Dr Rajiv Desai
An Educational Blog
INTERNET CENSORSHIP
INTERNET CENSORSHIP:
_
Caveat:
Please do read my previous article on ‘The computer and internet” before you read this article as it will make basics of computer & internet easy. Various circumvention techniques discussed in this article are purely for educational purpose and cannot evade existing laws of land. All court orders by competent court must be respected regarding viewing and/or publishing objectionable content on Internet. In many jurisdictions, accessing blocked content is a serious crime, particularly content that is considered child pornography, a threat to national security, or an incitement of violence. Thus it is important to understand the circumvention technologies and the protections they do or do not provide and to use only tools that are appropriate in a particular context. Great care must be taken to install, configure, and use circumvention tools properly. I am not expert on computers, internet or information technology; and therefore technical inaccuracies are inevitable.
_
Prologue:
Type the keywords “Internet censorship” into Google News and you will immediately understand to what degree the World Wide Web is under assault from attempts by governments globally to regulate and stifle free speech. From Australia to Belarus, from Turkey to Vietnam, from Pakistan to Egypt, from Afghanistan to Iran, huge chunks of the Internet are going dark as the Chinese model of Internet regulation is adopted worldwide. China’s 485 million web users are the world’s largest online population. And the Chinese government has developed the world’s most advanced Internet censorship and surveillance system to police their activity. Yet the days of Americans piously condemning China’s “Great Firewall” and hoping for a technological silver bullet that would pierce it are over. China’s system is a potent, vast and sophisticated network of computer, legal and human censorship. The Chinese model is spreading to other authoritarian regimes. Even though America and India are democratic nations with free society, their media were involved in blocking my comments on Internet curtailing my fundamental human right of freedom of expression. So tendency to censor bona fide comments/speech/picture on Internet exists even in free society and not necessarily among authoritarian regimes.
_
Censorship:
According to Merriam-Webster.com, to censor can be defined as “to examine in order to suppress or delete anything considered objectionable.” Censorship is the suppression of speech or deletion of communicative material which may be considered objectionable, harmful or sensitive as determined by the censor. Censorship has existed since people first organized into societies. First censorship law in china was introduced in 300 AD. It can be used as a method of governance and control, but can also be used as a form of civil protection, such as protecting young children from graphic or sexual images. Historic examples of censorship include the execution of Socrates in ancient Greece and the Index Librorum Prohibitorum (banned books) created by the Catholic Church in the 1600s. Both were authoritative attempts to suppress opposing religious, philosophical and scientific ideas. Today, censorship is generally discussed in the context of mass media. The Federal Communications Commission (FCC) enforces regulations on what can and can’t be shown in U.S. broadcast media such as radio and television. As of yet, attempts to censor and regulate Internet content have been largely unsuccessful. Still, a person may be prosecuted for posting illegal Internet content.
_
No Internet censorship discussion can start without Chinese model:
With more than half a billion Chinese now online, authorities in Beijing are concerned about the power of the Internet to influence public opinion in a country that maintains tight controls on its traditional media outlets. China has an advanced filtering system known internationally as the Great Firewall of China. It can search new Web pages and restrict access in real time. It can also search blogs for subversive content and block Internet users from visiting them.
_
The following diagram illustrates the current Internet censorship mechanisms used by China:
_
The following table illustrates various methods used by Chinese government to censor Internet:
|
Method |
Description |
| IP blocking | The access to a certain IP address is denied. If the target Web site is hosted in a shared hosting server, all Web sites on the same server will be blocked. This affects all IP protocols (mostly TCP) such as HTTP, FTP or POP. A typical circumvention method is to find proxies that have access to the target Web sites, but proxies may be jammed or blocked. Some large Web sites allocated additional IP addresses to circumvent the block, but later the block was extended to cover the new address. |
| DNS filtering and redirection | Doesn’t resolve domain names, or returns incorrect IP addresses. This affects all IP protocols such as HTTP, FTP or POP. A typical circumvention method is to find a domain name server that resolves domain names correctly, but domain name servers are subject to blockage as well, especially IP blocking. Another workaround is to bypass DNS if the IP address is obtainable from other sources and is not blocked. Examples are modifying the Hosts file or typing the IP address instead of the domain name in a Web browser. |
| URL filtering | Scan the requested Uniform Resource Locator (URL) string for target keywords regardless of the domain name specified in the URL. This affects the Hypertext Transfer Protocol. Typical circumvention methods are to use escaped characters in the URL, or to use encrypted protocols such as VPN and SSL. |
| Packet filtering | Terminate TCP packet transmissions when a certain number of controversial keywords are detected. This affects all TCP protocols such as HTTP, FTP or POP, but Search engine pages are more likely to be censored. Typical circumvention methods are to use encrypted protocols such as VPN and SSL, to escape the HTML content, or reducing the TCP/IPstack’s MTU, thus reducing the amount of text contained in a given packet. |
| Connection reset | If a previous TCP connection is blocked by the filter, future connection attempts from both sides will also be blocked for up to 30 minutes. Depending on the location of the block, other users or Web sites may be also blocked if the communications are routed to the location of the block. A circumvention method is to ignore the reset packet sent by the firewall. |
__
History of Internet:
According to Internet historians, the first inklings of the Internet began in the United States in 1969 as a network of four servers called the APRANET. ARPA (the Advanced Research Projects Agency), a division of the Department of Defense, created the ARPANET for military research so that the information on the network would be decentralized and could survive a nuclear strike. The network continued to grow in size and speed as technology increased over the next two decades. Standards began to set in such as the TCP/IP protocol for network transmission of data. By 1990 the Hypertext Transfer Protocol (HTTP) had been created to standardize the way in which Internet documents are sent and received. By 1994, the APRANET was disbanded, and the internet became a public network connecting more than 3,000,000 computers together worldwide. Commercial organizations began to offer services over the internet such as online ordering of pizzas. At present, millions of companies are now online offering products and services such as software, hardware, books, games and adult oriented photographs. Though estimates vary, the consensus is that the amount of providers and users of the internet has nearly doubled each year since 1987. Since the Internet grew into the public eye so fast, many people were caught off guard and concerns began to mount. The unregulated flow of information that the internet provides created concerns with parents and politicians beginning in the early and middle 1990’s.
_
Who owns Internet?
The greatest thing about the internet is that neither one individual nor one organization nor one country can own internet. It is a global collection of networks, both big and small. Thousands of people and organizations own the internet. The internet consists of lots of different bits and pieces, each of which has an owner. Some of these owners can control the quality and level of access you have to the Internet. They might not own the entire system, but they can impact your internet experience. The physical network that carries internet traffic between different computer systems is the Internet Backbone. In the early days of the internet, ARPANET served as the system’s backbone. Today, several large corporations provide the routers and cable that make up the Internet Backbone. These companies are upstream Internet Service Providers (ISPs). That means that anyone who wants to access the Internet must ultimately work with these companies. Many individual consumers and businesses subscribe to local/regional ISPs that aren’t part of the Internet Backbone. These ISPs negotiate with the upstream ISPs for Internet access.
_
Internet basics:
Every computer that is connected to the Internet is part of a network, even the one in your home. For example, you may use a modem and dial a local number to connect to an Internet Service Provider (ISP). Internet service provider (ISP) is defined as an organization/company that provides internet access services to the public. The ISP may then connect to a larger network (upstream ISP) and become part of their network. The internet is simply a network of networks.
Every computer on the Internet has a unique identifying number, called an IP Address. The IP stands for Internet Protocol, which is the language that computers use to communicate over the Internet. If we had to remember the IP addresses of all our favorite Web sites, we’d probably go nuts! Human beings are just not that good at remembering strings of numbers. We are good at remembering words, however, and that is where domain names come in. Since IP address was difficult to remember, domain name system (DNS) was invented which gave each IP address a domain name. For example, domain name of my website is drrajivdesaimd.com having IP address 208.91.198.23 which is the IP address of the sever cp-19.webhostbox.net on which my website is hosted. Every time you use a domain name, you use the internet’s DNS servers to translate the human-readable domain name into the machine-readable IP address. The Uniform Resource Locator (URL) https://www.drrajivdesaimd.com contains the domain name drrajivdesaimd.com and so does its e-mail address: [email protected]– however it must be understood that the server cp-19.webhostbox.net also hosts many other websites and therefore their IP addresses will be same as my website 208.91.198.23
_
Internet servers make the Internet possible. All of the machines on the Internet are either servers or clients. The machines that provide services to other machines are servers. And the machines that are used to connect to those services are clients. A server is a computer dedicated to running one or more such services as a host to serve the needs of users of the other computers on the network. Depending on the computing service that it offers it could be a database server, file server, mail server, print server, web server, or other. A DNS server is a special type of computer on the internet used to support the Domain Name System. The primary job of a domain name server, or DNS server, is to resolve (translate) a domain name into an IP address. Most of the time, your ISP automatically assigns a primary and secondary DNS server when your computer requests network information. All DNS servers are organized in a hierarchy. At the top level of the hierarchy, so-called root servers store the complete database of internet domain names and their corresponding IP addresses. The internet employs 13 root servers that have become somewhat famous for their special role. Ten of these servers reside in the United States, one in Japan, one in London, UK and one in Stockholm, Sweden. Basically DNS server convents domain name into IP address.
_
A server has a static IP address that does not change very often. A home machine that is dialing up through a modem, on the other hand, typically has an IP address assigned by the ISP every time you dial in. That IP address is unique for your session — it may be different the next time you dial in. This way, an ISP only needs one IP address for each modem it supports, rather than one for each customer. If any computer is behind a firewall or uses a proxy server, the IP address shown will be that of the firewall computer or proxy server. Many ISPs route internet traffic via a proxy server to reduce network traffic.
_
Any server machine makes its services available using numbered ports — one for each service that is available on the server. For example, if a server machine is running a Web server and a file transfer protocol (FTP) server, the Web server would typically be available on port 80, and the FTP server would be available on port 21. Clients connect to a service at a specific IP address and on a specific port number. Once a client has connected to a service on a particular port, it accesses the service using a specific protocol. Protocols are often text and simply describe how the client and server will have their conversation. Every Web server on the internet conforms to the hypertext transfer protocol (HTTP).
_
When you type URL in your web browser on Internet, your request goes to DNS server which can do one of four things with it:
1) It can answer the request with an IP address because it already knows the IP address for the requested domain.
2) It can contact another DNS server and try to find the IP address for the name requested. It may have to do this multiple times.
When the DNS server returns the IP address of your URL to your browser, then your browser contacts the server hosting the website to get a Web page.
3) It can say, “I don’t know the IP address for the domain you requested, but here’s the IP address for a DNS server that knows more than I do.”
4) It can return an error message because the requested domain name is invalid or does not exist.
__
When a file is sent from one computer to another, it is broken into small pieces called packets. The packets are labeled individually with origin, destination and place in the original file. Now the packets are sent sequentially over network. When a packet get on a router, the router looks at the packet to see where it needs to go. The routers determine where to send information from one computer to another. Routers are specialized computers that send your messages and those of every other Internet user speeding to their destinations along thousands of pathways. Using “pure” IP, a computer first breaks down the message to be sent into small packets, each labeled with the address of the destination machine; the computer then passes those packets along to the next connected Internet machine (router), which looks at the destination address and then passes it along to the next connected internet machine, which looks the destination address and pass it along, and so forth, until the packets (we hope) reach the destination machine. IP is thus a “best efforts” communication service, meaning that it does its best to deliver the sender’s packets to the intended destination, but it cannot make any guarantees. If, for some reason, one of the intermediate computers “drops” (i.e., deletes) some of the packets, the dropped packets will not reach the destination and the sending computer will not know whether or why they were dropped. By itself, IP can’t ensure that the packets arrived in the correct order, or even that they arrived at all. That’s the job of another protocol: TCP (Transmission Control Protocol). TCP sits “on top” of IP and ensures that all the packets sent from one machine to another are received and assembled in the correct order. Should any of the packets get dropped during transmission, the destination machine uses TCP to request that the sending machine resend the lost packets, and to acknowledge them when they arrive. TCP’s job is to make sure that transmissions get received in full, and to notify the sender that everything arrived OK.
_
In order to understand how Internet communication looks, feels, and actually works in between countries, we’re going to look closely at the path of an email exchange between Andrew is in Ulaanbaatar (Mongolia) to Ethan in Accra (Ghana) — a case study of TCP/IP in action.
Andrew’s packets go through the Ethernet connection to the cybercafe gateway machine, then through a modem and phone line to the Magicnet server, and then through a gateway machine at Magicnet. In the next seven tenths of a second, they take an epic journey through 23 machines in Mongolia, China, Hong Kong, San Jose, New York, Washington DC and Boston. These are twenty-three computers which work as routers.
_
Basics of internet censorship:
In a nutshell I describe a typical Internet search. I type www.google.com on web browser on my PC. The information (packets) will go to my ISP (Tata Docomo) server. My ISP server will resolve domain name google.com into IP address 74.125.224.72 through contacting DNS servers. Once IP address is found, the information will be sent via plenty of router computers in many countries to the server of google.com in the U.S which will return webpage of google.com to my ISP and thence to my PC. All these things in a fraction of a second. Now if somebody wants to censor google.com, he can block transfer of information (packets) at my PC, at my ISP server, at DNS server, at various router computers, at upstream ISP server and at the server of google.com—all will result in me not getting webpage of google.com –it is as simple as that and it also quite simple to circumvent the block. All you need to know is the basics of Internet technology. For example, try to type http://74.125.224.72/ in your web browser and you will reach google.com—if somebody was blocking domain name google.com, you can still reach google.com by directly typing IP address in web browser. Of course, Google has many IP addresses of google.com besides the one narrated by me. You can also type alternative IP address of google.com to access webpage.
_
Internet spread:
Over the first decade of the 21st century, the Internet and its convergence with mobile communications has enabled greater access to information and communication resources. In the last 10 years the Internet grew very, very fast. It is a bunch of thousands of little networks put together. Billion computers are connected and it is basically not controlled or even owned by a government or company. Everybody can put his web pages online which can be accessed by everybody on the world who is sitting in front of a computer with Internet access. I believe that this can and will change the world as we know it today. In 2010, nearly 2 billion people worldwide – over one quarter of the world’s population – use the Internet. During the same period, defenders of digital rights have raised growing concerns over how legal and regulatory trends might be constraining online freedom of expression. The continuing reinvention and worldwide diffusion of the Internet has made it an increasingly central medium of expression of the 21st century, challenging the role of more traditional mass media including radio, television, and newspapers.
_
Africa has the lowest level of Internet penetration at about 11 per cent, followed by Asia, the Middle East, Latin America and the Caribbean, Europe, Oceania and Australia, and finally North America, which has the highest proportion of its population online at over three-quarters (77 per cent) of the population.
_
The impact of these regional changes in Internet adoption is best summarized by the figure below, which shows North America declining from the largest plurality of the Internet population to a number below Europe and Asia. Europe is now also declining in its throw weight online, relative to Asia. These figures dramatically illustrate a global shift in the centre of the Internet’s gravity. Asia is replacing North America and Europe as the dominant presence on the Internet, constituting an increasingly large proportion of the world Internet population, and the implications of this development for freedom of expression online have yet to become clear.
_
Finally, while the growth in Internet penetration appears gradual on a global scale, compared for example with that of mobile telephony, content continues to expand at a fast pace. The number of active websites increased significantly after 2006 and appears to be growing steadily, creating a virtuous cycle of more content generating more use and more use generating more content.
_
This could have major societal implications, as the use of the Internet has the potential to reshape global access to information, communication, services, and technologies. Enduring issues, ranging from freedom of the press to the balance of world information flows in all sectors, and from the media to the sciences, will be tied to the Internet as a ‘network of networks’ – an interface between individuals and the news, information, stories, research, cultures and entertainment following worldwide. By 2010, mobile communication reached nearly 80 per cent of the world’s population, and is converging rapidly with Internet communication.
_
Internet as medium of communication:
The Internet is unlike any information medium in history. Though there are many similarities between the Internet and other means of communications, the free flow of information that the Internet provides makes it a completely unprecedented information medium. Unlike television and radio, the Internet affords users the capacity to access a breadth of information beyond just a channel-changer with only a limited number of stations. The capacity of the Internet is only limited by those who use it. Unlike traditional print media like the newspaper, the Internet is relatively cheap and widely accessible with no red tape. With a computer, network connection, and the proper software, anybody can become a web publisher. There is virtually no limit to how much content can be published on the Internet, whereas newspapers are limited by physical costs such as the cost of paper. The Internet is truly unprecedented information medium and should be treated like one.
_
Internet revolution:
The largest public response to the terrorist attacks in Mumbai was launched by a 13-year-old boy. He used social networks to organize blood drives and a massive interfaith book of condolence. In Colombia, an unemployed engineer brought together more than 12 million people in 190 cities around the world to demonstrate against the FARC terrorist movement. The protests were the largest antiterrorist demonstrations in history. And in the weeks that followed, the FARC saw more demobilizations and desertions than it had during a decade of military action. And in Mexico, a single email from a private citizen who was fed up with drug-related violence snowballed into huge demonstrations in all of the country’s 32 states. In Mexico City alone, 150,000 people took to the streets in protest. So the internet can help humanity push back against those who promote violence and crime and extremism. In Iran and Moldova and other countries, online organizing has been a critical tool for advancing democracy and enabling citizens to protest suspicious election results. And even in established democracies like the United States, we’ve seen the power of these tools to change history. Some of you may still remember the 2008 presidential election here. The freedom to connect to these technologies can help transform societies, but it is also critically important to individuals. There is a story of a doctor who was desperately trying to diagnose his daughter’s rare medical condition. He consulted with two dozen specialists, but he still didn’t have an answer. But he finally identified the condition, and found a cure, by using an internet search engine. That’s one of the reasons why unfettered access to search engine technology is so important in individuals’ lives.
_
Internet and freedom of expression:
Representatives of global institutions and national governments around the world have endorsed freedom of expression as a basic human right. While most often associated with freedom of the press and the First Amendment in the United States, freedom of expression is not only an American value. It has been upheld as a basic human right for decades by a number of international organizations, having been endorsed since 1948 in the United Nations Universal Declaration of Human Rights. In many states, the right to free expression is augmented by rights to freedom of information, providing citizens with a legal right to request and access government held information, and imposing duties on states to publish open records. The close connection between these rights is obvious, namely that the value of free expression is significantly weakened if it cannot be exercised in consideration of key political information relating to how citizens are governed and taxes spent. RTI act in India is classical example of right to information. “Freedom of expression is one of the most fundamental rights of our democracies … but that without freedom of information, freedom of expression often remains meaningless”. However, freedom of information should not result in breach in privacy or release of material related to nation’s security.
_
Clearly, freedom of expression is not absolute in any cultural setting, and this applies equally whether considering expression online or of offline. Contrary to popular belief, free speech is not an absolute right, as all countries establish some limitations to free speech. Certain limitations, such as criminal speech consisting of death threats or defamatory speech, are relatively unconventional. Other forms such as hate speech or obscenity are subject to differing rules in different countries. At the one end of the spectrum, the United States has adopted perhaps the most permissive free speech legal framework, with even the most hateful material enjoying constitutional protection. By contrast, Canada and many European countries have set limitations on hate speech, rendering certain forms illegal.
_
On the one hand, the global diffusion of the Internet, along with a continuing stream of innovations, such as the ease with which users can create as well as consume text and video, are making the Internet increasingly pivotal to the communicative power of individuals, groups and institutions with access to networks and the skills to use them effectively. On the other hand, this very shift in communicative power has spawned greater efforts to restrict and control the use of the Internet for information and communication on political, moral, cultural, security, and other grounds. It is leading also to legal and regulatory initiatives to mitigate risks associated with this new medium, ranging from risks to children, to privacy, to intellectual property rights, to national security, which might more indirectly, and often unintentionally, enhance or curtail freedom of expression. In some cases, limits on expression are intentional, but they are often unintended, such as when regulatory instruments, that might have been appropriate for newspapers, broadcasting or the press, are used inappropriately to control the Internet. As a consequence, defenders of freedom of expression have raised growing concerns over how legal and regulatory trends might be constraining freedom of expression at the very time that the Internet has become more widely recognized as a major medium for fostering global communication. These concerns are reinforced by surveys that provide evidence of encroachments on freedom of expression, such as through the filtering of Internet content. At the same time, despite Internet censorship and filtering, this network of networks continues to bring more information to increasing numbers of individuals around the world.
_
If you believe that progress of human civilization depends on individual expression of new ideas, especially unpopular ideas, then the principle of freedom of speech is the most important value society can uphold. The more experience someone has with the Internet, the more strongly they generally believe in the importance of freedom of speech, usually because their personal experience has convinced them of the benefits of open expression. The Internet not only provides universal access to free speech, it also promotes the basic concept of freedom of speech. If you believe that there is an inherent value in truth, that human beings on average and over time recognize and value truth, and that truth is best decided in a free marketplace of ideas, then the ability of the Internet to promote freedom of speech is very important indeed. “Truth” is a foundation of bedrock, consistent from day to day. Information is correct (absolute truth), incorrect (absolute falsehood) or somewhere in between (pertinent information is unknown or, in part, enough wrong so as to be misleading). It is only further defined by “more facts”. Genuine “truth” does not change. To such extent as “truth” is partially known, further definition (additional facts both relevant and also “true”) complete the puzzle as pieces are added. If you want to know truths about my life, then read my posts on my facebook page on Internet. If anybody in the world feels that my truths are untruths, then he/she can post his/her truth below my posts. So freedom of expression on internet can be regulated without censorship.
_
The Internet, though heralded as the modern medium of communication through which the entire world can be reached in a matter of seconds and which has demystified the hassles related with distance in the world, the same Internet that can be used for cyber democracy and freedom of expression; can be very harmful and indeed kill through the spread of hate speech. It should therefore be regulated to the extent it is harmful and be unregulated to the extent it is not harmful and not be used by the governments to suppress opposing/divergent views.
_
Freedom of expression on the Internet or in any other media is very helpful in building a culture of tolerance to divergent views and acceptance of opposing ideas. It is also asserted that the best way to fight prejudices is through freedom of expression through which people of different cultures and backgrounds exchange views and ideas in a more human and tolerant way especially on the borderless Internet. The right to freedom of expression is a fundamental right that safeguards the exercise of all other rights and is a critical underpinning of democracy.
__
BBC World Service global public opinion poll:
A poll of 27,973 adults in 26 countries, including 14,306 Internet users was conducted for the BBC World Service by the international polling firm GlobeScan using telephone and in-person interviews between 30 November 2009 and 7 February 2010. Overall the poll showed that despite worries about privacy and fraud, people around the world see access to the internet as their fundamental right. They think the web is a force for good, and most don’t want governments to regulate it.
_
_
Findings from the poll include:
1) Four in five adults (79%) regard internet access as their fundamental right. The poll of more than 27,000 adults conducted by GlobeScan found that 87 per cent of those who used the internet felt that internet access should be “the fundamental right of all people.” More than seven in ten (71%) non-internet users also felt that they should have the right to access the web. Countries where very high proportions regarded internet access as their fundamental right included South Korea (96%), Mexico (94%), and China (87%). Most web users are very positive about the changes the internet has brought to their lives, with strong support for the information available, the greater freedom it brings and social networking. Nearly four in five (78%) Internet users felt that the Internet had brought them greater freedom.
2) Most Internet users (53%) felt that “the internet should never be regulated by any level of government anywhere”.
3) Opinion was evenly split between Internet users who felt that “the internet is a safe place to express my opinions” (48%) and those who disagreed (49%). Somewhat surprisingly users in Germany and France agreed the least, followed by users in highly filtered countries such as China and South Korea, while users in Egypt, India and Kenya agreed more strongly.
4) The aspects of the Internet that cause the most concern include: fraud (32%), violent and explicit content (27%), threats to privacy (20%), state censorship of content (6%), and the extent of corporate presence (3%).
_
Definition of Internet censorship:
Internet censorship is defined as the control or suppression of, access to information on the Internet and/or publishing on internet. It may be carried out by governments, or by private organizations either at the behest of government or on their own initiative, or individuals (parents). Individuals and organizations may engage in self-censorship on their own or due to intimidation and fear. The concept of Internet censorship revolves around administrative control or suppression of publishing information on the Internet or accessing it. Under this concept, the reception of those web pages which are deemed unfit by the administrative body of the said country are blocked by government sanctions.
_
Internet censorship refers to technical and non-technical measures taken by repressive regimes to limit a user’s freedom to access information on the Internet. Such measures include, but are not limited to: monitoring of users Internet activities, denying users access to certain websites (blocking), tracking and filtering users’ data flow, and disciplining website operators to tailor their content to comply with censorship regulations. Sometimes the Internet censorship is also referred to as Internet blocking or jamming.
_
Internet censorship is the limiting of access to the internet based on the content of the sites or information blocked. It can be done by parents wishing to limit a child’s access to adult or subject matter that the parents find objectionable. This would be end user censorship. It can be done at the governmental level to block people from accessing information which the government deems to be detrimental or off limits for whatever reason. If you are in the United States, there is very little that is censored. If you are in Cuba or China, almost everything that happens on the internet in those countries is monitored and restricted.
_
Internet Censorship refers to the controlling of publishing and accessing the contents of the internet, in order to prevent citizens under a particular law from viewing or publishing socially unacceptable content. Websites can be blocked in a number of different ways by governments to prevent their citizens from accessing specific sites. However, the United States exercises the right to free speech allowing its citizens to view and post anything on the internet that does not infringe on other’s rights. The content within the internet remains free and available, yet inaccessible if there have been limitations on that content by an individual’s government. It is ultimately limited to a citizen’s location and their governmental laws as to what content is available and what gets censored or becomes unavailable.
_
Many different actors can restrict freedom of expression online. Individuals decide what to read, and what to delete or filter such as by installing spam filters on their personal computer. Parents, corporate information technology (IT) departments, and many other actors have a role in deciding what content is available to users in different social contexts. In general, however, studies of censorship and filtering and freedom of expression are most often concerned with governmental censorship. Governments can directly, or indirectly (through formal and informal agreements with ISPs) restrict freedom of expression by regulating access to the Internet or to particular Internet content. Many civil society advocates of freedom of expression are concerned that state-supported restrictions on Internet access and information are increasing and thereby threatening freedom of expression online.
_
Content related to Nazism or Holocaust denial is blocked in France and Germany. Child pornography, hate speech, and sites that encourage the theft of intellectual property are blocked in many countries throughout the world. In fact, most countries throughout the world, including many democracies with long traditions of strong support for freedom of expression and freedom of the press, are engaged in some amount of online censorship, often with substantial public support. The countries engaged in state-mandated filtering are clustered in three main regions of the world: East Asia, central Asia, and the Middle East/North Africa. A few countries in other regions also practice certain forms of filtering.
_
The legal issues are similar to offline censorship. One difference is that national borders are more permeable online: residents of a country that bans certain information can find it on websites hosted outside the country. Conversely, attempts by one government to prevent its citizens from seeing certain material can have the effect of restricting foreigners, because the government may take action against Internet sites anywhere in the world, if they host objectionable material. One of the early nicknames for the Internet was the “information superhighway” because it was supposed to provide the average person with fast access to a practically limitless amount of data. For many users, that’s exactly what accessing the Internet is like. For others, it’s as if the information superhighway has some major roadblocks in the form of Internet censorship.
