to moment, in real time. Big Data, in turn, will be processed with advanced analytics, transformed into predictive algorithms, and programmed into automated systems to improve thermodynamic efficiencies, dramatically increase productivity, and reduce the marginal cost of producing and delivering a full range of goods and services to near zero across the entire economy. Like the internet, there is no particular controller of the Internet of Things. In a general sense, the IoT is composed of all the connections between things and the “structured” (organized) and unstructured (unorganized) data from those objects. The IoT allows computer scientists, healthcare companies, finance companies, tech companies, food companies, energy companies, etc. to generate insights and analytics from the world’s data.
_
_
The connection of physical things to the Internet makes it possible to access remote sensor data and to control the physical world from a distance. The mash-up of captured data with data retrieved from other sources, e.g., with data that is contained in the Web, gives rise to new synergistic services that go beyond the services that can be provided by an isolated embedded system. The Internet of Things is based on this vision. A smart object, which is the building block of the Internet of Things, is just another name for an embedded system that is connected to the Internet. There is another technology that points in the same direction – the RFID technology. The RFID technology, an extension of the ubiquitous optical bar codes that are found on many every-day products, requires the attachment of a smart low-cost electronic ID-tag to a product such that the identity of a product can be decoded from a distance. By putting more intelligence into the ID tag, the tagged thing becomes a smart object. The novelty of the Internet-of-Things (IoT) is not in any new disruptive technology, but in the pervasive deployment of smart objects.
_
To achieve the notion of the Internet of things, you need most of the following pieces in place:
•Network connectivity, which is typically wireless
•Sensors and/or user input that capture or generate data
•Computational capabilities, at the device and/or back end
Also you could have a store-and-forward connectivity approach such as plugging a device into a USB port on a computer. Store-and-forward is essential in any case, because connectivity is not ubiquitous, so you need a way to send data captured when offline. That’s a hallmark of the Internet, which was initially designed to allow communications even after a nuclear war through store-and-forward and auto-rerouting. The IoT concept simply applies to devices connected and networked together through the Internet. Sometimes IoT devices are everyday devices that become Internet-enabled, and sometimes they are completely new devices that only make sense in a connected environment. All of this is enabled by more and more computing power in smaller and smaller packages and near-ubiquitous wireless Internet.
__
Internet of Things is a new revolution of the Internet. Objects make themselves recognizable and they get intelligence thanks to the fact that they can communicate information about themselves and they can access information that has been aggregated by other things. Alarm clocks go off early if there’s traffic; plants communicate to the sprinkler system when it’s time for them to be watered; running shoes communicate time, speed and distance so that their wearers can compete in real time with people on the other side of the world; medicine containers tell your family members if you forget to take the medicine. All objects can get an active role thanks to their connection to the Internet. The design of objects connected to the Internet is by now across the board in all sectors, and especially in the media.
_
Ubiquitous sensing enabled by Wireless Sensor Network (WSN) technologies cuts across many areas of modern day living. This offers the ability to measure, infer and understand environmental indicators, from delicate ecologies and natural resources to urban environments. The proliferation of these devices in a communicating–actuating network creates the Internet of Things (IoT), wherein sensors and actuators blend seamlessly with the environment around us, and the information is shared across platforms in order to develop a common operating picture (COP). Fuelled by the recent adaptation of a variety of enabling wireless technologies such as RFID tags and embedded sensor and actuator nodes, the IoT has stepped out of its infancy and is the next revolutionary technology in transforming the Internet into a fully integrated Future Internet. As we move from www (static pages web) to web 2 (social networking web) to web 3 (ubiquitous computing web), the need for data-on-demand using sophisticated intuitive queries increases significantly. Fuelled by the prevalence of devices enabled by open wireless technology such as Bluetooth, radio frequency identification (RFID), Wi-Fi, and telephonic data services as well as embedded sensor and actuator nodes, IoT has stepped out of its infancy and is on the verge of transforming the current static Internet into a fully integrated Future Internet. The Internet revolution led to the interconnection between people at an unprecedented scale and pace. The next revolution will be the interconnection between objects to create a smart environment.
_
Ubicomp:
Ubiquitous computing (or “ubicomp”) is a concept in software engineering and computer science where computing is made to appear anytime and everywhere. In contrast to desktop computing, ubiquitous computing can occur using any device, in any location, and in any format. A user interacts with the computer, which can exist in many different forms, including laptop computers, tablets and terminals in everyday objects such as a fridge or a pair of glasses. The underlying technologies to support ubiquitous computing include Internet, advanced middleware, operating system, mobile code, sensors, microprocessors, new I/O and user interfaces, networks, mobile protocols, location and positioning and new materials. This paradigm is also described as pervasive computing, ambient intelligence, ambient media or “everyware”. Each term emphasizes slightly different aspects. When primarily concerning the objects involved, it is also known as physical computing, the Internet of Things, haptic computing, and “things that think”. Mark Weiser defined a smart environment as “the physical world that is richly and invisibly interwoven with sensors, actuators, displays, and computational elements, embedded seamlessly in the everyday objects of our lives, and connected through a continuous network”.
_
Definitions of IoT:
There are several definitions of the Internet of Things (IOT). One that is salient for how the term is currently in use is provided by the U.S. National Intelligence Council: “The “Internet of Things” is the general idea of things, especially everyday objects, that are readable, recognizable, locatable, addressable, and controllable via the Internet – whether via RFID, wireless LAN, wide-area network, or other means.” A key point is that while the most familiar Internet-connected devices are computers such as laptops, servers, smartphones, and tablets, the IOT concept is much broader. In particular, everyday objects that have not previously seemed electronic at all are starting to be online with embedded sensors and microprocessors, communicating with each other and the Internet. This includes items such as food, clothing, household appliances, materials, parts, subassemblies, commodities, luxury items, landmarks, buildings, and roads. It is estimated that 5% of human-constructed objects currently have embedded microprocessors. These tiny microprocessor chips and sensors record and transmit data such as sound waves, temperature, movement, and other variables. Other terms for the Internet of Things include Internet-connected devices, smart connected devices, wireless sensor networks, machines and devices communicating wirelessly, ubiquitous computing, ambient intelligence, and smart matter.
_
The definition of “Internet of Things” has still some fuzziness, and can have different facets depending on the perspective taken. Considering the functionality and identity as central it is reasonable to define the IoT as “Things having identities and virtual personalities operating in smart spaces using intelligent interfaces to connect and communicate within social, environmental, and user contexts”. A different definition, that puts the focus on the seamless integration, could be formulated as “Interconnected objects having an active role in what might be called the Future Internet”. The semantic origin of the expression is composed by two words and concepts: “Internet” and “Thing”, where “Internet” can be defined as worldwide network of interconnected computer networks based on a standard communication protocol, the Internet suite (TCP/IP)”, while “Thing” is “an object not precisely identifiable” Therefore, semantically, “Internet of Things” means “a world-wide network of interconnected objects uniquely addressable, based on standard communication protocols”.
_
The internet of things (IoT) is the network of physical objects—devices, vehicles, buildings and other items—embedded with electronics, software, sensors, and network connectivity that enables these objects to collect and exchange data. They call it “the Internet of Things” — the rapidly growing network of everyday objects equipped with sensors, tiny power supplies, and internet addresses. In 2013 the Global Standards Initiative on Internet of Things (IoT-GSI) defined the IoT as “the infrastructure of the information society.” The IoT allows objects to be sensed and controlled remotely across existing network infrastructure, creating opportunities for more direct integration of the physical world into computer-based systems, and resulting in improved efficiency, accuracy and economic benefit; when IoT is augmented with sensors and actuators, the technology becomes an instance of the more general class of cyber-physical systems (CPS), which also encompasses technologies such as smart grids, smart homes, intelligent transportation and smart cities. Each thing is uniquely identifiable through its embedded computing system but is able to interoperate within the existing Internet infrastructure. Experts estimate that the IoT will consist of almost 50 billion objects by 2020. Typically, IoT is expected to offer advanced connectivity of devices, systems, and services that goes beyond machine-to-machine (M2M) communications and covers a variety of protocols, domains, and applications. The interconnection of these embedded devices (including smart objects), is expected to usher in automation in nearly all fields, while also enabling advanced applications like a smart grid, and expanding to the areas such as smart cities. “Things,” in the IoT sense, can refer to a wide variety of devices such as heart monitoring implants, biochip transponders on farm animals, electric clams in coastal waters, automobiles with built-in sensors, DNA analysis devices for environmental/ food/ pathogen monitoring or field operation devices that assist fire-fighters in search and rescue operations. Legal scholars suggest to look at “Things” as an “inextricable mixture of hardware, software, data and service”. These devices collect useful data with the help of various existing technologies and then autonomously flow the data between other devices. Current market examples include smart thermostat systems and washer/dryers that use Wi-Fi for remote monitoring.
_
The Internet of Things (IoT) is a computing concept that describes a future where every day physical objects will be connected to the Internet and will be able to identify themselves to other devices. The term is closely identified with RFID as the method of communication, although it could also include other sensor technologies, other wireless technologies, QR codes, etc. The IoT is enabled by the latest developments in RFID, smart sensors, communication technologies, and Internet protocols. The basic premise is to have smart sensors collaborate directly without human involvement to deliver a new class of applications. The current revolution in Internet, mobile, and machine-to-machine (M2M) technologies can be seen as the first phase of the IoT. In the coming years, the IoT is expected to bridge diverse technologies to enable new applications by connecting physical objects together in support of intelligent decision making. M2M, the acronym for Machine-to-Machine communication is an emerging area in the field of telecom technologies. Machine to machine (M2M) refers to technologies that allow both wireless and wired systems to communicate with other devices of the same ability. M2M uses a device (such as a sensor or meter) to capture an event, which is relayed through a network (wireless, wired or hybrid) to an application, that translates the captured event into meaningful information. IoT is connected network of embedded devices capable of having M2M communication without human intervention. M2M Communication when combined with logic of cloud services and remote operation becomes “Smart”.
_
Another IoT definition:
Internet of Things (IoT) is an integrated part of Future Internet and could be defined as a dynamic global network infrastructure with self-configuring capabilities based on standard and interoperable communication protocols where physical and virtual ‘things’ have identities, physical attributes, and virtual personalities and use intelligent interfaces, and are seamlessly integrated into the information network. In the IoT, ‘things’ are expected to become active participants in business, information and social processes where they are enabled to interact and communicate among themselves and with the environment by exchanging data and information ‘sensed’ about the environment, while reacting autonomously to the ‘real/physical world’ events and influencing it by running processes that trigger actions and create services with or without direct human intervention. Interfaces in the form of services facilitate interactions with these ‘smart things’ over the Internet, query and change their state and any information associated with them, taking into account security and privacy issues. Internet of Things (IoT) may also be defined as a global network infrastructure where physical and virtual objects with unique ID are discovered and integrated seamlessly (taking into account security and privacy issues) in the associated information network where they are able to offer and receive services which are elements of business processes defined in the environment they become active.
_
The Internet of Things allows people and things to be connected Anytime, Anyplace, with Anything and Anyone, ideally using Any path/network and Any service. The Internet of Things implies a symbiotic interaction among the real/physical and the digital/virtual worlds: physical entities have digital counterparts and virtual representation; things become context aware and they can sense, communicate, interact, exchange, data, information and knowledge.
_
Different kinds of IoT:
While IoT can be a multiple-layer system, it can roughly be broken down into three levels. The first is a rudimentary form, where cameras are used to monitor places or people. This application can be seen in schools, universities, malls. Further down, it goes into things which you can control without having additional integrated systems — drones, sensors for recording temperature, a counter in an assembly line. These are used in manufacturing plants. Then comes the integrated systems. These have a larger impact, for example, internet-controlled plants or sensors and actuators that are used in large-scale plants with complex systems.
_
IoT taxonomy:
_
In general, the “Internet of Things” is the networking of physical objects connecting through the Internet. The Internet of Things is not a new concept, as devices have been communicating with each other for a number of years. The difference now is that:
•electronic devices and everyday objects, especially consumer products, are increasingly being built to facilitate interoperable communication through sensors and Internet connectivity;
•sensors are becoming more sophisticated;
•objects and devices have the ability to seamlessly connect and communicate a wide range of online and offline information (including location, biometrics, purchases, and online browsing history);
•Internet of Things computing devices are becoming affordable and accessible for individuals and organizations of all sizes, including small- and medium-sized enterprises; and
•cloud computing and Big Data analytics are available for all organizations to store information, share it, and make inferences about their clientele.
_
As identified by Atzori et al., Internet of Things can be realized in three paradigms—internet-oriented (middleware), things oriented (sensors) and semantic-oriented (knowledge). Although this type of delineation is required due to the interdisciplinary nature of the subject, the usefulness of IoT can be unleashed only in an application domain where the three paradigms intersect.
_
_
Conceptual view of IoT:
_
According to the McKinsey report “Disruptive technologies: Advances that will transform life, business, and the global economy”, the Internet of things (IoT) is one of the top three technological advancements of the next decade (together with the mobile internet and the automation of knowledge work). The report goes on to say that “The Internet of Things is such a sweeping concept that it is a challenge to even imagine all the possible ways in which it will affect business, economies, and society.” According to McKinsey, IoT means “Sensors and actuators embedded in physical objects are linked through wired and wireless networks, often using the same Internet Protocol (IP) that connects the Internet.” The idea is that not only your computer and your smartphone can talk to each other, but also all the things around you. From connected homes and cities to connected cars and machines to devices that track an individual’s behavior and use the data collected for new kind of services.
________
________
History and evolution of IoT:
_
History of IoT:
The term Internet of Things is 17 years old. But the actual idea of connected devices had been around longer, at least since the 70s. Back then, the idea was often called “embedded internet” or “pervasive computing”. But the actual term “Internet of Things” was coined by Kevin Ashton in 1999 during his work at Procter&Gamble. Ashton who was working in supply chain optimization, wanted to attract senior management’s attention to a new exciting technology called RFID. Because the internet was the hottest new trend in 1999 and because it somehow made sense, he called his presentation “Internet of Things”. Even though Kevin grabbed the interest of some P&G executives, the term Internet of Things did not get widespread attention for the next 10 years. It is a new term, but not a new operation. It was known as pervasive computing, ubicomp, and ambient intelligence. These iterations could not make their demos and prototypes real as until the 90s database storage was too expensive. It is the Cloud, operational from 2000s, that enabled IoT. The concept of IoT started to gain some popularity in the summer of 2010. Information leaked that Google’s StreetView service had not only made 360 degree pictures but had also stored tons of data of people’s Wi-Fi networks. People were debating whether this was the start of a new Google strategy to not only index the internet but also index the physical world. The same year, the Chinese government announced it would make the Internet of Things a strategic priority in their Five-Year-Plan. In 2011, Gartner, the market research company that invented the famous “hype-cycle for emerging technologies” included a new emerging phenomenon on their list: “The Internet of Things”. Internet of Things has been identified as one of the emerging technologies in IT as noted in Gartner’s IT Hype Cycle as seen in the figure below. A Hype Cycle is a way to represent the emergence, adoption, maturity, and impact on applications of specific technologies. It has been forecasted that IoT will take 5–10 years for market adoption.
_
The next year the theme of Europe’s biggest Internet conference LeWeb was the “Internet of Things”. At the same time popular tech-focused magazines like Forbes, Fast Company, and Wired starting using IoT as their vocabulary to describe the phenomenon. In October of 2013, IDC published a report stating that the Internet of Things would be a $8.9 trillion market in 2020. The term Internet of Things reached mass market awareness when in January 2014 Google announced to buy Nest for $3.2bn. At the same time the Consumer Electronics Show (CES) in Las Vegas was held under the theme of IoT.
____
The evolution of IoT goes hand in hand with evolution of communication system.
The figure below shows evolution of communication system:
_
_
The figure below shows evolution of IoT from internet:
The first generation of Internet was about people getting on to the Internet to access information. Second Generation of Internet was about people connecting with other people. Third Generation of Internet would now be about everyday devices connecting with each other to provide amazing services.
_
The Evolution of the Internet of Things:
The Internet of Things is a gradual revolution that will lead to all the objects surrounding us being connected to the Internet in some way. On the other hand it’ll happen that all content starting with music going right up to film will migrate towards digital media. For this reason, the physical devices holding content will have less and less significance. Music will be listened to in MP3 format, books will be listened to as audio-books or read on devices for e-books, and newspapers will be read from PCs or tablets. But even the objects that access content are multiplying. For example, PlingPlong is a cushion that reads books that are brought close to it. Nabaztag, is a ‘rabbit’ connected to the Internet and it reads newspapers, emails, weather forecasts, messages and even audio- books downloaded from the Internet. The rabbit has recently also had an evolution with Tux Droid that in the ‘penguin’ version makes it possible to be programmed directly with open software. Digital content will be ever more accessible with the evolution of Internet readers that make it possible to exploit content in all occasions of use for which today we use physical data storage devices. For example Chumby, a viewer connected via wifi, and the iPad let you quickly get access to online content without needing to turn on your PC. The evolution that is partially happening right now is in the transformation to digital of the information needed to reproduce objects with 3D printers, or ‘making machines’ that make it possible to reproduce physical objects in your own home. As regards software services, we are seeing the evolution of platforms for accessing content directly online. For example, TV series in the United States can be viewed directly on the Hulu site that has free online broadcasting of TV serials with breaks for advertising.
__
The figure below shows that as technology advances, physical world merged with digital virtual world:
_________
_________
Understand nomenclature of IoT and its comparable:
While the Internet of Things is by far the most popular term to describe the phenomenon of a connected world, there are similar concepts that deserve some attention. Most of these concepts are similar in meaning but they all have slightly different definitions. Let us understand certain terms from internet to internet of things to web of things to machine-to-machine to cyber-physical-system to industrial IoT to internet of everything.
_
From the Internet of Computers to the Internet of Things:
Before we can begin to see the importance of IoT, it is first necessary to understand the differences between the Internet and the World Wide Web (or web)—terms that are often used interchangeably. The Internet is the physical layer or network made up of switches, routers, and other equipment. Its primary function is to transport information from one point to another quickly, reliably, and securely. The web, on the other hand, is an application layer that operates on top of the Internet. Its primary role is to provide an interface that makes the information flowing across the Internet usable.
_
Evolution of the Web vs. the Internet:
The web has gone through several distinct evolutionary stages from the research phase, when the web was called the Advanced Research Projects Agency Network (ARPANET) to where we are now, the “social” or “experience” web, where companies like Facebook and Twitter have become immensely popular and profitable by allowing people to communicate, connect, and share information (text, photos, and video) about themselves with friends, family, and colleagues. By comparison, the Internet has been on a steady path of development and improvement, but arguably hasn’t changed much. It essentially does the same thing that it was designed to do during the ARPANET era. For example, in the early days, there were several communication protocols, including AppleTalk, Token Ring, and IP. Today, the Internet is largely standardized on IP. In this context, IoT becomes immensely important because it is the first real evolution of the Internet—a leap that will lead to revolutionary applications that have the potential to dramatically improve the way people live, learn, work, and entertain themselves. Already, IoT has made the Internet sensory (temperature, pressure, vibration, light, moisture, stress), allowing us to become more proactive and less reactive. In addition, the Internet is expanding into places that until now have been unreachable. Patients are ingesting Internet devices into their own bodies to help doctors diagnose and determine the causes of certain diseases. Extremely small sensors can be placed on plants, animals, and geologic features, and connected to the Internet. At the other end of the spectrum, the Internet is going into space through Cisco’s Internet Routing in Space (IRIS) program.
_
Web 2 to Web 3:
Web 3 is the term used to describe the evolution of the Web as an extension of Web 2.0. This definition of Web 3.0 is the popular view held by Tim O’Reilly. In contrast, Nova Spivack defines Web 3.0 as connective intelligence; connecting data, concepts, applications and ultimately people. While some call the Semantic Web ‘Web 3.0’, Spivack’s opinion is that the Semantic Web is just one of several converging technologies and trends that will define Web 3.0 The Semantic Web is an extension of the Web through standards by the World Wide Web Consortium (W3C). The standards promote common data formats and exchange protocols on the Web. We can define Web 3.0 as the conjunction of the Internet of Things with the Semantic Web. Historically, the Internet of Things –IoT- is a concept wherein objects are uniquely identified. These IDs are written on barcodes, RFID tags, NFC… then tagged on the physical objects. During the physical object lifecycle, event readings are made using sensors (RFID & NFC readers, cameras, scanners, GPS/GSM/Wi-Fi, manual reading, etc.). Those events are then collected and recorded in databases, and further aggregated, consolidated or merged with other information already handled in computer systems for traceability, logistics, management or sales issues. As long as the processes are under control and well maintained, existing solutions work pretty well and provide satisfactory results. But, today, those approaches only fit the requirements of closed or semi-open loops or value chain management. Each implementation is segregated and cannot easily interoperate with others. Thus, maybe we should speak of a set of “Intranet of Things”, since using the term Internet is improper. However the primary ambition of the IoT was to publish these event related information on the Internet, in order to allow all actors involved with object manipulation or use to access them. Various techniques and standards have appeared with the aim of publishing and retrieving this information, some of which are inherited from the existing Internet static resolution systems: ONS – Object Naming system – derived from DNS by the MIT and adopted by EPCGlobal. On the existing Web, the clever actors are human beings and their social networks: this is the underlying concept of Web 2.0 as a distinction from Web 1.0. Analogically, making objects true actors on the Web 3.0 is no more than giving them enough autonomy and intelligence, suited to the roles we want them to play. Especially, we must give them the ability to move from one information ecosystem to another and accordingly pass from one information system to another seamlessly.
_
What is the IoT and how does it differ from the Internet?
The basic idea of the IoT is that virtually every physical thing in this world can also become a computer that is connected to the Internet. To be more accurate, things do not turn into computers, but they can feature tiny computers. When they do so, they are often called smart things, because they can act smarter than things that have not been tagged. Of course, one could question whether things would really have to feature computers to become smart. For instance, a consumer good could be considered to be already smart, when tagged with a visual code such as a bar code or equipped with a time-temperature indicator that, say, a mobile phone can use to derive and communicate the product’s state of quality, dynamic carbon footprint, effect on diabetics, or origin. Certainly the boundary between smart things, which autonomously can derive and transform to different states and communicate these states seamlessly with their surroundings, and not so smart things, which only have a single status and are not very active in communicating it, is blurring.
_
__
The following paragraphs describe the most important differences between the Internet and the IoT:
1. Invisible versus flashy hardware. First of all, the hardware in the IoT looks considerably different and serves a different purpose. Whereas the nerve ends of the Internet are full-blown computers, from high capacity work stations to mobile phones, that require regular access to the power grid, the nerve ends in the IoT are very small, in many cases even invisible, low-end and low energy consumption computers. They typically feature only a small fraction of the functions of their bigger Internet-siblings, often including sensing, storing and communicating a limited amount of information. In most cases, they cannot interact directly with human beings.
2. Trillions versus billions of network nodes. Today, about five billion devices such as mobile phones (3.3 billion), personal computers (1.2 billion), MP3 players (220k), digital cameras (120k), web cams (100k), PDAs (85k), and data servers (27k) serve a population of about 6.7 billion people, of whom only 1.5 billion are currently using the Internet. These numbers seem huge, but in comparison to the number of things we constantly create on this earth, they are not. One can grasp an idea of the order of magnitude by estimating the number of consumer products that are produced every year. Sanjay Sarma estimates 555 billion units in an Auto-ID Center-specific selection of supply chains (Sarma, 2001). These estimates already suggest that there will be so many computer enabled things around us that, firstly, people will not be willing and able to directly communicate with them, and secondly, a new network infrastructure, the IoT, might be required.
3. Last mile bottleneck versus highway. The last mile in a communications infrastructure refers to the communication link between the nerve endings, or the leaves in a local tree, and its next tier or layer. Driven by user demands, e.g., streaming videos, and technology progress, the speed of the last mile in the Internet has been increasing tremendously over recent years. Today, an average household in many countries can expect to have cable based Internet access with a bandwidth of at least 1 MBit/s. With the implementation of emerging technologies such as fiber optics to the home, the bandwidth will soon become as high as 50 – 100 MBit/s. By contrast, the speed of the last mile towards an average low energy consuming RFID tag is only about 100 kBit/s.
4. Classical versus global identification and addressing. The low end hardware of the IoT is responsible for another difference: the identification and addressing of the nerve endings. In most cases, the Internet-based identification and addressing schemes require too much capacity to become part of low-end smart things. Therefore, academic and industrial communities are searching for alternative technologies and standards (e.g. EPC, ucode, IPv6, 6LoWPAN, Handle System, or Internet0) to number and address the smartening physical world. So far, most identifiers for smart things and technologies bridge the last mile based on local, technology vendor-specific closed-loop schemes. However, if the IoT would like to follow the successful path of the classical Internet, its architecture would have to make sure that any tagged object could in principle be accessed by any computer. For that, a global standard protocol, identification and addressing scheme for bridging the last mile from the Internet to the smart things would be required.
5. Machine-centric versus user-centric. The characteristics of the Internet and the IoT define the range of services they support. The vast majority of Internet-based services are targeted towards human beings as users, e.g., the World Wide Web (WWW), email, file sharing, video, online chat, file transfer, telephony, shopping, or rating. The attributes of the IoT almost completely exclude humans from direct intervention. That is why Marc Weiser called for a paradigm shift towards human-out-of-the-loop-computing when he introduced the vision of ubiquitous computing. In most IoT-applications, the smart things communicate amongst each other and with computers in the Internet in a machine-to-machine way (Mattern, 2004). When users need to be involved, e.g., for decision making, they currently contribute via personal computers and mobile phones.
6. Focus on sensing versus on communication. The economic success story of the Internet started with the WWW, which allowed companies and individuals virtually for the first time to reach out to a global customer base at ridiculously low cost. Looking closely at the WWW’s communication abilities (distribution and presentation of content), it seems no big surprise that the first economic success stories were made in the areas of advertising (Google) and shopping (e.g., eBay or Amazon). However, looking backwards has always been far simpler than forecasting. The second boost of the Internet was largely driven by adding the ability to deal with user generated content, i.e., data that is not only consumed by users but also provided by users. The success stories of these Web 2.0-based services include Facebook, YouTube, Twitter, and Wikipedia. The IoT adds another data dimension. It allows the physical world, things and places, to generate data automatically. In fact, the IoT is all about sensing the physical world. It provides the infrastructure that for the first time enables us to measure the world. It is a cost-efficient means of growing a very finely granulated nerve system with trillions of new nerve endings. Linked together, they can provide humans with a measurement tool that opens the door to many new findings, applications, benefits, and risks.
____
In the diagram below, we get a clear differentiation of IP Suite and IP Smart Object (IoT) suite.
____
Web of things:
For the IoT to become a reality, we will need a single universal application layer protocol (think “language”) for devices and applications to talk to each other, regardless of how they are physically connected. Instead of creating yet another protocol from scratch (as many IoT projects have been – and keep – doing), why not simply reuse something that is already widely used for building scalable and interactive applications, such as the Web itself? This is what the Web of Things is all about: reuse and leverage readily available and widely popular Web protocols, standards and blueprints to make data and services offered by objects more accessible to a larger pool of (Web) developers. The Web of Things (WoT) is a computing concept that describes a future where everyday objects are fully integrated with the Web. The prerequisite for WoT is for the “things” to have embedded computer systems that enable communication with the Web. Such smart devices would then be able to communicate with each other using existing Web standards. Similarly to what the Web (Application Layer) is to the Internet (Network Layer), the Web of Things provides an Application Layer that simplifies the creation of Internet of Things applications. Rather than re-inventing completely new standards, the Web of Things reuses existing and well-known Web standards used in the programmable Web (e.g., REST, HTTP, JSON), semantic Web (e.g., JSON-LD, Microdata, etc.), the real-time Web (e.g., Websockets) and the social Web (e.g., oauth or social networks). The data that objects transmit to the Web usually takes the form of a structured XML document or a JSON object that is machine-readable (using JavaScript). These formats can be understood not only by machines but also by people, provided meaningful markup elements and variable names are used. They can also be supplemented with semantic information using microformats. In this way, smart objects can not only communicate on the Web but also create a user-friendly representation of themselves, making it possible to interact with them via normal Web browsers and explore the world of smart things with its many relationships (via links to other related things). Dynamically generated real-world data on smart objects can be displayed on such “representative” Web pages and can then be processed using the extensive functionality of widely available Web 2.0 tools. For example things could, via their digital representations, be indexed like Web pages, users could “Google” their properties, or they could be passed on as references. The physical objects themselves could become active and keep blogs or update each other using social networking tools like Twitter. Although this may sound like an odd humanizing of inanimate objects, it is of practical significance. The Web and its services are being used as ubiquitous middleware – facilitating the implementation of new functionality and innovative applications for smart things. So if, for example, your washing machine is in the basement and you want to monitor its progress, you could subscribe to its atom feed on a Web client and get information on major state changes, or follow its tweets on Twitter.
_
_
After reading through the differences between internet and ioT, one can argue that the IoT is not on the same level as the Internet, that it is in fact “only” an application of the Internet, in very much the same way as many existing Internet-enabled services. Following that path, the term IoT would be an exaggeration, and should be renamed something like Web of Things. On the other hand, one can easily argue that a Web of Things would require low level building blocks, e.g., for addressing the smart things, bridging the last mile and linking it with the Internet, that are peers with some Internet building blocks. As a consequence, the IoT may rightly be conceptualized as an extension of the Internet to reach out to the physical world of things and places that only can feature low-end computers. In fact, often enough when we use the term IoT, we do not differentiate between the infrastructure and application levels. We use IoT as a bracket-term to refer to one or both at the same time. On the infrastructure level, the IoT can be viewed as an extension to the Internet as we know it today. The IoT expands the technical Internet building blocks such as DNS, TCP, and IP with identification and addressing schemes, last mile communication technology, and an Internet gateway that matches the IoT requirements, foremost among them low energy consumption, low cost, and mobility. On the application level, the Web of Things provides an application Layer that simplifies the creation of Internet of Things applications.
____
Machine-to-machine (M2M):
M2M is defined as the technologies that allow machines, typically (small) computing sensors that perform specific tasks (intelligence) to communicate or relay information as needed typically over simple protocols but more recently over Internet protocols (IP) over wireless or wireline or even SMS. But the Internet of Things is so much more than M2M. IoT it is about interacting with the objects around us; even static non-intelligent objects and augmenting such interactions with context as provided by geo-location, time and so on. Even non-intelligent/non-connected devices can be brought into the IoT via the handset or smartphone serving as a gateway to the Internet. It is about interacting for example with the soda can via barcodes or with the movie poster via NFC, or with an advert on the newspaper via a shortcode, or with the book that you are reading, again via barcodes or even NFC. In the case of M2M, it is about communicating with machines such as the energy-meters or sensors or even your refrigerator via IP over wireless or wireline. So M2M is not the Internet of Things, but M2M is a subset of the Internet of Things. M2M is like a line connecting 2 points, and IoT is like a network, a system composed of lots of M2M and triggering lots of interactions/activities.
Giving a simple definition to M2M is transferring data from one machine to another one. It’s been used everywhere in our daily life. For example, entrance security. Just like using your employee card to unlock a door. When the security detector receives the ID from the employee card and then unlocks the door once the ID is approved. This is M2M. In this case, what IoT can offer? As mentioned, IoT is a network, is a system composed of lots of M2M and algorithms. When the system knows you are the person entering the office, it can turn on the light and the air conditioner of your partition, even it can adjust the most comfortable light level and temperature that you like the most from time to time after learning your behavior for a period of time. The system can get all the data from all the sensors and machines to know, for example, who and when enters the office, how much electricity you have consumed, what the environment makes you feel most comfortable, and other applications. IoT will make the facilities and things smarter and make people’s life more convenient. Not only machine to machine, but also human to machine, machine to human, and so on.
_
_
The word M2M was mainly used by the cellular operators worldwide. It is the data communication by using the cellular network. The cellular operators already started to cover business fields outside the cellular networks. Home appliance, home security and Ambient Assisted Living are examples for such applications. The cellular operators already sold one of the necessary equipment to us. We call this smart phone today. The smart phone is nothing else than one more machine in the concept. It is a machine in our hands with display. And the PC of the above mentioned dispatcher is a machine with display as well. And even if there is one machine without display that is communicating to another machine without display then there was always a gateway to a display in parallel. Somebody has to set up the parameter or somebody has to follow the processing data on a screen. M2M of today is just a part of the IoT. The IoT could use a cellular network, but the major part will be on other new communication networks. A lot of the networks (P2P, star, meshed) will be private area networks (PAN) on for example Wi-Fi, Bluetooth Low Energy, 6LoWPAN and a lot more. 6LoWPAN is the most interesting bearer because it covers the most bearers for now (wired power line communication, wireless on Sub GHz and wireless on 2400 MHz). 6LoWPAN is an acronym of IPv6 over Low power Wireless Personal Area Networks. IoT devices with IP connectivity are a subset of all IoT devices. Lots of IoT technologies, in fact the vast majority of “endpoint” devices today — barcode/QR codes, NFC, RFID tags — are not capable of supporting IP on the endpoint device and a gateway is required. Moreover, many IoT applications have no inherent need for IP connectivity — a building automation app (a “closed” loop) may not require IP, but it may be undesirable for security purposes, etc.
____
IoT vs. M2M vs. CPS not clear cut distinction, these terms are often used interchangeably;
M2M – Machine-to-Machine Telco world origins, tied to the network implications of connecting machines rather than people, explosion of connections with limited bit-rate, M2M is the glue of the IoT
CPS – Cyber Physical Systems merging real and virtual (cyber) worlds, focusing on systems that based on duly sampled representation of the physical world can intervene through digitized actuators to change behaviours in the physical world; CPS is the science bricks behind IoT
IoT hailed as a broader concept, where the focus is more on wide applications.
_____
Industrial Internet of Things:
The Industrial Internet of Things (IIoT) is the use of Internet of Things (IoT) technologies in manufacturing. Also known as the Industrial Internet, IIoT incorporates machine learning and big data technology, harnessing the sensor data, machine-to-machine (M2M) communication and automation technologies that have existed in industrial settings for years. The driving philosophy behind the IIoT is that smart machines are better than humans at accurately, consistently capturing and communicating data. This data can enable companies to pick up on inefficiencies and problems sooner, saving time and money and supporting business intelligence efforts. In manufacturing specifically, IIoT holds great potential for quality control, sustainable and green practices, supply chain traceability and overall supply chain efficiency. The term industrial internet is strongly pushed by GE. It goes beyond M2M since it not only focuses on connections between machines but also includes human interfaces.
_
The Industrial Internet of Things (Industrial IoT) is made up of a multitude of devices connected by communications software. The resulting systems, and even the individual devices that comprise it, can monitor, collect, exchange, analyze, and instantly act on information to intelligently change their behavior or their environment — all without human intervention. An example of one such Industrial IoT system would be a wind farm as seen in the figure below.
_
There are two perspectives on how the Industrial IoT differs from the IoT.
The first perspective is that there are two distinctly separate areas of interest. The Industrial IoT connects critical machines and sensors in high-stakes industries such as aerospace and defense, healthcare and energy. These are systems in which failure often results in life-threatening or other emergency situations. On the other hand, IoT systems tend to be consumer-level devices such as wearable fitness tools, smart home thermometers and automatic pet feeders. You may call them ‘consumer IoT’ as distinct from industrial IoT. They are important and convenient, but breakdowns do not immediately create emergency situations. The second perspective sees the Industrial IoT as the infrastructure that must be built before IoT applications can be developed. In other words, the IoT, to some extent, depends on the Industrial IoT. As the Industrial IoT becomes better defined and developed, more impactful IoT applications can and will be created.
_
| Internet of Things | Industrial Internet of Things |
| Everyday consumer-level devices connected to one another and made smarter and slightly self-aware. | Equipment and systems in industries and businesses where failures can be disastrous. |
| Examples: consumer cell phone, smart thermostat | Examples: individual health monitors and alert systems in hospitals |
__
How big is the economic power of the Industrial Internet? Consider one analysis that places a conservative estimate of worldwide spending at $500 billion by 2020, and which then points to more optimistic forecasts ranging as high as $15 trillion of global GDP by 2030. The Industrial Internet—the combination of Big Data analytics with the Internet of Things is producing huge opportunities for companies in all industries, but especially in areas such as Aviation, Oil and Gas, Transportation, Power Generation and Distribution, Manufacturing, Healthcare and Mining. Why? Because, as one recent analysis has it, “Not all Big Data is created equal.” According to the authors, “data created by industrial equipment such as wind turbines, jet engines and MRI machines … holds more potential business value on a size-adjusted basis than other types of Big Data associated with the social Web, consumer Internet and other sources.”
_
Industry 4.0
The term Industry 4.0 that is strongly pushed by the German government is as limited as the industrial internet in reach as it only focuses on industrial environments. However, it has the largest scope of all the concepts. Industry 4.0 describes a set of concepts to drive the next industrial revolution. It includes all kinds of connectivity concepts but also goes further to include real changes to the physical world around us such as 3D-printing technologies, new augmented reality hardware, robotics, and advanced materials.
_____
Internet of Everything (IoE):
_
According to Cisco, IoE brings together people (humans), process (manages the way people, data, and things work together), data (rich information), and things (inanimate objects and devices) to make networked connections more relevant and valuable than ever before—turning information into actions that create new capabilities, richer experiences, and unprecedented economic opportunity for businesses, individuals, and countries. To better understand this definition, it is helpful to take a quick look at the evolution of the Internet. In the early 1990s, devices connected to the Internet were essentially “fixed.” For example, you went to your desk to use your PC, dumb terminal, or other device. At its peak, this first wave reached about 200 million devices by the late 1990s. Around the year 2000, devices started to come with you. As the number of both fixed and mobile devices (including machines) ballooned, the number of things connected to the Internet increased, reaching about 10 billion this year. This second wave of Internet growth ushered in the “Age of the Device.” Cisco believes the third wave of Internet growth has already begun. As the things connected to the Internet are joined by people and more intelligent data (as Cisco’s definition describes), IoE could potentially connect 50 billion people, data, and things by 2020. So, what is the difference between IoT and IoE? As the evolution of the Internet suggests, IoE (four pillars: people, process, data, and things) builds on top of IoT (one pillar: things). In addition, IoE further advances the power of the Internet to improve business and industry outcomes, and ultimately make people’s lives better by adding to the progress of IoT.
_
_
The components of IoE — people, process, data, and things — play specific roles, and work together, to enable our future cities and communities.
• People
In IoE, people will be able to connect to the Internet in innumerable ways. Today, most people connect to the Internet through their use of devices (such as PCs, tablets, TVs, and smartphones) and social networks (such as Facebook, Twitter, LinkedIn, and Pinterest). As the Internet evolves toward IoE, we will be connected in more relevant and valuable ways. For example, in the future, people will be able to swallow a pill that senses and reports the health of their digestive tract to a doctor over a secure Internet connection. In addition, sensors placed on the skin or sewn into clothing will provide information about a person’s vital signs. According to Gartner, people themselves will become nodes on the Internet, with both static information and a constantly emitting activity system.
•Data
With IoT, devices typically gather data and stream it over the Internet to a central source, where it is analyzed and processed. As the capabilities of things connected to the Internet continue to advance, they will become more intelligent by combining data into more useful information. Rather than just reporting raw data, connected things will soon send higher-level information back to machines, computers, and people for further evaluation and decision making. This transformation from data to information in IoE is important because it will allow us to make faster, more intelligent decisions, as well as control our environment more effectively.
•Things
This group is made up of physical items such as sensors, consumer devices, and enterprise assets that are connected to both the Internet and each other. In IoE, these things will sense more data, become context-aware, and provide more experiential information to help people and machines make more relevant and valuable decisions. Examples of “things” in IoE include smart sensors built into structures like bridges, and disposable sensors that will be placed on everyday items such as milk cartons.
•Process
Process plays an important role in how each of these entities — people, data, and things — works with the others to deliver value in the connected world of IoE. With the correct process, connections become relevant and add value because the right information is delivered to the right person at the right time in the most appropriate way.
_____
Concept disambiguation: IoT vs. IoE vs. M2M vs. others:
IoT has yet a wider reach as it also includes connections beyond the industrial context such as wearable devices on people. In the above graph, the internet is a fairly small box. In its core it connects only people. Let us call it common internet.
_________
________
My view:
M2M is a subset of industrial IoT; industrial IoT is a subset of IoT; and IoT is a subset of IoE. Additionally, WoT is a subset of IoT and common internet used by us every-day is a subset of IoE.
________
________
IoT concepts and basics:
The Internet of Things (IoT) is about interconnecting embedded systems. It brings together two evolving technologies: wireless connectivity and smart sensors. Combined with recent advances in low power microcontrollers, these new “things” are being connected to the internet easily and inexpensively, ushering in a second industrial revolution. These connected embedded systems are small microcontroller-based computers that do not require a human interface. Instead of interacting with a human these systems use sensors or other advanced detection mechanisms. These sensors collect data, data that has value and that is part of a larger system. This data is then networked as part of a larger system. While the term “Internet of Things” implies that these sensors are networked via the world wide internet using WiFi or Ethernet, the networking can also be performed using protocol such as ZigBee or Bluetooth that does not have an IP address. The networking protocol is selected based on the distribution of nodes and the amount of data to be collected. This data is sent over the network to the main hub or computer. This main computer collects and analyzes the data, storing it in memory and even making system decisions based on the results of the analysis.
_
Embedded systems:
An embedded system is a computer that is part of a different kind of machine. Examples include computers in cars, traffic lights, digital televisions, ATMs, airplane controls, point of sale (POS) terminals, digital cameras, GPS navigation systems, elevators, digital media receivers and smart meters, among many other possibilities. An embedded system is some combination of computer hardware and software, either fixed in capability or programmable, that is specifically designed for a particular function. Industrial machines, automobiles, medical equipment, cameras, household appliances, airplanes, vending machines and toys (as well as the more obvious cellular phone and PDA) are among the myriad possible hosts of an embedded system. The Internet of Things (IoT) is the interconnection of uniquely identifiable embedded computing devices within the existing Internet infrastructure. So Internet of Things or IoT basically is connecting Embedded System to internet. So before we understand IoT, let us understand Embedded System a little. A general-purpose definition of embedded systems is that they are devices used to control, monitor or assist the operation of equipment, machinery or plant. “Embedded” reflects the fact that they are an integral part of the system. In many cases, their “embeddedness” may be such that their presence is far from obvious to the casual observer. Block diagram of a typical embedded system is shown in fig.