_
Internet and repressive regime:
The Internet has become a revolutionary force in repressive regimes. The free flow of information and idea exchange has been perceived as a threat, rather than a blessing, by the authorities in these countries. In response, they have imposed strong censorship on Internet usage by monitoring, filtering, tracing and blocking data flows using advanced technologies. Confined to a tailored and distorted cyberspace, innocent citizens face constant threats when they read, write or speak on the Internet, as their privacy is exposed under the authorities’ watchful eyes. The consequences can be life-threatening. In this environment, the service and content providers practice a great deal of self-censorship.
_
This graph below contains the results of an analysis of internet censorship news articles from 1993-2010 and shows trend of greater media coverage and greater importance over the years.
_
Levels of control:
The control of internet can be discussed as three levels:
A) First-generation controls that systematically and explicitly “focus on denying access to specific Internet resources by directly blocking access to servers, domains, keywords, and UP addresses. More sophisticated “second-generation” and “third-generation” controls are being developed by States to affect “information denial” and “access shaping.
_
B) Second-generation controls refer to the practice of creating “a legal and normative environment and technical capabilities that enable state actors to deny access to information resources as and when needed, while reducing the possibility of blowback or discovery. Common second-generation practices include the following in particular:
1) Compelling internet sites to register with authorities and to use noncompliance as grounds for taking down or filtering “illegal” content, and possibly revoking service providers’ licenses.
2) Strict criteria pertaining to what is “acceptable” within the national media space, leading to the de-registration of sites that do not comply.
3)Expanded use of defamation, slander, and “veracity” laws, to deter bloggers and independent media from posting material critical of the government or specific government officials, however benignly (including humor).
4) Evoking national security concerns, especially at times of civic unrest, as the justification for blocking specific Internet content and services.
5) Shutting down Internet access, as well as selected telecommunications services such as cell phone services and especially short message services (SMS).
6) Extensive use of computer network attacks especially the use of distributed denial of service (DDos) attacks, which can overwhelm ISPs and selected sites.
_
C)Third-generation controls on the other hand is less interested in “denying access than successfully competing with potential threats through effective counterinformation campaigns that overwhelm, discredit, or demoralize opponents.” In particular, it includes “warrantless monitoring of Internet users and usage,” employment of ‘Internet Brigades’ to engage, confuse, or discredit individuals or sources” through “the posting of prepackaged propaganda…, and disinformation through mass blogging and participation in Internet polls, or harassment of individual users, including the posting of personal information.” The intent of these highly sophisticated and multidimensional use of “surveillance, interaction, and direct physical action to achieve a disruption of target groups or networks” is the effecting of “cognitive change rather than to deny access to online information or services.”
_
Categories subject to Internet filtering:
Free expression and media freedom
Political transformation and opposition parties
Political reform, legal reform, and governance
Militants, extremists, and separatists
Human rights
Foreign relations and military
Minority rights and ethnic content
Women’s rights
Environmental issues
Economic development
Sensitive or controversial history, arts, and literature
Hate speech
Sex education and family planning
Public health
Gay/lesbian content
Pornography
Provocative attire
Dating
Gambling
Gaming
Alcohol and drugs
Minority faiths
Religious conversion, commentary, and criticism
Anonymizers and circumvention
Hacking
Blogging domains and blogging services
Web hosting sites and portals
Voice over Internet Protocol (VOIP)
Free e-mail
Search engines
Translation
Multimedia sharing
P2P
Groups and social networking
Commercial sites
_
One example is sufficient. The diagram below shows items that are censored in Kuwait.
_
The picture below shows what you see on internet in Bahrain if the site you are visiting is censored.
__
Size of blocking units:
There are several governments who think that unlimited access to information is dangerous for their citizens. So they established blocking units to censor internet. This ranks from DNS blocking of Nazi sites in parts of Germany to a government office with 30.000 employees only working in blocking thousands of websites, services and ports in China.
_
Worldwide distribution of internet censorship:
The magnitude or level of censorship is classified as follows:
Pervasive: A large portion of content in several categories is blocked.
Substantial: A number of categories are subject to a medium level of filtering or many categories are subject to a low level of filtering.
Selective: A small number of specific sites are blocked or filtering targets a small number of categories or issues.
Suspected: It is suspected, but not confirmed, that Web sites are being blocked.
No evidence: No evidence of blocked Web sites, although other forms of controls may exist
_
In terms of severity, the most pervasive Internet censorship is applied in: Burma, Cuba, Egypt, Iran, North Korea, China, Syria, Tunisia, Turkmenistan, Uzbekistan and Vietnam. Substantial censorship in: Bahrain, South Korea, Saudi Arabia, United Arab Emirates and Yemen. Nominal and other types of censorship are applied in: Australia, Belgium, Brazil, Canada, Chile, Colombia, Czech Republic, Denmark, Fiji, Finland, France, Germany, Ghana, Ireland, India, Israel, Italy, Jordan, Mexico, Morocco, Netherlands, Norway, Pakistan, Poland, Russia, Singapore, Sweden, Thailand, Turkey, United Kingdom and USA.
_
The largest democracy India and Internet censorship:
The growing Chinese belligerence seems to have motivated India to follow suit, but perhaps in the wrong context. China was recently rated as the most restricted country in terms of Internet censorship. And, if India’s new censorship laws are enforced, India could be right be in the league of countries with most restricted Internet usage policies. The new Information Technology Rules, 2011 lists down all the content restrictions that an ISP, cloud provider or a hosting provider needs to impose on bloggers, online news websites and individuals. It also defines the time frame within which the ‘intermediary’ needs to pull down a website or a blog in case any violation of the rules is observed. The new rules not only define censorship laws but also allows the government to abuse terms such as ‘invasion of another’s privacy’, ‘defamation’, ‘harassment’ and ‘threat to the nation’. China has already been prosecuting people exercising free speech by terming the content as ‘threat to nation’ etc. According to IT Rules 2011, Sub Rule 2, “Users shall not host, display, upload, modify, publish, transmit, update or share any information that is grossly harmful, harassing, blasphemous, defamatory, obscene, pornographic, pedophilic, libelous, invasive of another’s privacy, hateful, or racially, ethnically objectionable, disparaging, relating or encouraging money laundering or gambling, or otherwise unlawful in any manner whatever;” Additionally, Sub Rule 2 also states that users may not publish anything that threatens the unity, integrity, defense, security or sovereignty of India, friendly relations with foreign states, or public order or causes incitement to the commission of any cognizable offence or prevents investigation of any offence or is insulting any other nation. Leaving so much power in the hands of the ISPs may not be a good idea for a country like India where there are highest number of complaints to shut down Facebook pages and profile as ‘someone’ finds them offensive. Now, instead of first battling out a complaint in the court of law, the ISP would straight away block your website in case your content seems offensive to someone. However, ISP is not a regulatory body to enforce moral codes as portrayed by Indian IT rules. Role of ISP in Internet censorship is discussed later on in this article. Indian regime does not seem to have any respect for freedom of expression but bent on displaying moral policing to prevent adulteration of Indian culture by western culture. Indian regime and Indian courts are concerned about religious sentiments hurt by some comment/picture on Internet. I deplore any comment/picture that hurt religious sentiments but that does not mean that Internet should be censored. No religion is so narrow minded that it cannot tolerate offensive intimidation.
_
Unless the censor has total control over all Internet-connected computers, such as in North Korea or Cuba, total censorship of information is very difficult or impossible to achieve due to the underlying distributed technology of the Internet. Pseudonymity and data havens (such as Freenet) protect free speech using technologies that guarantee material cannot be removed and prevents the identification of authors. Technologically savvy users can often find ways to access blocked content. Nevertheless, blocking remains an effective means of limiting access to sensitive information for most users when censors, such as those in China, are able to devote significant resources to building and maintaining a comprehensive censorship system.
_
Freedom on the Net reports:
In the 2011 edition of Freedom House’s report Freedom on the Net, of the 37 countries surveyed, 8 were rated as “free” (22%), 18 as “partly free” (49%), and 11 as “not free” (30%). In their 2009 report, of the 15 countries surveyed, 4 were rated as “free” (27%), 7 as “partly free” (47%), and 4 as “not free” (27%). And of the 15 countries surveyed in both 2009 and 2011, 5 were seen to be moving in the direction of more network freedom (33%), 9 moved toward less freedom (60%), and one was unchanged (7%).
A green-colored bar represents status of “Free,” a yellow-colored one represents status of “Partly Free,” and a purple-colored one represents status of “Not Free” on the Freedom of the Net Index.
__
OpenNet Initiative reports:
Through 2010 the OpenNet Initiative had documented Internet filtering by governments in over forty countries worldwide. The level of filtering in 26 countries in 2007 and in 25 countries in 2009 was classified in the political, social, and security areas. Of the 41 separate countries classified, seven were found to show no evidence of filtering in all three areas (Egypt, France, Germany, India, the Ukraine, the United Kingdom, and the United States), while one was found to engage in pervasive filtering in all three areas (China), 13 were found to engage in pervasive filtering in one or more areas, and 34 were found to engage in some level of filtering in one or more areas. Of the 10 countries classified in both 2007 and 2009, one reduced its level of filtering (Pakistan), five increased their level of filtering (Azerbaijan, Belarus, Kazakhstan, South Korea, and Uzbekistan), and four maintained the same level of filtering (China, Iran, Myanmar, and Tajikistan.
_
_
The OpenNet Initiative (ONI), an organization dedicated to informing the public about Web filtering and surveillance policies around the world, classifies Web filtering into four categories:
1) Political: Content that includes views contrary to the respective country’s policies. The political category also includes content related to human rights, religious movements and other social causes,
2) Social: Web pages that focus on sexuality, gambling, drugs and other subjects that a nation might deem offensive.
3) Conflict/Security: Pages that relate to wars, skirmishes, dissent and other conflicts.
4) Internet tools: Web sites that offer tools like e-mail, instant messaging, language translation applications and ways to circumvent censorship.
_
Internet enemies:
In 2006, Reporters without Borders (Reporters sans frontières, RSF), a Paris-based international non-governmental organization that advocates freedom of the press, started publishing a list of “Enemies of the Internet”. The organization classifies a country as an enemy of the internet because “all of these countries mark themselves out not just for their capacity to censor news and information online but also for their almost systematic repression of Internet users.” In 2007 a second list of countries “Under Surveillance” (originally “Under Watch”) was added. Both lists are updated annually.
_
Enemies of the Internet:
Burma: The Burmese government’s Internet policies are even more repressive than those of its Chinese and Vietnamese neighbors. The military junta clearly filters opposition websites. It keeps a very close eye on Internet cafes, in which the computers automatically execute screen captures every five minutes, in order to monitor user activity.
_
China (excluding Hong Kong and Macau): China unquestionably continues to be the world’s most advanced country in Internet filtering. The authorities carefully monitor technological progress to ensure that no new window of free expression opens up. After initially targeting websites and chat forums, they nowadays concentrate on blogs and video exchange sites. In a country in which hundreds of people are currently in prison for expressing themselves too freely online, self-censorship is obviously in full force.
_
Cuba: With less than 2 per cent of its population online, Cuba is one of the most backward Internet countries. An investigation carried out by Reporters Without Borders in 2007-October revealed that the Cuban government uses several levers to ensure that this medium is not used in a “counter-revolutionary” way. Cuba has banned private Internet access completely — to get on the Internet, you have to go to a public access point.
_
Iran: Internet filtering has stepped up and Iran today boasts of filtering 10 million “immoral” websites. Pornographic sites, political sites and those dealing with religion are usually the ones most targeted.
_
North Korea: Till 2006, North Korea continues to be the world’s worst Internet black hole. Only a few officials are able to access the web, using connections rented from China. The country’s domain name – .nk – has still not been launched and the few websites created by the North Korean government are hosted on servers in Japan or South Korea. It is hard to believe this is simply the result of economic difficulties in a country which today is capable of manufacturing nuclear warheads.
_
Saudi Arabia: Saudi Arabia does not hide its online censorship. Unlike China, where website blocking is disguised as technical problems, Saudi Arabia’s filters clearly tell Internet users that certain websites are banned. Censorship concentrates on pornographic content, but it also targets opposition websites, Israeli publications, or sites dealing with homosexuality.
_
Syria: Syria’s existing Internet surveillance systems, which include hardware from Silicon Valley-based Blue Coat, have aided President Bashar al-Assad’s regime in his crackdown on protest. More than 100 Syrians have died in detention, and information gathered through Area SpA’s Internet surveillance system would have been used against people being detained and tortured, according a researcher for the Middle East and North Africa.
_
Turkmenistan: With less than 1 per cent of the population online, this is one of the world’s least connected countries.
_
Uzbekistan: Official censorship seems to have become even tougher since the bloody crackdown on the pro-democracy protests in Andidjan in May 2005.
_
Vietnam: Good news finally arrives from Vietnam this week, as a Vietnamese court reduced the jail sentence of blogger and human rights activist Professor Pham Minh Hoang from three years to 17 months. He’ll be released from jail in soon.
_
Bahrain: This fall, 63 Bahraini students were expelled from school for “participating in unlicensed gatherings and marches,” the evidence of which was pulled from their Facebook accounts which they reportedly used to organize pro-democracy protests in February.
_
Thailand: Clicking “like” on Facebook in Thailand can potentially land you in prison. The Thai Minister of Information and Communication Technology declared that they will begin charging Facebook users for “liking” or sharing content that could be deemed offensive to the Thai throne, the sentence for which could run anywhere between three to 15 years in prison.
_
Other names in list of internet enemies include
Belarus
Egypt
Eritrea
France
Libya
Malaysia
Russia
Australia
South Korea
Sri Lanka
Tunisia
Turkey
United Arab Emirates
Venezuela
_
Cyber dissident:
A cyber-dissident is an individual who could be professional journalist, an activist or citizen journalist who posts news, information, or commentary on the internet that implies criticism of a government or regime. Mohamad Reza Nasab Abdolahi was imprisoned in Iran for published an open letter to Ayatollah Ali Khamenei. His pregnant wife and other bloggers who commented on the arrest were imprisoned too. Several bloggers in Egypt were arrested for allegedly defaming then president Hosni Mubarak or expressing critical views about Islam. Blogger Karim Amer has been convicted to four years of prison. When Russian president Vladimir Putin in 2006 called on his nation’s women to have more children, journalist Vladimir Rakhmankov published a satiric article on the Internet calling Putin “the nation’s phallic symbol”. Rakhmankov was found guilty of offending Vladimir Putin, and fined by the court of the region he lived in to the sum equal of 680 US dollar. The overall story served as a good advertising for Rakhmanov’s article that was republished by numerous Russian sources afterwards.
_
The figure below shows how dissidents can communicate through internet when the state has blocked internet access.
_
Wikileaks:
The website Wikileaks is dedicated to providing access to information by protecting ‘whistleblowers, journalists and activists who have sensitive material to communicate to the public’. The site leads with a quote from Time Magazine that the site ‘… could become as important a journalistic tool as the Freedom of Information Act.’ It was founded and led by Julian Assange on the notion that ‘principled leaking’ of key documents can support greater public accountability, invoking the spirit of Daniel Ellsberg and the Pentagon Papers. The site was supported primarily by individual volunteers, but the release of notable documents led to some funding through donations.
_
Paid commentators in China:
China has growing army of paid internet commentators often referred to as the “50 Cent Party” for the alleged fee they collect for each posted comment. This is an effort by the Chinese Communist Party (CCP) to manipulate public debate. These private citizens are paid by the government to pretend to be “ordinary” netizens while in fact promoting the CCP line and seeking, in a nontransparent fashion, to guide public opinion in a particular direction. Though politicians around the world are increasingly using internet to reach their constituents, the kind of deceptive measures employed by the “50 Cent Party” would not be tolerated in a democracy. They would also be unnecessary for a democratic government, since elected leaders have genuine supporters willing to defend them on the internet free of charge, and the population can turn to a free press, rather than self-proclaimed “fellow citizens,” to verify officials’ public statements. There are about over 560,000 private citizens being paid by the government to manipulate discussions on the Chinese internet.
_
China’s Internet censorship as trade barrier:
China’s Internet filtering and censorship are causing real economic harm, and how these practices violate some of China’s formal trade commitments under the World Trade Organization. While the WTO allows exceptions to its rules for matters of public morals and national security, the boundaries of such exceptions need to be tested. The WTO also requires that all restrictions be transparent, provide due process, be minimally restrictive and apply equally to foreign and domestic entities. As of today, China complies with none of these requirements. In repeatedly blocking sites like Facebook, Twitter, Google, Flickr, YouTube and others, China is singling out U.S. companies for censorship even when Chinese-owned services carry some of the same, supposedly “banned” content. This double standard strongly suggests that protectionism is one of the motivations for that country’s aggressive censorship. The economic threat is real. Internet related commerce is already in the trillions and growing rapidly. Restricting the free flow of information has especially serious repercussions in the U.S. – home to the world’s leading companies involved in online communication, information exchange, and digital commerce. Besides Chinese Internet censorship as a trade barrier, it also causes considerable harm to fundamental human rights.
_
Arab spring:
The Arab Spring is a revolutionary wave of demonstrations and protests occurring in the Arab world that began on Saturday, 18 December 2010. To date, there have been revolutions in Tunisia and Egypt; a civil war in Libya resulting in the fall of its government; civil uprisings in Bahrain, Syria and Yemen; major protests in Algeria, Iraq, Jordan, Kuwait, Morocco, and Oman; and minor protests in Lebanon, Mauritania, Saudi Arabia, Sudan, and Western Sahara. During the Arab Spring media jihad (media struggle) was extensive. Most observers believe that the Internet and mobile technologies, particularly social networks such as Facebook and Twitter, played and are playing important new and unique roles in organizing and spreading the protests and making them visible to the rest of the world. An activist in Egypt tweeted, “we use Facebook to schedule the protests, Twitter to coordinate, and to tell the world”. This successful use of digital media in turn leads to increased censorship including the complete loss of Internet access for periods of time in Egypt and Libya in 2011. In Syria, the Syrian Electronic Army (SEA), an organization that operates with at least tacit support of the government, claims responsibility for defacing or otherwise compromising scores of websites that it contends spread news hostile to the Syrian regime. The success of several Arab Spring revolutions offers a chance to establish greater freedom of expression in countries that were previously subject to very strict censorship, especially online. At the same time success in this effort is not certain. In response to these dramatic events and opportunities, in March 2011, Reporters Without Borders moved Tunisia and Egypt from its “Internet enemies” list to its list of countries “under surveillance”. At the same time there are warnings that Internet censorship might increase following the events of the Arab Spring.
_
The success of the Tunisian and Egyptian protest movements inspired demonstrations throughout the Middle East including large-scale social media coordinated protests in Libya, Iran, Bahrain, Algeria, Jordan and Yemen. In several of countries, governments responded to the calls for reform with arrests and violent suppression of public demonstrations. Increasingly, several Middle Eastern governments also may be disrupting phone and Internet communication to contain the spread of unrest. These new Internet filtering efforts come a week after Egypt returned to the Internet following an abortive effort to block protests demanding the then president, Hosni Mubarak, resign. While other countries, including Iran and Myanmar, disrupted telecommunication following social unrest in the past, the Egyptian outage represents a new Internet milestone — the first highly connected telecommunication dependent society to intentionally disconnect from the Internet.
_
_
In an action unprecedented in Internet history, the Egyptian government appears to have ordered service providers to shut down all international connections to the Internet. At 22:34 UTC (00:34am local time) on January 27, 2011; there was virtually simultaneous withdrawal of all routes to Egyptian networks in the Internet’s global routing table. Approximately 3,500 individual BGP routes were withdrawn, leaving no valid paths by which the rest of the world could continue to exchange Internet traffic with Egypt’s service providers. Virtually all of Egypt’s Internet addresses were unreachable worldwide.
__
_
In the above chart of February 2011, the “normal” traffic in and out of each country averaged over the preceding three weeks is shown in green. The dotted red line in each graph shows the traffic over the last seven days. Orange shaded areas indicated periods of statistically abnormal traffic either last week or the week of February 14. Abnormal traffic volumes may represent network failures or periods of intentional traffic manipulation. Due to the near complete block of all Internet traffic (January 27 — February 2), the Egyptian graph shows orange for most of last week as traffic levels climbed to normal. Yemen Internet traffic also exhibited brief, though unusual dips, during the prior week (February 7-11) and also includes an orange period. While the Internet has proven a powerful tool for rallying social and political change, so too have governments recognized their regulatory and technical capability to disrupt communications. There is a major contest going between the continued evolution of the Internet as a vehicle for political change and authoritarian government’s continued assertion of control.
___
Since the beginning of the popular uprisings and protests in the Middle East and North Africa, events in the region have been characterized by increased contestation in cyberspace among regime sympathizers, governments, and opposition movements. One component of this contestation is the tendency among governments and networks of citizens supportive of the state to use offensive computer network attacks. Such tactics are supplements to legal, regulatory, and other controls, and technical forms of Internet censorship. For example, a group known as the Iranian Cyber Army has defaced Twitter and Iranian opposition websites. Also, Tunisian political activists and Yemeni oppositional websites have both accused their government security organizations of launching attacks on their sites in an attempt to silence their message and deny access to their content. The activities of the Syrian Electronic Army (SEA), which appears to be a case of an open and organized pro-government computer attack group that is actively targeting political opposition and Western websites. It is documented that how Syria has become the first Arab country to have a public Internet Army hosted on its national networks to openly launch cyber attacks on its enemies. The SEA continues to claim responsibility for defacing or otherwise compromising scores of websites that it contends spread news hostile to the Syrian regime. After a 4-day countdown meant to build anticipation, the SEA announced the defacement of over 130 websites and has continued to release the URLs of more defaced pages every few days. Although most of the websites were indeed defaced, the vast majority of the affected pages were online businesses and blogs with no apparent political content. SEA disseminates denial of service (DoS) software designed to target media websites including those of Al Jazeera, BBC News, Syrian satellite broadcaster Orient TV, and Dubai-based al-Arabia TV.
_
Twitter in the Iranian 2009 Election Protests:
In the midst of protests surrounding the contested 2009 election results in Iran, the Internet, and Twitter in particular, was claimed to have played an important role in organizing and supporting the protests on the streets of Tehran. Overall, there is little doubt that Twitter and videos posted on the Web played a significant role in providing a means for individuals in Iran to communicate with one another, but most often via the world outside Iran. The main role of Twitter was as a tool for the Iranian diaspora to relay protest news to the international media, which in turn became a significant factor in shaping and informing developments on the ground. The counter-measures used to break this cycle were quite effective. On important protest days, Iranian authorities effectively pulled the plug on the Internet, introducing 60 to 70 per cent packet loss into the network and closing all the major ports used by circumvention tools, making it nearly impossible for ordinary users to do anything online. On normal and non-critical days, Iran appeared to be doing deep packet inspection.
_
Success of Arab Spring:
The protesters openly acknowledge the role of Internet as a fundamental infrastructure for their work. Libya’s dictator Gadhafi’s former aides have advised him to submit his resignation through Twitter before his death. Just as the fall of Suharto in Indonesia is a story that involves the creative use of mobile phones by student activists, the falls of Zine El Abidine Ben Ali in Tunisia and Mubarak in Egypt will be recorded as a process of Internet-enabled social mobilization.
_
There are three possible ways in which freedom on the Internet can be limited:
1. Obstacles to access, including restrictions imposed by governmental policy or economic conditions, such as a lack of infrastructure;
2. Limits to content, such as through self- or government-censorship, when self-censorship includes that imposed by the Internet industry;
3. Restrictions on the rights of users, such as (un)lawful disconnection.
_
Table below summarizes the current state of Internet censorship in the world:
| Who Censors | What | Why | How |
| Government | Pornography; hate speech; terrorist information, e.g., directions for how to make bombs; information from/ about regimes felt to be threat | Protect children and citizens; decrease foreign influence; protect political stability; maintain security | Legislation; licensing/controlling telecommunication; labeling; |
| Academic institutions | Hate speech; criticism of administration/ faculty; expression judged to be in conflict with institutional policy, good taste, etc. | Institutional responsibility for setting high cultural/social standards, maintaining civility and security | Prevent publication; threaten suspension/ dismissal; |
| Religious groups, institutions | Pornography; in general, expressions thought to deny, contradict, or mock the particular religion espoused | Responsibility for maintaining moral standards and respect for religious teachings and institutions | Law suits; working to eliminate publication and use of information they deem objectionable |
| Corporations | Information thought to be harmful to company; employee use of electronic resources for “unauthorized” communication | Protect trade secrets; preserve image; guard against unproductive or damaging employee behavior | Law suits; counterintelligence or disinformation; dismissal/sanctions against offending employees |
| Media | Information that threatens advertisers | Preserve relationships with sponsors | Refrain from publishing |
| Libraries | Pornography, other information thought to be harmful to children | Respond to community pressure; avoid need to “police” terminals | Filters; contracts specifying online conduct; |
_
Motives for internet censorship:
There are five primary motives or rationales for Internet censorship: politics and power, social norms and morals, security concerns, protecting intellectual property rights and existing economic interests. In addition, networking tools and applications that allow the sharing of information related to these motives are often targeted.
1) Politics and power:
Censorship directed at political opposition to the ruling government is common in authoritarian and repressive regimes. Some countries block Web sites related to religion and minority groups, often when these movements represent a threat to the ruling regimes. Examples include: Political blogs and Web sites, sites with content that offends the dignity of or challenges the authority of a reigning sovereign or of a state, Tibetan exile group sites in China, indigenous hill tribes’ sites in Vietnam and Sites aimed at religious conversion from Islam to Christianity. The list of countries that engage in substantial political blocking includes Bahrain, China, Libya, Iran, Myanmar, Pakistan, Saudi Arabia, Syria, Tunisia, Uzbekistan, and Vietnam. Thailand and Ethiopia are the most recent additions to this group of countries that filter Web sites associated with political opposition groups. Yet in other countries with an authoritarian bent, such as Russia and Algeria, filtering of the Internet is not yet uncovered.
_
2) Social norms and morals:
Social filtering is censorship of topics that are held to be antithetical to accepted societal norms. In particular censorship of child pornography and to protect children enjoys very widespread public support and such content is subject to censorship and other restrictions in most countries. Examples include: Sex and erotic, fetishism, prostitution & pornographic sites; child pornography & pedophile related sites; Gay & Lesbian sites; sites seen as promoting illegal drug use; gambling sites; sites encouraging or inciting violence and sites promoting criminal activity. Sites that contain blasphemous content, particularly when directed at a majority or state supported religion; sites that contain defamatory, slanderous, or libelous content; and sites that include political satire are also censored. Web sites that deny the Holocaust or promote Nazism are blocked in France and Germany. Web sites that provide unflattering details related of the life of the king of Thailand are censored in that country.