Today, embedded systems are found in cell phones, digital cameras, camcorders, portable video games, calculators, and personal digital assistants, microwave ovens, answering machines, home security systems, washing machines, lighting systems, fax machines, copiers, printers, and scanners, cash registers, alarm systems, automated teller machines, transmission control, cruise control, fuel injection, anti-lock brakes, active suspension and many other devices/ gadgets.
_
An embedded system is a computer system with a dedicated function within a larger mechanical or electrical system, often with real-time computing constraints. It is embedded as part of a complete device often including hardware and mechanical parts. Embedded systems control many devices in common use today. Ninety-eight percent of all microprocessors are manufactured as components of embedded systems. Modern embedded systems are often based on microcontrollers (i.e. CPUs with integrated memory or peripheral interfaces), but ordinary microprocessors (using external chips for memory and peripheral interface circuits) are also common, especially in more-complex systems. In either case, the processor(s) used may be types ranging from general purpose to those specialised in certain class of computations, or even custom designed for the application at hand. Since the embedded system is dedicated to specific tasks, design engineers can optimize it to reduce the size and cost of the product and increase the reliability and performance. Embedded systems range from portable devices such as digital watches and MP3 players, to large stationary installations like traffic lights, factory controllers, and largely complex systems like hybrid vehicles, MRI, and avionics. Complexity varies from low, with a single microcontroller chip, to very high with multiple units, peripherals and networks mounted inside a large chassis or enclosure.
_
A microcontroller (or MCU, short for microcontroller unit) is a small computer (SoC) on a single integrated circuit containing a processor core, memory, and programmable input/output peripherals. Microcontrollers are designed for embedded applications, in contrast to the microprocessors used in personal computers or other general purpose applications consisting of various discrete chips. Microcontrollers are used in automatically controlled products and devices, such as automobile engine control systems, implantable medical devices, remote controls, office machines, appliances, power tools, toys and other embedded systems. By reducing the size and cost compared to a design that uses a separate microprocessor, memory, and input/output devices, microcontrollers make it economical to digitally control even more devices and processes. Control networks move small packets of data to a large set of nodes, so as to integrate and automate everything from home appliances to entire factories. This is due to the use of embedded microprocessors. These microprocessors are usually smaller, use a surface mount form factor and consume less power.
__
Key concepts that serve as a foundation for exploring the opportunities and challenges of IoT include:
• IoT Definitions: The term Internet of Things generally refers to scenarios where network connectivity and computing capability extends to objects, sensors and everyday items not normally considered computers, allowing these devices to generate, exchange and consume data with minimal human intervention. There is, however, no single, universal definition.
• Enabling Technologies: The concept of combining computers, sensors, and networks to monitor and control devices has existed for decades. The recent confluence of several technology market trends, however, is bringing the Internet of Things closer to widespread reality. These include Ubiquitous Connectivity, Widespread Adoption of IP-based Networking, Computing Economics, Miniaturization, Advances in Data Analytics, and the Rise of Cloud Computing.
• Connectivity Models: IoT implementations use different technical communications models, each with its own characteristics. Four common communications models described by the Internet Architecture Board include: Device-to-Device, Device-to-Cloud, Device-to-Gateway, and Back-End Data-Sharing. These models highlight the flexibility in the ways that IoT devices can connect and provide value to the user.
_
Although the term was IoT was coined in 1999, but it is now in the process of becoming a reality in recent years due to several key factors.
1. Emergence and wide acceptance of IPv6 leading to very huge addresses to assign to each and every “thing”
2. It is easier and cheaper to produce hardware , than what it was ten years ago . For example, open sourced microControllers like arduino , beaglebone black , raspberry Pi etc. are readily available and are very cheap .
3. The world of wireless connectivity has dramatically evolved over the last few years (Wi-Fi , Bluetooth , Zigbee , Z-Wave, 4G etc. ) .
4. IoT is able to leverage on an entire infrastructure that has emerged in related areas. Cloud computing enables the creation of “dumb” (simpler, cheaper) devices, with all the intelligence processed in the cloud. Big data tools often open sourced enable the processing of massive amounts of data captured by the devices and will play a crucial role in the space
____
What are ‘things’?
In the context of “Internet of Things” a “thing” could be defined as a real/physical or digital/virtual entity that exists, and move in space and time, and is capable of being identified. Things are commonly identified either by assigned identification numbers, names and/or location addresses. Things would include physical objects, products and devices.
____
Intelligent (smart) objects/products and the internet of things (IoT):
With the advent of the information and related emerging technologies, such as RFID, small size sensors and sensor networks or, more generally, product embedded information devices (PEID), a new generation of products called smart or intelligent products is available in the market. We find the mention of “Smart Objects” and “Smart Devices” quite often in general definition and description of IoT alongside network connectivity of embedded system. But what exactly are smart object? Any object which not only has a state, which has certain data associated with a state but an object which can also determine nature of connectivity, duration of connectivity and connectivity protocol are called smart objects. A smart object is an object that enhances the interaction with not only people but also with other smart objects. It can not only refer to interaction with physical world objects but also to interaction with virtual (computing environment) objects. A smart physical object may be created either as an artifact or manufactured product or by embedding electronic tags such as RFID tags or sensors into non-smart physical objects. Radio Frequency Identification (RFID), Bluetooth Low Energy (BLE), and Near Field Communication (NFC) make it possible to use our phone as readers. We can extract information from certain objects just by tapping it or bringing our device close to it. RFID tags do not have any embedded system nor does a NFC tag has. But data can still be brought to internet by reading through a reader. These are called smart objects. Non-processor entity whose data can be acquired and migrated over internet falls under these category. Short-range low-energy sensor technology has given rise to smart objects. So say a T-Shirt comes with a smart tag. We can tap our phone over it and we get information about the quality of material, it’s size, other color variants, dye information and so on which helps us making our purchase decision. As the information is acquired, it can be passed as a search query to obtain similar results where we can compare the price-quality for similar tags.
_
A Smart Thing is a physical object that is digitally augmented with one or more of the following:
1. Sensors (temperature, light, motion, etc.),
2. Actuators (displays, sound, motors, etc.),
3. Computation (can run programs and logic),
4. Communication interfaces (wired or wireless).
Things extend the world we live in by enabling a whole new range of applications. Being able to put a bunch of powerful, tiny, and cheap computers everywhere around us makes it possible to monitor and interact with the physical world with a much finer spatial and temporal resolution than ever before.
________
The Structure of Internet of Things:
The Internet of Things can be viewed as a gigantic network consisting of networks of devices and computers connected through a series of intermediate technologies where numerous technologies such as RFIDs, barcodes, wired and wireless connections may act as enablers of this connectivity. By International Telecommunications Union (ITU), the perception of IoT was structured as four dimensions of things:
1) Tagging Things (RFID, NFC, QR Codes, Digital Watermarking, etc.)
2) Sensing Things (Sensors act as primary devices to collect data from the environment. Recent advances in technologies make them consume less power with low cost and high efficiency)
3) Shrinking Things (Making products smaller, yet smarter. Miniaturization and nanotechnology has provoked the ability of smaller things to interact and connect within the “things” or “smart devices”.)
4) Thinking Things (objects that access semantic web and open cloud data to customize things)
_______
Building Blocks of IoT:
Four things form basic building blocks of IoT system –sensors, processors, gateways, applications. Each of these blocks has its own characteristics in order to form a useful IoT system.
Sensors (vide infra):
These form the front end of the IoT devices. These are part of the so called “Things” of the system. Their main purpose is to collect data from its surrounding (sensors) or give out data to its surrounding (actuators). These may have a unique IP address so that they can be easily identifiable over a large network. These have to be active in nature which means that they should be able to collect real time data. These can either work on their own (autonomous in nature) or can be made to work by the user depending on their needs (user controlled). Examples of sensors are: gas sensor, water quality sensor, moisture sensor etc.
Processors:
Processors are the brain of the IoT system. Their main function is to process the data captured by the sensors and process them so as to extract the valuable data from the enormous amount of raw data collected. In a word, we can say that it gives intelligence to the data. Processors mostly work on real-time basis and can be easily controlled by applications. These are also responsible for securing the data – that is performing encryption and decryption of data. Embedded hardware devices, microcontroller etc. are the ones that process the data because they have processors attached to it.
Gateways:
Gateways are responsible for routing the processed data and send it to proper locations for its (data) proper utilization. In other words, we can say that gateway helps in to and fro communication of the data. It provides network connectivity to the data. Network connectivity is essential for any IoT system to communicate. LAN, WAN, PAN etc. are examples of network gateways.
Applications:
Applications form another end of an IoT system. Applications are essential for proper utilization of all the data collected. Many cloud based applications are responsible for rendering effective meaning to the data collected. Applications are controlled by users and are delivery point of particular services. Examples of applications are: home automation apps, security systems, industrial control hub etc.
___
__
We’ve always had sensors, and that we’ve been at pains for some time to make information processing smaller, faster and cheaper. Convergence has long been the name of the game with wireless communication (RFID, GSM, 3G, WLAN, WiMAX, LTE) communication, product identification (barcodes, RFID), process control (sensor networks, home automation) and network interconnection (Ethernet, Internet, www, email). Embedded intelligence (smart cities, homes, transportation, and beyond), real-time monitoring (medical applications and environmental management), augmented reality (real and virtual world seamlessness) and semantic information (where a smart web known as Web 3.0 could meet the Internet of Things) are the major complimentary technologies to look forward to. Broadband Internet is become more widely available, the cost of connecting is decreasing, more devices are being created with Wi-Fi capabilities and sensors built into them, technology costs are going down, and smartphone penetration is sky-rocketing. All of these things are creating a “perfect storm” for the IoT.
_______
Overview of basic IoT:
______
______
Technology of IoT:
____
Essential Technologies involved in IoT
• RFID Technology
• Sensor Technology
• Wireless Communication
• Energy Harvesting Technologies
• Cloud Computing
• Advanced Internet Protocol IPv6.
_
Enablers of IoT technology:
A number of significant technology changes have come together to enable the rise of the IoT. These include the following:
•Cheap sensors – Sensor prices have dropped to an average 60 cents from $1.30 in the past 10 years.
•Cheap bandwidth – The cost of bandwidth has also declined precipitously, by a factor of nearly 40X over the past 10 years.
•Cheap processing – Similarly, processing costs have declined by nearly 60X over the past 10 years, enabling more devices to be not just connected, but smart enough to know what to do with all the new data they are generating or receiving.
•Smartphones – Smartphones are now becoming the personal gateway to the IoT, serving as a remote control or hub for the connected home, connected car, or the health and fitness devices consumers are increasingly starting to wear.
•Ubiquitous wireless coverage – With Wi-Fi coverage now ubiquitous, wireless connectivity is available for free or at a very low cost, given Wi-Fi utilizes unlicensed spectrum and thus does not require monthly access fees to a carrier.
•Big data – As the IoT will by definition generate voluminous amounts of unstructured data, the availability of big data analytics is a key enabler.
•IPv6 – Most networking equipment now supports IPv6, the newest version of the Internet Protocol (IP) standard that is intended to replace IPv4.
____
____
____
Device:
___
Devices for the internet of things must have three basic properties:
•A constant data connection
•Low power usage
•The ability to communicate short distances
______
Sensor:
_
A sensor is not a machine. It doesn’t do anything in the same sense that a machine does. It measures, it evaluates; in short, it gathers data. The Internet of Things really comes together with the connection of sensors and machines. That is to say, the real value that the Internet of Things creates is at the intersection of gathering data and leveraging it. All the information gathered by all the sensors in the world isn’t worth very much if there isn’t an infrastructure in place to analyse it in real time. Cloud-based applications are the key to using leveraged data. The Internet of Things doesn’t function without cloud-based applications to interpret and transmit the data coming from all these sensors. The cloud is what enables the apps to go to work for you anytime, anywhere. Let’s look at one example. In 2007, a bridge collapsed in Minnesota, killing many people, because of steel plates that were inadequate to handle the bridge’s load. When we rebuild bridges, we can use smart cement: cement equipped with sensors to monitor stresses, cracks, and twists. This is cement that alerts us to fix problems before they cause a catastrophe. And these technologies aren’t limited to the bridge’s structure. If there’s ice on the bridge, the same sensors in the concrete will detect it and communicate the information via the wireless internet to your car. Once your car knows there’s a hazard ahead, it will instruct the driver to slow down, and if the driver doesn’t, then the car will slow down for him. This is just one of the ways that sensor-to-machine and machine-to-machine communication can take place. Sensors on the bridge connect to machines in the car: we turn information into action. You might start to see the implications here. What can you achieve when a smart car and a smart city grid start talking to each other? We’re going to have traffic flow optimization, because instead of just having stoplights on fixed timers, we’ll have smart stoplights that can respond to changes in traffic flow. Traffic and street conditions will be communicated to drivers, rerouting them around areas that are congested, snowed-in, or tied up in construction. So now we have sensors monitoring and tracking all sorts of data; we have cloud-based apps translating that data into useful intelligence and transmitting it to machines on the ground, enabling mobile, real-time responses. And thus bridges become smart bridges, and cars smart cars. And soon, we have smart cities, and….
_
Types of sensors with representative examples:
| Sensor types | Sensor description | Examples |
| Position | A position sensor measures the position of an object; the position measurement can be either in absolute terms (absolute position sensor) or in relative terms (displacement sensor). Position sensors can be linear, angular, or multi-axis. | Potentiometer, inclinometer, proximity sensor |
| Occupancy and motion | Occupancy sensors detect the presence of people and animals in a surveillance area, while motion sensors detect movement of people and objects. The difference between the two is that occupancy sensors will generate a signal even when a person is stationary, while a motion sensor will not. | Electric eye, Radar |
| Velocity and acceleration | Velocity (speed of motion) sensors may be linear or angular, indicating how fast an object moves along a straight line or how fast it rotates. Acceleration sensors measure changes in velocity. | Accelerometer, gyroscope |
| Force | Force sensors detect whether a physical force is applied and whether the magnitude of force is beyond a threshold. | Force gauge, viscometer, tactile sensor (touch sensor) |
| Pressure | Pressure sensors are related to force sensors and measure the force applied by liquids or gases. Pressure is measured in terms of force per unit area. | Barometer, bourdon gauge, piezometer |
| Flow | Flow sensors detect the rate of fluid flow. They measure the volume (mass flow) or rate (flow velocity) of fluid that has passed through a system in a given period of time. | Anemometer, mass flow sensor, water meter |
| Acoustic | Acoustic sensors measure sound levels and convert that information into digital or analog data signals. | Microphone, geophone, hydrophone |
| Humidity | Humidity sensors detect humidity (amount of water vapor) in the air or a mass. Humidity levels can be measured in various ways: absolute humidity, relative humidity, mass ratio, and so on. | Hygrometer, humistor, soil moisture sensor |
| Light | Light sensors detect the presence of light (visible or invisible). | Infrared sensor, photodetector, flame detector |
| Radiation | Radiation sensors detect radiations in the environment. Radiation can be sensed by scintillating or ionization detection. | Geiger–Müller counter, scintillator, neutron detector |
| Temperature | Temperature sensors measure the amount of heat or cold that is present in a system. They can be broadly of two types: contact and non-contact. Contact temperature sensors need to be in physical contact with the object being sensed. Non-contact sensors do not need physical contact, as they measure temperature through convection and radiation. | Thermometer, calorimeter, temperature gauge |
| Chemical | Chemical sensors measure the concentration of chemicals in a system. When subjected to a mix of chemicals, chemical sensors are typically selective for a target type of chemical (for example, a CO2 sensor senses only carbon dioxide). | Breathalyser, olfactometer, smoke detector |
| Biosensors | Biosensors detect various biological elements such as organisms, tissues, cells, enzymes, antibodies, and nucleic acids. | Blood glucose biosensor, pulse oximetry, electrocardiograph |
_
The figure below shows convergence of sensor, RFID and internet:
_
Actuators:
Actuators convert information or energy from sensors into action by transmitting it to another power mechanism or system, such as heating or cooling a room. No human intervention need be involved in the decision-making process.
_
Most definitions of the Internet of Things include physical objects or devices that can sense and/or affect the physical environment, as shown in figure below. The IoT also includes virtual objects, such as electronic tickets, agendas, books, and wallets. The Internet of Things also includes people – this is particularly important in areas such as home automation, where humans can control the environment via mobile applications. Through services, such as cloud services, massive volumes of data (“big data”) are being processed and turned into valuable information, innovative applications are built and run, and business processes are being optimized by integrating device data, as shown below.
__
Unique addressability of things:
The ability to uniquely identify ‘Things’ is critical for the success of IoT. This will not only allow us to uniquely identify billions of devices but also to control remote devices through the Internet. The few most critical features of creating a unique address are: uniqueness, reliability, persistence and scalability. Every element that is already connected and those that are going to be connected, must be identified by their unique identification, location and functionalities. The current IPv4 may support to an extent where a group of cohabiting sensor devices can be identified geographically, but not individually. The Internet Mobility attributes in the IPV6 may alleviate some of the device identification problems; however, the heterogeneous nature of wireless nodes, variable data types, concurrent operations and confluence of data from devices exacerbates the problem further. Persistent network functioning to channel the data traffic ubiquitously and relentlessly is another aspect of IoT. Although, the TCP/IP takes care of this mechanism by routing in a more reliable and efficient way, from source to destination, the IoT faces a bottleneck at the interface between the gateway and wireless sensor devices. Furthermore, the scalability of the device address of the existing network must be sustainable. The addition of networks and devices must not hamper the performance of the network, the functioning of the devices, the reliability of the data over the network or the effective use of the devices from the user interface. To address these issues, the Uniform Resource Name (URN) system is considered fundamental for the development of IoT. URN creates replicas of the resources that can be accessed through the URL. With large amounts of spatial data being gathered, it is often quite important to take advantage of the benefits of metadata for transferring the information from a database to the user via the Internet. IPv6 also gives a very good option to access the resources uniquely and remotely. Another critical development in addressing is the development of a lightweight IPv6 that will enable addressing home appliances uniquely. Wireless sensor networks (considering them as building blocks of IoT), which run on a different stack compared to the Internet, cannot possess IPv6 stack to address individually and hence a subnet with a gateway having a URN will be required. With this in mind, we then need a layer for addressing sensor devices by the relevant gateway. At the subnet level, the URN for the sensor devices could be the unique IDs rather than human-friendly names as in the www, and a lookup table at the gateway to address this device. Further, at the node level each sensor will have a URN (as numbers) for sensors to be addressed by the gateway. The entire network now forms a web of connectivity from users (high-level) to sensors (low-level) that is addressable (through URN), accessible (through URL) and controllable (through URC).
__
IoT nodes:
IoT nodes are simple end points—mono-function, ubiquitous, free-standing sensors and actuators. In abstract terms, it’s easier to talk about a node, rather than list different possible node types (sensors, actuators, meters, devices, gateways, etc.). Each node has a Node ID. Node ID is an ID uniquely identifying a node within its corresponding context. If a globally unique ID is desired, an architecture should be used using a universally accepted ID scheme. Imposing low power consumption and lower cost, these devices can be mostly stateless or highly stateful; they can be “headless” or boast device-local UI/UX functions; they can be completely independent or tightly networked with their peers; their communications can be terse or “chirpy,” and the data they transmit and receive can be slow-changing or highly dynamic. Think light switches and sockets, thermostats and HVAC controls, motion sensors and perimeter alarm switches, soil moisture and air temperature sensors. The prototypical node deploys fairly minimal software, supporting core functionality for sensing or affecting its environment and communicating state/status information upstream. Such devices may benefit from an actual embedded OS or just run a main loop and device service code. With minimalist 4/8/16-bit CPUs, they are unlikely to deploy a full OSI TCP/IP stack, instead employing point-to-point communications, mesh networking, 6LowPAN or partial IP networking (UDP, etc.). There are three fundamental components that combine to form an IoT node: intelligence, sensing, and wireless communications. Wireless connectivity is vital because it will allow sensor nodes to be deployed quickly and easily without the requirement to route network cables to each location. There are a number of possible approaches for introducing low-power communications to an IoT node, ranging from purpose-designed protocols such as ZigBee to low-power variants of Bluetooth and Wi-Fi. Some of these protocols offer direct compatibility with the internet protocol (IP). Others rely on a gateway to map between IP packets and the leaner protocols used by the IoT sensor nodes.
_
In order to survive for long periods of time on a single battery charge, an IoT node needs to exhibit low power consumption. Typically, the node will be dormant for long periods of time, waking up for short periods to take a reading and then make a decision on whether to send out an alert based on the change or go back to sleep. A large number of microcontrollers are designed around this core requirement, sporting ultralow-energy sleep modes combined with high-performance instruction pipelines to streamline processing while awake. Each node must be able to operate uninterrupted without external power sources or batteries for at least 10 years, which is no small feat.
_
Node vs. Edge:
In Internet of Things, sensors, actuators, meters, devices, gateways, etc., are often depicted as nodes whereas links between sensors (friendships) are depicted as edges.
_
There are three aspects to the IoT – the central computing resource (cloud), the access points and hubs (gateways), and the distributed nodes.
The advancements and convergence of micro-electro-mechanical systems (MEMS) technology, wireless communications, and digital electronics has resulted in the development of miniature devices having the ability to sense, compute, and communicate wirelessly in short distances. These miniature devices called nodes interconnect to form a wireless sensor networks (WSN) and find wide ranging applications in environmental monitoring, infrastructure monitoring, traffic monitoring, retail, etc. This has the ability to provide a ubiquitous sensing capability which is critical in realizing the overall vision of ubicomp as outlined by Weiser. For the realization of a complete IoT vision, efficient, secure, scalable and market oriented computing and storage resourcing is essential. Cloud computing is the most recent paradigm to emerge which promises reliable services delivered through next generation data centers that are based on virtualized storage technologies. This platform acts as a receiver of data from the ubiquitous sensors; as a computer to analyze and interpret the data; as well as providing the user with easy to understand web based visualization. The ubiquitous sensing and processing works in the background, hidden from the user. This novel integrated Sensor–Actuator–Internet framework shall form the core technology around which a smart environment will be shaped: information generated will be shared across diverse platforms and applications, to develop a common operating picture (COP) of an environment, where control of certain unrestricted ‘Things’ is made possible. As we move from www (static pages web) to web2 (social networking web) to web3 (ubiquitous computing web), the need for data-on-demand using sophisticated intuitive queries increases. To take full advantage of the available Internet technology, there is a need to deploy large-scale, platform-independent, wireless sensor network infrastructure that includes data management and processing, actuation and analytics. Cloud computing promises high reliability, scalability and autonomy to provide ubiquitous access, dynamic resource discovery and composability required for the next generation Internet of Things applications. Consumers will be able to choose the service level by changing the Quality of Service parameters.
___
Radio Frequency Identification (RFID):
_
RFID stands for Radio-Frequency IDentification. The acronym refers to small electronic devices that consist of a small chip and an antenna. The chip typically is capable of carrying 2,000 bytes of data or less. RFID (Radio Frequency Identification) devices are wireless microchips used for tagging objects for automated identification. RFID systems consist of a reading device called a reader, and one or more tags. The reader is a powerful device with ample memory and computational resources. The RFID device serves the same purpose as a bar code or a magnetic strip on the back of a credit card or ATM card; it provides a unique identifier for that object. And, just as a bar code or magnetic strip must be scanned to get the information, the RFID device must be scanned to retrieve the identifying information. RFID is a system where a radio signal is transmitted to a specific transponder and to which it responds with another radio signal. Its aim is to carry data in suitable transponders (e.g. tags) and get it through by automatic reading, in the right place, at the right time, depending on the target application. RFID technology enables putting an identification label (e.g. tag) into a certain object and, by means of a reader, gets the information related to it without any physical contact. Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. The tags contain electronically stored information. RFID technology is a major breakthrough in the embedded communication paradigm which enables design of microchips for wireless data communication. They help in the automatic identification of anything they are attached to acting as an electronic barcode. The passive RFID tags are not battery powered and they use the power of the reader’s interrogation signal to communicate the ID to the RFID reader. This has resulted in many applications particularly in retail and supply chain management. The applications can be found in transportation (replacement of tickets, registration stickers) and access control applications as well. The passive tags are currently being used in many bank cards and road toll tags which are among the first global deployments. Active RFID readers have their own battery supply and can instantiate the communication. Of the several applications, the main application of active RFID tags is in port containers for monitoring cargo. NFC can be understood as having evolved from RFID and is a short-range, low-power wireless way to transfer small amounts of data between devices. NFC, short for Near Field Communication, is a short range wireless RFID technology that makes use of interacting electromagnetic radio fields instead of the typical direct radio transmissions used by technologies such as Bluetooth.
_
Long checkout lines at the grocery store are one of the biggest complaints about the shopping experience. Soon, these lines could disappear when the ubiquitous Universal Product Code (UPC) bar code is replaced by smart labels, also called radio frequency identification (RFID) tags. RFID tags are intelligent bar codes that can talk to a networked system to track every product that you put in your shopping cart. Imagine going to the grocery store, filling up your cart and walking right out the door. No longer will you have to wait as someone rings up each item in your cart one at a time. Instead, these RFID tags will communicate with an electronic reader that will detect every item in the cart and ring each up almost instantly. The reader will be connected to a large network that will send information on your products to the retailer and product manufacturers. Your bank will then be notified and the amount of the bill will be deducted from your account. No lines, no waiting.
_
Radio frequency identification system (RFID) is an automatic technology and aids machines or computers to identify objects, record metadata or control individual target through radio waves. Connecting RFID reader to the terminal of Internet, the readers can identify, track and monitor the objects attached with tags globally, automatically, and in real time, if needed. This is the so-called Internet of Things (IoT). RFID is often seen as a prerequisite for the IoT. The main advantage of using RFID is the possibility of reading without physical contact or any other direct connection between the reader and tag. RFID systems use many different frequencies, but generally the most common are low- (around 125 KHz), high- (13.56 MHz) and ultra-high frequency, or UHF (850-900 MHz). Microwave (2.45 GHz) is also used in some applications. Radio waves behave differently at different frequency, so you have to choose the right frequency for the right application. Radio waves bounce off metal and are absorbed by water at ultra-high frequencies. That makes tracking metal products or those with high water content problematic, but good system design and engineering can overcome this shortcoming. Low- and high-frequency tags work better on products with water and metal. In fact, there are applications in which low-frequency RFID tags are actually embedded in metal auto parts to track them. RFID technology has been available for more than fifty years. One reason that it has taken so long for RFID to come into common use is the lack of standards in the industry. Most companies invested in RFID technology only use the tags to track items within their control; many of the benefits of RFID come when items are tracked from company to company or from country to country.
_
RFID communication:
_
The Electronic Product Code (EPC) is a code number that gives the unique identification of a given physical object. The information about the object can be stored in databases located on the Internet or private networks. A RFID tag contains the binary representation of the EPC value that can be coded 64bits, 96bits or 198 bits long. There are different encoding schemes compatible with the EPC and the format chosen for the prototype development was the Serial Global Trade Item Number (SGTIN-96) of 96bits. Using the Internet as a basis, EPCs are encoded as URIs (Uniform Resource Identifier), which are a basic addressing scheme for all World Wide Web, thus ensuring that the EPC network is compatible with Internet developments. Finally, the Object Name Service (ONS) provides a global search service that supports an EPC code, where it is translated into a URL (Uniform Resource Locator), thus having more information about the object to be found. It is also important to notice that this service can be built using the same technology as DNS (Domain Name System). As mentioned, the ONS service can use the already existing DNS service, making use of the NAPTR (Naming Authority Pointer) resource record. Presently, ONS returns the URL(s) of services where a customer can possibly get more information about the object identified by an EPC tag owner company. Such services may be web services or any other type of service provided by the EPC tag.
_
The basic form of an EPC consists of a Header, EPC Manager Number, Object Class and Serial Number. The first two are part of the EPC global signing and the others are part of the EPC Manager owner signature. For example a 96-bit length SGTIN format is shown in table below.
This prototype is able to translate between EPC’s binary and decimal formats, make ONS queries and handle the received NAPTR records using its URL to access services such as HTML and EPCIS.
_
Wireless Sensor Networks (WSN):
Recent technological advances in low power integrated circuits and wireless communications have made available efficient, low cost, low power miniature devices for use in remote sensing applications. The combination of these factors has improved the viability of utilizing a sensor network consisting of a large number of intelligent sensors, enabling the collection, processing, analysis and dissemination of valuable information, gathered in a variety of environments. Active RFID is nearly the same as the lower end WSN nodes with limited processing capability and storage. The scientific challenges that must be overcome in order to realize the enormous potential of WSNs are substantial and multidisciplinary in nature. Sensor data are shared among sensor nodes and sent to a distributed or centralized system for analytics. The components that make up the WSN monitoring network include:
(a)WSN hardware—Typically a node (WSN core hardware) contains sensor interfaces, processing units, transceiver units and power supply. Almost always, they comprise of multiple A/D converters for sensor interfacing and more modern sensor nodes have the ability to communicate using one frequency band making them more versatile.
(b)WSN communication stack—The nodes are expected to be deployed in an ad-hoc manner for most applications. Designing an appropriate topology, routing and MAC layer is critical for the scalability and longevity of the deployed network. Nodes in a WSN need to communicate among themselves to transmit data in single or multi-hop to a base station. Node drop outs, and consequent degraded network lifetimes, are frequent. The communication stack at the sink node should be able to interact with the outside world through the Internet to act as a gateway to the WSN subnet and the Internet.
(c)WSN Middleware—A mechanism to combine cyber infrastructure with a Service Oriented Architecture (SOA) and sensor networks to provide access to heterogeneous sensor resources in a deployment independent manner. This is based on the idea of isolating resources that can be used by several applications. A platform-independent middleware for developing sensor applications is required, such as an Open Sensor Web Architecture (OSWA). OSWA is built upon a uniform set of operations and standard data representations as defined in the Sensor Web Enablement Method (SWE) by the Open Geospatial Consortium (OGC).
(d)Secure Data aggregation—An efficient and secure data aggregation method is required for extending the lifetime of the network as well as ensuring reliable data collected from sensors. Node failures are a common characteristic of WSNs, the network topology should have the capability to heal itself. Ensuring security is critical as the system is automatically linked to actuators and protecting the systems from intruders becomes very important.
_
RFID to IP (internet protocol) for things:
If, in a future Internet of Things, everyday objects are to be addressed and controlled via the Internet, then we should ideally not be resorting to special communications protocols as is currently the case with RFID. Instead, things should behave just like normal Internet nodes. In other words, they should have an IP address and use the Internet Protocol (IP) for communicating with other smart objects and network nodes. And due to the large number of addresses required, they should use the new IPv6 version with 128-bit addresses. The benefits of having IP-enabled things are obvious, even if the objects in question are not going to be made globally accessible but instead used in a controlled intranet environment. This approach enables us to build directly on existing functionality such as global interoperability, network-wide data packet delivery (forwarding and routing), data transport across different physical media, naming services (URL, DNS) and network management. The use of IP enables smart objects to use existing Internet services and applications and, conversely, these smart objects can be addressed from anywhere since they are proper Internet participants. Last but not least, it will be easy to use important application layer protocols such as HTTP. IPv6 also provides the interesting capability of automatic address configuration, enabling smart objects to assign their own addresses. Until recently, however, the prospect of full IP support for simple things appeared illusory due to the resources required (such as processor capacity and energy) and thus the costs involved. Instead, it was suggested to connect smart objects to the Internet indirectly via proxies or gateways. But the disadvantage of such non-standardized solutions is that end-to-end functionality is lost because standardized Internet protocols would be converted to proprietary protocols over the last few meters. Gateways would also generate added complexity, making installation, operation and maintenance time-consuming and costly. However, there are now not only 16-bit microcontrollers with sufficient storage that require less than 400 μW/MIPS, but also TCP/IPv6 stacks that can operate with 4 kB RAM and 24 kB flash memory. Equally important are wireless communications standards such as IEEE 802.15.4 that cover the layers below IP and consume relatively little power – ZigBee implementations require approximately 20 to 60 mW (for 1 mW transmission power, a range of 10 to 100 meters and a data transmission rate of 250 kbit/s). Whenever possible, the wireless unit is being used for short periods of time only in order to save energy. This approach enables AA batteries to provide a modest level of computing power and wireless communication that is nevertheless sufficient for many purposes over many months.
_
IPv4 to IPv6:
Integration with the Internet implies that devices will use an IP address as a unique identifier. However, due to the limited address space of IPv4 (which allows for 4.3 billion unique addresses), objects in the IoT will have to use IPv6 to accommodate the extremely large address space required. IPv4 is assigned 32-bit addresses, with a total limit of 4.3 billion; IPv6 is 128-bit, and allows for 340 trillion trillion trillion addresses. This makes it possible to assign a unique identifier to anything that’s part of the IoT (although not everything needs to be IP addressable, such as light switches). Objects in the IoT will not only be devices with sensory capabilities, but also provide actuation capabilities (e.g., bulbs or locks controlled over the Internet). To a large extent, the future of the internet of things will not be possible without the support of IPv6; and consequently the global adoption of IPv6 in the coming years will be critical for the successful development of the IoT in the future.
__________
Attributes of IoT:
Main attributes that make “things” a part of the Internet of Things:
• Sensors: IoT devices and systems include sensors that track and measure activity in the world.
• Connectivity: Internet connectivity is either contained in the item itself, or a connected hub, smartphone, or base station. If it’s the latter, then the base station will likely be collecting data from an array of sensor-laden objects, and relaying data to the cloud and back.
• Processors: Just like any computing device, IoT devices will contain some computing power “under the hood,” if only to be able to parse incoming data and transmit it. These characteristics all apply to today’s smartphones, of course, but many IoT devices will also need to be equipped with several special features to be truly useful. These will differentiate IoT devices, particularly remote ones, from today’s smartphones.
• Energy-efficiency: Many devices in the IoT may be difficult, costly, or dangerous to access for charging or battery replacement. Therefore, they may need to be able to operate for many years unattended using a conservative amount of energy or be able to wake up only periodically to relay data.
• Cost-effectiveness: Objects that contain sensors may need to be distributed broadly to be useful, as in the case of sensors in food products in supermarkets that would indicate if an item has spoiled. These would need to be relatively inexpensive to purchase and deploy.
• Quality and reliability: Some IoT devices will need to operate in harsh environments outdoors and for extended periods of time.
• Security: IoT devices may need to relay sensitive or regulated information such as health-related data, so data security will be critical.
_________
Components of IoT:
There are three IoT components which enables seamless ubicomp: (a) Hardware—made up of sensors, actuators and embedded communication hardware (b) Middleware—on demand storage and computing tools for data analytics and (c) Presentation—novel easy to understand visualization and interpretation tools which can be widely accessed on different platforms and which can be designed for different applications. Internet of Things middleware is software that serves as an interface between components of the IoT, making communication possible among elements that would not otherwise be capable.
_
| IoT Components | Description |
| Physical Objects: | Things |
| Sensors | Sense the physical environment |
| Actuators | Affect the physical environment |
| Virtual Objects | Electronic tickets, Agendas, Books, Wallets |
| People | E.g.: Humans can control the environment via mobile apps |
| Services | E.g.: Cloud services – can be used to:• Process big data and turn it into valuable information• Build and run innovative applications• Optimize business processes by integrating device data. |
| Platforms | Type of middleware used to connect IoT components (objects, people, services, etc.) to IoT. Provide numerous functions:• Access to devices• Ensuring proper installation/behavior of device• Data analytics• Interoperable connection to local network, cloud or other devices. |
| Networks | IoT components are tied together by networks, using various wireless and wireline technologies, standards, and protocols to provide pervasive connectivity. |
_
Internet of Things builds on three major technology layers: Hardware (including chips and sensors), Communication (including mostly some form of wireless network), and Software (including data storage, analytics, and front end applications). Computer chip, also called chip is a small piece of semiconducting material (usually silicon) on which an integrated circuit is embedded. A typical chip can contain millions of electronic components (transistors). Computers consist of many chips placed on electronic boards called printed circuit boards. There are different types of chips. For example, CPU chips (also called microprocessors) contain an entire processing unit, whereas memory chips contain blank memory. CPU (central processing unit) is the brains of the computer where most calculations take place.
The reason for the Internet of Things coming up so quickly right now is that there have been major technological advancements in all three of these technology layers:
• Hardware
Costs of sensors have declined by 54% over the last 10 years. Moreover, form factors are shrinking quickly. Complete sensor packages that are smaller than fingertips have become the standard.
• Communication
Mobile devices have become a commodity for the wider public. At the same time the cost of bandwidth has declined by 97% over the last 10 years.
• Software
The cost of processing has even declined 98% in the same timeframe. Moreover, a number of big data tools and big data infrastructure such as efficient databases have emerged over the last 5 years.
_____
IoT platform:
IoT needs IoT Platforms – the type of middleware that is used to connect the IoT components (objects, people, services, etc.) to the IoT. The IoT platforms provide numerous functions, such as access to devices, ensuring the proper installation and behavior of the device, data analytics, and interoperable connection to the local network, cloud, or other devices. Finally, all of the components in an IoT environment should be tied together by networks through various wireless and wireline technologies, standards, and protocols to provide pervasive connectivity.
_
Hardware Sensor Platforms:
One of the biggest drivers of the IoT is the increasing number of low-cost sensors available for many different kinds of functionality. Some of the standard sensors include movement (via accelerometer), sound, light, electrical potential (via potentiometer), temperature, moisture, location (via GPS), heart rate and heart rate variability, and GSR (galvanic skin response or skin conductivity). Other sensors include ECG/EKG (electrocardiography to record the electrical activity of the heart), EMG (electromyography to measure the electrical activity of muscles), EEG (electroencephalography to read electrical activity along the scalp), and PPG (photoplethysmography to measure blood flow volume). These sensors are included in a variety of devices and solutions. The trend is moving towards multi-sensor platforms that incorporate several sensing elements. For example, the standard for the next-generation of personalized self-tracking products appears to be some mix of an accelerometer, GSR sensor, temperature sensor, and possibly heart rate sensor (from which heart rate variability may be calculated). Some recognized first-generation quantified tracking devices and applications include the Fitbit, myZeo, BodyMedia, MapMyRun, RunKeeper, MoodPanda, Nike Fuelband, The Eatery, Luminosity’s Brain Trainer, and the NeuroSky and Emotiv brain-computer interfaces (BCI). The next generation of IOT quantified tracking devices is visible in product announcements, many of which fall into the category of wearable electronics and/or multi-sensor platforms. These products include smartwatches, wristband sensors, wearable sensor patches, artificial reality-augmented glasses, brain computer interfaces and wearable body metric textiles. Other important categories include smartphone applications and their enhancements, and environmental monitoring and home automation sensors.
_
BOLT IoT Platform:
BOLT (formerly NetPlug) is an Internet of Things platform (Hardware + Software) that enables user to build IoT products and projects. Using BOLT, users can control and monitor devices from any part of the world. It provides the ability to embed Wi-Fi capabilities within other systems, or to function as a standalone application. The manufacturers can embed the Bolt hardware in their product, develop a custom UI and then their users can control their products using the NetPlug app. Bolt works on pay as you go basis, which means the manufacturers have no capital investments to get their products IoT enabled. This lets even small scale players to build IoT enabled products and services. BOLT (Formally NetPlug) was developed by Inventrom, a Goa, India based IoT company.
_
Software Processing and Data Transmission:
Now having an idea of the different kinds of sensor hardware, and quantified self, home, and environment applications, let us look more closely at the software processing tools and the technical landscape of the developing IoT ecosystem. Data streams collected from the underlying hardware sensors and circuit boards may need to be processed in a variety of stages. Some data processing may occur locally, where the hardware is based geographically and the data is collected, and then additional processing may take place after the data has been transmitted to the Internet, and still more for eventual end-user consumption. For the data transmission portion of the process, any variety of standard communication protocols may be used including Wi-Fi, Bluetooth, ANT, ZigBee, USB, and 2G, 3G, and 4G. An important recent innovation is Bluetooth low-energy (BLE) which allows mobile devices to send data more efficiently with much greater battery efficiency than traditional Bluetooth, essentially enabling the regular ongoing if not continuous transmission of relevant data. The volume of IoT sensor data being generated is already significant and could grow in an accelerating manner. Most of the data may be stored in the cloud, e.g., on the Internet somewhere, and it is important to consider data privacy, security, ownership, and access concerns. Cloud services vendors like AT&T and Qualcomm are developing services specifically for biosensor and health data collection and storage. Salesforce.com’s Heroku and Microsoft’s Azure are other examples of cloud platforms-as-a-service (data collection and analysis services) which run on either public or private clouds like Amazon Web Services, Joyent, and Rackspace.
_______
Architecture of IoT:
_
Implementation of IoT is based on an architecture consisting of several layers: from the field data acquisition layer at the bottom to the application layer at the top. The layered architecture is to be designed in a way that can meet the requirements of various industries, enterprises, societies, institutes, governments etc. Figure below presents a generic layered architecture for IoT. The layered architecture has two distinct divisions with an Internet layer in between to serve the purpose of a common media for communication. The two layers at the bottom contribute to data capturing while the two layers at the top are responsible for data utilization in applications.
_
The functionalities of the various layers are discussed briefly in the following:
1. Edge layer: this hardware layer consists of sensor networks, embedded systems, RFID tags and readers or other soft sensors in different forms. These entities are the primary data sensors deployed in the field. Many of these hardware elements provide identification and information storage (e.g. RFID tags), information collection (e.g. sensor networks), information processing (e.g. embedded edge processors), communication, control and actuation.
2. Access gateway layer: the first stage of data handling happens at this layer. It care of message routing, publishing and subscribing and also performs cross platform communication, if required.
3. Middleware layer: this is one of the most critical layers that operates in bi-directional mode. It acts as an interface between the hardware layer at the bottom and the application layer at the top. It is responsible for critical functions such as device management and information management and also takes care of issues like data filtering, data aggregation, semantic analysis, access control, information discovery such as EPC (Electronic Product Code) information service and ONS(Object Naming Service).
4. Application layer: this layer at the top of the stack is responsible for delivery of various applications to different users in IoT. The applications can be from different industry verticals such as: manufacturing, logistics, retail, environment, public safety, healthcare, food and drug etc. With the increasing maturity of RFID technology, numerous applications are evolving which will be under the umbrella of IoT.