_
Child pornography is defined as a material that visually depicts:
A. a minor engaged in sexually explicit conduct;
B. a person appearing to be a minor engaged in sexually explicit conduct;
C. realistic images representing a minor engaged in sexually explicit conduct.
_
Child Protection:
The Internet is an increasingly central component in the lives of children and young people in the developed world. It cannot be seen as an ‘adults-only’ environment. It is in this context that some of the most emotive debates around freedom of expression online arise, at the point where the crucial regulatory goal of preventing harm to minors pushes up against the noble ideal of free speech for all. Many, possibly even most states, have introduced some regulatory tools to protect children online, at least in terms of prohibiting illegal activity; the question remains as to how much regulation is enough, and how much is too much. In many jurisdictions, this debate hinges in large part on the distinction between activities that are illegal and those that are harmful. In attempting to combat activity that is clearly illegal, many countries have expressed revulsion at the production, dissemination and consumption of child sexual abuse images. In most countries, the removal of these images is deemed to be a justified limitation to freedom of expression. As far as child abuse is concerned; should Internet content be controlled by law enforcement agencies or should it rather be a responsibility undertaken by ISPs and search engines? If so, should this occur with or without government support and mandates?
_
What harm pornography does?
Pornography is defined in Webster’s Dictionary as pictures, film, or writing which deliberately arouse sexual excitement. One thing might sexually excite one person but not another. So by this definition, one can understand why there is a lot of room for discrepancy. Pornography demeans and degrades women, victimizes children and ruins men. It contributes to domestic and spouse abuse, rape, incest and child molestation. And a great share of it is not protected speech, any more than libel, slander or false advertising are protected speech; therefore, it is not a freedom of expression issue. It is not legal material. Many people do not realize this fact.
_
Child pornography laws that exist on the federal, state and local levels also apply to the Internet. Thus creating a new set of laws for the Internet are unnecessary because federal, state and local laws already apply to users of the Internet if they are in the jurisdiction of said laws. Also, Software Systems which allow parental control of Internet material are already widely available on the Internet. Many parents turn to software and hardware solutions to this problem. They can purchase Web filtering programs like Net Nanny or CYBERsitter to block access to undesirable Web sites. These programs usually have a series of options parents can select to limit the sites their children can access. These options tell the program which filters to enable. For example, CYBERsitter has 35 filter categories, including pornography and social networking sites. Net Nanny’s software system allows parents to “monitor, screen and block access to anything residing on, or running in, out or through your PC, online or off”. There are many other parental control software systems that are similar to Net Nanny including SurfWatch and Cyber Patrol. Another option for parents is to install a firewall. Tech-savvy parents might not have a problem installing and maintaining a firewall. Others prefer to use Web filters, which do most of the work for them.
_
3) Security concerns:
Internet filtering related to threats to national security that targets the Web sites of insurgents, extremists, and terrorists often enjoys wide public support. Examples include: Blocking of pro–North Korean sites by South Korea, Blocking sites of groups that encourage domestic conflict in India, Blocking of sites devoted to the Balochi independence movement by Pakistan, Blocking of sites of the Muslim Brotherhood in some countries in the Middle East and Blocking Wikileaks. The perceived threat to national security is a common rationale used for blocking content. Internet filtering that targets the Web sites of insurgents, extremists, terrorists, and other threats generally garners wide public support. This is best typified by South Korea where pro–North Korean sites are blocked, or by India where militant and extremist sites associated with groups that encourage domestic conflict are censored.
_
4) Protection of intellectual property rights:
Sites that share content that violates copyright or other intellectual property rights are often blocked, particularly in Western Europe and North America.
_
5) Existing economic interests:
The protection of existing economic interests is sometimes the motivation for blocking new Internet services such as low-cost telephone services that use Voice over Internet Protocol (VoIP). These services can reduce the customer base of telecommunications companies, many of which enjoy entrenched monopoly positions and some of which are government sponsored or controlled.
_
Libel for Defamation:
Most nations’ courts seek to protect the reputations of individuals and companies from irresponsible accusations of libel. However, restrictions on spoken or written expression that are meant to prevent defamation vary widely. In Asia, governments have enacted laws which deter acts of online defamation and frequently impose serious sanctions such as imprisonment. These measures are often seen as stifling freedom of expression and freedom of the press on the Internet. In the United States, Australia and United Kingdom, libel cases for online defamation have tested the limits of legal jurisdiction in the online world. United Kingdom is widely perceived to have some of the greatest restrictions on the publication of defamatory information, and is said to have spawned libel tourism in the country. Nonetheless, everybody must understand that the truth cannot be libel.
_
Hate speech:
Hate speech is defined as: “racist and xenophobic material” meaning any written material, any image or any other representation of ideas or theories which advocates, promotes or incites hatred, discrimination or violence; against any individual or group of individuals; based on race, color, descent, religion or national / ethnic origin; or any material used as a pretext for any of these factors. As much as the Internet is a mechanism for spreading democracy it is also a breeding ground for hate speech by groups who have used it to promote their cause. While most people tend to agree that this is a negative consequence of the Internet, some think that inappropriate regulation of online hate speech can lead to the suppression of the right to freedom of expression. Others believe that prohibiting hate speech altogether may further proliferate its discourse in society. Moreover, active censorship usually tends to backfire in a democracy, especially when filtering and online monitoring are used. So how can a balance be found between both, in order to avoid online censorship? There are two major approaches to this issue. The first is to encourage free and open exchange of ideas online (mainly a US approach). The second is to directly block hate speech on the Internet, which has been the approach adopted by Germany, amongst other countries. It is difficult and highly unlikely that an international consensus will be found on how to deal with this problem. Some suggest establishing an ombudsman bureau and using exposure as an effective means to reduce hate speech online. Others argue that the solution lies in public education and the teaching of tolerance and acceptance of diverse values.
_
Illegal Content:
A useful starting point in addressing problematic Internet content is to differentiate between controversial or offensive or harmful content and illegal content. Illegal content is defined objectively, in the sense that existing laws determine which content is illegal — whether it is in cyberspace or in the physical world. More precisely, illegal content is defined as content that is in violation of country’s laws of general application. Illegal content includes child pornography; online solicitation of children for sexual acts; hate propaganda; obscenity; online harassment; and communicating threats. It is wrong to consider the Internet a “lawless place” and the law of the land also applies to the Internet in theory. This is also true regarding the availability of illegal content over the Internet. The most common and most frequently cited example of illegal content is the availability of child pornography over the Internet. Consequently, the whole issue of illegal content and how to deal with this has revolved around child pornography, even though child pornography and pedophilia are not necessarily Internet specific problems. Another concern for content-related criminal activity by law enforcement agencies is the possibility of using the Internet for harassment and threats. As Table below illustrates, it is not always easy to categorize certain types of content as illegal even though these may sometimes be regarded as objectionable or harmful and that categorization of content is not straightforward and is often problematic.
_
| Child pornography | Hate speech | Pornography |
| Society sees it as a problem.•Child pornography is not a new problem.• Digital child pornography is
not a new problem – it can be traced back to the mid-1980s. • Clear cut example of “illegal content”. • Criminalized by the CoE Cybercrime Convention, the UN Optional Protocol to the Convention on the Rights of the Child on the sale of children, child prostitution and child pornography, and the EU Council Framework Decision on combating the sexual exploitation of children and child pornography (not adopted yet). • UN Optional Protocol: 108 signatories, 71 parties as of February 2004. |
• Society sees it as a problem.• Racism and xenophobia are not new problems.• Digital hate is not a new
problem – it can be traced back to the mid-1980s. • Difficult to categorize: Depending upon its nature and the laws of a specific State it could be considered illegal or harmful/offensive (BUT legal). • Harm criteria are different in different European States. • CoE Additional Protocol to the Cybercrime Convention on the criminalization of acts of a racist and xenophobic nature committed through computer systems: 23 signatories so far but no ratifications |
• Society does not always see it as a problem.• Pornography is certainly not new.• Difficult to categorize:
Depending upon its nature and the laws of a specific State it could be considered illegal or harmful/offensive (BUT legal). • Harm criteria are different in different European States. • UK approach is rather different to the German or Scandinavian approaches to sexually explicit content. • No international attempt to regulate “sexually explicit content”. |
| Illegal universally |
In between | Legal in many nations |
_
Harmful Content (offensive content). The difference between illegal and harmful content is that the former is criminalized by national laws, while the latter is considered offensive, objectionable, unwanted, or disgusting by some people but is generally not criminalized by national laws. Controversial or offensive content is for the most part defined subjectively in the sense that, while it is not illegal under country law, it is deemed to be controversial or offensive according to individual, community, or culturally based standards. In some cases, this type of content may be considered to be harmful to children. Offensive content includes such things as legal pornography; violence; alcohol and tobacco advertising aimed at minors; and other content that may be considered to be objectionable on social, religious, cultural, or other grounds. Internet content that may also be labeled “harmful” includes sexually explicit material, political opinions, religious beliefs, views on racial matters, and sexuality. But it should be noted that in the Handyside case, the European Court of Human Rights confirmed that freedom of expression extends not only to ideas and information generally regarded as inoffensive but even to those that might offend, shock, or disturb, and this sort of information legally exists over the Internet as well as in other media. The governance of this sort of Internet content may differ from country to country. This is certainly the case within Europe where there are different approaches to sexually explicit content, hate speech, or Holocaust denial. For example, under the Obscene Publications Act in the UK, it is illegal to publish and distribute obscene publications. Yet possessing or browsing through sexually explicit and obscene content on the Internet is not an illegal activity for consenting adults. Furthermore, there are no UK laws making it illegal for a child to view such content in a magazine or on the Internet. The laws normally deal with the provision of such content to children. Therefore, harm is a criterion which depends upon cultural differences and this is accepted within the jurisprudence of the European Court of Human Rights. Nevertheless, the availability of harmful Internet content is a politically sensitive area and a cause for concern for European regulators.
_
Pros and cons of internet censorship:
The series of events related to Internet censorship in various parts of the world over the last year or so has brought this issue back to the debating table. This has, in turn, left the entire world divided into two groups – those advocating Internet censorship and those opposing it. While those who advocate it argue that such regulations are necessary to keep certain problems, such as sexual exploitation of children and spread of drug cartels, at bay; its critics are of the opinion that this is a mere authoritative practice which questions the fundamental principles of democracy.
_
The internet is the fastest growing and largest tool for mass communication and information distribution in the world. It can be used to distribute large amounts of information anywhere in the world at a minimal cost. In the last ten years there has been increasing concern about damaging internet content right from violence & sexual content to bomb-making instructions, terrorist activity and child pornography. Irrespective of whether it is on the television or on Internet, racial comments and pornography can never be justified. It may be easier to trace a person who uses television as a medium to spread hatred or porn, but it is very difficult to do so on the Internet with no boundaries whatsoever. The fact that the chances of being traced are very rare makes many resort to various criminal activities, right from sexual exploitation of children to running drug cartels from a particular part of the world, on the Internet. While laws pertaining to various Internet crimes do exist, it is very difficult to book a person on such charges – especially if he is not from the same country. The rising number of crimes validates this very fact, and advocates of Internet censorship cite this as one of the most prominent reason in their justification of Internet regulation. According to the critics of Internet censorship, it is a blatant violation of Internet privacy and freedom of press – which is used by authoritative administration to suppress the effectiveness of this means of mass media. The critics also question the idea of Internet Service Providers deciding what to put on the Internet and what to omit, as the chances of these service providers being biased cannot be ruled out. As far as government regulation is concerned, the government can only regulate what is going on in their country, but it is very difficult to regulate web pages which are generated from other countries. On the legal front, the owners of these websites can sue the administration over blocking their websites as well. While that may seldom work in non-democratic countries, it is an effective tool for such companies in democratic countries. At the same time, such censorship is also bound to come heavy on taxpayers pocket because the government will have to put in more funds to tackle new concepts of Internet technology, such as proxy server, which keep on changing every now and then.
__
Pros of Internet Censorship:
1. Censorship of pornographic material prevents the corrupting of the children.
2. Religious conflicts are avoided by the censorship of material deemed insulting or offensive to a particular religious community.
3. Censorship is necessary to preserve the secrets of a nation.
4. Censorship is useful in hiding sensitive military information, which could be used by an enemy state.
5. It keeps the internet safe for the kids (even though it’s a parent’s responsibility to do that).
6. Makes the internet a more useful tool for people, instead of a porn filled toy.
7. Internet may be used to portray wrong information about individuals or groups that could incite violence against them.
8. It can be used to prevent politically motivated propaganda.
9. It protects the privacy of people.
10. Breach of copyright is prevented.
11. Crazy disturbing ideas wouldn’t have a chance to reach the ears of the public.
12. It protects indigenous cultures from the bad influence of foreign cultures.
13. It prevents companies from spreading inaccurate or grossly exaggerated claims about their products.
14. Censoring sensitive information can stop unsuitable people gaining access to potentially harmful information.
15. Terrorists are prevented from learning about dangerous technology like the atom bomb.
16. Children are prevented from learning things that could harm them and others.
17. It can protect the safety of the public and can prevent disturbing the social order.
18. It shields the morals of society.
19. It restrains vulgarity and obscenity.
20. It prevents the public display of disrespect to any particular individual or community.
21. It also helps prevent hate groups and other similar organizations aiming to spread hate speech or related propaganda.
_
Cons of Internet Censorship:
1. Dictators and dictatorship use it to promote a flattering image of them and for removing any information that is negative to them. In some countries, dictators use censorship to further their own agendas while squashing those of the opposition.
2. Unscrupulous governments and individuals are apt to take advantage of censorship and use it to hide their own misdeeds from scrutiny of the world. Censorship has often been used by dictators to prevent the media reporting unsavory events in war torn and politically unstable countries.
3. Why should someone else decide what I can watch, or read, or play on the internet, I’m an adult, allow me to do what I want.
4. There is a very fine line between censorship and protectiveness—removing some types of information from the eyes and ears of children can lead to a lack of informative information on vital subjects like sex, drugs, and alcohol.
5. People should have the freedom to choose the type of information and ideas they wish to be exposed to rather than be told what they can and cannot do by a higher body.
6.Censorship can be used to prevent the public finding out what immoral and illegal activities certain individuals have been up to in their private lives—information that the public has a right to know.
7. Not everyone has the same idea of what images and ideas are appropriate for dissemination.
8. Freedom of speech/expression is compromised.
9. It prevents the free flow of ideas.
10. Withholding of information only leads to ignorance in the society.
11. Censoring of information may lead to a wrong image perceived by the public.
12. It is generally associated with dictatorship.
13. We live in a country of freedom. Censorship is against that freedom (for those who live in democratic nations).
14. It is a force against globalization.
15. It works against creativity.
16. If you hide something from people they will become extra curious about it.
17. It has no place in a truly democratic society.
18. It gives rise to and hides human rights abuses.
19. It is used to control people.
20. There can be different standards of morals among different societies quite different from the imposed ones by the censorship.
21. It may be used to block legitimate criticism.
22. Governments and media conglomerates can use censorship to distort facts or hide truths from ordinary citizens.
23. Governments should not control people. It should be the other way around.
24. It stifles the opposition, broadcasting only a particular point of view.
25. People have a right to know.
26. Censorship can prevent people who have an emergency from getting help.
27. Censorship can lead to ignorance of the world and other cultures.
28. Extreme censorship can lead to social upheaval.
29. Extreme censorship can lead to an oppressed and uneducated society.
30. It leads to international trade barriers lead to a further gap between the rich and the poor.
31. Some adult people want to view porn, and it’s their right to watch it.
32. Sites that are likely to be censored are billion dollar industries, and it would harm the economy.
33. Internet censorship harms communication during calamities like earthquakes and hurricanes when other modes of communications are disrupted.
_
In my view, cons have better & superior point of view than pros of Internet censorship. Besides child pornography, copy right/intellectual property right infringement and incitement of violence, I see no reason for Internet censorship.
__
Firewall:
A computer firewall provides protection from dangerous or undesirable content. Firewalls can be software or hardware. They act as a barrier between the Internet and your computer network. They only let safe content through and keep everything else out. Firewalls have helped protect computers in large companies for years. Now, they’re a critical component of home networks, as well. A firewall is simply a program or hardware device that filters the information coming through the Internet connection into your private network or computer system. Firewalls are customizable. This means that you can add or remove filters based on several conditions. Some common protocols that you can set firewall filters for include: IP (Internet Protocol) – the main delivery system for information over the Internet; TCP (Transmission Control Protocol) – used to break apart and rebuild information that travels over the Internet; HTTP (Hyper Text Transfer Protocol) – used for Web pages; FTP (File Transfer Protocol) – used to download and upload files; UDP (User Datagram Protocol) – used for information that requires no response, such as streaming audio and video; ICMP (Internet Control Message Protocol) – used by a router to exchange the information with other routers; SMTP (Simple Mail Transport Protocol) – used to send text-based information (e-mail); SNMP (Simple Network Management Protocol) – used to collect system information from a remote computer and Telnet – used to perform commands on a remote computer. Firewalls use one or more of three methods to control traffic flowing in and out of the network.
1) Packet filtering – Packets (small chunks of data) are analyzed against a set of filters. Packets that make it through the filters are sent to the requesting system and all others are discarded.
2) Proxy service – Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa.
3) Stateful inspection – A newer method that doesn’t examine the contents of each packet but instead compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded.
_
Concept of filtering information on Internet:
Filtering consists of social, political, and technical methods, all of which interact in ways that can strongly reinforce one another. In most filtered countries, the social pressure not to visit forbidden information is the most effective form of filtering (and applies equally well to on- and off-line information). Unfiltered Internet access increases the diversity of information and opinions users see. This increased diversity not only provides users with the new information and viewpoints but also, in itself, exerts a counteracting social pressure in favor of free information. Unfortunately, all of the tools used by social pressure lead to explicit aware actions, discouraging users from ever entering the positive feedback loop of free information. The combination of the social pressure to filter information and the initial hurdle of using circumvention technology reinforce one another. When social pressure fails, political pressures apply. In practice, the arrest of users for accessing blocked information is rare, but laws regulate at a higher level as well. For example, China has implemented regulations on Internet cafes that place Internet cafe users under increasingly strong surveillance, including requiring credentialing for access to the Internet. These sorts of measures both make clear the threat of the application of political force and reinforce the social pressures to filter. Also, laws are most likely to be enforced against known political dissidents, who are some of the key early users of circumvention technology. Technical filters are both the first and last line of defense against the dissemination of unwanted information. In the first place, technology allows the filtering country easily to designate which pieces of information it wants its citizens to avoid; this mere designation enables the social pressures to function. Technical filters only need to apply force (by actually blocking rather than merely designating offensive material) when social and political forces fail. It is the combination of social, political, and technical filtering methods that proves very difficult to break through and explains why circumvention tool use remains very small in proportion to the total number of Internet users in filtered countries.
_
Non-technical censorship:
Internet content is subject to censorship methods similar to those used with more traditional media. For example:
Laws and regulations may prohibit various types of content and/or require that content be removed or blocked either proactively or in response to requests.
Publishers, authors, and ISPs may receive formal and informal requests to remove, alter, slant, or block access to specific sites or content.
Publishers and authors may accept bribes to include, withdraw, or slant the information they present.
Publishers, authors, and ISPs may be subject to arrest, criminal prosecution, fines, and imprisonment.
Publishers, authors, and ISPs may be subject to civil lawsuits.
Equipment may be confiscated and/or destroyed.
Publishers and ISPs may be closed or required licenses may be withheld or revoked.
Publishers, authors, and ISPs may be subject to boycotts.
Publishers, authors, and their families may be subject to threats, attacks, beatings, and even murder.
Publishers, authors, and their families may be threatened with or actually lose their jobs.
Individuals may be paid to write articles and comments in support of particular positions or attacking opposition positions, usually without acknowledging the payments to readers and viewers.
Censors may create their own online publications and Web sites to guide online opinion.
Access to the Internet may be limited due to restrictive licensing policies or high costs.
Access to the Internet may be limited due to a lack of the necessary infrastructure, deliberate or not.
_
Technical Internet filter (filter):
Internet filter is any hardware or software installed intentionally to disallow/restrict retrieval of information/text/picture/video on internet. Content-control software, also known as censorware or web filtering software is a term for software designed and optimized for controlling what content is permitted to a reader, especially when it is used to restrict material delivered over the Web. Companies that make products that selectively block Web sites do not refer to these products as censorware, and prefer terms such as “Internet filter” or “URL Filter”. Content-control software determines what content will be available. Internet filters are setup by a System Administrator to prevent user access to sites that could be either inappropriate, or a potential security risk to the network. The restrictions can be applied at various levels: a government can attempt to apply them nationwide, or they can, for example, be applied by an ISP to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child’s computer, or by an individual user to his or her own computer. The motive is often to prevent persons from viewing content which the computer’s owner(s) or other authorities may consider objectionable; when imposed without the consent of the user, content control can constitute censorship. Some content-control software includes time control functions that empowers parents to set the amount of time that child may spend accessing the Internet or playing games or other computer activities.
__
Almost all data on the Internet is exchanged in a client server model, meaning simply that a client requests some data over the network that a server then returns over the same network. A filter can operate in three places in such a system – on the client requesting the data, on the server returning the data, or on the network between, during either the request or the response. Perhaps the most straightforward way to filter the Internet is to install software on a client machine that prevents the client from requesting offensive information in the first place. Many Internet accessible computer labs, including those at schools and libraries, use this sort of filtering because they have easy control over a small number of computers to be filtered. Parents can also install filter in home computer to prevent children from accessing pornographic sites. As with client side filtering, the technology of server side filtering is simple in practice – you need either remove the offending content from the server or prevent the server from sending a response with the offending content. In practice, most Internet servers are located in non-filtering countries, so filtering countries need the participation of either the hosting content owner or the hosting country. Another possible mode of server side filtering is to engage in hostile attacks on offending servers, for example via machine intrusions or denial of service attacks. Such attacks are expensive, however, and only temporarily effective and so have not been used widely to date. Internet traffic aggregates onto a small number of huge backbone data pipes and then disaggregates back out to the individual local networks. Filtering the vast majority of traffic on a large network requires only filtering the traffic on this small number of pipes (only regional traffic that never hits a backbone avoids such filtering). Specialized computers called routers control all Internet traffic, including that on the backbones. Filters can be installed on routers to block a site. All filtering countries use a combination of social, political, and technical filtering methods, and most filtering countries use a combination of technical filtering methods including client, server, and router filtering. Many countries use only a single router filtering method, such as IP blocking or DNS blocking. China has the most sophisticated technical filtering infrastructure, consisting of overlapping implementations of IP blocking, DNS blocking, and Keyword blocking.
_
__
Types of filter:
1) PC-based (end user) Filters: This type of filter is installed as software on your computer. This filter can be customized to meet a family’s needs. The parents can restrict child’s access to objectionable content. This filter can be disabled only by someone with the password. Client-side filters usually work well in places like libraries, because only some access points need to be filtered, for instance, the computers in the children’s playing and reading section.
2) PC-based Filter Product with Server-Based Filtering
3) Server-based Filters (installed on ISP server, DNS server, host server or any router computer between origin and destination of web request): Content limited ISPs are intended for both children & adults to allow access to almost everything, except what the ISP considers inappropriate.
4) Search-engine filters: Many search engines, such as Google and Alta Vista offer users the option of turning on a safety filter. When this safety filter is activated, it filters out the inappropriate links from all of the search results.
_
Most Web filters use two main techniques to block content: Blacklists and keyword blocking. A blacklist is a list of Web sites that the Web filter’s creators have designated as undesirable. Blacklists change over time, and most companies offer updated lists for free. Any attempt to visit a site on a blacklist fails. With keyword blocking, the software scans a Web page as the user tries to visit it. The program analyzes the page to see if it contains certain keywords. If the program determines the Web page isn’t appropriate, it blocks access to the page. Many filtering programs allow blocking to be configured based on dozens of categories and sub-categories such as these from Websense: “abortion” (pro-life, pro-choice), “adult material” (adult content, lingerie and swimsuit, nudity, sex, sex education), “advocacy groups” (sites that promote change or reform in public policy, public opinion, social practice, economic activities, and relationships), “drugs” (abused drugs, marijuana, prescribed medications, supplements and unregulated compounds), “religion” (non-traditional religions occult and folklore, traditional religions), …. The blocking categories used by the filtering programs may contain errors leading to the unintended blocking of websites. The blocking of DailyMotion in early 2007 by Tunisian authorities was, according to the OpenNet Initiative, due to Secure Computing wrongly categorizing DailyMotion as pornography for its SmartFilter filtering software. It was initially thought that Tunisia had blocked DailyMotion due to satirical videos about human rights violations in Tunisia, but after Secure Computing corrected the mistake access to DailyMotion was gradually restored in Tunisia. No matter what the censors’ reasons are, the end result is the same: They block access to the Web pages they identify as undesirable. Internet censorship isn’t just a parental or governmental tool. There are several software products on the consumer market that can limit or block access to specific Web sites. Most people know these programs as Web filters. Regulations and accountability related to the use of commercial filters and services are typically non-existent, and there is no or little oversight from civil society or other independent groups. Vendors often consider information about what sites and content is blocked valuable intellectual property that is not made available outside the company, sometimes not even to the organizations purchasing the filters. Thus by relying upon out-of-the-box filtering systems, the detailed task of deciding what is or is not acceptable speech has been outsourced to the commercial vendors.
_
White-list:
Most Internet filters works with a blacklist, which means that access to all sites is allowed, except some special sites (well, sometimes there are a lot of exceptions…). A white-list works the other way around: Access to all sites is blocked, except some special ones. For a normal ISP it is almost impossible to offer – because the Internet is nearly worthless. The white-list scheme is used by free Internet terminals that are sponsored by a company which allows users the free access to their e-commerce site. This filter scheme is the most difficult to circumvent.
_
Governments, Internet Service Providers (ISPs), Internet access providers, companies, parents or individuals can install software that restricts content to users. This software can be installed on an individual personal computer, but may also be installed ‘upstream’ on a home, company or ISP network server. In some cases, it is installed at a national ‘backbone’ level. A filter can screen particular words, email addresses, websites or other addresses and be used for example, if the installer wishes to prevent users within its borders from seeing particular content or a particular site. When used by governments, it is often branded as ‘censorship’, particularly if aimed at political speech. But in the case of ISPs, where filters are used for example to combat spam, it can be viewed as an essential service to users. In the household, parents might use a filter as a means of ‘child protection. These examples underscore the need to assess the social and political context in which filtering is conducted.
_
_
The most common points at which filtering can be applied include:
1. Internet Service Providers: ISPs are often mandated, encouraged, or incentivized to filter illegal or immoral content, or prevent search results from specified websites, by a regulator or other agency authorized by a government with jurisdiction over their activities. They also routinely filter spam and attempt to prevent infection by malware for reasons of stability and user protection.
2. Gateways to the Internet backbone: State-directed implementation of national content filtering schemes and blocking technologies may be carried out at the backbone level, often with filtering systems set up at links to the Internet backbone, such as international gateways in order to eliminate access to content throughout an entire country.
3. Institutions: Companies, schools, libraries and households can filter on the basis of their own criteria or on behalf of state authorities.