_
Simplified IoT architecture:
__________
Embedded system to IoT:
The Internet of Things (IoT) is about interconnecting embedded systems, bringing together two evolving technologies: wireless connectivity and sensors. These connected embedded systems are independent microcontroller-based computers that use sensors to collect data. These IoT systems are networked together usually by a wireless protocol such as WiFi, Bluetooth, 802.11.4, or a custom communication system. The networking protocol is selected based on the distribution of nodes and the amount of data to be collected. This data is sent over the network to the main hub or computer. This main computer collects and analyzes the data, storing it in memory and even making system decisions based on the results of the analysis. The integration of embedded devices into the Internet introduces several new challenges, since many of the existing Internet technologies and protocols were not designed for this class of devices. These embedded devices are typically designed for low cost and power consumption and thus have very limited power, memory and processing resources and are often disabled for long-times (sleep periods) to save energy. The networks formed by these embedded devices also have different characteristics than those typical in today’s Internet. These constrained networks have different traffic patterns, high packet loss, low throughput, frequent topology changes and small useful payload sizes. In the past few years, several innovations were developed to enable the extension of Internet technologies to constrained devices, moving away from proprietary architectures and protocols. Most of these efforts focused on the networking layer: IPv6 over Low-Power Wireless Personal Area Network, Transmission of IPv6 Packets over IEEE 802.15.4 Networks, IETF routing over low-power and lossy networks or the ZigBee adoption of Internet Protocol Version 6 (IPv6). These new standards enable the realization of an Internet of Things, where end-to-end IP-based network connectivity with tiny objects such as sensors and actuators becomes possible.
______
IoT Network:
_
Broad network classes with representative examples by connection types:
| Personal area network(PAN) | Local area network(LAN) | Wide area network(WAN) | |
| Wired connections | USB | Ethernet | Not applicable |
| Wireless connections | Bluetooth, ZigBee, Near Field Communication, Wi-Fi | Wi-Fi, WiMAX | WiMAX, weightless, cellular technologies such as 2G, 3G, 4G (LTE) |
__
IoT connectivity:
In 2016 an operational definition of Internet of Things (IoT) is the seamless data flow between the
• BAN (body area network): the ambient hearing aide, the smart t-shirt, Glass
• LAN (local area network): the smart meter as a home interface
• WAN (wide area network): Telematics, ITS, Connected Car
• VWAN (very wide area network): the smart city as e-gov services everywhere no longer tied to physical locations
_
In IoT network some of the technologies that rules are:
WPAN (Wireless Personal Area Network) which include networks like Zigbee, Bluetooth, 6LoWPAN etc. On a slightly larger wireless network area scale, WLAN (Wireless Local Area Network) which includes Wi-Fi is to be used. On a larger scale, the mobile communication technologies like 2G, 3G, 4G, LTE remains. Smartphones and mobile communication system are used and they connect to the base stations and base stations will provide connectivity to the Wide Area Network (WAN) which is the Internet. Smartphones are equipped with Bluetooth and Wi-Fi, therefore we can connect an IoT network. The most common topology control is the WPAN which is Bluetooth or NFC (Near Field Communication). The WPAN are connected to a smartphone and the smartphone can bring the signal up through 3G, 4G LTE through the base station and the base station will connect that to the WAN. Therefore we get a technology linking on another technology.
_
Wi-Fi:
•Wi-Fi is a WLAN (Wireless Local Area Network) technology based on the IEEE 802.11 standards.
•Wi-Fi Devices: Smartphones, Smart Devices, Laptop Computers, PC, etc.
•Applications Areas:
•Home, School, Computer Laboratory, Office Building, etc.
•Wi-Fi devices and APs (Access Points) have a wireless communication range of about 30 meters indoors.
•Wi-Fi data rate is based on its protocol type:
•IEEE 802.11a can achieve up to 54 Mbps
•IEEE 802.11b can achieve up to 11 Mbps
•IEEE 802.11g can achieve up to 54 Mbps
•IEEE 802.11n can achieve up to 150 Mbps
•IEEE 802.11ac can achieve up to 866.7 Mbps
•IEEE 802.11ad can achieve up to 7 Gbps
Wi-Fi uses 2.5GHz radio bands for 802.11b, 802.11g, or 802.11n, and 5GHz for 802.11a. Having been in use in various forms for more than 15 years, Wi-Fi has the benefit of being the most mature wireless-networking radio technology suitable for IoT applications. Through protocols such as WPS, Wi-Fi can offer easy integration into an existing network for devices that have little to no physical user interface. Of the wireless technologies suitable for IoT applications, Wi-Fi has the best power-per-bit transmission efficiency. In general, Wi-Fi tends to suit applications where compliance with the IP stack is an advantage, there is a requirement to deliver large amounts of data, such as audio or video, or the remote devices can be powered by external energy sources.
_
Bluetooth:
•Bluetooth is a WPAN (Wireless Personal Area Network) protocol designed by the Bluetooth SIG (Special Interest Group)
•Replaces cables connecting many different types of devices
•Mobile Phones & Headsets
•Heart Monitors & Medical Equipment
•Bluetooth’s standard PAN range is usually 10 meters (50 m in Bluetooth 4.0)
•Bluetooth Low Energy (in Bluetooth 4.0) provides reduced power consumption and cost while maintaining a similar communication range.
•Bluetooth 2.0 + EDR can achieve up to 2.1 Mbps
•Bluetooth 3.0 + HS can achieve up to 24 Mbps
•Bluetooth 4.0 can achieve up to 25 Mbps
Bluetooth Low-Energy (BLE) or Bluetooth Smart provides a similar range to classic Bluetooth but with reduced power consumption. In place of the 1MHz channels used by the original Bluetooth protocol, BLE uses a smaller set of wider-bandwidth channels of 2MHz but with a lower peak data rate. The channel bandwidth is similar to that of ZigBee but with narrower spacing. A key advantage of BLE is its lower latency, just 3ms versus the 100ms of classic Bluetooth, as well as lower complexity so that its software stack can easily be incorporated into lower-cost microcontrollers. BLE retains support for frequency hopping from the original Bluetooth protocol, which makes it more robust than ZigBee in the presence of strong interfering signals. One of the main application areas for BLE is medical instrumentation, where a number of on-body sensors to monitor heart rate, blood pressure, and posture relay their readings at regular intervals to a central controller, which may be a mobile phone or a dedicated medical instrument.
_
IEEE 802.15.4 Standard:
•Low-cost, low-speed, low-power WPAN (Wireless Personal Area Network) protocol.
•IEEE 802.15.4 applications are ZigBee, 6LoWPAN (IPv6 over Low power Wireless Personal Area Networks), WirelessHART (Highway Addressable Remote Transducer), RF4CE (Radio Frequency for Consumer Electronics), MiWi (Microchip Wireless Protocol), and ISA100.11a
_
ZigBee:
•Supported by the ZigBee Alliance
•Provides IEEE 802.15.4 higher layer protocols required for low powered radio system.
•IEEE 802.15.4 defines the physical and MAC layers.
•ZigBee provides the application and network layer protocols.
•ZigBee works well in isolated network environments.
Zigbee network is made up of Coordinator (C) which is required to establish a network connection. ‘C’ establishes PAN, router (R) which provides the network connection to the end devices and End Device (E) which are the IoT devices connected to the network. ZigBee is a low-power wireless network specification based on the IEEE 802.15.4 (2003) standard that was developed by a group of 16 companies involved in industrial and building automation. A novel aspect of ZigBee compared to many other networking protocols lies in its use of mesh networking. This allows IoT nodes far away from a central controller to use nodes in between to carry their communications. This not only extends the range of a central gateway, it also increases robustness as a transmission can use a number of different routes through the mesh.
_
6LoWPAN (IPv6 over Low power Wireless Personal Area Networks):
•Supports IPv6 packets over IEEE 802.15.4 WPANs
•Enables IPv6 IoT wireless network support
•Low power design aspect included.
•Good for battery operated IoT devices
•6LoWPAN is an IETF (Internet Engineering Task Force) standard that uses the IEEE 802.15.4 WPAN technology.
In the 6LoWPAN node, Bluetooth Smart devices can connect to the internet over Bluetooth Smart using a border router. The border router acts as a device that is connected to the internet and provides access for the nodes to the internet.
_
Z- Wave:
The Z-Wave protocol is an interoperable, wireless, RF-based communications technology designed specifically for control, monitoring and status reading applications in residential and light commercial environments.
•Low Powered RF communications technology that supports full mesh networks without the need for a coordinator node.
•Operates in the sub-1GHz band; impervious to interference from Wi-Fi and other wireless technologies in the 2.4-GHz range (Bluetooth, ZigBee, etc.).
•Designed specifically for control and status apps, supports data rates of up to 100kbps, with AES128 encryption, IPV6, and multi-channel operation.
_
UDP:
There are two types of Internet Protocol (IP) traffic. They are TCP or Transmission Control Protocol and UDP or User Datagram Protocol. TCP is connection oriented – once a connection is established, data can be sent bidirectional. UDP is a simpler, connectionless Internet protocol. UDP is an alternative communications protocol to TCP used primarily for establishing low-latency and loss tolerating connections between applications on the Internet. UDP in embedded systems can be used to transmit data in IoT.
_
BLE and Wi-Fi can be used together efficiently as they both support coexistence protocols designed to reduce interference between the two on their common frequency band of 2.4GHz. This coexistence ability lends itself to implementation in gateway designs where BLE is used for connections to sensor nodes and Wi-Fi for relaying aggregated data to a backbone network. The APx4 from Bluegiga provides an off-the-shelf solution for this, providing support for both Wi-Fi and the full Bluetooth 4.0 software stack that includes BLE, based around a powerful 450MHz ARM9 processor. A number of integrated microcontrollers and support chipsets from vendors such as Atmel, CSR, Freescale, STMicroelectronics and Texas Instruments provide support for protocols such as BLE, Wi-Fi and ZigBee. For implementations that need flexibility, the configurable radio transceivers made by Lime Microsystems make it easier to deploy nodes that can be programmed with a specific RF interface personality at the point of manufacture to suit different networking needs in the target system.
_
Bluetooth, of course, does many of these things, and it does so securely. But even with the latest Bluetooth LE (Low Energy) standard it can sap a lot of energy from a small product, and thereby reduce its usefulness. It also doesn’t really do mesh networks, so its 10-meter range can be limiting. Then there is Wi-Fi. It has much better range (although having just one router in a house often leads to dead spots) but it comes at a huge power cost. Any IoT device using Wi-Fi is going to need a big battery or a power supply. And so that, again, limits its IoT uses. Because of these restrictions, IoT specific protocols have emerged. ZigBee and Z-Wave are typically grouped together because they both fill the two biggest gaps: they use very little power and they allow for mesh networks. With these protocols, you can run your devices all over your house, you don’t need to plug them all in, and they can communicate with each other in a mesh, so coverage is good. The problem is that neither protocol appears in most computing devices, so you need a hub somewhere in the home to get them to communicate with and be controlled by your phone or laptop. There are some differences between ZigBee and Z-Wave. ZigBee uses a higher frequency and as a result can transmit more data, but Z-Wave has a bigger range – about 30 meters, compared to ZigBee’s Bluetooth-like 10 meters. As for Thread – the new kid on the block – this protocol was created last year by a number of big IoT names (Google, ARM, Samsung). The big advantage of Thread is that it is an IP protocol and so can work with the vast internet infrastructure that already exists, particularly in home routers, as well as take advantage of the future expansion to IPv6 networks. When it came out, many felt that Thread was a threat to ZigBee (it uses the same frequency band, for example). But recently, Thread and ZigBee announced they would interoperate with one another. That partnership could turn the market on its head and put Z-Wave – which is the most popular protocol at the moment for IoT devices – under threat. And all of that is ignoring the incumbent big Insteon, which has its own system that uses both radio and its own old-school powerline protocol to spread networking information around the house.
_
How do IoT devices communicate?
An IoT device will have a radio that can send and receive wireless communications. IoT wireless protocols are designed to accomplish some basic services: Operate on low power, use low bandwidth and work on a mesh network. Some work on the 2.4 GHz band, which is also used by Wi-Fi and Bluetooth, and the sub-GHz range. The sub-GHz frequencies, including 868 and 915 MHz bands, may have the advantage of less interference.
_
Why is low power and low bandwidth important in IoT?
Some IoT devices will get power from electrical systems, but many, such as door locks and standalone sensors, will use batteries. These devices send and receive small amounts of information intermittently or periodically. Consequently, the battery life of an IoT device can range from 1.5 years to a decade, if the battery lasts that long. One IoT maker, Insteon, uses both radio and powerline communication, which can send data over existing electrical wiring as well as via a radio, which it says will offer an increased measure of reliability.
_
What is a mesh network?
Devices in a mesh network connect directly with one another, and pass signals like runners in a relay race. It is the opposite of a centralized network. The transmission range of an IoT device on a mesh network is anywhere from 30 feet to more than 300 feet. Since mesh network devices can hand-off signals, they have an ability to connect thousands of sensors over a wide area, such as a city, and operate in concert. Mesh networks have the added ability of working around the failure of any individual device. Wireless mesh IoT protocols include the Z-Wave Alliance, the Zigbee Alliance, and Insteon, which also has an alliance of vendors. These protocols aren’t directly interoperable, although there are workarounds via hubs. ZigBee is an open protocol, but its critics say that not all of its implementations are necessarily the same. ZigBee runs a certification to ensure standard deployments. Insteon and Z-Wave are proprietary, which may ensure standardization of implementation.
_
What’s the best wireless network for the IoT?
Today, no wireless technology has a dominant market share in IoT applications. Nick Jones, an analyst at research firm Gartner, said more than 10 IoT wireless technologies will “get significant traction” in IoT applications. These wireless technologies include cellular, satellites and new communications such as Weightless, which uses “white space,” or unoccupied TV channels. More importantly, no one wireless technology will meet every need and circumstance. A connected car, for instance, will use a cellular network to contact your home network.
_
Will I need a gateway or hub in the IoT?
A gateway, bridge or hub provides a connection point between your home network and other devices. The hub works with your home router and provides communications to the machines, devices and sensors that are part of your IoT universe. You will want, by default, your Zigbee smart meter to communicate with your Z-Wave or Insteon thermostat. This will also be true for the washing machine that is connected to a smart metering system and starts a wash only when electric rates are at their lowest point. These connections will be established through hubs that support multiple wireless technologies. SmartThings, for instance, makes a hub that supports both Zigbee and Z-Wave, as well as a platform to build connecting applications. Eventually, these wireless technologies may be included in home routers, set-top boxes from your cable companies, or even devices such as a Google Chromecast.
_
Won’t Bluetooth win in the end?
Bluetooth Low Energy was originally aimed at wearable technology, not the broad IoT market. But in early 2014, CSR, a semiconductor maker, announced a mesh network for Bluetooth, meaning it could now connect to thousands of things. Bluetooth’s ubiquity in mobile devices means that a Bluetooth mesh network as a broad IoT platform will have some advantages. Because Bluetooth is already a feature on smartphones, a smartphone could act as a management hub inside a home. But it’s not perfect. A hub will be needed if someone wants to connect with the home network remotely, such as from work.
__
Wireless connectivity in IoT:
Wireless connectivity technology has come a long way and just in time to meet the growing needs of the IoT. But what changed?
1. First, wireless connectivity is now microcontroller (MCU) friendly – meaning that you can pair connectivity with an MCU rather than a larger and more power-hungry microprocessor (MPU). The complexity of the networking stack and protocols is encapsulated and replaced with simplified APIs. This shift is key for the IoT since most end-nodes will be powered by MCUs and will be wirelessly connected to the cloud in some way.
2. Second, more development kits, reference designs and evaluation modules are available to speed development. So whether you want to add Bluetooth low energy, Wi-Fi, ZigBee, 6LoWPAN or Sub-1 GHz wireless connectivity there is a kit out there to help get you started. This is helping novices play around with wireless connectivity to see how it fits in their designs and prototypes.
3. Third, it is easier to connect to the cloud than ever before. The IoT is a new business model that many companies don’t understand how to manage. There is the physical connection through connectivity, but also cloud services, data management and more that need to be considered. There are several companies that offer IoT cloud services with many specializing in specific markets or applications. However, semiconductor companies are working with these cloud service providers to port the cloud APIs to their MCUs and wireless connectivity devices to make it easier for customers to add cloud connectivity.
4. Last, in order for the IoT to be successful, it needs to be easy for consumers. Devices need to be easy to connect, configure and use otherwise they will not be successful. If the IoT is going to reach the anticipated 50 billion connected devices by 2020, easy is mandatory.
_______
Cellular IoT:
We all know about internet which is collection of computers connected together to share the information and resources. It is also referred as Inter-Connection of Networks. Internet basically connects only people. Internet of Things basically connects all the things/devices/objects into the internet world. IoT has changed the concept of “connecting people” to “connecting Every-Things”.
As IoT standard has not yet been finalized, companies are working towards converting their existing IPs compliant for IoT support. There will be change in the physical layer and upper layer protocol stack will remain same. As mentioned in figure IoT device gets connected with device gateway on the network side which in turn interfaced with internet via WAN connection. This way two IoT devices can communicate with each other.
_______
IoT with 5G network:
______
Wearable IoT Networks:
This is a technology where the above discussion is brought to reality. Wearable devices (e.g., shoes, watch, glasses, belt, etc.) can be used to detect biometric information. Smart device collects the information and communicates with control center and/or medical server through the Internet.
_
IoT as a Network of Networks:
Currently, IoT is made up of a loose collection of disparate, purpose-built networks. Today’s cars, for example, have multiple networks to control engine function, safety features, communications systems, and so on. Commercial and residential buildings also have various control systems for heating, venting, and air conditioning (HVAC); telephone service; security; and lighting. As IoT evolves, these networks, and many others, will be connected with added security, analytics, and management capabilities as seen in the figure below. This will allow IoT to become even more powerful in what it can help people achieve.
______
______
The figure below shows how IoT works:
________
The Internet of Things has a Gateway Problem:
The vision of an Internet of Things (IoT) has captured the imagination of the world and raised billions of dollars, all before we stopped to deeply consider how all these Things should connect to the Internet. The current state-of-the-art requires application-layer gateways both in software and hardware that provide application specific connectivity to IoT devices. In much the same way that it would be difficult to imagine requiring a new web browser for each website, it is hard to imagine our current approach to IoT connectivity scaling to support the IoT vision. The IoT gateway problem exists in part because today’s gateways conflate network connectivity, in-network processing, and user interface functions and disentangling these functions would improve the connectivity potential for IoT devices.
_
Mobile computers, including laptops, tablets, and smartphones, have experienced unparalleled success due in no small part to an abundance of wireless connectivity. Widespread Wi-Fi and cellular networks provide universal and transparent access to the Internet and cloud-powered applications. This has driven the success of mobile computing. The coming wave of tiny, embedded, low-power, wireless, mobile, and wearable devices, however, does not currently enjoy the same level of ubiquitous and universal access to the Internet. Due to battery constraints and lifetime considerations, these devices tend to rely on low-power wireless communications like Bluetooth Low Energy (BLE) instead of more well-connected, but also more power intensive, Wi-Fi and 3G/4G cellular radios, despite their increasing ubiquity. To connect to the Internet, these devices require an application layer gateway—a system capable of translating data from the low-power link to the Internet at large. However, current implementations of these low-power links do not provide an Internet gateway, but rather, as figure below depicts, a narrow connection to a device-specific application that must be installed on a smartphone or laptop.
_
Opening a new webpage on a laptop does not require a new application on the Wi-Fi router, but connecting a new IoT device does require a new smartphone app, a new laptop dongle, or a new base station device, as figure below illustrates.
_
From smartwatches that interoperate with only a small subset of smartphones to wearable health monitors that cease communicating when their paired phone dies, it is clear that the Internet of Things (IoT) has a gateway problem. While the global network of well-connected smartphones provides a promising foundation for ubiquitous, low-power, last-inch networking, the current siloed, segmented, and application-specific approach to wireless connectivity is hampering the growth potential of this emerging device class. Addressing this problem requires a new networking architecture for low-power wireless devices that better leverages the opportunities provided by the worldwide network of smartphones. Such architecture would need to provide convenient and transparent access to the Internet for low-power devices while offering data integrity, security, throughput, and lifetime for the phone and device. A novel approach uses BLE, common on modern smartphones, as the primary link between low-power peripherals and capable smartphones. In contrast to the application-specific design of device phone interactions, however, researchers envision an open, two-prong gateway model. First, they envision that any BLE device could leverage any smartphone as a temporary IP router and act as a normal IP end host. Second, any phone could proxy a Bluetooth profile to the cloud on behalf of a device. The former allows for a high degree of flexibility while the latter may be better suited to the power and processing constraints of the device. Both can be implemented as part of an independent app or OS service on the phone.
________
Intelligence:
Ambient intelligence and autonomous control are not part of the original concept of the internet of things. Ambient intelligence and autonomous control do not necessarily require Internet structures, either. However, there is a shift in research to integrate the concepts of the internet of things and autonomous control, with initial outcomes towards this direction considering objects as the driving force for autonomous IoT. In the future the internet of things may be a non-deterministic and open network in which auto-organized or intelligent entities (Web services, SOA components), virtual objects (avatars) will be interoperable and able to act independently (pursuing their own objectives or shared ones) depending on the context, circumstances or environments. Autonomous behavior through the collection and reasoning of context information as well as the objects ability to detect changes in the environment, faults affecting sensors and introduce suitable mitigation measures constitute a major research trend, clearly needed to provide credibility to the IoT technology. Modern IoT products and solutions in the marketplace use a variety of different technologies to support such context-aware automation but more sophisticated forms of intelligence are requested to permit sensor units to be deployed in real environments.
_____
Information Visualization:
Ultimately the large volumes of IoT sensor data need to be translated into something human-readable and human-usable. The first two steps in this process are data acquisition from hardware sensor platforms, and information creation through software processing. Then the information needs to be made accessible so that meaning-making can happen. The usual way is through graphical presentation. Visualization is critical for an IoT application as this allows the interaction of the user with the environment. With recent advances in touch screen technologies, use of smart tablets and phones has become very intuitive. For a lay person to fully benefit from the IoT revolution, attractive and easy to understand visualization has to be created. As we move from 2D to 3D screens, more information can be provided in meaningful ways for consumers. This will also enable policy makers to convert data into knowledge, which is critical in fast decision making. Extraction of meaningful information from raw data is non-trivial. This encompasses both event detection and visualization of the associated raw and modelled data, with information represented according to the needs of the end-user.
_
The ‘So What’ Interface:
What is even more challenging to develop than meaning-making through the human-readable information visualization layer, and which arguably has been mostly nonexistent to date, is the ‘So What’ layer that impels action-taking. This is the information presented in context, in such a way where it would be obvious and intuitive which actions to take as a result of seeing the information. The ‘So What’ layer makes sense of the data, and allows action items to be derived based on real information. Data can be seen more scientifically, relating what might have seemed not to be related with what is actually related. There are several reasons why the reaction to some of the new IoT data flows might be ‘So What?’ A lot of these data flows are completely new—they are being created for the first time, and have not been previously available, especially on a consumer basis. In the past, individuals did not interact directly with a lot of data or unprocessed data. Moreover, not only are there new data flows now available, there are also new kinds of data flows. The new kinds of data flows are forcing conceptual and behavioral changes in how humans interact with data. As usual, there is typically a lag time between the availability of new technologies, and the individual and societal maturation process around them. It is just starting to be realized that there are these new data flows available, that they are new kinds of data flows, where perhaps a change in mind-set is required to understand them, and further, that a deeper contemplation of the appropriate uses of the different kinds of data flows is also required.
_
Supporting Infrastructure:
Underlying the development of the IoT ecosystem (sensor hardware, software processing, information visualization, and action-taking) are some important enabling mechanisms. Some of these include new business models like crowdfunding, software developer community formation, and structural changes.
_______
_______
Big Data:
_
1 exabyte = 1018bytes = 1000 petabytes = 1millionterabytes = 1billiongigabytes
One zettabyte is equal to a thousand exabytes or a billion terabytes.
1000 Exabytes = 1 Zettabyte
1000 Zettabytes = 1 Yottabyte
1000 Yottabytes = 1 Brontobyte
1000 Brontobytes = 1 Geopbyte
_
Total data on common internet:
Humankind has stored more than 295 billion gigabytes (or 295 exabytes) of data since 1986, according to a report based on research by scientists at the University of Southern California in 2011. The sum total of data held by all the big online storage and service companies like Google, Amazon, Microsoft and Facebook is at least 1,200 petabytes between them in 2013. That is 1.2 million terabytes (one terabyte is 1,000 gigabytes).
_
IoT is about data, devices, and connectivity. Data – big and small – is front and center in the IoT world of connected devices. There is clearly a relationship between big data and IoT. The Mauritius conference helps confirm that. Big data is a subset of the IoT discussion. There’s a ton of applications Internet of Things. The Internet of Things, giving all these devices and sensors, creates a lot of data on usage. This is called Big Data. Big Data, in turn, is stored in the cloud. The number of connected devices on the IoT network will be huge. One estimate says that the number will be nearly 40 billion, which is approximately 30 devices for each and every active social network user in the world. That is actually a conservative estimate. Another analyst predicts that “trillions of sensors” will comprise the IoT. The quantity of data being collected and analyzed in and through the IoT will be huge. No one can predict this “enormous data” volume reliably, but we frequently see articles that mention zettabytes, yottabytes, brontobytes, and even as high as geopbytes. For example: it is already true that sensors on a single Boeing aircraft jet engine can generate 20 terabytes of data per hour; the future astronomy optical telescope LSST (Large Synoptic Survey Telescope) will produce about 200 petabytes of data in its survey lifetime; and the future astronomy radio telescope ensemble SKA (Square Kilometer Array) will alone produce several exabytes per day as it senses the changes and behaviors of objects in the Universe. Each of these examples corresponds to one single node out of the billions (or trillions) that will be collecting and delivering data through the IoT. Those are huge “devices”, whereas most devices on the IoT will be small (e.g., your home thermostat, your car tires, your toaster oven, and everything else).
_
Now, considering the fact that millions of devices will be connected and will be generating enormous volumes of data, the efficiency of data collection mechanism is going to be challenged.
1. First, companies need to employ highly efficient data collection mechanisms.
2. Second, companies are going to face unprecedented security issues which are probably not going to be addressed with traditional security mechanisms.
3. Third, not all data generated by the devices will be useful. Companies need to distinguish between useful and redundant data. So, they face huge challenges to improve their data analysis capabilities.
4. Last, IoT Big Data is going to change our day-to-day lives at a fundamental level.
_
Data storage and analytics:
When we talk about IoT, one of the first things that comes to mind is a huge, continuous stream of data hitting companies’ data storage. Data centers must be equipped to handle this additional load of heterogeneous data. In response to this direct impact on big data storage infrastructure, many organizations are moving toward the Platform as a Service (PaaS) model instead of keeping their own storage infrastructure, which would require continuous expansion to handle the load of big data. PaaS is a cloud-based, managed solution that provides scalability, flexibility, compliance, and a sophisticated architecture to store valuable IoT data. Cloud storage options include private, public, and hybrid models. If companies have sensitive data or data that is subject to regulatory compliance requirements that require heightened security, a private cloud model might be the best fit. Otherwise, a public or hybrid model can be chosen as storage for IoT data.
_
One of the most important outcomes of this emerging field is the creation of an unprecedented amount of data. Storage, ownership and expiry of the data become critical issues. The data have to be stored and used intelligently for smart monitoring and actuation. It is important to develop artificial intelligence algorithms which could be centralized or distributed based on the need. Novel fusion algorithms need to be developed to make sense of the data collected. State-of-the-art non-linear, temporal machine learning methods based on evolutionary algorithms, genetic algorithms, neural networks, and other artificial intelligence techniques are necessary to achieve automated decision making. These systems show characteristics such as interoperability, integration and adaptive communications. They also have a modular architecture both in terms of hardware system design as well as software development and are usually very well-suited for IoT applications. More importantly, a centralized infrastructure to support storage and analytics is required. This forms the IoT middleware layer. As of 2012, Cloud based storage solutions are becoming increasingly popular and in the years ahead, Cloud based analytics and visualization platforms are foreseen. The limitations of associated devices in the IoT in terms of storage, network and computing, and the requirements of complex analysis, scalability, and data access, require a technology like Cloud Computing to supplement this field. Moreover, the IoT can generate large amounts of varied data and quickly when there are millions of things feeding data to Cloud Computing.
_
Cloud-IoT:
IoT and cloud computing:
The Internet of Things (IoT) paradigm is based on intelligent and self-configuring nodes (things) interconnected in a dynamic and global network infrastructure. It represents one of the most disruptive technologies which make the ubiquitous and pervasive computing scene. Internet of things is usually refers to the real world and little things limited storage and processing ability, and the important problems about reliability, performance, security and privacy. On the other hand, cloud computing has the almost unlimited capacity of storage and processing power which is a more mature technology at least to a certain extent to solve the problem of most of the Internet of things. Thus, a novel IT paradigm in which Cloud and IoT are two complementary technologies merged together is expected to disrupt both current and future world. It is called Cloud-IoT the new paradigm. The two worlds of Cloud and IoT have seen an independent evolution. However, plenty of common advantage is the result of their integration have been identified in literature, predict the future. On the one hand, the Internet of things can benefit from cloud almost unlimited capacity and resources to make up for the technical constraints. Specifically, cloud computing can provide an effective solution to realize management of Internet services and composition and use of things or data applications. Cloud computing can benefit from the Internet of things, on the other hand, by extending its scope to deal with things in the real world more distributed and dynamic way, and to provide new services on a large number of real life scenarios. The complementary characteristics of cloud computing and Internet of things is attractive because of the different proposals reported in literature and encouraging Cloud-IoT paradigm shown in table below. Essentially, the Cloud acts as intermediate layer between the things and the applications, where it hides all the complexity and the functionalities necessary to implement the latter.
_
The Complementarity and Integration of Issues:
| Internet of Things | Cloud Computing |
| pervasive | ubiquitous |
| real world | virtual resources |
| limited computational | unlimited computational |
| limited storage | unlimited storage |
| point of convergence | service delivery |
| big data source | means to manage big data |
_
_
•IoT applications will need support from a reliable, fast, and agile computing platform.
•IoT devices can overcome lack of Software, Firmware, Memory Storage, Hardware, Data Processing capability through Cloud computing.
•Cloud service models –
1. SaaS (Software as a Service)
2. PaaS (Platform as a Service)
3. IaaS (Infrastructure as a Service)
_
Some things to consider when building an IoT cloud is to include support for
•connecting IoT devices through internet either directly or using gateways (micro-controllers). IoT device can connect to gateway using any communication method like 2G/3G/4G, Bluetooth, Ethernet, ZigBee, Serial/USB, VPN, WI-FI access point, MQTT etc.
•having open adapters to connect with other IoT clouds and facilitating real-time synchronization, and services ready to configure and manage more IoT devices on go, identify and authenticate IoT device and apply/map appropriate service etc. The cloud should also have ready-to-integrate vertical platform layers and support to easily configurable public, private and/or hybrid clouds
•facilitating on-demand or periodic analytics, insight services, and remote management using panels and GUIs
•providing a service creation layer for development/interface community. These services may include Data services, business services, partner services etc.
•scalable yet robust secured compressed data communication layers
_
IoT involves by definition a large amount of information sources. It produces a large amount of unstructured or semi-structured data of the three major characteristics of the data: volume, velocity and variety. Hence this means that the collection, acquisition, processing and visualization, archive, share, search large amounts of data. Providing almost unlimited and on-demand storage capacity at low cost, cloud is the most convenient and cost effective solutions to deal with the data generated by the Internet of things. This integration realizes a new convergence scenario, where new opportunities arise for data aggregation, integration, and sharing with third parties. Once to the cloud, data can be in a uniform way through a standard API, can use the top security protection, direct access from anywhere, and visualization. IoT equipment processing resources are not allowed to field data processing. Collected data are usually aggregated and transmitted to a more powerful node processing is feasible, but not an appropriate scalability challenges to achieve infrastructure. Cloud and its on-demand model of infinite capacity allows appropriate content, make the Internet of things to deal with unprecedented demand complex analysis. Data-driven decision making and prediction algorithms would be possible at low cost and would provide increasing revenues and reduced risks. One of the requirements of the Internet of things is to make the IP access devices communicate through dedicated hardware, and support the communication can be very expensive. Cloud connection provides an effective and cheap solution such as tracking and managing anything at any time from any place to use a custom portal and built-in applications. The integration with the Cloud solves most of these problems also providing additional features such as ease-of-access, ease-of-use, and reduced deployment costs.
_______
Fog computing:
Fog computing extends the Cloud Computing paradigm to the edge of the network, thus enabling a new breed of applications and services. Defining characteristics of the Fog are: a) Low latency and location awareness; b) Wide-spread geographical distribution; c) Mobility; d) Very large number of nodes, e) Predominant role of wireless access, f) Strong presence of streaming and real time applications, g) Heterogeneity. These characteristics make the Fog the appropriate platform for a number of critical Internet of Things (IoT) services and applications, namely, Connected Vehicle, Smart Grid , Smart Cities, and, in general, Wireless Sensors and Actuators Networks (WSANs). Fog computing is a viable alternative to prevent such large burst of data flow through Internet. The edge devices’ computation power can be used to analyse and process data, thus providing easy real time scalability.
______
Computing at edge or cloud:
Collection happens at the edge. Analysis happens at the edge (real-time) or in the cloud (data mining). View/Display happens in the enterprise (dashboards, C2) and exploitation is how you make teh monies. Exploitation can happen anywhere, whether you have a new sensor, actuator, radio, gateway, service, technique or security tool. The problem is that you are going to have so much available data, that if you want to analyze it, and react in real-time, you do not have time to send it to the cloud. For example, a wind turbine at the edge of the field reacts to a sudden unexpected gust of wind. It can send a notice that it has done so “to the cloud”, or it can send it to the other turbines. The first results in sooner-than-expected burned out turbines, the second results in turbines that feather their own blades to protect themselves from the same gust of wind. So computing at edge has advantages of real time action and saving money & time for sending to cloud. On the other hand, cloud has advantage of unlimited data storage and analysis.
_______
Vertical to horizontal IoT:
_
_
As IoT products start rolling out, two different business models have emerged: One is vertical, the other horizontal. It’s anyone’s guess as to which will thrive or if hybrids will arise. In the vertical business model, the IoT device, the gateway (if used), and the cloud-based service are all provided and controlled by the same company. This approach has the advantage for the end-user that there are no compatibility issues to deal with among the various elements, and a single point of contact to deal with if anything goes wrong. The disadvantages are that the end-user is entirely dependent on the vendor for improvements, enhancements, or upgrades to the offering. An IoT home-security system that monitors an empty house for intruders, for instance, has the same hardware as one that monitors an elderly person’s activity so that it can summon aide if the person falls or loses consciousness. But if someone wants a system that will do both, they are dependent on the system vendor to offer those features when dealing with a vertically defined business. Vertical business models can also result in users needing several different systems to achieve a spectrum of tasks, each with its own gateway and cloud operations. In a smart home, for instance, it is easy to end up with separate providers for security, HVAC, and appliance systems. This complicates system management for the end-user. Most of the first IoT offerings to come to market follow this vertical model. That’s not surprising, given that there is as yet little infrastructure in place to support a horizontal business. But that is changing. The motivation behind a horizontal model is to foster rapid growth and innovation in the industry by allowing multiple providers to work with a common framework. The idea is that by making the gateway and cloud resources something that can be assumed to be in place and have known and open functionality, innovators can concentrate their efforts on creating devices and services. Further, by working on a common framework, those devices and services can more easily share information and resources. So, motion detectors and cameras could serve multiple applications instead of only one. To foster this horizontal model, many companies are starting to roll out cloud platforms and gateway hardware that allow multiple users.
_
The paradigm of the Internet-of-Things (IoT) is quickly becoming a reality, with day-to-day applications continuously and unnoticeably emerging in all contexts of our lives. For instance, terms such as Smart Home or Smart Transport have been coined to describe whole categories of products for use in domestic and public transportation environments, many of which are already commercially available. As an example of the latter, smartphone applications that enables us to find and reserve the closest free park space near our workplace, or to monitor the energy consumption of our homes are not only a reality today, but also a window into the future “Smart Life”. These and all other application scenarios of the IoT so-far envisioned and currently addressed have in common the “smartness” concept which tantamount to the IoT concept. While each of such “smart applications” can bring some improvements to the quality-of-life of common citizens in its own right, the fact that they are developed for separated (in the following referred to as “vertical”) scenarios is in contrast to the universal, seamless (“horizontal”) vision of IoT. There are many reasons for the persistence of such a separation, the first of which is technological: the current state-of-the-art (Sota) in terms of wireless technologies for IoT does not include complete solutions capable of meeting all the functional requirements of a truly horizontal IoT. From an architectural point of view, and as far as wireless communication technologies is concerned, the main challenge is inter-operability. The solution to this challenge requires the standardization of a “Protocol Layer”, to stand in between the Transport and Application Layers, so as to enable a smooth integration of the various communication technologies there under. It is no coincidence therefore that this objective has been already incorporated under current standardization efforts of machine-to-machine (M2M) technologies. From an applications point of view, however, the solutions are more diverse, but can still be conceptually unified under the notion that the main challenge therein is how to hand over to devices the ability to make decisions on behalf of users, and to do so securely. Current research effort in M2M is focused on vertical domains. The Smart Life vision requires, however, to move from a mere collection of such vertical scenarios to a seamless, pervasive and ubiquitous horizontal domain. While many commercial products for the Smart Home domain exist today, they typically utilize proprietary or in-compatible technologies e.g. KNX, ZigBee, Wi-Fi, leading to a severe lack of interoperability at all layers, which has prevented their incorporation into the IoT. Fortunately, a good number of these solutions rely on technologies that are currently under consideration by M2M standardization efforts seeking interoperability.
________
________
Are smart phones IoT devices?
One of the most common we see in day to day life are smart phones. Smart phone is essentially an embedded system with a processor at the core having display and keypad. They support wide variety of sensors like Ambient light Sensors, Accelerometer, Gyroscope and so on. They are connected to internet. Smart phones gets IP addresses, can access internet. In other words it virtually fits every description of IoT. So can we call smart phones IoT devices? This doubt was clarified at a keynote event during Sept 2011’s Mobile World Congress in Barcelona by Qualcomm Chairman and CEO Dr. Paul Jacobs. Paul Jacobs talked about how mobile technology could be used to connect non-phone, non-tablet devices called IoT devices and objects to the Internet. In this future where everything is Web-connected, smart phones will serve as the hub, or the remote control, for Internet of Things. So IoT is internet connectivity of smart objects and embedded system other than smart phones which are remote control/access center of IoT.
_
_
The Internet of Things is more complex than the mobile Internet system. If the mobile Internet is 10 billion units, the Internet of Things is 100 billion units. If PCs had two form factors, and mobile computing had tens of form factors, then IoT will have millions of form factors. In addition to Wi-Fi and Cellular, Internet of Things will also include other low-power radios like Bluetooth LE and 802.15.4/g enabling a wide range of applications covering a myriad of environments from indoor to outdoor. This will bring massive choice and diversity – there will not be 100 billion of the same devices. There will be millions of different devices and apps: the requirement for a healthcare sensor is different from those for an air conditioning system; a temperature sensor is different to the controller in an electric motor. All of which are different to the controllers used in cars. Clearly one size will not fit all. To fulfil the potential of the Internet of Things, diversity will be essential.
_
IoT and mobile apps:
When speaking about how mobile apps are typically used today, it’s best to start at the end — that is, the endpoint. In most cases, people are using apps as endpoints — to play games, stream music, locate restaurants, or interact with friends on social media. While apps can serve two purposes — gateway or endpoint — IoT fundamentally requires an endpoint from which to send back data. IoT endpoints, such as connected devices in the home, generally have simpler architectures when compared to mobile devices. These endpoints are capable of monitoring events — like room temperature — before sending back data to services through which trends can be analyzed. A well-known example of mobile app and IoT integration is a Wi-Fi-enabled thermostat. In this case, the thermostat itself is considered the IoT endpoint, and a mobile app can be used as a remote or gateway to control the device. This emerging dynamic between mobile apps and IoT devices has remarkable potential, and as a result, has effectively opened the minds of organizations seeking to harness the full potential of the coming IoT. And, because of the preexistence of mobile-app development within many organizations, developers now have a baseline from which they can build frameworks for the future, freeing them from the traditional HTML web-browser approach.
_
The relationship between IoT as an endpoint and mobile apps as remotes is rather clear, but apps also have the ability to act as sensors, similar to IoT devices. If your brand is thinking about leveraging native operating-system (OS) functionality and using mobile apps as sensors, such apps can be utilized to collect background data before sending it to a server in ways that they — from a technical standpoint — have never been able to do before. One such example would include sending information about a user’s location in the background. This might not qualify as a traditional visit, session, or user interaction, but it can remain an important event along the customer journey, and the data collected could — and should — provide a more personalized user experience. This data can be used to enhance a user’s relationship with the brand. Such mobile app use cases have helped IoT define the relationship between data coming through and the ultimate problem the user is trying to solve. By analyzing the various ways that mobile apps as sensors have helped businesses report, collect, and analyze data, brands already have a head start in the transition to understanding the possibilities of IoT devices. Most of these devices connect to a user interface through an app accessible by smartphone, tablet, or desktop computer. These control points allow users to view their data, perform basic analytics, send updates to social media platforms, or share information with a circle of friends. These devices, along with the apps and cloud storage facilities that store the data, comprise the Internet of Things. The value of cultivating such a network of devices comes from the ability to personalize services, use analytics to detect patterns, send information to remote locations, and motivate users into achieving specific goals.
________
________
IoT devices and technology – classified:
_______
_______
IoT companies:
_
_
Most powerful Internet of Things companies:
The Internet of Things (IoT) is still nascent, but growing quickly. Research firm IDC predicts it will become a $1.46 trillion international market by 2020, up from $700 billion last year. A trillion-dollar market means a lot of companies will want a slice. So who are the leaders of the IoT?
1. Amazon Web Services:
Many expect the cloud will play a big role in IoT, and the biggest cloud provider is Amazon Web Services. The cloud is a natural spot to store huge amounts of data, and Amazon is increasingly offering powerful services to gain insights on that data. In 2015 AWS launched its Internet of Things platform, which uses tools like Kinesis (a real-time streaming service), S3 (the Simple Storage Service), and DynamoDB (the massively-scalable NoSQL database).
2. AT&T
AT&T is banking on its broadband network being a key enabler of IoT. The company has launched M2X, a cloud-based data storage service and Data Flow, a development portal for building applications for the world of IoT. AT&T hopes to have 10 million vehicles connected to its network by 2017, including 1.2 million fleet vehicles and 243,000 shipping containers.
3. Bosch
German conglomerate Bosch is perhaps best known for its automotive parts division, but it also makes products ranging from home appliances to enterprise software. Bosch says its range of products will be connected to the IoT to ease maintenance and monitoring of devices, making it one of the key enablers of IoT. Plus, the company has built an IoT cloud to process all that data.
4. Cisco
Cisco predicts that by 2020, there could be 50 million devices connected to what it calls the Internet of Everything. It’s hoping many of those devices will use the company’s networking equipment to communicate. Cisco has carved out a range of IoT services, from network connectivity (including switching, routing, wireless access and embedded network hardware), to fog computing services (which bring data collection, storage and analysis to the network edge), to data analytics, security, management and automation.
5. Dell
As an enterprise hardware manufacturer, Dell is preparing its infrastructure components for a world of IoT. It’s offering endpoint connectivity for devices plus back-end storage and analytics platforms to manage IoT data. In 2014 Dell opened its IoT Lab in Silicon Valley in partnership with Intel.
6. GE
GE is credited with coining the term the ‘Industrial Internet of Things’ to depict the idea of connecting devices used in manufacturing to the Internet. GE hopes to help facilitate that through its Asset Performance Management platform, which aims to use data and real-time analytics to prevent unplanned downtime. Predix, a cloud-based data and analytics service, is another pillar of GE’s IIoT plans.
7. Google
Google’s IoT ambitions span consumer and enterprise-facing initiatives. Google paid $3.2 billion for smart thermostat maker Nest, which the company could expand to include a whole connected, smart-home system. On the business side, Google says its combination of fiber-optic back-end network, combined with its massive public cloud mean it is in a unique position to serve the needs of IoT.
8. Hitachi Data Systems
HDS, the technology arm of Japanese industrial conglomerate Hitachi, has two important components to take on the IoT market. On the Hitachi side, the company is partnering with Intel to ensure its machine and industrial equipment are connected. On the HDS side, the company is rolling out new cloud-based platforms to collect and analyze IoT data. It’s hoping this combination of industrial hands-on equipment and back-end technical services will make it an IoT powerhouse.
9. Huawei
Chinese telecom/network vendor Huawei made a big push in the IoT market last year by releasing LiteOS, a micro operating system for IoT devices. It joined the Cloud Foundry open source community to help create an IoT application development platform, too. Huawei is taking on the IoT market in Asia and increasingly in the U.S., hoping a world of connected devices will usher in new opportunities for its core networking products.
10. IBM
IBM has been making a big push with its Watson “smart” products and is hoping to inject its cognitive capabilities into its IoT services. The Watson IoT platform combines a cloud-based development and production environment for applications, software and services tailored for specific industries, and cognitive analytics atop it all.
11. Intel
In a world of connected devices, all those gadgets are going to need processor chips. Intel wants to be the company supplying silicon for the Internet of Everything. The company has rolled out a variety of products to serve IoT, from its Quark line that provides low-power computing for small-form factor appliances, to Atom processors that are ideal for rich graphic rendering.
12. Microsoft
Microsoft has rolled out an IoT Suite for its Azure public cloud, which includes an IoT Hub for users to connect, monitor and control devices; a streaming analytics service combined with machine learning; a notification hub for sending messages across IoT devices, and Power BI. To ease customers’ transition to IoT, Microsoft has a handful of preconfigured IoT templates, including one for customers to remotely monitor IoT devices, and another for rolling out predictive maintenance.
13. Oracle
Oracle wants its databases and applications to be the platform its customers use to manage and analyze IoT data. Oracle is building connections for its SQL, NoSQL and Hadoop databases to ingest IoT data and integrate data back into the company’s applications (Oracle Sales cloud, Service Cloud and CRM). Oracle has an IoT service and IoT cloud that prepackage these workflow services into a product.
14. PTC
PTC – a company known for its design modeling software and product lifecycle management (PLM) tools – has become an important IoT company through an aggressive acquisition strategy. PTC bought ThingWorx, an IoT application development platform; Axeda, a cloud service for managing connected devices and processing machine-to-machine data; and Coldlight, a machine learning/artificial intelligence platform for analyzing data.
15. Salesforce.com
While many other companies on this list are building ways for connected devices to impact industrial and commercial operations, Salesforce.com says that the IoT presents a new opportunity for marketers to gain deeper insights into their prospects and customers. Connected devices allow chief marketing officers (CMO) to learn how their products are being evaluated and used, what stage of the process the prospects are in and potentially what factors influence buying behavior. Salesforce.com has introduced its IoT Cloud, powered by its real-time processing engine named Thunder. IoT is not just about connected machines; it’s about connected products and marketing, too.
16. Samsung
Samsung promises to make all of its devices IoT ready by 2020. As one of the largest makers of phones, appliances, televisions and robots – Samsung will be one of the companies leading the charge to connect devices to the Internet. The company is developing a series of ARM chips for its devices, along with APIs that it says will allow its devices to connect to any IoT platform customers want.
17. Siemens
The company perhaps best known for making medical equipment makes a lot of other gadgets too, all of which it says can benefit from being connected to the IoT. Siemens is working to connect its devices, and has partnered with SAP to provide analysis, while also building customer software for what it calls the “Web of Systems.”
18. Qualcomm
Semiconductor company Qualcomm has its fingers in all sorts of IoT initiatives, including helping to start the AllJoyn initiative, which aims to create an open source protocol for IoT devices, to introducing a series of IoT-optimized chips named SnapDragon, to offering a variety of connectivity services and platforms.
________
________
Trends, expansion and growth of IoT:
_
Growth of connected devices:
The Internet of Things (IoT) is the interconnection of uniquely identifiable embedded computing devices within the existing Internet infrastructure. In 2014, Gartner predicted that by 2020 there would be 25 billion connected devices. Cisco predicted that number would be closer to 50 billion, and Morgan Stanley thinks 75 billion. ABI Research predicted that 30 billion devices on the Internet of Things by 2020. The economic impact and benefits of the IoT will be huge. Gartner predicts that the aggregated value and economic benefit of the IoT will exceed $1.9 trillion in the year 2020 alone. With advancements in technology, IoT is growing at a rapid pace. According to IDC, the worldwide IoT market will grow from $655.8 billion in 2014 to $1.7 trillion in 2020. As per Intel, Cities will spend $41 trillion in the next 20 years on infrastructure upgrades for IoT. According to Mckinsey, wide deployment of IoT technologies in the auto industry could save $100 billion annually in accident reductions. IoT has the potential to be a disruptive technology. Traditional consumer manufacturers may not be the most obvious long-term beneficiaries and companies that are not currently in the consumer goods market could shape the way this develops. Google’s $3.2bn purchase earlier this year of Nest, which manufactures connected thermostats, is an example of this.
_
World population vis-à-vis population of connected devices:
The rapid growth of the IoT is pictured in the figure above, comparing the number of devices on the Internet to the number of people on the Internet. Connected devices surpassed connected people in 2008. Cisco estimates that by 2020 there will be 50 billion connected devices, 7 times the world’s population. Around one-third of them will be computers, smartphones, tablets, and TVs. The remaining two-thirds will be other kinds of “things”: sensors, actuators, and newly invented intelligent devices that monitor, control, analyse, and optimize our world. Similarly, the Connected Life initiative sponsored by the GSMA (GSM Association, an industry-association for worldwide mobile operators) found that in 2011, there were 9 billion total Internet-connected devices (compared to the total human population of less than 7 billion), two-thirds (6 billion) of which were mobile, and estimates that in 2020, there will be 24 billion total Internet-connected devices, 12 billion mobile. Moreover, these 24 billion Internet-connected devices are estimated to have an economic impact of over $4.5 trillion in 2020.
_
The Internet of Things (IoT) has been called the next Industrial Revolution — it will change the way all businesses, governments, and consumers interact with the physical world. For more than two years, BI Intelligence has closely tracked the growth of the IoT. Specifically, they analysed how the IoT ecosystem enables entities (i.e. consumers, businesses, and governments) to connect to, and control, their IoT devices in 16 environments, including manufacturing, the connected home, transportation, and agriculture. In a new report from BI Intelligence, all of the components of the IoT ecosystem, including its devices, analytics, networks, and security are discussed. It also provide estimates and forecasts on the burgeoning IoT market, including device growth, amount invested, and potential return on investment. Here are some key points from the report:
•In total, there will be 34 billion devices connected to the internet by 2020, up from 10 billion in 2015. IoT devices will account for 24 billion, while traditional computing devices (e.g. smartphones, tablets, smartwatches, etc.) will comprise 10 billion.
•Nearly $6 trillion will be spent on IoT solutions over the next five years.
•Businesses will be the top adopter of IoT solutions. They see three ways the IoT can improve their bottom line by 1) lowering operating costs; 2) increasing productivity; and 3) expanding to new markets or developing new product offerings.
•Governments are focused on increasing productivity, decreasing costs, and improving their citizens’ quality of life and they will be the second-largest adopters of IoT ecosystems.
•Consumers will lag behind businesses and governments in IoT adoption. Still, they will purchase a massive number of devices and invest a significant amount of money in IoT ecosystems.
_
Figure below shows list of countries by IoT devices online:
South Korea tops the list while India is at bottom.
_
65% of enterprises are already using internet of things technology:
The majority of enterprises have already deployed internet of things solutions, according to a new report from 451 Research, which saw the greatest adoption coming from utilities and manufacturers. Taking stock of the source of enterprise IoT data, 451 found 51% comes from data center information technology equipment, 34% from camera/surveillance equipment, 33% from data center facilities equipment, and 29% from smartphones and other end-user devices. In terms of how the data is used to improve enterprise operations, researchers found 66% of IoT deployments reduce risk, 33% facilitate developing new or enhance existing products or services and 21% for enhancing customer segmenting. The term internet of things has proliferated rapidly and taken on different meanings depending on the audience. As is reflected in this survey data, these connected endpoint scenarios are both old and new. They vary immensely from traditional use cases such as IP connected cameras, building automation, warehouse automation and telematics to emerging industrial use cases such as crop monitoring and remote patient monitoring. Organizations are both enhancing their already connected endpoints with greater capabilities as well as connecting new objects with sensors and circuitry to derive net new value for the business.
_
The figure below shows growth of smart product sales:
_
Netherlands gets world’s first nationwide Internet of Things:
Connecting everyday objects to networks, allowing them to send and receive data, is widely seen as the next major evolution of the internet and one that may transform how many businesses operate and people live. Dutch telecoms group KPN said on June 30, 2016 that The Netherlands had become the first country in the world to implement a nationwide long range (LoRa) network for the Internet of Things (IoT). LoRa means Long-range Wireless IoT Protocol. LoRa chips transmit in the sub-gigahertz spectrum (109MHz, 433MHz, 866MHz, 915MHz), which is an unlicensed band that has less interference than others (like the 2.4 GHz range used by Wi-Fi, Bluetooth, and other protocols). At those frequencies, signals penetrate obstacles and travel long distances while drawing relatively little power — ideal for many IoT devices, which are often constrained by battery life. The rollout of LoRa mobile communications network is critical to connect objects as many may not be able to link up with home or work wi-fi networks to gain internet access. This makes The Netherlands the first country in the world to have a nationwide LoRa network for Internet of Things application. The LoRa network is complementary to KPN’s networks for the 2G, 3G, and 4G phones. KPN has already reached deals to connect some 1.5 million objects, a number which should steadily grow now that the LoRa network is available across the country.
________
________
Challenges and obstacles to IoT:
The IoT promises to bring new problems and concerns, some technical, and others social or environmental. So far, most of these new problems and concerns are barely acknowledged, although many are already starting to appear: While the initial generation of IoT solutions have focused on frameworks that enable communication with smart sensors, the new generation of platforms that enable backend capabilities for IoT solutions is about to emerge. But there are many obstacles to adoption; including the lack of differentiated platforms, out-dated regulatory requirements, unclear business models, and most important no killer applications identified by businesses and consumers yet. Some of the major IoT challenges are privacy, data storage, smart sensing instrumentation and measurements, data analytics, and visualization of real-time data in the IoT enabled application. Apart from having robust cloud computing facilities, the challenges related to WSN such as the optimal number of sensing devices required for monitoring applications, security of the sensor data, protocols to be considered for low power consumption, optimum data compression, and Quality of Service (QoS) persist in the design and deployment of the IoT framework in the present business situation. In the near future, Smart Things should be easily deployed in the form of plug-n-play in any context using the IoT framework. The internetworking mechanisms of Smart Things in the IoT framework are crucial with respect to the standardization of communication protocols. It should be mentioned that to safeguard everything in the future, electrical power, computing systems and the internet should be ensured as a fail-safe operation, and this may be a huge challenge. Additionally, changing dynamics in the global economy can look into the issues related to security and misuse of data/information, and formulate appropriate protocols.
_
The development of the Internet of Things would critically depend on progress in machine-to-machine interfaces and protocols of electronic communication, embedded systems, wireless communication, RFID, sensors, actuators, location technology, energy harvesting techniques, and software. In IoT each of the networked object need to have an Identity. Managing a globally integratable unified ID with mechanisms for naming, addressing and discovery are of paramount importance. Governance, standardisation and interoperability are absolute necessities for things to be able to communicate with each other. Communication protocols and standards must be scalable, power efficient, secure and fully global. Scale will be such that traditional internet management approach will not work efficiently. This will demand autonomic features such as self-organisation and self-management built into the devices. While RFID is one of the sensors, there are numerous sensors in the market with different technologies, packages, specifications and it is major contributor to the cost of the whole solution. Large scale applications can standardise some of the sensors to reduce the cost. Robustness is one of the key requirement where the smart devices are able withstand any kind of harsh environment and harvest energy from their surroundings. Efficient implementation of energy neutral platforms with non-polluting energy sources is of great social value. Reducing carbon footprint by eliminating or minimizing the use of batteries is an important aspect of this. Another central issue of the Internet of Things will be related to trust, privacy and security. Here there is also a concern regarding the ownership of data and mechanisms of managing it dynamically. For example the medical data of a patient need to be accessed by the doctor to whom the patient gives consent and this permission may be revoked once the consultation is over. But what happens to the data which is already downloaded by the doctor. Who is the owner of the data once the patient is dead? Creation of awareness among public regarding these technologies is very important for its success in the market. This can be more convincing with some real-life implementations and help in building customer confidence.
___
Major Challenges to IoT:
1. Cost
2. Big Data Explosion
3. Countless components
4. Security & Privacy
5. Advanced Internet Protocol
6. Power efficiency
7. Lack of Standards
__
Many issues have kept IoT from becoming truly a part of our day like smartphones and the Internet. We need to understand that for IoT to reach its full potential, most of the “things” we will need to connect will be small, low-cost and most important – battery operated. Until recently, the IoT technology for these mass markets used connected sensors that are simply too expensive for most uses. Then, there were issues with battery life (some of these devices require 10-15 years of life on a single charge of a battery), what standards will be used (i.e. Bluetooth® vs. Wi-Fi vs. Ethernet) and protocols (how IoT connected devices speak to the cloud). But by far the biggest challenge keeping IoT from being everywhere is simplicity.
_
Biggest Challenges for the Internet of Things (IoT)
____
Cost:
It’s one thing to embed a sensor in a new consumer product; it’s another thing to place them on items and structures that are already widely dispersed throughout the world. One idea for the Internet of Things is to place sensors on roads, traffic lights, utility grids, and buildings, but doing so represents an expensive venture. Many companies, while optimistic about the potential of the IoT, have yet to be convinced it’s an investment worth making on such a large scale. Progress has been made concerning the expenses of the IoT, particularly in the creation of cheaper sensors, but more progress is needed before organizations truly embrace using them in everything. Until then, the full implementation of the Internet of Things will likely be delayed.
_
Consumer Awareness:
While businesses may talk excitedly about the Internet of Things, consumers are largely unaware of it. In a recent survey of 2,000 people, 87% of consumers said they had never even heard of the IoT. While hearing about the Internet of Things doesn’t necessarily signify a consumer would not use an item connected to the IoT, the survey results show a lack of awareness and understanding about what can be gained from it. If this lack of knowledge about the IoT leads to lack of interest, a major driving force for widespread adoption will be missing. Having said that, there is a lot of interest in wearable technology, which could be a gateway for more connected items. As a result, many companies are focusing on wearable tech. Even so, other uses of the Internet of Things may take several years to really catch on. These and many other hurdles represent some significant challenges businesses will have to contend with over the next few years, but many view it as a challenge worth facing. The number of developers specifically devoted to the Internet of Things is expected to increase to 4.5 million by 2020, a big jump from the 300,000 currently doing so. With more attention being paid to the IoT, solutions will likely come, and with them new innovations and creative applications. Consumers can expect a much more connected life as a greater understanding of the IoT is put into practice.
_
Big Data:
Handling and maintenance of large volume data along with the investment needed for storing and maintaining such data would be very high and thus it is among the big challenges for the Internet of Things. IT administrators that are already tasked with keeping the storage centers running, will also have to figure out how to store, protect and make all the incoming data accessible. If, as Gartner, estimated, storage servers are only being used to between 30 and 50 percent of capacity, the physical capabilities are there. Managing them, however, is an entirely different problem.
_
Internet of Things may strangle Enterprise Bandwidth:
In a recent InformationWeek survey on next-generation WANs, 68% of respondents said demand for WAN bandwidth will increase over the next year, but only 15% said they were expanding capacity. The bandwidth gap — the difference between required and available bandwidth — is large and growing. This limited bandwidth will stifle IT convergence. In some parts of the world, companies can buy a lot of bandwidth. In other regions, the capacity does not yet exist. The limitations in these regions will prevent some global companies from deploying bandwidth-hungry enterprise IT strategies worldwide. In the coming decade, the IoT will cause the bandwidth gap to balloon out of control. Enterprises will see enormous amounts of traffic coming from a massive number of sources. In addition to more bandwidth, enterprises need to plan for bandwidth optimization and stricter traffic management. IT departments will need to ensure they have mechanisms that prioritize Internet and intranet access to business-critical applications and devices first.
_
Power Consumption:
Things typically move around and are not connected to a power supply, so their smartness needs to be powered from a self-sufficient energy source. Although passive RFID transponders do not need their own energy source, their functionality and communications range are very limited. In many scenarios, batteries and power packs are problematic due to their size and weight, and especially because of their maintenance requirements. Unfortunately, battery technology is making relatively slow progress, and “energy harvesting”, i.e. generating electricity from the environment (using temperature differences, vibrations, air currents, light, etc.), is not yet powerful enough to meet the energy requirements of current electronic systems in many application scenarios. For IoT to reach its full potential, sensors will need to be self-sustaining. Imagine changing batteries in billions of devices deployed across the planet and even into space. Obviously, this isn’t possible. What’s needed is a way for sensors to generate electricity from environmental elements such as vibrations, light, and airflow. Hopes are pinned on future low-power processors and communications units for embedded systems that can function with significantly less energy. Energy saving is a factor not only in hardware and system architecture, but also in software, for example the implementation of protocol stacks, where every single transmission byte will have to justify its existence. There are already some battery-free wireless sensors that can transmit their readings a distance of a few meters. Like RFID systems, they obtain the power they require either remotely or from the measuring process itself, for example by using piezoelectric or pyroelectric materials for pressure and temperature measurements. Koomey’s Law says since the 1950s, the amount of electricity needed to do a computation halves every 18 months. So for fairly simple computational processes you need in wireless sensors, it is gradually becoming possible to have a small battery or in some cases an RFID tag with no battery. Most RFID tags get power from the radio waves talking to them. Batteryless computing and power-less computing is something we’ll see more and more of. This leads us to disposable computing and ubiquitous computing. In a significant breakthrough, scientists announced a commercially viable nanogenerator—a flexible chip that uses body movements such as the pinch of a finger to generate electricity. Several years ago, Gartner predicted that 4.9 billion smart devices would be used by 2015 — an increase of thirty percent from 2030. By 2020, Gartner estimated that the number of smart devices would reach 25 billion by 2020, an increase of 100% each year. Along with this boost will come an increase in energy demands comparable to the one created by the Internet. In 2012, the data centers that powered the Internet were estimated to require 30 billion watts of electricity a year — enough to power a medium-sized town, and the Internet of Things is likely to require even more. Even with improved batteries and green sources like solar and wind, just meeting the demand will be difficult. However, add issues like the wasted energy and pollutants, and powering the IoT could become a major social problem in its own right within the next decade.
_
Internet Availability:
The Internet of Things sounds good in principle, giving consumers unparalleled convenience and access to the latest technology, but there is one requirement that can’t be ignored: the internet. Without an actual internet connection, the IoT can’t function. While that may not be a problem for the majority of people, there are still many places in the world without an internet connection. Many companies, including Google, are trying to rectify this issue, but any solutions are still years away. Even countries that do have high connectivity to the internet, like the United States, will often have spots where that connection is spotty or even non-existent. Worldwide internet connections have to happen for the IoT to become a fully functioning reality.
_
Backend connectivity:
The old expression ‘garbage in, garbage out’ is all the more relevant with the Internet of Things. It’s now easier than ever to gather all manner of personal and environmental data, but people won’t engage with that information unless it’s both meaningful and useful. Creating thoughtful services that collect and then display the right data, at the right time, and in a way that users can understand and (crucially) act upon, depends a great deal on the design of your API.
_
Interoperability:
Since the world of physical things is extremely diverse, in an Internet of Things each type of smart object is likely to have different information, processing and communication capabilities. Different smart objects would also be subjected to very different conditions such as the energy available and the communications bandwidth required. However, to facilitate communication and cooperation, common practices and standards are required. This is particularly important with regard to object addresses. These should comply with a standardized schema if at all possible, along the lines of the IP standard used in the conventional Internet domain. Internet of Things is inclusive of integration of various layers of software’s, hardware’s and other system in order to facilitate the service of connecting devices to the cloud. There are also set standards and protocols along with various number of Application Program Interface (API) testing that prove to be a challenge for the Internet of Things. Interoperability is a persistent problem. While it may be trivial to connect one ‘hero’ device to another, it’s still hard to make meaningful connections between more random devices. This is solvable if we can agree on standards instead of constantly aiming to disrupt, define or own aspects of this growing ecosystem. The IoT has the potential to redefine our world and could help solve some of its most pressing problems but for that to happen, we’ll need to work together. The ‘things’ need a common language to communicate. The real value of the internet of things lies on the ability of devices to communicate each other, which requires a common language for communication. However, there is not a standardized protocol to enable the communication of the devices from different brands. For instance, wearable health monitor of your grandmother will need to contact your mobile phone, hospital’s emergency department and her house’s door lock in case of an emergency. Your Siemens alarm clock should be able to communicate with your Bosch coffee maker, Philips toaster and Vaillant boiler when you wake up.
_
Waste Disposal:
Thanks to planned obsolescence, fifty million tons of e-waste — the disposal of computers, phones, and peripherals — are produced each year in the United States alone. As countries like China and India continue to industrialize, and the Internet of Things comes online, the problem is only going to continue. Meanwhile, less than twenty percent of e-waste is recycled, and despite the Basel Convention, much of the rest continues to be shipped overseas to developing nations where it is salvaged in unsafe working conditions. Smart devices did not originate e-waste, but, assuming they are built the way that computers are today, with a lifespan of only a few years, they seem likely to double or triple the problem.
_
Obstacles faced in deploying Internet of Things (IoT) technologies:
When considering an IoT-based initiative, companies have a number of concerns. At the top of the list is ensuring privacy and regulatory compliance (cited by 46 percent of respondents). This is not surprising given the massive volumes of data involved and the increased concern about privacy—and both factors likely explain for why healthcare is one of the leading areas of interest. Most current legislation and industry regulation predates the widespread use of IoT, leaving companies to interpret how rules affect their initiative and what the public will accept as well as addressing the security needs that go with any new IT project. Another challenge is acquiring the skills needed to turn the wealth of data generated by IoT-based projects into actionable intelligence (cited by 39 percent) and managing the growing volumes of data (35 percent). To fully leverage the potential benefits of IoT, organizations will need to change the way they develop products and how they interact with customers. This can present multiple challenges, such as the need to have customer service processes and people in place to address the feedback they receive from connected products. They also need to have mechanisms in place to provide insight into new product development and customer support. Some of these issues can be addressed automatically through product alert systems.
______
Security and personal privacy:
Business and homes security devices are connected to Internet of Things and cloud has many confidential and sensitive information of business and individuals stored which is turning to point of attraction for hackers. Management of Security challenge for the Internet of Things needs a smart solution for raising the level of security with respect to hardware, software and connectivity. In addition to the security and protection aspects of the Internet with which we are all familiar (such as communications confidentiality, the authenticity and trustworthiness of communication partners, and message integrity), other requirements would also be important in an Internet of Things. We might want to give things only selective access to certain services, or prevent them from communicating with other things at certain times or in an uncontrolled manner; and business transactions involving smart objects would need to be protected from competitors’ prying eyes.
_
_
Personal privacy concerns:
In the wake of major security breaches at Home Depot and Target, along with the recent iCloud celebrity photo scandal, privacy and security are clearly on the minds of businesses and individuals. For now, the IoT only appears to raise those concerns exponentially. When everything from a toaster to a shirt is connected to the web, what does that mean for personal privacy and sensitive data? Companies will need to show they can protect customer information if consumers will ever trust wearing shoes that keep track of where they go and how many steps they take. Potentially, the Internet of Things is a wealth of information about those who use it. Smart phones can already be tracked, but smart devices point to a future where governments supplement census information with the output of smart devices, and manufacturers harvest information about your habits so efficiently that they make Facebook’s insights into your interests and buying habits seem vague. Imagine, too, being stalked by government agencies through your smart devices, or your devices being used against you in a court of law. These are — probably — nightmare scenarios. All the same, you can expect the Internet of Things to produce dozens of legal precedents and class action suits as countries debate just what rights to privacy the users of smart devices retain and which they forfeit. The information being transferred becomes prone to the access by government agencies, data collectors and hackers. This might not only intervene with the privacy of the concerned individual, but also pose a security threat to the same. The personal information might get passed to the non-intended recipient, which might get misused and eventually cause security breach. After all, no one really likes to get watched all the time. In this case, network security devices such as network guards and firewalls, are essential to meet the security requirement. The adoption of technology specifically designed to prevent information leakage is also necessary.
_
A research team of the National Science Foundation and University of Arkansas at Little Rock discovered that the privacy of households using smart home devices could be compromised by analyzing network traffic. The American Civil Liberties Union (ACLU) expressed concern regarding the ability of IoT to erode people’s control over their own lives. The ACLU wrote that “There’s simply no way to forecast how these immense powers – disproportionately accumulating in the hands of corporations seeking financial advantage and governments craving ever more control – will be used. Chances are Big Data and the Internet of Things will make it harder for us to control our own lives, as we grow increasingly transparent to powerful corporations and government institutions that are becoming more opaque to us.”
_____
Security concerns:
_
Concerns have been raised that the internet of things is being developed rapidly without appropriate consideration of the profound security challenges involved and the regulatory changes that might be necessary. According to the BI (Business Insider) Intelligence Survey conducted in the last quarter of 2014, 39% of the respondents said that security is the biggest concern in adopting internet-of-things technology. In particular, as the internet of things spreads widely, cyber-attacks are likely to become an increasingly physical (rather than simply virtual) threat. In a January 2014 article in Forbes, cybersecurity columnist Joseph Steinberg listed many Internet-connected appliances that can already “spy on people in their own homes” including televisions, kitchen appliances, cameras, and thermostats. Computer-controlled devices in automobiles such as brakes, engine, locks, hood and truck releases, horn, heat, and dashboard have been shown to be vulnerable to attackers who have access to the onboard network. In some cases, vehicle computer systems are internet-connected, allowing them to be exploited remotely. By 2008 security researchers had shown the ability to remotely control pacemakers without authority. Later hackers demonstrated remote control of insulin pumps and implantable cardioverter defibrillators. David Pogue wrote that some recently published reports about hackers remotely controlling certain functions of automobiles were not as serious as one might otherwise guess because of various mitigating circumstances; such as the bug that allowed the hack having been fixed before the report was published, or that the hack required security researchers having physical access to the car prior to the hack to prepare for it. The U.S. National Intelligence Council in an unclassified report maintains that it would be hard to deny “access to networks of sensors and remotely-controlled objects by enemies of the United States, criminals, and mischief makers… An open market for aggregated sensor data could serve the interests of commerce and security no less than it helps criminals and spies identify vulnerable targets. Thus, massively parallel sensor fusion may undermine social cohesion, if it proves to be fundamentally incompatible with Fourth-Amendment guarantees against unreasonable search.” In general, the intelligence community views internet of things as a rich source of data. As a response to increasing concerns over security, the Internet of Things Security Foundation (IoTSF) was launched on 23 September 2015. IoTSF has a mission to secure the internet of things by promoting knowledge and best practice. Its founding board is made from technology providers and telecommunications companies including BT, Vodafone, Imagination Technologies and Pen Test Partners.
__
U.S. Federal Trade Commission chairwoman, Edith Ramirez, addressed the Consumer Electronics Show in Las Vegas warning that embedding sensors into everyday devices, and letting them record what we do, could pose a massive security risk.
Ramirez outlined three key challenges for the future of IoT:
•Ubiquitous data collection.
•Potential for unexpected uses of consumer data.
•Heightened security risks.
She urged companies to enhance privacy and built secure IoT devices by adopting a security-focused approach, reducing the amount of data collected by IoT devices, and increasing transparency and providing consumers with a choice to opt-out of data collection. Ramirez went on to say that developers of IoT devices have not spent time thinking about how to secure their devices and services from cyber-attacks. The Internet is still not secure, so we can’t expect IoT to be secure, either. However, security is constantly evolving to meet new challenges, we’ve seen it before, and we’ll see it again, with IoT and subsequent connected technologies.
_____
The Internet of Things Top 10 Project conducted by the Open Web Application Security Project (OWASP) names the top 10 security challenges facing the IoT and its related devices as:
1. Unsecured interfaces with the Web.
2. Weak protocols for authentication and authorisation.
3. Poor security for network services.
4. Lack of encryption for data in transit.
5. Concerns with confidentiality and privacy, due to data recording and tracking.
6. Unsecured interfaces with cloud-based resources and infrastructure.
7. Poorly secured mobile apps and interfaces.
8. Badly configured and unprotected network resources.
9. Vulnerabilities and glitches with software and firmware.
10. Inadequate measures to ensure physical security of devices and users.
____
Mauritius Conference of Data Protection and Privacy Commissioners 2014:
In October 2014, representatives from the private sector and academia came together in Mauritius for the 36th International Conference of Data Protection and Privacy Commissioners. The purpose was to discuss both the positive and negative impact of big data and IoT in our daily lives, and the objective was to establish principles and recommendations on how to reduce the risks associated with collecting and using data in this big data-IoT era. The observations and conclusions of the conference were captured in two documents: the Mauritius Resolution on Big Data and the Mauritius Declaration on the Internet of Things. Both documents acknowledge that IoT’s connected devices coupled with big data can make our lives easier, but there are still important concerns about individuals’ privacy and civil rights. Here’s a summary of both documents:
_
Mauritius Resolution on Big Data:
•Implement privacy by design.
•Be transparent about what data is collected, how data is processed, for what purposes data will be used, and whether data will be distributed to third parties.
•Define the purpose of collection at the time of collection and, at all times, limit use of the data to the defined purpose.
•Obtain consent.
•Collect and store only the amount of data necessary for the intended lawful purpose.
•Allow individuals access to data maintained about them, information on the source of the data, key inputs into their profile, and any algorithms used to develop their profile.
•Allow individuals to correct and control their information.
•Conduct a privacy impact assessment.
•Consider data anonymization.
•Limit and carefully control access to personal data.
•Conduct regular reviews to verify if results from profiling are “responsible, fair and ethical and compatible with and proportionate to the purpose for which the profiles are being used.”
•Allow for manual assessments of any algorithmic profiling outcomes with “significant effects to individuals.”
_
Mauritius Declaration on the Internet of Things:
•Self-determination is an inalienable right for all human beings.
•Data obtained from connected devices is “high in quantity, quality and sensitivity” and, as such, “should be regarded and treated as personal data.”
•Those offering connected devices “should be clear about what data they collect, for what purposes and how long this data is retained.”
•Privacy by design should become a key selling point of innovative technologies.
•Data should be processed locally, on the connected device itself. Where it is not possible to process data locally, companies should ensure end-to-end encryption.
•Data protection and privacy authorities should seek appropriate enforcement action when the law has been breached.
•All actors in the internet of things ecosystem “should engage in a strong, active and constructive debate” on the implications of the internet of things and the choices to be made.
_______
______
Applications of IoT:
The ability to network embedded devices with limited CPU, memory and power resources means that IoT finds applications in nearly every field. Such systems could be in charge of collecting information in settings ranging from natural ecosystems to buildings and factories, thereby finding applications in fields of environmental sensing and urban planning. On the other hand, IoT systems could also be responsible for performing actions, not just sensing things. Intelligent shopping systems, for example, could monitor specific users’ purchasing habits in a store by tracking their specific mobile phones. These users could then be provided with special offers on their favorite products, or even location of items that they need, which their fridge has automatically conveyed to the phone. Additional examples of sensing and actuating are reflected in applications that deal with heat, electricity and energy management, as well as cruise-assisting transportation systems. Other applications that the internet of things can provide is enabling extended home security features and home automation. The concept of an “internet of living things” has been proposed to describe networks of biological sensors that could use cloud-based analyses to allow users to study DNA or other molecules. All these advances add to the numerous list of IoT applications. Now with IoT, you can control the electrical devices installed in your house while you are sorting out your files in office. Your water will be warm as soon as you get up in the morning for the shower. All credit goes to smart devices which make up the smart home. The IoT products and solutions in each of these markets have different characteristics. Everything connected with the help of Internet. However, the application of the IoT is not only restricted to these areas. Other specialized use cases of the IoT may also exist. An overview of some of the most prominent application areas is provided here.
__
The IoT landscape:
The IoT is a network of Things, which are anything that can be connected in some form to the Internet. From a box of oranges with an RFID tag, to a smart city, and to every Thing in between, all these digitally augmented objects make up the IoT.
_
According to their 2010 book entitled “Vision and Challenges for Realizing the Internet of Things”, the author identified and discussed nearly twenty areas where the IoT is being applied or will be applied in the very near future.
•Aerospace and aviation (systems status monitoring, green operations)
•Automotive (systems status monitoring, V2V and V2I communication)
•Telecommunications
•Intelligent Buildings (automatic energy metering/ home automation/ wireless monitoring)
•Medical Technology, Healthcare, (personal area networks, monitoring of parameters, positioning, real time location systems)
•Independent Living (wellness, mobility, monitoring of an aging population)
•Pharmaceutical
•Retail, Logistics, Supply Chain Management
•Manufacturing, Product Lifecycle Management (from cradle to grave)
•Processing industries – Oil and Gas
•Safety, Security and Privacy
•Environment Monitoring
•People and Goods Transportation
•Food traceability
•Agriculture and Breeding
•Media, entertainment and Ticketing
•Recycling
This list is far from exhaustive and the potential applications are nearly limitless.
_____
____
IoT applications fall in two broad categories: first, information and analysis and, second, automation and control.
Information and analysis:
As the new networks link data from products, company assets, or the operating environment, they will generate better information and analysis, which can enhance decision making significantly. Some organizations are starting to deploy these applications in targeted areas, while more radical and demanding uses are still in the conceptual or experimental stages.
Automation and control:
Making data the basis for automation and control means converting the data and analysis collected through the Internet of Things into instructions that feedback through the network to actuators that in turn modify processes. Closing the loop from data to automated applications can raise productivity, as systems that adjust automatically to complex situations make many human interventions unnecessary. Early adopters are ushering in relatively basic applications that provide a fairly immediate payoff. Advanced automated systems will be adopted by organizations as these technologies develop further.
______
To the public, IoT currently appears to be a mixture of smart home applications, wearables and an industrial IoT component. But actually it has the potential to have a much wider reach. When the connected world becomes reality, the Internet of Things will transform nearly all major segments – from homes to hospitals and from cars to cities. Today’s major applications include:
• Smart home
Smart Home or “Home automation” describes the connectivity inside our homes. It includes thermostats, smoke detectors, lightbulbs, appliances, entertainment systems, windows, door locks, and much more. Popular companies include Nest, Apple, Philips, and Belkin.
• Wearables
Whether it be the Jawbone Up, the Fitbit Flex, or the Apple Smartwatch – wearables make up a large part of the consumer facing Internet of Things applications.
• Smart City
Smart city spans a wide variety of use cases, from traffic management to water distribution, to waste management, urban security and environmental monitoring. Smart City solutions promise to alleviate real pains of people living in cities these days. Like solving traffic congestion problems, reducing noise and pollution and helping to make cities safer.
• Smart grids
A future smart grid promises to use information about the behaviors of electricity suppliers and consumers in an automated fashion to improve the efficiency, reliability, and economics of electricity.
• Industrial internet
Many market researches such as Gartner or Cisco see the industrial internet as the IoT concept with the highest overall potential. Applications among others include smart factories or connected industrial equipment. In 2014 GE reported roughly $1bn revenue with Industrial Internet products.
• Connected car
The battle is on for the car of the future. Whether it is self-driving or just driver-assisted: Connectivity with other cars, mapping services, or traffic control will play a part. Next generation in-car entertainment systems and remote monitoring are also interesting concepts to watch. And it is not only large auto-makers that play a role: Google, Microsoft, and Apple have all announced connected car platforms.
• Connected Health (Digital health/Tele-health/Tele-medicine)
The concept of a connected health care system and smart medical devices bears enormous potential, not just for companies also for the well-being of people in general: New kinds of real-time health monitoring and improved medical decision-making based on large sets of patient data are some of the envisioned benefits.
• Smart retail
Proximity-based advertising, In-store shopping behavior measurement and intelligent payment solutions are some of the IoT concepts of Smart Retail.
• Smart supply chain
Supply chains are getting smarter. Solutions for tracking goods while they are on the road, or getting suppliers to exchange inventory information are some of the Supply chain applications as part of the Internet of Things.
• Smart farming
The remoteness of farming operations and the large number of livestock that could be monitored makes farming an interesting case for the Internet of Things.
The Internet of Things is also expected to change business models in baking, insurance, and government for example. These use cases, however, are not yet as advanced as the business cases listed above.
______
______
______
Potential IoT applications identified by different focus groups:
| Citizens | |
| Healthcare | Triage, patient monitoring, personnel monitoring, disease spread modelling and containment—real-time health status and predictive information to assist practitioners in the field, or policy decisions in pandemic scenarios |
| Emergency services, defence | Remote personnel monitoring (health, location); resource management and distribution, response planning; sensors built into building infrastructure to guide first responders in emergencies or disaster scenarios |
| Crowd monitoring | Crowd flow monitoring for emergency management; efficient use of public and retail spaces; workflow in commercial environments |
| Transport | |
| Traffic management | Intelligent transportation through real-time traffic information and path optimization |
| Infrastructure monitoring | Sensors built into infrastructure to monitor structural fatigue and other maintenance; accident monitoring for incident management and emergency response coordination |
| Services | |
| Water | Water quality, leakage, usage, distribution, waste management |
| Building management | Temperature, humidity control, activity monitoring for energy usage management, DD heating, Ventilation and Air Conditioning (HVAC) |
| Environment | Air pollution, noise monitoring, waterways, industry monitoring |
________
________
Smart application domains:
| Smart home/office | Smart retail | Smart city | Smart agriculture/forest | Smart water | Smart transportation | |
| Network size | Small | Small | Medium | Medium/large | Large | Large |
| Users | Very few, family members | Few, community level | Many, policy makers, general public | Few, landowners, policy makers | Few, government | Large, general public |
| Energy | Rechargeable battery | Rechargeable battery | Rechargeable battery, energy harvesting | Energy harvesting | Energy harvesting | Rechargeable battery, Energy harvesting |
| Internet connectivity | Wifi, 3G, 4G LTE backbone | Wifi, 3G, 4G LTE backbone | Wifi, 3G, 4G LTE backbone | Wifi, satellite communication | Satellite communication, microwave links | Wifi, satellite communication |
| Data management | Local server | Local server | Shared server | Local server, shared server | Shared server | Shared server |
| IoT devices | RFID, WSN | RFID, WSN | RFID, WSN | WSN | Single sensors | RFID, WSN, single sensors |
| Bandwidth requirement | Small | Small | Large | Medium | Medium | Medium/large |
| Example testbeds | Aware home | SAP future retail center | Smart Santander, citySense | SiSViA | GBROOS, SEMAT | A few trial implementations |
__________
__________
IoT applications in detail:
_
Smart home:
In simple words a smart home is the one in which the devices have the capability to communicate with each other as well as to their intangible environment. A smart home gives owner the capability to customize and control home environment for increased security and efficient energy management. With the use IoT network protocols, devices in the home are connected to the home network and are accessible directly, over the home network, and even remotely from across the world. These connected home devices are able to coordinate energy usage, consumer convenience, and possibly accurately and consistently anticipate the needs of the people who dwell in the homes. Mobile apps controlled thermostats and lighting solutions can already be found on retail store shelves. There is also a noticeable range of safety devices, which include remote system failure indicators, virtual tracking etc. The technology is also being extended to all other home use gadgets and devices.
Some of the IoT smart home applications are:
•Home security – Access control
•Lighting control
•Home health care
•Fire detection – Leak detection
•Energy efficiency
•Solar panel monitoring and control
•Temperature monitoring and HVAC control
•Automated meter reading
_
IoT Applications for Connected/Smart Home:
Nest Learning Thermostat [vide infra]:
Philips Hue-Smart Home Lighting [vide infra]:
The Air Quality Egg:
Based on the community-led air quality sensing network, the Air Quality Egg is a smart sensor system which his designed to track traces of CO and NO2 in the home environment. It is dependent on the participation of community to determine air quality in their environment. It is highly extensible and inexpensive system which can be made from DIY sensors.
Amazon Echo:
Take control of your home with your voice, this is the concept around which Amazon Echo is built. Designed to be highly sensitive listener, Echo has 7 inbuilt microphones to hear you from across the room even among other noises. Get answers, hear news, play music, listen to audio books and integrate to other smart home devices like Philips Hue, Samsung SmartThings and WeMo. It is backed with 360º omni-directional audio.