4. Individual computers: Filtering software can be installed on individual computers, such as a personal computer, to restrict the ability to access certain sites or use certain applications.
5. Law enforcement: Actions can be taken against users who engage in unlawful file sharing of music, malicious hacking, fraud, etc
_
The table below shows different technical methods of Internet filtering in various countries.
_
Various Internet censorship techniques include:
1. Internet Protocol (IP) address blocking: The most straightforward way to block traffic on a router is to block the IP addresses of servers hosting offensive material. The IP address is the number used to uniquely identify every computer (server or client) on the Internet, so blocking the IP address of a given machine makes it inaccessible. A router already needs to examine the destination IP of every bit of data it handles, so the only extra cost of filtering based on the destination (or origin) IP is the cost to lookup the destination IP address in a table of blocked IP addresses. Such lookups require relatively little computing power even at the scale required for a country level backbone router, making IP blocking a cheap method of filtering traffic on a large scale. Access to a certain IP address is denied. If the target Web site is hosted in a shared hosting server, all websites on the same server will be blocked. This affects IP-based protocols such as HTTP, FTP and POP. A typical circumvention method is to find proxies that have access to the target websites, but proxies may be jammed or blocked, and some Web sites, such as Wikipedia (when editing) also block proxies. Some large websites such as Google have allocated additional IP addresses to circumvent the block, but later the block was extended to cover the new addresses.
_
2. Domain name system (DNS) filtering and redirection: Another way to filter traffic on the network is to block the lookup of DNS names of offensive sites. The DNS name is the plain text name generally used by end users to lookup a site (e.g., google.com). These DNS names are translated into IP addresses by DNS servers. To block specific DNS name lookups requires only removing those DNS zones from all of a country’s DNS servers. There are more DNS servers than backbone routers, but the number is still relatively small, and the work of maintaining DNS block lists can be outsourced to individual ISPs simply by distributing the list to the participating ISPs. Blocked domain names are not resolved or an incorrect IP address is returned. This affects all IP-based protocols such as HTTP, FTP and POP. A typical circumvention method is to find an alternative DNS root that resolves domain names correctly, but domain name servers are subject to blockage as well, especially IP address blocking. Another workaround is to bypass DNS if the IP address is obtainable from other sources and is not itself blocked. Examples are modifying the Hosts file or typing the IP address instead of the domain name as part of a URL given to a Web browser.
_
3. Uniform Resource Locator filtering: URL strings are scanned for target keywords regardless of the domain name specified in the URL. This affects the HTTP protocol. Typical circumvention methods are to use escaped characters in the URL, or to use encrypted protocols such as VPN and TLS/SSL.
_
4. Keyword blocking which denies access to websites based on the words found in pages or URIs, or blocks searches involving blacklisted terms. Advances are enabling increasingly dynamic, real-time analysis of content, but this is not yet in wide use. Keyword block filtering examines the content of the traffic, rather than merely the destination and can examine content in any part of a request, including a specific URL in a web request or an offending keyword in an email. As such, keyword blocks can be much more precise than IP or DNS blocks, blocking only specific pages with a complete URL (http://hrw.org/china but not http://hrw.org/usa) or only specific pages with an offensive keyword (“Taiwan independence”). Keyword based blocking can be used for any Internet application that uses text, including web pages, email, and most instant messaging. Keyword blocking can be circumvented by encrypting all data sent over a connection, since encryption renders content into a form the filter cannot read. So a request that is blocked by a keyword filter as an HTTP request will not be blocked as an HTTPS request. Likewise, non-text data is generally impossible to filter by simple keyword filtering, since most such data must be interpreted as entire files, rather than as individual packets.
_
5. Packet filtering: Terminate TCP packet transmissions when a certain number of controversial keywords are detected. This affects all TCP-based protocols such as HTTP, FTP and POP, but Search engine results pages are more likely to be censored. Typical circumvention methods are to use encrypted connections – such as VPN and TLS/SSL – to escape the HTML content, or by reducing the TCP/IPstack’s MTU/MSS to reduce the amount of text contained in a given packet.
_
6. Connection reset: If a previous TCP connection is blocked by the filter, future connection attempts from both sides can also be blocked for some variable amount of time. Depending on the location of the block, other users or websites may also be blocked, if the communication is routed through the blocking location. A circumvention method is to ignore the reset packet sent by the firewall.
_
7. Full block: A technically simpler method of Internet censorship is to completely cut off all routers, either by software or by hardware (turning off machines, pulling out cables). This appears to have been the case on 27/28 January 2011 during the 2011 Egyptian protests, in what has been widely described as an “unprecedented” internet block. About 3500 Border Gateway Protocol (BGP) routes to Egyptian networks were shut down from about 22:10 to 22:35 UTC 27 January. This full block was implemented without cutting off major intercontinental fiber-optic links. Full blocks also occurred in Myanmar/Burma in 2007 and Libya in 2011.
_
8. Portal censorship and search result removal: Major portals, including search engines, may exclude web sites that they would ordinarily include. This renders a site invisible to people who do not know where to find it. When a major portal does this, it has a similar effect as censorship. Sometimes this exclusion is done to satisfy a legal or other requirement, other times it is purely at the discretion of the portal. For example Google.de (http://www.google.de/) and Google.fr (http://www.google.fr/) remove Neo-Nazi and other listings in compliance with German and French law.
_
9. Computer network attacks: Denial-of-service attacks and attacks that deface opposition websites can produce the same result as other blocking techniques, preventing or limiting access to certain websites or other online services, although only for a limited period of time. This technique might be used during the lead up to an election or some other sensitive period. It is more frequently used by non-state actors seeking to disrupt services.
__
10. Forced proxy server / transparent proxy: You have to specify a proxy server in your ‘Internet Explorer’ settings in order to get a connection to the Internet. Sometimes, the ISP is using a transparent proxy. With these you can’t see easily if there is a proxy or not. Every request you send to or receive from the Internet is checked at this server and redirected to you. Filtering can occur at forced proxy or transparent proxy.
_
11. Blocked ports: Ports are like doors for a special service to a server or PC. They rank from 0 to 65535. The standard ports are from 0 to 1024; these are the well known ports. If a censor blocks a port, every traffic on this port is dropped, so it’s useless for you. Most censors block the ports 80, 1080, 3128 and 8080, because these are the common proxy ports. Because all of the proxies on common ports are useless for you, you have to find proxies that are listening on an uncommon port. These are very difficult to find.
___
12. Deep packet inspection (DPI): Most forms of filtering require some inspection of the content of a message, which could be derived from the identity of the source, header information, for example, or the actual content of the message, such as the words, strings of words or images in the message or on the website. Increasingly this involves what is called ‘deep packet inspection’. Deep packet inspection is the use of computer systems that can inspect packets sent over networks using the Internet Protocol suite in ways that enable a third party, not the sender or receiver, to identify particular aspects of the communication. Inspection is done by a ‘middle-man’, not an endpoint of a communication, using the actual content of the message. For example, ISPs can apply this technology for the lawful intercept of messages on public networks to determine if customers are using the network for unlawful purposes or purposes that violate their user agreements. Governments in North America, Asia and Africa use DPI for various purposes such as surveillance and censorship. DPI can serve as a ‘one for all’ solution to monitor or regulate traffic and communication elements: e.g. the interception and logging of Internet traffic, enforcement of copyright, prioritizing limited bandwidth, and tracking users’ behavior.
_
Over- and under-blocking:
Technical censorship techniques are subject to both over- and under-blocking since it is often impossible to always block exactly the targeted content without blocking other permissible material or allowing some access to targeted material and so providing more or less protection than desired. An example is that automatic censorship against sexual words in matter for children, set to block the word “cunt”, has been known to block the Lincolnshire (UK) placename Scunthorpe. Another example is blocking an IP-address of a server that hosts multiple websites, which prevents access to all of the websites rather than just those that contain content deemed offensive. Internet filtering is almost impossible to accomplish with any degree of precision. Some filtering software blocks hate group sites. If a student is trying to research about skinheads or neoNazis, that information will be blocked on the Internet. Some software programs block any mention of the word “sex” and will therefore block out sites dealing with biological and botanical issues involving procreation. Filtering programs will block the word “breast” and therefore block information about breast cancer. Early Web filters would often block access to chicken breast recipes. The programs couldn’t tell the difference between an innocent site about cooking and a pornographic site, so they blocked all of them indiscriminately. A country that is deciding to filter the Internet must make an ‘‘overbroad’’or ‘‘underbroad’’ decision at the outset. The filtering regime will either block access to too much or too little Internet content. Very often, this decision is tied to whether the state opts to use a home-grown system or whether to adopt a commercial software product, such as SmartFilter or Websense, two products made in the United States and licensed to some states that filter the Internet. Bahrain, for instance, has opted for an underbroad solution for pornography; its ISPs appear to block access to a small and essentially fixed number of blacklisted sites. Bahrain may seek to indicate disapproval of access to pornographic material online, while actually blocking only token access to such material, much as Singapore does. United Arab Emirates, by contrast, seems to have made the opposite decision by attempting to block much more extensively in similar categories, thereby sweeping into its filtering basket a number of sites that appear to have innocuous content by any metric. Censorship opponents have some big problems with Web filtering software. Many Web filtering programs encrypt their blacklists, claiming that it helps minimize abuse. Opponents point out that the encrypted blacklist could also include Web pages that aren’t inappropriate at all, including pages that criticize the creators of the Web filter. Even if the programs’ creators aren’t blocking these sites on purpose, it’s easy for a Web filter to restrict access to the wrong sites. That’s because programs that search for keywords can’t detect context.
_
Transparency of filtering or blocking activities:
Among the countries that filter or block online content, few openly admit to or fully disclose their filtering and blocking activities. States are frequently opaque and/or deceptive about the blocking of access to political information. For example: Saudi Arabia and the United Arab Emirates (UAE) are among the few states that publish detailed information about their filtering practices and display an acknowledgment to the user when accessing a blocked website. In contrast, countries such as China and Tunisia send users a false error indication. China blocks requests by users for a banned website at the router level and an error message is sent, effectively preventing the user’s IP address from making further http requests for a varying time, which appears to the user as “time-out” error with no explanation. Tunisia has altered the block page functionality of SmartFilter so that users attempting to access blocked websites receive a fake “File not found” error page. In Uzbekistan users are frequently sent block pages stating that the website is blocked because of pornography, even when the page contains no pornography. Uzbeki ISPs may also redirect users’ request for blocked websites to unrelated websites, or sites similar to the banned websites, but with different information. When media was blocking my views on internet, it never admitted before people that they were blocking my views for whatever reason they have. I believe that if anybody is blocking internet content, he/she ought to have courage to tell the reason for blocking rather than hiding cowardly. Also, not giving reason for blocking amount to mala fide intention.
_
Internet circumvention technology:
Internet censorship circumvention is the processes used by technologically savvy Internet users to bypass the technical aspects of Internet filtering and gain access to otherwise censored material. Circumvention is an inherent problem for those wishing to censor the Internet, because filtering and blocking do not remove content from the Internet and as long as there is at least one publicly accessible uncensored system, it will often be possible to gain access to otherwise censored material. However, circumvention may not be very useful to non tech-savvy users and so blocking and filtering remain effective means of censoring the Internet for many users. There is a vast amount of energy, from commercial, non-profit and volunteer groups, devoted to creating tools and techniques to bypass Internet censorship, resulting in a number of methods to bypass Internet filters. Collectively, these are called circumvention methods, and can range from simple work-arounds, protected pathways, to complex computer programs. Different techniques and resources are used to bypass Internet censorship, including proxy websites, virtual private networks (VPN), sneakernets, and circumvention software tools. Solutions have differing ease of use, speed, security, and risks. Most, however, rely on gaining access to an Internet connection that is not subject to filtering, often in a different jurisdiction not subject to the same censorship laws. There are risks to using circumvention software or other methods to bypass Internet censorship. In some countries individuals that gain access to otherwise restricted content may be violating the law and if caught can be expelled, fired, jailed, or subject to other punishments and loss of access.
_
Circumvention Users: Users are individuals who use circumvention technologies to bypass Internet content filtering.
Circumvention Providers: Install software on a computer in a non-filtered location and make connections to this computer available to those who access the Internet from a censored location. Circumvention providers can range from large commercial organizations offering circumvention services for a fee to individuals providing circumvention services for free.
Circumvention Technologies: These are any tools, software, or methods used to bypass Internet filtering. These can range from complex computer programs to relatively simple manual steps, such as accessing a banned website stored on a search engine’s cache, instead of trying to access it directly.
_
The decision to use circumvention technology should be taken seriously, carefully analyzing the specific needs, available resources, and security concerns of everyone involved. There is a wide variety of technologies available for users who want to circumvent Internet filtering. However, using them for successful and stable circumvention service depends on a variety of factors, including the user’s level of technical skill, potential security risk, and contacts available outside the censored jurisdiction.
_
Many technologically savvy users can find alternative methods to access blocked content. However, for most people, blocking is an effective means for preventing access. Nevertheless, as filtering or blocking content does not erase the original content, some users can still access the content by using other connections for which access has not been blocked, creating a cat and mouse game between actors seeking to gain or block access to particular content. The fact that websites are not removed, but blocked, can mean that, for example in the case of child protection, the content has not been destroyed, but it has been made invisible for most non tech-savvy users.
_
While there are some outspoken supporters and opponents of Internet censorship, it’s not always easy to divide everyone into one camp or another. Not everyone uses the same tactics to accomplish goals. Some opponents of censorship challenge government policies in court. Others take the role of information freedom fighters, providing people with clandestine ways to access information.
_
Circumvention sites and tools should be provided and operated by trusted third parties located outside the censoring jurisdiction that do not collect identities and other personal information. Best are trusted family and friends personally known to the circumventor, but when family and friends are not available, sites and tools provided by individuals or organizations that are only known by their reputations or through the recommendations and endorsement of others may need to be used. Commercial circumvention services may provide anonymity while surfing the Internet, but could be compelled by law to make their records and users’ personal information available to law enforcement.
_
There is no absolutely effective filtering or circumvention methods. The battle between those who would filter and those who would circumvent that filtering turns on the amount of resources each side expends and the effectiveness of those resources. So there are always ways to filter a piece of information if the filterer is willing expends enough resources, and there are always ways to circumvent a filter if the circumventor is willing to expend enough resources. The goal is to find tools that meet users’ needs cheaply, and require disproportionate resources to block.
_
Hiding your IP address, using a proxy, using the onion router & obtaining an IP address to a website so you won’t have to rely on a public DNS server – these seem like a very intimidating task for the unprepared or novice internet user. You have to choose to bypass the Internet censorship or not. I can only educate you about circumvention technology but I can’t take any responsibility for misuse/abuse by you. In several censor countries you will go to jail if they catch you, in a lot of companies you will get fired and some schools will ban you. Of course, the censors not only block Internet traffic, they are also looking at it (in countries/companies with a little Internet population) and try to find out who is bypassing their firewall and how. An easy way to find out who (and how) is bypassing the firewall is by just looking for some identicators in the logfiles.
_
Things to remember while using circumvention techniques:
1. There are a many ways to get access to a blocked site. Most methods do not allow you to do this securely. Find a method that provides you with both access and security.
2. The more private your circumvention solution the better. Regardless of the choice of technology, private solutions stand the best chance of not being discovered and blocked.
3. You increase your level of stable and secure circumvention if you are able to use a trusted out of country contact.
4. Never use an out of country contact you do not know and trust! Your contact can be your key to safety and your most important source of vulnerability.
5. Remember that your provider (ISP) can potentially see everything you are doing through a circumvention system.
6. Violating state laws regarding Internet censorship can be a major risk. Do not use any technology you do not fully understand or know how to operate.
7. Make a thorough threat assessment based on your country context, skill level, and social network.
8. Make sure to understand fully the technology you are using. Some services advertize security and anonymity, but do not actually provide them or require extra configuration or fees in order to activate such features.
_
The Berkman Center for Internet & Society’s 2007 Circumvention Landscape Report included the following observations: It is reassuring to discover that most [circumvention] tools function as intended. They allow users to circumvent Internet censorship, even in countries like China and Vietnam, which use sophisticated technology to filter. However, all tools slow down access to the Internet, that most tools featured serious security holes [some of which were patched during or shortly after the study], and that some tools were extremely difficult for a novice Internet user to use. …It is estimated that the number of people using circumvention tools is around two to five million users worldwide. This number is quite high in absolute terms but quite low relative to the total number of filtered Internet users (China alone has over 450 million Internet users). Even accepting likely high end estimates of the project developers, it is estimated that less than two percent of all filtered Internet users use circumvention tools. … Simple web proxies represent at least as great if not greater proportion of circumvention tool usage as do the more sophisticated tools.
_
Identity:
Is protecting your identity online of paramount importance to you?
Do you want to surf and/or publish anonymously?
What is the difference between circumvention and anonymous surfing?
Circumvention and anonymity are different. Anonymous systems protect your identity from the website you are connecting to and from the anonymity system itself. They can be used for circumvention, but are not designed for this purpose and thus can easily be blocked. Circumvention systems are designed to get around blocking but do not protect your identity from the circumvention provider. Do not mistake open public proxies for anonymous systems – they are not. Although they may not ask for personal information, they can view and record the location of the computer from which you are connecting and all of the websites you visit through them. Commercial services which advertize anonymous surfing may still record your connection information and the web sites you visit. There is an important distinction to be made between circumvention and anonymity technologies. Circumvention technologies focus, with varying degrees of security, on allowing users to bypass censorship, while anonymity technologies focus on protecting the users’ identity from outside observers, such as government surveillance, as well as from the anonymity system itself. Circumvention systems that use encryption can protect users in some surveillance scenarios, but are not anonymous because owners of the circumvention system can see everything that the user does. They also cannot protect users from traffic analysis attacks in the same way that anonymity systems can. Anonymity systems protect privacy by shielding the identity of the requesting user from the content provider. In addition, they employ routing techniques to ensure that the user’s identity is shielded from the anonymous communications system itself. In addition to providing anonymity, these technologies are also used in many countries to bypass Internet censorship. Anonymity systems are increasingly being recommended by privacy advocates. The most widely known anonymity system is Tor. Tor works by routing a user’s request through at least three Tor servers. As the request hops from one Tor server to another, a layer of encryption is removed, so no individual server knows both the original source and destination of the request. The last server in the chain of hops, known as a circuit, actually connects to the requested content and then sends that information back through the circuit to the user. However, anonymity technologies are currently not difficult to block. Tor’s developers are working on building in blocking resistance to the anonymity system.
_
Invisible (anonymous) browsing:
Anonymous web browsing is browsing the World Wide Web while hiding the user’s IP address and any other personally identifiable information from the websites that one is visiting. Anonymous web browsing is generally useful to internet users who want to ensure that their sessions cannot be monitored. For instance, it is used to circumvent traffic monitoring by organizations which want to find out or control which web sites employees visit.
Your IP———-Your location——
Invisible Browsing has following advantages:
1. Protect your online privacy! It is your right!
From the moment you connect to Internet you are exposed to multiple online privacy threats and challenges. Whether we like it or not, the Internet is for everybody, including bad persons, cyber thieves that might easily compromise your computer and steal your sensitive data. It is your right to protect your online privacy and to stop them following you. The hide IP software will let you surf anonymously and prevent your IP or other confidential information to be collected without your permission.
2. No discrimination – protect your right to free speech!
Even if you live in China, Saudi Arabia or any other corner of the world you have the right to read what news you want, to see what movie you want and to comment what blog post/forum discussion you want, even if it is in American “space”. You are free to present your opinion.
3. Access Restricted Websites & Blogs!
For many years, the web has been heavily censored in countries around the world. That censorship continues at this very moment and it is happening right now even in America. It did not happen overnight but slowly came to America’s shores from testing grounds in China and the Middle East. Get around blocked sites with Invisible Browsing.
4. Bypass Internet censorship and surf the web anonymously!
Government and other organizations set Internet restrictions in order to control the users’ habits. You need to go over the rules they set for you without ever asking your opinion. Invisible Browsing will help you bypass these restrictions by allowing you to change your real IP address according to your browsing needs.
_
Anonymous Communication Systems:
Anonymous technologies conceal a user’s IP address from the server hosting the web site visited by the user. Some, but not all, anonymous technologies conceal the user’s IP address from the anonymizing service itself and encrypt the traffic between the user and the service. Since users of anonymous technologies make requests for web content through a proxy service, instead of to the server hosting the content directly, anonymous technologies can be a useful way to bypass Internet censorship. However, some anonymous technologies require users to download software and can be easily blocked by authorities. It is possible to hide your real IP address on the Web by using an anonymous proxy server or a VPN server. A proxy acts as an intermediary, routing network packets between your computer and the Internet. When using a proxy for anonymous web surfing, an IP address of that proxy is relayed instead of your own helping you stay anonymous. And remember: “Privacy is not a crime and anonymity is not morally ambiguous or wrong, they are your right.”
_
With AnonymoX, a Firefox add-on (on Firefox browser), you can gain access to all such websites by browsing the web anonymously. With it, you can change your IP address, location and visit websites that are blocked or inaccessible in your country. You can change the IP and location with only a few simple clicks without having to use proxies. All you need to do is either click the blue button next to the search bar or in the add-on bar, or click Change Identity to get a new IP Address. Also, delete cookies by simply clicking the more option.
__
Anonymizers are not entirely secure. If an anonymizer keeps logs of incoming and outgoing connections and the anonymizer is physically located in a country where it is subjected to warrant searches then there is a potential risk that government officials can reverse trick and identify all users who used the anonymizer and how they used it. Most anonymizers state they do not keep logs but there is currently no way to confirm that. However, if the user used another anonymizer to connect to the exposed anonymizer, that user is still anonymous. This is sometimes called daisy-chaining. The safest way therefore is to use a chain of Proxy servers to make your requests or use a specialist service like TOR which is designed to make it hard to track internet usage.
_
Different ways to bypass Internet censorship:
Using a different ISP:
Well, it’s as easy as it sounds: Just change your Internet Service Provider! For example, only in ‘Nordrhein-Westfalen’ (a state of Germany) is there a censoring firewall, so you can just subscribe to an ISP outside that state. But normally the censorship counts for all the country. One possibility is to try out an ISP outside the country. That costs a lot, but that way you will have a normal Internet access and won’t have to worry about getting around filters. This could be a normal dialup provider in an neighbor country or even better, a 2-way Internet access via satellite like http://www.europeonline.com/, http://www.remoteworkcentral.com/, http://registrierung.tiscali.de/produkte/1400_satellit.php, http://www.gilat.de/, http://www.hns.com/, http://www.vsatnet.com/, http://www.starband.com/, http://www.wildblue.com/, http://www.skycasters.com/, http://www.directduo.com/, http://www.orbitsat.com/, http://www.ottawaonline.com/ and so on, just search with a search engine for ’2-way Internet via satellite [your country or neighbor country]‘ or something like that.
_
Using a non censoring DNS-server:
Normally, you would automatically would use the DNS-server of your ISP to resolve domain names. Internally, only these IP-addresses are used to send/receive data on the Internet. If your DNS-server is censoring, you simply can use another DNS-server. Under Windows, just right-click in your system panel on the ‘network’ icon and select properties of the TCP/IP-protocol. In Linux you have to edit the ‘/etc/resolv.conf’ file. Use the server that is (virtual) your nearest. If you want to setup your own DNS-server use Bind (http://www.isc.org/products/BIND/). Using DNS servers other than those supplied by default by an ISP may bypass DNS based blocking. OpenDNS and Google offer DNS services or see List of Publicly Available and Completely Free DNS Servers.
_
Using a non censoring proxy server:
You can put a proxy server between your Internet connection and the site you want to visit. You send your request for a special website to that proxy server, which request the page from the Internet and deliver it to you. Normally, those servers cache the requested pages, so that on the next request he can deliver the page directly from the cache. That would be faster and cheaper. For the eyes/computers of our ISP/Government we are only connecting to the proxy, they can’t easily see, that we are connecting to a “blocked site”. But sometimes the standard proxy ports (80, 1080, 3128 and 8080) are blocked. In that case you have to use the proxies that are listening on an uncommon port.
_
Instruct your Web browser to take a detour through an intermediary computer, called a proxy, that:
–is located somewhere that is not subject to Internet censorship.
–has not been blocked from your location.
–knows how to fetch and return content for users like you.
_
_
One of the most popular ways is to use proxy servers. You can get updated proxy information sent to you automatically by sending an e-mail to [email protected]. Note: Send an email regularly to get currently working proxies. If you don’t know how to use a proxy server, learn it through any computer engineer about how to set up your own computer to use proxy or use a proxy on another Web site.
_
Open Proxies:
An open proxy is a proxy server which will accept client connections from any IP address and make connections to any Internet resource. It is not hard to find open proxy servers on the Web. Lists of open proxy servers can be found in seconds with a simple online search. These lists are frequently updated, and some even include bandwidth statistics info and where the server is hosted. Configure your Internet browser to access an open proxy. However, many open proxy servers are short-lived and you may have to repeat this process as necessary and open proxies may not work well if your ISP has installed content filters.
_
How to bypass the great firewall of china (GFW) or any such censorship mechanism?
The ultimate function of an anti-censorship system is to connect censored users to uncensored Internet securely and anonymously. This function requires a complex system with many components working together. Figure below shows the components of a typical anti-censorship system. Censored users (1) use circumvention client software (2) on their computers to connect to circumvention tunnels (4), usually with the help of a tunnel discovery agent (3). Once connected to a circumvention tunnel, a user’s network traffic will be encrypted by the tunnels and penetrate the GFW (7) without being detected by the censors (6). On the other side of the GFW, the network traffic will enter a circumvention support network (8) set up and operated by anti-censorship supporters (9). The computers, sometimes called nodes, in the circumvention support network act as proxies to access content from the unobstructed Internet (10) and send the information back, not necessarily taking the same route, to the censored user’s computer.
_
In fact, the most mysterious component in an anti-censorship system is the tunnel discovery agent (3). With such an agent, a user does not need to configure the software. The agent will automatically find circumvention tunnels for the user’s particular client software. Little public information is available from the most successful anti-censorship tools, because their technologies are proprietary and source code is not available. Some of the agent implementations may have exploited weaknesses in the GFW technologies and can blend the discovery traffic with regular traffic without being detected. The continual success of the leading anti-censorship tools (Garden, UltraSurf and DynaWeb, ) for so many years can be significantly attributed to their innovative tunnel discovery agent designs. _
_
Client side software:
Increasingly in China, people can access censored Web sites via special portal pages called “Client side software.” These are services provided by companies that specialize in offering free access to information. Experts recommend Freegate, Dynaweb, Fire Phoenix, UltraSurf, freenet, and several others. Client-side software enables users to browse the Internet freely. The experience is the same as while using the regular Internet Explorer browser but it automatically searches the highest speed proxy servers in the background or it uses a parallel network of servers maintained by a company that promotes freedom of information on the Internet.