_____
Smart wearable:
Wearables are one of the hottest trends in IoT currently. Apple, Samsung, Jawbone and plenty of others all are surviving in a cut throat competition. Wearable IoT tech is a very large domain and consists of an array of devices. These devices broadly cover the fitness, health and entertainment requirements. The prerequisite from internet of things technology for wearable applications is to be highly energy efficient or ultra-low power and small sized. Here are some top examples of wearable IoT devices that fulfil these requirements.
_
IoT Applications for Wearable:
Jawbone UP2:
This tracker band is an excellent IoT application example in healthcare as well as wearable. It comes with features like activity tracking, food logging and sleep patterns. Also it is offered in many styles and colors. It has features like Activity Tracking, Sleep Tracking and Smart Coach.
Fitbit ChargeHR:
Charge HR is a high performance IoT wearable which is provided with many smart features. It tracks your heart rate as well as activities sitting on your wrist. It provides you capability to automatically track heart rate, track workouts, monitor sleeping pattern, get call notifications, and synchronize data with your PC and hundreds of Smart Phones wireless and many more.
Motorola Moto 360 Sport:
It’s time to get your healthy space personalized even without your smart phone. Motorola Moto 360 Sport is designed with this fact in mind. It delivers all the important information that you need from your phone directly. Available in men’s and women’s collection you will hardly run out of choice with this. It supports both Android as well as iOS apps.
_____
Smart building:
IoT devices can be used to monitor and control the mechanical, electrical and electronic systems used in various types of buildings (e.g., public and private, industrial, institutions, or residential) in home automation and building automation systems. The smart building where photovoltaic generation takes place may adapt to known journey patterns, and divert locally generated power to be available in advance of likely usage. This will reduce expenditure, make transport more affordable, and drive down the carbon footprint of the community. Smart buildings will be able to react to information derived from sensor networks across the city to adjust ventilation and window settings based on the cross-referencing of pollution levels and prevailing weather conditions in the locale. IoT technology, embedded within the building, will support the needs of older and vulnerable people enabling them to live within their own communities for longer, therefore supporting social cohesion. Smart lighting solutions will mimic the spectral characteristics of natural daylight in the home, office, or ward, helping to maintain the natural circadian rhythm and general well-being of those who are required to remain indoors. As IoT functionality becomes embedded in everyday items such as light bulbs, switches, utility meters, and other appliances, digital health systems to support vulnerable people will be a simple software configuration of that pre-existing hardware. Some of the most important benefits from smart buildings have been in terms of energy conservation. In the past, buildings were typically heated and cooled throughout, independent of occupancy levels. Smart systems that manage lighting, temperature, and air quality levels and which can enable or disable controlled zones have revolutionized building management systems. The benefits of smart technology are not restricted to energy conservation, either. Once you enter a smart building, there wouldn’t be any surprises like a burst water pipe to encounter; intelligent sensors would have already detected pressure variation along pipes and communicated this information to avert a leak in the building. Structural health monitoring of the building can even be undertaken, by analysis of vibrations and material conditions within the structure. In order for this type of monitoring to occur, unique IP addresses will have to be created for each device that is connected. IoT will not only take care of your indoor environment; external aspects of life will also be enhanced. Improvements might involve being alerted to an open parking space that will fit your car size as you cruise up to a building. Once you have parked, you will be able to enter your home or workplace safely, as sensor networks, using a combination of audio, video, and vibration detection devices, will have detected unauthorized individuals entering restricted areas. IoT systems can also track the whereabouts of various items in a building through geo-location.
_
Smart city:
Many of the world’s major cities have embarked on smart city projects, including Seoul, New York, Tokyo, Shanghai, Singapore, Amsterdam, Cairo, Dubai, Kochi and Malaga. Smart cities may still be viewed as cities of the future, but considering today’s rate of innovation it is highly likely that smart city models will over the coming decade become very feasible and certainly very popular strategies for cities’ development. A smart city has been defined as a ‘knowledge’, ‘digital’, ‘cyber’ or ‘eco’ city; representing a concept open to a variety of interpretations, depending on the goals set out by a smart city’s planners. We might refer to a smart city as an improvement on today’s city both functionally and structurally, using information and communication technology (ICT) as an infrastructure. A smart city can perhaps be defined as “a city that strategically utilizes many smart factors such as Information and Communication Technology to increase the city’s sustainable growth and strengthen city functions, while guaranteeing citizens’ happiness and wellness. A human-centric smart city thus relies on an advanced ICT infrastructure and continued urban development, always taking environmental and economic sustainability into account. As it is with homes, our cities are also benefiting from this technology (IoT). The most clear examples are driving convenience (real time traffic tracking and parking information) and electricity optimization (using resources like lightning as per weather conditions and automated malfunction reporting). All major cities of the world are welcoming IoT based solutions. Examples of hyper-connected smart cities include Masdar in United Arab Emirates, Songdo in South Korea, over a dozen of cities in China, and many more cities in Europe and the rest of the world. In the UK, Bristol City Council is developing a smart city service within the SPHERE project (Sensor Platform for Healthcare in a Residential Environment) to monitor the health and well-being of people living at home. Bristol also has a more extensive smart city agenda that goes beyond home telehealthcare services. Moving north, Glasgow (Scotland) is similarly running an ambitious £24 million programme to demonstrate how technology can make life in the city smarter, safer and more sustainable. Love Clean Streets is a UK app that enables Internet-connected citizens to use their mobile phones’ built-in GPS (Global Positioning System) and camera to document and directly report to their local authorities any environmental or neighbourhood issues or crimes they might come across while travelling in the city. Users can later visit the Love Clean Streets Web site to review the progress of their reports. City councils across the UK are responding very well and promptly to citizens’ reports filed via the Love Clean Streets mobile app, which is a good example of the active engagement and participation of members of the general public in the day-to-day running and maintenance of their own cities.
_
Smart surveillance, safer and automated transportation, smarter energy management systems and environmental monitoring all are examples of internet of things applications for smart cities. Smart cities are the real substantial solutions for the troubles people usually face due to population outburst, pollution, poor infrastructure and shortage of energy supplies.
_
Large scale deployments:
There are several planned or ongoing large-scale deployments of the IoT, to enable better management of cities and systems. For example, Songdo, South Korea, the first of its kind fully equipped and wired smart city, is near completion. Nearly everything in this city is planned to be wired, connected and turned into a constant stream of data that would be monitored and analyzed by an array of computers with little, or no human intervention. Another application is a currently undergoing project in Santander, Spain. For this deployment, two approaches have been adopted. This city of 180,000 inhabitants, has already seen 18,000 city application downloads for their smartphones. This application is connected to 10,000 sensors that enable services like parking search, environmental monitoring, digital city agenda among others. City context information is used in this deployment so as to benefit merchants through a spark deals mechanism based on city behavior that aims at maximizing the impact of each notification. Other examples of large-scale deployments underway include the Sino-Singapore Guangzhou Knowledge City; work on improving air and water quality, reducing noise pollution, and increasing transportation efficiency in San Jose, California; and smart traffic management in western Singapore. French company, Sigfox, commenced building an ultra-narrowband wireless data network in the San Francisco Bay Area in 2014, the first business to achieve such a deployment in the U.S. It subsequently announced it would set up a total of 4000 base stations to cover a total of 30 cities in the U.S. by the end of the 2016, making it the largest IoT network coverage provider in the country thus far. Another example of a large deployment is the one completed by New York Waterways in New York City to connect all their vessels and being able to monitor them live 24/7. The network was designed and engineered by Fluidmesh Networks, a Chicago-based company developing wireless networks for critical applications. The NYWW network is currently providing coverage on the Hudson River, East River, and Upper New York Bay. With the wireless network in place, NY Waterway is able to take control of its fleet and passengers in a way that was not previously possible. New applications can include security, energy and fleet management, digital signage, public Wi-Fi, paperless ticketing and others.
______
Smart healthcare:
The use of these tags in medical context enables a rapid and precise identification of each patient and, by means of Internet of Things (IoT), enables a ubiquitous and quick access to medical related records. These technologies, RFID and IoT, integrated within a suitable system, promote a better physician-patient interaction. A simple IoT-enabled system can send warnings to any physician, nurse or other health caregiver. Therefore, with a simple IoT architecture one may remotely monitor and control the patient’s well-being. In health there are devices that support RFID which are placed in patients suffering from Alzheimer’s, diabetes, cardiovascular diseases, among others, that require complex treatment. The device placed on the patient only contains an identification number and, using a reader, the health professional, as long as he entitled with all the necessary authorizations, may access the hospital database and get information about the patient. Of course, whenever personal or private information is to be accessed, all the necessary security mechanisms must be present, protecting the data access. Physicians can access all authorized health patient information using Internet of Things enabled access. A more extensive use of RFID-enabled ”things”, either objects or persons, can improve several e-health services and specifically can foster patient medication control. Although a complete set of sensors can monitor the patient’s health, a much simpler architecture may allow to automatically monitor and check if patients follow medical prescriptions: if patients had the recommended doses of the right pharmaceutical drug at the right time.
_
IoT devices can be used to enable remote health monitoring and emergency notification systems. These health monitoring devices can range from blood pressure and heart rate monitors to advanced devices capable of monitoring specialized implants, such as pacemakers, Fitbit electronic wristbands or advanced hearing aids. Specialized sensors can also be equipped within living spaces to monitor the health and general well-being of senior citizens, while also ensuring that proper treatment is being administered and assisting people regain lost mobility via therapy as well. Other consumer devices to encourage healthy living, such as, connected scales or wearable heart monitors, are also a possibility with the IoT. More and more end-to-end health monitoring IoT platforms are coming up for antenatal and chronic patients, helping one manage health vitals and recurring medication requirements.
_
IoT-driven, monitoring systems are used for hospitalized patients whose physiological status requires constant close attention. These monitoring systems employ sensors to collect physiological information which is analyzed and stored using gateways and the cloud. This information is then sent wirelessly to caregivers for further analysis and review. A simple IoT-enabled system can send warnings to any physician, nurse or other health caregiver. Therefore, with a simple IoT architecture one may remotely monitor and control the patient’s well being.
_
mHealth (also written as m-health) is an abbreviation for mobile health, a term used for the practice of medicine and public health supported by mobile devices. An amalgamated concept of Internet of m-health Things (m-IoT) has been introduced recently and defined as a new concept that matches the functionalities of m-health and IoT for a new and innovative future (4G health) applications.
______
Smart agriculture:
The agricultural sector is not behind in IoT applications. In fact, it is doing more innovation with IoT. IoT strategy is being utilized in agricultural industry and it is a huge success in terms of productivity, pest control, water conservation and continuous production based on improved technology and methods.
Some influences of IoT in agriculture:
•Crop monitoring: Sensors can be used to monitor crops and health of plants with the help of data collected. Sensors can also be used for early monitoring of pests and disease.
• Food safety: The whole supply chain – the farm, logistics and retails are all getting connected. Farm products can be connected with RFID tags – increasing customer confidence.
•Climate monitoring: Sensors can be used to monitor temperature, humidity, light intensity and soil moisture. These data can be sent to the central system to trigger alerts and automate water, air and crop control.
•Logistics monitoring: Location based sensors can be used to track vegetables and other farm products during transport and storage. This enhances scheduling and automates supply chain.
•Livestock farming monitoring: The monitoring of farm animals can be monitored via sensors to detect potential signs of disease. These data can be analyzed from the central system and relevant information can be sent to the farmers.
_
The OpenIoT Phenonet Project:
The Phenonet Project is designed to help farmers monitor crucial vitals like humidity, air temperature and soil quality using remote sensors. This project helps farmers to improve the yield, plan irrigation as well as make harvest forecasts. It is also helpful for biologists to study the effect of genome and microclimate on crop production.
CleanGrow’s Carbon Nanotube Probe:
Based in Ireland the CleanGrow’s project helps with monitoring the crop nutrients making use of a carbon nanotube-based sensor system. This information helps farmers to alter maturity rate or color of the crop production. As opposed to analog devices used conventionally the CleanGrow device uses a nanotube sensor that detects quantity and presence of specific ion in the production.
______
Smart transportation:
A very useful implementation of IoT is the introduction of connected cars. The cars have sensors attached to them which help them analyze the traffic of the road, keeps them updated about the road condition and also keeps them connected with the road control center for further assistance. There are on-board diagnostic systems that alert you about almost everything in the car, from faulty lights to tire pressure. The IoT can assist in integration of communications, control, and information processing across various transportation systems. Application of the IoT extends to all aspects of transportation systems (i.e. the vehicle, the infrastructure, and the driver or user). Dynamic interaction between these components of a transport system enables inter and intra vehicular communication, smart traffic control, smart parking, electronic toll collection systems, logistic and fleet management, vehicle control, and safety and road assistance.
______
Smart energy and smart grid:
Smart energy:
Integration of sensing and actuation systems, connected to the Internet, is likely to optimize energy consumption as a whole. It is expected that IoT devices will be integrated into all forms of energy consuming devices (switches, power outlets, bulbs, televisions, etc.) and be able to communicate with the utility supply company in order to effectively balance power generation and energy usage. Such devices would also offer the opportunity for users to remotely control their devices, or centrally manage them via a cloud based interface, and enable advanced functions like scheduling (e.g., remotely powering on or off heating systems, controlling ovens, changing lighting conditions etc.). In fact, a few systems that allow remote control of electric outlets are already available in the market.
_
Smart grid:
A smart grid is a modernized electrical grid that uses analog or digital information and communications technology to gather and act on information – such as information about the behaviors of suppliers and consumers – in an automated fashion to improve the efficiency, reliability, economics, and sustainability of the production and distribution of electricity. Power grids of the future will not only be smart enough but also highly reliable. Smart grid concept is becoming very popular. The basic idea behind the smart grids is to collect data in automated fashion and analyze the behavior of electricity consumers and suppliers for improving efficiency as well as economics of electricity use.
Reasons for smart grid:
•Stopping power threat.
•Higher quality/reliability of power, fewer blackouts.
•Efficient energy utilization.
•Smart grid is required for renewable power.
_
Smart meter:
A smart meter is usually an electronic device that records consumption of electric energy in intervals of an hour or less and communicates that information at least daily back to the utility for monitoring and billing. Smart meters enable two-way communication between the meter and the central system. Unlike home energy monitors, smart meters can gather data for remote reporting. With Smart Energy Metering, not only do technicians not have to come and physically read your meter, you have access personally to your energy usage so you can see what impact your consumption patterns have on your wallet and on the environment.
________
Smart media:
In order to hone the manner in which the internet of things (IoT), the media and big data are interconnected, it is first necessary to provide some context into the mechanism used for media process. It has been suggested by Nick Couldry and Joseph Turow that practitioners in media approach big data as many actionable points of information about millions of individuals. The industry appears to be moving away from the traditional approach of using specific media environments such as newspapers, magazines, or television shows and instead tap into consumers with technologies that reach targeted people at optimal times in optimal locations. The ultimate aim is of course to serve, or convey, a message or content that is (statistically speaking) in line with the consumer’s mind-set. For example, publishing environments are increasingly tailoring messages (advertisements) and content (articles) to appeal to consumers that have been exclusively gleaned through various data-mining activities.
The media industries process big data in a dual, interconnected manner:
•Targeting of consumers (for advertising by marketers)
•Data-capture
Thus, the internet of things creates an opportunity to measure, collect and analyse an ever-increasing variety of behavioural statistics. Cross-correlation of this data could revolutionise the targeted marketing of products and services. For example, as noted by Danny Meadows-Klue, the combination of analytics for conversion tracking with behavioural targeting has unlocked a new level of precision that enables display advertising to be focused on the devices of people with relevant interests. Big data and the IoT work in conjunction. From a media perspective, data is the key derivative of device interconnectivity, whilst being pivotal in allowing clearer accuracy in targeting. The internet of things therefore transforms the media industry, companies and even governments, opening up a new era of economic growth and competitiveness. The wealth of data generated by this industry (i.e. big data) will allow practitioners in advertising and media to gain an elaborate layer on the present targeting mechanisms used by the industry.
_____
Smart environmental monitoring:
Another significant implementation of IoT is in the field of environmental care. Global warming being an issue, IoT is being used to tackle this critical problem. Also, IoT allows quicker notification of natural disaster, thus saving crucial time. It also promotes better analysis and reporting. Also this technology helps in pollution and waste management using warning sensor. Environmental monitoring applications of the IoT typically use sensors to assist in environmental protection by monitoring air or water quality, atmospheric or soil conditions, and can even include areas like monitoring the movements of wildlife and their habitats. Development of resource constrained devices connected to the Internet also means that other applications like earthquake or tsunami early-warning systems can also be used by emergency services to provide more effective aid. IoT devices in this application typically span a large geographic area and can also be mobile. It has been argued that the standardization IoT brings to wireless sensing will revolutionize this area.
Smarter Natural Disaster Management:
The ability to predict, with fine-grained accuracy, the onset of conditions that promote forest fires before they get out of control or even begin, allow containment teams to respond more quickly and first responders to rapidly manage targeted evacuations. This same concept applies equally to the smarter detection of and reaction to mudslides, avalanches, earthquakes and other natural disasters.
____
Smart waste management:
There are two innovative functions of smart waste management: operational efficiency and waste reduction.
1. Operational efficiency: Smart trash cans:
Although public services and waste management companies have been around for a long time, they have seen only limited innovation with operational efficiency. One big problem that they’ve faced is that it is better to pick up trash receptacles too often than to allow overflow of waste. Even with great route optimization, the sanitation specialists must still physically go to the dumpster to check trash levels. Because of this, trucks often visit containers that do not need emptying, which wastes both time and fuel. But with the rise of the Internet of Things (IoT), smart sensors and sensor-level M2M technology have begun popping up in all kinds of places—including trash receptacles. Imagine if your trash bin not only collected garbage, but helped better manage the waste you produce. This is what the city of Barcelona, Spain, has done by placing monitoring sensors on recycling bins that send out an alert when full to help its residents reduce household waste and increase recycling. Similar programs are in place in other cities around the world. The Internet of Things (IoT) is now being used to aid waste management companies and sanitation departments in tracking waste and recycling volumes. In Barcelona’s case, more than $4 billion in savings is projected in the next 10 years. With Internet-connected sensors embedded in the bins, collection frequency is determined by bin capacity alone rather than fixed collection schedules.
2. Waste reduction:
The other side of smart waste management deals with managing the sheer quantity of waste created on a daily basis. Consumers and businesses toss millions of pounds of garbage each year. Educating these entities on how to reduce waste is particularly important for municipalities, who must pay for the landfills and waste removal services. This topic is a bit more complex; it goes beyond the need for IoT-based sensors, and more towards an efficient purchasing process. In the U.S., consumers waste about 30% or 133 billion pounds of food each year! This could be dramatically reduced with the right M2M applications in place, which could help with things like asset and material tracking. Using the right IoT technology, a grocery store could track exact quantities of the food they regularly sell, cut back on waste, and reduce spoilage. This is a bit different than what we traditionally think of as waste management, but the “upstream” waste problem is massive, so it’s worth addressing. From a consumer perspective, the makers of smart refrigerators and other appliances may eventually be able to bring this technology into the home. These smart products will soon be able to alert consumers when their food is going to spoil, or when they’re running low on key provisions. This allows them to consume their purchases before they go bad, become more aware of the foods that they purchase and eat regularly, and eventually turn into more conscientious shoppers.
_____
Smart Infrastructure management:
Monitoring and controlling operations of urban and rural infrastructures like bridges, railway tracks, on- and offshore- wind-farms is a key application of the IoT. The IoT infrastructure can be used for monitoring any events or changes in structural conditions that can compromise safety and increase risk. It can also be used for scheduling repair and maintenance activities in an efficient manner, by coordinating tasks between different service providers and users of these facilities. IoT devices can also be used to control critical infrastructure like bridges to provide access to ships. Usage of IoT devices for monitoring and operating infrastructure is likely to improve incident management and emergency response coordination, and quality of service, up-times and reduce costs of operation in all infrastructure related areas. Even areas such as waste management can benefit from automation and optimization that could be brought in by the IoT.
_____
Smart Manufacturing:
Network control and management of manufacturing equipment, asset and situation management, or manufacturing process control bring the IoT within the realm on industrial applications and smart manufacturing as well. The IoT intelligent systems enable rapid manufacturing of new products, dynamic response to product demands, and real-time optimization of manufacturing production and supply chain networks, by networking machinery, sensors and control systems together. Digital control systems to automate process controls, operator tools and service information systems to optimize plant safety and security are within the purview of the IoT. But it also extends itself to asset management via predictive maintenance, statistical evaluation, and measurements to maximize reliability. Smart industrial management systems can also be integrated with the Smart Grid, thereby enabling real-time energy optimization. Measurements, automated controls, plant optimization, health and safety management, and other functions are provided by a large number of networked sensors. National Science Foundation established an Industry/University Cooperative Research Center on intelligent maintenance systems (IMS) in 2001 with a research focus to use IoT-based predictive analytics technologies to monitor connected machines and to predict machine degradation, and further to prevent potential failures. The vision to achieve near-zero breakdown using IoT-based predictive analytics led the future development of e-manufacturing and e-maintenance activities. The term IIoT (industrial internet of things) is often encountered in the manufacturing industries, referring to the industrial subset of the IoT. IIoT in manufacturing would probably generate so much business value that it will eventually lead to the fourth industrial revolution, so the so-called Industry 4.0. It is estimated that in the future, successful companies will be able to increase their revenue through internet of things by creating new business models and improve productivity, exploit analytics for innovation, and transform workforce. The potential of growth by implementing IIoT will generate $12 trillion of global GDP by 2030.
_
Design architecture of cyber-physical systems-enabled manufacturing system:
While connectivity and data acquisition are imperative for IIoT, they should be the foundation and path to something bigger but not the purpose. Among all the technologies, predictive maintenance is probably a relatively “easier win” since it is applicable to existing assets and management systems. The objective of intelligent maintenance systems is to reduce unexpected downtime and increase productivity. And to realize that alone would generate around up to 30% over total maintenance costs. Industrial big data analytics will play a vital role in manufacturing asset predictive maintenance, although that is not the only capability of industrial big data. Cyber-physical systems (CPS) is the core technology of industrial big data and it is will be an interface between human and the cyber world. Cyber-physical systems can be designed by following the 5C (connection, conversion, cyber, cognition, configuration) architecture, and it will transform the collected data into actionable information, and eventually interfere with the physical assets to optimize processes.
______
Smart industry:
Industrial automation is one of the most profound applications of IoT. With help of internet of things infrastructure backed with advanced sensor networks, wireless connectivity, innovative hardware and machine-to-machine communication, conventional automation process of industries will transform completely. IoT automation solutions for industries from all big names like NEC, Siemens, Emerson and Honeywell are already in the market.
Here are some examples of the impact the IoT has on industries:
•Intelligent transport solutions speed up traffic flows, reduce fuel consumption, prioritize vehicle repair schedules and save lives.
•Smart electric grids more efficiently connect renewable resources, improve system reliability and charge customers based on smaller usage increments.
•Machine monitoring sensors diagnose – and predict – pending maintenance issues, near-term part stockouts, and even prioritize maintenance crew schedules for repair equipment and regional needs.
•Data-driven systems are being built into the infrastructure of “smart cities,” making it easier for municipalities to run waste management, law enforcement and other programs more efficiently.
_____
Smart Business:
With the growth of IoT, business models are hugely innovated. It has become much easier to manage multiple location and keep a close quality check. More customers can be reached all at once and hence a greater growth of the business.
_____
Smart Government:
With the help of connected government, government sectors can keep a track of its local governing bodies like municipal corporation. It can also keep a track of its employee productivity. Common people can request their needs and government can deliver the service quickly. Also, with the massive amount of data collected from IoT sensors, it can lead to new innovations. And not to forget, citizens can also gain knowledge about the working of their respective government.
_______
Real Life examples of Internet of Things:
1. Nest Learning Thermostat:
Nest Learning Thermostat is a revolutionary concept which gives you many benefits. Its breakthrough technology and internet of things based concepts make it highly efficient electric appliance. Usually thermostats incur almost half of the energy bills. However with Nest you can save up to 15% on cooling bills as well as 12% on heating bills on average. Imagine that you can control the temperature of your home from anywhere, with just a simple touch on your smart phone or tablet, and you get the desired temperature before getting home so that you don’t need to wait. Nest Learning Thermostat is the most popular Thermostat in this ‘Smart’ category, this company has been bought by Google. Nest thermostat not only controlled from anywhere but also it learns by itself by following your daily routing and change the temperature of your home without bothering you, Like if you have set low temperature at night continuously for 7 days, then this device learns that and automatically lowers the temperature at night. This is very helpful device for saving the energy.
_
2. Baby Mimo meter:
They have been around for some time now. Mimo Monitors are not only affordable but also presents a new technology. Used for several business purposes, this loT has been making things easier, simpler and is said to be very productive. But now Mimo Monitors offers something unique and unexpected. The technology now enables you get updated to your baby’s body position, their breathing level, body temperature, response to activities and health. The information collected is intimated to you through your mobile phones. Further the above explained, “Nest Learning Thermostat”, can automatically change the temperature of your baby’s nursery, according to the data, got by Mimo meter. The main goal behind it is to provide the best safety measure available to avoid SIDS (Sudden Infant Death Syndrome).
_
3. Philips-Hue Bulbs:
What is the real potential of internet of things applications for designing smart homes is aptly projected by Philips Hue. The same hue bulb gives you 600 to 800 color lumens which mean there is a light for every mood of yours. It is compatible with known smart home platforms like HomeKit for Apple iPhone and Amazon Echo. Philips hue bulbs have now stepped into a new stage of innovation with these smart bulbs. Linked with your mobile phones, you can now actually control the intensity of lights on your fingertips. The combination of bulb with mobile technology is next thing for your home. Instead of going for different watt of bulbs to suit the mood and the environment, simply change the intensity from dim to medium to full using your phone. These bulbs can be programmed to get dim at night, also it can work as alarm by setting it in blinking mode on any intruder detection. The lighting can be dynamically changed according to the environment, like a different lighting when watching a movie. ON and OFF timer can also be set for these bulbs to automatically ON and OFF after a particular time.
_
4. Ralph Lauren Polotech Shirt:
Ralph Lauren is an American clothing company which has launched The Polotech Shirt for athletes and become a pioneer to bring IoT in clothing industry. This Shirt can record the biometric readings of Athletes like Heart rate, calories burned, activity levels, breathing depths etc. and can help him to deliver the best performance. It can be connected to the Apple watch or an iPhone, and can track & record all the activities in your iPhone. So this Polotech Shirt along with the iPhone can become your complete fitness tracker or we can say fitness trainer.
_
5. Apple Watch and HomeKit:
And the most talked company of gadgets and devices. Apple has changed the world with its inventive and ultra-modern devices. Be it phones, laptops or any other electronic device, Apple has itself strongly established. The Apple watch is the example of how advanced the technology is at Apple. Apart from time and date, the Apple watch enables you to keep a track record of your health and daily activities. Also the voice activation allows you to get notifications in instant. View maps, listen to music and take care of your calls just by a single watch. Surprised at what a watch can do? Well, it’s has lot more features for you to explore and make life easier. Apart from Apple watch, Apple has also released Apple HomeKit Framework, which enables Siri (voice assistant in Apple’s iOS) to communicate with the devices and accessories at your home, so that they can be controlled remotely.
_
6. Microchips:
We are hearing about microchips for a long time and have their applications in some of the sensitive and dangerous fields like defense. But now one of the most integrated circuit have found its way to our day-to-day life. Microchips are generally used in the forms of tracer as the radar detectors can detect data about various things. Now with ioT, you can fit a microchip on collars of pet or attach it to them to keep a track of their movement without being physically looking for them. There is more freedom to your pets now and this also enables you to keep a record of their health too.
_
7. Google Glass:
We are talking about innovation and how can we forget to mention the company that defines innovation and internet the best. Google has always come up with things that have made our life easy always and with Google glass it is more like repeating history for the company. A headset designed with optical-head display, if only you knew eyeglasses could be this much efficient. You can now wear it and together with voice activation you can interact, see, surf the net, click pictures and do many others things in a Smartphone-like-hands-free form. This Google glass is the result of ‘Project Glass’ from Google.
______
From fixed to mobile applications of IoT:
______
The Internet of Things applications ranking:
Authors measured three things: What people search for on Google, what people talk about on Twitter, and what people write about on LinkedIn. The highest score received a rating of 100%, the other Internet of Things applications were ranked with a percentage that represents the relation to the highest score (relative ranking).
_______
_______
IoT and society, economy, law and regulation:
_
IoT and social issues:
The Internet has long since changed from being a purely informational system to one that is socio-technological and has a social, creative and political dimension. But the importance of its non-technological aspects is becoming even more apparent in the development of an Internet of Things, since it adds an entirely new quality to these non-technological aspects. Much of the public debate on whether to accept or reject the Internet of Things involves the conventional dualisms of “security versus freedom” and “comfort versus data privacy”. Smart objects can accumulate a massive amount of data, simply to serve us in the best possible way. Since this typically takes place unobtrusively in the background, we can never be entirely sure whether we are being “observed” when transactions take place. Individual instances of observation might seem harmless enough, but if several such instances were to be amalgamated and forwarded elsewhere, this could under certain circumstances result in a serious violation of privacy. Irrespective of the data protection issues, there is also the question of who would own the masses of automatically captured and interpreted real-world data, which could be of significant commercial or social value, and who would be entitled to use it and within what ethical and legal framework. Another critical aspect is that of dependence on technology. In business and also in society generally we have already become very dependent on the general availability of electricity – infrequent blackouts have fortunately not yet had any serious consequences. But if everyday objects only worked properly with an Internet connection in the future, this would lead to an even greater dependence on the underlying technology. If the technology infrastructure failed for whatever reason – design faults, material defects, sabotage, overloading, natural disasters or crises – it could have a disastrous effect on the economy and society. Even a virus programmed by some high-spirited teenagers that played global havoc with selected everyday objects and thus provoked a safety-critical, life-threatening or even politically explosive situation could have catastrophic consequences. Remotely controlled things could also cause us to become dependent and lose our supremacy on a personal level. And even with no ill intent, our own smart objects might not behave as we would wish, but rather as they “believe” is best for us – presaging a subtle type of technological paternalism. The prompt feedback that smart things can give us about themselves or that helpful tools such as smartphones and augmented reality spectacles can give us about our environment is also a mixed blessing. While it can encourage us to do good, useful things (such as an animated smiley in a smart bathroom mirror that praises us for brushing our teeth properly with the electric toothbrush), it can also seduce us into making unnecessary impulse purchases.
______
IoT and democracy:
The basis of a democracy is voluntary civic engagement: A person’s participation in setting government policy is intentional and a matter of choice. In democracies, citizens express their preference through activism and voting. Historically, governments and politicians eager to do a good job interpreting citizen intent also relied on opinion polls, conversations with civic groups, social science research, and huge record-keeping projects like the census. Politicians have long tried to interpret citizen intent and manipulate it through rhetoric and campaign tricks. But pervasive device networks will change the rules, making voluntary conversations among elected officials, political parties, lobbyists and civic groups less important than the plethora of near-perfect data generated by the objects around us. Occasional activism and petition-signing will be overshadowed by volumes of behavioral information cleverly extracted from the Internet of Things. Firms want to know consumer habits, governments want to anticipate the needs of citizens, and politicians will pay handily to understand the whims of voters. Political lobbying isn’t a new sport, but the Internet of Things is going to be a particularly powerful resource for lobbyists. The more a lobbyist knows about the behavior of voters and donors, the easier it is to activate those people and organize them into AstroTurf movements on clients’ behalf. Considering that smart data mining costs good money, it’s worth considering whether civic groups, scientists and journalists will have anywhere near enough resources to be effective checks on what the big political players are doing with the Internet of Things. With billions of sensors to learn from, there’s no reason governments shouldn’t try to learn about public preferences, or firms do in-depth market research on the behavior of their customers. And it’s very likely that citizens and consumers will benefit from better products and services. But the governments must provide ways to ensure that people are presented, first and foremost, with active choices about the political use of individual data. Politics used to be what happened whenever one person or organization tried to represent another person or organization. In the years ahead, much of that representative work will be done by devices. Governments, businesses and data protection authorities around the world are trying to anticipate the possible impacts of the Internet of Things and with good reason. Several international experts, thinkers and technology builders are forecasting profound political, social and economic transformations; concerns about privacy and surveillance are chief among them. Governments in Europe and the US have undertaken public consultations to probe into anticipated impacts. A number of industry associations are working on Internet of Things-related projects. European Commission’s Article 29 Data Protection Working Party, which includes representatives from European data protection offices, adopted an opinion on the Internet of Things, where it set out a number of serious privacy risks and detailed recommendations for addressing them. Echoing several of the messages in the Article 29 Working Party opinion, international data protection authorities adopted the Mauritius Declaration on the Internet of Things. In this declaration, regulators made several observations, concluding that sensor data are so high in quantity, quality and sensitivity, that such data should be regarded and treated as personal data. They commented on the business models that they anticipate to be spawned by the Internet of Things, recognizing that the value is not in the devices themselves, but rather in new services related to the Internet of Things and in the data they can amass and combine. Some scholars and activists argue that the IoT can be used to create new models of civic engagement if device networks can be open to user control and inter-operable platforms. Philip N. Howard, a professor and author, writes that political life in both democracies and authoritarian regimes will be shaped by the way the IoT will be used for civic engagement. For that to happen, he argues that any connected device should be able to divulge a list of the “ultimate beneficiaries” of its sensor data, and that individual citizens should be able to add new organizations to the beneficiary list. In addition, he argues that civil society groups need to start developing their IoT strategy for making use of data and engaging with the public.
_
The Internet of Things has now arrived in politics. A study for the “Global Trends 2025” project carried out by the US National Intelligence Council states that “foreign manufacturers could become both the single source and single point of failure for mission-critical Internet-enabled things”, warning not only of the nation becoming critically dependent on them, but also highlighting the national security aspect of extending cyber-wars into the real world: “U.S. law enforcement and military organizations could seek to monitor and control the assets of opponents, while opponents could seek to exploit the United States” . The European Commission is reflecting vocally but somewhat vaguely on the problem of governance for a future Internet of Things. The issue here is how to safeguard the general public interest and how to prevent excessively powerful centralized structures coming into being or the regulatory power of the Internet of Things falling exclusively into the hands of what they describe as a single “specific authority”. The European Commission’s action plan on the Internet of Things has also provoked a huge emotional backlash, as critically noted in the German “Telepolis” online magazine with its lead story entitled “A brief route to collective incapacitation” (the tone of the article is that the Internet of Things would cost a lot of money, that consumers would have to pay for it, and that its benefits would be small). Readers’ comments on the article describe the Internet of Things as a “world of enforced networking” and a “gigantic funny farm”; it would make us “totally dependent on technology and those in power” and would mean “surrendering all freedom”. It was even called a perversion of the Internet and its alleged political mission: “a medium that was developed to free mankind and that should be used for this purpose could hence be misused in order to establish total control”. Although these extreme opinions are not representative, it must be said that for an Internet of Things to be truly beneficial requires more than just everyday objects equipped with microelectronics that can cooperate with each other. Just as essential are secure, reliable infrastructures, appropriate economic and legal conditions and a social consensus on how the new technical opportunities should be used. This represents a substantial task for the future.
_______
Emerging economy and Development issues:
The Internet of Things holds significant promise for delivering social and economic benefits to emerging and developing economies. This includes areas such as sustainable agriculture, water quality and use, healthcare, industrialization, and environmental management, among others. As such, IoT holds promise as a tool in achieving the United Nations Sustainable Development Goals. The broad scope of IoT challenges will not be unique to industrialized countries. Developing regions also will need to respond to realize the potential benefits of IoT. In addition, the unique needs and challenges of implementation in less-developed regions will need to be addressed, including infrastructure readiness, market and investment incentives, technical skill requirements, and policy resources. IoT provides a great platform for enablement of social development in varied societies across the world and with the proliferation of Internet across the various sections of the society in developing countries coupled with lowering costs of microprocessors and sensors will make IoT devices accessible to low income households. But there are lot of shortcomings related to enablement of high speed internet and basic technology services architecture for commercial and business usage in developing countries. Until and unless, a basic infrastructure is in place, devices would be of no value to the users. While IoT brings about new opportunities; at the same time, it adds multiple layers of complexity. Such a new environment of devices will add a new dimension for policy makers in emerging economies who will need to chalk out a new blueprint for IoT related regulatory concerns.
_______
_______
The legal considerations of the internet of things:
As with many new technologies, there are a number of tricky legal challenges to consider as part of widespread IoT adoption.
1. Cyber security:
The National Fraud Intelligence Bureau recently said that around 70% of the 230,845 frauds recorded in 2013/14 included a cyber-element, compared to approximately 40% five years ago. It could be argued that if consumers cannot protect the devices that are already connected to the internet, perhaps we should not be adding more web-enabled devices to our homes and businesses. For example, would it be possible for criminals to use your central heating system to access your mobile phone and gain access to your credit card details? Security researchers recently proved they could hack into home networks through Wi-Fi-enabled smart light bulbs. Could they tell when you’re not in and rob your house?
2. Language and culture:
Behind the scenes, businesses that adopt IoT solutions will need to ensure the way in which they do this is going to address legal requirements. Much of this will relate to the contractual relationships that will support the technology and connectivity. A business will need to ensure that its internal departments work together. An IoT solution will require IT managers, who may be sourcing some of the service providers to implement an IoT solution, to understand the customer facing issues. Data protection, security and privacy will be at the forefront of this.
3. Data protection:
The way in which a business using IoT manages the vast amounts of data that those engaged objects produce will need to be filtered. This will be a challenge for developers to ensure the system works as efficiently as possible, as well as having data protection implications so irrelevant data is not collected. As we have already seen, precautions against data security breaches and misuse of data need to be designed into IoT solutions. Another risk identified is that data may be re-purposed. This addresses the need to safeguard data subjects by ensuring data is only used for the purpose for which it was collected and originally contemplated. With many IoT applications operating together and communicating with each other autonomously, data subjects will be unaware of the entire processing taking place. This will impact the ability to give the right consent and exercise their rights in respect of the data collected. It is not unrealistic to expect that there will be different IoT regulations in different jurisdictions, just as has happened with cloud, data privacy and other technologies
4. Regulation and standards:
Governments and other regulators have begun to focus on IoT. This includes the EU commission, which has published a report on the result of its public consultation on the IoT. Top of the list of issues that the law needs to address are loss of privacy and data protection. The EU Commissioner’s report recommended that IoT should be designed from the start to meet suitable detailed requirements that underpin the right of deletion, right to be forgotten, data portability, privacy and data protection principles. The draft Data Protection Regulation addresses some of these measures including:
•Privacy by design and default – to ensure that the default position is the least possible accessibility of personal data
•Consent
•Profiling – clearer guidelines on when data collected to build a person’s profile can be used lawfully, for example to analyse or predict a particular factor such as a person’s preferences, reliability, location or health
•Privacy policies
•Enforcement and sanctions – violations of data privacy obligations could result in fines of up to 5% of annual worldwide turnover or €100m, whichever is greater
In the US, privacy and data security in the IoT is also being considered by regulators with the same focus on privacy and security. Any new solution, which is based on integration, will require standards. So far, the software industry has not been great at adopting standard terms for provision of services, including for cloud computing, although this is something which is being addressed. The IoT may be the beneficiary of this, but it is not unrealistic to expect that there will be different regulations in different jurisdictions, just as has happened with cloud, data privacy and other technologies.
_
Legal, regulatory and rights issues:
There are no concrete laws present which encompasses the various layers of IoT across the world. The gamut of devices connected to each other raises many security issues and no existing legal laws address such exposures. The issues lie in whether current liability laws will extend their arm for devices which are connected to the internet all the time because such devices have complex accountability issues. The use of IoT devices raises many new regulatory and legal questions as well as amplifies existing legal issues around the Internet. The questions are wide in scope, and the rapid rate of change in IoT technology frequently outpaces the ability of the associated policy, legal, and regulatory structures to adapt. One set of issues surrounds cross-border data flows, which occur when IoT devices collect data about people in one jurisdiction and transmit it to another jurisdiction with different data protection laws for processing. Further, data collected by IoT devices is sometimes susceptible to misuse, potentially causing discriminatory outcomes for some users. Other legal issues with IoT devices include the conflict between law enforcement surveillance and civil rights; data retention and destruction policies; and legal liability for unintended uses, security breaches or privacy lapses. While the legal and regulatory challenges are broad and complex in scope, adopting the guiding Internet Society principles of promoting a user’s ability to connect, speak, innovate, share, choose, and trust are core considerations for evolving IoT laws and regulations that enable user rights.
___
Algorithmic regulation:
Algorithmic regulation is an alternative form of government where the advantages and usages of computer algorithms are applied to regulations and law enforcement. Written laws are not replaced but stressed to test its efficiency. It was coined by Tim O’Reilly, Founder and CEO of O’Reilly Media Inc. Sometimes the “rules” aren’t really even rules. Gordon Bruce, the former CIO of the city of Honolulu, explained: when he entered government from the private sector and tried to make changes, he was told, “That’s against the law.” His reply was “OK. Show me the law.” “Well, it isn’t really a law. It’s a regulation.” “OK. Show me the regulation.” “Well, it isn’t really a regulation. It’s a policy that was put in place by Mr. Somebody twenty years ago.” “Great. We can change that!” Laws should specify goals, rights, outcomes, authorities, and limits. If specified broadly, those laws can stand the test of time. Regulations, which specify how to execute those laws in much more detail, should be regarded in much the same way that programmers regard their code and algorithms, that is, as a constantly updated toolset to achieve the outcomes specified in the laws. It’s time for government to enter the age of big data. Algorithmic regulation is an idea whose time has come. Algorithmic regulation is supposed to be a system of governance where more exact data collected from citizens via their smart devices and computers are used for more efficiency in organizing human life as a collective.
____
What about the neutrality principle in IoT?
(e.g. for ensuring competition and innovation dissemination on all IoT market segments, for allowing new isolated players and small scale structures to propose and disseminate innovations on a large scale, for promoting innovation via new business models.) Neutrality means transparency and lack of specific actions to promote one actor or perspective over others. In the development of the IoT, there are a number of dimensions to which neutrality should apply including forming, operating within, and the evolution of the IoT. Neutrality also has an impact in terms of privacy and data protection as far as some specific actions can lead to expose personal data (e.g. deep packet inspection). Standards have an important role to play in forming the IoT and it is essential that all actors have equal access to the standards making process for the IoT. For a concept as vast as the IoT there will of course be many simultaneous standards making activities, distributed not only by technologies and applications but also geographically. Coordination of standards development, without constraining freedom to innovate, will promote efficient development of IoT infrastructure and consequently applications, services and devices. In the same manner that global coordination of M2M standards is being considered within the GSC, similar coordination may be applied to IoT standards. Another perspective is that the IoT will in fact function as an infrastructure that a wide variety of applications and services will rely on. As a consequence access to this infrastructure will be important in order to develop and roll out new and innovative applications and services.
______
Open source and the IoT:
The concept of open source or free software has been around since the 1950s and for many it’s more than “free” firmware; it’s a philosophy and ethos to uphold. Many believe that software should be accessible and open source; just not at all cost. The market trends have given engineers a mandate: 50 billion connected devices by 2020 (Cisco and others); 500 connected devices in a home (Gartner). We are 3.5 years out and are still without standards for IoT development as well as security issues to iron out amongst other things. It is not the right time to get precious about code. We need more developers to easily access the internet of things and code for connected devices. We need to share ideas amongst engineers and product developers to better understand what works and what doesn’t. There is no reason why startups, DIYers and even established companies should have to pay for firmware as they experiment and prototype exciting new products that will help fulfil the market mandate. At the same time, businesses who develop IoT solutions need to be able to compensate their developers to keep making those IoT solutions stronger, simpler and more scalable for everyone. That’s why the GPLv2 option works again for IoT firmware. [General Public License (GPL) is a widely used free software license, which guarantees end users (individuals, organizations, companies) the freedoms to run, study, share (copy), and modify the software; v2 means version two] Once someone commercially applies your code and doesn’t want to open their own solution, they pay. Facilitating the growth of the Internet of Things is what all solution providers should focus on. IoT-enabled products need to be taken to the next level. This is only possible if we make firmware easily available and affordable for prototyping and DIYing. At the same time, everyone involved should profit from commercial applications; the firmware providers as well as the product makers.
_________
_________
Pros and cons of IoT:
The advantages of course of these highly networked and connected devices mean productive and enhanced quality of lives for people. For example, health monitoring can be rather easy with connected Rx bottles and medicine cabinets. Doctors supervising patients can monitor their medicine intake as well as measure blood pressure, sugar levels and alert them when something goes wrong to their patients online. In the aspect of energy conservation, household appliances can suggest optimal setting based on the user’s energy consumption like turning the ideal temperature just before the owner arrives home as well as turning on and off the lights whenever the owner is out on vacation just to create the impression that somebody is still left inside the house to prevent burglars from attempting to enter. Smart refrigerators, on the other hand, can suggest food supplies that are low on inventory and needs immediate replenishment. The suggestions are based on the user’s historical purchasing behavior and trends. Wearable technology are also part of this Internet of Things, where these devices can monitor sleeping patterns, workout measurements, sugar levels, blood pressure and connecting these data to the user’s social media accounts for tracking purposes. There are three main areas of benefit for manufacturers associated with the internet of things—the design, development, and manufacture of products; tracking and improving products throughout their lifecycle; and the management of the assets used in the process. Compare these advantages to its feared drawbacks like Radio Frequency Identification (RFID) tagging each item to be placed inside the smart refrigerator, each piece of clothing to be placed inside a smart closet or medicines inside a smart medicine cabinet are just too taxing an activity for many. The other disadvantage is the fact that most devices are not yet ready to communicate with another brand of devices. Specific products can only be networked with their fellow products under the same brand name. The reality of a “universal remote control” for all these devices and products is still in its infantile development. The most important drawback with regard to the full implementation of the Internet of Things is with regard to the privacy and security issue. Smart home devices have the ability to devour a lot of data and information about a user. These data can include personal schedules, shopping habits, medicine intake schedule and even location of the user at any given time. If these data fall into the wrong hands great harm and damage can be done to people.
_
What benefits is your organization seeing, or does it expect to see, from using IoT solutions?
_
IoT Benefits:
• Improved performance, visibility & scalability of business process automation
• Providing better, more cost effective service through real-time higher solution visibility /capture and analysis of real-time product performance information. This is useful for efficient decision making.
• Better transparency of physical flows and detailed status information. This is also important for regulatory compliance and public dissemination.
• Creation/transformation of new and existing business processes by enhancing efficiency, accuracy, mobility and automation
• Improved citizen’s quality of life, healthcare from anywhere
•New business opportunities, IoT can be used in every vertical for improving the efficiency, creates new businesses, and new and better jobs
•Economic growth, billions of dollars in savings and new services
•Better environment, saves natural resources and trees, helps in creating a smart, greener and sustainable planet
____
The Advantages of IoT:
1. Communication
IoT encourages the communication between devices, also famously known as Machine-to-Machine (M2M) communication. Because of this, the physical devices are able to stay connected and hence the total transparency is available with lesser inefficiencies and greater quality.
2. Automation and Control
Due to physical objects getting connected and controlled digitally and centrally with wireless infrastructure, there is a large amount of automation and control in the workings. Without human intervention, the machines are able to communicate with each other leading to faster and timely output.
3. Information
It is obvious that having more information helps making better decisions. Whether it is mundane decisions as needing to know what to buy at the grocery store or if your company has enough widgets and supplies, knowledge is power and more knowledge is better.
4. Monitor
The second most obvious advantage of IoT is monitoring. Knowing the exact quantity of supplies or the air quality in your home, can further provide more information that could not have previously been collected easily. For instance, knowing that you are low on milk or printer ink could save you another trip to the store in the near future. Furthermore, monitoring the expiration of products can and will improve safety.
5. Time
As hinted in the previous examples, the amount of time saved because of IoT could be quite large. And in today’s modern life, we all could use more time.
6. Money
The biggest advantage of IoT is saving money. If the price of the tagging and monitoring equipment is less than the amount of money saved, then the Internet of Things will be very widely adopted. IoT fundamentally proves to be very helpful to people in their daily routines by making the appliances communicate to each other in an effective manner thereby saving and conserving energy and cost. Allowing the data to be communicated and shared between devices and then translating it into our required way, it makes our systems efficient.
7. Better Quality of Life
All the applications of this technology culminate in increased comfort, convenience, and better management, thereby improving the quality of life.
In 1999, Ashton said it best in this quote from an article in the RFID Journal:
“If we had computers that knew everything there was to know about things – using data they gathered without any help from us – we would be able to track and count everything, and greatly reduce waste, loss and cost. We would know when things needed replacing, repairing or recalling, and whether they were fresh or past their best”.
______
IoT benefits to businesses:
1. Access to sales data:
Sales data collection and analysis is a fundamental necessity for all businesses. IoT devices can generate sales data based on how, why, and where products are used and purchased, which helps businesses to strategize their production and marketing efforts. Additionally, the data generates real time insights on consumers and their preferences, which businesses can use to address customer feedback quickly and effectively.
2. Reduced business costs
IoT has potential to save a significant amount of money and time for businesses. Consider the IoT system as a factory where all the devices are interconnected. If a particular product is failing in the market, the sales department can alert the production department and suggest changes. For example, General Electric believes that using IoT to develop gas and oil could save them $90 billion a year.
3. Targeted customer service
IoT connects devices like phones, automobiles, televisions, refrigerators, etc. to one ecosystem. The interconnected devices can then be synced to provide customer data to companies. Through integration of all the data, businesses can gain valuable insights on consumers, trends, and preferences to provide personalized and improved service to their customers.
4. Marketing Automation
Many IoT enabled smart applications, like Apple’s iBeacon, create knowledge about customer’s location, purchase history, preferences, and buying patterns. This allows businesses to find out in real time about where, how, and why products are being purchased. Based on this data, companies can categorize customers and customize marketing efforts by providing information that appeal to their customer’s interests.
5. New business Opportunities
The global IoT market will be worth $7.1 trillion by 2020, a significant increase from $1.9 trillion in 2013. This overwhelming estimate, along with advancement in sensor technologies, wireless sensor networks, and data management technologies, is paving the way for new business opportunities.
6. Applications in various industries
According to a Industrial Internet Insights Report, 53 % of global businesses are planning to implement IoT solutions within the next couple of years. IoT is still in its infancy and many potential investment opportunities exist across various industries, such as healthcare, automobiles, and energy.
7. Data management
The world’s overall virtual data will rise to 44 zettabytes in 2020, with 10% of it arriving from IoT, according to IDC’s Digital Universe report. Thus, the challenge will be to analyze and use this enormous amount of data efficiently. Companies will require better analytic systems as the data continues to grow.
8. New social medial networks
IoT is already compatible with social media networks that allow automated posts, while simultaneously allowing the users of particular devices to connect and create new online communities. Businesses, likewise, have the opportunity to connect with those new communities and take advantage of new emerging trends.
_____
Disadvantages of IoT:
Three of the main concerns that accompany the Internet of Things are the breach of privacy, over-reliance on technology, and the loss of jobs. When anything is put on the internet it will always be there. Of course there are security measures that are taken to protect information, but there is always the possibility of hackers breaking into the system and stealing the data. For example, Anonymous is a group of individuals that hacked into federal sites and released confidential information to the public. Meanwhile the government is supposed to have the highest level of security, yet their system was easily breached. Therefore, if all of our information is stored on the internet, people could hack into it, finding out everything about individuals lives. Also, companies could misuse the information that they are given access to. This is a common mishap that occurs within companies all the time. Just recently Google got caught using information that was supposed to be private. Information, such as the data collected and stored by IoT, can be immensely beneficial to companies. The privacy issues also leads to the question of who will control the Internet of Things? If there is only one company, that could potentially lead to a monopoly hurting consumers and other companies. If there are multiple companies that are given access to the information acquired, doesn’t that breach consumers privacy? Also, where is the information going to be stored? Phone service suppliers such as Verizon and AT&T are no longer offering unlimited data usage for mobile phones because it is too costly, yet by 2020 it is expected that 50 billion devices will be connected, collecting and storing data (Evans, 2011). Another argument against IoT is the over-reliance on technology. As time has progressed, our current generation has grown up with the readily availability of the internet and technology in general. However, relying on technology on a day to day basis, making decisions by the information that it gives up could lead to devastation. No system is robust and fault-free. We see glitches that occur constantly in technology, specifically involving the internet. Depending on the amount that an individual relies on the information supplied could be detrimental if the system collapses. The more we entrust and the more dependent we are on the Internet could lead to a potentially catastrophic event if it crashes. Finally the connecting of more and more devices to the Internet will result in the loss of jobs. The automation of IoT will have a devastating impact on the employment prospects of less-educated workers. For example, people who evaluate inventory will lose their jobs because devices can not only communicate between each other, but transmit that information to the owner. We already are witnessing jobs being lost to automated machines, such as the checkout line in supermarkets. These disadvantages can be largely devastating to society as a whole, as well as individuals and consumers.
_____
Limitations of IoT:
There’s a bunch of limits that people working on low powered distributed and embedded systems bump into all the time. You typically have a limited power budget, limited memory space, slow processors, weak radios, tightly constrained budgets, and as such a limited range of sensors and controllers to pick from when building something. The only other meaningful limitation would be something like available IP addresses – but the Internet of things would exist on a subnet in your home network and they would not need public IPs. Bandwidth will definitively be limited due to physical constraints, but it will vary widely depending on the type of device. Most important limit is the ability to process the data and extract meaningful information. You could put an IoT device (light, temperature, inductive proximity sensors) in every square yard of highway in the country. It would only be a few hundred million sensors, with a few billion pieces of data. Technically that is easy enough (sort of – installation, power, cost, bandwidth can get in the way). It is also easy enough to store that data away. The trick is doing something meaningful with that data. Even asking the right question about how the data is useful can be problematic. Not only do you have to build and run an analytic model, you also have the ability to combine your road sensor dataset with the weather dataset, and the vehicle telemetry dataset. Assuming you can move the datasets around, and have enough compute available to process the data, you are limited by the skills of the people who can figure out to get insight into the data to turn it into something more valuable.
_____
Digital Fatigue:
Too much social media, too many smartphones, too many YouTube videos to watch, too many apps to download, too much of everything digital and wired and online. We can’t even go for a lovely stroll without checking Twitter every five minutes. Now along comes the IoT, promising to connect the Internet to our eyeglasses and our wristwatches and our thermostats and our appliances and our streetlights and on and on. Digital fatigue is inevitable.
___
Intentional bricking of devices:
The Electronic Frontier Foundation has raised concerns that companies can use the technologies necessary to support connected devices to intentionally disable or “brick” their customers’ devices via a remote software update or by disabling a service necessary to the operation of the device. In one example, home automation devices which were sold with the promise of a “Lifetime Subscription” were rendered useless after Nest Labs acquired Revolv and made the decision to shut down the central servers the Revolv devices had used to operate. As Nest is a company owned by Alphabet (Google’s parent company), the EFF argues this sets a “terrible precedent for a company with ambitions to sell self-driving cars, medical devices, and other high-end gadgets that may be essential to a person’s livelihood or physical safety.” Owners should be free to point their devices to a different server or collaborate on improved software. But such action violates the United States DMCA section 1201, that only has an exemption for “local use”. This forces tinkerers that want to keep using their own equipment into a legal grey area. EFF thinks buyers should refuse electronics and software that prioritize the manufacturer’s wishes above their own. Examples of post-sale manipulations include Google Nest Revolv, disabled privacy settings on Android, Sony disabling GNU/Linux on PlayStation 3, enforced EULA on Wii U.
_____
Environmental impact:
A concern regarding IoT technologies pertains to the environmental impacts of the manufacture, use, and eventual disposal of all these semiconductor-rich devices. Modern electronics are replete with a wide variety of heavy metals and rare-earth metals, as well as highly toxic synthetic chemicals. This makes them extremely difficult to properly recycle. Electronic components are often simply incinerated or dumped in regular landfills, thereby polluting soil, groundwater, surface water, and air. Such contamination also translates into chronic human-health concerns. Furthermore, the environmental cost of mining the rare-earth metals that are integral to modern electronic components continues to grow. With production of electronic equipment growing globally yet little of the metals (from end-of-life equipment) being recovered for reuse, the environmental impacts can be expected to increase. Also, because the concept of IoT entails adding electronics to mundane devices (for example, simple light switches), and because the major driver for replacement of electronic components is often technological obsolescence rather than actual failure to function, it is reasonable to expect that items that previously were kept in service for many decades would see an accelerated replacement cycle, if they were part of the IoT. For example, a traditional house built with 30 light switches and 30 electrical outlets might stand for 50 years, with all those components still being original at the end of that period. But a modern house built with the same number of switches and outlets set up for IoT might see each switch and outlet replaced at five-year intervals, in order to keep up-to-date with technological changes. This translates into a ten-fold increase in waste requiring disposal.
_______
IoT security:
Security experts are worried that consumers won’t be able to tell the difference between secure and insecure devices on their home network. It will be a threat to enterprise networks as well. These devices, many of which will be cheap and junky and made by who-knows-who overseas, may not have any security of their own. Security researchers imagine problems, such as the connected toilet, demonstrated at a recent Black Hat conference, which flushed and closed its lid repeatedly. Hackers could create havoc by turning appliances and HVAC systems on and off. Baby monitors have been successfully taken over by outsiders. One advantage that IoT security may have is it’s still in its early stages, and the security community has a chance to build IoT systems with a strong measure of protection.
_
Fatal IoT:
Researcher Marie Moe woke up after emergency surgery in 2011 with a new pacemaker to correct a heart condition. What she didn’t realize at the time was that the lifesaving device in her chest exposed her to a completely different kind of threat. The pacemaker keeping her alive has wireless connectivity capabilities — a detail her doctors didn’t tell her — meaning it could be hacked. Moe was understandably disturbed that it never occurred to her doctors to tell her that her device had wireless capability, and they had not considered the security implications. “They really had not thought about the pacemaker security at all,” she said. Vulnerabilities like Moe’s are moving quickly from the rare to the extremely common. The FBI recently warned consumers that the proliferation of connected devices — from medical devices to security systems — means even more potential targets for malicious cybercriminals. That opportunity will be huge, as there are more connected devices than humans. Security experts believe the tech industry needs to figure out how to secure the “Internet of Things” now, while the architecture is still being developed. That means building in features such as encryption, authentication and the ability to remotely update devices now.
______
IoT may break internet:
Research firm IDC estimates that by 2025, 152,000 new devices will be jumping, directly or indirectly, onto the Internet every minute, bringing the total number of connected devices to 80 billion worldwide. Partly as a result, the world’s collection of digital data will zoom from 44 zettabytes in 2020 to approximately 180 zettabytes. Currently, we’re burbling around 10 zettabytes. A smart factory might generate over 1,000 terabytes a day. Self-driving cars can produce 1 GB a second. While the vast majority of this data won’t be seen by human eyes, machines will use and need it. As a result, a huge proportion of data, and especially Internet of Things data, likely won’t “go” anywhere. We aren’t going to send it to computers. We’re going to plant computers where data gets generated. Smart buildings will monitor their own vital signs and fix problems locally. “Fast Data” applications for controlling freeway traffic or analyzing how people move around in stories will be controlled at by smart lights talking to computers in the stockroom wall. Intel has estimated that 40% of IoT data will stay local. The crux of the problem is that data grows at an exponential pace. Networks grow at a linear pace. Why? Data is abstract and networks are physical. But more importantly, networks cost money. Information might be free, but compression algorithms, land use permits and new multiplexers are not.
_____
IoT and artificial intelligence (AI):
Many caution against the potentially dangerous combination of the IoT and artificial intelligence (AI). World renowned physicist Stephen Hawking believes that thinking machines pose a threat to our very existence, and technology entrepreneur Elon Musk considers AI to be “potentially more dangerous than nukes“. But surely that’s just hyperbole. We’re already using AI in our day-to-day lives (for example whenever we interact with a virtual assistant such as Siri or Cortana) and the world hasn’t ended quite yet. In fact, for most people it just got more convenient. So what does happen when AI meets the IoT? Well initially, good things. For example, many smart home devices can “learn” from their users’ behavior patterns and regulate themselves accordingly. A thermostat that “knows” when you’re home and adjusts the temperature to suit, is not only extremely convenient, but can also save you quite a bit of money. Multiply that saving by the growing number of households installing such devices and we’ve taken a small, but significant step to addressing our energy consumption problems. And therein lies danger. The combination of the IoT and AI presents a vast amount of potentially life-changing possibilities. But this doesn’t mean that we should embrace them blindly! The need for caution was underscored recently by a fatal crash involving a self-driving car. The exact cause of the accident is not yet clear, however what is clear is that the car was in autopilot mode and that there was no reaction by the software before the crash. AI of car failed. And then of course there’s the human component. Remember Tay, Microsoft’s smart chat bot? Within 24 hours of being launched, Tay notoriously embarked upon a racist, genocidal Twitter rampage. Sadly, this was in large part, down to the humans she interacted with. It took Microsoft’s AI less than a day to go from “humans are super cool” to agreeing with Hitler. So AI can go weird by interacting with humans.
______
Unstructured Data and cognitive computing:
Unstructured Data is data that hasn’t been organized. Most of the information humans create is unstructured. Classic computers need structured data to process, cognitive computers don’t. They can make sense of unstructured data by learning, thinking, and drawing connections the way humans do. The problem is, 80% of data on the IoT is unstructured. Traditional computers can only make sense of a small fraction of the unstructured data. Every day the amount of data grows and compounds the problem. Luckily companies like IBM have been working on something called cognitive computing that can help humans make sense of the unstructured data on the IoT. Cognitive Computing is a computer program that can think like a human. Or rather, artificial intelligence that can think learn, and make connections. Cognitive AI can make sense out of massive unstructured data and reformulate it into simple analytics that can be requested quickly by humans. Watson is a cognitive computer. He has been in the works for years, and professionals in industries like healthcare already use him (similar to how someone would use Google or Wolfram Alpha). His next mission is to make sense of the IoT. Google has its own cognitive AI DeepMind. Right now they aren’t focused on the IoT, so we won’t discuss this more now. A cognitive computer like Watson can receive a lot of data and make sense of it quickly. However, to process every possible combination of data from 50 billion plus devices instantly, Watson will be likely to require moving beyond the boundaries of classical computing. Cognitive computing uses classic computers because we don’t have working quantum computers yet outside experimental research. Quantum cognitive computing would make Quantum AI.
_____
Your IoT Devices may be spying on you:
These innocent-looking devices may be spying on you, or performing other nefarious actions:
Your Television:
Televisions may track what you watch. Some LG televisions were found to spy on not only what channels were being watched, but even transmitted back to LG the names of files on USB drives connected to the television. Hackers have also demonstrated that they can hack some models of Samsung TVs and use them as vehicles to capture data from networks to which they are attached, and even watch whatever the cameras built in to the televisions see.
Your Kitchen Appliances:
Many recent-generation kitchen appliances come equipped with connectivity that allows for great convenience, but this benefit comes at a price – potential spying and security risks. Information about when you wake up in the morning (as extrapolated from data on your Internet-connected coffee maker) and your shopping habits (as determined by information garnered from your smart fridge) can help robbers target your home. Furthermore, potential vulnerabilities have been reported in smart kitchen devices for quite some time, a smart refrigerator was found to have been used by hackers in a malicious email attack. You read that correctly – hackers successfully used a refrigerator to send out malicious emails.
Your DVR/Cable-Box/Satellite-TV Receiver:
Providers of television programming can easily track what you are watching or recording, and can leverage that information to target advertisements more efficiently. Depending on service agreements, providers could potentially even sell this type of information to others, and, of course, they are likely to furnish this information to the government if so instructed.
Your Modem (and Internet Service Provider):
If it wanted to, or was asked by the government to do so, your ISP could easily compile a list of Internet sites with which you have communicated. Even if the providers themselves declined to spy as such, it may be possible for some of their technical employees to do so. Worse yet, since people often subscribe to Internet service from the same providers as they do television service, a single party may know a lot more about you then you might think.
Your smartphone:
Not only may your cellular provider be tracking information about you – such as with whom you communicate and your location – but it, as well as Google (in the case of Android), Apple (in the case of iPhones), or other providers of software on the device, may be aware of far more detailed actions such as what apps you install and run, when you run them, etc. Some apps sync your contacts list to the providers’ servers by default, and others have been found to ignore privacy settings. Phones may even be capturing pictures or video of you when you do not realize and sending the photos or video to criminals!
Your Webcam or Home Security Cameras:
On that note, malware installed on your computer may take control of the machine’s webcam and record you – by taking photos or video – when you think the camera is off. Miss Teen USA was allegedly blackmailed by a hacker who took control of her laptop’s webcam and photographed her naked when she thought the camera was not on. Likewise, malware on computers or hackers operating on those machines could potentially intercept transmissions from security cameras attached to the same network as the devices (some cameras transmit data unencrypted), and copy such videos for their own systems. Such information is invaluable to burglars.
Your Telephone:
It is common knowledge that the NSA has been tracking people’s calls, and even the changes proposed by President Obama won’t truly eliminate the spying. Of course, phone companies also track phone calls as they need call information for their billing systems. So, even if you use an old, analog phone your calls may be tracked. If you are receiving phone service from the same provider as you get your Internet and/or television service, phone records are yet another element of information that a single party knows about you.
Your Lights, Home Entertainment System, and Home Alarm System:
Various newer lighting, home entertainment, and home security systems can be controlled via Wi-Fi or even across the Internet. Remote control is a great convenience, but it also raises questions as to whether information is reported to outside parties.
Your Thermostat (Heat and/or Air Conditioning):
Various Internet-connected thermostats are now available. They provide great convenience, but might they also be transmitting information about your preferences to others.
Your Laundry Equipment:
Like kitchen appliances, washers and dryers that connect to the Internet may report information that users may not realize is being shared, and that if intercepted, or misused, could help criminals identify when you are home and when you are not.
Your Medical Devices:
It is not news that pacemakers, insulin pumps, and other medical devices can be hacked. But even normal functioning devices may spy on you. Various pacemakers relay patient status information over the Internet – this may be valuable in some cases, but also creates risks. Could unauthorized parties obtain information from such data in transmit? What if a criminal sent out phony “pacemaker impersonating” messages stating that a patient is in distress in order to have his physician instruct him to go to the hospital – and leave his home vulnerable?
Your iPod or Other Entertainment Devices:
Yes, there are still millions of people using specialized non-phone-equipped electronic devices, but these devices are often Wi-Fi enabled and pose similar to risks to smartphones as discussed above. Of course if you are reading books or magazines, watching videos, or listening to audio supplied by an online provider, your choices and preferences are likely being tracked.
_
Government may tap into your IoT gadgets and use your smart devices to spy on you:
‘In the future, intelligence services might use the internet of things for identification, surveillance, monitoring, location tracking, and targeting for recruitment’, says James Clapper, US director of national intelligence. Clapper made clear that the internet of things – the many devices like thermostats, cameras and other appliances that are increasingly connected to the internet – are providing ample opportunity for intelligence agencies to spy on targets, and possibly the masses. And it’s a danger that many consumers who buy these products may be wholly unaware of.
_______
How to make IoT secure:
_
Data storage has undergone a huge shift over the last decade, and an explosion of information driven by inter-device connectivity is creating similarly transformative waves in networking and security. Security threats represent the biggest obstacle to Internet of Things adoption, and Microsoft, Amazon, and Cisco face daunting challenges as cloud and IoT platform holders. Cisco estimates the current number of connected devices to be roughly 10 billion, and expects 50 billion connected devices and sensors in 2020. Sharing data between new devices presents huge analytics opportunities, but the data needs to be funnelled and protected to reduce the potential for misuse. New IoT devices open new security challenges, but the biggest vulnerabilities will likely be found on networks. Application programming interfaces (APIs) from IoT platform holders enable devices and software to interact, but a lack of standardization across networks and APIs leads to vulnerabilities. Gartner estimates that more than 25% of enterprise security attacks will involve IoT connections by 2020, and threat growth is expected to outstrip security spending. IoT will account for just 10% of IT security spending in 2020 according to Gartner. Platforms holders have to build in preparation for the IoT data boom. Vulnerabilities for IoT data have potentially severe implications. Multi-layered protection is needed. Network segmentation helps wall off information, and will be one of the keys to making the Internet of Things secure. Digital walls can function as detection points and regulate what data comes and goes, but they also need to learn in order to keep up with threats. Amazon, Microsoft, and Cisco are looking to improve network segmentation capabilities through internal development and acquisitions, and stand to gain competitive advantages from strength in this area, but there’s likely an even more important key to making interoperability a reality. Even with improvements in threat detection, the different network standards employed by IoT devices and platforms will proliferate vulnerabilities. Information needs to be movable between public and private clouds and local networks, but doing this securely requires greater standardization. IoT is already prompting a wave of collaborations, but greater cooperation could still be needed to reduce the security issue. Authentication standards would greatly reduce the IoT security threat, but the wide range of competing interests involved makes standardization a challenge.
______
Protect yourself in the new world of the Internet of Things:
1. Don’t store personal identifying information on any device. Don’t even use your real name.
2. Use a unique and complex password for all of your devices so that if one is hacked, all of your devices are not jeopardized.
3. Read the fine print and find out what information is gathered and stored by your devices as well as how that information is used by the manufacturer.
4. Your smartphone is the entrance way to your car’s connectivity. Keep your smartphone protected with a strong and unique password as well as anti-virus and anti-malware security software.
5. Change the default usernames and passwords on all of your home network devices.
6. Use and update anti-virus and anti-malware software on your home computer network.
______
______
IoT research:
_
Internet of Things could get big with battery free devices powered by Wi-Fi signals:
The ability to power remote sensors and devices using Wi-Fi signals could be the enabling technology behind the Internet of things, say electrical engineers. University of Washington researchers have developed a way to broadcast power to remote devices using an existing technology that many people already have in their living rooms: ordinary Wi-Fi. They call their new approach power over Wi-Fi or PoWi-Fi. PoWiFi is the first power over Wi-Fi system that works with existing Wi-Fi chipsets and minimizes its impact on Wi-Fi performance. The work is also related to efforts from startups such as Ossia and Wattup. These efforts claim to deliver around 1 W of power at ranges of 15 feet and charge a mobile phone. Analysis shows that this requires continuous transmissions with an EIRP (equivalent isotropic radiated power) of 83.3 dBm (213 kW). This not only jams the Wi-Fi channel but also is 50,000 times higher power than that allowed by FCC regulations part 15 for point to multi-point links. In contrast, new system is designed to operate within the FCC limits and has minimal impact on Wi-Fi traffic. Researchers note that in the event of an FCC exception to these startups, their multi-channel design can be used to deliver high power while having minimal effect on Wi-Fi performance. Recent work on Wi-Fi backscatter enables low-power connectivity with existing Wi-Fi devices. Backscatter communication is more power-efficient than traditional radio communication and hence enables Wi-Fi connectivity without incurring Wi-Fi’s power consumption. However, it is focused on the communication mechanism and does not evaluate the feasibility of delivering power using Wi-Fi. This new work is complementary to and can in principle be combined to achieve both power delivery and low power connectivity using Wi-Fi devices. The idea is simple in concept. Wi-Fi radio broadcasts are a form of energy that a simple antenna can pick up. Until now, Wi-Fi receivers have all been designed to harvest the information that these broadcasts carry. The University of Washington team’s approach to this is refreshingly straightforward. They simply connect an antenna to a temperature sensor, place it close to a Wi-Fi router and measure the resulting voltages in the device and for how long it can operate on this remote power source alone. The simple answer is that the voltage across the sensor is never high enough to cross the operating threshold of around 300 millivolts. However, it often comes close. But a closer examination of the data makes for interesting reading. The problem is that Wi-Fi broadcasts are not continuous. Routers tend to broadcast on a single channel in bursts. This provides enough power for the sensor but as soon as the broadcast stops, the voltages drop. The result is that, on average, the sensor does not have enough juice to work. That gave researchers an idea. Why not program the router to broadcast noise when it is not broadcasting information and employ adjacent Wi-Fi channels to carry it so that it doesn’t interfere with data rates. Wi-Fi broadcasts can be on any of 11 overlapping channels within a 72 MHz band centered on the 2.4 GHz frequency. This allows for three non-overlapping channels to be broadcast simultaneously. The results are impressive. It turns out that the temperature sensor can operate at distances of up around six meters from the router and by adding a rechargeable battery to the mix, researchers were able to increase that to about nine meters. Even more ambitiously, they also connected a camera to their antenna. This was a low-power Omnivision VGA sensor capable of producing 174 x 144 pixel black and white images, which requires 10.4 milliJoules of energy per picture. To store energy, they attached a low leakage capacitor to the camera, which activates when the capacitor is charged to 3.1V and continues operating until the voltage drops to 2.4 Volts. The images were stored in a 64 KB non-volatile ferroelectric random access memory. In the subsequent tests, the camera performed remarkably well. “The battery-free camera can operate up to [about five meters] from the router, with an image capture every 35 minutes,” say researchers. By adding a rechargeable battery they increased that to seven meters. The router could even power the camera through a brick wall, demonstrating that it would be possible to attach the device outside while keeping the power supply inside.
_
LED bulbs could be used to connect the Internet of Things:
Consumer-grade light-emitting diode (LED) bulbs can, with some modifications, be used for connecting devices such as appliances, wearable devices, sensors, toys and utilities that could comprise the Internet of Things (IoT), says a study. Interconnecting appliances, sensors and a wide variety of devices into the Internet of Things has many potential benefits but using radio links to do so threatens to make the radio spectrum an even scarcer resources. Visible light communication networks conserve the radio spectrum, while also making it difficult to eavesdrop for anyone out of line of sight of the network. By having individual LEDs alternate between sending modulated light signals and serving as receivers of signals, it is possible to create a network of bulbs that can send messages to each other and connect to devices, while having no discernible effect on room lighting. Disney Research in ETH Zurich implemented such a visible light communication (VLC) system, demonstrating that it is a viable way to interconnect devices within a room. They used commercially available, off-the-shelf LED light bulbs as a starting point, which are readily available at low cost and can be used in any lamp with standard sockets. This leads to an easy-to-setup and flexible testbed that can be readily duplicated. The bulbs were modified, however. A “System-on-a-Chip” running an embedded version of Linux was added to each bulb, as well as photodiodes to enhance sensing of incoming signals and an additional power supply for the added electronics. The findings were presented recently at the IEEE International Conference on Sensing, Communication and Networking (SECON) 2016 in London.
_________
_________
Future of IoT:
___
Internet of Things Technologies for 2017 and 2018:
Gartner, Inc. has highlighted the top 10 Internet of Things (IoT) technologies that should be on every organization’s radar through the next two years. The IoT demands an extensive range of new technologies and skills that many organizations have yet to master. A recurring theme in the IoT space is the immaturity of technologies and services and of the vendors providing them. Architecting for this immaturity and managing the risk it creates will be a key challenge for organizations exploiting the IoT. In many technology areas, lack of skills will also pose significant challenges. The technologies and principles of IoT will have a very broad impact on organizations, affecting business strategy, risk management and a wide range of technical areas such as architecture and network design. The top 10 IoT technologies that will enable Organizations to unlock the full Potential of the IoT for 2017 and 2018 are:
1. IoT Security
The IoT introduces a wide range of new security risks and challenges to the IoT devices themselves, their platforms and operating systems, their communications, and even the systems to which they’re connected. Security technologies will be required to protect IoT devices and platforms from both information attacks and physical tampering, to encrypt their communications, and to address new challenges such as impersonating “things” or denial-of-sleep attacks that drain batteries. IoT security will be complicated by the fact that many “things” use simple processors and operating systems that may not support sophisticated security approaches. Experienced IoT security specialists are scarce, and security solutions are currently fragmented and involve multiple vendors. New threats will emerge through 2021 as hackers find new ways to attack IoT devices and protocols, so long-lived “things” may need updatable hardware and software to adapt during their life span.
2. IoT Analytics
IoT business models will exploit the information collected by “things” in many ways — for example, to understand customer behavior, to deliver services, to improve products, and to identify and intercept business moments. However, IoT demands new analytic approaches. New analytic tools and algorithms are needed now, but as data volumes increase through 2021, the needs of the IoT may diverge further from traditional analytics.
3. IoT Device (Thing) Management
Long-lived nontrivial “things” will require management and monitoring. This includes device monitoring, firmware and software updates, diagnostics, crash analysis and reporting, physical management, and security management. The IoT also brings new problems of scale to the management task. Tools must be capable of managing and monitoring thousands and perhaps even millions of devices.
4. Low-Power, Short-Range IoT Networks
Selecting a wireless network for an IoT device involves balancing many conflicting requirements, such as range, battery life, bandwidth, density, endpoint cost and operational cost. Low-power, short-range networks will dominate wireless IoT connectivity through 2025, far outnumbering connections using wide-area IoT networks. However, commercial and technical trade-offs mean that many solutions will coexist, with no single dominant winner and clusters emerging around certain technologies, applications and vendor ecosystems.
5. Low-Power, Wide-Area Networks
Traditional cellular networks don’t deliver a good combination of technical features and operational cost for those IoT applications that need wide-area coverage combined with relatively low bandwidth, good battery life, low hardware and operating cost, and high connection density. The long-term goal of a wide-area IoT network is to deliver data rates from hundreds of bits per second (bps) to tens of kilobits per second (kbps) with nationwide coverage, a battery life of up to 10 years, an endpoint hardware cost of around $5, and support for hundreds of thousands of devices connected to a base station or its equivalent. The first low-power wide-area networks (LPWANs) were based on proprietary technologies, but in the long term emerging standards such as Narrowband IoT (NB-IoT) will likely dominate this space.
6. IoT Processors
The processors and architectures used by IoT devices define many of their capabilities, such as whether they are capable of strong security and encryption, power consumption, whether they are sophisticated enough to support an operating system, updatable firmware, and embedded device management agents. As with all hardware design, there are complex trade-offs between features, hardware cost, software cost, software upgradability and so on. As a result, understanding the implications of processor choices will demand deep technical skills.
7. IoT Operating Systems
Traditional operating systems (OSs) such as Windows and iOS were not designed for IoT applications. They consume too much power, need fast processors, and in some cases, lack features such as guaranteed real-time response. They also have too large a memory footprint for small devices and may not support the chips that IoT developers use. Consequently, a wide range of IoT-specific operating systems has been developed to suit many different hardware footprints and feature needs.
8. Event Stream Processing
Some IoT applications will generate extremely high data rates that must be analyzed in real time. Systems creating tens of thousands of events per second are common, and millions of events per second can occur in some telecom and telemetry situations. To address such requirements, distributed stream computing platforms (DSCPs) have emerged. They typically use parallel architectures to process very high-rate data streams to perform tasks such as real-time analytics and pattern identification.
9. IoT Platforms
IoT platforms bundle many of the infrastructure components of an IoT system into a single product. The services provided by such platforms fall into three main categories: (1) low-level device control and operations such as communications, device monitoring and management, security, and firmware updates; (2) IoT data acquisition, transformation and management; and (3) IoT application development, including event-driven logic, application programming, visualization, analytics and adapters to connect to enterprise systems.
10. IoT Standards and Ecosystems
Although ecosystems and standards aren’t precisely technologies, most eventually materialize as application programming interfaces (APIs). Standards and their associated APIs will be essential because IoT devices will need to interoperate and communicate, and many IoT business models will rely on sharing data between multiple devices and organizations. Many IoT ecosystems will emerge, and commercial and technical battles between these ecosystems will dominate areas such as the smart home, the smart city and healthcare. Organizations creating products may have to develop variants to support multiple standards or ecosystems and be prepared to update products during their life span as the standards evolve and new standards and related APIs emerge.
___
Emerging Trends in development and deployment of IoT based applications are:
1. Miniaturization of devices – While VLSI technologies are moving towards lesser microns, Micro Electric Machines (MEMS) and nano electronics are making the sensors, smaller and power efficient so that they can be used inside smaller devices and even living systems.
2. IPV6 as an integration layer – Drawing from the OSI layer structure and protocols from Internet, it is natural to extend the IP layer as an integration layer for Internet of things as well. But unlike desktops and laptops the nodes attached to the ‘things’ are low in resources such as battery and computing power. However there have been successful attempt to develop a standard named 6LoWPAN, which is an acronym of IPv6 over Low power Wireless Personal Area Networks, bringing IPV6 over IEEE 802.15.4. The uIPv6 is one of the world’s smallest open-source, IPv6-ready protocol stack, which could enable every device, no matter how limited by power or memory to have an Internet Protocol address.
3. Mobile phones as data capturing devices – Another development that is taking place and beginning to spread globally is to extend data capture systems on mobile phones. Camera, NFC readers and Bluetooth are used for many diverse data capture applications. The advantage of mobile phone as pervasive device with a support for internet connectivity will enable its wide application and acceptance. For example there are mobile applications which uses camera to read 2-D barcodes and LCD screen to display barcodes such that it can be interfaced to registration/payment systems.
4. Low power and energy-neutral devices – The energy required to operate the intelligent devices will be dramatically decreased. The search is on for a zero level of entropy where the device or system will have to harvest its own energy. In addition to relatively established solar cells, there are success stories such as vibration energy harvesting (perpetuum), powering from RF beams (Powercast), energy from shakes (Sandia national Laboratories) and many attempts by exploiting wind, thermal, strain etc. From energy storage perspective thin film batteries (Cymbet) and thin film micro energy cells (Infinite Power Solutions) can be harvested.
5. Handling High Volume and high bandwidth data – Just to give some numbers, in the year 2015 more than 220 Exabaytes of data was stored. As current network are ill-suited for this exponential traffic growth, there is a need by all the actors to re-think current networking and storage architectures. It will be imperative to find novel ways and mechanisms to find, fetch, and transmit data.
6. Autonomic management – The ever growing complexity of systems will be unmanageable, and will hamper the creation of new services and applications, unless the systems will show self-properties, such as self-management, self-healing and self-configuration.
___
The Internet of Things and wearable computing will progress significantly between now and 2025:
Many experts believe infrastructure and adoption of the Internet of Things will substantially progress in the next decade. Many believe there will be clear advantages as that happens. Some believe it will happen, but disagree that the benefits will be great or outweigh the problems. A modest minority flatly disagree and many see a mixed picture, where the technology advances that add to life also create problems. Even most of those who worry about the trend towards the Internet of Things do not challenge the notion that more objects, appliances, cars, and other parts of the environment will be connected. JP Rangaswami, chief scientist for Salesforce.com, was particularly pointed in describing the benefits that will emerge in this new environment: The proliferation of sensors and actuators will continue. ‘Everything’ will become nodes on a network. The quality of real-time information that becomes available will take the guesswork out of much of capacity planning and decision-making. We will really understand what it means to move from ‘stocks’ to ‘flows,’ as in the Hagel-Seely Brown-Davison model. The net effect will be to reduce waste everywhere: in physical flows and logistics, in the movement of people and goods; in logical flows and logistics, in the movement of ideas and information; decisions will be made faster and better, based on more accurate information; prior errors in assumption and planning will be winkled out more effectively. ‘Inventory’ will be reduced, as will the waste associated with the decay that is an intrinsic part of inventory. This will affect the food you buy and cook and eat; the fuel you use to power yourself, your devices, and your vehicles; the time you take to do things; and, as you learn to live longer, the burden of care will reduce as a result of far better monitoring of, and response to, your physical and emotional state, in terms of healthcare. Our notions of privacy and sharing will continue to evolve as a result, with new tradeoffs needing to be understood and dealt with. People will engage with information using all of their senses: touch and feel, sight, sound, smell, and taste—using them in combination, more often than not. Wearable, connected devices will become embedded more and more in our bodies, more like implants, as in the [Google] Glass becoming more like contact lenses. As that happens, our ability to use nerve impulses to engage with information will expand dramatically. We will see today’s connected devices become smaller and smaller and slowly merge into the part of the body from where the particular sense related to that device operates. Most of our devices will be communicating on our behalf—they will be interacting with the physical and virtual worlds more than interacting with us. The devices are going to disappear into what we wear and/or carry. For example, the glasses interface will shrink to near-invisibility in conventional glasses. The devices will also become robustly inter-networked. The biggest shift is a strong move away from a single do-everything device to multiple devices with overlapping functions and, above all, an inter-relationship with our other devices. An iconic example that many cite is that milk cartons—themselves carrying sensors or perhaps sitting on “smart” refrigerator shelves in people’s homes—will send signals to the homeowner or grocery stores when they are nearing empty and this information will be conveyed to the homeowner when she is conveniently near a store. Some respondents liked that; others thought that kind of progress would be less than cosmic.