_
Tunneling Software:
Tunneling encapsulates one form of traffic inside of other forms of traffic. Typically, insecure, unencrypted traffic is tunneled within an encrypted connection. The normal services on the user’s computer are available, but run through the tunnel to the non-filtered computer which forwards the user’s requests and their responses transparently. Users with contacts in a non-filtered country can set up private tunneling services while those without contacts can purchase commercial tunneling services. “Web” tunneling software restricts the tunneling to web traffic so that web browsers will function but not other applications. “Application” tunneling software allows one to tunnel multiple Internet applications, such as email clients and instant messengers.
_
Using a VPN (virtual private network) Service:
VPN is about creating a virtual private network or tunnel over the public network “internet”. Each VPN tunnel is totally anonymous on the public internet and it helps to keep your activities of internet users anonymous, private and secure. A VPN connection is an attractive option for people concerned about their security and privacy. It is not a web proxy and it is much more advanced and secure. A security tunnel that protects your data as it travels from your computer to the VPN server before letting it out on to the internet. As long as that VPN service is outside user’s country, it’ll be very difficult to stop users using such services to circumvent DNS censorship. Using VPN services, you can now surf the web anonymously & prevent your ISP from keeping logs on your online activities! If sites are blocked you can access Blocked websites … Unblock blocked websites by bypassing proxies & it works with Skype and other VoIP applications too! Unlike using a proxy site that is very limited constantly being blocked, VPN services are compatible with pretty much any internet application such as dreamweaver, Internet Explorer, FireFox, Skype, Google Talk, Net2Phone, MSN, ICQ, and many more! If you are concerned about your privacy on the web, a VPN will allow you to be anonymous on the web by hiding your real IP! Via an encrypted VPN tunnel you can secure your internet connection to the web, when using an unsecured wireless network. In the Middle East, Asia and around the world internet service providers are blocking websites and VoIP applications. Bypass Internet Censorship in China, Malaysia, UAE, Bahrain, Oman etc. using VPN services. You can unblock all blocked sites like Orkut, Myspace, YouTube, Photobucket, bebo etc.
_
Using TOR:
I have already discussed TOR earlier in anonymous surfing. TOR is more or less a network of proxies. One person accesses a proxy and that proxy forwards that access to another proxy, trying to erase the user’s tracks. That proxy sends that stream to another proxy and the stream keeps going through these steps until it finally reaches what is known as an “exit-node”. That exit node then accesses the internet on the user’s behalf and acts as an intermediary in the process. As long as that exit node exists outside of the user’s country, there is a very good chance that it won’t be affected by DNS censorship imposed by the ISPs onto their DNS servers. Tor is a network designed to protect privacy and security by making use of encrypted traffic tunneled through a collection of relays. In practical terms, Tor makes it possible for someone subject to Internet censorship to conceal the ultimate destination of any request for data and any data sent. It is far superior to the earlier method of swapping around lists of proxy servers since the Tor software handles for you the task of connecting to a growing and rapidly changing list of relays that carry traffic in not one but several jumps to its ultimate destination. To use Tor as a client, download and install the software as well as a browser plug-in such as the Torbutton for Firefox and activate it when you wish to connect through the Tor network. Depending on the number of relays available and your connection, traffic can be significantly slower than what you’re used to so turn it off when you don’t need it. If you are fortunate to be in a country without significant Internet censorship, consider installing Tor and then adding your own computer as a relay for traffic through its network. The more people run relays, the stronger the network becomes.
_
JAP:
JAP is a free and open source anonymity tool invented by a German university. It sends your traffic encrypted through different mixes, so that absolutely nobody, not even the owner of one of the mixes know who is accessing which site. This is also one of the best tools to circumvent censorship. Just follow the installation instructions on http://anon.inf.tu-dresden.de/index_en.html or http://www.anon-online.org/index_en.html on installing the Java client (available for Windows, Unix, Linux, OS/2, Macintosh and others).
_
Using a Web-2-phone service:
These are services which you dial into with a normal telephone. Then you request the website you want to visit and the operator/computer voice then reads the content to you.
__
CGI Web-Proxy:
A CGI proxy is a free script that can be found on many Web pages that acts as an HTTP or FTP proxy. What this means is that through a CGI proxy, you can access any Web site using the server of a different Web site. A CGI proxy allows the Web user to be anonymous and access Web sites that may be restricted. CGI proxy will help you get around blocking software. CGI Proxy is the engine that most web-based circumvention systems use. Private web-based circumvention systems turn a computer into a personal, encrypted server capable of retrieving and displaying web pages to users of the server connecting remotely. Private web-based circumventors include providers, who install and run circumvention software in an uncensored jurisdiction, and users, who access the service from a jurisdiction that censors the Internet. The circumvention provider grows his/her private network based on social relations of trust and private communications making it difficult for censors to find and block. CGI proxies use a script running on a web server to perform the proxying function. A CGI proxy client sends the requested URL embedded within the data portion of an HTTP request to the CGI proxy server. The CGI proxy server pulls the ultimate destination information from the data embedded in the HTTP request, sends out its own HTTP request to the ultimate destination, and then returns the result to the proxy client. A CGI proxy tool’s security can be trusted as far as the operator of the proxy server can be trusted. CGI proxy tools require no manual configuration of the browser or client software installation, but they do require that the user use an alternative, potentially confusing browser interface within the existing browser. Webproxies are CGI-scripts that you access with your browser. The addresses under CGI proxy are not really meant as proxies. They act as translators, html-checkers or as a web archive. You can use them as a kind of proxy anyway. These webproxies are good instruments for bypassing. You don’t have to configure your browser or anything, but it’s kind of slow and won’t work with all webpages. Only the proxies that are going over a secure connection can be used for phrase filtering, but the others are perfect for URL/IP filtering. Use them in your school, company or library when you have no privileges to install/change something on the machine. These links points to google.de because the site is very small, useful, always on, and does not contain the “.com” extension of DOS-Files that are filtered by some proxies.
Translators, warpers, etc that can be used as a proxy are:
http://babelfish.altavista.com/ (Translator)
http://www.freetranslation.com/web.htm (Translator)
http://translation.langenberg.com/ (Translator)
http://www.systransoft.com/ (Translator)
http://www.translate.ru/srvurl.asp?lang=de (Translator)
http://translator.abacho.de/ (Translator)
http://www.t-mail.com/cgi-bin/tsail (Translator)
http://www.google.com/language_tools?hl=de (Translator)
http://tarjim.ajeeb.com/ajeeb/default.asp?lang=1 (Translator)
http://rinkworks.com/dialect/ (Fun Translator)
_
HTTP proxies send HTTP requests through an intermediate proxying server. A client connecting through an HTTP proxy sends exactly the same HTTP request to the proxy as it would send to the destination server unproxied. The HTTP proxy parses the HTTP request; sends its own HTTP request to the ultimate destination server; and then returns the response back to the proxy client. An HTTP proxy tool’s security can be trusted as far as the operator of the proxy server can be trusted. HTTP proxy tools require either manual configuration of the browser or client side software that can configure the browser for the user. Once configured, an HTTP proxy tool allows the user transparently to use his normal browser interface.
__
Using steganography:
Hide content inside of images. More Info: http://en.wikipedia.org/wiki/Steganography
Camera/Shy is the only steganographic tool that automatically scans for and delivers decrypted content straight from the Web. It is a stand-alone, Internet Explorer-based browser that leaves no trace on the user’s system and has enhanced security. Camera/Shy is an application that enables stealth communications, such software can be useful in countries where Email communications are regularly monitored and censored, such as happens in China.
_
Using a special proxy like P2P program:
A peer-to-peer computer network relies primarily on the power and bandwidth of each of the participants in the network. It is a connection between equals and it is typically used to share audio or video files, or anything in digital format. There are different projects of peer-2-peer programs to bypass censorship. They work like Napster, Kazaa and eDonkey, which means that you have to download a little tool that contains a server and a client part. Freenet is the oldest and most widely spread P2P-program to beat censorship, so a lot of people use it and it has actually worked well for several years. Freenet works by storing small encrypted snippets of content distributed on the computers of its users and connecting only through intermediate computers which pass on requests for content and sending them back without knowing the full file, similar to routers in the internet which route packets without knowing anything about files – but with a layer of strong encryption, caching and without reliance on centralized structures. This allows users to anonymously publish or retrieve various kinds of information.
_
Peek a Booty:
The goal of the Peekabooty Project is to create a product that can bypass the nationwide censorship of the World Wide Web practiced by many countries. Peek a booty uses a complicated communications system to allow users to share information while revealing little about their identity. When a node receives a request for a web page it randomly decides whether to pass this on or access the page itself. It also only knows the address of its nearest partner. This makes it difficult to determine who requested what information and is designed to protect users from anyone trying to infiltrate the system from inside.
_
Usenet:
The normal port for newsservers 119 is usually blocked, so you have to access the Usenet via a different port. If you sometimes only want to read some very common newsgroups you can easily visit them via free web-based newsservers like http://groups.google.com/ and http://news.spaceports.com/ . A lot of newsserver companies offer their services on a non standard port. Just ask them before signup. If you need access to a newsserver with your newsclient you have to subscribe to one of these newsserver-companies which allow access to their newsservers on an uncommon port.
_
Instant Messenger:
Instant Messengers are very popular. You have to register your nickname at one of the companies and download their software. Then when you are on the Internet you can start the software and log onto their servers. You are then marked as “online” and all your friends who know your nickname and have the same Instant Messenger client can see that you are online and easily chat with you. Yahoo messenger and MSN messengers are very popular.
_____
Psiphon:
New software that helps Web users skirt Internet censorship and surveillance by connecting to the computers of family or friends in such countries as the U.S. and Canada. Psiphon relies on people in uncensored countries to install the software on their computers. By connecting to a Psiphon computer through the Internet, friends and family in such places as China or Iran can surf the Web as though they were in Canada or U.S.
_
Infranet:
An increasing number of countries and companies routinely block or monitor access to parts of the Internet. To counteract these measures, new system is proposed named Infranet, a system that enables clients to surreptitiously retrieve sensitive content via cooperating Web servers distributed across the global Internet. These Infranet servers provide clients access to censored sites while continuing to host normal uncensored content. Infranet uses a tunnel protocol that provides a covert communication channel between its clients and servers, modulated over standard HTTP transactions that resemble innocuous Web browsing. In the upstream direction, Infranet clients send covert messages to Infranet servers by associating meaning to the sequence of HTTP requests being made. In the downstream direction, Infranet servers return content by hiding censored data in uncensored images using steganographic techniques. A research paper described the design, a prototype implementation, security properties, and performance of Infranet. The security analysis shows that Infranet can successfully circumvent several sophisticated censoring technique.
_
Using a Web DNS Tool:
Just by using publicly available DNS look-up tools, one can easily obtain server IP addresses for later use. If a domain is censored, one can simply replace the domain name part of the URL with the IP address and still access the website.
_
Using Foxy Proxy:
It’s a simple plug-in for FireFox you can download and install. After getting a nice list of simple proxies that preside outside of your country, you have a better chance at accessing the website that has been censored by your government and/or corporate interests.
_
Using MAFIAAFire:
A simple plug-in for FireFox (or Chrome) you can download and install. If a website has had its domain seized, then you can be redirected to an alternate domain and still access the website.
_
How to publish information:
It is one thing is to access information that is already censored, but another challenge is to publish one’s own information that can’t easily be censored. Here you can see few ideas on how to avoid censorship while publishing on internet:
1) Publish with a lot of mirrors. Especially dynamic IP’s with a dyndns.org redirector are useful. Put your pages on so many different servers that the censor’s can’t successfully block all servers.
2) Fax Polling. You can either use a service on the Internet or provide that service on your own computer with a fax modem.
3) Use one-time-addresses. These are links/URLs that are only valid for 1 visit or 1 hour, they are often used for paid downloads.
4) Hide the ‘dangerous’ content. For example, save text as images. The users won’t notice it, but it is difficult for the censor-spiders to ‘read’ the content.
5) Host with a secure server in another country. For example, with http://www.havenco.com/ which is located at Sealand, an independent country on a little island in the North Sea near England?
6) Encrypt the content. Use .htaccess and/or SSL for your website and AES, Twofish or Rijndael for files.
7) Offer your data in P2P-Programs. Filesharing programs like Kazaa or eDonkey are very difficult to censor.
8) Send content via email. Create an autoresponder from which everyone with a hotmail account can receive your content.
9) Martus. It’s an encrypted bulletin service to post and view information. See: http://www.martus.org/
10) Individuals associated with high profile rights organizations, dissident, protest, or reform groups should take extra precautions to protect their online identities while publishing their views.
__
How do I Get Past Blocked Websites?
1) Using a Web Proxy:
Any internet search engine can direct you to an infinite number of proxy web sites. Systems Administrators add proxy sites to their block sites list all the time, but there are always new proxies opening, so there will never be a short supply. There are several webpages that you can go to, to bypass your ISP’s block on websites. Some of these websites are: www.ctunnel.com…, www.gtunnel.com…, www.backdoor.com…, www.proxyvan.com… and www.mirrorproxy.com…. All you have to do on these websites is type in the website that you want to go to in the space provided click Go and you’ve bypassed the ISP. However do keep in mind that if your ISP has the above mentioned websites blocked and others like them then there is no way around the block.
2) Use translation service:
Begin by going to a free translation web site, such as Google’s language tools, or freetranslation.com. Look for a link that says something along the lines of “web translator” or “web site translator.” Select your language. Select the language you want to “translate”. You should select that you are translating from a foreign language into English. English words on the website will remain in English, so you are basically making use of the translation engine without changing any of the words. Set your destination. Type in the URL of the web site that has been blocked by your ISP and click the translate button. You will arrive on a page that has the translation tools in a frame on the top of the page, with the blocked site appearing in the frame below it.
3) URL Redirection Service:
Begin by visiting a web site that provides URL redirection services. Two popular sites are tinyurl.com and shorturl.com, but you can easily find others by conducting a keyword search. Type in a new URL that will be your secret web address to get to the site that has been blocked. The system will check to see if your desired URL is available. If so, you may claim it to use. Fill out the required information about yourself (in case you ever want to edit your link) and the blocked site that you are trying to get access to. You will be offered a premium account, which costs money. Select the basic account, which is free, and you should now be able to access the blocked site by typing in your private URL.
Note:
Some administrators may have a number of popular web proxies and redirection services blocked as well. If this happens to you, simply look for another one to try. The more obscure and hard to find the web proxy or redirection site is, the less likely it will be that the administrator will find it to block.
4) An exact replica of the online story in print:
Create a free account at Adobe website and provide the URL address that you wish to convert. This service will create a nice PDF of the webpage and send that you as an attachment in an email.
5) Using Akamai to bypass Internet censorship:
Take the URL of the site you want to access, e.g. http://www.yahoo.com/, drop the “http://” at the beginning, and add the rest to the end of the akamaitech.net URL: http://a1.g.akamaitech.net/6/6/6/6/www.yahoo.com/ (Don’t forget the “/” on the end, or the trick won’t work.) Load the URL into your browser. You should be able to view the contents of the page — in this case, the contents of http://www.yahoo.com/.
6)”Cached” Pages:
Many search engines provide copies of web pages, known as cached pages, of the original pages they index. When searching for a web site, look for a small link labeled “cached” next to your search results. Since you are retrieving a copy of the blocked page from the search engine’s servers, and not from the blocked web site itself, you may be able to access the censored content. However, some countries have targeted caching services for blocking.
7) RSS Aggregators:
RSS Aggregators are web sites that allow you to bookmark and read your favorite RSS feeds. RSS Aggregator sites will connect to the blocked we sites and download the RSS feed and make it available to you. Since it is the aggregator connecting to the site, not you, you will be able to access the censored content.
8) Alternate Domain Names:
One of the most common ways to censor a website is to block access to its domain name, e.g. news.bbc.co.uk. However, sites are often accessible at other domain names such as newsrss. bbc.co.uk. Therefore if one domain name is blocked try to see if the content can be accessed at another domain. For example the following domain names refer to the same web site: http://www.wikimedia.org/ and http://text.pmtpa.wikimedia.org/. The alternative URLs may not be blocked. Entering an IP address rather than a domain name (http://208.80.152.2/) or a domain name rather than an IP address (http://wikimedia.org/) will sometimes allow access to a blocked site.
9) Web Accelerators:
Web Accelerators cache web pages and make it appear as if your Internet connection is faster. Since you are retrieving the website from the cache and not from the blocked website directly, you can access censored content.
Example: webaccelerator.google.com
10) Mirror and archive sites:
Copies of web sites or pages may be available at mirror or archive sites such as http://www.archive.org/ (http://www.archive.org/) and the alternate sites may not be blocked.
11) Web to E-mail services:
Web to e-mail services such as http://www.web2mail.com/ (http://www.web2mail.com/) will return the contents of web pages with or without images as an e-mail message and such access may not be blocked. Several years ago when the Internet connections where slow and the “www” was just invented, many people just got email restricted access to the Internet. That’s the origin of the “Agora” and “www4email” software. Some of these email robots are still available and we can use them to bypass Internet censorship.
12) Using Your HOSTs File:
For most users, there is actually a hosts file on their computer that can be used to connect domain name to server IP address without the use of a public DNS server. If a website is censored through a DNS server, one can simply use the HOSTs file so that a public DNS server isn’t even used in the first place. You just type in the domain name in your URL and the website would still appear.
_
Other tricks:
Pakistan Blogspot hack – pkblogs.com – is excellent but limited only to blogspot.com blogs. It won’t work for sites like typepad.com or geocities.com which are also blocked. Secondly, we sometimes don’t see images when accessing blogspot sites via pkblogs.com The anonymous proxy surfing services use different ports which may be blocked by your local firewall. Also, these services sometimes append their own ads to the visiting site.
_
Alternatives to Filtering:
Government agencies have used a number of techniques to deny access or censor particular types of content that differ from content filtering. These include:
1.Denial of service attacks, which produce the same end result as other technical blocking techniques – blocking access to certain websites – although only temporarily, and this is more often used by non-state actors seeking to disrupt services. A ‘denial of service’ attack disables servers hosting particular Web sites, either of opposition media outlets or of foreign governments;
2. Restricting access to domains or to the Internet, such as by installing high barriers (costs, personal requirements) to register a domain or even to get Internet access;
3. Search result removals, by which search engine providers can filter web content and exclude unwanted websites and web pages from search results. By using blacklists, parsing content and keywords of web pages, search engines are able to hinder access. This method makes circumventing the denial of access more difficult as search engines are not always transparent about the filtering of search results;
4. Take-down of websites, by removing illegal sites from servers, is one of the most effective ways of regulating content. To do so, regulators need to have direct access to content hosts, or legal jurisdiction over the content hosts, or an ability to force ISPs to take down particular sites. In several countries, where authorities have control of domain name servers, officials can deregister a domain that is hosting restricted content.
5. Type of ‘cyberwarfare’ that occurs more regularly is hacking into computers and stealing information, as well as planting Trojans or viruses.
_
Self-regulation of Internet content:
Most would agree that there is no single or absolute definition of self-regulation. Instead, the definition lies somewhere on a spectrum ranging from the formal delegation of regulatory powers to industry by government, to self-initiated, organized, and managed “regulation” by industry and other private sector players. In the current context, self-regulation is defined as a system of Internet governance that relies on the private sector — the market — to lead in the definition of the rules that such a system will follow, and in the development and implementation of a set of mechanisms and activities that will support these rules and govern behavior. In particular, we focus on market-based approaches to the management and control of controversial Internet content. It is widely accepted that the Internet is not conducive to traditional forms of content control such as broadcasting regulations. In the first instance, the Internet is not conducive to regulation due to its international nature and underlying packet-based communication mechanism. Any attempt to regulate the flow of content on the Internet at a national level would be immensely expensive, detrimental to the performance of the network, and easily circumvented (one can simply obtain Internet access in a jurisdiction that is not regulated), rendering such regulation impractical, if not technologically unfeasible. An equally important point is that regulation is not considered to be an effective means of addressing the challenge of offensive Internet content from a public policy point of view. Of fundamental importance to our discussion of Internet content is the “freedom of thought, belief, opinion, and expression, including freedom of the press and other media of communication.” This right is only subject to “such reasonable limits prescribed by law as can be demonstrably justified in a free and democratic society.”
_
Voluntary rating systems:
Another viable solution to the problem of children viewing objectionable material on the Internet is the use of a voluntary rating system. Voluntary rating systems are increasingly viewed as a means of addressing controversial Internet content while, at the same time, strengthening freedom of expression on the Internet. Used in conjunction with both browser-based and stand-alone filtering technologies, rating systems are used to filter or block undesirable content and to direct users to desirable content. In voluntary systems, content providers label their Web sites according to the category in which the site’s content falls. Filtering or browser software then “read” the label and determine whether or not it will, based on the user’s predetermined criteria, provide access to the particular content. The RSACi (Recreational Software Advisory Council on the Internet rating system) is a completely voluntary rating system which allows web publishers to have their site rated by the Recreational Software Advisory Council. The ratings measure the web site’s content levels of sex, nudity, language and violence (Recreational Software Advisory Council Web Site). RSACi is being used in conjunction with Microsoft’s popular web browser, Internet Explorer, to allow parents to decide what rating is appropriate for their child. The parents needs only to follow a few simple steps in which they enter a security password and decide what ratings are appropriate for their child. After the rating system is enabled, the child user will be unable to browse web sites that have ratings above the standards set by the parents without knowledge of the password. Emerging from RSACi is a new organization called the Internet Content Rating Association (ICRA). ICRA was formed in mid-1999 by a variety of industry players and has set out to establish and implement an international, culturally neutral system that is based on the voluntary rating of Internet content by Web site and other content providers.
__
Content labeling:
Content labeling may be considered another form of content-control software. In 1994, the Internet Content Rating Association (ICRA) — now part of the Family Online Safety Institute — developed a content rating system for online content providers. Using an online questionnaire a webmaster describes the nature of his web content. A small file is generated that contains a condensed, computer readable digest of this description that can then be used by content filtering software to block or allow that site. ICRA labels come in a variety of formats. These include the World Wide Web Consortium’s Resource Description Framework (RDF) as well as Platform for Internet Content Selection (PICS) labels used by Microsoft’s Internet Explorer Content Advisor.
_
The World Wide Web Consortium has recently developed a set of technical standards called PICS (platform for internet content selection) that enable people to distribute electronic descriptions or ratings of digital works across the internet in a computer readable form. PICS was originally developed to support applications for filtering out pornography and other offensive material, to protect children. An information provider that wishes to offer descriptions of its own materials can directly embed labels in electronic documents or other items (such as images)—for example, such labels may indicate whether the content is appropriate for particular audiences such as minors, patients, etc.
_
PICS:
PICS, the Platform for Internet Content Selection, is designed to enable supervisors-whether parents, teachers, or administrators-to block access from their computers to certain Internet resources, without censoring what is distributed to other sites. It draws on two unique features of the Internet. First, publishing is instantaneous, world-wide, and very inexpensive, so it is easy to publish rating and advisory labels. Labels and ratings already help consumers choose many products, from movies to cars to computers. Such labels are provided by the producers or by independent third parties, such as consumer magazines. Similarly, labels for Internet resources could help users to select interesting, high-quality materials and could help supervisors to block access to inappropriate ones. Second, access to Internet resources is mediated by computers that can process far more labels than any person could. Thus, parents, teachers, and other supervisors need only configure software to selectively block access to resources based on the rating labels; they need not personally read them. The basic idea is to interpose selection software between the recipient and the on-line resources. Several selection software products were either under development or already on the market when work began on PICS, including SurfWatch, CyberPatrol, NewView, and Parental Guidance. Each product included labels indicating whether certain Internet sites were acceptable as well as software that blocked access to unacceptable sites. But none of them could process the labels provided by a competing product. It was clear to the on-line services and many of the filtering software vendors that some technical conventions would be needed to allow innovations in labeling systems and services to proceed independent of innovations in software that makes use of labels. PICS separates the selection software from the rating labels: any PICS-compliant selection software can read any PICS-compliant labels. In fact, a single site or document may have many labels, provided by different organizations. Consumers choose their selection software and label sources. Labels may come from many sources. Information publishers may self-label, just as manufacturers of children’s toys currently label products with text such as, “Fun for ages 5 and up.” Much as independent consumer magazines rate products, third-party ratings of information resources can also be useful. For example, the Wiesenthal Center, which is concerned about Nazi propaganda and other hate speech available on-line, could label materials that are historically inaccurate or promote hate. A teacher might label a set of NASA photographs and block access to everything else for the duration of an astronomy lesson. A service like Yahoo might rate everything, or at least the most popular resources. With multiple perspectives to choose from, parents and other supervisors can choose labeling sources that reflect their goals and values, and ignore all other labels. PICS also allows labels to use non-binary rating scales. Rather than being limited to permitted/prohibited labels, services can invent more complex scales. For example, Yahoo labels might include a “coolness” value and a subject category. Non-binary labels enable more flexible blocking rules. For example, if a rating service used the MPAA’s movie-rating scale, an eight-year-old might be permitted access only to G-rated sites while a fifteen-year-old might be permitted access to PG-rated sites as well. PICS provides a labeling infrastructure for the Internet. It is value-neutral-it can accommodate any set of labeling dimensions, and any criteria for assigning labels. Any PICS-compatible software can interpret labels from any source, because each source provides a machine-readable description of its labeling dimensions. A new labeling service can distribute labels directly to clients over the network, or arrange with information providers or on-line services to redistribute the labels. This system permits the implementation of context-specific rules rather than blanket rules. Around the world, governments are considering restrictions on on-line content. Since children differ, contexts of use differ, and parents’ values differ, such blanket restrictions can never meet everyone’s needs. PICS will enable labeling services and software to meet supervisors’ diverse needs, and the labels will also help users surf the Internet more efficiently.
_
Medical information on internet;
The principal dilemma of the internet is that, while its anarchic nature is desirable for fostering open debate without censorship, this raises questions about the quality of information available, which could inhibit its usefulness. While the internet allows “medical minority interest groups to access information of critical interest to them so that morbidity in these rare conditions can be lessened, it also gives quacks such as the “cancer healer” Ryke Geerd Hamer a platform. I have seen many CAM practitioners boasting cure from asthma to cancer on internet. The quality of medical information is particularly important because misinformation could be a matter of life or death. Thus, studies investigating the “quality of medical information” on the various internet venues—websites,mailing lists and newsgroups, and in email communication between patients and doctors—are mostly driven by the concern of possible endangerment for patients by low quality medical information. Thus, quality control measures should aim for the Hippocratic injunction “first, do no harm.” Labeling and filtering technologies such as PICS (platform for internet content selection) could supply professionals and consumers with labels to help them separate valuable health information from dubious information. Doctors, medical societies, and associations could critically appraise internet information and act as decentralized “label services” to rate the value and trustworthiness of information by putting electronic evaluative and descriptive “tags” on it.
_
What could be government policy and/or laws regarding Internet censorship in various countries around the world?