Other examples of Internet of Things activities are:
•Subcutaneous sensors or chips that provide patients’ real-time vital signs to self-trackers and medical providers.
•Remote control apps that allow users’ phones to monitor and adjust household activities—from pre-heating the oven to running a bath to alerting users via apps or texts when too much moisture or heat is building up in various parts of the home (potentially alerting users to a leak or a fire).
•Smart cities where ubiquitous sensors and GPS readouts allow for vastly smoother flows of traffic; warnings and suggestions to commuters about the best way to get around traffic– perhaps abetted by smart alarm clocks synched to their owners’ eating and commuting habits and their day-to-day calendars.
•Sensored roadways, buildings, bridges, dams and other parts of infrastructure that give regular readings on their state of wear and tear and provide alerts when repairs or upgrades are needed.
•Vastly improved productivity in manufacturing at every stage, as supply chain logistics are coordinated.
•Paper towel dispensers in restrooms that signal when they need to be refilled. Municipal trash cans that signal when they need to be emptied. Alarm clocks that start the coffee maker.
•Smart appliances working with smart electric grids that run themselves or perform their chores after peak loads subside.
Many expect believe that a major driver of the Internet of Things will be incentives to try to get people to change their behavior—maybe to purchase a good, maybe to act in a more healthy or safe manner, maybe work differently, maybe to use public goods and services in more efficient ways. Every part of our life will be quantifiable, and eternal, and we will answer to the community for our decisions. For example, skipping the gym will have your gym shoes auto tweet (equivalent) to the peer-to-peer health insurance network that will decide to degrade your premiums.
_______
IoT Roadmap:
_____
Internet of Things Predictions:
According to IDC, IoT will go through a hug growth in the coming years in many directions:
1. IoT and the Cloud. Within the next five years, more than 90% of all IoT data will be hosted on service provider platforms as cloud computing reduces the complexity of supporting IoT “Data Blending”.
2. IoT and security. Within two years, 90% of all IT networks will have an IoT-based security breach, although many will be considered “inconveniences.” Chief Information Security Officers (CISOs) will be forced to adopt new IoT policies.
3. IoT at the edge. By 2018, 40% of IoT-created data will be stored, processed, analyzed, and acted upon close to, or at the edge, of the network.
4. IoT and network capacity. Within three years, 50% of IT networks will transition from having excess capacity to handle the additional IoT devices to being network constrained with nearly 10% of sites being overwhelmed.
5. IoT and non-traditional infrastructure. By 2017, 90% of datacenter and enterprise systems management will rapidly adopt new business models to manage non-traditional infrastructure and BYOD device categories.
6. IoT and vertical diversification. Today, over 50% of IoT activity is centered in manufacturing, transportation, smart city, and consumer applications, but within five years all industries will have rolled out IoT initiatives.
7. IoT and the Smart City. Competing to build innovative and sustainable smart cities, local government will represent more than 25% of all government external spending to deploy, manage, and realize the business value of the IoT by 2018.
8. IoT and embedded systems. By 2018, 60% of IT solutions originally developed as proprietary, closed-industry solutions will become open-sourced allowing a rush of vertical-driven IoT markets to form.
9. IoT and wearable. Within five years, 40% of wearables will have evolved into a viable consumer mass market alternative to smartphones.
10. IoT and millennials. By 2018, 16% of the population will be Millennials and will be accelerating IoT adoption due to their reality of living in a connected world. Millennials are people born between early 1980s to early 2000s who are digitally native, generally enjoy living and working in urban areas. These are people of internet generation.
______
______
My view:
The consumer IoT is synonymous with functions that affect human-perceived comfort, security, and efficiency. Fitbit are activity trackers, wireless-enabled wearable technology devices that measure data such as the number of steps walked, heart rate, quality of sleep, steps climbed, and other personal metrics. Nest is a programmable, self-learning, sensor-driven, Wi-Fi-enabled thermostat and smoke detector. Smart refrigerator is a refrigerator which has been programmed to sense what kinds of products are being stored inside it and keep a track of the stock through barcode or RFID scanning. This kind of refrigerator is often equipped to determine itself whenever a food item needs to be replenished. The milk is running out of stock, so the fridge has sent a message to your phone. Your phone knows that you’re in the supermarket and has told your trolley. Your shopping trolley vibrates, and the screen mounted on the trolley handles displays a message: “There is no milk in your fridge. Would you like to purchase some?” Your trolley knows you’re next to the milk fridge in the supermarket and has told you that you’re out of milk. So, you buy milk.
_
Would it be useful to me?
An organised person is someone who never loses or forgets anything, who knows where everything is, who always has time to do things etc. A systematic person is someone who performs, organizes, or acts in a systematic (orderly / methodical) way. I am a systematic organised person. Everything I do is methodical and organized. I remember what things are there in refrigerator, what to replenish and what to discard. Every day I make note of what to do tomorrow; whether it is bank or post or grocery or lecture. IoT will be of little use to me. I am sure there are millions of people in the world who are systematic and organised. They may find IoT useless. On the other hand, there are billions of people in the world who are neither systematic nor organised. They will be immensely benefitted by IoT. For the IoT to deliver on its potential, billions of devices must be able to capture, process, analyze, and store massive amounts of data; and memory technologies are critical to the flow of that data in the connected world as memory plays a vital role in building the connected world. IoT will be extremely helpful to those with fallible memory.
_
Machines are able to make very good decisions at rapid pace. Their ability has been previously limited by the information available to them. As you combine information from multiple sources and they are synchronized on the same timeline, you’ll start to see machines making smarter and smarter decisions, anticipating things to a high degree. For example, a traditional “dumb” thermostat consists of only a sensor and an actuator — when the temperature goes out of the desired range, the heat or air conditioning goes on. The addition of a network, the ability to control your thermostat from your smartphone, say, turns it into a simple IoT device. But consider the Nest thermostat: where it stands out from the crowd of connected thermostats is that it uses a complex of sensors (temperature, moisture, light, and motion) as well as both onboard and cloud software to provide a rich and beautiful user interface with a great deal more intelligence. While you can schedule your heating manually, you can also let the Nest “learn” when you get up in the morning and turn on the heat, and when you go to bed and turn it off. After a week or so, it will “understand” and repeat the pattern. When you are away, the Nest will notice the absence of movement and automatically turn off the heat. Well, it looks nice. Nest is doing everything that you could do because you are not a systematic and organised person. Nest is covering up your mediocrity and laziness.
_
There are two distinct aspects of human intellect, namely fluid and crystallized intelligence. Fluid intelligence refers to the ability to acquire and process information. In computers, this would be the processing speed and RAM capacity — the more you have, the faster and more effortlessly you can multi-task, and the higher the quantity and complexity of stuff you can handle. Evidence suggests that — in humans — fluid intelligence has been increasing for decades (what psychologists refer to as the Flynn effect). The average child from 1950 would be handicapped by today’s standard IQ tests, and the average child today would be gifted by 1950s standards… but that just in terms of their fluid intelligence or ability to process complex information quickly and effectively. The second aspect of intellect — crystallized IQ — refers not to our ability to gather info but what we actually know; in simple terms, crystallized intelligence means knowledge. Unsurprisingly, with all the knowledge of the world being now outsourced, crowdsourced, cloudsourced and IoTsourced, the individual storage of information is minimal (at least in comparison). Humans today are like most smartphones and tablets – their ability to solve problems depends not on the knowledge they can store but on their capacity to connect to a place where they can retrieve the answer to find a solution. The only knowledge we need to have is the knowledge of where to find stuff. IoT will make everything autonomous and automatic so that our fluid and crystallized intelligence will become redundant. Of course, if you have lower intelligence in the first place, IoT will make your life easy and convenient. But for people with higher intelligence, IoT will make their intelligence redundant.
_
In a nutshell, consumer IoT (everyday consumer-level smart devices connected to one another) will maximally benefit people who are neither systematic nor organised; and those with fallible memory. For those who have excellent memory, who have systematic and organized approach to life, consumer IoT will be of little use. If you have lower intelligence in the first place, IoT will make your life easy and convenient. But for people with higher intelligence, IoT will make their intelligence redundant.
__________
__________
Moral of the story:
_
1. The basic idea of the internet of things (IoT) is everyday object can also become a computer that is connected to the Internet. To be more accurate, objects themselves do not turn into computers, but they feature tiny low-end computers (in most cases, these cannot interact directly with human beings) which connect them to internet, and objects without embedded tiny low-end computers connect internet using RFID, NFC, QR codes, sensor etc. through a gateway. IoT allows network connectivity and computing capability to everyday objects not normally considered computers, allowing these devices to generate, exchange and consume data with minimal human intervention.
_
2. Any everyday object/device/product which has in-built ability to connect to internet to transmit and/or receive data either directly or indirectly, with or without data storing/processing ability, is a smart (intelligent) object/device/product within the description of IoT.
_
3. ‘Things’ in IoT are physical or virtual objects that can be tagged, sensed, networked and made intelligent or autonomous. Although physical objects do have virtual counterpart in IoT, there are some primary virtual objects without any physical counterparts, for e.g. electronic tickets, agendas, books, and wallets. Humans, animals (pets) and plants have also become part of the IoT through sensors, wearable devices and clothing.
_
4. The first version of Internet was about data created by people (humans are always there in the loop), while the next version (IoT) is about data created by things (humans are out of the loop mostly). The Internet revolution led to the interconnection between people at an unprecedented scale and pace. The IoT revolution will be the interconnection between objects to create a smart environment.
_
5. Common internet used by us every day connects only people i.e. human to human interaction. IoT includes not only machine to machine, but also human to machine and machine to human interactions.
_
6. M2M (machine-to-machine communication) is a subset of industrial IoT; industrial IoT is a subset of IoT; and IoT is a subset of IoE (Internet of Everything). Additionally, WoT (Web of Things) is a subset of IoT and common internet is a subset of IoE. Web is an application layer to the Internet; similarly, Web of Things is an application layer to the Internet of Things.
_
7. The evolution of IoT from internet due to technological advancement goes hand in hand with evolution of communication system and merging of physical world with virtual (digital) world.
_
8. IoT means RFID tags, sensors, actuators, microcontrollers etc. are embedded in physical objects to link them to internet making everyday objects readable, recognizable, locatable, addressable, and controllable via Internet mostly without human intervention. The IoT implies a symbiotic interaction among the real/physical and the digital/virtual worlds: things become context aware and they can sense, communicate, interact and exchange; data, information and knowledge. Computational capabilities could be at the device end (microprocessor/microcontroller) and/or back end (cloud analytics). Everyday object becomes somewhat intelligent and somewhat autonomous to take decisions, invoke actions and provide amazing services. IoT describes a world where just about anything can be connected and communicate in an intelligent fashion to enable their remote, real-time monitoring; to enable vast collection, storage, usage, and sharing of information about them in order to provide a service to the user and to enable increase in efficiency & productivity. IoT devices benefit the user by saving money and time, improving quality of life, and increasing convenience.
_
9. In total, there will be 30 to 50 billion devices connected to the internet by 2020; out of them two third will be IoT devices and one third will be traditional computing devices (e.g. smartphones, tablets, laptops etc.). Smart phones are not classified as IoT devices but act as hub or remote control/access for IoT.
_
10. Although the concept of combining computers, sensors, and networks to monitor and control devices has existed for decades, what IoT technology include is ubiquitous connectivity, widespread adoption of IP-based networking, computing economics, miniaturization, advances in data analytics, and rise of cloud computing.
_
11. Internet of Things has three major components: Hardware (including computer chips and sensors), Communication / Protocols (including mostly some form of wireless network), and Software (including data storage, analytics, and front end applications).
_
12. Implementation of IoT is based on an architecture consisting of several layers from the field data acquisition layer at the physical objects/device level to the application layer at user level. IoT middleware is software that serves as an interface between components of the IoT, making communication possible among elements that would not otherwise be capable. Middleware layer is one of the most critical layers that operates in bi-directional mode and acts as an interface between the hardware layer at the edge and the application layer at the user. The IoT platform (type of middleware) provide numerous functions, such as access to devices, ensuring the proper installation and behavior of the device, data analytics, and interoperable connection to the local network, cloud, or other devices.