As in 2002, Government policies concerning censorship of the Internet may be broadly grouped into four categories:
1) Government policy to encourage Internet industry self-regulation and end-user voluntary use of filtering/blocking technologies:-
This approach is taken in the United Kingdom, Canada, and a considerable number of Western European countries. It also appears to be the current approach in New Zealand where applicability of offline classification/censorship laws to content on the Internet seems less than clear. In these countries laws of general application apply to illegal Internet content such as child pornography and incitement to racial hatred. Content “unsuitable for minors” is not illegal to make available on the Internet, nor must access to same be controlled by a restricted access system. Some (perhaps all) such governments encourage the voluntary use of, and ongoing development of, technologies that enable Internet users to control their own, and their children’s, access to content on the Internet.
2) Criminal law penalties (fines or jail terms) applicable to content providers who make content “unsuitable for minors” available online:-
This approach is taken in some Australian State jurisdictions and has been attempted in the USA (although no such US Federal law is presently enforceable, and to the best of EFA’s knowledge nor is any such US State law). In these countries, in addition, laws of general application apply to content that is illegal for reasons other than its unsuitability for children, such as child pornography.
3) Government mandated blocking of access to content deemed unsuitable for adults:-
This approach is taken in Australian Commonwealth law (although it has not been enforced in this manner to date) and also in, for example, China, Saudi Arabia, Singapore, the United Arab Emirates and Vietnam. Some countries require Internet access providers to block material while others only allow restricted access to the Internet through a government controlled access point.
4) Government prohibition of public access to the Internet:-
A number of countries either prohibit general public access to the Internet, or require Internet users to be registered/licensed by a government authority before permitting them restricted access as in (3) above. Information on countries in this category is available in the Reporters Without Borders report as Enemies of the Internet.
_
Arrest of Bloggers:
Control is not limited to filtering or censorship. Recent years have seen an increase in a wide variety of threats to freedom on the Internet, such as an increase in arrests of bloggers and Internet users. The Committee to Protect Journalists found that in 2008, there were, for the first time, more jailed ‘cyber-dissidents’, such as bloggers, than traditional media journalists. The arrest or detention of content producers, such as bloggers, or users, such as those who are accessing or consuming unlawful or otherwise targeted material, is one of the most traditional forms of content control. In doing so, surveillance and monitoring methods are often used to identify users or producers.
_
Digital rights:
Imposing indirect liability on private companies or threatening them with other legal issues has generated fears that industry self-regulation, driven by government policy, will lead to over-zealous censorship online and therefore will decrease or limit access to copyrighted material. In any case, a narrow governmental focus on law or direct regulation cannot deliver a comprehensive picture of the extent of limitations imposed on freedom of expression online. Table below illustrates the variety of goals and objectives which underlie explicit or implicit policies of content control within a larger ecology of evolving ‘digital rights’.
_
_
Net Neutrality:
Net neutrality is one of the more technical aspects of Internet regulation that has been viewed as a potential threat to freedom of expression online. There is no single definition for net neutrality but it usually means that ISPs do not discriminate against users through access fees, nor do they favor one type of content or content provider over another, or charge content providers for sending information to consumers over their broadband cables. In a nutshell, net neutrality refers to a level playing ground where Internet service providers (ISPs) allow access to all content without favoring any particular company or Web site. As digital media evolves with the creation of new technology, the need for bandwidth has made the net neutrality debate more prominent. It is attractive to many as a possible solution to managing existing bandwidth more efficiently as demands begin to exceed supply, rather than simply expanding available bandwidth. Without net neutrality, ISPs can charge content providers a fee for bandwidth usage. Content providers that pay the fee will get more broadband access, meaning their Web sites will load faster than competitors who didn’t pay the fee. For example, if Yahoo pays a fee to an ISP and Google didn’t, the ISP’s customers would discover that Yahoo’s search engine loads much faster than Google’s. Supporters of net neutrality argue that such preferential treatment amounts to censorship.
__
Intellectual property rights and copyright violations:
It’s wrong to steal a 30 cent pack of gum and it’s a felony to steal a 30 thousand dollar car but if a 30 million dollar movie is pirated and put up on the internet, people don’t blink an eye. Illegal downloading of music and films is on the rise. In many ways it has become socially acceptable to watch pirated material online. The issue of piracy is a significant problem for the entertainment industry. Millions of people have illegal access to movies and TV shows and these needs to be addressed. Something ought to be done to crackdown on sites that promote illegal streaming and downloading of films and shows. Rogue sites illegally upload content such as movies to sites which often look “authentic” because they do a really good job of pretending to be legal. Consumers watch films for free and in some cases even pay for the service with their credit cards.
_
A study examined approximately 100 rogue sites and found that these sites attracted more than 53 billion visits per year which average out to approximately nine visits for every man, woman, and child on Earth. Global sales of counterfeit goods via the Internet from illegitimate retailers reached $135 billion in 2010. No country can tolerate such criminal activity. Not only are jobs and consumers at risk, but rogue sites contribute absolutely nothing to the economy of a country from which they pirated out goods & services. The operators of rogue sites break laws, do not pay taxes, and skirt accountability.
_
Stop online piracy act (SOPA) and Internet:
SOPA is a legislation that would prevent Americans from visiting websites the government claims are violating copyright rules. Proponents of SOPA say that not only are online piracy and counterfeiting drains on their economy, they expose consumers to fraud, identity theft, confusion and to harm. It allows the Justice Department to obtain court orders demanding that American ISPs prevent users from visiting blacklisted websites. ISPs receiving such orders would have to alter records in the net’s system for looking up website names, known as DNS. It also allows the Justice Department to order search sites like Google to remove an allegedly “rogue” site from its search results. Both proposals amount to the holy grail of intellectual-property enforcement that the recording industry, movie studios and their union and guild workforces have been clamoring. SOPA is ostensibly designed to squelch pirate content sites by allowing the US Attorney General to get a court order forcing ISPs to block access, and by denying sites financial services like credit card or Paypal access. The Stop Online Piracy Act specifically targets foreign websites primarily dedicated to illegal activity or foreign websites that market themselves as such. The bill targets online criminals who profit from stolen American content and counterfeit goods and are a danger to American consumers. Under current practice, copyright owners such as TV networks and Hollywood studios reach out to websites to request that pirated videos be taken down. Under the new regime, they could ask banks, Internet service providers and domain name registrars to stop doing business with websites that they believed were devoted to piracy. They could, for instance, go straight to YouTube’s domain registration company and demand that the entire YouTube website be taken down. And if the registrar resisted, the copyright owners would have the legal ability to take the registrar to court.
_
“We support the bill’s stated goals,” says an open letter signed by nine Internet companies, including Google, Facebook, Twitter, Yahoo, AOL and eBay. “Unfortunately, the bills as drafted would expose law-abiding U.S. Internet and technology companies to new uncertain liabilities.” The companies believe the government should “consider more targeted ways to combat foreign ‘rogue’ websites dedicated to copyright infringement and trademark counterfeiting.” Requiring Internet-service providers and search engines to remove links to websites accused of trafficking in counterfeit movies and music would amount to “ Internet censorship” and set a bad example for other countries.
_
Are proponents of SOPA pirates themselves?
Major entertainment entities including NBCUniversal, CBS, Disney, Fox, Sony Pictures, Viacom and Warner Brothers are all lobbying for greater monitoring and punishment of what they term “content theft.” After all, they make the shows, and pirates (the consumers who download copyrighted content free of charge on the Internet) lift them without so much as watching an ad. These studios recently formed a coalition to support the Stop Online Piracy Act (SOPA), a proposed bill in American Congress that could lead to new levels of web censorship. However, according to data gathered by TorrentFreak via spy site YouHaveDownloaded, employees at Sony, Fox and Universal are a bunch of torrent-happy fiends just like the pirates. TorrentFreak used IP ranges for a handful of major Hollywood studios, entered that information into YouHaveDownloaded and saw a stream of TV shows, music and movies being downloaded by employees. At Sony, folks were downloading Conan the Barbarian and music by the Black Keys. Over at NBC’s Fort Lauderdale office, someone was pirating Cowboys and Aliens and new sitcom Two Broke Girls. And at Fox, downloads included the newly-released-on-DVD film Super 8. These are the same companies who want to disconnect people from the Internet after they’ve been caught sharing copyrighted material. So is there a double standard by proponents of SOPA?
_
SOPA is “Unconstitutional”:
Constitutional law experts at Harvard Law School, argues that SOPA violates the First Amendment of the U.S. constitution. The bill would empower the Justice Department and copyright holders to demand that search engines, Internet providers and payment processors cut ties with websites “dedicated” to copyright infringement. Experts argue that the bill amounts to illegal “prior restraint” because it would suppress speech without a judicial hearing. Additionally, the law’s definition of a rogue website is rather vague. Conceivably, an entire website containing tens of thousands of pages could be targeted if only a single page were accused of infringement. Such an approach would create severe practical problems for sites with substantial user-generated content, such as Facebook, Twitter, and YouTube, and for blogs that allow users to post videos, photos, and other materials.
_
Free speech concerns and SOPA:
Many proxy servers such as those used during the Arab Spring can also be used to thwart copyright enforcement and therefore may be made illegal by the act. Some US-funded “internet in a suitcase” projects allow users in China to circumvent the Chinese government’s control of DNS. The Chinese program is technically very similar to SOPA provisions. Communication problems during Hurricane Katrina, the Fukushima earthquake and the Arab Spring have led to proposals of technology changes to enable ad-hoc emergency networks. Whistleblowers already risk punitive copyright lawsuits, no less ruinous because they are eventually decided in favor of the whistleblowers. A bill that was to target only the ‘worst of the worst’ foreign Web sites committing blatant and systemic copyright and trademark infringement has morphed inexplicably into an unrestricted hunting license for media companies to harass anyone foreign or domestic—who questions their timetable for digital transformation.
_
Firefox add-on DeSopa circumvents internet blacklisting if SOPA becomes law:
DeSopa is a simple Firefox extension that allows internet users to revert to using a site’s IP (internet protocol) address, thereby bypassing DNS blockades of foreign websites such as The Pirate Bay. At the Firefox DeSopa download page, the add-on is described as such, “DNS Evasion to Stop Oppressive Policy in America.”
_
Technical problems with SOPA:
Internet security experts are concerned over ordering American internet service providers to stop giving out the correct DNS entry for an infringing website under the .com, .org and .net domains. Putting false information into the DNS system — the equivalent of the net’s phonebook — would be ineffective, frustrate security initiatives and lead to software workarounds. These actions would threaten the Domain Name System’s ability to provide universal naming, a primary source of the internet’s value as a single, unified, global communications network. In other words, the bill would break the internet’s universal character and hamper U.S. government-supported efforts to rollout out DNS-SEC, which is intended to prevent hackers from hijacking the net through fake DNS entries.
_
My view on SOPA and all such legislations:
I sincerely believe in preservation of intellectual property rights and copy rights. I condemn piracy of movies, videos and music. However, SOPA is not the best way to do it. Technically it will harm Internet’s universal character and may frustrate internet functioning during disasters like earthquakes & hurricanes when lifeline services and telecommunication structure is disrupted. Also, technical circumvention of SOPA is possible and feasible. Legally, it can be misused easily against any whistleblower, anybody who is critical of government and any dissident. The law can also be misused by competitors to blackmail genuine websites who are profiting from bona fide services. No government or investigative agency or company should have right to censor any website unilaterally. That decision must be taken by competent court after hearing both parties.
_
ISP treatment:
When the author or publisher of books cannot be traced or are insolvent, the printers can be sued or prosecuted in some circumstances and therefore some say that internet service providers (ISPs) should be made liable if they assist in the provision of dangerous and harmful information such as bomb making instructions, hard core pornography etc. I disagree. Internet Service Providers (ISPs) should be treated as carriers of data and not publishers of the data. ISPs are similar to telephone companies in that they allow the transport of data. Telephone companies are considered carriers and not publishers because they are not expected too, and furthermore, not allowed to regulate the content of private communications between individuals. ISPs should be treated in the same ways. Microsoft CEO and computer industry expert Bill Gates in his book on the future of the Internet, The Road Ahead, asserts that the idea of having Internet Service Providers act as censors would be absurd. Some critics have suggested that communications companies be made gatekeepers, charged with filtering the content of what they carry. This idea would put companies in the business of censoring all communication. It’s entirely unworkable, for one thing because the volume of communicated information is way too large. This idea is no more feasible or desirable than asking a telephone company to monitor and accept legal responsibility for everything that’s spoken or transmitted on its telephone wires. Indeed, it would be absurd to ask a telephone company to be legally responsible for their client’s content, just as it is absurd to ask an ISP to be legally liable for their client’s content.
_
A study of ISP:
A different approach to surveying the state of Internet censorship was taken by Westphal and Towell of Northern Illinois University, who queried companies that provide Internet services around the world about pressures to regulate and the source of the pressure. While the response rate to this survey was very low, 86 providers from 38 countries participated. A majority of 56% said that the pressure to regulate came from the government. However, about the same percent claimed that they, as providers, had the most control over the material transmitted, and that parents/users controlled 51%. Terrorism, pornography, and racism were the primary targets of regulation reported, but there were also countries that stated that astrology, religion, birth control, and politics needed to be regulated. The study concluded that the majority of the Internet providers indicated that the Internet needs regulating, but the degree of regulation is still unclear. Knowing that the Internet is a global network and countries all over the world operate under their own sets of laws, regulating the Internet on an international level may be impossible… If Internet participants cannot agree on who has control and what should be censored, then the reasons for discrepancies in all the other basic issues surrounding this topic become obvious. What is legal and acceptable in one country may be illegal or unacceptable in another.
_
The sliding scale toward “self-regulatory” censorship:
A new report suggests that nations are slowly turning ISPs into the off-duty information cops of the world. Eager to placate politicians in order to achieve their own goals (like the selective throttling of data), networks are cooperating with governments looking for easy, informal solutions to difficult problems like copyright infringement, dangerous speech, online vice, and child pornography. Network and content providers are ostensibly engaging in “self-regulation,” but that’s a deceptive phrase, warns the European Digital Rights group. It is not regulation—it is policing—and it is not ‘self’ because it is their consumers and not themselves that are being policed.
_
Big Businesses and Internet Censorship:
Corporations that restrict employee Internet access usually do so for a few reasons. One of the most common reasons is to increase productivity. While employees can use the Internet for research or communication, they may also use it as a distraction. Some companies restrict Internet access severely in order to prevent employees from wasting time online. Another corporate concern is harassment. Without restrictions, an employee could surf the Web for inappropriate content, such as pornography. If other employees see this material, they may feel that their work environment is a hostile one. Some companies resort to using Internet censorship in order to avoid lawsuits. While several companies use Web filtering software similar to the products available for home use, many also rely on firewalls. With a firewall, a company can pick and choose which Web pages or even entire domains to block. This way, the company is more likely to avoid blocking sites that employees may need to access legitimately.
_
Internet and democracy:
The Internet is a potential force for democracy by increasing means of citizen participation in the regimes in which they live. The Internet is increasingly a way to let sunlight fall upon the actions of those in power—and providing an effective disinfectant in the process. The Internet can give a megaphone to activists and to dissidents who can make their case to the public, either on the record or anonymously or pseudonymously. The Internet can help make new networks, within and across cultures, can be an important productivity tool for otherwise underfunded activists, and can foster the development of new communities built around ideas. The Internet can open the information environment to voices other than the organs of the state that have traditionally had a monopoly on the broadcast of important stories and facts, which in turn gives rise to what William Fisher refers to as ‘‘semiotic democracy.’’ Put another way, the Internet can place the control of cultural goods and the making of meaning in the hands of many rather than few. The Internet is increasingly an effective counterweight to the consolidation in big media, whether the Internet is controlled by a few capitalists or the state itself. Anybody who analyzed my life will say that Internet has strengthened democracy by exposing role of traditional media working as a proxy of their respective government in so called democratic countries like America & India.
_
Internet and economy:
The Internet also can be a force for economic development, which is most likely the factor holding back some states from filtering the Internet more extensively or from imposing outright bans on related technologies. The Internet is widely recognized as a tool that is helping to lead to the development of technologically sophisticated, empowered middle classes. Entrepreneurship in the information technology sector can lead to innovation, the growth of new firms, and more jobs. Internet without censorship leads to open information environment which can lead to a beneficial combination of greater access to information, more transparency, better governance, and faster economic growth. The Internet, in this sense, is a generative network in human terms. In the hands of the populace at large, the Internet can give rise to a more empowered, productive citizenry.
_
Hackers to launch satellites to block Internet censorship:
Hackers are rallying behind a new plan to launch satellites into space to prevent Internet censorship. It is a project that will involve setting up low-cost ground stations to track and communicate with the fast-moving satellites. However, there is a technical hitch. Low-Earth-orbit satellites, such as have been launched by amateurs so far, do not stay in a single place but rather orbit, typically every 90 minutes. That’s not to say they can’t be used for communications, but obviously only for the relatively brief periods that they are in your view. It’s difficult to see how such satellites could be used as a viable communications grid other than in bursts. Also, outer space is not governed by the countries beneath it, so any country could take the law into their own hands and disable the satellites.
_
U.S. bill targets exports of Web Censorship Tools:
One of the most popular filtering software programs is SmartFilter, owned by Secure Computing in California, a company that’s just been bought by McAffee for $465m (£311m). SmartFilter has been used by some of the world’s most authoritarian regimes: Tunisia, Saudi Arabia and Sudan. The list of sites that are blocked by the software is so secret that not even the countries that use the technology know what is actually being censored. It’s unconscionable that U.S. technology is putting democracy activists at risk. U.S. companies should not, knowingly or unwittingly, be providing the technology used by repressive regimes to hunt down and punish human rights activists. There is a criminal cooperation between Western hi-tech companies and authoritarian regimes. Every day we learn of more democratic activists being arrested through the use of a growing array of Internet censorship and surveillance tools, abused by the governments of China, Belarus, Egypt, Syria and many other countries. The surveillance tools sold by these companies are used all over the world by armed forces, intelligence agencies, democratic governments and repressive regimes. The leading exporters of these technologies include the United States, France, Germany, Italy, United Kingdom and Israel. The bill Global Online Freedom Act will stop the vicious merry-go-round of exporting Internet-restricting technologies from the U.S. and then the U.S. has to spend millions of dollars helping activists circumvent. The legislation would prohibit American companies from exporting hardware or software that could be used for online surveillance or censorship to nations that restrict the Internet. It would also require Internet companies listed on U.S. stock exchanges to disclose to American regulators their practices in collecting and sharing personally identifiable information and steps taken to notify users when removing content.
__
EU to Give Secret Anti-Censorship Software to Human Rights Activists:
Arab Spring had been the wake-up call to governments around the world to recognize the power of the Internet, and social networking in particular, in building freedom and democracy. When peaceful protests are being planned, connectivity is everything. Communications networks must stay switched on. Enabling citizens of authoritarian countries to bypass surveillance and censorship measures depends on two basic conditions: availability of appropriate technologies (in particular software programs that can be installed on one’s desktop computer, laptop, smart-phone or other device) and awareness, both of the techniques used by authoritarian regimes to spy on citizens and censor their communications, and of the appropriate counter-measures to use. The so-called Internet survival packs would include currently available technology as well as potential new software aimed specifically at allowing activists to use the Internet to get their message across while at the same time remaining safe from persecution. EU has recently announced the “No Disconnect Strategy” to provide support to Internet users, bloggers and cyberactivists living in countries with poor track records on human rights.
_
Internet and earthquake:
One of the attributes that makes the Internet so popular is the ability to withstand partial outages and still function as a medium for transferring video, audio and text simultaneously. Kobe, Japan, experienced an enormous earthquake on 17 January 1995, named the Hanshin-Awaji Earthquake. At that time, “lifeline” public services such as gas, electricity, and water service stopped. Many people outside of the afflicted area were anxious to know if their family and friends were safe, and so many telephone calls were made to the afflicted area that the local telephone system was paralyzed. From this experience, we learned that the Internet stayed alive because of its robustness even in disasters. It became clear that the information system on the Internet should be prepared for burst access. A major earthquake caught people off guard in Turkey, Izmit, on August 17, 1999, at 03:02AM while they were asleep. A second occurred on November 12, 1999, at 18:58PM in Duzce. Thousands died and thousands more were wounded. People lost their lives, homes, livelihoods and dreams. In the wake of this earthquake, many national and international communities offered help and assistance. However, it rapidly became apparent that one of the main obstacles to efficiency in conducting the rescue operation was the lack of coordination in the earthquake region. A significant contributing factor was the disruption to the telecommunications infrastructure. All the phone lines were overloaded; even the mobile phones were not working. It soon became apparent that the only reliable working telecommunication medium was the Internet. As a consequence, it became the medium of choice for informing volunteers and nongovernmental organizations (NGOs), both nationally and internationally, about the needs of the earthquake region.
_
Discussion on internet censorship:
Is Internet censorship right? That is the question millions of people around the world are asking themselves— people like you and me who freely surf the Web every day reading the latest news or simply checking our e-mail. This freedom that we exercise daily is in danger of becoming another government-regulated part of our lives. The Internet, a technological masterpiece, has become subject of great controversy. Certain individuals feel as though the Internet should be governmentally regulated and censored in order to protect the youth of the world. On the other hand, the regulation of material on the Internet would, in fact, violate the fundamental human right to free speech and expression. Thomas Emerson once stated “Those who seek to impose limitation on expression do so ordinarily in order to forestall some anticipated effect of expression in causing or influencing other conduct”.
_
Let me first present what American Supreme Court and the UN stated on this issue:
On June 26, 1997, the United States Supreme Court held that communications over the Internet deserve the highest level of constitutional protection and the Court’s most fundamental holding is that communications on the Internet deserve the same level of constitutional protection as books, magazines, newspapers, and speakers on a street corner soapbox. The Court found that the Internet “constitutes a vast platform from which to address and hear from a world-wide audience of millions of readers, viewers, researchers, and buyers,” and that “any person with internet access can become a town crier with a voice that resonates farther than it could from any soapbox”.
_
UN and Internet:
On 10 December 1948, the adoption by the United Nations General Assembly of the Universal Declaration of Human Rights launched a new era. One of the fundamental rights the Universal Declaration described, in Article 19, was the right to freedom of speech: “Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive, and impart information and ideas through any media and regardless of frontiers”. When those words were written sixty three years ago, no one imagined how the global phenomenon of the Internet would expand people’s ability to “seek, receive and impart information”, not only across borders but at amazing speeds and in forms that can be copied, edited, manipulated, recombined and shared with small or large audiences in ways fundamentally different than the communications media available in 1948. The unbelievable growth in the past several years of what is on the Internet and where it is available has the effect of making an unimaginably vast portion of human knowledge and activities. But the Internet does not contain only relevant and helpful educational information, friendship and communication. Like the world itself, it is vast, complex and often scary. It is just as available to people who are malicious, greedy, unscrupulous, dishonest or merely rude. With all of the best and worst of human nature reflected on the Internet and certain kinds of deception and harassment made much easier by the technology, it should not surprise anyone that the growth of the Internet has been paralleled by attempts to control how people use it. For example, we use spam-filtering tools to prevent spam from being delivered to our own e-mail accounts. However, when our access to internet is blocked or filtered by other people’s concerns, and when we don’t agree that the blocking is appropriate or in our interest; it cause significant conflicts and disagreements.
_
UN report on freedom of expression vis-à-vis Internet:
The United Nations Special Reporter on the promotion and protection of the right to freedom of opinion and expression submitted his report to the seventeenth session of the Human Rights Council on 16 May 2011. This report explores key trends and challenges to the right of all individuals to seek, receive and impart information and ideas of all kinds through the Internet. The Special Reporter underscores the unique and transformative nature of the Internet not only to enable individuals to exercise their right to freedom of opinion and expression, but also a range of other human rights, and to promote the progress of society as a whole. It outlines some of the ways in which States are increasingly censoring information online, namely through: arbitrary blocking or filtering of content; criminalization of legitimate expression; imposition of intermediary liability; disconnecting users from Internet access, including on the basis of intellectual property rights law; cyber attacks; and inadequate protection of the right to privacy and data protection. The UN Special Reporter is cognizant of the fact that, like all technological inventions, the Internet can be misused to cause harm to others. As with offline content, when a restriction is imposed as an exceptional measure on online content, it must pass a three-part, cumulative test:
(1) It must be provided by law, which is clear and accessible to everyone (principles of predictability and transparency);
(2) it must pursue one of the purposes set out in article 19, paragraph 3, of the International Covenant on Civil and Political Rights , namely: (a) to protect the rights or reputations of others; (b) to protect national security or public order, or public health or morals (principle of legitimacy); and
(3) It must be proven as necessary and the least restrictive means required to achieve the purported aim (principles of necessity and proportionality).
In addition, any legislation restricting the right to freedom of expression must be applied by a body which is independent of any political, commercial, or other unwarranted influences in a manner that is neither arbitrary nor discriminatory. There should also be adequate safeguards against abuse, including the possibility of challenge and remedy against its abusive application.
The UN Special Reporter in his report to the Human Rights Council reiterates the call to all States to decriminalize defamation. Additionally, he underscores that protection of national security or countering terrorism cannot be used to justify restricting the right to expression unless it can be demonstrated that: (a) the expression is intended to incite imminent violence; (b) it is likely to incite such violence; and (c) there is a direct and immediate connection between the expression and the likelihood or occurrence of such violence.
_
UN and Internet censorship:
Amidst raging controversy over the government of India’s proposal to monitor content in cyber space, UN Secretary General Ban Ki Moon said access to the Internet and various social media must not be blocked as a way to prevent criticism and public debate. In his speech on the eve of the Human Rights Day which was released at the United Nations Information Centre here, Moon said, “Today, within their existing obligation to respect the rights of freedom of assemble and expression, governments must not block access to the internet and various forms of social media as a way to prevent criticism and public debate.” Emphasizing on the important role that the social networking sites played in global events, Moon said, “Many of the people seeking their legitimate aspirations were linked through social media.”
_
Freedom of speech is a right of the citizens of the world; on the other hand, this freedom is not absolute to the point that society thinks that it is. One person’s right to freedom of expression should not infringe upon rights of others. Some forms of speech are thoroughly outlawed in many democratic nations such as fraudulent advertising, child pornography, obscenity, fighting words, help-wanted ads that discriminate on the basis of race, words used in a criminal transaction, unlicensed broadcasts, libel, speech that infringes a copyright, and unauthorized disclosure of data used to make atomic weapons. Naturally, most of these forms of speech have a compelling government interest. Government may regulate, or censor speech if it has a compelling interest, is a public concern, or threatens national safety. In turn, this demonstrates that the ideas and expressions of private institutions cannot be regulated, unless one of the preceding requirements is met. William Turner writes that “Government may not restrict or penalize speech because of its content or its viewpoint. It must remain neutral in the marketplace of ideas”. Overall, government may not regulate speech, unless there is a major national or public concern.
_
Despite the generally prevailing principle of freedom of speech in democratic countries, it is widely accepted that certain types of speech are not given protection as they are deemed to be of insufficient value compared to the harm, they cause. Child pornography in the print or broadcast media for instance is never tolerated. The internet should be no exception to these basic standards. Truly offensive material such as hardcore pornography and extreme racial hatred are no different simply because they are published on the World Wide Web as opposed to a book or video. Censorship is tailored to the power of the medium. Accordingly there is a higher level of censorship attached to television, films and video than to newspapers and books. This is because we recognize that moving pictures and sound are more graphic and powerful then text and photographs or illustrations. There is also normally more regulation of videos then cinema films because the viewer of a video is a captive audience with the power to rewind, view again and distribute more widely. The internet, which increasingly uses video and sound should be attached the same level of power and regulated accordingly. Also, more relevant difficulty is the anonymity provided by the internet which gives pornographers and criminals the opportunity to abuse the medium. Asian countries have experimented with requiring citizens to provide identification before posting content on to the internet; such a system if universally adopted could be a relatively simple way of enforcing laws against truly offensive and harmful content. The issues at stake in this debate are protection of children, terrorist activity, crime, racial hatred etc. all of which are international problems. If a global solution is required then it can be achieved by international co-operation and treaties. It is acknowledged that it is justifiable to censor where harm is caused to others by the speech, words or art of an author, all the examples cited above are clearly causing harm to various groups in society.
__
Internet should be free, but not lawless:
Liberty, the ability to maximize one’s talents free from interference with respect for the rights of others, is not the same as lawlessness, the state in which the Internet property pirates find themselves. It is the function, indeed the obligation, of government to put an end to lawlessness, provided that it shows a decent respect for due process and the other constitutional protections we are all afforded. Protecting copyrights is in fact a property rights issue. We must distinguish between protected free speech and the outright theft of another’s property. They are not the same thing. It’s the difference between liberty and lawlessness. I am in favor of the former and opposed to the latter.
_
There is a common perception that the Internet is a ‘Wild West’ or lawless and unregulated territory. This ignores the fact that laws in the offline world also apply to the online world. In fact, user behavior is very much a focus of law and regulation in every nation. However there are many reasons why criminal behavior is (in practice) less well regulated online. Firstly, many of the simpler regulatory solutions that apply offline (zoning, age restrictions or proof of identity requirements) are harder to implement online. In addition, there is the problem of managing and deploying law enforcement resources online and also the complexity of reconciling cross-national differences in laws and sanctions. Harvard law professor Jonathan Zittrain (2003) argues that jurisdiction built upon the movement of information traveling across the Internet has proven too costly for governments. However, the extent to which offline laws and regulations targeting user behavior are also applied in the online world can be illustrated by the examples given in Table below.
_
__
Fear as basis of censorship:
Overall, one can say that the instinct to censor is quite universal, and that the stated aim is protection — of children, of cultural values, of government stability, and so on. The objective is to maintain control. But why is there this need to be protective, to be in control? Perhaps underlying this instinct is the more basic one of fear. It’s that the theocratic right is driven by an irrational fear — a fear that the citizens can’t be trusted to do the right thing if they’re presented with unvarnished, unmanufactured facts. Across the world, similar fears seem to drive the censors, suggesting a mistrust of free speech and people’s ability to deal with it rationally, and perhaps an unacknowledged lack of confidence on the part of the censor in their own infallibility.
__
Intellectual freedom vis-à-vis Internet:
As a society we want our young people to be literate, thoughtful, and caring human beings; but we also attempt to control what they read, think, and care about. We feel the need to “protect” children from dangerous or disturbing ideas and information. Of course, what is dangerous or disturbing to one person or segment of society may be exciting and innovative to others and perhaps just “the truth” to still others. This combination of multiplicity of values and concern for young people keeps censorship alive in school and public libraries. Current concerns for literacy and critical thinking in education may actually increase incidents of censorship. Literacy assumes the power of texts and encourages exposure to competing ideas and beliefs. Critical thinking implies questioning, the analysis and evaluation of those beliefs to come to a personal judgment that empowers young people to take ownership of ideas and control of their own intellectual and moral lives. New technologies are causing an increase in incidents of censorship. The history of communications technologies, from the written word to modern electronic media, has been written with fear as critics contemplate the most dire consequences of each move that takes us farther from the personal one-on-one interaction with another human being in real time and space. The internet and the World Wide Web are especially problematic. In the virtual world of these media, there is a potential for a kind of anonymous intimacy that can be very seductive in our often fragmented, disconnected lives. Young people, often very comfortable with and eager to explore these new media at the same time they are coping with the myriad problems of coming-of-age in our society, may be especially susceptible to such seduction. Like most things, this can be either good or bad. I am encouraged and impressed by students who have exhausted traditional school and library resources, who now discover new and more current material on the internet and the web. At times they even participate in dialogues that move knowledge to new dimensions. I am even more impressed to see previously unmotivated students, seduced by information and ideas, discovering the power of their own intellects through electronic exchange. For me, the question becomes: Are we willing to give up this potential (if we could) to “protect” young people from “dangerous” encounters? As concerned adults, we need to understand conflicts of intellectual freedom, not as something negative or practiced by those less enlightened than ourselves, but as a process in which we are all participants playing various roles based on age, family background, societal position, religious beliefs, and profession. Professional teachers who serve youth in school have a pivotal part to play in this ongoing intellectual and moral drama. In order to best serve young people, we need consciously to consider both the basic underpinnings of intellectual freedom in our society and the requirements of the professional roles we play. I invite others to read, question, think, criticize, and share their own interpretations to help keep this drama alive. Without this ongoing dialogue and challenge to ideas and beliefs, there is no intellectual freedom.
__
Censorship of the Internet, as evidenced by national filtering of online content, appears to be more widely acceptable, even within states with liberal democratic traditions. Concerns over issues such as child protection, online decency and fraud have been deemed significant enough to justify restrictions on freedom of expression. This is not to say that such considerations are not important to address in the digital age; the eradication of child abuse images online, for example, is almost universally accepted as a vital goal. Yet research indicates that disproportionate reliance on disconnecting users or filtering content could seriously undermine essential aspects of freedom of expression without resolving the policy problem at hand, unless the larger ecology of policies and regulations is taken into account in balancing conflicting objectives. Protecting certain human rights or freedoms often has a direct and immediate impact on other rights and freedoms. Thus, the preservation of one freedom can limit another. Balancing these conflicting values and interests is only likely to be a resolved through negotiation and legal-regulatory analyses. This will probably vary cross-nationally, if not locally. Resolution of these balancing issues requires a broad view of the larger ecology of policies and regulations shaping freedom of expression as seen in the figure below.
_
_
The benefits of open, free expression and freedom of connection are immense. There are many ways to mitigate the risks of an open society, and filtering or censorship is rarely the most effective of these. Should the Internet be regulated as if it were a newspaper, broadcaster or a common carrier network? Or should it follow a new regulatory framework, which could well be the most sensible way forward. Some have viewed content on the Internet as impossible or inappropriate to regulate; a position well developed and most influenced by Ithiel de Sola Pool (1983) in his discussion on videotext. Impossible, because control over content production and consumption on the Internet was thought to be inherently distributed and incapable of being centrally controlled or censored. Inappropriate, because computers were thought to become newspapers of the future and should therefore enjoy the same freedom as the press.
_
Should it be illegal to publish literature with “indecent” content on the Internet but perfectly legal to publish that same work in print? This question has spawned the debate over Internet censorship. The proponents of internet censorship suggest creating laws for the Internet similar to those now in place for television and radio. Those strongly opposing Internet regulations, such as the Citizens Internet Empowerment Coalition (CIEC), assert that the Internet is not like a television and should not be regulated like one. The issues associated with Internet censorship are similar to those for offline censorship of more traditional media such as newspapers, magazines, books, music, radio, television, and films. One difference is that national borders are more permeable online: residents of a country that bans certain information can find it on websites hosted outside the country. Thus censors must work to prevent access to information even though they lack physical or legal control over the websites themselves. This in turn requires the use of technical censorship methods that are unique to the Internet, such as site blocking and content filtering. Blocking and filtering can be based on relatively static blacklists or be determined dynamically based on an examination of the information being exchanged. Blacklists may be produced manually or automatically and are often not available to the public. Blocking or filtering can be done at a centralized national level, at a decentralized sub-national level, or at an institutional level, for example in libraries, universities or Internet cafes. Blocking and filtering may also vary within a country across different ISPs. Countries may filter sensitive content on an on-going basis and/or introduce temporary filtering during key time periods such as elections. In some cases the censoring authorities may block content while leading the public to believe that censorship has not been applied. This is done by causing a fake “Not Found” error message to be displayed when an attempt to access a blocked web page is made.
_
The ability to speak one’s mind has never been easier, thanks to the Internet and social media. The ability to publish has never been easier, thanks to the Internet and social media. The ability to defame has never been easier. The ability to be irresponsible in news coverage has never been easier. The ability to insult, provoke and incite has never been easier. If technology makes it frighteningly easy to publish, it’s clear that, while you have the freedom to publish and to speak, it’s a freedom that comes with conditions attached. The freedoms come with responsibility – and irresponsibility, we now learn, can be punished. Continued irresponsibility could lead to a curb on the freedoms in the form of regulation, perhaps even a slice of censorship
__
Internet censorship is the removal of material from open access by government authority. Those who endorse censorship say that it is to protect minors from access to harmful and objectionable material. This is a noble, but impractical point of view, as it raises too many unanswerable questions. Who will decide what is indecent or objectionable? How do you censor only the explicit material used as pornography versus explicit material used to educate? How can one country censor something that is global? Where does censorship stop-explicit material, political opinion, religious beliefs? Most people believe there is no way to partially censor the Internet, and are deeply disturbed by attempts to do so. Whether it is ethical or not to censor the Internet should be considered. Ethics are often a matter of social culture, what is ethical in one culture may be unethical in another. Since the Internet is global is would be nearly impossible to set one standard. People are taking the narrow view, that banning or controlling information is the only way to fight incorrect or harmful information. The best way to fight misinformation is with correct information. Non-factual truth is subjective and matter of personal perspective. Only by effectively debating your argument with contentious and logical discourse, can you persuade your audience to share your point of view. Censorship denies the people their right to decide for themselves. This denial implies a lack of trust in the people to know and do what is correct and it is an attempt to control people. This same lack of trust and desire to control people has existed for as long as humanity. “Knowledge is Power”, a common and ever more truthful phrase. Those in power have always tried to control knowledge in order to control people. With the Internet that is no longer a possibility. China is a classical example of regime trying to control people by controlling internet. Freedom of speech and expression in any form, has taken on a whole new meaning because of the Internet and other new technologies. Those who value freedom must act to protect this freedom of knowledge or it could be impaired or lost.
_
There is a more efficient way to control obscene material on the Internet. Through the use of special programs designed to filter obscene Internet material, parents can allow their children to enjoy the Internet without the risk of viewing inappropriate images or ideas. Parental regulation is the only way to allow unregulated Internet use and the expansion of knowledge. Our world is not perfect. We are a world filled with sex, drugs, racism, and violence. It would seem that those parents are just trying to protect their children from the outside world. But does it really help? These days, the average elementary school student is aware of many things that their parents would rather be oblivious to their knowledge of. A wide range of sources, from television and other forms of media, to their environment at home and school influence them. All of these things combined will help to shape their moral values and personality. In order for the youth to grow up to be productive, capable adults, we must start by teaching them to individually make responsible decisions. It is the responsibility of the parents to instilling these values early on, therefore making it that much easier to communicate with them later on in their lives. I understand that parents are trying to protect their children from the harsh realities of life, but are they really helping, or hindering?
_
The human faculties of perception, judgment, discriminative feeling, mental activities and moral preference are exercised only in making a choice and Internet censorship or for that matter any censorship takes away that choice. Censorship deprives us from the opportunity to evaluate, learn from, and choose what we want to see, read and hear. The argument that something is harmful to minors ignores so many other issues;
1) How such censorship of the Internet would also deprives adults of the same material and have the effect of making all Internet content only suitable for children,
2) How “minors” covers a broad range of intellectual abilities, from ages 0 to 18 or 21,
3) That all children do not develop the same way at the same age,
4) That these arguments ignore cultural differences,
5) That we set a bad example of how to deal with controversial issues,
6) And most particularly, it ignores the context within which the censored material is delivered.
_
The context within which all the “objectionable” material being censored exists is clearly important. Studies are reported where teaching critical viewing skills and media literacy eliminate the supposedly negative effects. Yet we reject teaching such skills, and allow ideas to be suppressed. Does this prepare young people for life in the real world, or does it stifle their ability to make intelligent choices? To quote Heins: “The ponderous, humorless overliteralism of so much censorship directed at youth not only takes the fun, ambiguity, cathartic function, and irony out of the world of imagination and creativity; it reduces the difficult, complicated, joyous, and sometimes tortured experience of growing up to a sanitized combination of adult moralizing and intellectual closed doors.” Intellectual protectionism frustrates rather than enhances young people’s mental agility and capacity to deal with the world. It inhibits straightforward discussion about sex. Indeed, like TV violence, censorship may also have “modeling effects,” teaching authoritarianism, intolerance for unpopular opinions, erotophobia, and sexual guilt. Censorship is an avoidance technique that addresses adult anxieties and satisfies symbolic concerns, but ultimately does nothing to resolve social problems or affirmatively help adolescents and children cope with their environments and impulses or navigate the dense and insistent media barrage that surrounds them.
__
Censorship is generally an evil and should be avoided where ever possible. Except child pornography, other forms of speech may well be truly offensive but the only way a society can deal with them is by being exposed to them and combating them. Otherwise these groups are driven underground and become martyrs. The reason why the print media is comparatively unregulated is because we recognize that this is the primary means of distributing information in society. For this reason the internet must be allowed at least the same protection as freedom of press. Even allowing for the extreme problems surrounding freedom of speech, internet censorship would be more or less impossible. Governments can attempt to regulate what is produced in their own country but it would be impossible to regulate material from abroad. What is the point in the USA removing all domestic reference to hardcore pornography when it is possible to access material from the United Kingdom or Sweden? It is also possible for citizens to produce material and store it in an overseas domain further complicating the issue. True freedom of speech requires anonymity in some cases to protect the author; the governments who have introduced ID requirements for internet use also deny many basic rights to their citizens. The internet allows citizens to criticize their government and distribute news and information without reprisal from the state and such a system clearly could not survive with ID requirements. Internet Service Providers are certainly the wrong people to decide what can and cannot be placed on the internet. There is already far too much control of this new technology by big business without also making them judge and jury of all internet content. In any case the sheer bulk of information ISPs allow to be published is such that vetting would be more or less impossible. Many ISPs have shown themselves to be responsible in immediately removing truly offensive content where they have been alerted to it. What is required is self regulation by the industry recognizing their responsibility to internet users but not imposing arbitrary and draconian restrictions upon its use.
_
Governmental censorship would primarily attempt to stop an unintentional effect of certain speech or expression on the Internet; in other words, the government would be opposing the idea of individualism in society. When controlling what people read or view, whether in a book or on a computer monitor, the government limits people’s ideas and their thought capacities. Frederick Schauer, a law professor at the College of William and Mary, stated “Freedom of speech meant not only freedom from any form of governmental control, but also freedom from private social pressures that could also inhibit thought and opinion”. As citizens of any country, individuals have the right to be free from governmental control that inhibits thoughts, ideas, and free expression. Every individual in democratic nations has the right to read or view whatever book or magazine they choose. How should this be different from viewing the same type of material on the Internet? The separation between the individual and government is central to the Free Speech Principle, and this feature is often lost when . . . we conflate social intolerance and governmental intolerance. Governmental regulation of thoughts and ideas results in less freedom, therefore condoning less wisdom; these, in turn, result in the absence of individualistic character which is necessary in a democratic society. Government believes that it knows what is best for society; however, this can also be seen as those who are in power know what is the best method to keep power. Censorship is a possible way for the powerful to terminate individualism, wisdom, and the marketplace of ideas; it not only facilitates less freedom, but also promotes governmental coercion, collectivism, and possibly totalitarianism. Preventing individuals from exploring others’ thoughts and ideas is a way to prevent the expansion of knowledge and power.
_
I support promoting the free flow of ideas by word and image. Part of this mission, therefore, is to promote freedom of expression and freedom of information as a central element in building strong democracies, contributing to good governance, promoting civic participation and the rule of law, and encouraging human development and security. I recognize that the principle of freedom of expression must apply not only to traditional media, but also to the Internet. Providing an unprecedented volume of resources for information and knowledge, the Internet opens up new opportunities for expression and participation and holds enormous potential for development. Freedom of expression vis-à-vis internet is not just a by-product of technical change; it must be protected by legal and regulatory measures that balance a variety of potentially conflicting values and interests in a complex global ecology of choices. Freedom of expression is not an inevitable outcome of technological innovation. It can be diminished or reinforced by the design of technologies, policies and practices – sometimes far removed from freedom of expression.
_
Impending fiasco:
You’re sitting at your PC and you log into your Internet access server to read your email. You’re expecting a message from a friend, who is sending you some information on breast cancer as your mother is suffering from breast cancer, but when you check your inbox, there is instead a message from the server. It says the message that was sent to you from the address of your friend has been intercepted because it contained indecent material that did not comply with FCC regulations of the Internet. You call your friend only to find that the police have come and taken him away, and he is now facing up to two years in prison and/or up to $100,000 in fines. The message sent by your friend contained the word “breast” which by current FCC standards is indecent, and thus not permitted to be transferred on the Internet. Due to this, your friend is now subject to criminal charges. Sound ridiculous, unreasonable or scary? It is all three together and further it is impending reality. This situation is very possible in the very near future. This will happen when the government censors the Internet, by any means it deems necessary in so called democratic nations. Imagine, what will happen to you if you live in non-democratic nation?
_
Why engineers oppose Internet censorship?
The internet is a result of the collaborative effort of tens of thousands of brilliant minds who understand how the underlying technologies work together. The people supporting internet censorship however, come from a non-technical background. As they try to change how these things work in order to fit with their business models, they will most certainly break something. Would you let a chiropractor “fix” the car that you drive to work every day, against the express recommendations of your mechanic and the engineers that built it? The internet is the car that many of us drive to work every day, and almost everyone who understands what goes on under the hood are opposed to internet censorship.
_
Internet censorship and science:
Turkish Government has censored Darwin & Evolution. Concerns about censorship have risen in Turkey since November 2011 when the Council of Information Technology and Communications (BTK) placed blocks on websites that contain the words “Darwin” and “Evolution.” This filtering system blocks websites about the theory of evolution, along with pornographic sites, to any Turkish computer user who has the children’s security profile activated on his or her computer. Websites that remain unprotected include those referencing the theory of creationism, Intelligent Design and anti-evolution sentiments. While Turkey is often considered one of the most secular Islamic countries, it also houses a significant population of Islamic creationism believers. It is the sentiments of this group that provided the impetus for the evolution website filtering. Denying evolution is equivalent to denying gravity, and that students sell themselves short if they believe otherwise. To me, the censorship of any scientific theory (unrelated to obscene or inappropriate content) is not only a cause for concern but it gives wrong education to students and make them live in fictitious world. Also, it destroys creativity in students. Everybody has right to adhere to his/her religious beliefs but not at a cost of genuine scientific education. Religion is a personal matter while education is enlightenment of an individual. Religious believers & followers who assert that religion is above science must stop using benefits of science including using computer/internet, cars, air-conditioners, TV etc.
_
Who is bad, Internet or you?
What exactly is censorship? Some feel censorship is a violation of their rights. Others say censorship is a must in the violent, abusive world we call “society.” Who has the right to censor? Who doesn’t? What needs to be censored, and what doesn’t? The fact of the matter is that there are many pros and cons about internet censorship. Internet is important for understanding contemporary social change and internet is also a mirror of contemporary social change. No webpage comes to your home/office on its own. You switch on computer, you connect to internet and you search for so called vulgar, derogatory and defamatory contents. Then you blame the pornographic sites, then you blame the sites which spread racist hatred, then you blame the sites which cause blasphemy. It makes no sense. Who is bad, Internet or you? It is akin to ask doctors not to do sex determination test on fetuses to prevent female feticide. In India, social structure is such that female child is having lesser worth than male child and so thousands of parents want to abort female fetuses. Now this social evil must be tackled as social level and not at doctor’s level. If all parents decide that male child and female child are same, nobody will go for sex determination test. Same thing about corruption in India. Corruption in India is established as a socially acceptable phenomenon. How can you eradicate corruption by laws when majority population is indulging in corrupt practices? Social evil ought to be corrected by social reformers and not by enforcing laws enacted by the elite whose moral standard is different from moral standard of ordinary people.
_
Who makes laws?
Society makes laws. Laws against rape and murder exist because society wants it that way. Whether it is leader’s daughter’s rape or businessman’s wife’s rape or a beggars’ sister’s rape, law is applied equally because everybody agrees that rape is a rape no matter who is the victim. When it comes to criminalize objectionable content on internet, who is the victim? Does society wants such laws? Who defines what objectionable content is? Yes, as far as child pornography or provocation of violence is concerned, everybody in society agrees to make laws against it and such laws will work. What about pirated movies or videos or music? I am sorry to say that most people do watch pirated stuff. When society itself has downgraded its morals, how laws will prevent piracy? People will use circumvention techniques and see pirated movies. Some of the content on Internet criticizes various governments or regimes. So government wants to enact laws to censor it because it harms its interest but society has nothing to do with it because criticism of government or regime on Internet does not affect anybody in society. In such case, such a law is a repressive weapon to destroy freedom of expression and eventually society will either change government or disobey such laws.
_
Internet as human right:
The lead scientist of internet Vinton Cerf argues that the Internet cannot be considered a human right. According to him, human rights must be among the things we as humans need in order to lead healthy, meaningful lives, like freedom from torture or freedom of conscience. Technology is an enabler of rights, not a right itself. Also, technology is often a point of differentiation between the “haves” and “have-nots,” that does not necessarily make any piece of technology a human right. I respectfully disagree with Cerf. Look at my life. Traditional media has conspired to kill my talent and my existence. Had there been no internet, I was destined to die in oblivion and my talent would go waste. I am internet child. The internet is the greatest facilitator of freedom of expression and freedom of information that the world has ever seen. If freedom of expression is human right, then, its greatest facilitator cannot be separated from it. What happened in my life can happen in your life too. I therefore urge the UN to declare Internet as fundamental human right.
_
Internet and future generation:
Please read my article on “The Stress”. Stress in biology is defined as a response to change. Exposure to internet is a major change in environment of humans. Stress induced changes in genetic code including the creation of novel genes, the alteration of gene expression in development, and the genesis of major genomic rearrangements are carried forward in next generation to help next generation to adapt to stress. So internet exposure will also bring about change in genetic code to adapt to it. Inherited intelligence improvises in subsequent generation due changes in genetic code caused by exposure to various environmental factors including internet. Internet censorship leads to stifling of free flow of ideas, free flow of information and suppression of creativity. Massive internet censorship in countries like China, Cuba and North Korea leads to very little change in genetic codes of their population as compared to free societies of Europe, America and India whose population would have significant change in genetic code due to exposure to free internet. So subsequent populations of China, Cuba and North Korea will have weaker inherited intelligence as compared to inherited intelligence of free societies. In other words, exposure to free Internet will lead to development of more intelligent future generation.
_
The moral of the story:
1. Internet is a fundamental human right akin to freedom of expression and freedom of information.
_
2. Freedom of expression must coexist with freedom of information for it to make sense.
_
3. The right to freedom of expression must not infringe on other’s rights. The right to freedom of information must not violate other’s right to privacy. No fundamental human right is absolute. What we need is balance of everybody’s rights.
_
4. Arab Spring has been the wake-up call to governments around the world to recognize the power of the Internet, and social networking in particular, in building freedom and democracy. Freedom of Internet strengthens democracy.
_
5. Freedom of Internet leads to augmentation of economic growth.
_
6. Freedom of Internet unites people by bridging gaps of cultural, social and religious divide.
_
7. Every medium has different power and different audience, and therefore you cannot apply same yardstick of regulation of traditional media to Internet.
_
8. Internet needs to be regulated but by whom and how are the unresolved issues. Since Internet permeates boundaries of nations; and different nations have different cultures having different parameters of obscenity, morality and legality in the sense that what is legal and acceptable in one country may be illegal or unacceptable in another country; suggests that self-regulation is the best way forward otherwise we risk losing freedom of expression, freedom of information and liberty under pretext of regulating Internet.
_
9. Except for child pornography, copy right/intellectual property right infringement and incitement of violence; I see no reason for Internet censorship.
_
10. It is the responsibility of parents to regulate internet access for their children according to the prevailing culture of the society, family values and social structure by installing suitable filtering software in the home computer or by teaching them to make responsible decisions.
_
11. The progression of human civilization depends on expression of new ideas (however unpopular) and this can be achieved only by freedom of expression. Internet censorship curtails freedom of expression and thereby curtails progression of human civilization.
_
12. Exposure to free Internet will lead to development of more intelligent future generation.
_
Dr. Rajiv Desai. MD.
January 12, 2012
_
Postscript:
Metaphorically, I am an internet child. Had there been no internet, I would have lived in oblivion and died in oblivion. I am grateful to the inventors of computer and internet for my existence. Between the two extremes of free internet on one side and censored internet on the other side, I will go for free internet because advantages of free internet far outweigh advantages of censored internet.