_
13. Typical IoT devices consume low power and typical IoT speed (data transfer rate) is slow in Kb/s; while typical internet devices (smartphone/ laptop/ tablet) consume high power and typical internet speed is fast in Mb/s.
_
14. IoT generates ‘Big Data’ and we need to distinguish between useful and redundant data by improving data analytics either at edge or at cloud level. Computing at edge has advantage of real time action plus saving money & time for not sending to cloud. On the other hand, cloud-IoT has advantage of unlimited data storage and analysis. The limitations of IoT in terms of storage, network & computing, complex analysis, scalability and data access require cloud computing to supplement this field. Big Data is processed with advanced analytics, transformed into predictive algorithms, and programmed into automated systems to improve efficiencies, increase productivity, and reduce cost and waste. By 2018, 40% of IoT-created data will be stored, processed, analyzed, and acted upon close to or at the edge of the network.
_
15. Widespread Wi-Fi and cellular networks provide universal and transparent access to the Internet and cloud-powered applications driving the success of mobile computers, including laptops, tablets, and smartphones. The coming wave of tiny, embedded, low-power, wireless, mobile, and wearable devices of the IoT, however, does not currently enjoy the same level of ubiquitous and universal access to the Internet due to necessity of an application layer gateway. Currently a separate physical router or a smartphone app is required for each IoT device to connect to internet. This contrasts with any mobile computer’s ability to connect to internet from single Wi-Fi router. Opening a new webpage on smart phone does not require a new app, but IoT devices are different for healthcare, air-conditioning and windmill; therefore would need different apps on smartphone.
_
16. If the IoT would like to follow the successful path of the classical Internet, its architecture would have to make sure that any tagged object could in principle be accessed by any computer. For that, a global standard protocol having identification & addressing scheme for bridging the last mile from Internet to smart things would be required.
_
17. Major challenges facing IoT include big data management, power efficiency, bandwidth limitation, interoperability, privacy, security and lack of legal framework or policy regulation for IoT network.
_
18. Lack of awareness and knowledge about IoT prevents widespread adoption of IoT by consumers. Top adopters of IoT solutions will be businesses and governments rather than consumers.
_
19. IoT finds applications in nearly every field right from smart wearable to smart home to smart grid to smart city to smart health to smart retail to smart business to smart infrastructure to smart manufacturing to smart transportation to smart aviation to smart agriculture to smart environment to smart waste management to smart media to smart government to smart living. IoT applications spread from fixed to mobile applications and from concentrated to dispersed applications. Smart home and smart wearable are the most popular IoT applications. Socio-economic impact of the connected life will be great.
_
20. The “smart applications” can bring some improvement in the quality of life of common citizens, but they are developed for separated (“vertical”) scenarios, which is in contrast to the universal, seamless (“horizontal”) vision of IoT. In the vertical business model, the IoT device, the gateway (if used), and the cloud-based service are all provided and controlled by the same company so that there are no compatibility issues to deal with among the various elements, and a single point of contact to deal with if anything goes wrong. The ‘Smart Life’ vision requires moving from a mere collection of such vertical scenarios to a seamless, pervasive and ubiquitous horizontal domain by overcoming lack of interoperability due to incompatible or proprietary technologies.
_
21. In democracy, government functions as per people’s wish. In the years ahead, much of that people’s wish will be represented by IoT devices that collect volumes of behavioural information about public preferences; and these data will be used by government to change its policies. In other words, IoT will change the way democracy functions.
_
22. Sensors are still expensive, battery life remains an issue, data transmission is not seamless, wireless coverage is not ubiquitous, bandwidth is limited, location data is problematic, and in most cases large data streams cannot yet be analysed instantly. The ability to process big data and extract meaningful information is also limited. These are the limitations of IoT.
_
23. IoT big data grows at an exponential pace while networks grow at a linear pace because data is abstract and networks are physical. A day may come when big data becomes too much to be handled by networks resulting in breakdown of internet.
_
24. Many innocent-looking IoT devices may be spying on you at the behest of your government.
_
25. IoT will lead to greater dependence on the underlying technology. If the technology infrastructure failed for whatever reason – design faults, material defects, sabotage, overloading, natural disasters or crises – it could have a disastrous effect on the economy and society. On the other hand, if the technology works very well, we become fully dependent on technology resulting in technological paternalism where smart objects might not behave as we would wish, but rather as they “believe” is best for us. Also automation of IoT will have a devastating impact on the employment prospects of less-educated workers.
_
26. Consumer IoT will maximally benefit people who are neither systematic nor organised; and those with fallible memory. For those who have excellent memory, who have systematic and organized approach to life, consumer IoT will be of little use. If you have lower intelligence in the first place, consumer IoT will make your life easy and convenient. But for people with higher intelligence, consumer IoT will make their intelligence redundant.
________
Dr. Rajiv Desai. MD.
July 19, 2016
_______
Postscript:
The English word ‘smart’ has got a new meaning. We have smart refrigerator, smart washing machine, smart wearable, smart home and smart city. Smart means connected, intelligent and autonomous. What about smart husband or smart wife?
_______

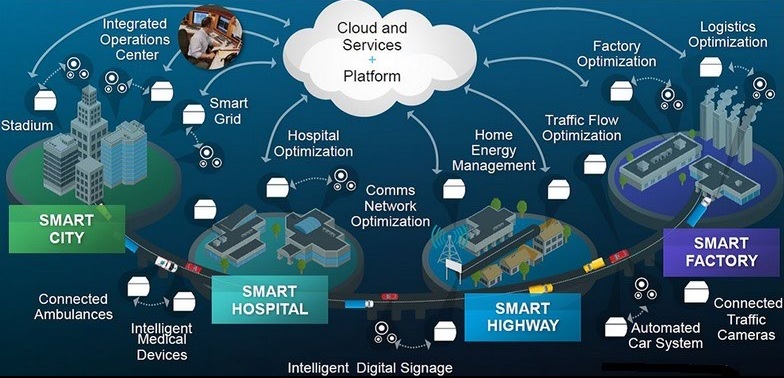
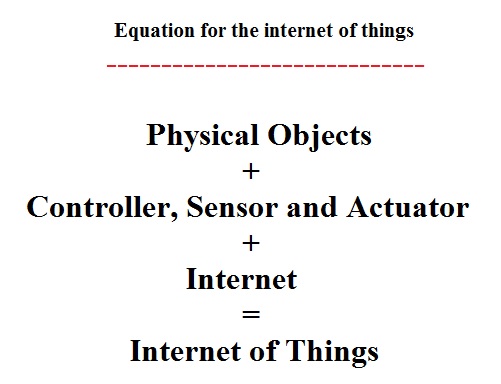
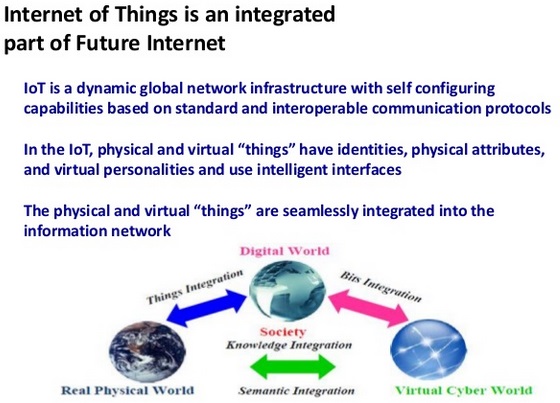
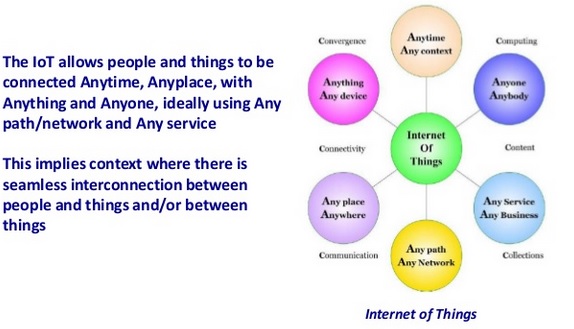
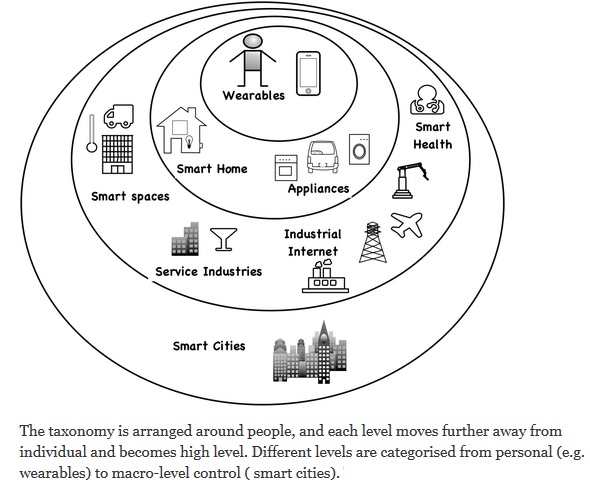
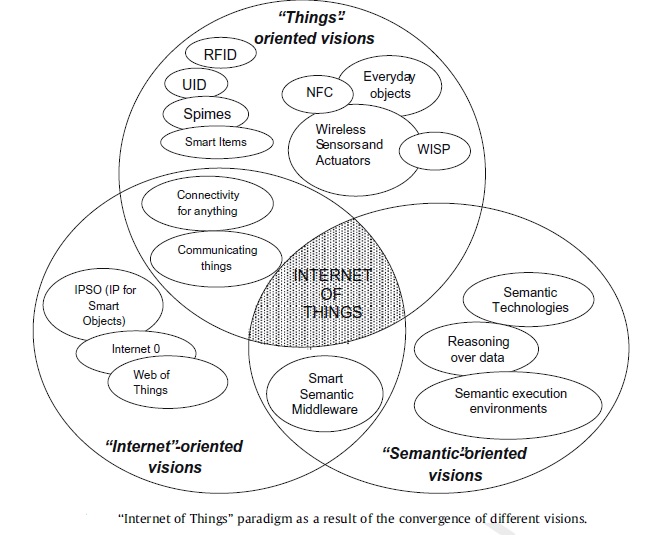
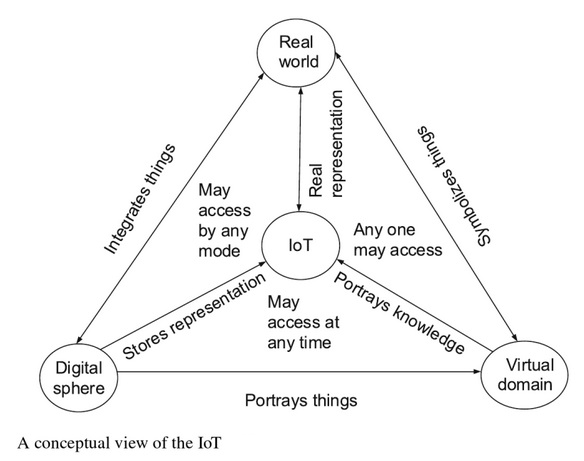
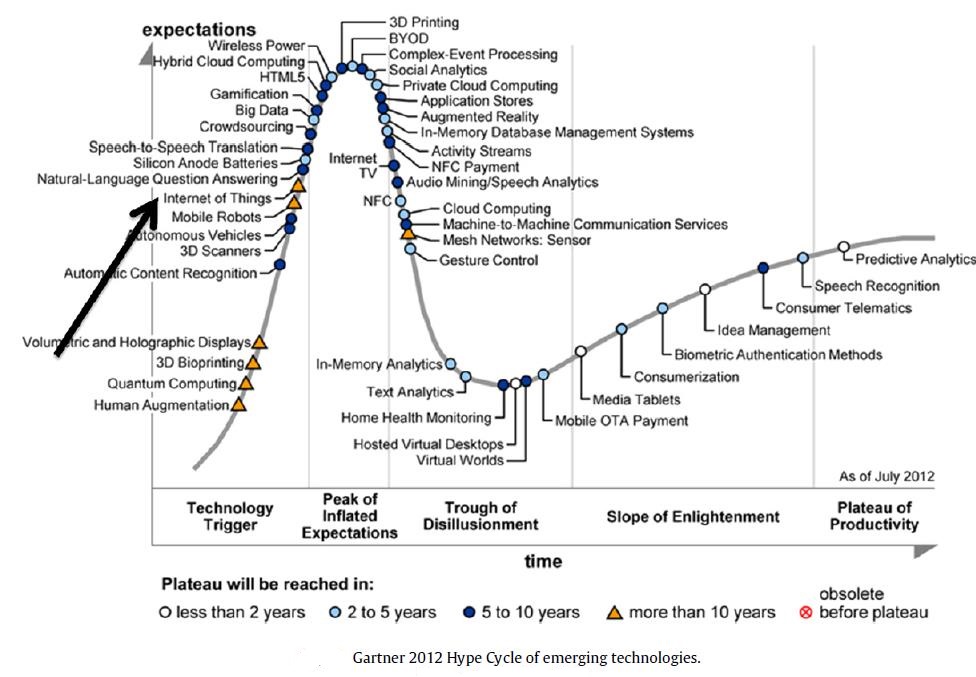
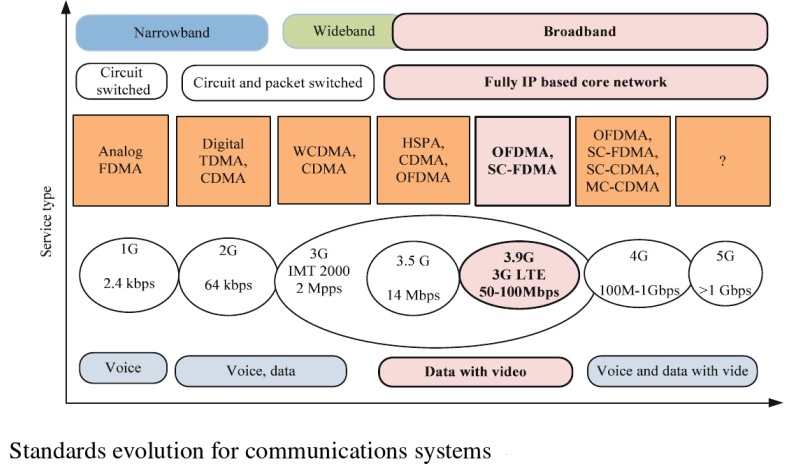

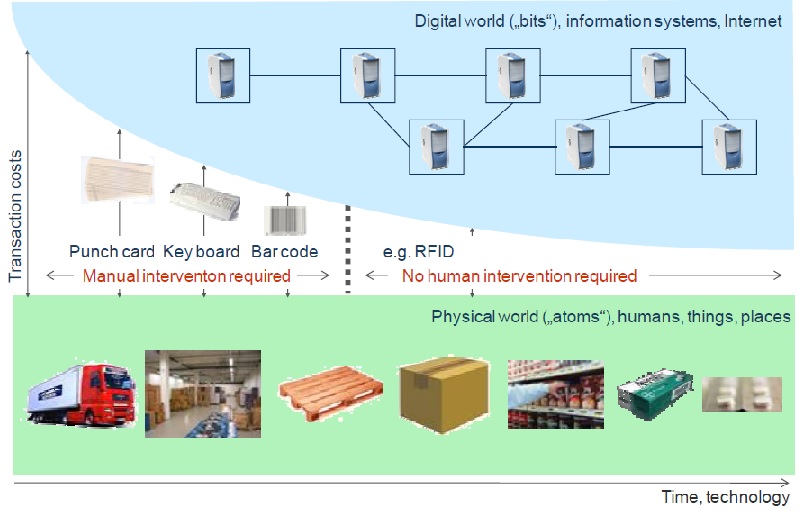
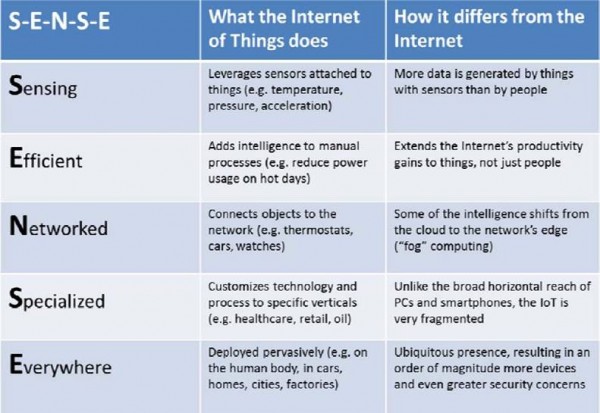
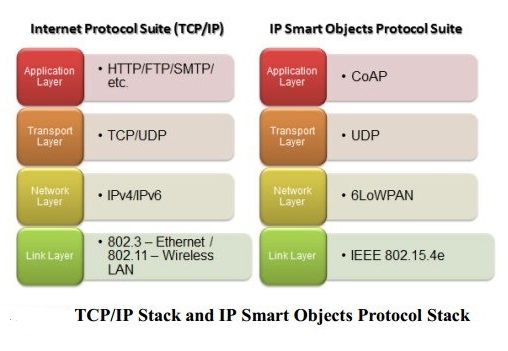
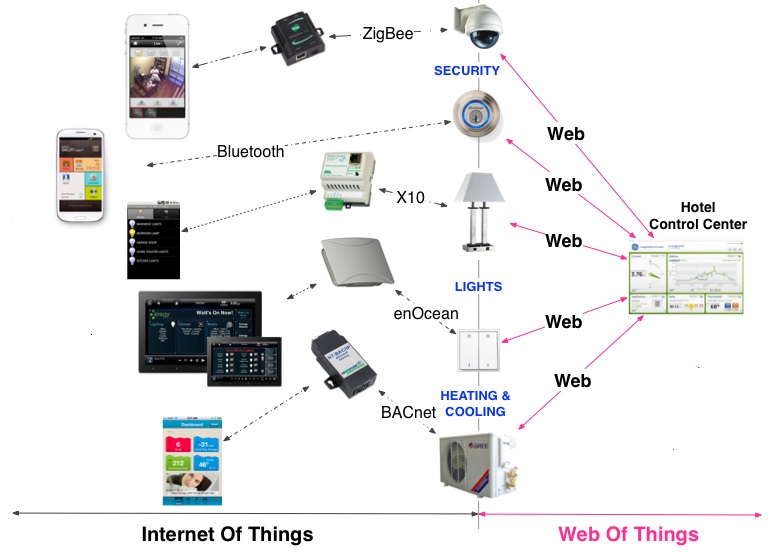
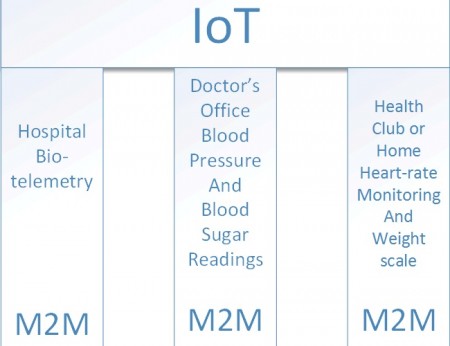
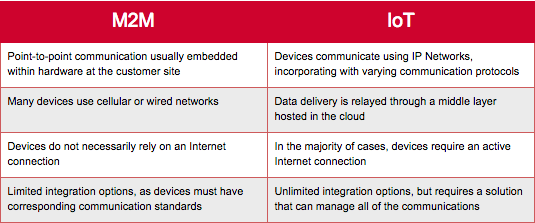

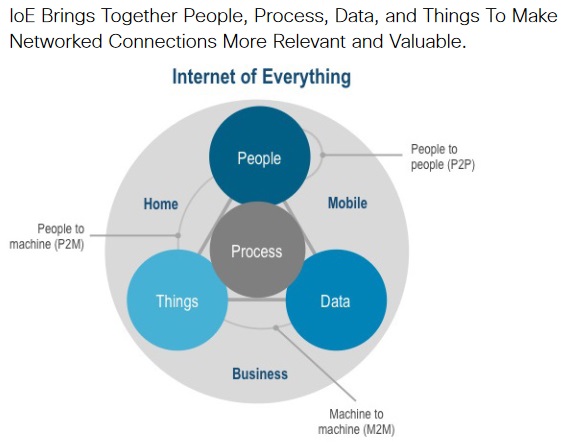
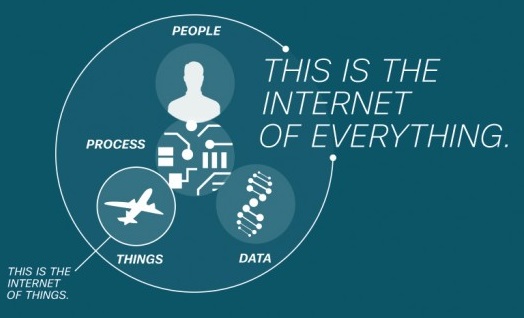
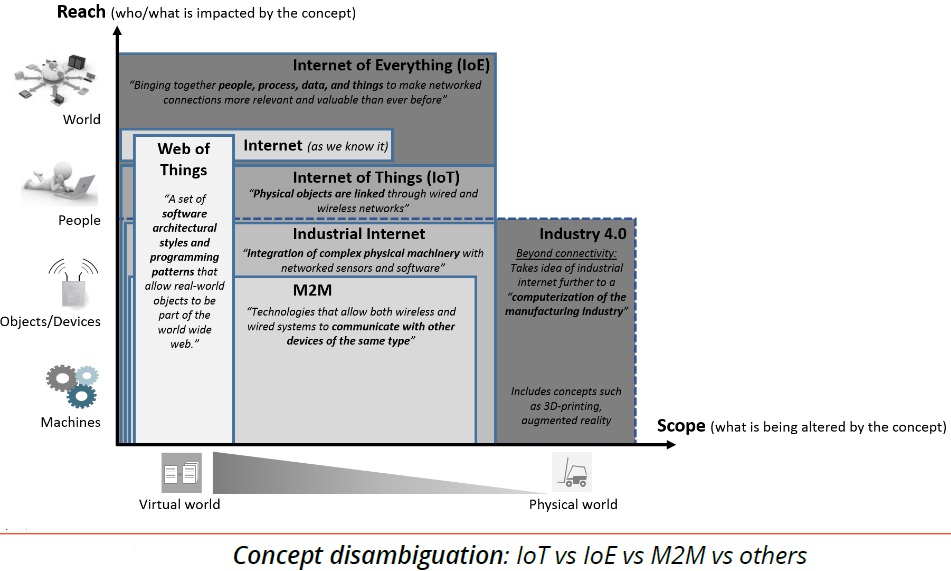
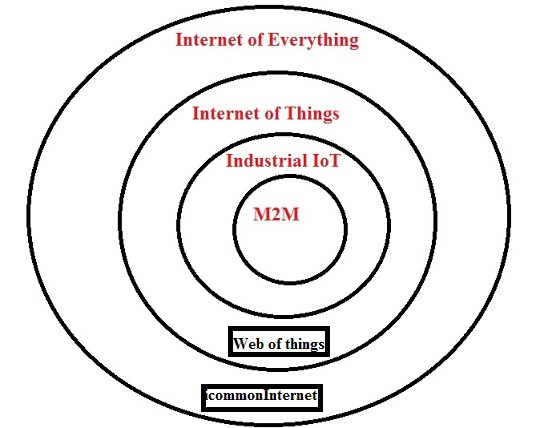
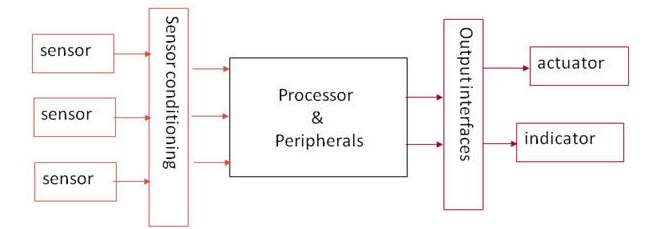
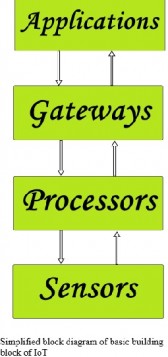
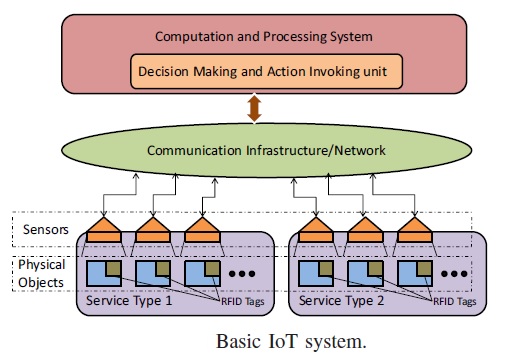
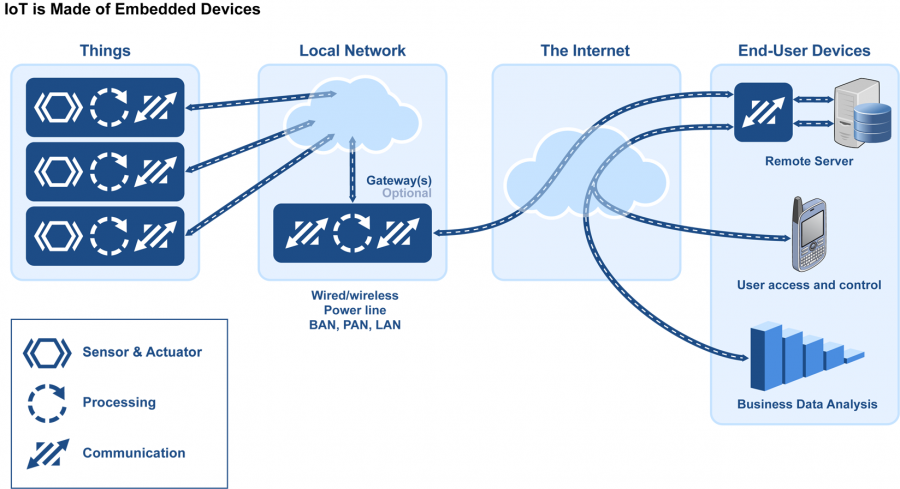
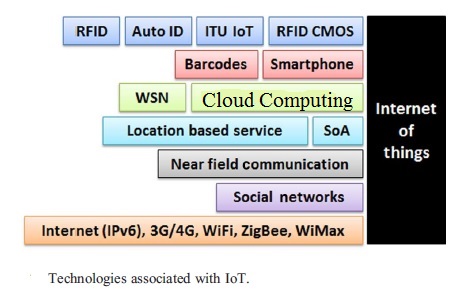
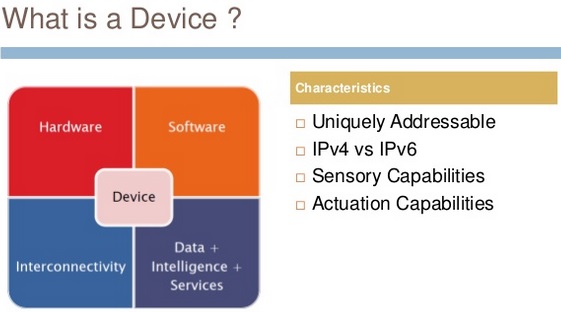

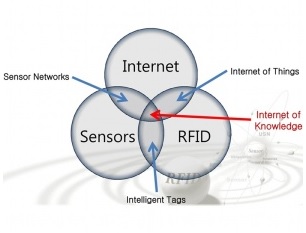
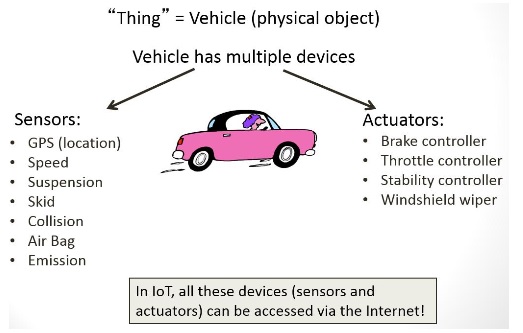
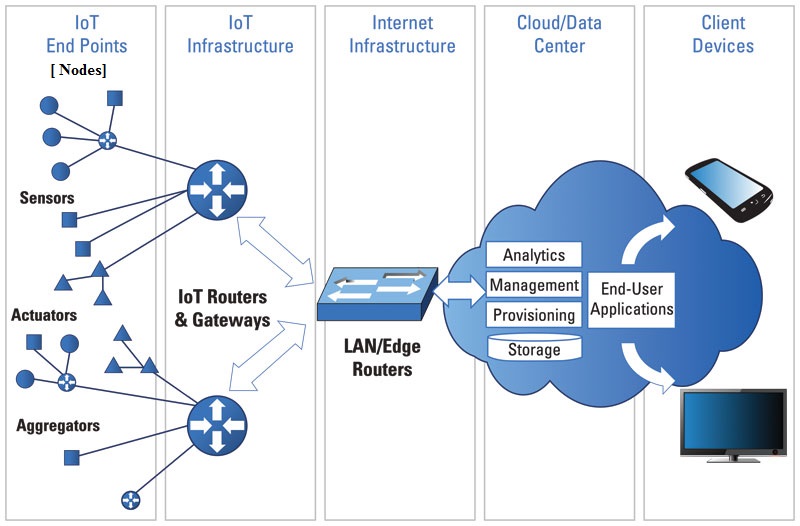
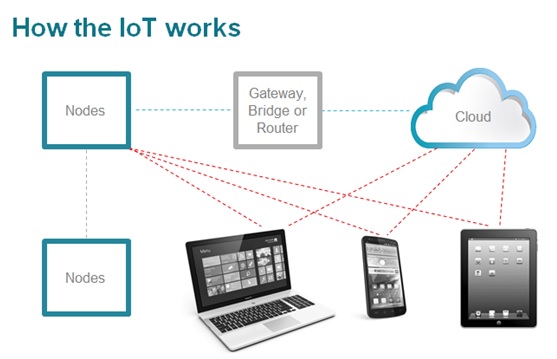

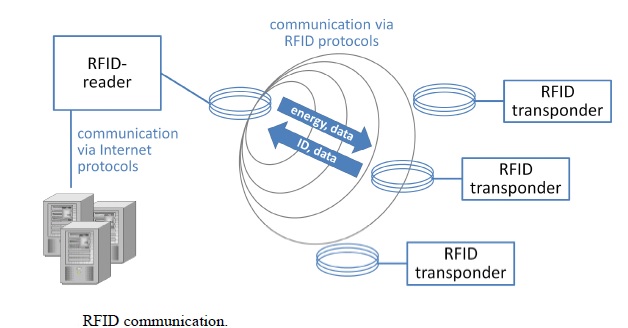
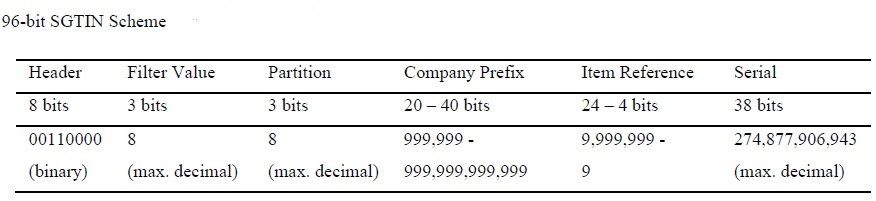
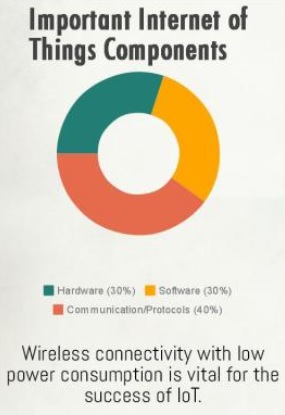
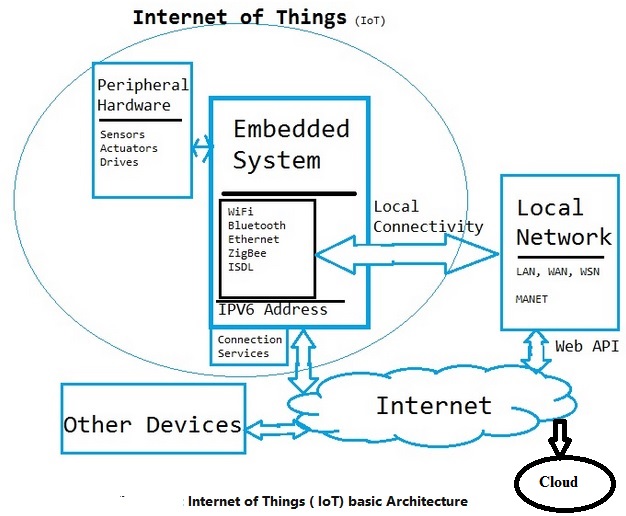
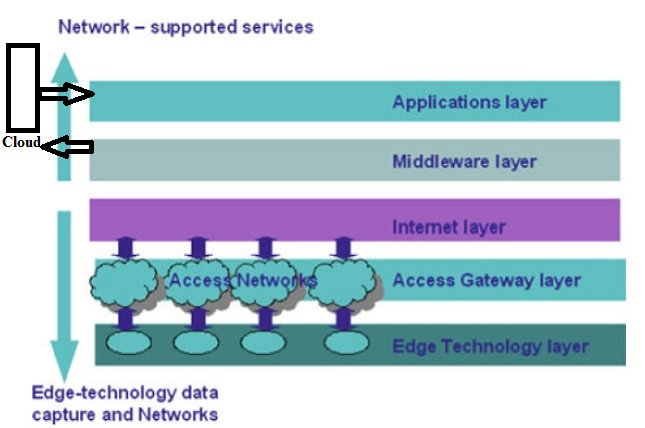
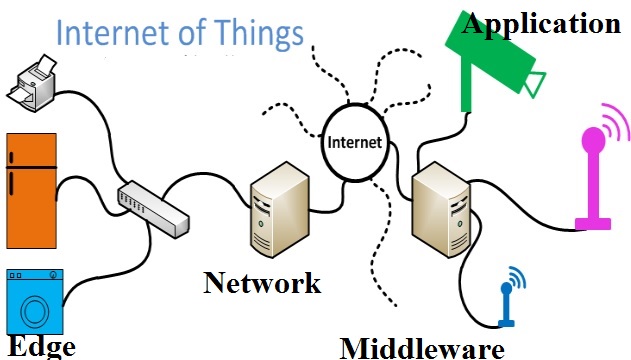
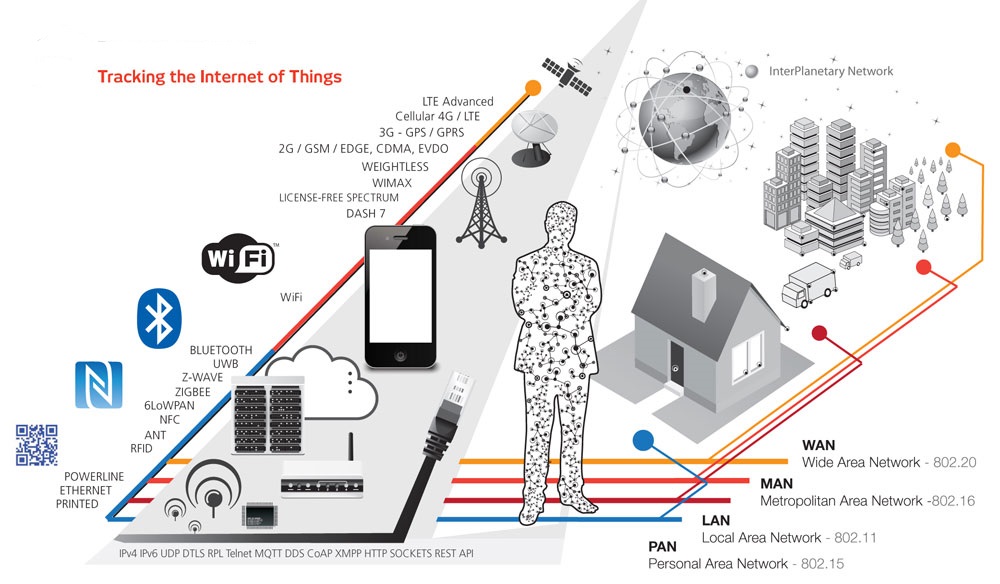
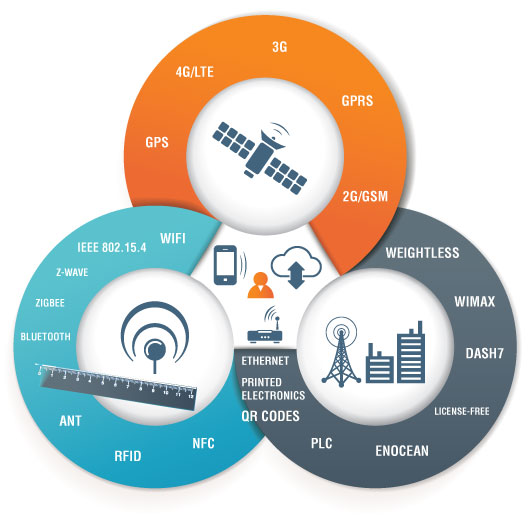
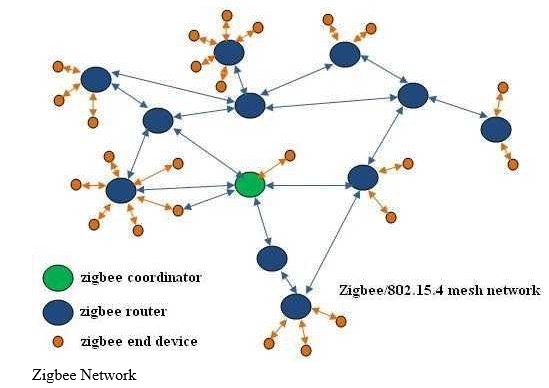
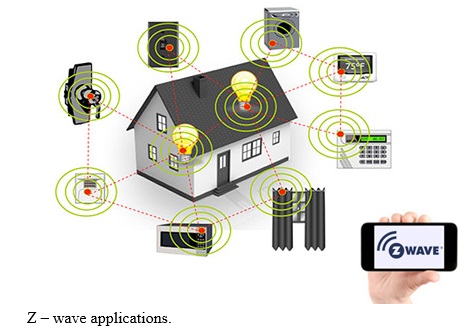
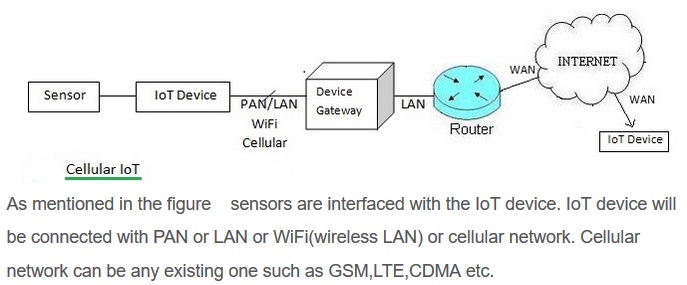
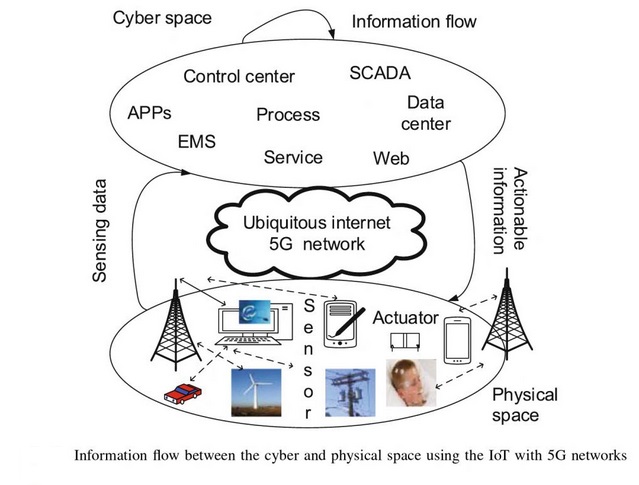
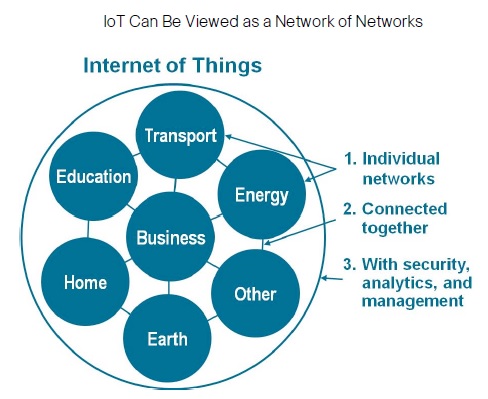
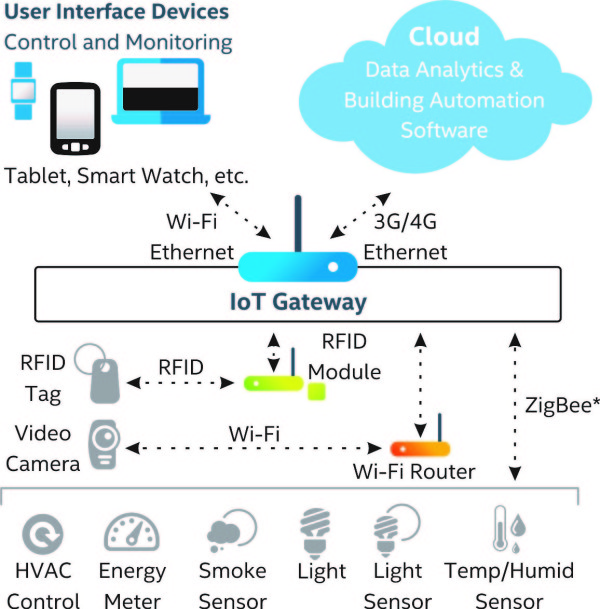
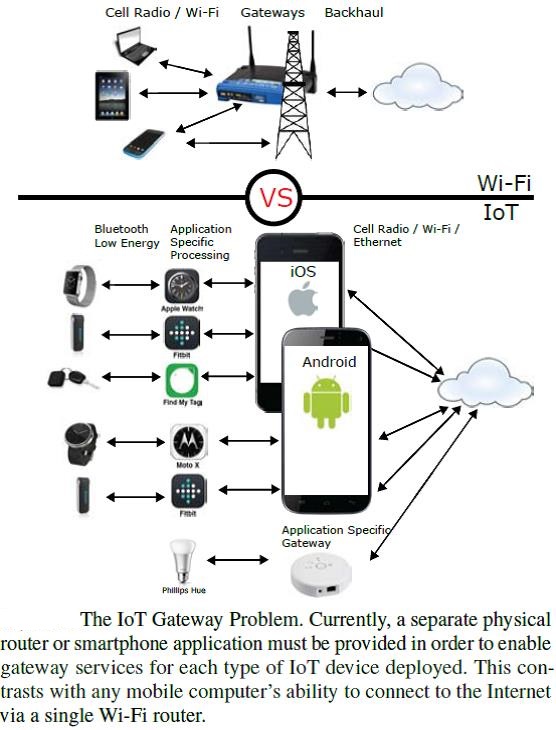
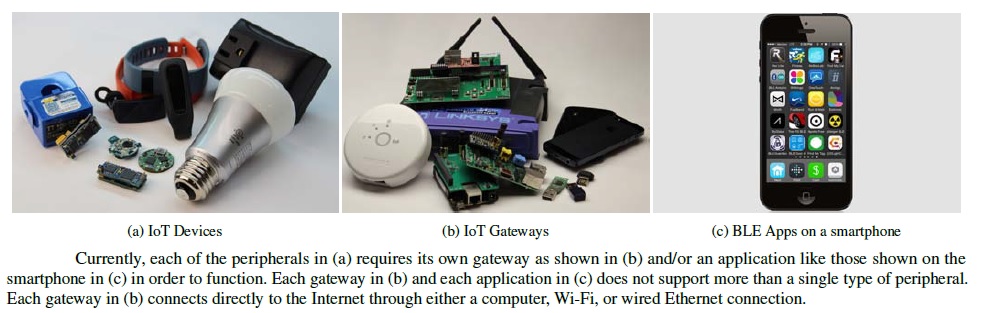
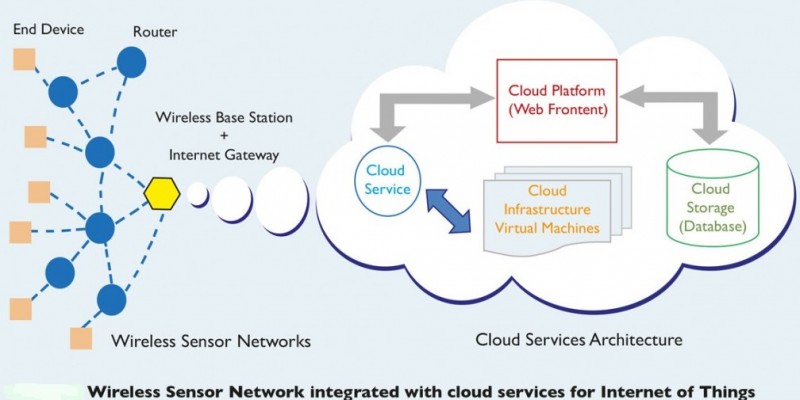
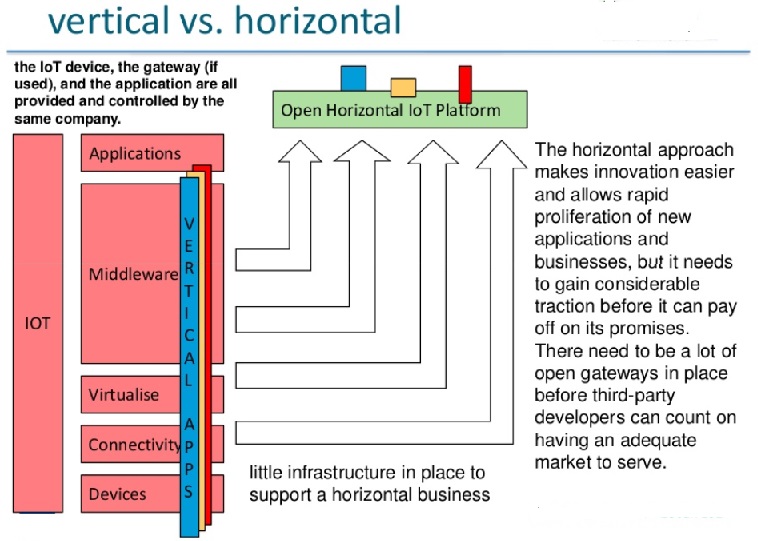
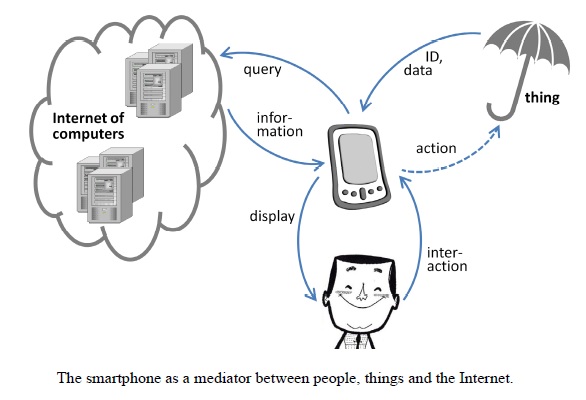
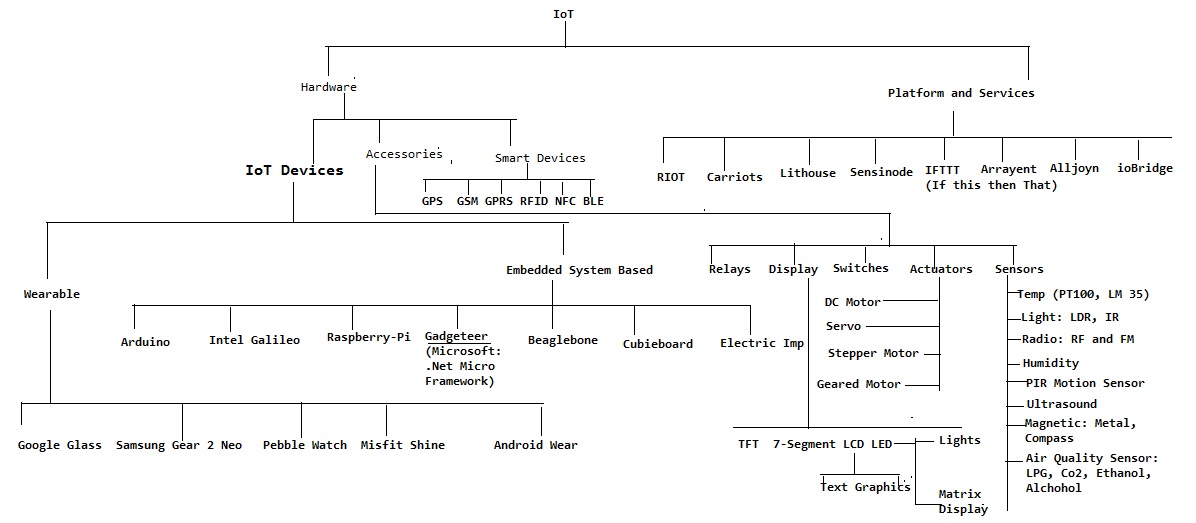
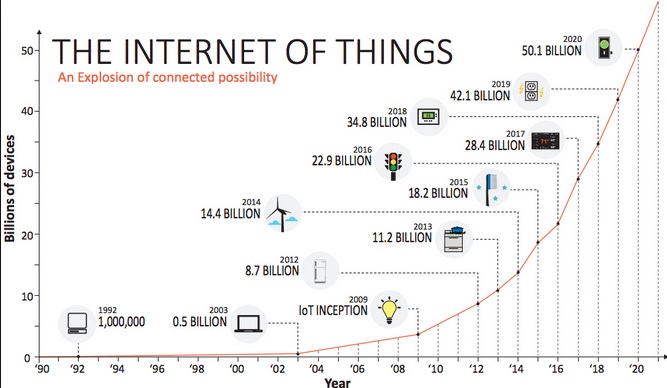
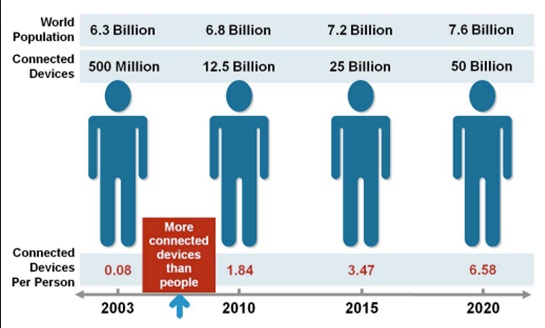
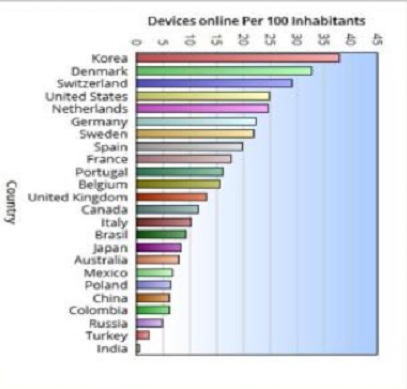
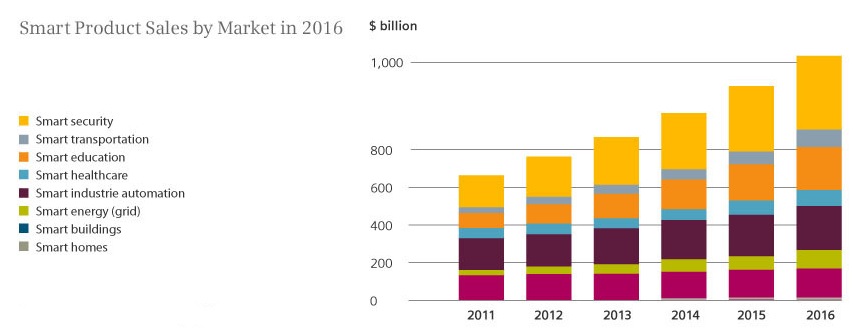
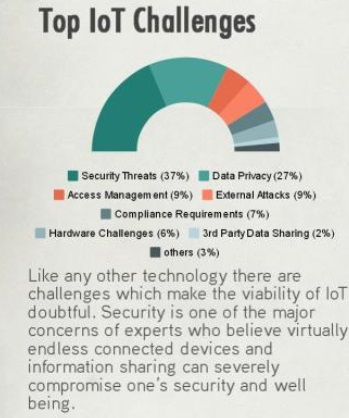
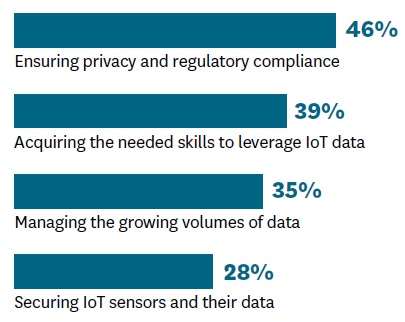
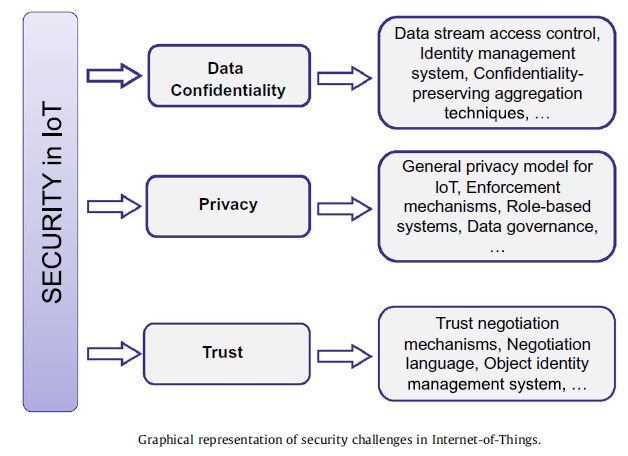
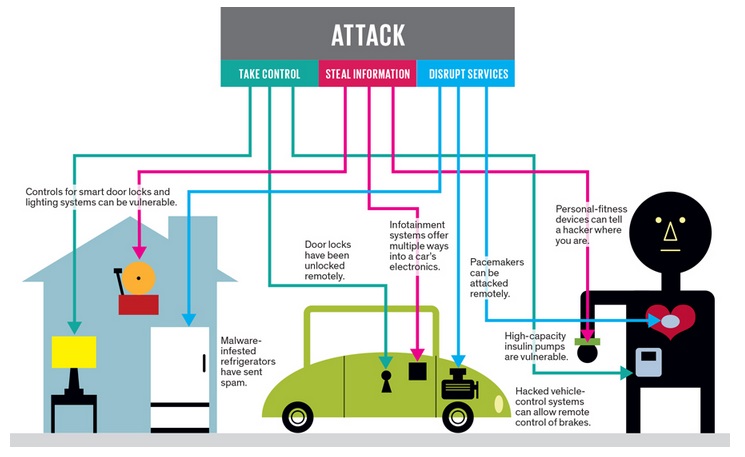
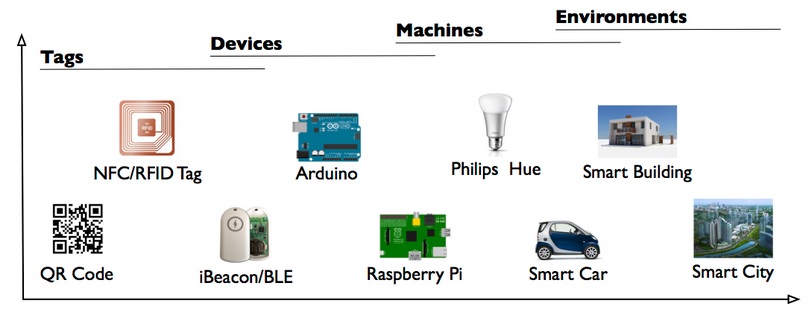
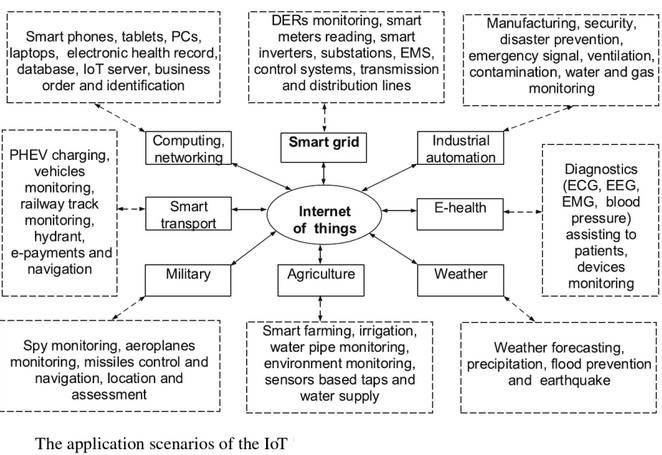
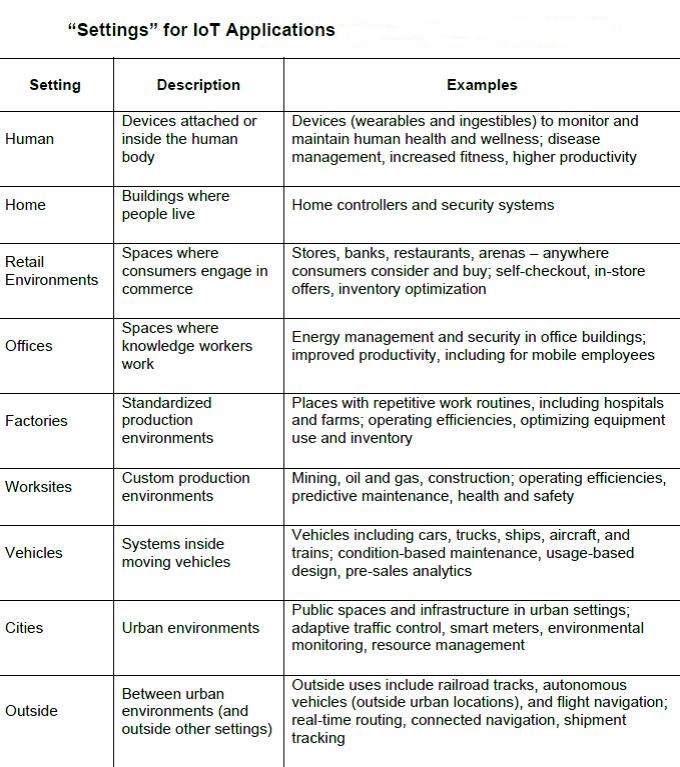
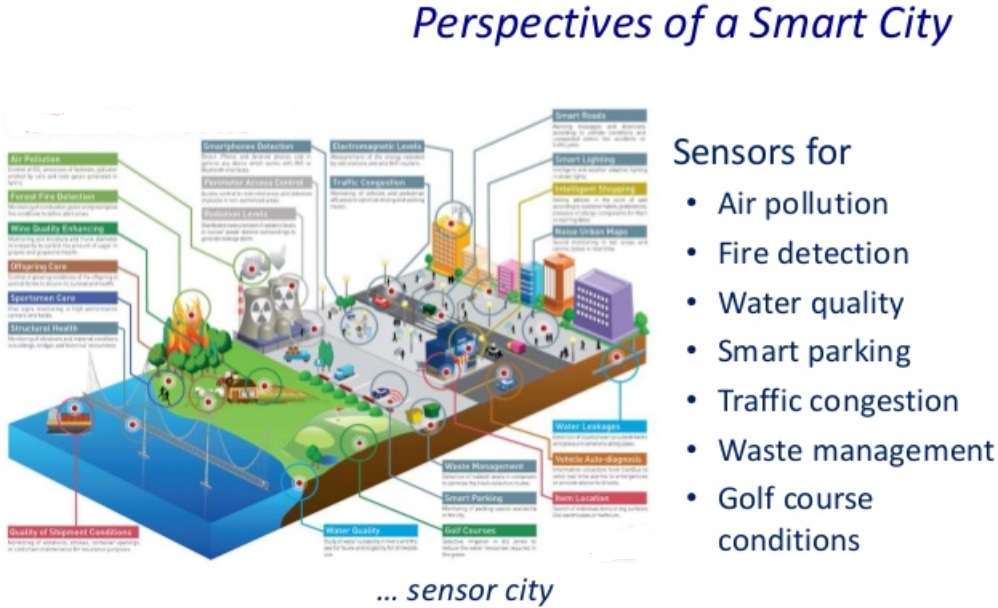
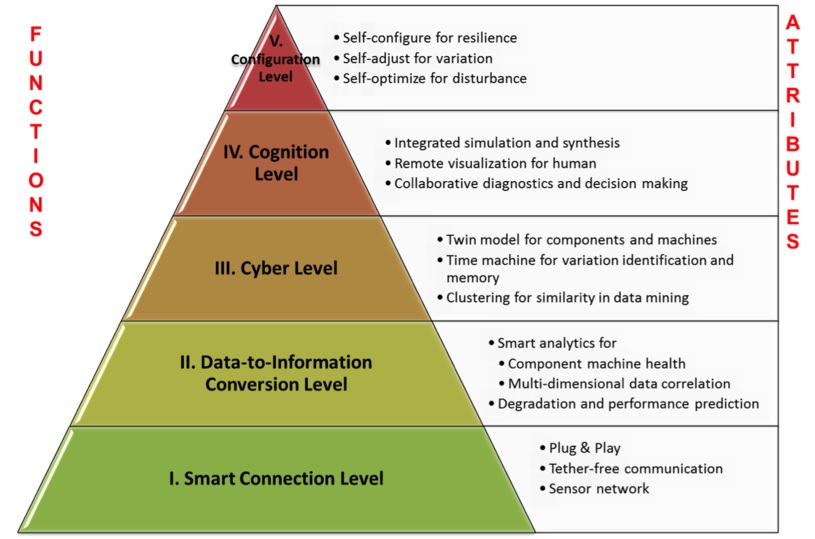
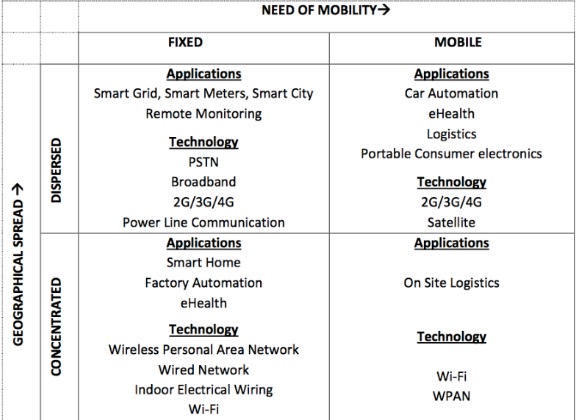
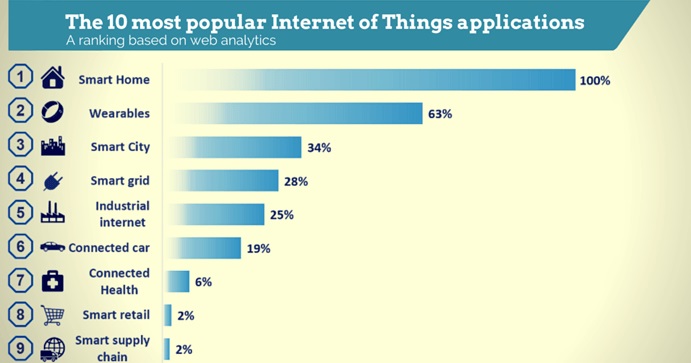
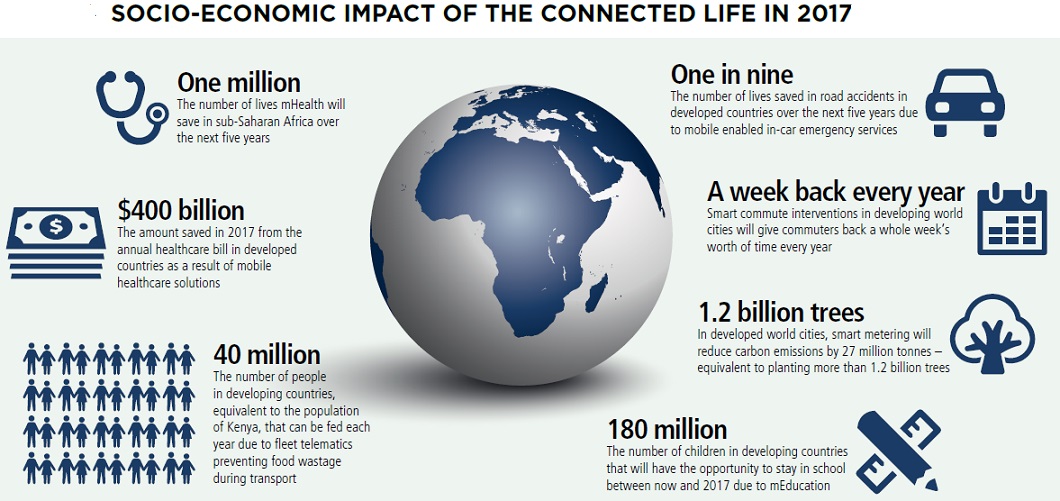
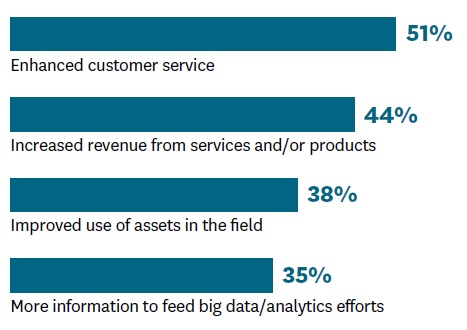
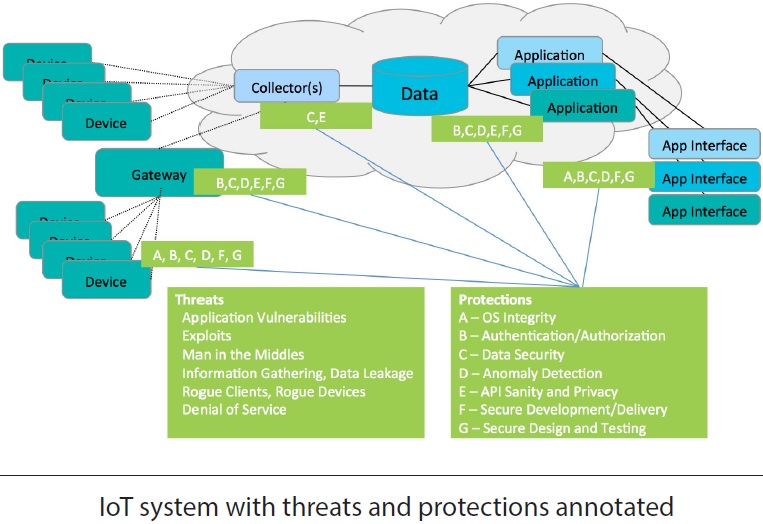
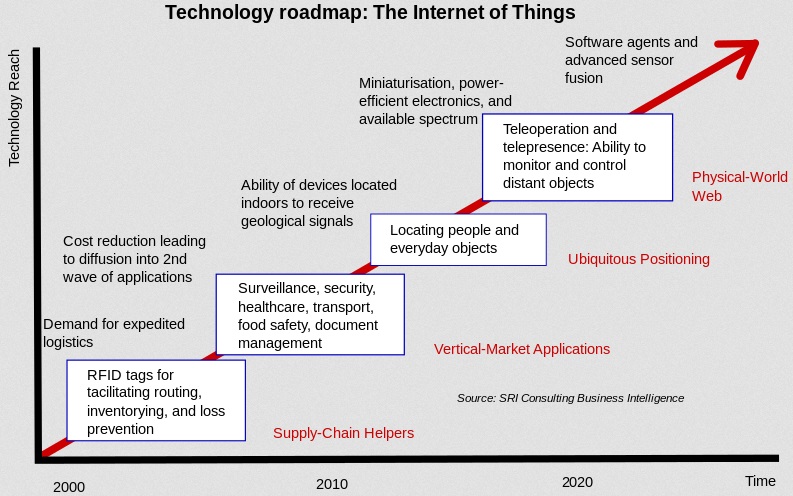
What are you stating, man? I recognize everyones got their own opinion, but really? Listen, your website is awesome. I like the work you put into it, especially with the vids and the pics. But, come on. Theres gotta be a better way to say this, a way that doesnt make it seem like everybody here is stupid!
I was so glad to find you through Google. This is preciselywhat I was searching for.
There is noticeably a lot of money to know about this. I suppose you have made certain nice points in features also.
Very nice post. I just stumbled upon your blog and wanted to say that I’ve really enjoyed browsing your blog posts. After all I will be subscribing in your feed and I am hoping you write again soon!|
Hi there, every time i used to check blog posts here early in the dawn, since i love to learn more and more.|
Your writing reflect your authenticity, making readers feel connected as if engaged in a meaningful conversation.
I just could not depart your website prior to suggesting that I really enjoyed the standard info a person provide for your visitors? Is going to be back often in order to check up on new posts
I’d need to examine with you here. Which is not one thing I often do! I get pleasure from reading a submit that may make people think. Also, thanks for allowing me to remark!
I simply couldn’t go away your web site before suggesting that I really loved the usual information an individual provide for your guests? Is gonna be back frequently to check out new posts
wow, awesome blog article.Thanks Again.
Whats up very cool website!! Guy .. Beautiful .. Amazing .. I will bookmark your web site and take the feeds also? I am satisfied to search out a lot of helpful info here within the publish, we need work out more strategies on this regard, thanks for sharing. . . . . .|
After looking at a handful of the blog posts on your blog, I really appreciate your technique of writing a blog. I saved it to my bookmark website list and will be checking back soon. Please check out my web site as well and let me know how you feel.
Exceptional ability to get things done.
Your excitement encourages others to do their ideal. I appreciate your nerve and decision.
The one you must have but didn’t learn about!
Quality articles or reviews is the secret to interest the viewers to visit the site, that’s what this web site is providing.|
It’s that time once again to obtain everything done in a extremely brief amount of time.
End up being a master in everything with this!
I really enjoy the post.Much thanks again. Really Cool.
Way cool! Some very valid points! I appreciate you writing this write-up and also the rest of the site is really good.
An intriguing discussion is worth comment. I believe that you ought to write more about this topic, it may not be a taboo subject but generally people do not discuss these issues. To the next! Kind regards!!
There is definately a great deal to find out about this issue. I really like all of the points you have made.
Everything is very open with a very clear explanation of the issues. It was really informative. Your website is useful. Thanks for sharing!
Excellent blog post. I certainly appreciate this site. Stick with it!
This is a topic that is near to my heart… Take care! Where are your contact details though?
Nice post. I learn something totally new and challenging on sites I stumbleupon on a daily basis. It’s always exciting to read through content from other authors and practice a little something from other web sites.
This is a topic that is close to my heart… Best wishes! Where are your contact details though?
Everything is very open with a very clear explanation of the challenges. It was definitely informative. Your website is very helpful. Thank you for sharing!
Pretty! This has been an incredibly wonderful article. Thanks for providing this info.
Pretty! This was an extremely wonderful post. Thank you for providing these details.
You are so interesting! I don’t suppose I’ve read through a single thing like that before. So good to find another person with a few unique thoughts on this topic. Really.. thank you for starting this up. This web site is something that is needed on the internet, someone with a bit of originality!
Your place is valueble for me. Thanks!…
Pretty! This has been an incredibly wonderful post. Thank you for supplying this information.
Good post. I learn something totally new and challenging on sites I stumbleupon everyday. It will always be helpful to read content from other authors and practice a little something from their sites.
Hi there! This article could not be written any better! Looking through this post reminds me of my previous roommate! He constantly kept preaching about this. I’ll send this information to him. Pretty sure he will have a great read. Thanks for sharing!
An impressive share! I have just forwarded this onto a friend who has been doing a little homework on this. And he in fact ordered me breakfast due to the fact that I found it for him… lol. So let me reword this…. Thank YOU for the meal!! But yeah, thanx for spending time to talk about this topic here on your blog.
Way cool! Some very valid points! I appreciate you penning this article and also the rest of the website is really good.
That is a very good tip especially to those new to the blogosphere. Short but very accurate information… Thank you for sharing this one. A must read article!
This page definitely has all the information I needed concerning this subject and didn’t know who to ask.
Very good information. Lucky me I ran across your blog by chance (stumbleupon). I’ve bookmarked it for later!
thanks for you ,, im msc student now in iraq and now im writting review paper on iot and big data
Excellent goods from you, man. I’ve understand your stuff previous to and you’re just too great. I actually like what you have acquired here, certainly like what you’re saying and the way in which you say it. You make it enjoyable and you still take care of to keep it sensible. I can not wait to read far more from you. This is actually a great web site.