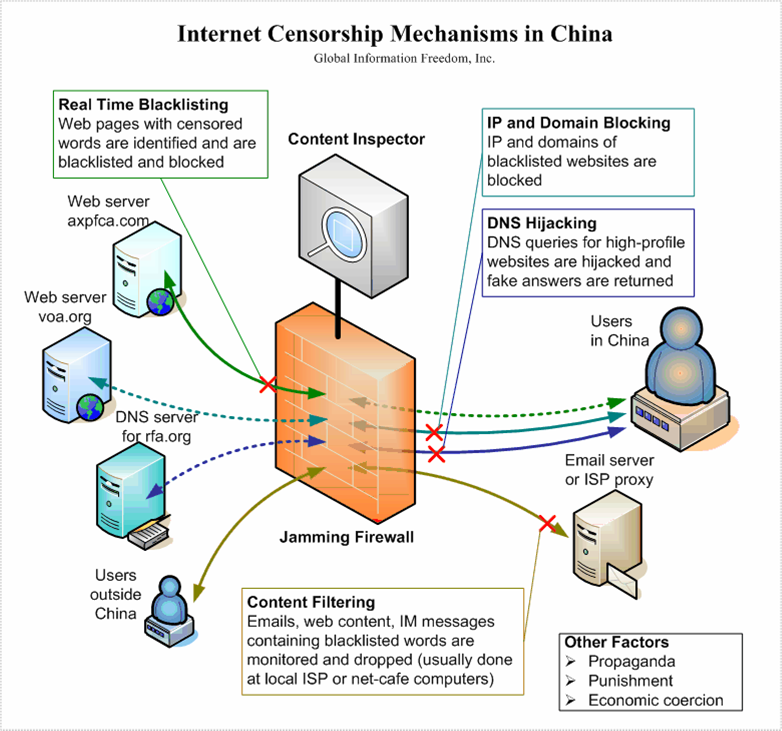
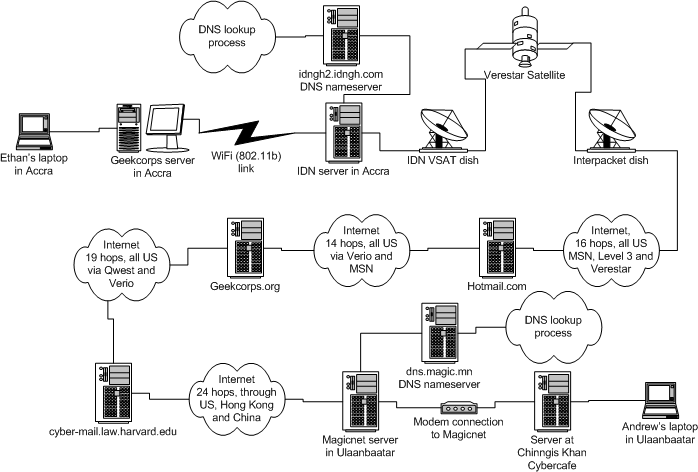
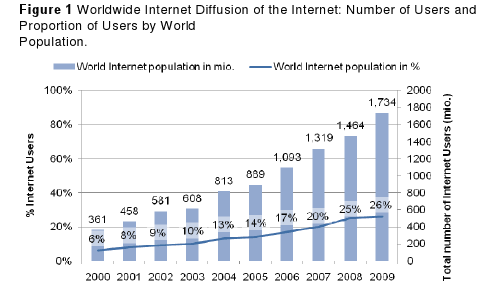
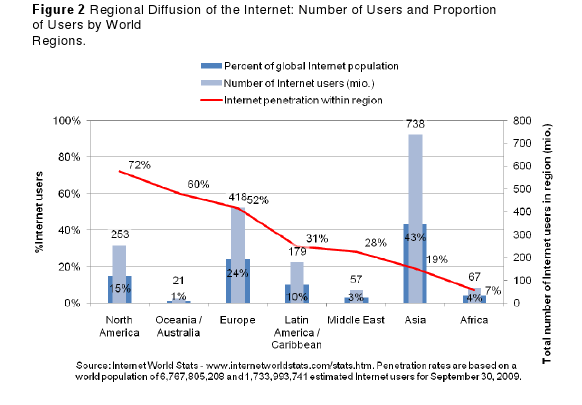
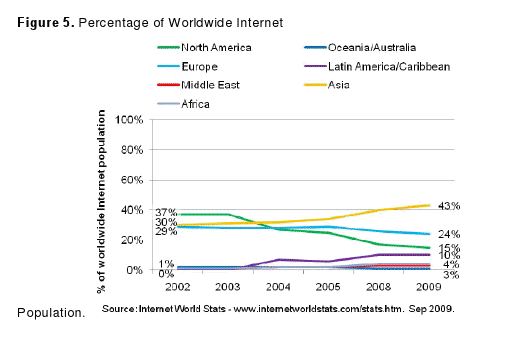
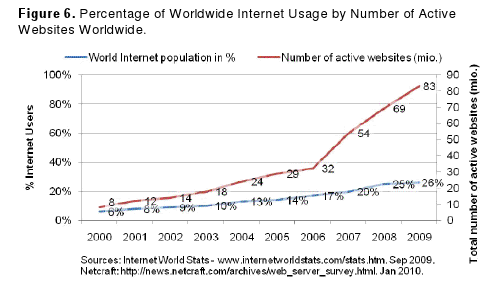
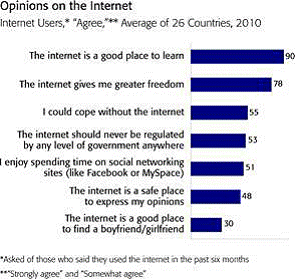
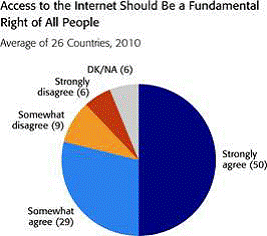
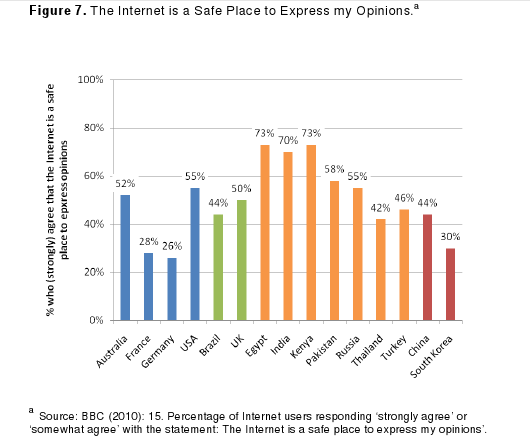
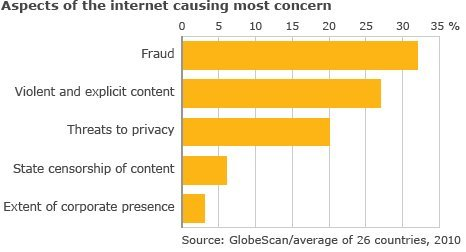
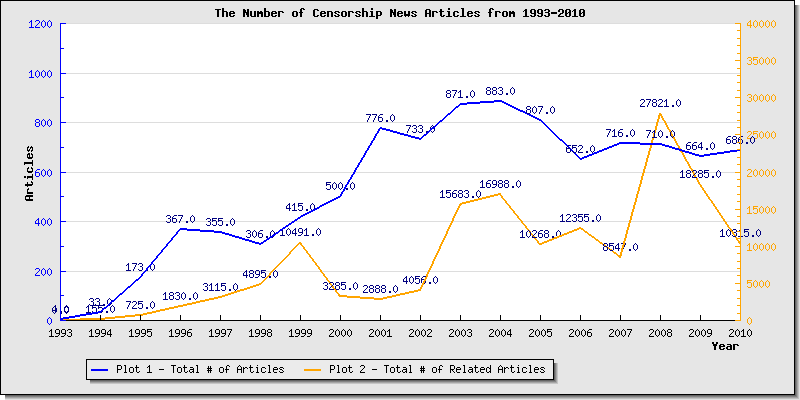
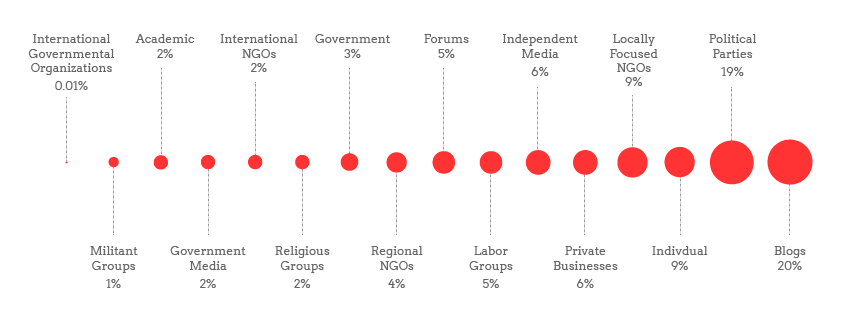
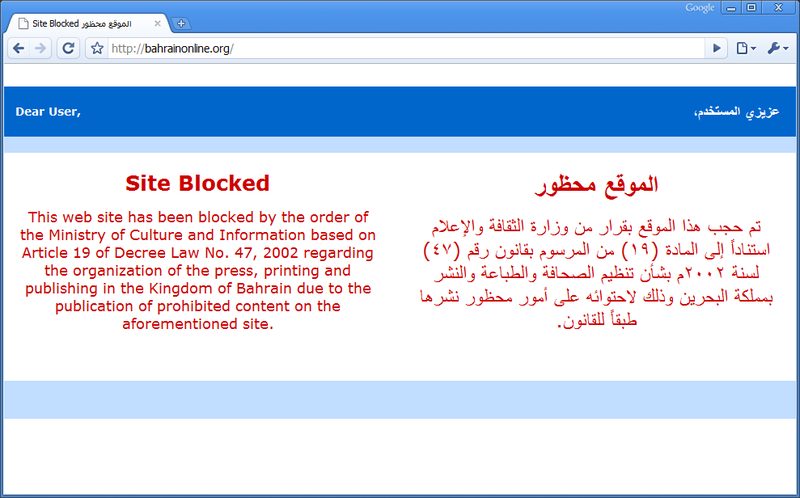
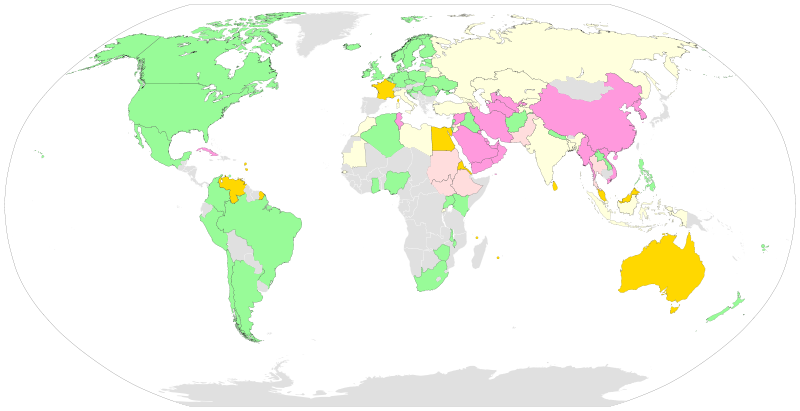
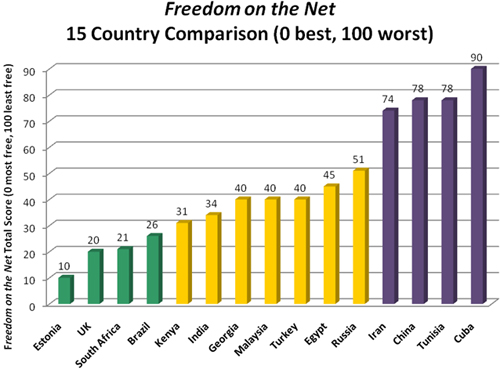
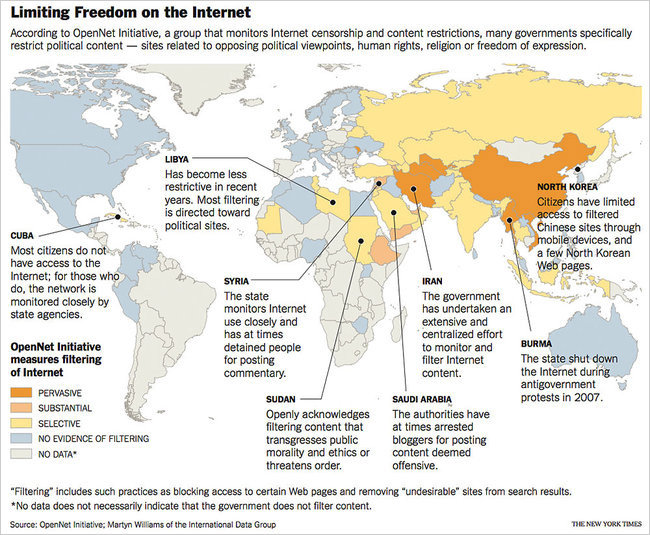
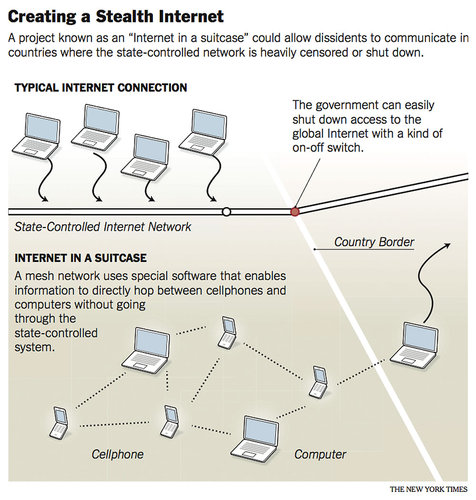
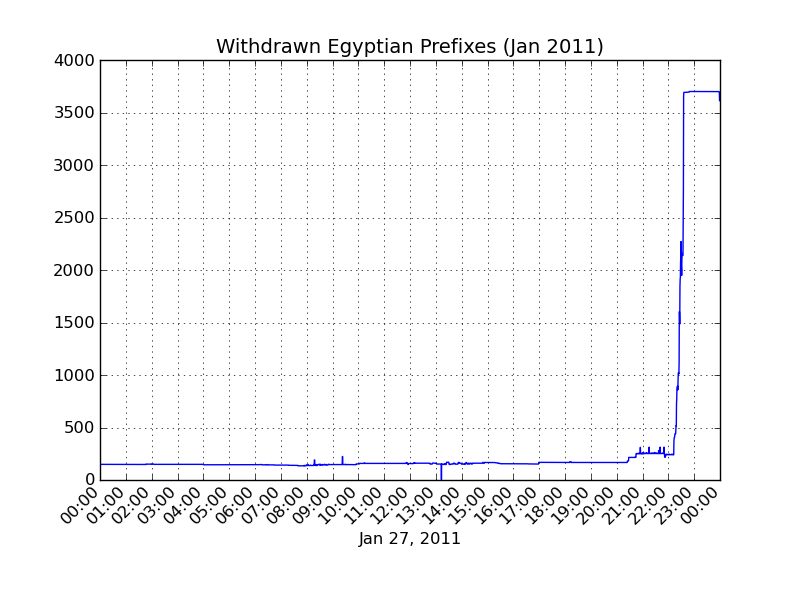
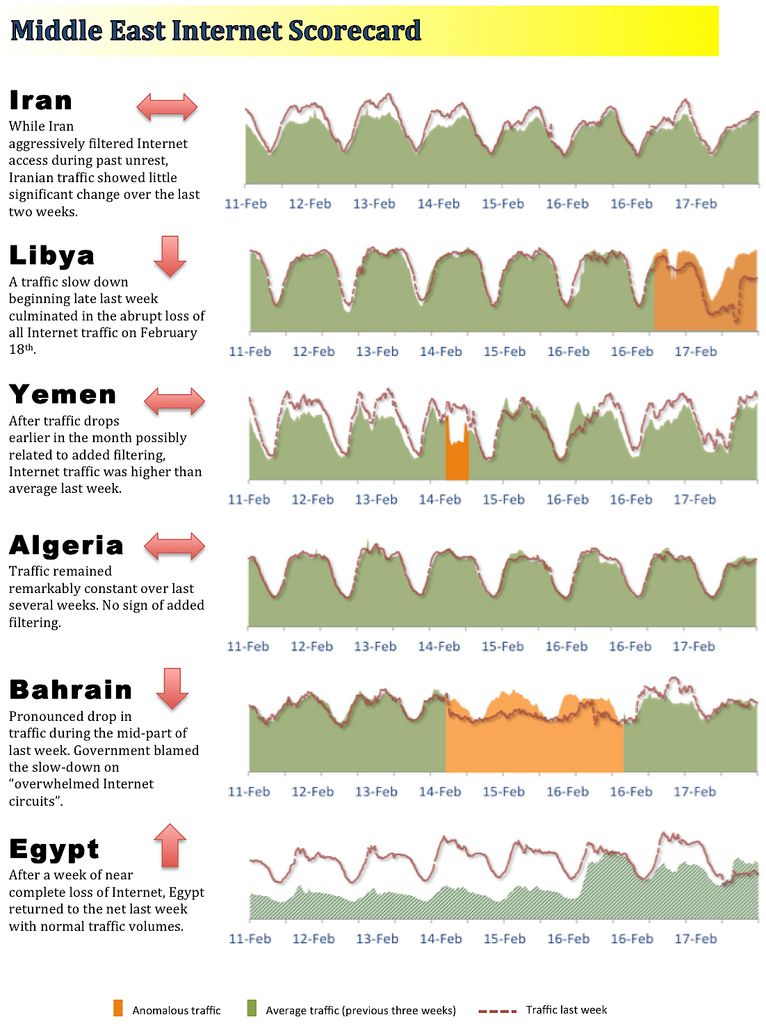
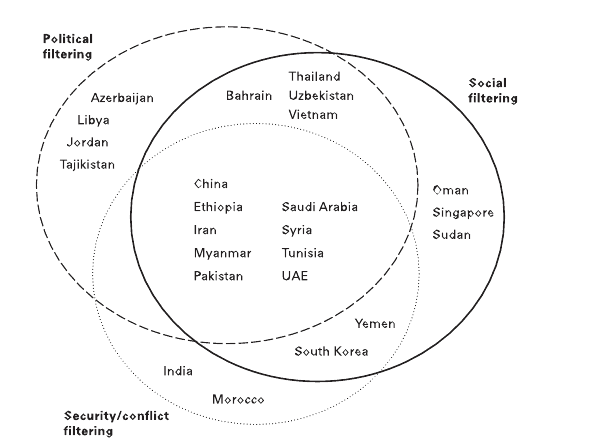
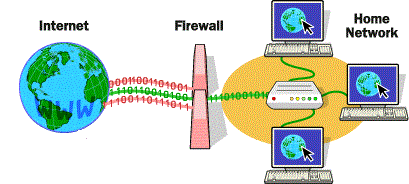

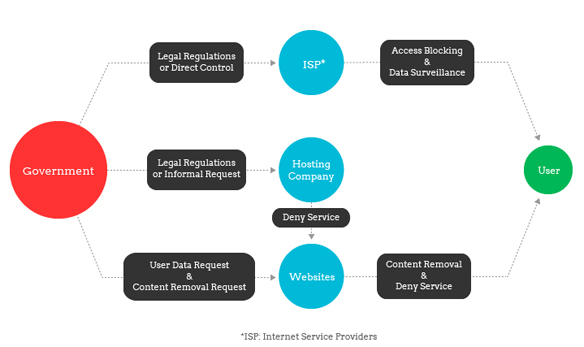
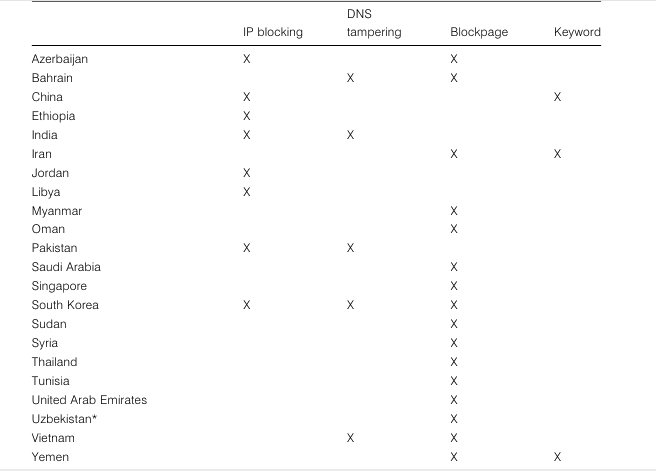
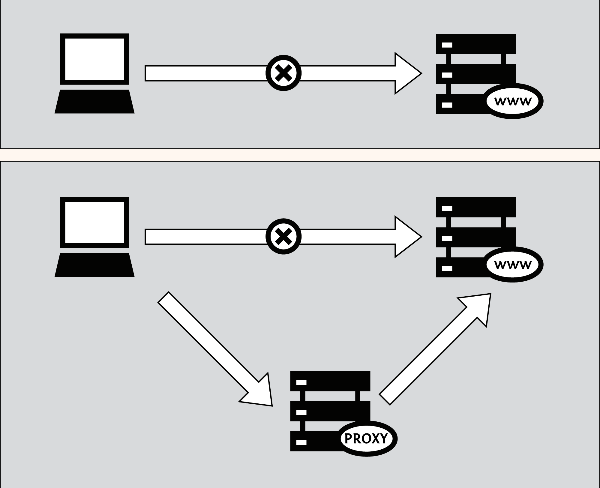
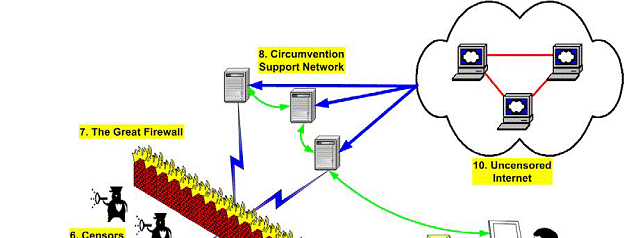
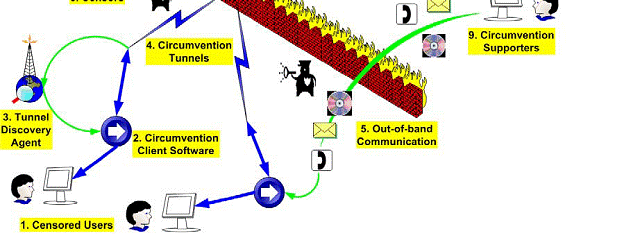
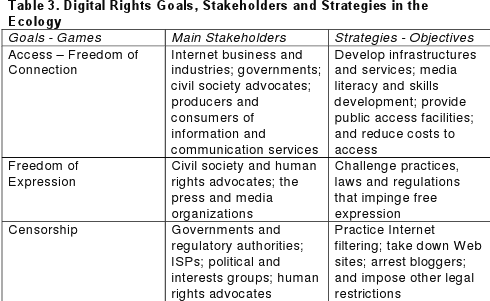
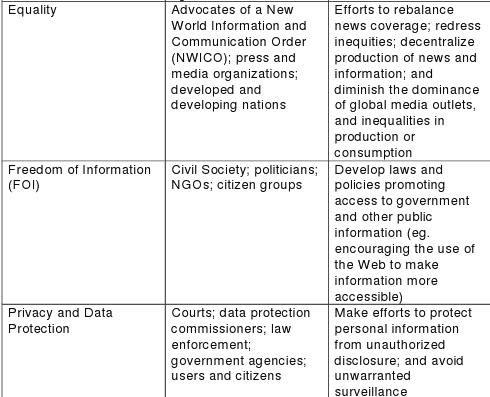
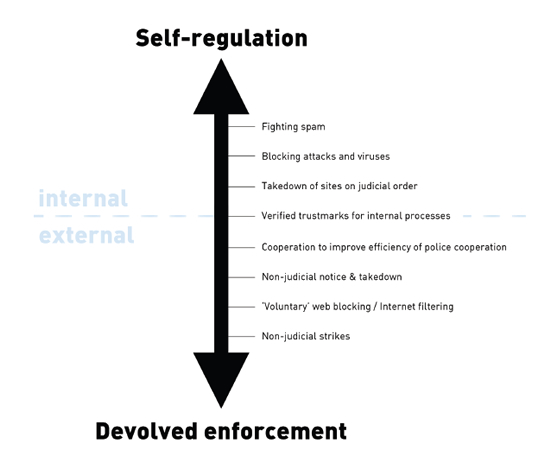
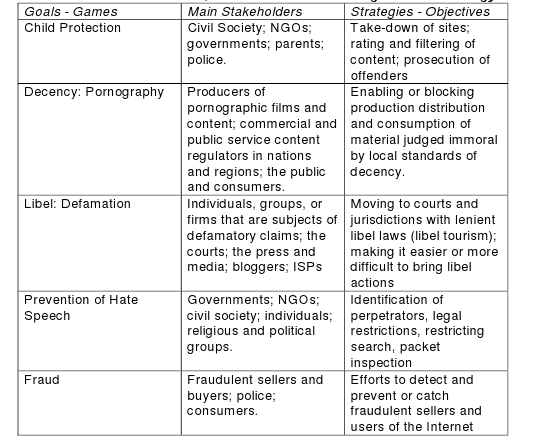
A big thank you for your blog post.Really looking forward to read more. Cool.
I’m impressed, I have to admit. Seldom do I come across a blog that’s both equally educative and engaging, and let me tell you, you’ve hit the nail on the head. The problem is an issue that not enough folks are speaking intelligently about. I’m very happy I found this during my hunt for something relating to this.|
Exactly what a man of capability! You have the capability to create great items that you can’t get anywhere. to envy
Wow, great blog post.Thanks Again. Fantastic.
Spot on with this write-up, I really feel this web site needs a lot more attention. Iíll probably be returning to see more, thanks for the information!
Good article. I am dealing with some of these issues as well..
Hi mates, its fantastic post concerning educationand
completely explained, keep it up all the time.
Saved as a favorite, I love your website!
Hi, I do think this is an excellent web site. I stumbledupon it 😉 I will come back once again since i have bookmarked it. Money and freedom is the greatest way to change, may you be rich and continue to help others.
I could not refrain from commenting. Very well written!
Excellent blog you have here.. Itís hard to find excellent writing like yours nowadays. I truly appreciate individuals like you! Take care!!
You’re so cool! I do not suppose I have read something like this before. So nice to discover somebody with a few genuine thoughts on this issue. Seriously.. thank you for starting this up. This site is something that is needed on the web, someone with a little originality!
Your style is unique in comparison to other folks I’ve read stuff from. Thanks for posting when you’ve got the opportunity, Guess I’ll just bookmark this page.
Way cool! Some extremely valid points! I appreciate you writing this post and the rest of the site is also really good.
Hi there! I simply would like to give you a big thumbs up for your great information you have here on this post. I will be coming back to your site for more soon.
This is a topic that’s near to my heart… Cheers! Where are your contact details though?
This is really interesting, You are a very skilled blogger. I have joined your feed and look forward to seeking more of your excellent post. Also, I have shared your website in my social networks!|
I am really inspired together with your writing abilities as smartly as with the structure in your blog. Is that this a paid theme or did you customize it your self? Anyway keep up the excellent quality writing, it’s uncommon to see a nice weblog like this one today..|
Way cool! Some very valid points! I appreciate you writing this post and the rest of the site is extremely good.
A fascinating discussion is worth comment. There’s no doubt that that you ought to publish more on this subject, it might not be a taboo matter but usually people do not discuss such issues. To the next! All the best!!|
Woah! I’m really loving the template/theme of this website. It’s simple, yet effective. A lot of times it’s very hard to get that “perfect balance” between user friendliness and visual appearance. I must say that you’ve done a superb job with this. Also, the blog loads super fast for me on Opera. Exceptional Blog!|
It’s a shame you don’t have a donate button! I’d definitely donate to this outstanding blog! I suppose for now i’ll settle for book-marking and adding your RSS feed to my Google account. I look forward to new updates and will share this blog with my Facebook group. Chat soon!|
great article!
Awesome blog article.Really looking forward to read more. Much obliged.
what a great read!
thanks for the amazing post
Pretty section of content. I just stumbled upon your weblog and in accession capital to assert that I acquire actually enjoyed account your blog posts. Anyway I’ll be subscribing to your feeds and even I achievement you access consistently quickly.
My brother suggested I might like this website. He was entirely right. This post actually made my day. You can not imagine simply how much time I had spent for this info! Thanks!
I don’t even know how I ended up here, but I thought this post was great. I don’t know who you are but certainly you are going to a famous blogger if you aren’t already 😉 Cheers!
Normally I do not learn post on blogs, however I wish to say that this write-up very forced me to take a look at and do so! Your writing style has been amazed me. Thanks, quite great article.
Excellent read, I just passed this onto a friend who was doing a little research on that. And he actually bought me lunch since I found it for him smile So let me rephrase that: Thanks for lunch!